Introduction to Information Security Lecture 6 Other Cryptographic














- Slides: 46

Introduction to Information Security Lecture 6: Other Cryptographic Primitives 2009. 7.

Contents 1. 2. 3. 4. 5. Mode of Operation Blind Signatures Secret Sharing and Threshold Cryptography Zero-knowledge Proofs Identification, Authentication 2

Mode of Operation 3

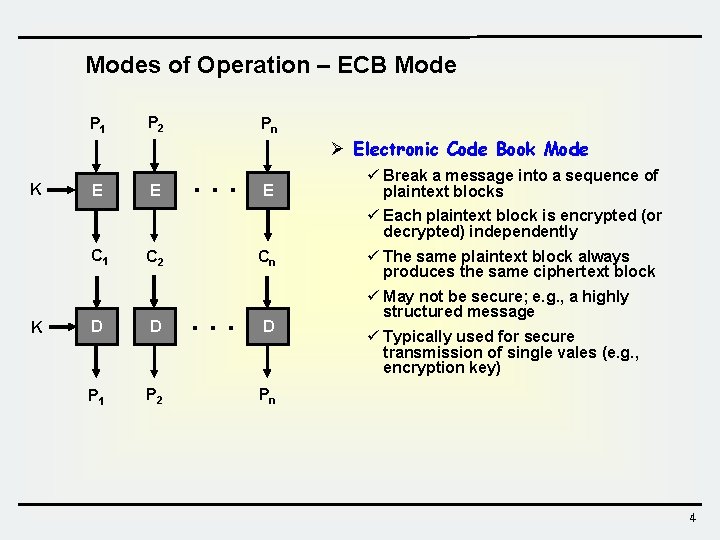
Modes of Operation – ECB Mode P 1 K E P 2 E Pn . . . E Ø Electronic Code Book Mode ü Break a message into a sequence of plaintext blocks ü Each plaintext block is encrypted (or decrypted) independently C 1 K Cn C 2 D D P 1 P 2 . . . D ü The same plaintext block always produces the same ciphertext block ü May not be secure; e. g. , a highly structured message ü Typically used for secure transmission of single vales (e. g. , encryption key) Pn 4

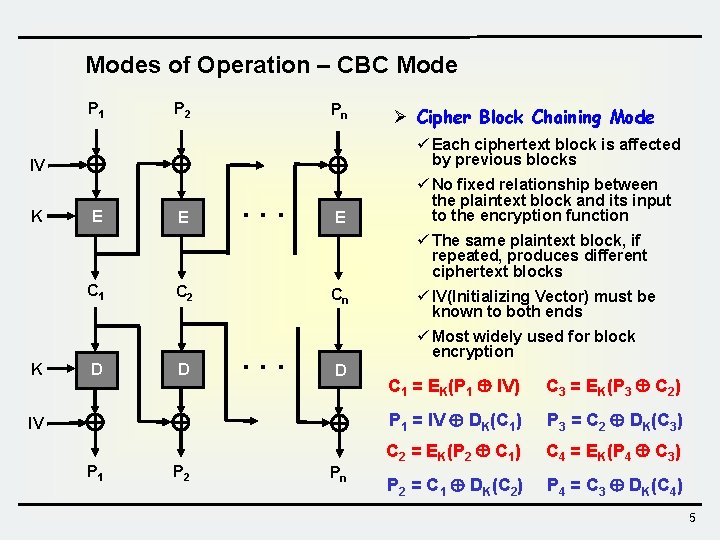
Modes of Operation – CBC Mode P 1 P 2 Pn Ø Cipher Block Chaining Mode IV ü Each ciphertext block is affected by previous blocks K ü No fixed relationship between the plaintext block and its input to the encryption function E E . . . E ü The same plaintext block, if repeated, produces different ciphertext blocks C 1 K D C 2 D Cn . . . ü Most widely used for block encryption D IV P 1 P 2 ü IV(Initializing Vector) must be known to both ends Pn C 1 = EK(P 1 IV) C 3 = EK(P 3 C 2) P 1 = IV DK(C 1) P 3 = C 2 DK(C 3) C 2 = EK(P 2 C 1) C 4 = EK(P 4 C 3) P 2 = C 1 DK(C 2) P 4 = C 3 DK(C 4) 5

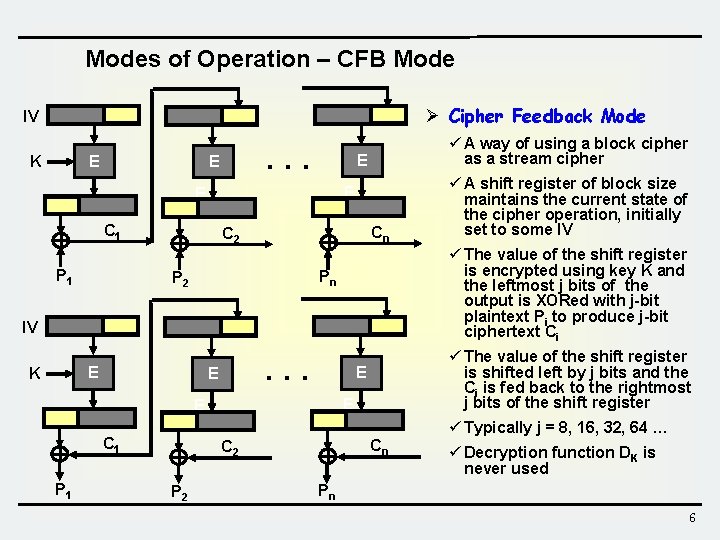
Modes of Operation – CFB Mode Ø Cipher Feedback Mode IV E K . . . E E C 1 P 1 ü A way of using a block cipher as a stream cipher Cn C 2 ü The value of the shift register is encrypted using key K and the leftmost j bits of the output is XORed with j-bit plaintext Pi to produce j-bit ciphertext Ci Pn P 2 IV E K . . . E E ü Typically j = 8, 16, 32, 64 … C 1 P 1 ü The value of the shift register is shifted left by j bits and the Ci is fed back to the rightmost j bits of the shift register E E ü A shift register of block size maintains the current state of the cipher operation, initially set to some IV Cn C 2 P 2 ü Decryption function DK is never used Pn 6

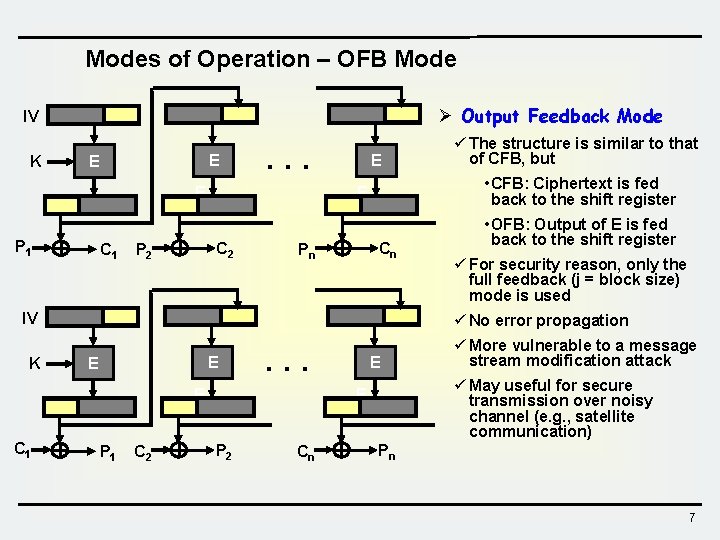
Modes of Operation – OFB Mode Ø Output Feedback Mode IV K E E . . . E P 1 C 1 • CFB: Ciphertext is fed back to the shift register E C 2 P 2 E Cn Pn IV K • OFB: Output of E is fed back to the shift register ü For security reason, only the full feedback (j = block size) mode is used ü No error propagation E E . . . E C 1 ü The structure is similar to that of CFB, but P 1 C 2 E ü May useful for secure transmission over noisy channel (e. g. , satellite communication) E P 2 Cn ü More vulnerable to a message stream modification attack Pn 7

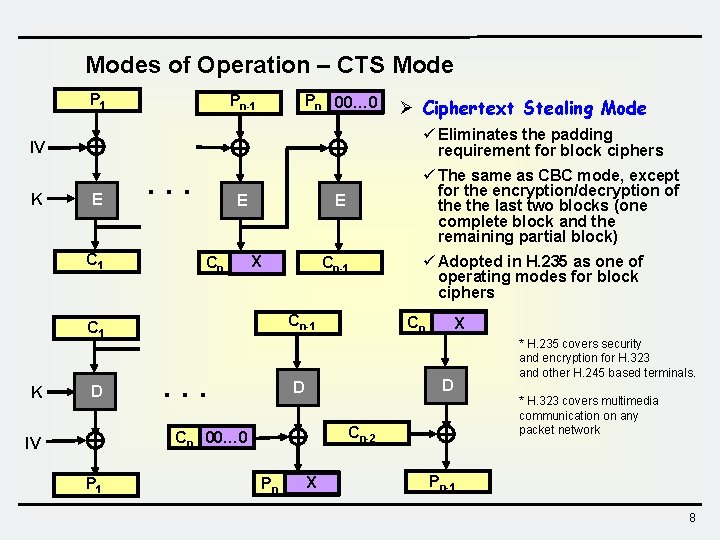
Modes of Operation – CTS Mode P 1 Pn-1 Pn 00… 0 ü Eliminates the padding requirement for block ciphers IV K E C 1 . . . Cn IV D E P 1 ü The same as CBC mode, except for the encryption/decryption of the last two blocks (one complete block and the remaining partial block) E E X Cn-1 C 1 K Ø Ciphertext Stealing Mode . . . Cn E Pn X D D Cn 00… 0 ü Adopted in H. 235 as one of operating modes for block ciphers Cn-2 X E * H. 235 covers security and encryption for H. 323 and other H. 245 based terminals. * H. 323 covers multimedia communication on any packet network Pn-1 8

Cryptographic Protocols 9

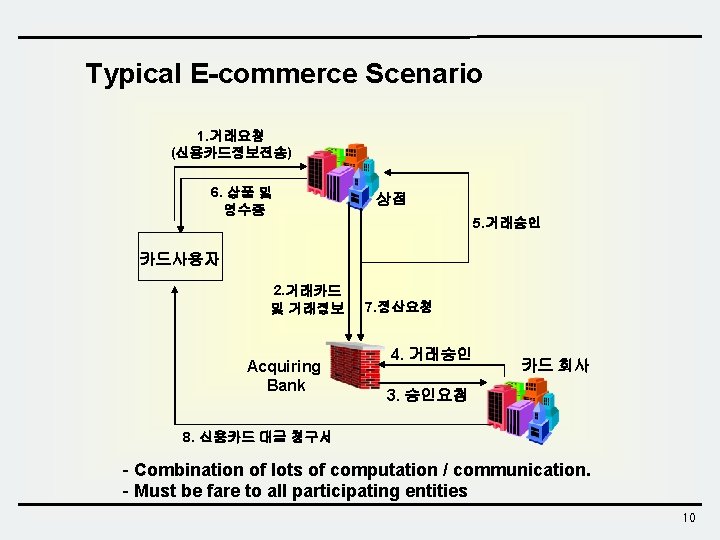
Typical E-commerce Scenario 1. 거래요청 (신용카드정보전송) 6. 상품 및 영수증 상점 5. 거래승인 카드사용자 2. 거래카드 및 거래정보 Acquiring Bank 7. 정산요청 4. 거래승인 카드 회사 3. 승인요청 8. 신용카드 대금 청구서 - Combination of lots of computation / communication. - Must be fare to all participating entities 10

Cryptographic Protocols Ø Cryptographic algorithms ü Algorithm executed by a single entity ü Algorithms performing cryptographic functions ü Encryption, Hash, digital signature, etc… Ø Cryptographic protocols ü Protocols executed between multiple entities through pre-defined steps of communication performing security-related functions ü Perform more complicated functions than what the primitive algorithms can provide ü Primitives: Key agreement, secret sharing, blind signature, coin toss, secure multiparty computations, etc … ü Complex application protocols: e-commerce, e-voting, e-auction, etc … 11

Cryptographic Protocols Ø Protocols ü Designed to accomplish a task through a series of communication steps, involving two or more entities Ø Cryptographic Protocols ü Protocols that use cryptography ü Non-face-to-face interaction over an open network ü Cannot trust other entities Threat Entity A Internet Entity B 12

Security Requirements in Protocols ü Confidentiality ü Integrity ü Authentication ü Non-repudiation ü Correctness ü Verifiability ü Fairness Combinations of these requirements according to applications ü Anonymity ü Privacy ü Robustness ü Efficiency ü Etc…… 13

Protocol Primitives Ø Coin Toss game over Communication Network ü Two parties play coin toss game over the communication network ü Can it be made fair? Ø Blind Signatures ü Signer signs a document without knowledge of the document and the resulting signature ü Message and the resulting signature are hidden from the signer ü Many applications which require anonymity or privacy ü Digital cash, e-voting Ø Key Agreements ü Two or more parties agree on a secret key over communication network in such a way that both influence the outcome. ü Do not require any trusted third party (TTP) 14

Protocol Primitives Ø Secret Sharing ü Distribute a secret amongst a group of participants ü Each participant is allocated a share of the secret ü Secret can be reconstructed only when the shares are combined together ü Individual shares are of no use on their own. Ø Threshold Cryptography ü A message is encrypted using a public key and the corresponding private key is shared among multiple parties. ü In order to decrypt a ciphertext, a number of parties exceeding a threshold is required to cooperate in the decryption protocol. 15

Protocol Primitives Ø Zero-knowledge Proofs ü An interactive method for one party to prove to another that a (usually mathematical) statement is true, without revealing anything other than the validity of the statement. Ø Identification, Authentication ü Over the communication network, one party, Alice, shows to another party, Bob, that she is the real Alice. ü Allows one party, Alice, to prove to another party, Bob, that she possesses secret information without revealing to Bob what that secret information is. 16

Application Protocols Ø Electronic Commerce ü SET (Secure Electronic Transaction) – Credit card transaction ü Digital cash, micropayment, e-check, e-money ü e-auction ü e-banking Ø e-government Ø e-voting Ø Fair exchange of digital signature (for contract signing) Ø Application Scenarios Ø Traditional applications transfer to electronic versions Ø New applications appear with the help of crypto 17

Blind Signatures 18

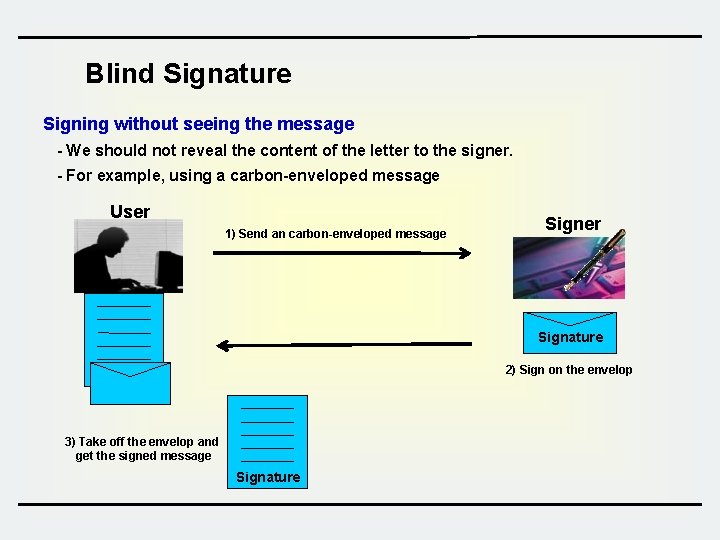
Blind Signature Signing without seeing the message - We should not reveal the content of the letter to the signer. - For example, using a carbon-enveloped message User 1) Send an carbon-enveloped message Signer Signature 2) Sign on the envelop 3) Take off the envelop and get the signed message Signature

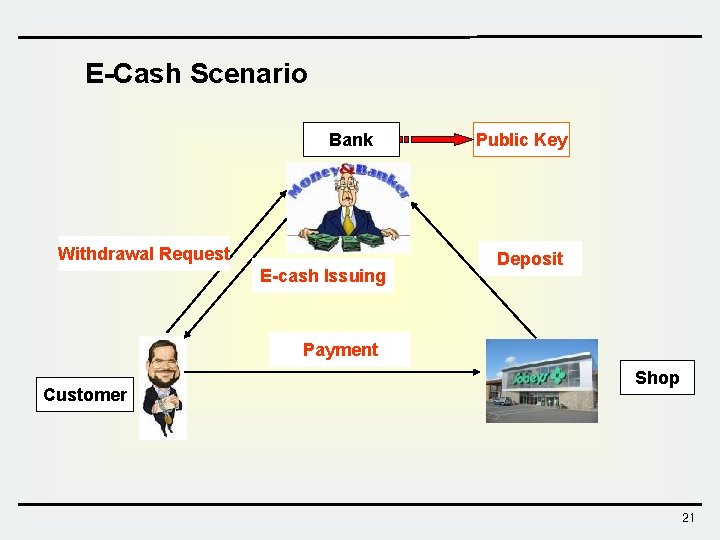
Motivation of Blind Signature v One interesting question of public key cryptosystem is whether we can use digital signature to create some form of digital currency. The scenario is described as follows: 1) A bank published his public key. 2) When one of his customer makes a withdrawal from his account, the bank provides it with a digitally signed note that specifies the amount withdrawn. 3) The customer can present it to a merchant, who can then verify the bank’s signature. 4) Upon completing a transaction, the vender can then remit the note to the bank, which will then credit the vendor the amount specified in the note. 5) This note is, in effect, a digital monetary instrument, we called it as “Electronic Cash or E-Cash”. v Privacy issue of digital cash? ? ? ü The bank can easily trace a cash to a specific user. 20

E-Cash Scenario Bank Withdrawal Request E-cash Issuing Public Key Deposit Payment Customer Shop 21

David Chaum’s Blind Signature v David Chaum proposed a very elegant solution to this problem, known as blind signature. He is also named as the “father of E-cash” 22

Blind Signature Blind signature scheme is a protocol that allows the provider to obtain a valid signature for a message m from the signer without him seeing the message and its signature. If the signer sees message m and its signature later, he can verify that the signature is genuine, but he is unable to link the message-signature pair to the particular instance of the signing protocol which has led to this pair. Many applications ü Useful when values need to be certified, yet anonymity should be preserved ü e-cash, e-voting 23

Blind Signature Protocol Steps 1) Alice takes the document and uses a “blinding factor” to blind the document. (Blinding Phase) 2) Alice sends the blinded document to Bob and Bob signs the blinded document. (Signing Phase) 3) Alice can remove the blinding factor and obtain the signature on the original document. (Unblinding Phase) 24

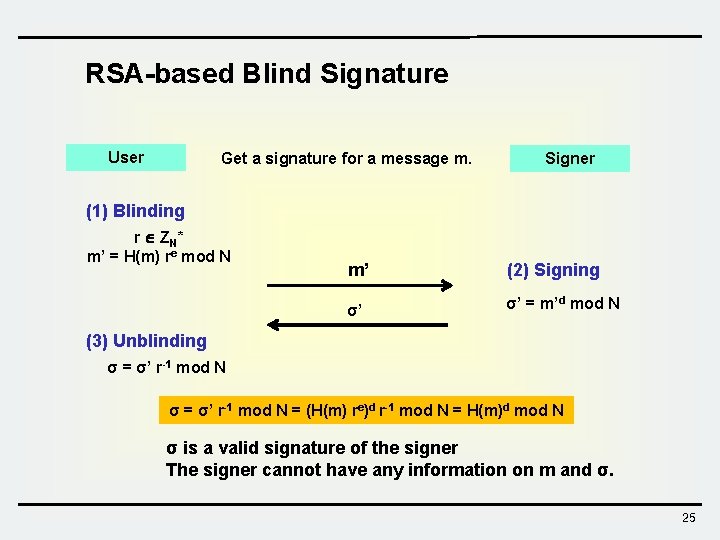
RSA-based Blind Signature User Get a signature for a message m. Signer (1) Blinding r Z N* m’ = H(m) re mod N m’ (2) Signing σ’ σ’ = m’d mod N (3) Unblinding σ = σ’ r-1 mod N = (H(m) re)d r-1 mod N = H(m)d mod N σ is a valid signature of the signer The signer cannot have any information on m and σ. 25

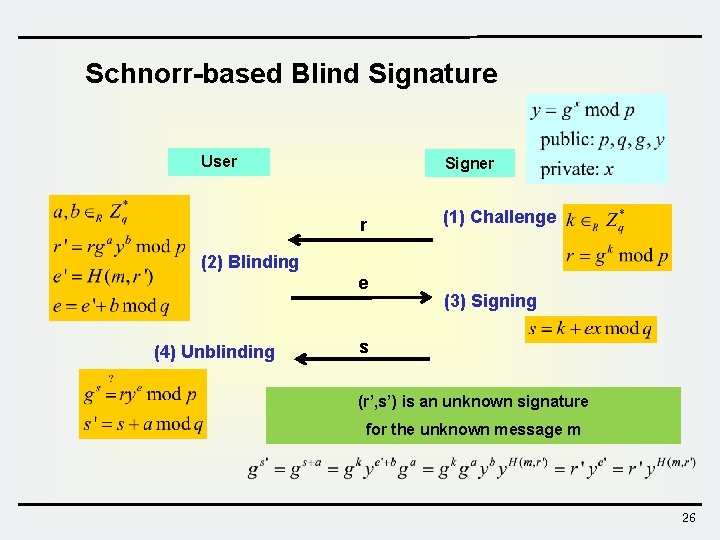
Schnorr-based Blind Signature User Signer r (1) Challenge (2) Blinding e (4) Unblinding (3) Signing s (r’, s’) is an unknown signature for the unknown message m 26

Zero-Knowledge Proofs 27

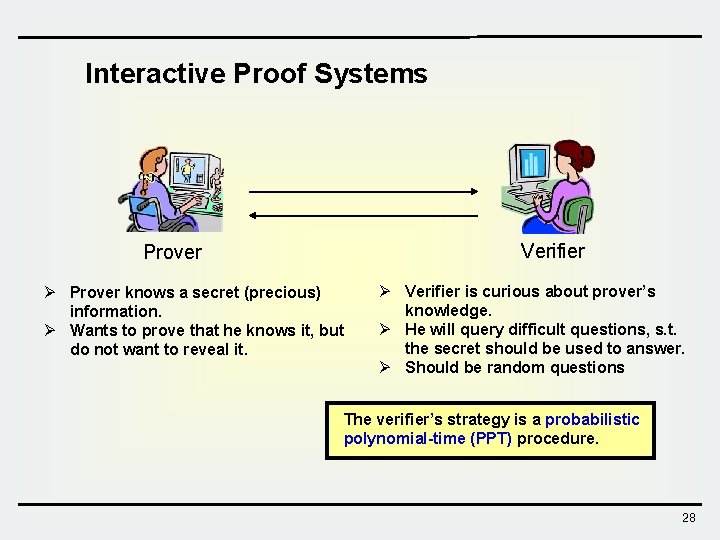
Interactive Proof Systems Verifier Prover Ø Prover knows a secret (precious) information. Ø Wants to prove that he knows it, but do not want to reveal it. Ø Verifier is curious about prover’s knowledge. Ø He will query difficult questions, s. t. the secret should be used to answer. Ø Should be random questions The verifier’s strategy is a probabilistic polynomial-time (PPT) procedure. 28

Ali Baba’s Cave • Alice wants to prove to Bob that she knows how to open the secret door between A and B, but will not reveal the secret itself. • Procedure – Alice and Bob go to cave – Alice goes to A or B randomly (Bob cannot see) – Bob tells Alice to come from A or B – If Alice knows the secret, she can appear from the correct side of the cave every time • Bob repeats as many times until he believe Alice knows the secret to open the secret door • How about Trudy? Can he convince Bob without knowing the secret? 29

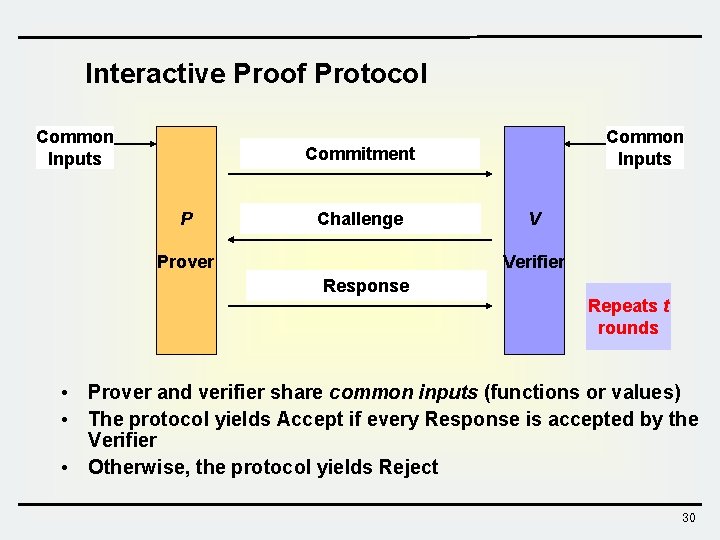
Interactive Proof Protocol Common Inputs Commitment P Challenge Prover V Verifier Response Repeats t rounds • Prover and verifier share common inputs (functions or values) • The protocol yields Accept if every Response is accepted by the Verifier • Otherwise, the protocol yields Reject 30

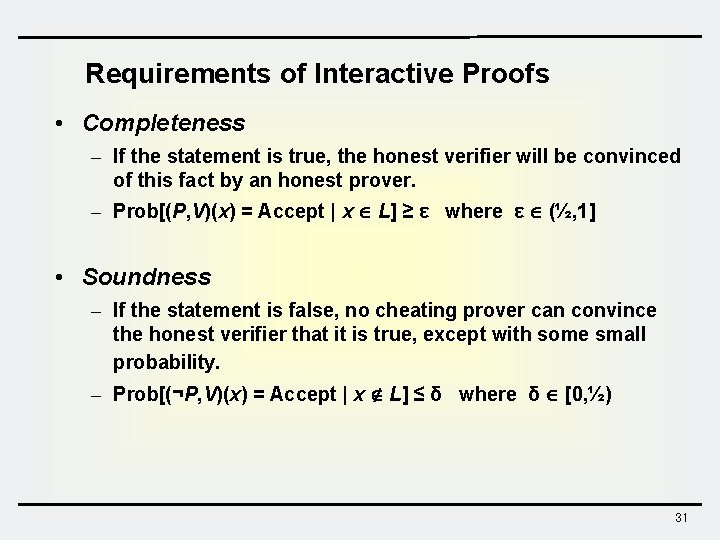
Requirements of Interactive Proofs • Completeness – If the statement is true, the honest verifier will be convinced of this fact by an honest prover. – Prob[(P, V)(x) = Accept | x L] ≥ ε where ε (½, 1] • Soundness – If the statement is false, no cheating prover can convince the honest verifier that it is true, except with some small probability. – Prob[(¬P, V)(x) = Accept | x Ï L] ≤ δ where δ [0, ½) 31

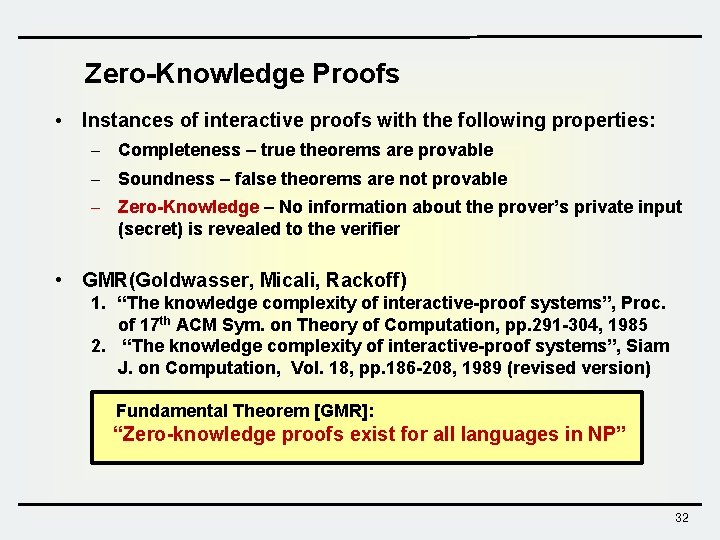
Zero-Knowledge Proofs • Instances of interactive proofs with the following properties: – Completeness – true theorems are provable – Soundness – false theorems are not provable – Zero-Knowledge – No information about the prover’s private input (secret) is revealed to the verifier • GMR(Goldwasser, Micali, Rackoff) 1. “The knowledge complexity of interactive-proof systems”, Proc. of 17 th ACM Sym. on Theory of Computation, pp. 291 -304, 1985 2. “The knowledge complexity of interactive-proof systems”, Siam J. on Computation, Vol. 18, pp. 186 -208, 1989 (revised version) Fundamental Theorem [GMR]: “Zero-knowledge proofs exist for all languages in NP” 32

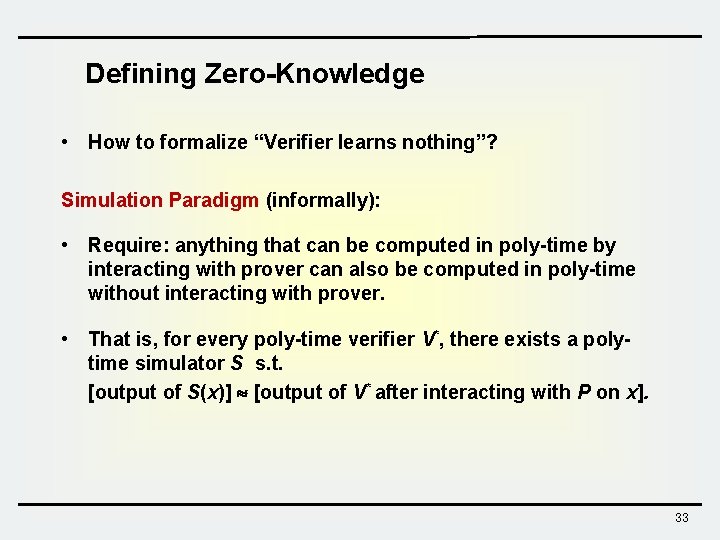
Defining Zero-Knowledge • How to formalize “Verifier learns nothing”? Simulation Paradigm (informally): • Require: anything that can be computed in poly-time by interacting with prover can also be computed in poly-time without interacting with prover. • That is, for every poly-time verifier V*, there exists a polytime simulator S s. t. [output of S(x)] [output of V* after interacting with P on x]. 33

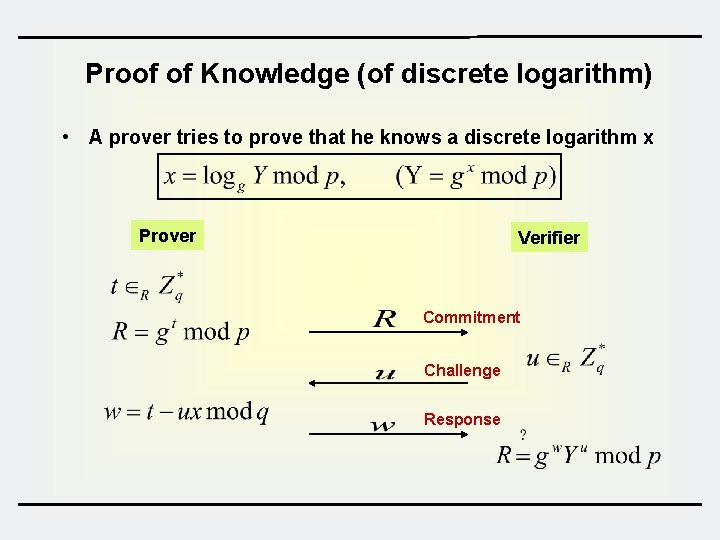
Proof of Knowledge (of discrete logarithm) • A prover tries to prove that he knows a discrete logarithm x Prover Verifier Commitment Challenge Response

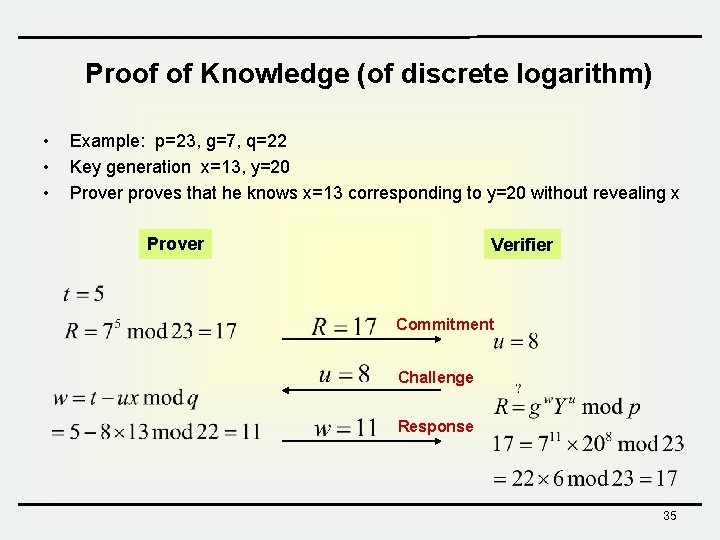
Proof of Knowledge (of discrete logarithm) • • • Example: p=23, g=7, q=22 Key generation x=13, y=20 Prover proves that he knows x=13 corresponding to y=20 without revealing x Prover Verifier Commitment Challenge Response 35

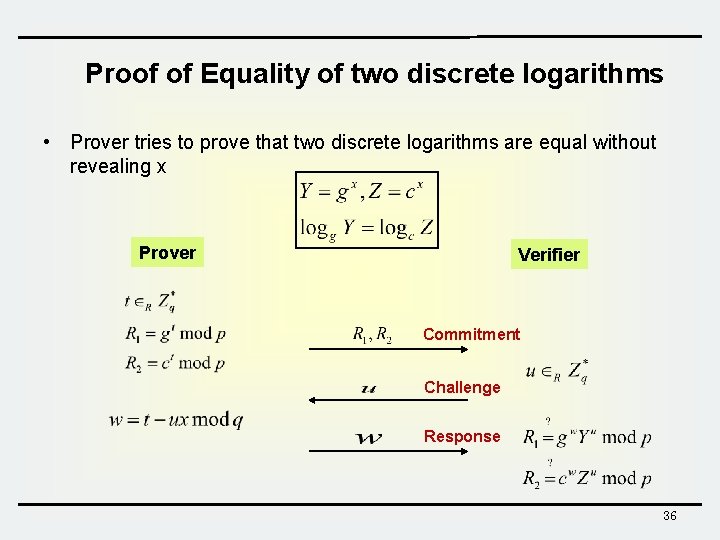
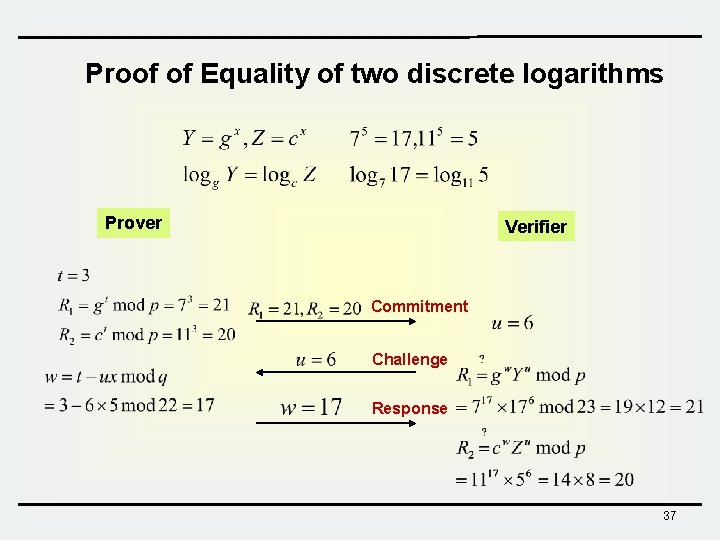
Proof of Equality of two discrete logarithms • Prover tries to prove that two discrete logarithms are equal without revealing x Prover Verifier Commitment Challenge Response 36

Proof of Equality of two discrete logarithms Prover Verifier Commitment Challenge Response 37

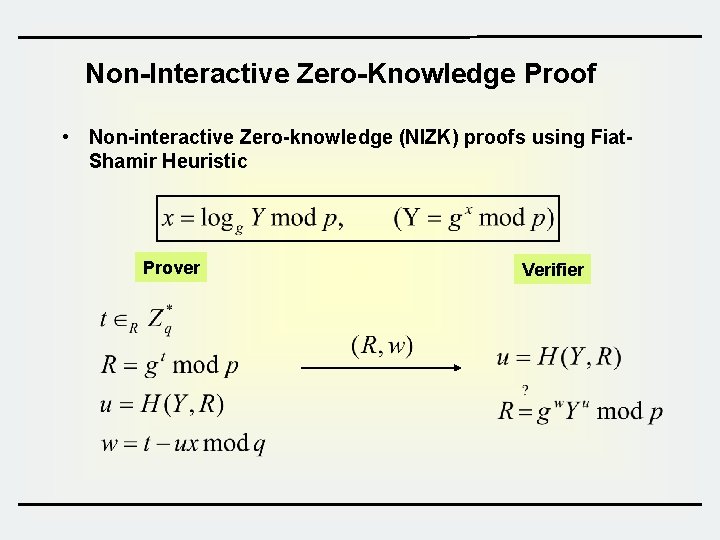
Non-Interactive Zero-Knowledge Proof • Non-interactive Zero-knowledge (NIZK) proofs using Fiat. Shamir Heuristic Prover Verifier

Identification, Authentication 39

Authentication v Entity Authentication (Identification) • Over the communication network, one party, Alice, shows to another party, Bob, that she is the real Alice. • Authenticate an entity by presenting some identification information • Should be secure against various attacks • Through an interactive protocols using secret information v Message Authentication • Show that a message was generated by an entity • Using digital signature or MAC 40

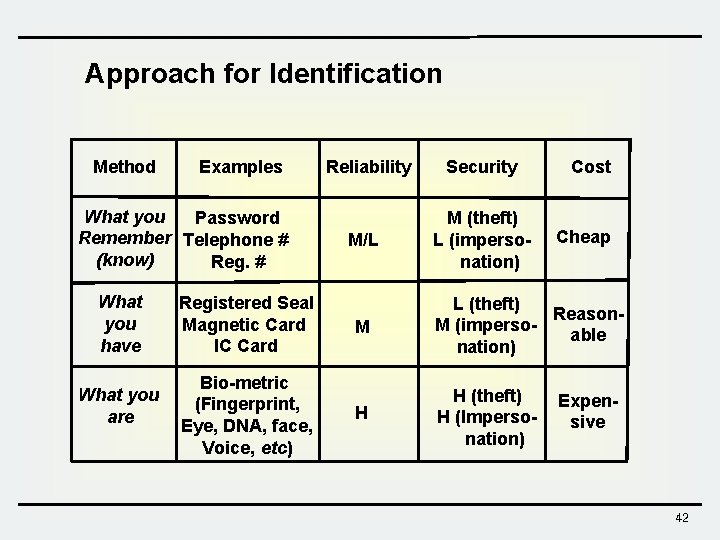
Approach for Identification v Using Something Known • Password, PIN v Using Something Possessed • IC card, Hardware token v Using Something Inherent • Biometrics 41

Approach for Identification Method Examples What you Password Remember Telephone # (know) Reg. # What you have Registered Seal Magnetic Card IC Card What you are Bio-metric (Fingerprint, Eye, DNA, face, Voice, etc) Reliability Security M/L M (theft) L (impersonation) Cost Cheap M L (theft) Reason. M (impersoable nation) H H (theft) H (Impersonation) Expensive 42

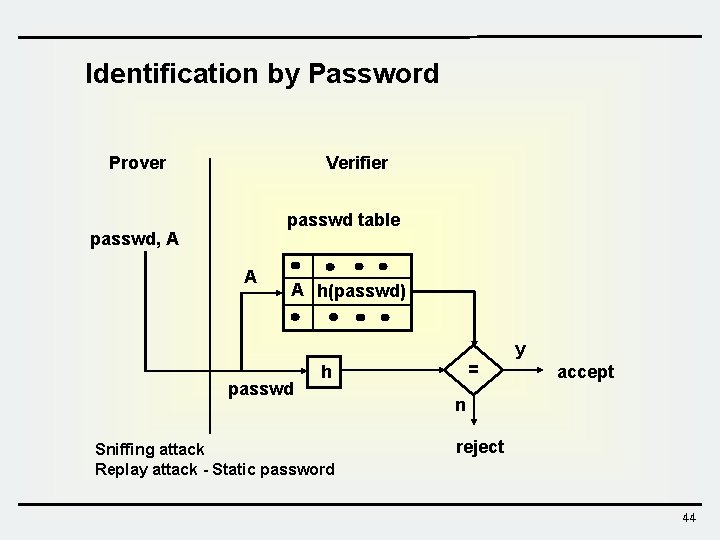
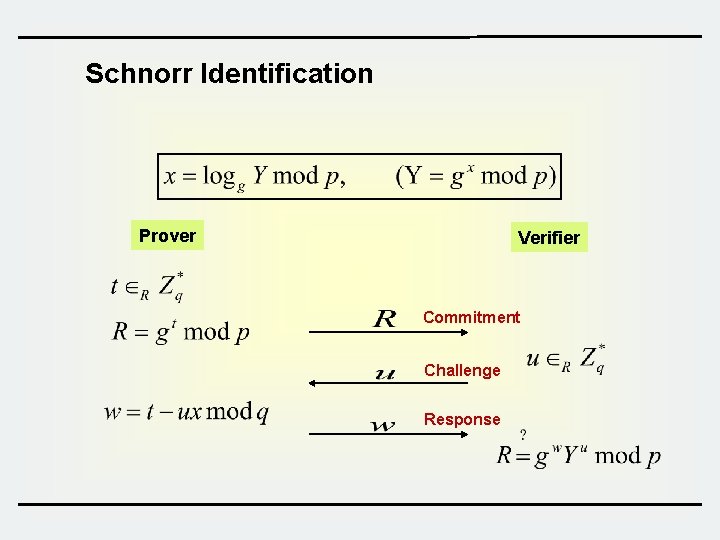
Approach for Identification v Password-based scheme (weak authentication) – crypt passwd under UNIX – one-time password v Challenge-Response scheme (strong authentication) – Symmetric cryptosystem – MAC (keyed-hash) function – Asymmetric cryptosystem v Using Cryptographic Protocols – Fiat-Shamir identification protocol – Schnorr identification protocol, etc 43

Identification by Password Prover Verifier passwd table passwd, A A A h(passwd) passwd = h Sniffing attack Replay attack - Static password y accept n reject 44

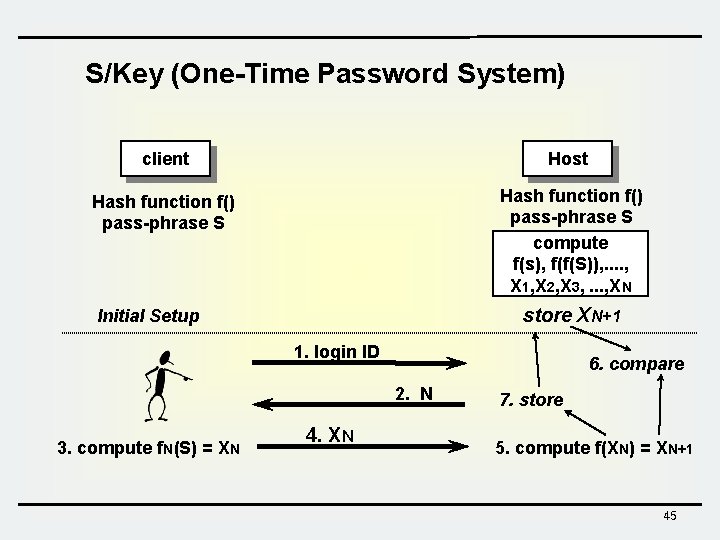
S/Key (One-Time Password System) client Host Hash function f() pass-phrase S compute f(s), f(f(S)), . . , X 1, X 2, X 3, . . . , XN store XN+1 Initial Setup 1. login ID 6. compare 2. N 3. compute f. N(S) = XN 4. XN 7. store 5. compute f(XN) = XN+1 45

Schnorr Identification Prover Verifier Commitment Challenge Response