Chapter 14 Technology and Crime Frank Schmalleger Power




































- Slides: 45

Chapter 14 Technology and Crime Frank Schmalleger Power. Point presentation created by Ellen G. Cohn, Ph. D.

The Advance of Technology n n n Technology and criminology have always been closely linked Technology can be used by crime fighters and lawbreakers As technology progresses, it facilitates new forms of behavior, including new crimes Criminology Today, 5 th ed Frank Schmalleger 2 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n High-tech criminals have several routes to obtain illegitimate access to computerized information n Direct access Computer trespass EMF decoders Criminology Today, 5 th ed Frank Schmalleger 3 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n Hacker: n n n A person who uses computers for exploration and exploitation May seek to destroy or alter data without otherwise accessing or copying the information Computer virus: A set of computer instructions that propagates copies or versions of itself into computer programs or data when it is executed Criminology Today, 5 th ed Frank Schmalleger 4 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n n The greatest threat to computers and data comes from inside the company The person most likely to invade a computer is an employee currently on the payroll Criminology Today, 5 th ed Frank Schmalleger 5 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n Computer crime: Any violation of a federal or state computer crime statute Criminology Today, 5 th ed Frank Schmalleger 6 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n David L. Carter’s typology of computer crime n n Crimes in which computers serve as targets Crimes in which computers serve as the instrumentality of the crime Crimes in which the computer is incidental to other crimes Crimes associated with the prevalence of computers Criminology Today, 5 th ed Frank Schmalleger 7 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n FBI typology of computer crime n n n Internal computer crimes (viruses) Internet and telecommunications crimes Support of criminal enterprises Computer-manipulation crimes Hardware, software, and information theft Criminology Today, 5 th ed Frank Schmalleger 8 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n Software piracy: The unauthorized and illegal copying of software programs • Softlifting • Hard disk loading • Internet piracy • Renting • Software counterfeiting • Original equipment manufacturer unbundling Criminology Today, 5 th ed Frank Schmalleger 9 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

High Technology and Criminal Opportunity n Cybercrime: Crime committed with the use of computers or via the manipulation of digital forms of data n Phone phreaks: n n n Use switched, dialed-access telephone services for exploration and exploitation One of the earliest forms of cybercrime Phishing n An internet-based scam that uses official-looking email messages to steal valuable information Criminology Today, 5 th ed Frank Schmalleger 10 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Technology and Criminal Mischief n Some computer crime is not committed for financial gain but is classified as “criminal mischief” n n Creating and transmitting malicious forms of programming code (malware) Typically associated with young, technologically sophisticated male offenders Criminology Today, 5 th ed Frank Schmalleger 11 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Technology and Criminal Mischief n Computer virus: Computer program designed to secretly invade computer systems to modify the way they operate or to alter the information they store n Polymorphic viruses n Use advanced encryption techniques to assemble varied but fully operational clones of itself Criminology Today, 5 th ed Frank Schmalleger 12 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime and the Law n n Cyber Security Enhancement Act (2002) Digital Theft Deterrence and Copyright Damages Improvement Act (1999) n No Electronic Theft Act (1997) n Communications Decency Act n Reno v. ACLU (1997) Criminology Today, 5 th ed Frank Schmalleger 13 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime and the Law n n Computer Fraud and Abuse Act (1984) Electronic Communications Privacy Act (1986) n National Stolen Property Act n Federal Wiretap Act (1968) Criminology Today, 5 th ed Frank Schmalleger 14 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime and the Law n Computer-related crime: Any illegal act for which knowledge of computer technology is involved for its perpetration, investigation, or prosecution n Computer abuse: Any unlawful incident associated with computer technology in which a victim suffered or could have suffered loss or in which a perpetrator by intention made or could have made gain Criminology Today, 5 th ed Frank Schmalleger 15 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

A Profile of Computer Criminals n Cyberspace: The computer-created matrix of virtual possibilities, including online services, wherein human beings interact with one another and with the technology itself n Cyberpunk: n n Literature that glorifies cyberspace and the people who inhabit it May be the counterculture movement of the future Criminology Today, 5 th ed Frank Schmalleger 16 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

A Profile of Computer Criminals n The average hacker is: n n Male, aged 16 -25, lives in the U. S. Computer user, not a programmer Hacks with software written by others Primary motivation is to gain access to Web sites and computer networks, not to profit financially Criminology Today, 5 th ed Frank Schmalleger 17 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

A Classification of Hackers n Pioneers n Game players n Scamps n Vandals n Explorers n Addicts Criminology Today, 5 th ed Frank Schmalleger 18 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

The History and Nature of Hacking n n n Not all hackers are kids Some hackers are high-tech computer operators Not all high-tech crimes are committed using computer technology n Some use the fruits of high technology to further crime Criminology Today, 5 th ed Frank Schmalleger 19 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime as a Form of White-Collar Crime n n Some see computer crime as a new form of white-collar crime The “ultimate expression of white-collar crime” Criminology Today, 5 th ed Frank Schmalleger 20 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime as a Form of White-Collar Crime n n Both types of crime are often committed through nonviolent means Access to computers or computer storage media, through employment-related knowledge or technical skills, is often needed Criminology Today, 5 th ed Frank Schmalleger 21 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime as a Form of White-Collar Crime n n Both involve information manipulations that either directly or indirectly create profits or losses Both can be committed by one or more individuals or by organizations, with victims ranging from individual clients, customers, employees, or other organizations Criminology Today, 5 th ed Frank Schmalleger 22 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime as a Form of White-Collar Crime n n Both are difficult to detect – discovery is often by accident or customer complaint The general public views many of these acts as less serious than violent crimes Criminology Today, 5 th ed Frank Schmalleger 23 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computer Crime as a Form of White-Collar Crime n n These crimes cost individuals, organizations, and society large amounts of money and other resources Prevention of these crimes requires a combination of legal, technical, managerial, security, and audit-monitoring controls Criminology Today, 5 th ed Frank Schmalleger 24 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Identity Theft n Identity theft: The misuse of another individual’s personal information to commit fraud n n A special kind of larceny Has the “feel” of a personal crime Criminology Today, 5 th ed Frank Schmalleger 25 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Identity Theft n Existing account fraud: n n n Thieves obtain account information involving accounts that are already open Less costly, more prevalent New account fraud: n n Thieves use personal information to open accounts in the victim’s name, make charges, and then disappear Less common, imposes greater costs and hardships on victims Criminology Today, 5 th ed Frank Schmalleger 26 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Identity Theft n Direct costs of identity theft n n n Out-of-pocket costs to victims and businesses Cost to repair identity Indirect costs n n Businesses pay for fraud prevention and mitigation of harm Victims may incur costs such as those involved in civil litigation initiated by creditors and in overcoming obstacles in obtaining or retaining credit Criminology Today, 5 th ed Frank Schmalleger 27 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Identity Theft Incidence n BJS definition of identity theft n n n Unauthorized use or attempted use of existing credit cards Unauthorized use or attempted use of other existing accounts Misuse of personal information to obtain new accounts or loans, or to commit other crimes Criminology Today, 5 th ed Frank Schmalleger 28 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

The Identity Theft Life Cycle n n n First stage: the identity thief attempts to acquire a victim’s personal information Second stage: the thief attempts to misuse the personal information s/he has acquired Third stage: thief has completed the crime and is enjoying the benefits while the victim is realizing the harm Criminology Today, 5 th ed Frank Schmalleger 29 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Identity Thieves: Who They Are n n Hard to classify identity thieves – most victims do not know who stole or misused their information Thieves often have no prior criminal background – may have preexisting relationship with the victim Steady increase in involvement of groups and organizations of career criminals in identity theft Increased involvement of foreign organized criminal groups Criminology Today, 5 th ed Frank Schmalleger 30 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

What Can Be Done? n n n Public awareness campaigns n Legislation n Information protection n Training Victim assistance Partnership and collaboration Criminology Today, 5 th ed Frank Schmalleger 31 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Technology in the Fight Against Crime Technology helps criminals and criminal justice personnel n n n Provides criminals new weapons to commit crimes Provides the criminal justice system with new tools to fight crime Criminology Today, 5 th ed Frank Schmalleger 32 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Technology in the Fight Against Crime Key law enforcement technology: n n n n n Traffic radar Computer databases of known offenders Machine-based expert systems Cellular communications Electronic eavesdropping DNA analysis Less-than-lethal weapons Computer-aided dispatch systems Criminology Today, 5 th ed Frank Schmalleger 33 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

DNA Technology DNA profiling n n The use of biological residue found at a crime scene for genetic comparisons aiding in the identification of criminal suspects Has resulted in the release of a number of unjustly convicted people and, in some cases, the discovery of the true offender A highly reliable forensic tool but not infallible Criminology Today, 5 th ed Frank Schmalleger 34 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

DNA Technology n Daubert standard: n n Test of scientific acceptability applicable to the gathering of evidence in criminal cases Factors used to determine if scientific evidence is reliable: n n Whether it was subjected to testing Whether it was subjected to peer review Known/potential rates of error Existence of standards controlling application of the techniques involved Criminology Today, 5 th ed Frank Schmalleger 35 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

DNA Technology Several states and the federal government are building digitized forensic DNA databases n n FBI’s National DNA Index System n DNA Identification Act of 1994 n Genetic profiling The use of biotechnology to identify the unique characteristics of an individual’s DNA Criminology Today, 5 th ed Frank Schmalleger 36 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computers as Crime-Fighting Tools n n n Specialized Web sites to connect people Automated fingerprint identification systems (AFIS) Online criminal information and database services Criminology Today, 5 th ed Frank Schmalleger 37 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Computers as Crime-Fighting Tools n PC radios n Expert systems n Specialized software programs to assist police artists Criminology Today, 5 th ed Frank Schmalleger 38 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Combating Computer Crime Threat analysis (risk analysis): n A complete and thorough assessment of the kinds of perils facing an organization Once threats are identified, strategies to deal with them can be introduced n n n An audit trail traces and records the activities of computer operators and allows auditors to examine the sequence of events relating to any transaction A powerful tool for identifying instances of computer crime Criminology Today, 5 th ed Frank Schmalleger 39 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Police Investigation of Computer Crime n n n Few police departments have the time or the qualified personnel to investigate computer crimes effectively Many departments place a low priority on computer crime May intentionally avoid computer-crime investigations Criminology Today, 5 th ed Frank Schmalleger 40 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Police Investigation of Computer Crime n n n FBI’s National Computer Crime Squad investigates violations of federal computer crime laws The U. S. DOJ’s Computer Crime and Intellectual Property Section focuses on computer and intellectual property crime DCS-1000 – FBI’s network “sniffer” Criminology Today, 5 th ed Frank Schmalleger 41 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Dealing with Computer Criminals Sanctions that may deter high-tech offenders include: n n n Confiscating equipment used to commit a computer crime Limiting the offender’s use of computers Restricting the offender’s freedom to accept jobs involving computers Can supplement with a short jail term Criminology Today, 5 th ed Frank Schmalleger 42 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Securing the Internet The Internet: n n n The world’s largest computer network Consists of tens of thousands of computers around the world that are linked together Commission on Critical Infrastructure Protection – created by Pres. Clinton, 1996 n n Assessed threats to the nation’s computer networks and recommended policies to protect them Led to 1998 creation of the National Infrastructure Protection Center (NIPC) Succeed by the Information Analysis and Infrastructure Protection Directorate (part of DHS) Criminology Today, 5 th ed Frank Schmalleger 43 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Securing the Internet U. S. Computer Emergency Readiness Team (US-CERT) – established in 2003 n n Partnership between DHS and public and private sectors Created to protect U. S. Internet infrastructure and coordinate defenses against cyberattacks US-CERT is also in charge of the National Cyber Alert System Criminology Today, 5 th ed Frank Schmalleger 44 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.

Policy Issues: Personal Freedoms in the Information Age n First Amendment n n n Freedom of speech Are electronic communications protected? Fourth Amendment n n Freedom from unreasonable searches and seizures Does this include electronic information? Criminology Today, 5 th ed Frank Schmalleger 45 © 2009 Pearson Education, Upper Saddle River, NJ 07458. All Rights Reserved.
 Frank william abagnale jr wife
Frank william abagnale jr wife Power triangle formula
Power triangle formula Chapter 7 deviance crime and social control
Chapter 7 deviance crime and social control Locard exchange principle
Locard exchange principle Solar power satellites and microwave power transmission
Solar power satellites and microwave power transmission Potential power
Potential power Dispersive power of a grating can be defined as
Dispersive power of a grating can be defined as Street law chapter 7
Street law chapter 7 Born a crime chapter 15 summary
Born a crime chapter 15 summary Druggist fold steps
Druggist fold steps Fluid power technology
Fluid power technology Flex28024a
Flex28024a Power of a power property
Power of a power property General power rule
General power rule Power angle curve in power system stability
Power angle curve in power system stability Powerbi in powerpoint
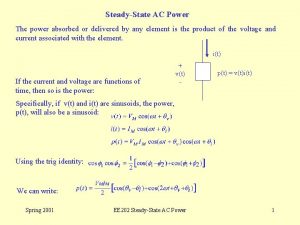
Powerbi in powerpoint Power delivered vs power absorbed
Power delivered vs power absorbed Henry taylor management
Henry taylor management People who work with computers while doing business.
People who work with computers while doing business. Chapter 28 12-volt and hv battery technology
Chapter 28 12-volt and hv battery technology Chapter 12 computer and technology in health care
Chapter 12 computer and technology in health care What service industries make extensive use of computers?
What service industries make extensive use of computers? Chapter 1 information technology the internet and you
Chapter 1 information technology the internet and you Chapter 1 information technology the internet and you
Chapter 1 information technology the internet and you Unit 4 criminology revision
Unit 4 criminology revision Crime scene factoring and quadratic functions answer key
Crime scene factoring and quadratic functions answer key Crime and deviance sociology revision
Crime and deviance sociology revision What is rational choice theory?
What is rational choice theory? Processing crime and incident scenes
Processing crime and incident scenes Crime scene factoring and quadratic functions answer key
Crime scene factoring and quadratic functions answer key Transnational crime and the developing world
Transnational crime and the developing world Compass point method
Compass point method Crime and punishment revision guide
Crime and punishment revision guide Crime and punishment characters
Crime and punishment characters Tudor crime and punishment
Tudor crime and punishment Difference between crime and deviance
Difference between crime and deviance Hirschi gottfredson
Hirschi gottfredson Unit 4 wjec criminology
Unit 4 wjec criminology War making and state making as organized crime summary
War making and state making as organized crime summary Medieval crime and punishment facts
Medieval crime and punishment facts Gcse history past papers edexcel
Gcse history past papers edexcel Assignment
Assignment Biology and crime
Biology and crime Kahoot crime and punishment
Kahoot crime and punishment Crime and punishment in medieval japan
Crime and punishment in medieval japan Developmental theories
Developmental theories