Exploring the Weakest Link A Study of Personal





![Insecure Password Practices [Adams & Sasse, 1999] • Posting written passwords in obvious locations. Insecure Password Practices [Adams & Sasse, 1999] • Posting written passwords in obvious locations.](https://slidetodoc.com/presentation_image_h2/ba617e37c501c1890801d89ba5887e83/image-6.jpg)
















- Slides: 25

Exploring the Weakest Link: A Study of Personal Password Security Clark Thomborson Gilbert Notoatmodjo Computer Science Department, The University of Auckland

Contents 1. 2. 3. 4. Introduction Our Study and Ethical Considerations Results Recommendations and Future Work

Password Authentication • The most commonly used authentication method. • Practical, simple, easy to use, and cost effective. • The identity of an individual is verified only by his/her ability to present a single word.

Four Categories of Attack • If an adversary learns a single word, they will gain access to victim’s account…. 1. Attacks on the password server (at the passwords while “at rest”), for example a password guessing attack. Attacks on the communication channel (at the passwords while “in motion”), for example replay, eavesdropping, and man-in-the-middle attacks. Attacks on password client (at the passwords while “in use”), for example a password sniffer using a keylogger Trojan. Attacks on the user, for example social engineering, shoulder surfing, dumpster diving, and phishing. 2. 3. 4.

Attacks on the User • Only requires a minimal level of technical knowledge, and yet may have a high chance of success. • Users are protected only by security policies and guidelines, which may be unknown, neglected, or avoided. • Kevin Mitnick’s testimonial before the US Congress: I was so successful in [the social engineering] line of attack that I rarely had to resort to a technical attack. . . Companies can spend millions of dollars on firewalls, encryption, and secure access devices, and it’s money wasted, because none of these measures address the weakest link in the security chain.
![Insecure Password Practices Adams Sasse 1999 Posting written passwords in obvious locations Insecure Password Practices [Adams & Sasse, 1999] • Posting written passwords in obvious locations.](https://slidetodoc.com/presentation_image_h2/ba617e37c501c1890801d89ba5887e83/image-6.jpg)
Insecure Password Practices [Adams & Sasse, 1999] • Posting written passwords in obvious locations. • Creating weak passwords based on obvious dictionary words or personal information, such as – – birth date, personal names, nicknames, names of partners or favorite celebrities, even the word ‘password’! • Sharing passwords with friends and work colleagues. – This is largely due to convenience and practical reasons, or as a result of social pressure.

Password Reuse • Another risky practice! • The risk of password reuse is that if a password is compromised, all other accounts which share the same password are also compromised – ‘domino effect’. • Password reuse is almost inevitable for most users, due to the rising number of e-commerce and other services requiring passwords. • A recent study showed that password reuse tends to increase as people accumulate more accounts.

The Not-So-Effective Remedies 1. Forcing users to change their passwords on a regular basis. 2. Prohibiting reuse of passwords. Why are these remedies ineffective? • Users will be unable to remember a large number of passwords. • Users may react to these remedies by engaging in unsafe practices (weak passwords, written passwords, shared passwords).

The Password Problem • Password management is a non-trivial problem which will only worsen over time, unless we provide users with appropriate assistance: – password management systems and – account management systems. • These systems will not be effective unless we understand – the factors that influence users’ password usage behavior, and – how users would like to organize their accounts and passwords.

Our Study • We focused our investigation on how users’ perceptions of their accounts and passwords affect the way in which they manage their accounts and passwords. Our organising hypothesis: • Users manage their passwords and accounts by mentally classifying their accounts and passwords using various perceived similarities, such as – importance of accounts, and – length of passwords.

Ethical Issues and Considerations • Ideally, we would gather and analyze real passwords and accounts from our survey participants. However: – Our participants might not trust us to handle their passwords and accounts safely. – If a participant’s password was stolen by someone else, then we might be falsely accused. • We designed our survey instrument to answer our questions without asking participants to reveal their passwords and accounts.

An Unethical Experiment? • • • Choose 921 university students who have social-networking accounts. Collect 810 of their friends’ email addresses (at the same university). Send 921 phishing emails – Social-phishes: appear to come from a friend at that university. – Unknown-phishes: appear to come from an unknown fictitious person with a university email address. From: Alice@indiana. edu (spoofed by Eve) To: Bob@indiana. edu Subject: This is Cool! Hey, check this out! https: //www. indiana. edu/%7 e%70 hi%73%68%69 n%67. . . Alice • Redirect the https queries to https: //www. whuffo. com Findings: • 72% of the social-phishing victims visited the whuffo. com website, and typed in their university user account and passwords. • Only 16% of the unknown-phishes were successful.

Ethical and Legal Concerns • • Unconsenting subjects: “The human subjects committee approved a waiver of consent. . . A debriefing email message explained the participants’ role in the experiment after the fact and directed them to our research Web site for further information. ” Emotional harm to subjects: “. . . subjects whose names and email had been spoofed. . . were notified by the corresponding receivers and initially believed that their computers were infected by an email virus. . Many subjects were convinced the experimenters (with the complicity of university officials) had hacked into their email. . . ” 30 complaints were lodged with the campus support center. The researchers used information from one or more socialnetworking sites. Did they abide by its terms of use? –http: //www. myspace. com/: “Prohibited activity includes, but is not limited to: . . . attempting to impersonate another member or person. . . ”

Our Experiment • Our experiment was designed to explore – the factors that influence users’ password use and reuse behavior, and – how users organize their accounts and passwords. • We prevented participants from revealing their passwords and accounts. – They wrote notes on a piece of paper which they shredded before leaving the room.

More ‘Secure’ Passwords are Harder to Recall… 5 Difficulty of Recall 4 3 2 1 0 0 1 2 3 4 5 Perceived Security Level • Our participants thought their hard-to-recall passwords are more ‘secure’.

Growth of Accounts and Passwords • The number of online accounts of our participants increases as they gain more internet experience (~1. 2 accounts per year on average). • However, we found no evidence that the number of years of internet experience is related to the number of passwords.

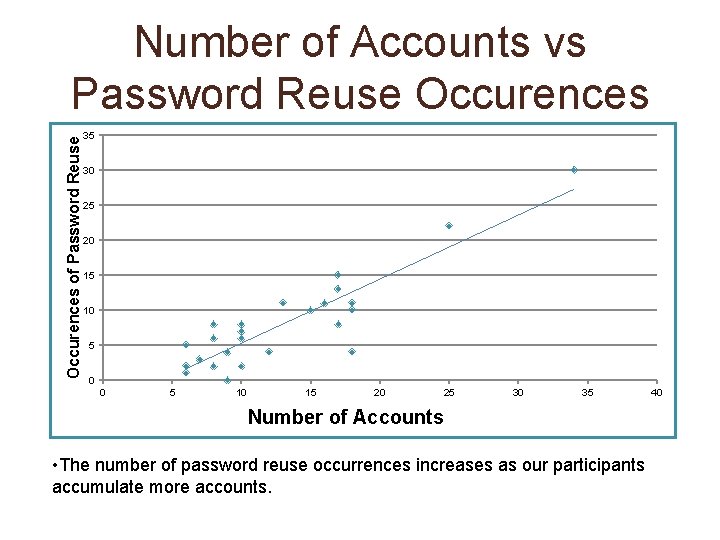
Occurences of Password Reuse Number of Accounts vs Password Reuse Occurences 35 30 25 20 15 10 5 0 0 5 10 15 20 25 30 35 Number of Accounts • The number of password reuse occurrences increases as our participants accumulate more accounts. 40

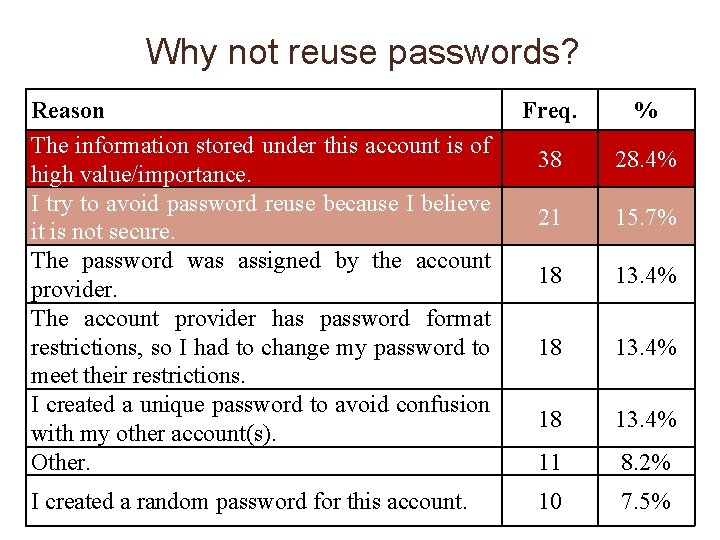
Why not reuse passwords? Reason The information stored under this account is of high value/importance. I try to avoid password reuse because I believe it is not secure. The password was assigned by the account provider. The account provider has password format restrictions, so I had to change my password to meet their restrictions. I created a unique password to avoid confusion with my other account(s). Other. I created a random password for this account. Freq. % 38 28. 4% 21 15. 7% 18 13. 4% 11 8. 2% 10 7. 5%

Why reuse passwords? Reason Freq. % I reuse password for this account because it is easy to 72 35. 1% remember. The information that is stored under this account is of 19% similar value/importance to the information stored under the 39 other account(s) which use the same password. This account belongs to the same category as the other 38 18. 5% account(s) which use the same password. This account belongs to the same domain (leisure/ work/ 27 13. 2% family) as other account(s) which use the same password. I use this account in the same frequency as the other 16 7. 8% account(s) which use the same password. I have several passwords and I randomly assigned them to 7 3. 4% my accounts. I only have one password and I use it for all my accounts. 3 1. 5% Other. 3 1. 5%

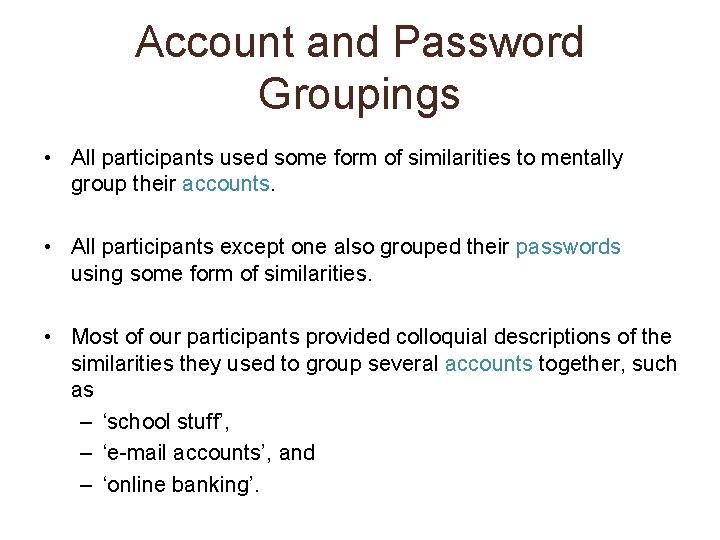
Account and Password Groupings • All participants used some form of similarities to mentally group their accounts. • All participants except one also grouped their passwords using some form of similarities. • Most of our participants provided colloquial descriptions of the similarities they used to group several accounts together, such as – ‘school stuff’, – ‘e-mail accounts’, and – ‘online banking’.

Reasons for Grouping Accounts • Type of service (72%) Accounts for financial purposes, email, education, . . . • Risk (18. 6 %) High-risk accounts, unimportant accounts, . . . • Frequency (5. 2%) Commonly-used accounts, rarely-used accounts, . . . • Alias (2. 5%) Accounts with username#1, accounts with username#2, . . . • Sharing (1. 7%) Accounts shared with friends, co-workers, family members, . . .

Reasons for Grouping Passwords • Semantic (44. 4%) Similarities in length, number of letters or numbers, number of words, permutation of similar phrases, pronunciation, . . . • Inspiration (15. 3%) Based on a comic book character, a pet, a person, . . . • Accounts (15. 3%) Passwords for online banking, for email accounts, for. . . • Perception of Security (12. 5%) More secure passwords, less secure passwords, . . . • Creation (6. 9%) Assigned by service providers, created by self, . . . • Recallability (5. 5%) Easy to remember, hard to remember, . . .

Passwords are Reused Less in High Importance Account Groups • Participants reused passwords less in their highest importance group(s) than in their other groups. • Highest importance account groups Total = 68 Accounts Assigned Unique Password = 43 (63%) Assigned Reused Password = 25 (37%) • Other/low importance account groups Total = 253 Accounts Assigned Unique Password = 82 (32%) Assigned Reused Password = 171 (68%)

Major Findings • Our participants understand the risk of reusing passwords or using weak passwords. • Our participants mentally classified their accounts by type of service (72%) • Our participants mentally classified their passwords by semantic similarities e. g. length (44%).

Recommendations and Future Work • Password and account grouping should be promoted in user interfaces for password and account management systems. • Reusing passwords on the less-important accounts should not be discouraged! – Users are unable to remember more than a few passwords. – Strong and unique passwords should be reserved for accounts that truly deserve them. • Could users be taught how to identify which accounts are truly important? • What are your three most important accounts? (Can you remember more than three passwords? )