Connecting Networks Prof Aiman Hanna Department of Computer






















- Slides: 58

Connecting Networks © Prof. Aiman Hanna Department of Computer Science Concordia University Montreal, Canada

C onnecting Networks u u The larger the number of devices in a single LAN, the higher the chances that the LAN performance degrades One possible solution is to separate devices into multiple LANs Yet, these devices must still be able to communicate Consequently, new protocols must be developed to cross over LAN boundaries 2

C onnecting Networks Figure 10. 1 – Interconnecting Networks 3

C onnecting Networks Figure 10. 2 – OSI Connections 4

C onnecting Networks u u u Protocol converters are used to connect different networks The most common protocol converters exist at layers 1, 2&3 At layer 1: hubs, repeaters At layer 2: bridges, switches, … At layer 3: routers 5

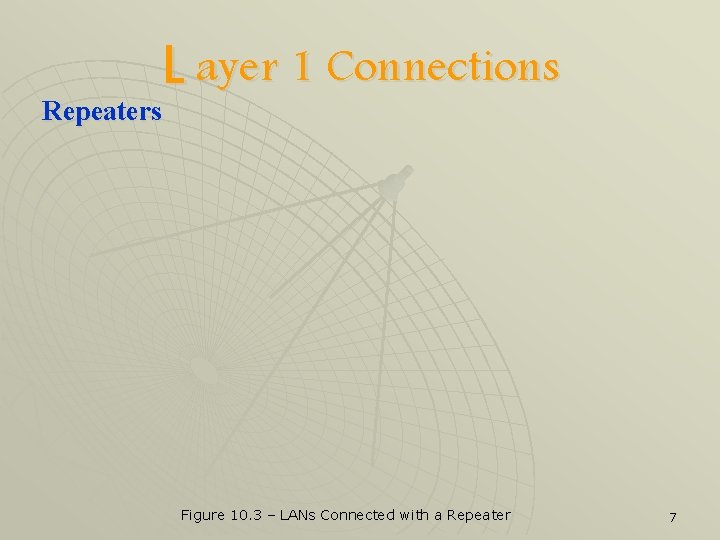
L ayer 1 Connections Repeaters u Operate at the physical layer (layer 1) u u Connect LANs that are using the same protocol and frame format Main function is to just regenerate signals then send them again, hence extend the distance covered by a LAN protocol 6

L ayer 1 Connections Repeaters Figure 10. 3 – LANs Connected with a Repeater 7

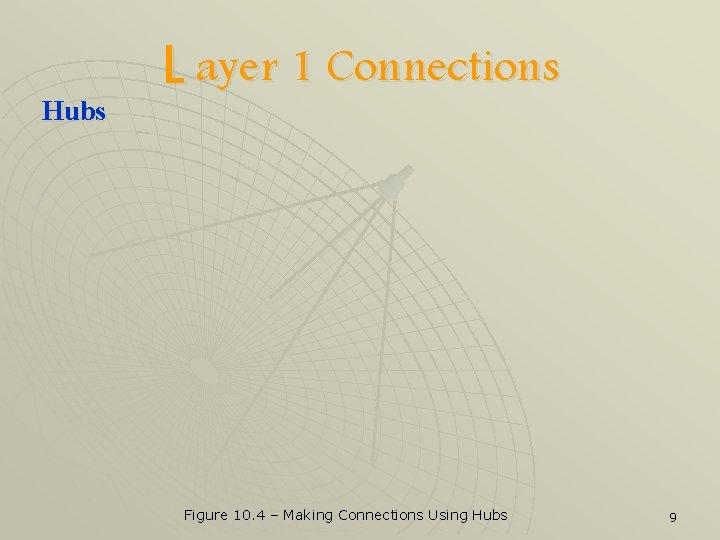
L ayer 1 Connections Hubs u Sometimes called multi-port repeaters u u u The main difference between a hub and repeater is that a hub has multiple ports, hence many devices can directly be connected to it All devices connected to a hub are still in the same collision domain The more the devices connected to hubs, the more the chances that the network performance will degrade 8

Hubs L ayer 1 Connections Figure 10. 4 – Making Connections Using Hubs 9

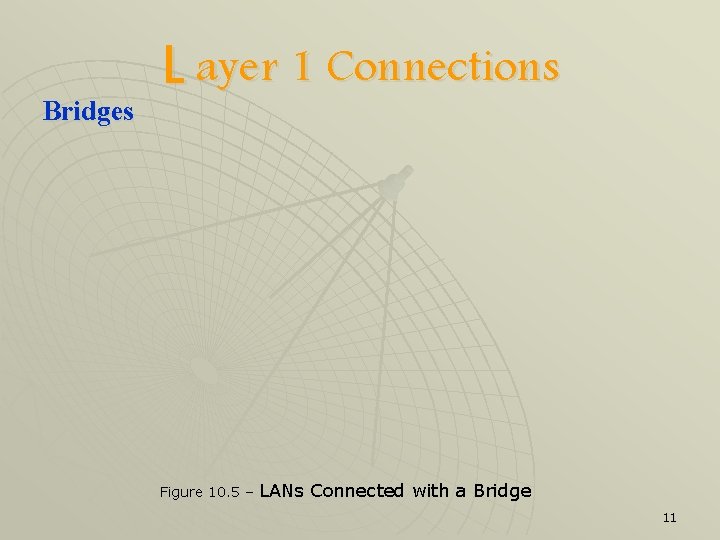
L ayer 2 Connections Bridges u A bridge connects two LANs u Operate at layer 2; so they are capable of: • Making decision about when to forward any frame they received • Performing data link function such as error detection, frame formatting, frame routing, …etc. u A bridge examines an incoming frame and route it to its LAN only if it is destined to a device in that LAN 10

Bridges L ayer 1 Connections Figure 10. 5 – LANs Connected with a Bridge 11

L ayer 2 Connections Bridging different types of LANs u A bridge may connects two LANs of different types u This is more difficult however since many issues must be considered: • What if the two LANs operate on different speed • How about bridges delay; will they cost any further problems • What if the frame formats of the two network are different 12

L ayer 2 Connections Bridges - Routing u How would a bridge know that a specific device in its LAN u u u Worst, what if the device is not in the bridge's LAN but the frame must be passed by the bridge to another in order to deliver the frame What if a device is initially served (either directly or indirectly) by a bridge but then the device is moved The process of deciding which frames to accept/forward and where to forward them is called bridge routing 13

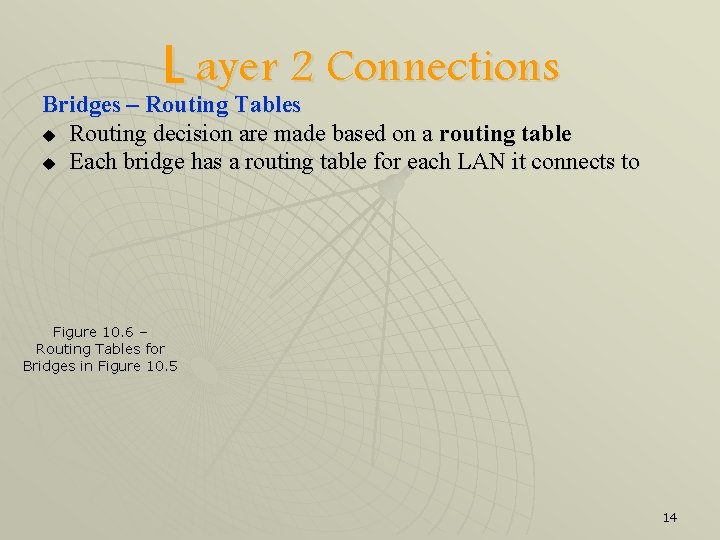
L ayer 2 Connections Bridges – Routing Tables u Routing decision are made based on a routing table u Each bridge has a routing table for each LAN it connects to Figure 10. 6 – Routing Tables for Bridges in Figure 10. 5 14

L ayer 2 Connections Bridges – Routing Tables u How does a bridge defines it routing table? u u u Fixed routing: program the bridge with each device address and the LAN to which a frame forward to that device should be forwarded to Fixed routing however is not that feasible in reality since changes are always possible (remove device, add device, . . etc) To accommodate more dynamic environment either: • Keep in changing the routing table whenever a change is done, or • Determine some way for the bridges to update their routing tables automatically à The first alternative is not that viable in a more dynamic environment à Bridges that are capable of creating and updating their routing tables automatically are referred to as transparent bridges 15

L ayer 2 Connections Bridges - Transparent Bridges u Bridge that are capable of creating and updating their routing tables u u Once plugged, they can immediately work regardless of the topology or device locations Determine location of devices automatically then create/update the routing tables If devices move, the tables are also automatically updated (by the bridges) The capability to update routing tables automatically is referred to as route learning or address learning 16

L ayer 2 Connections Bridges – Route Learning u Bridge creates routing table by observing traffic u When a frame is received, the bridge can know two things: • Address of device • The LAN from which the frame came from u u The bridge then examines its routing table to confirm that this information matches the table entries for that device If not, the bridge updates the routing table to match the latest configuration 17

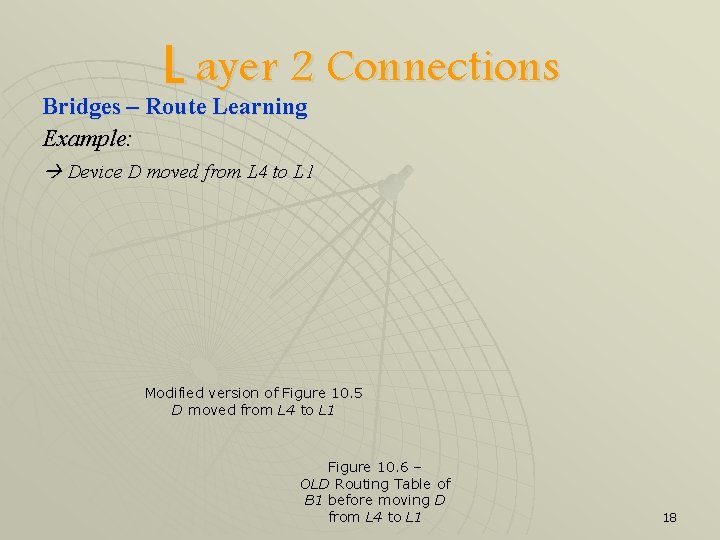
L ayer 2 Connections Bridges – Route Learning Example: Device D moved from L 4 to L 1 Modified version of Figure 10. 5 D moved from L 4 to L 1 Figure 10. 6 – OLD Routing Table of B 1 before moving D from L 4 to L 1 18

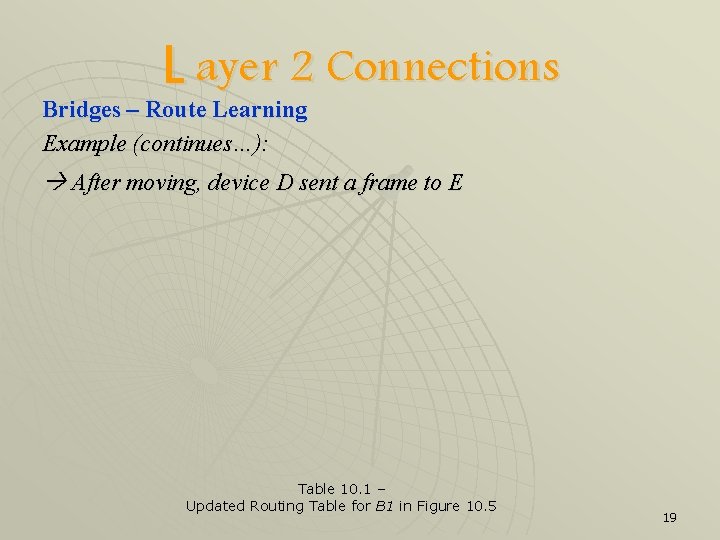
L ayer 2 Connections Bridges – Route Learning Example (continues…): After moving, device D sent a frame to E Table 10. 1 – Updated Routing Table for B 1 in Figure 10. 5 19

L ayer 2 Connections Bridges – Route Learning Questions: àWhat if D never sent a frame? àWhat about tables for L 3 & L 4; there are not updated! Another question: What happens at startup when all tables are empty? 20

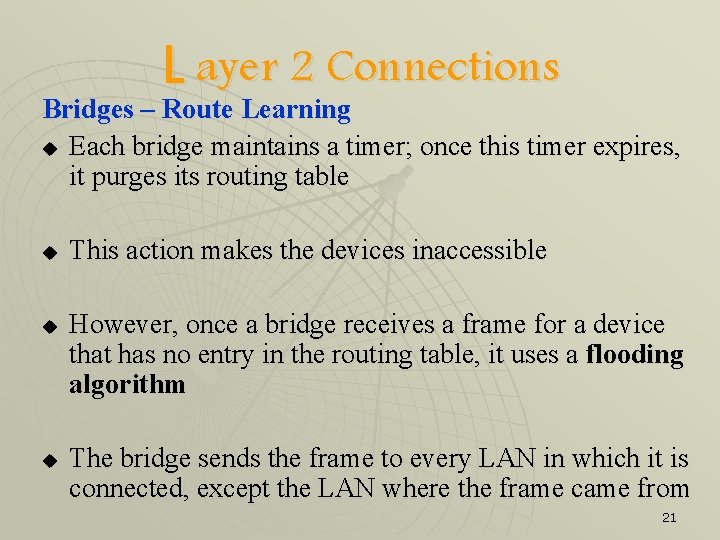
L ayer 2 Connections Bridges – Route Learning u Each bridge maintains a timer; once this timer expires, it purges its routing table u u u This action makes the devices inaccessible However, once a bridge receives a frame for a device that has no entry in the routing table, it uses a flooding algorithm The bridge sends the frame to every LAN in which it is connected, except the LAN where the frame came from 21

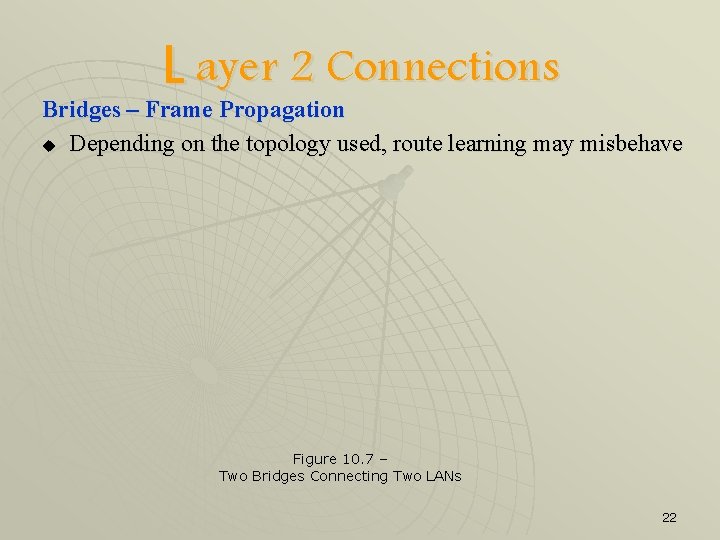
L ayer 2 Connections Bridges – Frame Propagation u Depending on the topology used, route learning may misbehave Figure 10. 7 – Two Bridges Connecting Two LANs 22

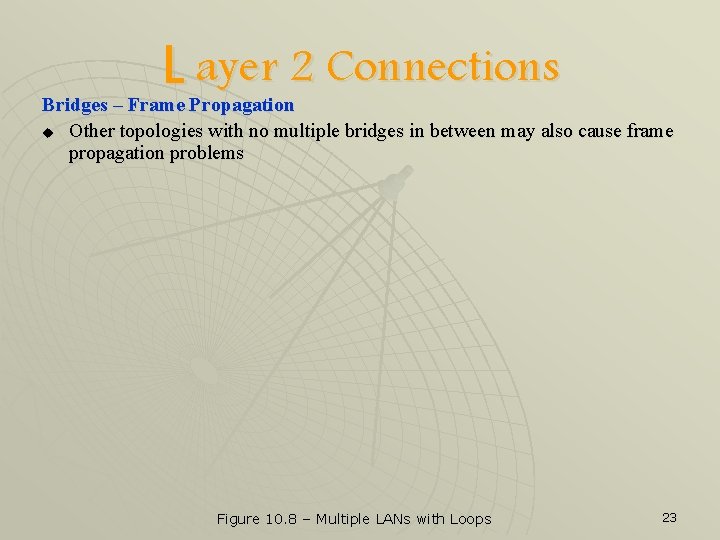
L ayer 2 Connections Bridges – Frame Propagation u Other topologies with no multiple bridges in between may also cause frame propagation problems Figure 10. 8 – Multiple LANs with Loops 23

L ayer 2 Connections Bridges – Spanning Tree Algorithm u u u One solution to the frame propagation problem is to eliminate loops Keep the bridges connected but prevent them from forwarding frames The bridges are still connected just in case they are needed as backup if the functional bridge fails To achieve needed transparency, the bridges must be capable of automatically determining which ones are used for backup and which ones should connect when failure occurs To achieve that, bridges can execute a spanning tree algorithm 24

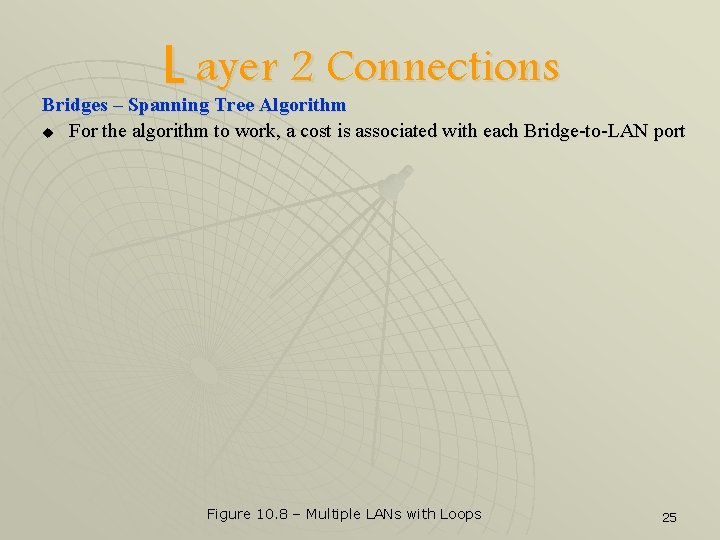
L ayer 2 Connections Bridges – Spanning Tree Algorithm u For the algorithm to work, a cost is associated with each Bridge-to-LAN port Figure 10. 8 – Multiple LANs with Loops 25

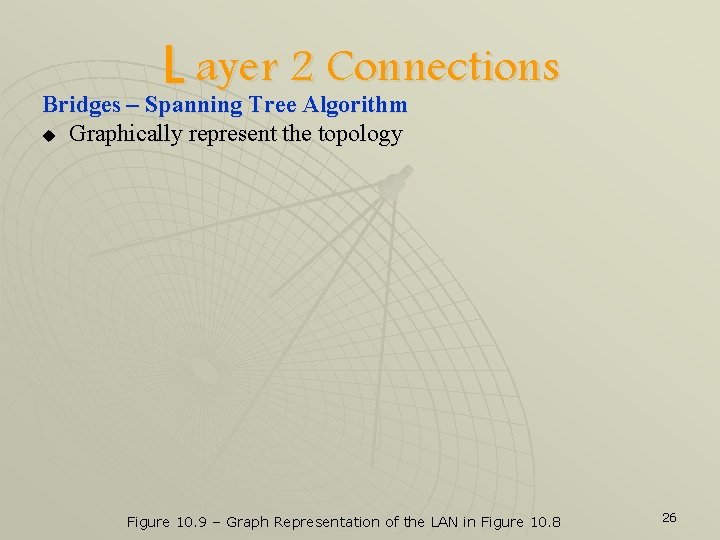
L ayer 2 Connections Bridges – Spanning Tree Algorithm u Graphically represent the topology Figure 10. 9 – Graph Representation of the LAN in Figure 10. 8 26

L ayer 2 Connections Bridges – Spanning Tree Algorithm u Determine the root bridge and the root port (that is the port corresponding to the cheapest path to the root bridge Figure 10. 10 – Graph After Determining Root Ports 27

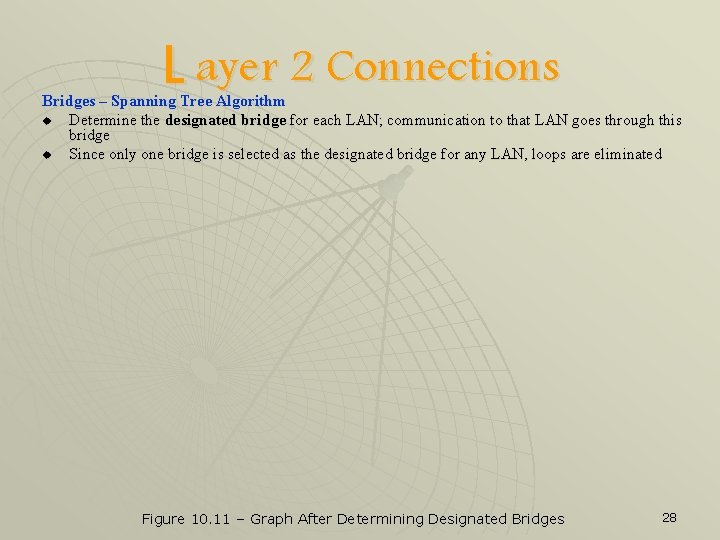
L ayer 2 Connections Bridges – Spanning Tree Algorithm u Determine the designated bridge for each LAN; communication to that LAN goes through this bridge u Since only one bridge is selected as the designated bridge for any LAN, loops are eliminated Figure 10. 11 – Graph After Determining Designated Bridges 28

L ayer 2 Connections Bridges – Spanning Tree Algorithm u Once designated bridges are determined, they become the active bridges in the network u Other bridges are still connected but can only send/receive PDUs; they cannot forward frames Figure 10. 12 – Network Topology Showing Active Bridge Connections 29

L ayer 2 Connections Bridges – Spanning Tree Algorithm u u u Each bridge maintains a timer, called a message timer Before that timer expires, the bridge must hear from the root bridge; the root bridge send periodic BPDUs for that If the timer expires without getting any messages from the root, then this is flagged as a root failure, and the process is initiated again Configuration BPDUs are also sent to indicate that the designated bridge is still alive; if these BPDUs are not received, the affected bridges reinitiates the designated bridge selection process In either case, the bridges reconfigure the active topology dynamically 30

L ayer 2 Connections Switches & Switched Ethernet u u Switches are similar to bridges, with one primary difference While a bridge can connect two LANs, a switch can connect multiple LANs through ports Figure 10. 13 – Connections Using Hubs & Switches 31

L ayer 2 Connections Switches & Switched Ethernet u u Although there may be many collision domains, a single broadcast domain can be defined The destination MAC address in an Ethernet frame can specify either a device address or a broadcast address A broadcast frame is forwarded over all ports and accepted by all devices Effectively, collision is now possible in a topology that uses hubs and switches (as in figure 10. 13) 32

L ayer 2 Connections Switches & Switched Ethernet u A fully Switched Ethernet topology solves this collision problem u With Switched Ethernet, all hubs are replaced by switches u u u Because switch ports lead to different collision domains, and each device is connected to a separate port, there is no more collision anywhere Furthermore, if connection between the device and the switch operate in fullduplex mode, there is no more need for CSMA/CD Each device is still capable of communicating with any other device, broadcast domain is also still there; there is just no more collision problems 33

L ayer 2 Connections Switches & Switched Ethernet u Another advantage of Switched Ethernet is that the bit rate for ports can vary Figure 10. 14 – Connections Using Only Switches 34

L ayer 2 Connections Switches & Switched Ethernet u Multiple layers of switches are also possible Figure 10. 15 – Private, Workgroup & Backbone Switches 35

u u u L ayer 3 Connections LANs, as well as layer 1 & 2 connections, typically cover small geographic areas and work over a simple topology, Bus, Ring, . . On the other hand Wide Area Networks, WANs, span the globe WANs however work over a more generalized topologies and require more sophisticated techniques to perform what they are expected to Figure 10. 18 – Generalized Network Topology 36

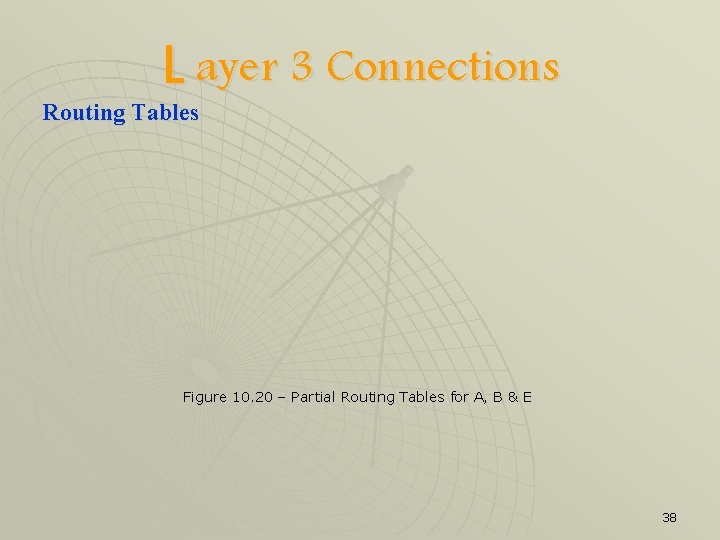
L ayer 3 Connections Routing Tables u u Similar to the ones that bridges/switches use, however these table do not normally specify the entire route Rather, they specify the next node in a route to a specified destination and the cost to get there Figure 10. 19 –Network & Associated Connection Costs 37

L ayer 3 Connections Routing Tables Figure 10. 20 – Partial Routing Tables for A, B & E 38

L ayer 3 Connections Routing Tables u u u Who defines the routing tables & how? The process that defines the routing tables is called routing algorithm Four such algorithms are: • • Centralized Routing Distributed Routing Static Routing Adaptive Routing 39

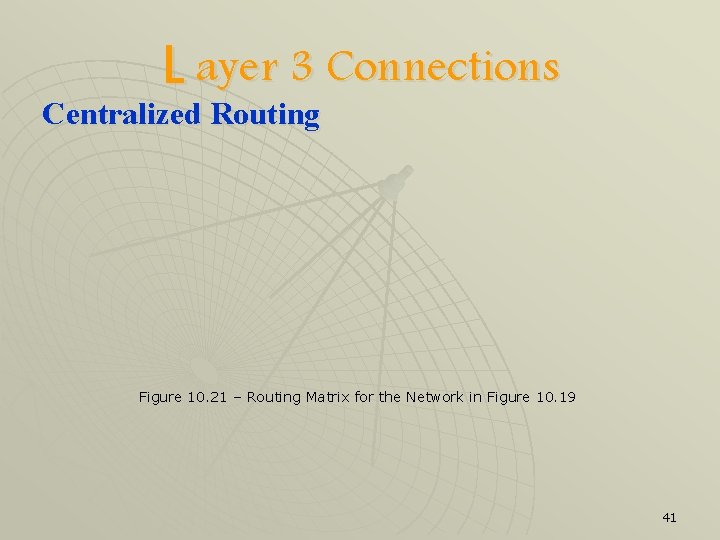
L ayer 3 Connections Centralized Routing u u u All interconnection information is generated and maintained at a single central station That station then broadcasts this information to all network nodes, so they can define their own routing tables One way to maintain the central information is through routing matrix 40

L ayer 3 Connections Centralized Routing Figure 10. 21 – Routing Matrix for the Network in Figure 10. 19 41

L ayer 3 Connections Distributed Routing u u No central control; each node must determine and maintain routing information independently This can be achieved by knowing the neighbors, cost to get to a neighbor and the cost from that neighbor to a destination More complex than centralized since each node must communicate with each of its neighbors instead of just one central station The complexity is driven also by the fact that the devices have a very limited knowledge of the entire network 42

L ayer 3 Connections Static Routing u u Once the node determines the routing table, it does not change it In other words, the initial cheapest path may not really be the cheapest path after sometime, yet it is always considered as the cheapest path The assumption here is that the conditions that led to the initial definition of the tables do not change Sometimes, this is a reasonable assumption, when? 43

L ayer 3 Connections Adaptive Routing u u Allows the network to respond to changes and update its routing tables accordingly If the cost of the route to be used changed, then adapt and use another route Could this lead to serious problems sometime? In general, it is difficult to implement adaptive routing efficiently, why? 44

D ijkstra’s Algorithm u u Sometimes called the Shortest-path Algorithm or Forward Search Algorithm Centralized, static algorithm, however it can be made adaptive by executing it periodically A node executing this algorithm is required to know the link costs among the nodes Each node executes this algorithm to determine the cheapest route to each network node 45

u D ijkstra’s Algorithm Iterative procedure. S: Set of nodes to which cheap route is known, W: Set of nodes direct connected to a node in S, X: A node in W to where cheap path found. Figure 10. 24 – Adding Nodes to S using Dijkstra’s Algorithm 46

D ijkstra’s Algorithm Figure 10. 25 – Network and Associated Connection Costs 47

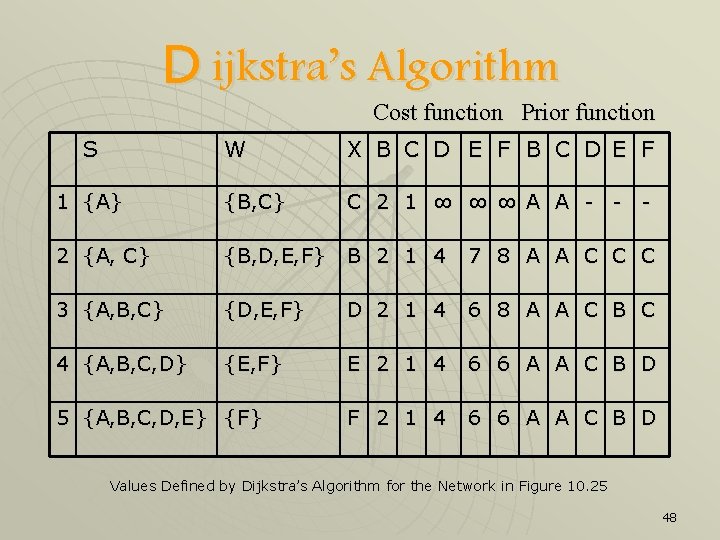
D ijkstra’s Algorithm Cost function Prior function S W X B C D E F 1 {A} {B, C} C 2 1 ∞ ∞ ∞ A A - - - 2 {A, C} {B, D, E, F} B 2 1 4 7 8 A A C C C 3 {A, B, C} {D, E, F} D 2 1 4 6 8 A A C B C 4 {A, B, C, D} {E, F} E 2 1 4 6 6 A A C B D F 2 1 4 6 6 A A C B D 5 {A, B, C, D, E} {F} Values Defined by Dijkstra’s Algorithm for the Network in Figure 10. 25 48

C ongestion & Deadlock Congestion u u u Excessive build-up of packets at one or more network nodes Reasons behind that include failed link, number of transmitted packets exceed network capacity, larger number of nodes than expected, …etc. Once congested, network suffers delays, possible retransmissions, incapability of a node to receive quickly due to being busy sending (or attempting to send), …etc. 49

C ongestion & Deadlock Congestion u There are several ways to handle congestion: • • Packet elimination Flow control Buffer allocation Choke packets 50

C ongestion & Deadlock Congestion – Packet Elimination u u u If excessive buildup of packets occur at a node, eliminate some of them This reduces the network load but suffer loss of packets Eventually, the higher level protocol will handle this loss by retransmitting the packets, hoping for sure that the congestion has subsided 51

C ongestion & Deadlock Congestion – Flow Control u u Designed to control the number of packets sent, however it does not really a congestion control approach Flow control limits the number of packets between two points, whereas congestion often involves packets coming into a node from many sources One solution is to limit the number that can be sent by a node, so the total may not congest the network; this has a bad side effect however; what is it? Let the nodes communicate with each others so that one reduces its traffic if total traffic is high; this won’t work either, why? 52

C ongestion & Deadlock Congestion – Buffer Allocation u u Very suitable for virtual circuit connections When the circuit is reserved, a specific amount of buffer is allocated to this communication Further requests for the same circuit will consume other portions of the available buffers If there is no more buffers, requests to use that circuit will be rejected and the higher level protocol must then fins an alternative route 53

C ongestion & Deadlock Congestion – Choke Packets u u More dynamic way to handle congestion Each node monitors the activity on its outgoing links and traces the utilization of the links u An increased utilization indicates higher risk of congestion u If the utilization exceeds specific threshold, the node is put into a warning state u u u While in the warning state, if the node receives a packet for further forwarding, it will respond by sending special choke packet to the sender When the sender receives a choke packet, it knows that congestion risk is high and hence reduces the number of sent packets for a period of time If the time expires without receiving any further choke packets, the sender goes back to its normal transmission rate; otherwise, it reduces the number of sent packets even further 54

C ongestion & Deadlock u In the worst case, congestion can become so sever that nothing moves Figure 10. 33 – Store-and-Forward Deadlock 55

C ongestion & Deadlock u Deadlock is also possible due to other causes Figure 10. 34 – Reassembly Deadlock 56

C ongestion & Deadlock u u One way to deal with store-and-forward deadlock is to do nothing until it happens Once occurred, try to handle it, possibly by dropping some packets to release buffer space It might be better however to try to prevent deadlock, or at least reduce the chances it occurs One approach is to maintain the number of hops (intermediate nodes) that a packet can go through then allocate a buffer based on that number 57

C ongestion & Deadlock Figure 10. 35 – Storing Packets Depending on Hop Count 58
 Aiman hanna
Aiman hanna Aiman hanna
Aiman hanna Aiman hanna
Aiman hanna Virtual circuit tables
Virtual circuit tables Backbone networks in computer networks
Backbone networks in computer networks Michelle chong company
Michelle chong company Aiman
Aiman Aiman habib
Aiman habib Crc in computer networks
Crc in computer networks Crc in computer networks
Crc in computer networks Traffic management in computer networks
Traffic management in computer networks Tanenbaum
Tanenbaum What is optimality principle in computer networks
What is optimality principle in computer networks Snmp supports which formatted protocol
Snmp supports which formatted protocol What is optimality principle in computer networks
What is optimality principle in computer networks Uses of computer networks in business applications
Uses of computer networks in business applications Definition of computer
Definition of computer Intro dns
Intro dns Diffserv vs intserv
Diffserv vs intserv Icmp in computer networks
Icmp in computer networks Http computer networks
Http computer networks Character stuffing in computer networks
Character stuffing in computer networks Dns in computer networks
Dns in computer networks Data communication and networking assignment questions
Data communication and networking assignment questions Distributed systems vs computer networks
Distributed systems vs computer networks Computer networks routing algorithms
Computer networks routing algorithms Crc example
Crc example Error detection and correction in computer networks
Error detection and correction in computer networks Internet transport protocol in computer networks
Internet transport protocol in computer networks Error control in computer networks
Error control in computer networks What is optimality principle in computer networks
What is optimality principle in computer networks Switching in data link layer
Switching in data link layer Apdatal
Apdatal Byte stuffing example
Byte stuffing example Character stuffing example
Character stuffing example Bit stuffing in hdlc
Bit stuffing in hdlc Sockets de berkeley
Sockets de berkeley What is the reverse request protocol
What is the reverse request protocol File sender uga
File sender uga Principles of network applications
Principles of network applications Https://speakerdeck.com/
Https://speakerdeck.com/ 15-441
15-441 Utopian simplex protocol
Utopian simplex protocol Sonet/sdh in computer network
Sonet/sdh in computer network Cell switching in computer networks
Cell switching in computer networks Physical structures in computer networks
Physical structures in computer networks Osi modeli
Osi modeli The network layer is concerned with of data.
The network layer is concerned with of data. History of computer network
History of computer network Fddi frame format
Fddi frame format Fast ethernet network
Fast ethernet network Exponential backoff in computer networks
Exponential backoff in computer networks Unrestricted simplex protocol
Unrestricted simplex protocol Dns in computer networks
Dns in computer networks Analogue and digital transmission in computer networks
Analogue and digital transmission in computer networks Cs1302 computer networks
Cs1302 computer networks Data communication components
Data communication components Congestion control principles
Congestion control principles William stallings computer networks
William stallings computer networks