Communications Standards Protocols Prof Aiman Hanna Department of



















- Slides: 56

Communications, Standards & Protocols © Prof. Aiman Hanna Department of Computer Science Concordia University Montreal, Canada

H istory of Communications u For 1000 s of years through auditory & visual senses • Visual senses: u u Face to face Reading messages/letters/symbols/sketches Seeing visual signals (smoke, fire, . . etc). … • Auditory senses: u u u Direct listening Listening through messengers. . . 2

H istory of Communications u (continue. . . ) Drastic change in 1837 The invention of the telegraph by Samuel Morse u Characters of a message were translated into long and short electrical impulses u These impulses were then transmitted over a copper wire u The association between the characters and the impulses was called Morse Code u u 1876: The Magical invention of Telephony by Alexander Graham Bell showed that voice can be converted directly into electrical energy u This energy can then be transmitted over a wire using continuously varying voltages u 3

H istory of Communications u (continue. . . ) Switchboards u u u Early telephones required a pair of wires that connects telephones at both ends That changed with the invention of the switchboard, a switching device that connected lines between two phones Establishing connections was activated through an operator at the switchboard 4

H istory of Communications u 1945: ENIAC u u u (continue. . . ) Electronic Numerical Integrator And Calculator The 1 st electronic computer Designed for computing ballistics for World War II Although did not play a direct role in communication, it did show that calculations and decision making could be done electronically 1947: The Transistor u u u Allowed smaller and affordable computers to be built Computers applications developed during the 1960 s made routing and processing telephone calls economically possible The increased utilization of computers by businesses resulted in a growing need to transfer information between these computers as well 5

H istory of Communications u Electronic Communications The massive need in relatively short time u u u (continue. . . ) The 1 st form of communication between systems were done through magnetic tapes Information were copied from on system into a tape; which is transferred to another system, possibly a remote one The development of the Personal Computer (PC) in the 1980 s was a milestone in electronic communication The infusion of millions of PCs into, virtually, everywhere created a further massive need to make information easily accessible At this point it was clear that the need for electronic communication was no longer a luxury, rather a necessity and a must 1990 s: The World Wide Web (WWW) & The Internet u u u WWW is application that enabled information from around the world to become easily accessible from one’s desk. The Internet is an electronic network of computers that includes nearly every university, government, and research facility in the world, as well as many commercial sites The Internet started with four interconnected computers in 1969 and was known as ARPAnet 6

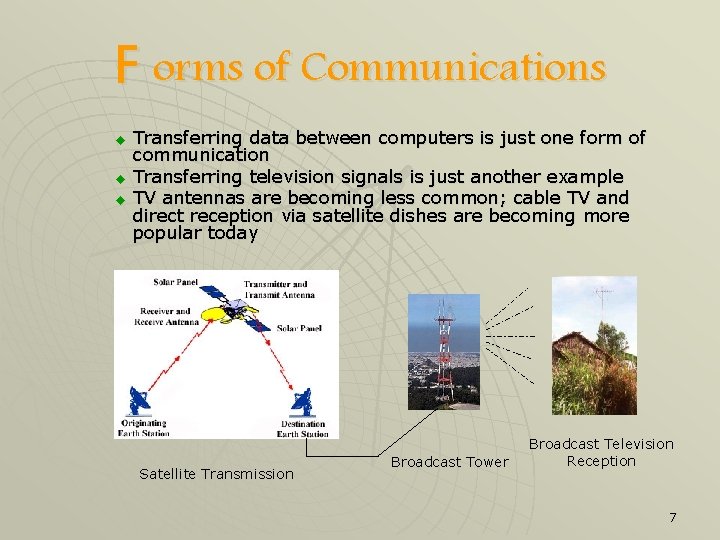
F orms of Communications u u u Transferring data between computers is just one form of communication Transferring television signals is just another example TV antennas are becoming less common; cable TV and direct reception via satellite dishes are becoming more popular today Satellite Transmission Broadcast Tower Broadcast Television Reception 7

F orms of Communications (continue. . . ) Other communications applications use local area networks (LANs) and wide are networks (WANs) systems that allow communication over short (LAN) or long (WAN) distances. u Once connected to LANs or WANs, users can send or receive data files, log into remote machine, send Electronic Mails (E-mails), or connect to the Internet u Other forms of communications include: u • • • Facsimile machines (Fax) Voice and video communications over computers Teleconferencing / Videoconferencing Cellular telephones Peer-to-peer networking 8

Okay! Let us Connect, but what about: Security u Performance u Medium of communication u Ease of use u Cost and cost-effectiveness u After all, is there a law? 9

C omputer Networks u u u u A network is a system connecting different devices, such as PCs, printers, scanners, . . etc. A PC may be dedicated to manage a disk drive containing shared files; such a PC is referred to as file server Often, a network covers a small geographical area (up to few kilometers), such a network is referred to as LAN A network that connects large areas, such as state, country, or the world, is referred to as WAN Now, with many users connecting to a network it is significant to avoid conflicts as well as provide service to all of them with a minimal delay Connections to the network hence must be made in a way that achieves such requirements The connection strategy is referred to as Network Topology The best topology depends on the network needs 10

N etwork Topologies Common Bus Topology u Star Topology u Ring Topology u Fully Connected Topology u Tree Topology u Combined Topology u 11

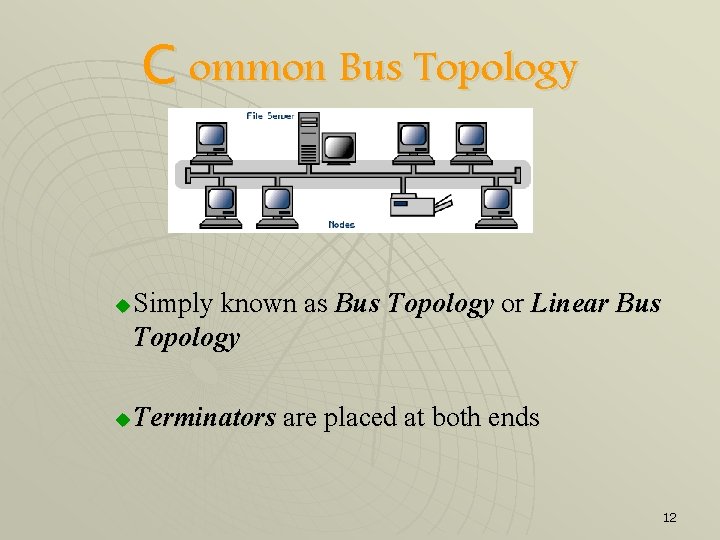
C ommon Bus Topology u u Simply known as Bus Topology or Linear Bus Topology Terminators are placed at both ends 12

C ommon Bus Topology Collision is possible u A collision results on noise u The interfaces detect the noise on the bus, stop transmission, wait for a random amount of time then attempt transmission again u This process is called Carrier Sense Multiple Access with Collision Detection (CSMA/CD) u The Ethernet (original configuration) is an example of a common bus network u Advantages u Disadvantages u 13

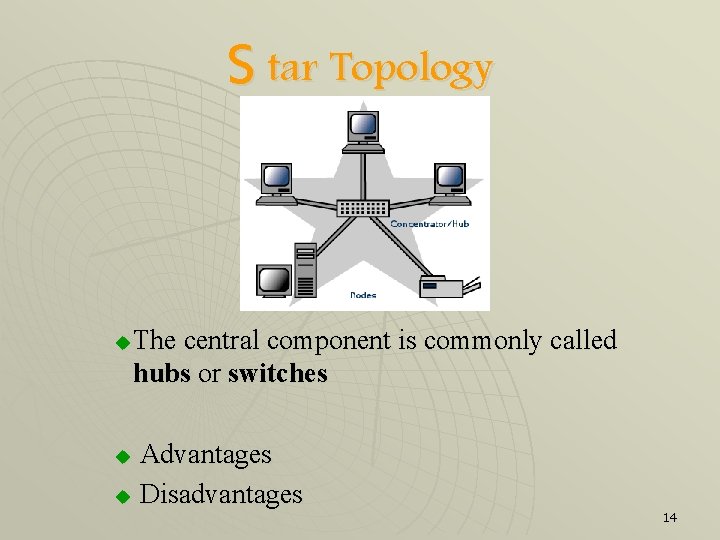
S tar Topology u The central component is commonly called hubs or switches Advantages u Disadvantages u 14

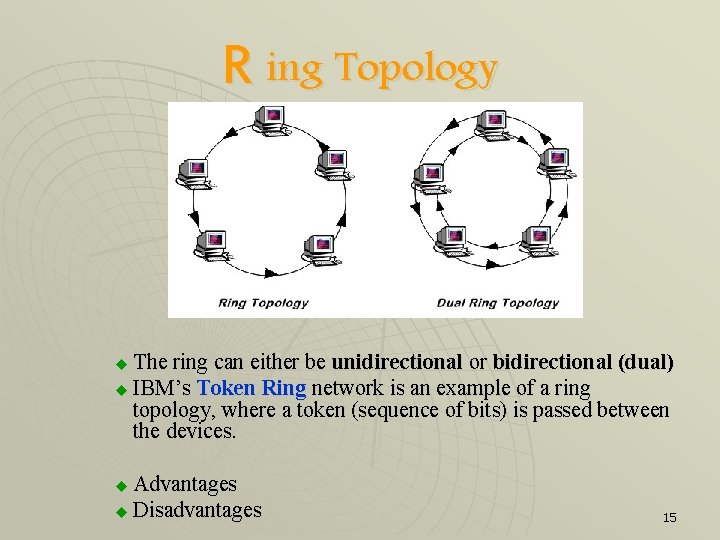
R ing Topology The ring can either be unidirectional or bidirectional (dual) u IBM’s Token Ring network is an example of a ring topology, where a token (sequence of bits) is passed between the devices. u Advantages u Disadvantages u 15

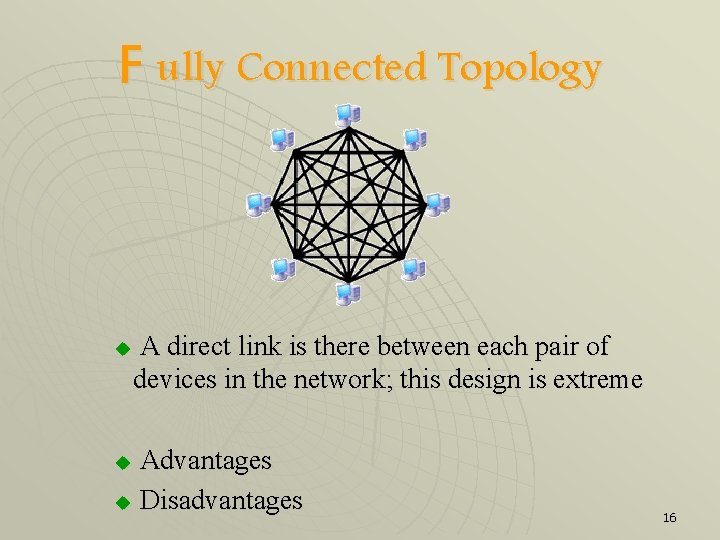
F ully Connected Topology u A direct link is there between each pair of devices in the network; this design is extreme Advantages u Disadvantages u 16

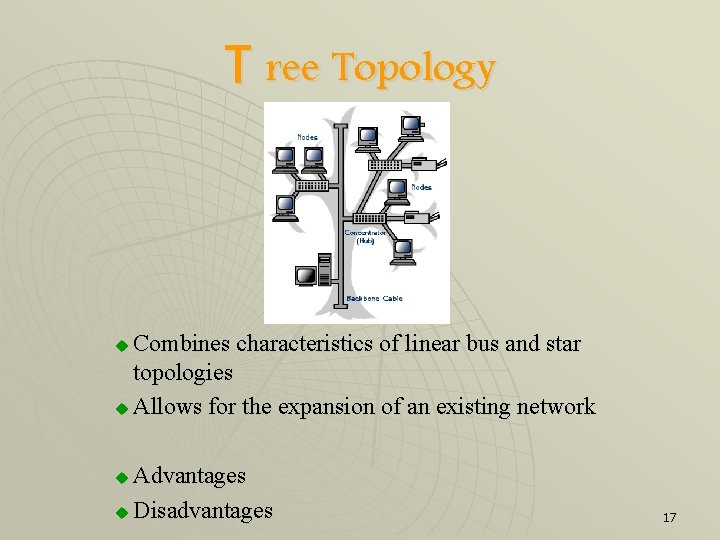
T ree Topology Combines characteristics of linear bus and star topologies u Allows for the expansion of an existing network u Advantages u Disadvantages u 17

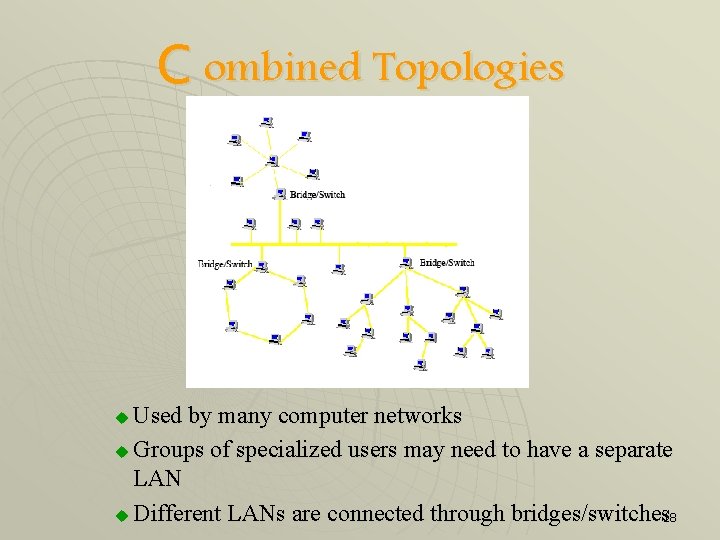
C ombined Topologies Used by many computer networks u Groups of specialized users may need to have a separate LAN u Different LANs are connected through bridges/switches 18 18 u

S tandards u u u u u Computers have different architecture, understand different languages, store data in different formats, …etc. , so how can they communicate then! For communication to occur, the system must use, and agree upon, a protocol to communicate A protocol is a set of rules that define an exact format and rules for communication between systems If two system agree to follow a protocol, but different protocol, they might as well follow none! If all systems agree to follow one same protocol, then this protocol would become a standard Fortunately, there is a standard; BUT Unfortunately, there are few of them Through the years, different goals and ideas have cause this creation of various standards In general, there are two types of standards: De facto standards, and standards through standards organizations De facto standards are those who exist by virtue of their widespread use, such as many of IBM products 19

S tandards Organizations u u Few standards organizations are important to the field of computer networks and data communication Such organizations are: • ANSI: American National Standards Institute (www. ansi. org) – ASCII, FDDI, … • IEC: International Electrotechnical Commission (www. iec. ch) – JPEG, … • ITU: International Telecommunication Union (www. itu. int) - X. 25, … • EIA: Electronic Industries Association (www. eia. org) – optical cables, wires, … • IETF: Internet Engineering Task Force (www. ietf. org) – the next-generation Internet protocol • IEEE: Institute of Electrical and Electronics Engineers (www. ieee. org) – journals, 802 LAN Standard, … • ISO: International Standards Organization (www. iso. org) – OSI, … • NIST: National Institute of Standards and Technology (www. nist. gov) – DES, … • IBM: International Business Machines (www. ibm. com) – SNA, EBCDIC, … 20

O pen Systems & the OSI Model A set of protocols that would allow any two different systems to communicate regardless of their underlying architecture u Open System: u The Open System Interconnect (OSI) Model: • Introduced by ISO • Employs 7 layers, where each layer performs specific functions and communicate with the one above and below it • Higher layers deal more with the user applications, services and activities • Lower layers deal more with the actual transmission of information • Advantages of layered model 21

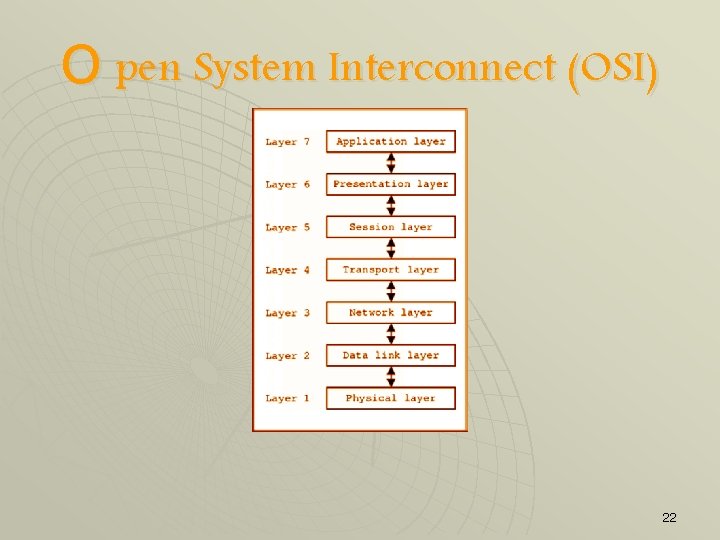
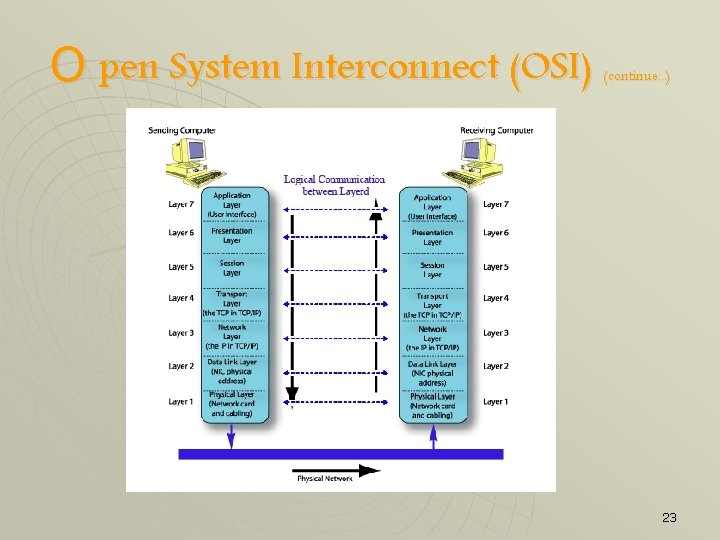
O pen System Interconnect (OSI) 22

O pen System Interconnect (OSI) (continue. . . ) 23

O verview of OSI u Layer 7: The Application Layer: Interfaces directly with the user. At this layer: • Communication partners are identified • Quality of service is identified • User authentication and privacy are considered • This layer provides application services such as file transfers & e-mail • Telnet and FTP are examples of applications that exist entirely in the application level 24

O verview of OSI u Layer 6: The Presentation Layer: • Responsible for presenting data in a format the user can understand • Provides data encryption for security reasons • Sometimes, this layer is referred to as the Syntax Layer 25

O verview of OSI u Layer 5: The Session Layer: • Allows applications on two different computers to establish a session, or in other words, a logical connection • A session is established when the communication start and ended when the communication ends • This layer also handles error recovery • The session layer allows the insertion of checkpoints in the middle of the stream • This layer also brackets ([…], perform it as atomic) 26

O verview of OSI u Layer 4: The Transport Layer: • Lowest layer that deals with end-to-end communication; lower layers deal with the network itself • A computer may be connected to several networks; this layers determines which network to use for communication depending on many factors • Ensures complete data transfer • Provides end-to-end error recovery, and flow control 27

O verview of OSI u Layer 3: The Network Layer: • Deals with routing strategies • In specific, this layer controls the communication subnet (the collection of transmission media and switching elements over that media required for routing and data transmission) • Provides congestion control • May also contain billing and accounting routines – information need to bill users based on their use of the network 28

O verview of OSI u Layer 2: The Data Link Layer: • Supervises the flow of information between adjacent network nodes • Uses error detection or correction techniques to ensure that a transmission is error-free • Controls how much information is sent at a time in order to avoid both congestion and long delays • The data link layer is divided into two sublayers: The Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. • The MAC sublayer controls how a computer on the network gains access to data and permission to transmit data. • The LLC layer controls flow control and error checking 29

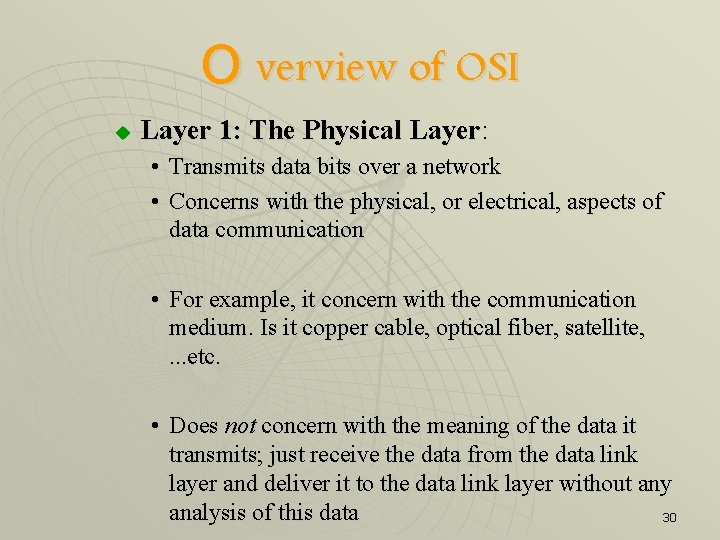
O verview of OSI u Layer 1: The Physical Layer: • Transmits data bits over a network • Concerns with the physical, or electrical, aspects of data communication • For example, it concern with the communication medium. Is it copper cable, optical fiber, satellite, . . . etc. • Does not concern with the meaning of the data it transmits; just receive the data from the data link layer and deliver it to the data link layer without any analysis of this data 30

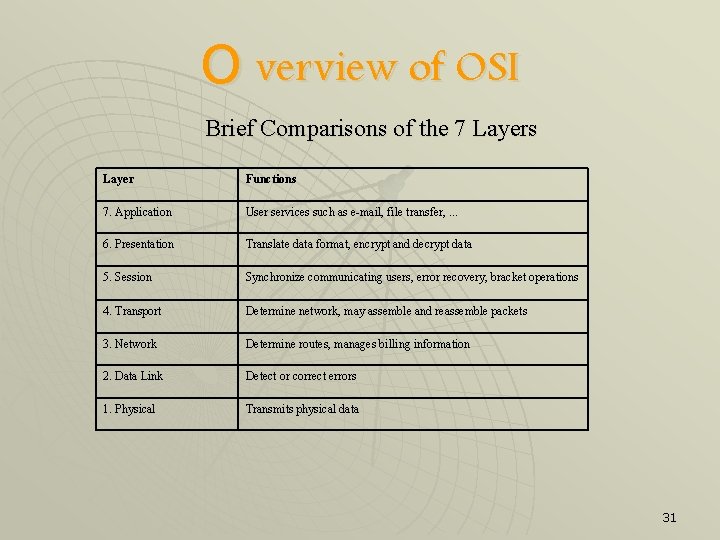
O verview of OSI Brief Comparisons of the 7 Layers Layer Functions 7. Application User services such as e-mail, file transfer, . . . 6. Presentation Translate data format, encrypt and decrypt data 5. Session Synchronize communicating users, error recovery, bracket operations 4. Transport Determine network, may assemble and reassemble packets 3. Network Determine routes, manages billing information 2. Data Link Detect or correct errors 1. Physical Transmits physical data 31

C onnection Strategies Computers must be connected to communicate, however u the traversal of information though the network is a design issue u Figure 1. 13 page 25 32

C onnection Strategies u (continue. . . ) There are 3 strategies: • Circuit Switching • Message Switching • Packet Switching 33

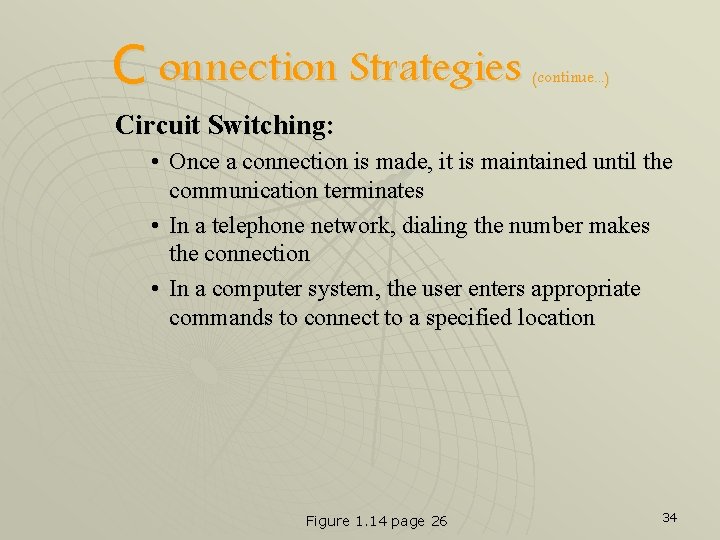
C onnection Strategies (continue. . . ) Circuit Switching: • Once a connection is made, it is maintained until the communication terminates • In a telephone network, dialing the number makes the connection • In a computer system, the user enters appropriate commands to connect to a specified location Figure 1. 14 page 26 34

C onnection Strategies (continue. . . ) Circuit Switching (continue): • Circuit switching requires that the route be determined and that the connection is made before any information is transmitted • The connection is then maintained until the communication terminates 35

C onnection Strategies u (continue. . . ) Message Switching: • Message: unit of information • A route is established when a message is to be sent • A sending node attach the message along with the destination address, chooses a route, then forwards it to the first node in that route • The message, in its entirety, is temporarily stored at that node, while logic is working the next node in the following possible route • Once the following node is known the message is routed to it • This is know as Store-and-Forward Figure 1. 15 page 27 36

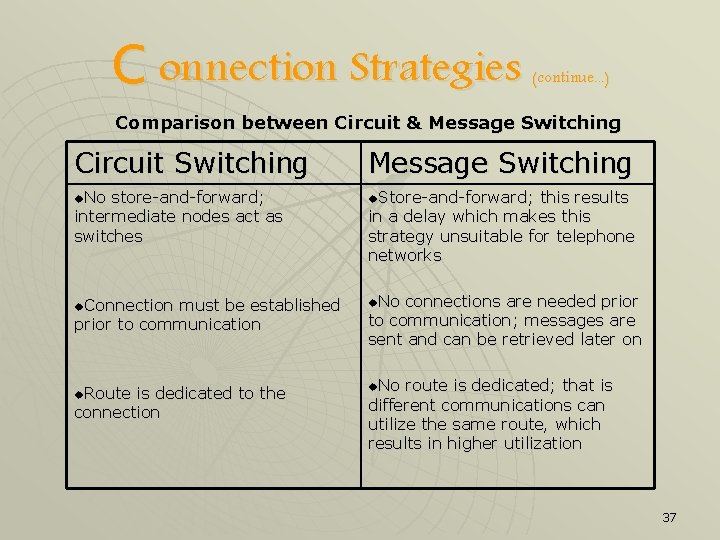
C onnection Strategies (continue. . . ) Comparison between Circuit & Message Switching Circuit Switching Message Switching u. No store-and-forward; intermediate nodes act as switches u. Store-and-forward; u. Connection u. No must be established prior to communication u. Route is dedicated to the connection this results in a delay which makes this strategy unsuitable for telephone networks connections are needed prior to communication; messages are sent and can be retrieved later on u. No route is dedicated; that is different communications can utilize the same route, which results in higher utilization 37

C onnection Strategies u (continue. . . ) Packet Switching: • A message is divided into smaller units, called packets • Each packet contains its destination address (or other indicators to where it should go) • Packets are then sent, possibly through different routes • At the destination, packets are reassembled to from the original message Figure 1. 16 page 28 (datagram in fact) 38

C onnection Strategies (continue. . . ) Packet Switching (continue): • Similar to message switching, no connection is maintained • The small size of the packets reduces buffering problems and long delays • Packet switching has two common routing methods: u Datagram u Virtual Circuit 39

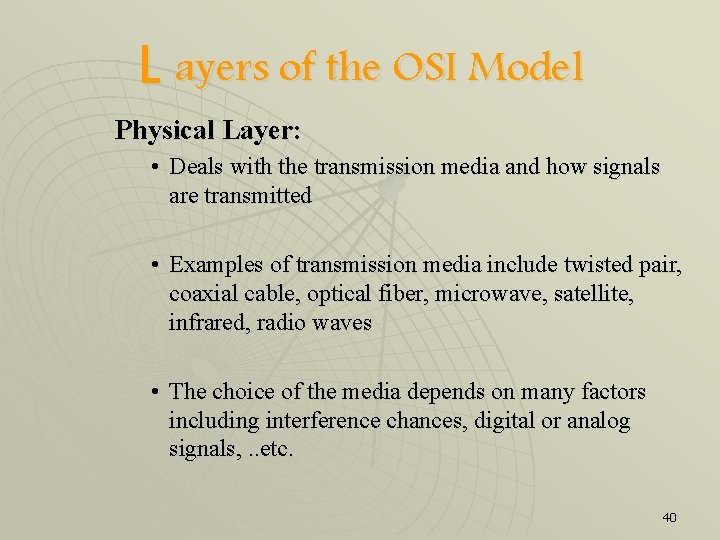
L ayers of the OSI Model Physical Layer: • Deals with the transmission media and how signals are transmitted • Examples of transmission media include twisted pair, coaxial cable, optical fiber, microwave, satellite, infrared, radio waves • The choice of the media depends on many factors including interference chances, digital or analog signals, . . etc. 40

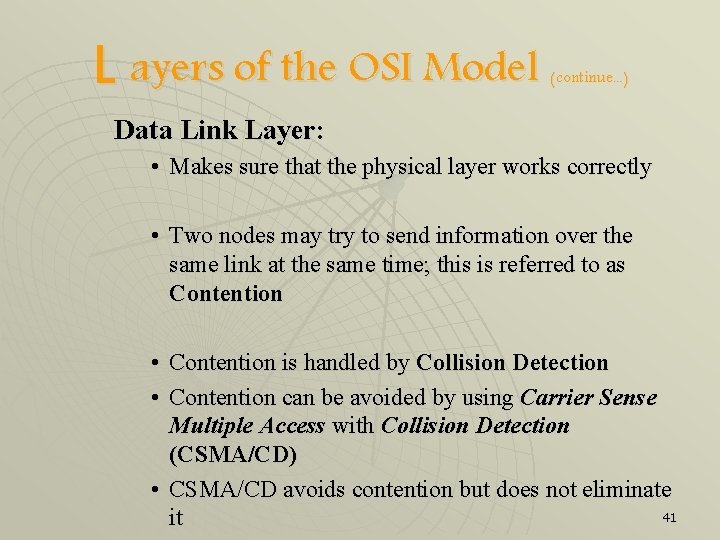
L ayers of the OSI Model (continue. . . ) Data Link Layer: • Makes sure that the physical layer works correctly • Two nodes may try to send information over the same link at the same time; this is referred to as Contention • Contention is handled by Collision Detection • Contention can be avoided by using Carrier Sense Multiple Access with Collision Detection (CSMA/CD) • CSMA/CD avoids contention but does not eliminate 41 it

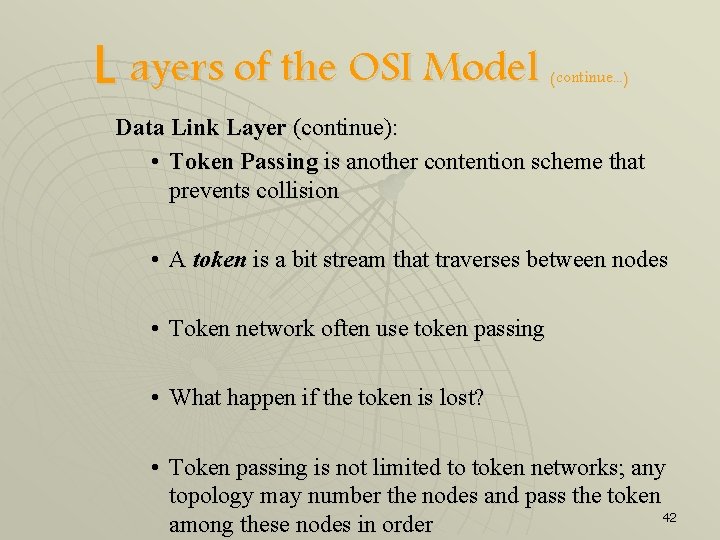
L ayers of the OSI Model (continue. . . ) Data Link Layer (continue): • Token Passing is another contention scheme that prevents collision • A token is a bit stream that traverses between nodes • Token network often use token passing • What happen if the token is lost? • Token passing is not limited to token networks; any topology may number the nodes and pass the token 42 among these nodes in order

L ayers of the OSI Model (continue. . . ) Figure 1. 17 page 31 Data Link Layer (continue): • Data is sent over the physical link from one node and received by another, however have they arrived correctly • The data link layer performs error detection and if errors are detection then it performs error correction 43

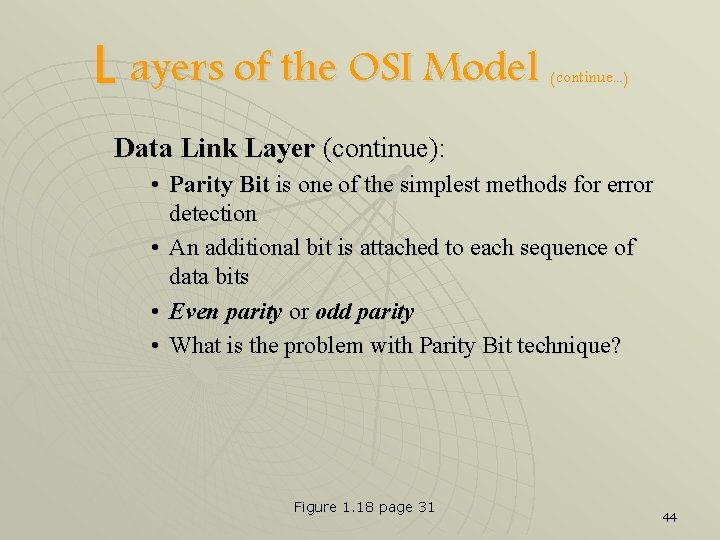
L ayers of the OSI Model (continue. . . ) Data Link Layer (continue): • Parity Bit is one of the simplest methods for error detection • An additional bit is attached to each sequence of data bits • Even parity or odd parity • What is the problem with Parity Bit technique? Figure 1. 18 page 31 44

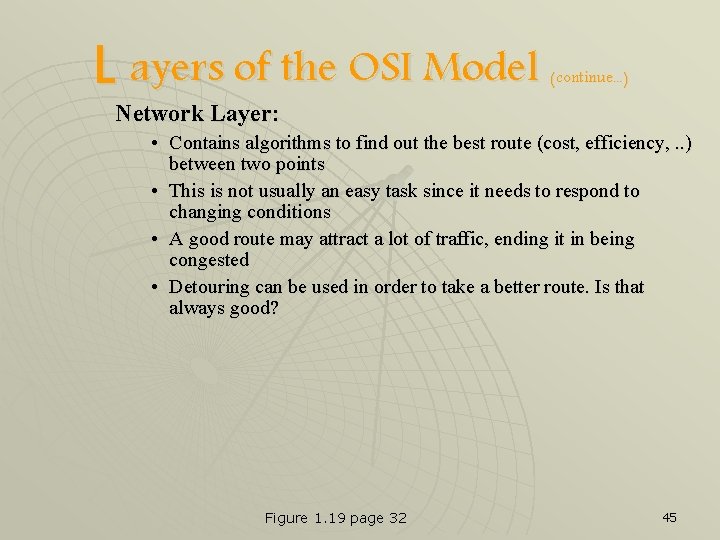
L ayers of the OSI Model (continue. . . ) Network Layer: • Contains algorithms to find out the best route (cost, efficiency, . . ) between two points • This is not usually an easy task since it needs to respond to changing conditions • A good route may attract a lot of traffic, ending it in being congested • Detouring can be used in order to take a better route. Is that always good? Figure 1. 19 page 32 45

L ayers of the OSI Model (continue. . . ) Transport Layer: • This layer, and the three layers above it, provide user services • They execute at the sending and receiving nodes to ensure information arrival at the destination as well as acknowledgment to the sending node Figure 1. 20 page 33 46

L ayers of the OSI Model (continue. . . ) Transport Layer (continue): • Provides reliable and efficient communication • In practice, networks are unreliable; data can be lost or delayed • This layer insulates the session layer from many details of the network • TCP (Transport Control Protocol) is one of the most famous transport layer protocols 47

L ayers of the OSI Model (continue. . . ) Transport Layer (continue): • Transport functions include multiplexing, buffering and connection management • Multiplexing: Several transport users share a single node; for example three users may connect to the same node (login, download a file, and view a website) • The transport layer ensures that the proper data is routed to the appropriate user Figure 1. 21 page 34 48

L ayers of the OSI Model (continue. . . ) Transport Layer (continue): Buffering: it may occur at either the destination or the source • Data received from the session layer is broken into Transport Protocol Data Units (TPDUs) 49

L ayers of the OSI Model (continue. . . ) Transport Layer (continue): Connection Management: the protocol by which the transport establishes and releases connections • Two-Way Handshake may seem easy, but will it always work? Figure 1. 22 page 35 50

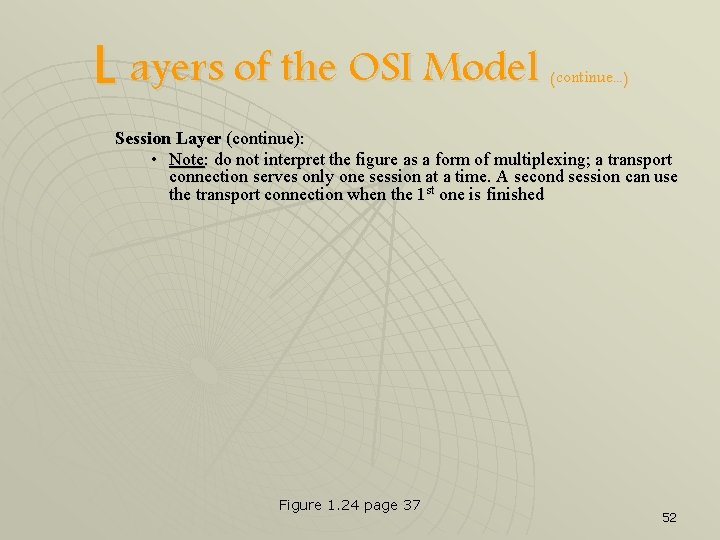
L ayers of the OSI Model (continue. . . ) Session Layer: • Contains the protocols necessary for establishing and maintaining a connection, or session, between end users • Well, then what did the transport layer do? ! Figure 1. 23 page 36 51

L ayers of the OSI Model (continue. . . ) Session Layer (continue): • Note: do not interpret the figure as a form of multiplexing; a transport connection serves only one session at a time. A second session can use the transport connection when the 1 st one is finished Figure 1. 24 page 37 52

L ayers of the OSI Model (continue. . . ) Presentation Layer: • Computers do not speak the same language; language here refers to the way information is represented • There is a difference between data and information • A problem exists because different computers may have different ways to represent the same information • For example, integers may have different sizes (sometimes, transformation is impossible), 2 -D array can be stored based on rows or columns, • Thus, it is not enough to provide effective data communication; rather, effective communication of information is needed • The presentation layer performs that task • Data encryption and data compression can also be performed at this layer 53

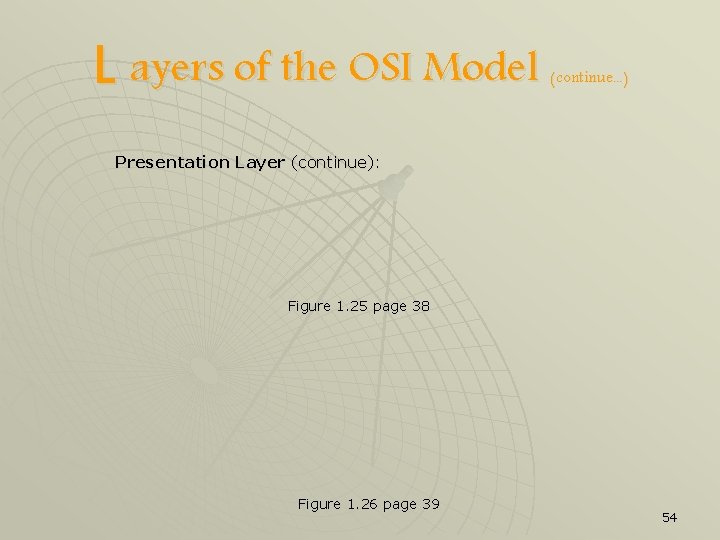
L ayers of the OSI Model (continue. . . ) Presentation Layer (continue): Figure 1. 25 page 38 Figure 1. 26 page 39 54

L ayers of the OSI Model (continue. . . ) Application Layer: • Communicates directly with user/user applications • Contains network applications, such as: u FTP, u Telnet, E u E-mail, u Virtual terminal, u … 55

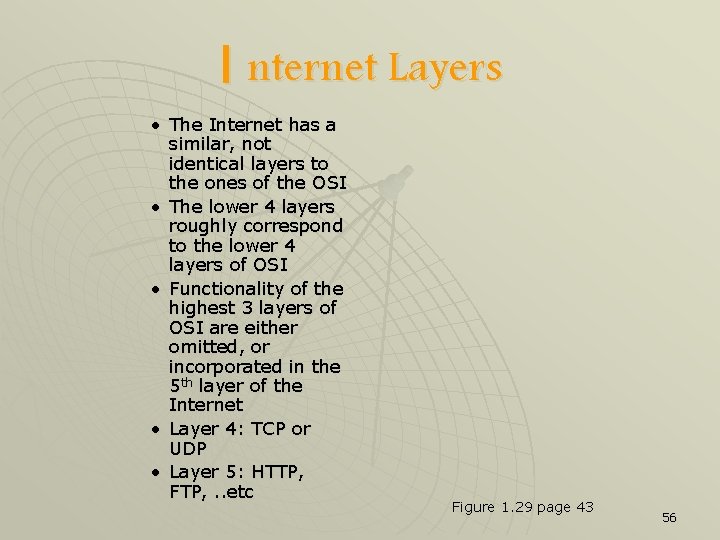
I nternet Layers • The Internet has a similar, not identical layers to the ones of the OSI • The lower 4 layers roughly correspond to the lower 4 layers of OSI • Functionality of the highest 3 layers of OSI are either omitted, or incorporated in the 5 th layer of the Internet • Layer 4: TCP or UDP • Layer 5: HTTP, FTP, . . etc Figure 1. 29 page 43 56