Chapter 11 Data Link Control DLC Copyright The














- Slides: 43

Chapter 11 Data Link Control (DLC) Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.

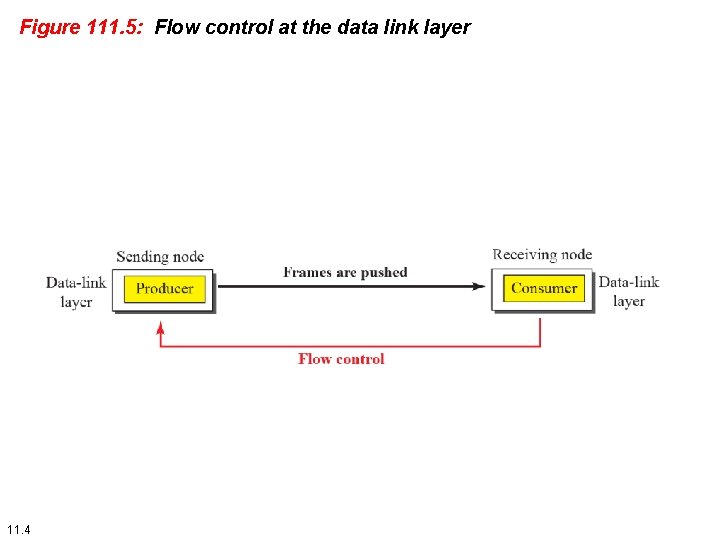
11 -1 DLC SERVICES The most important responsibilities of the data link layer are flow control and error control. these functions are known as : data link control. 11. 2

111. 2 Flow and Error Control Ø Data must be checked and processed before they can be used. Ø The rate of such processing is often slower than the rate of transmission. Ø For this reason , each receiver has a buffer to store incoming data until they are processed. Ø If buffer begin to fill up, the sender must slow or halt transmission. 11. 3

Figure 111. 5: Flow control at the data link layer 11. 4

11 -2 DATA-LINK LAYER PROTOCOLS Traditionally four protocols have been defined for the data-link layer to deal with flow and error control: Simple, Stop-and-Wait, Go-Back-N, and Selective-Repeat. 11. 5

Figure 111. 6: FSMs 11. 6

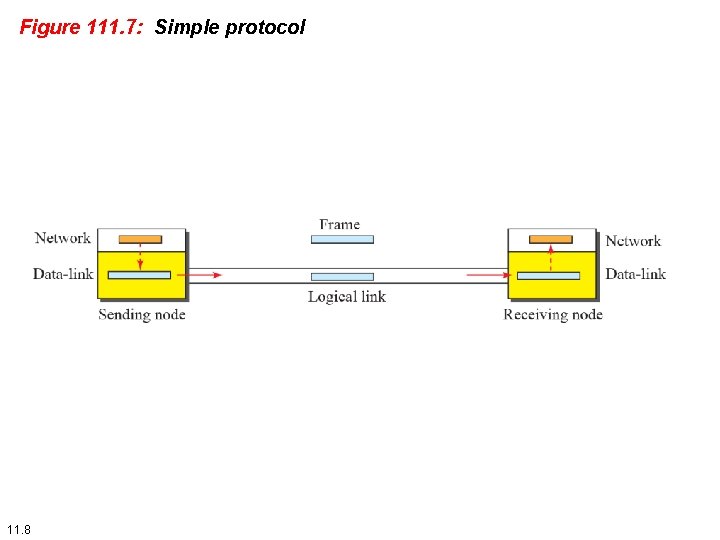
111. 2. 1 Simple Protocol Our first protocol is a simple protocol with neither flow nor error control. We assume that the receiver can immediately handle any frame it receives. In other words, the receiver can never be overwhelmed with incoming frames. Figure 111. 7 shows the layout for this protocol. 11. 7

Figure 111. 7: Simple protocol 11. 8

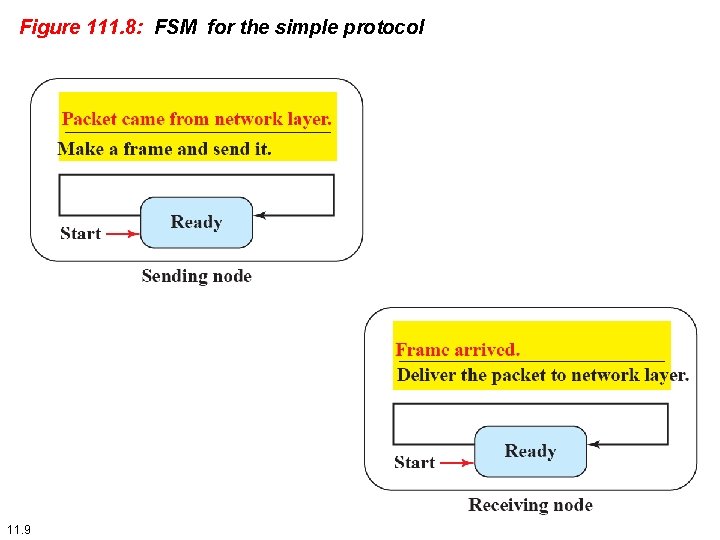
Figure 111. 8: FSM for the simple protocol 11. 9

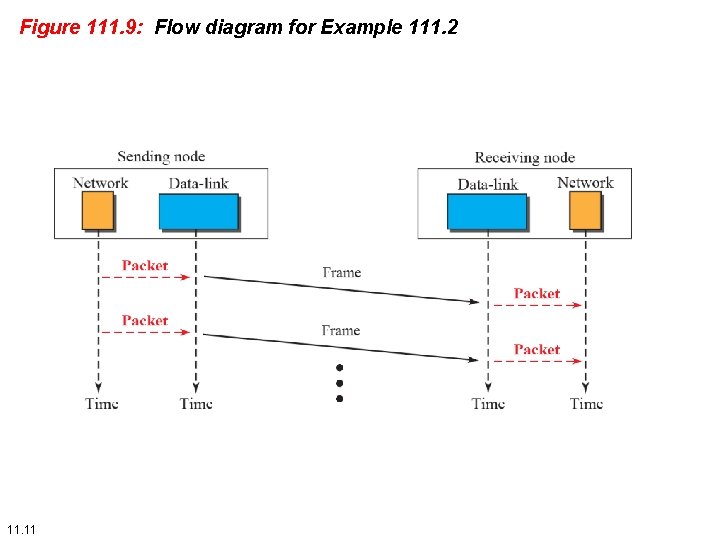
Example 111. 2 Figure 111. 9 shows an example of communication using this protocol. It is very simple. The sender sends frames one after another without even thinking about the receiver. 11. 10

Figure 111. 9: Flow diagram for Example 111. 2 11. 11

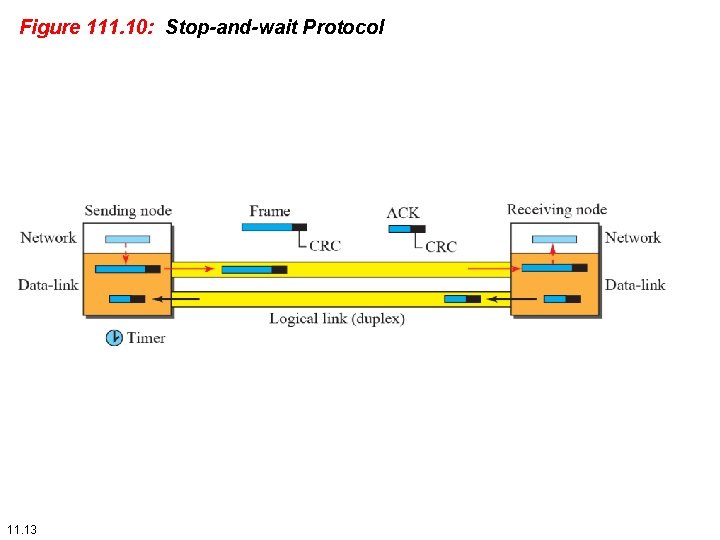
111. 2. 2 Stop-and-Wait Protocol Our second protocol is called the Stop-and-Wait protocol, which uses both flow and error control. We show a primitive version of this protocol here, but we discuss the more sophisticated version in Chapter 23 when we have learned about sliding windows. In this protocol, the sender sends one frame at a time and waits for an acknowledgment before sending the next one. To detect corrupted frames, we need to add a CRC (see Chapter 10) to each data frame. 11. 12

Figure 111. 10: Stop-and-wait Protocol 11. 13

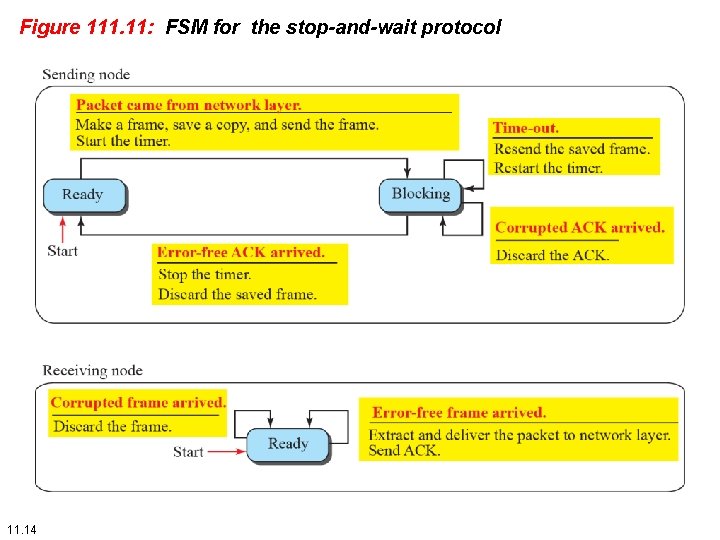
Figure 111. 11: FSM for the stop-and-wait protocol 11. 14

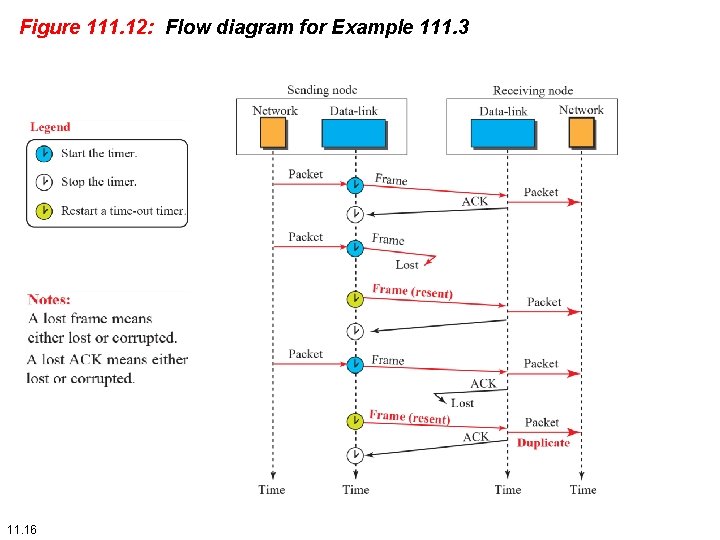
Example 111. 3 Figure 111. 12 shows an example. The first frame is sent and acknowledged. The second frame is sent, but lost. After time -out, it is resent. The third frame is sent and acknowledged, but the acknowledgment is lost. The frame is resent. However, there is a problem with this scheme. The network layer at the receiver site receives two copies of the third packet, which is not right. In the next section, we will see how we can correct this problem using sequence numbers and acknowledgment numbers. 11. 15

Figure 111. 12: Flow diagram for Example 111. 3 11. 16

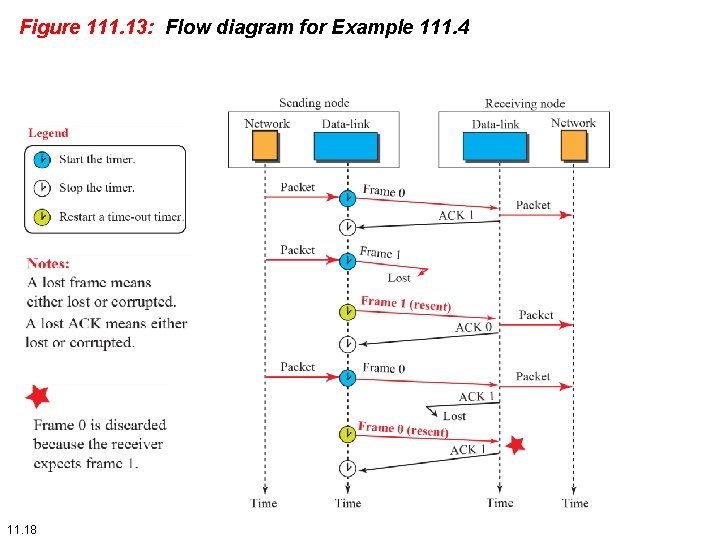
Example 111. 4 Figure 111. 13 shows how adding sequence numbers and acknowledgment numbers can prevent duplicates. The first frame is sent and acknowledged. The second frame is sent, but lost. After time-out, it is resent. The third frame is sent and acknowledged, but the acknowledgment is lost. The frame is resent. 11. 17

Figure 111. 13: Flow diagram for Example 111. 4 11. 18

111. 2. 3 Piggybacking The two protocols we discussed in this section are designed for unidirectional communication, in which data is flowing only in one direction although the acknowledgment may travel in the other direction. Protocols have been designed in the past to allow data to flow in both directions. However, to make the communication more efficient, the data in one direction is piggybacked with the acknowledgment in the other direction. 11. 19

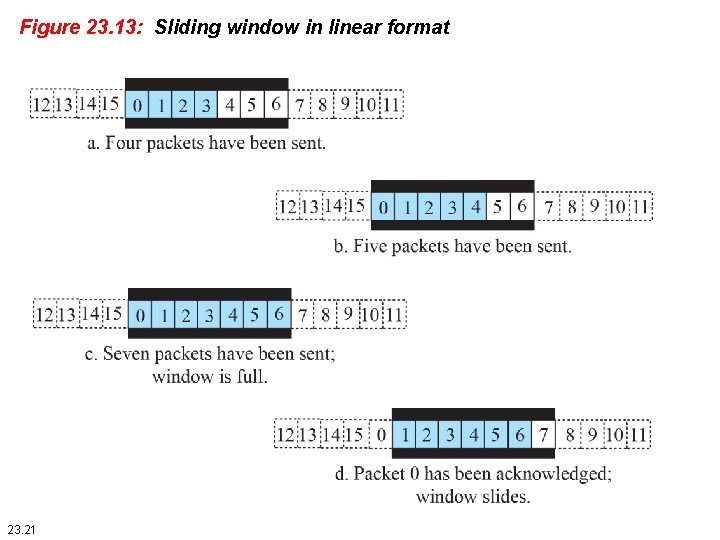
Sliding window protocols apply Pipelining : üGo-Back-N ARQ üSelective Repeat ARQ Ø Sliding window protocols improve the efficiency Ø multiple frames should be in transition while waiting for ACK. Let more than one frame to be outstanding. Ø Outstanding frames: frames sent but not acknowledged Ø We can send up to W frames and keep a copy of these frames(outstanding) until the ACKs arrive. Ø This procedures requires additional feature

Figure 23. 13: Sliding window in linear format 23. 21

23 -2 TRANSPORT-LAYER PROTOCOLS We can create a transport-layer protocol by combining a set of services described in the previous sections. To better understand the behavior of these protocols, we start with the simplest one and gradually add more complexity. The TCP/IP protocol uses a transport-layer protocol that is either a modification or a combination of some of these protocols. 23. 22

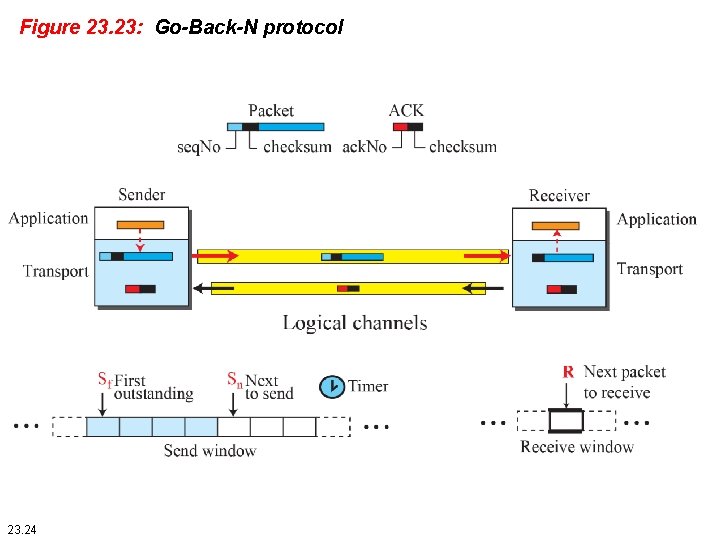
23. 2. 3 Go-Back-N Protocol (GBN) To improve the efficiency of transmission (to fill the pipe), multiple packets must be in transition while the sender is waiting for acknowledgment. In other words, we need to let more than one packet be outstanding to keep the channel busy while the sender is waiting for acknowledgment. In this section, we discuss one protocol that can achieve this goal; in the next section, we discuss a second. The first is called Go-Back-N (GBN). 23. 23

Figure 23. 23: Go-Back-N protocol 23. 24

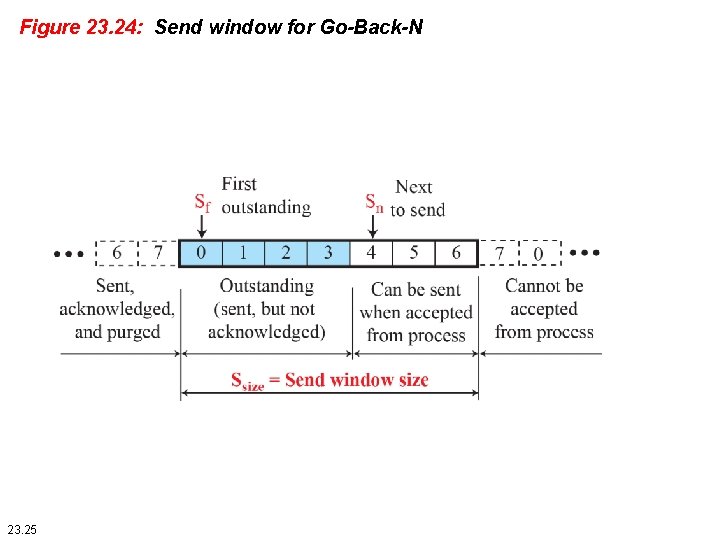
Figure 23. 24: Send window for Go-Back-N 23. 25

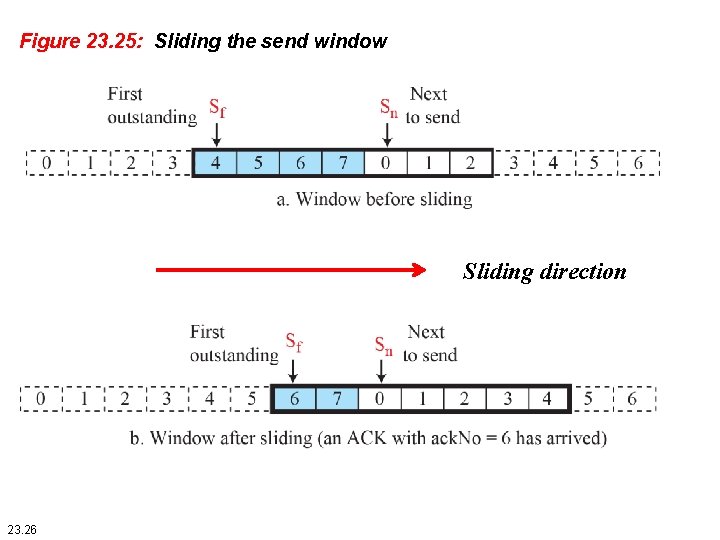
Figure 23. 25: Sliding the send window Sliding direction 23. 26

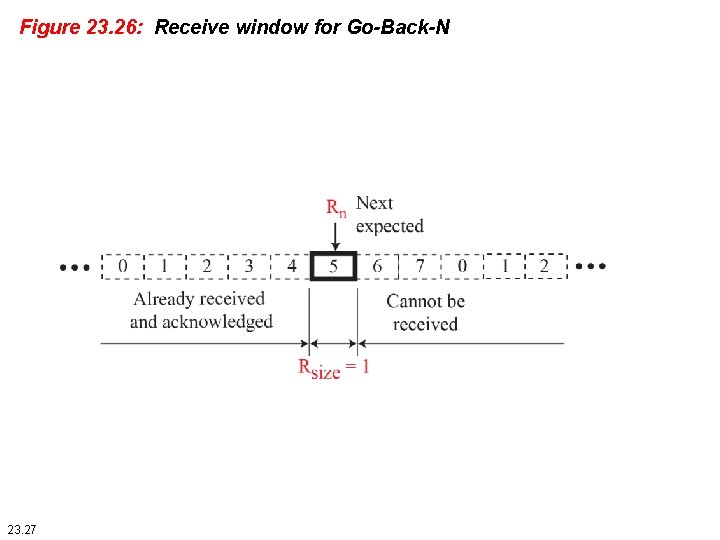
Figure 23. 26: Receive window for Go-Back-N 23. 27

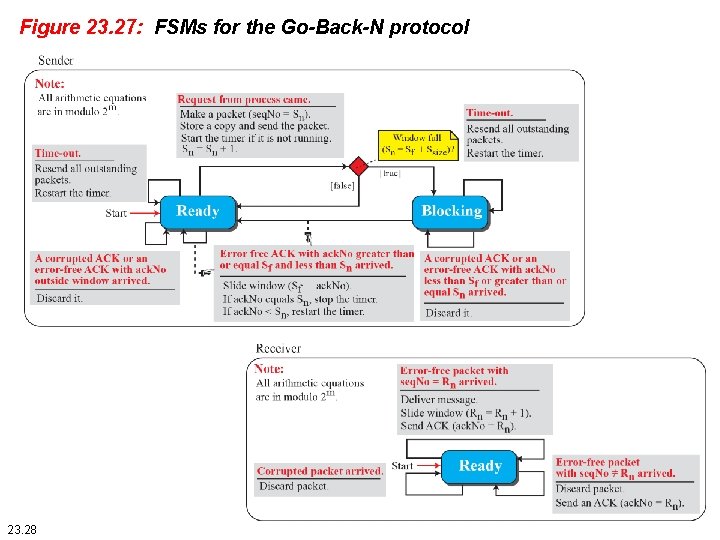
Figure 23. 27: FSMs for the Go-Back-N protocol 23. 28

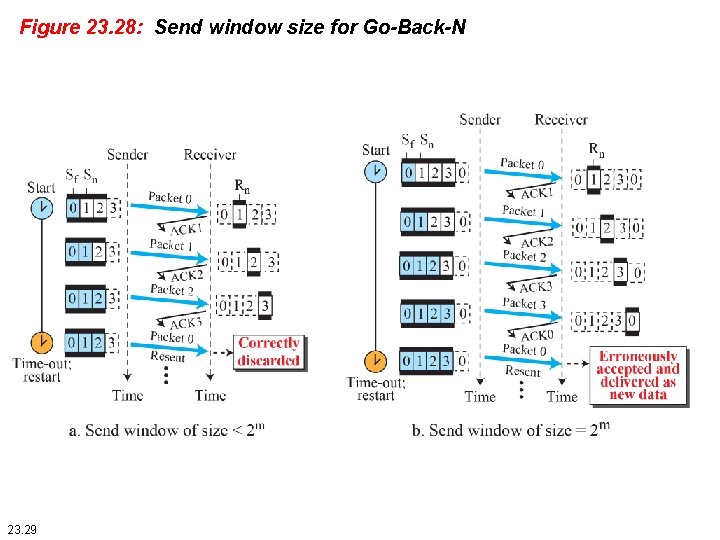
Figure 23. 28: Send window size for Go-Back-N 23. 29

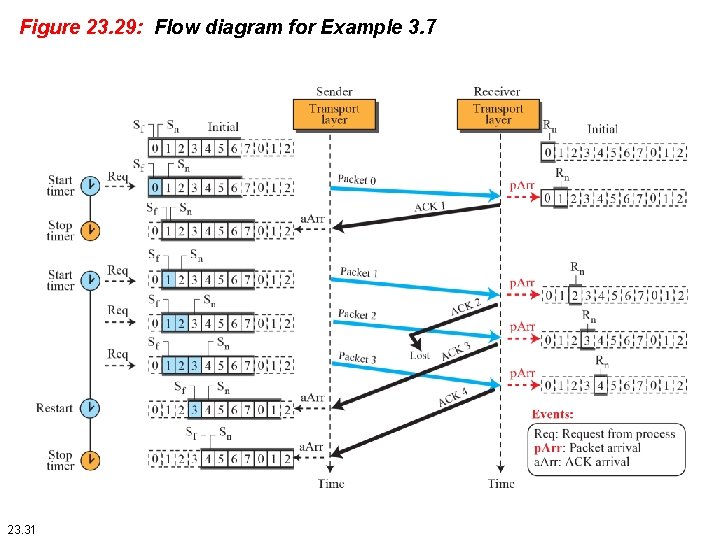
Example 23. 7 Figure 23. 29 shows an example of Go-Back-N. This is an example of a case where the forward channel is reliable, but the reverse is not. No data packets are lost, but some ACKs are delayed and one is lost. The example also shows how cumulative acknowledgments can help if acknowledgments are delayed or lost. 23. 30

Figure 23. 29: Flow diagram for Example 3. 7 23. 31

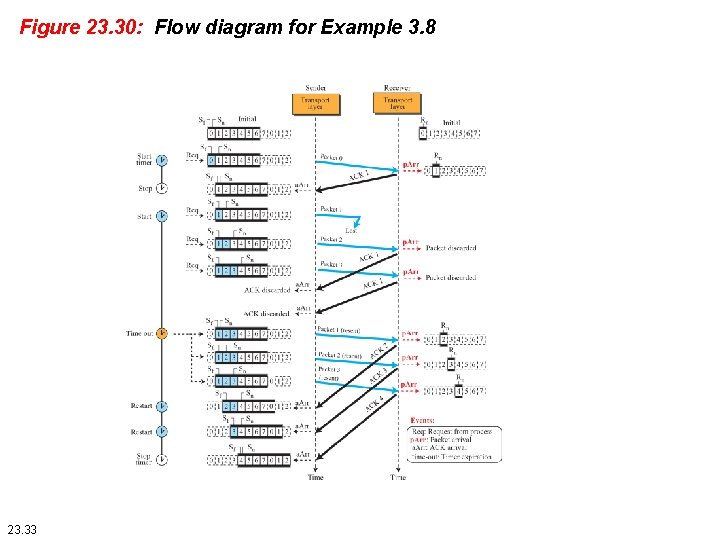
Example 23. 8 Figure 23. 30 shows what happens when a packet is lost. Packets 0, 1, 2, and 3 are sent. However, packet 1 is lost. The receiver receives packets 2 and 3, but they are discarded because they are received out of order (packet 1 is expected). When the receiver receives packets 2 and 3, it sends ACK 1 to show that it expects to receive packet 23. However, these ACKs are not useful for the sender because the ack. No is equal to Sf, not greater that Sf. So the sender discards them. When the time-out occurs, the sender resends packets 1, 2, and 3, which are acknowledged. 23. 32

Figure 23. 30: Flow diagram for Example 3. 8 23. 33

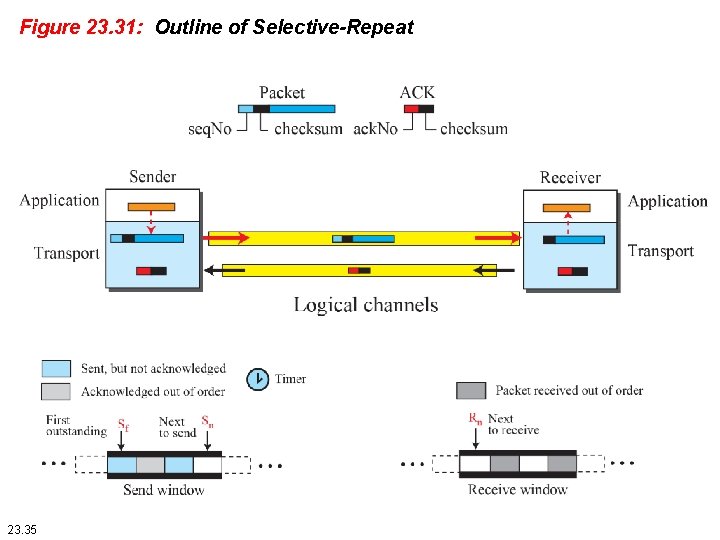
23. 2. 4 Selective-Repeat Protocol The Go-Back-N protocol simplifies the process at the receiver. The receiver keeps track of only one variable, and there is no need to buffer out-of-order packets; they are simply discarded. However, this protocol is inefficient if the underlying network protocol loses a lot of packets. Each time a single packet is lost or corrupted, the sender resends all outstanding packets, even though some of these packets may have been received safe and sound but of order. 23. 34

Figure 23. 31: Outline of Selective-Repeat 23. 35

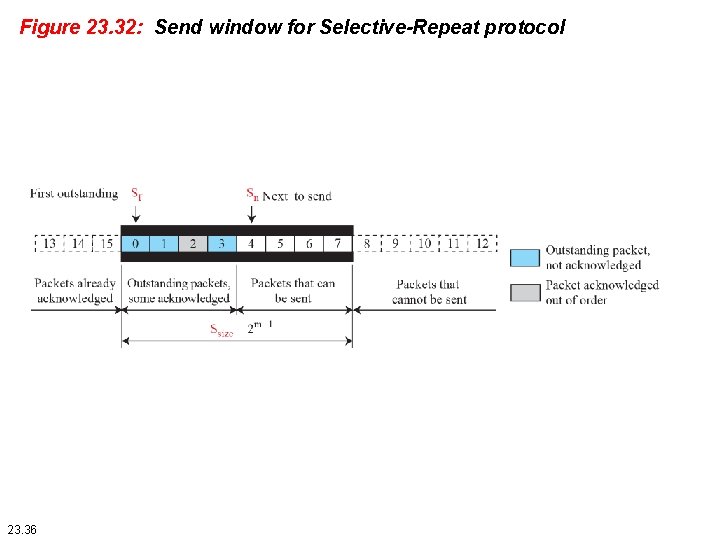
Figure 23. 32: Send window for Selective-Repeat protocol 23. 36

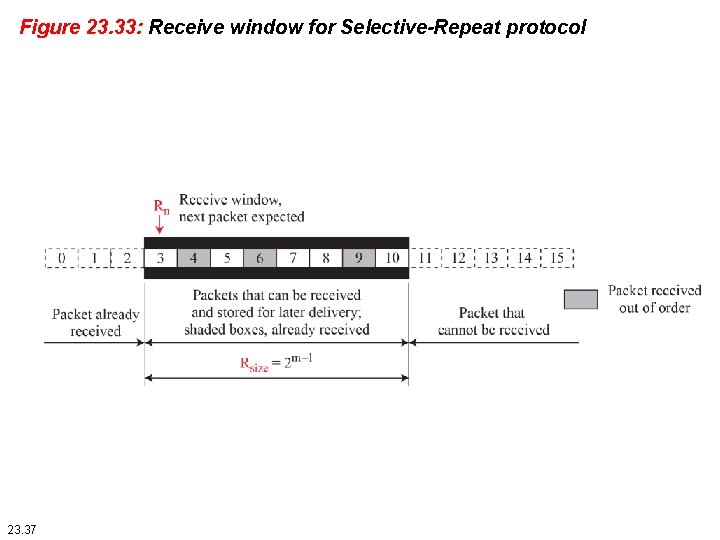
Figure 23. 33: Receive window for Selective-Repeat protocol 23. 37

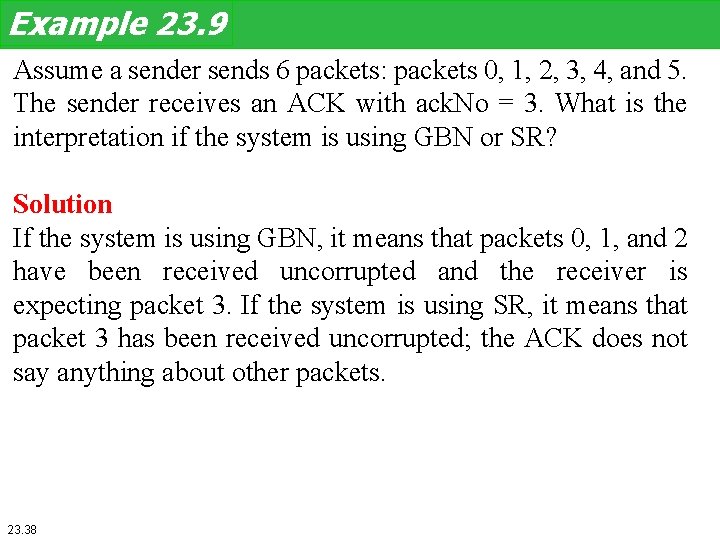
Example 23. 9 Assume a sender sends 6 packets: packets 0, 1, 2, 3, 4, and 5. The sender receives an ACK with ack. No = 3. What is the interpretation if the system is using GBN or SR? Solution If the system is using GBN, it means that packets 0, 1, and 2 have been received uncorrupted and the receiver is expecting packet 3. If the system is using SR, it means that packet 3 has been received uncorrupted; the ACK does not say anything about other packets. 23. 38

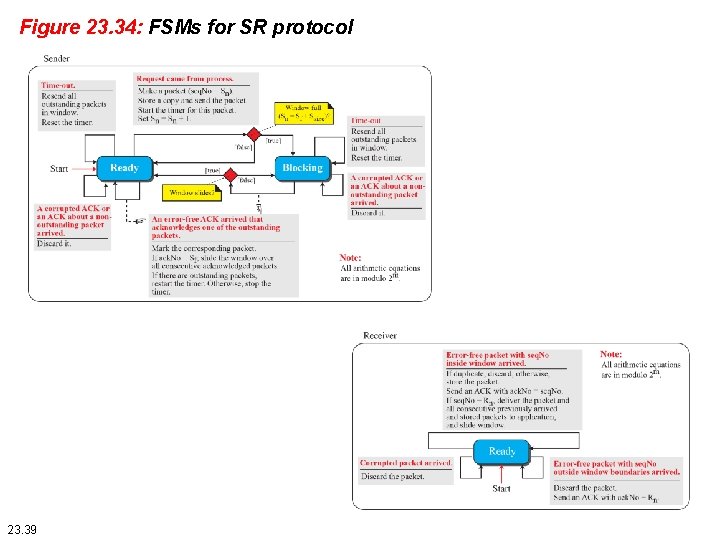
Figure 23. 34: FSMs for SR protocol 23. 39

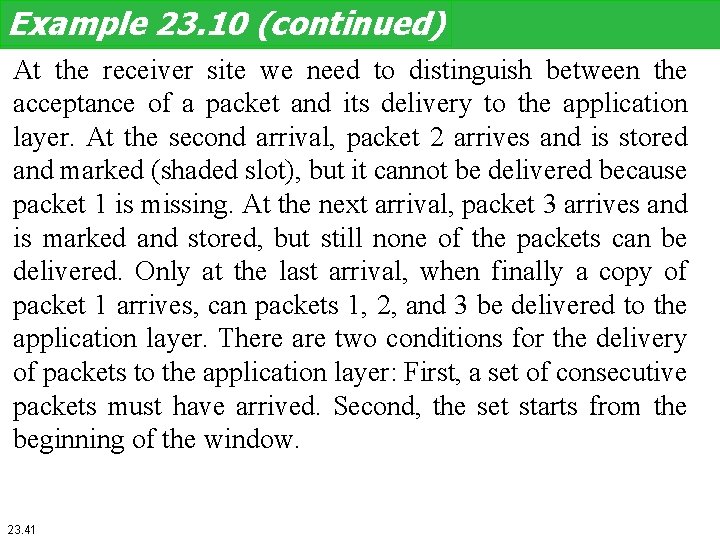
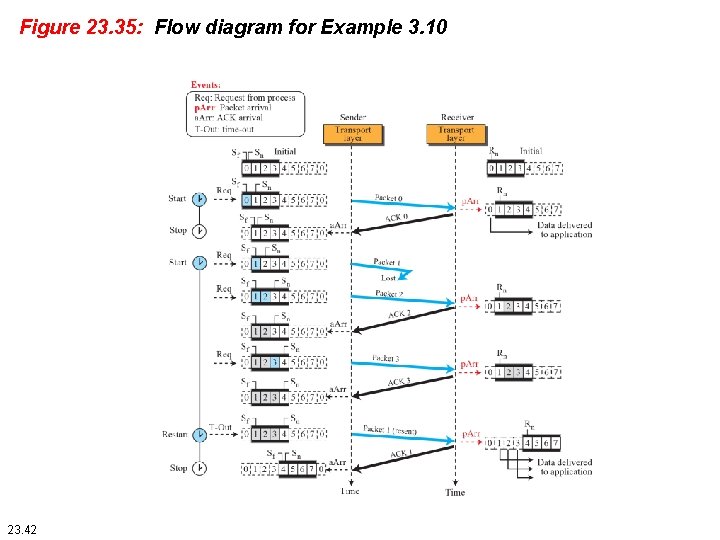
Example 23. 10 This example is similar to Example 23. 8 (Figure 23. 30) in which packet 1 is lost. We show Selective-Repeat behaves in this case. Figure 3. 35 shows the situation. At the sender, packet 0 is transmitted and acknowledged. Packet 1 is lost. Packets 2 and 3 arrive out of order and are acknowledged. When the timer times out, packet 1 (the only unacknowledged packet) is resent and is acknowledged. The send window then slides. 23. 40

Example 23. 10 (continued) At the receiver site we need to distinguish between the acceptance of a packet and its delivery to the application layer. At the second arrival, packet 2 arrives and is stored and marked (shaded slot), but it cannot be delivered because packet 1 is missing. At the next arrival, packet 3 arrives and is marked and stored, but still none of the packets can be delivered. Only at the last arrival, when finally a copy of packet 1 arrives, can packets 1, 2, and 3 be delivered to the application layer. There are two conditions for the delivery of packets to the application layer: First, a set of consecutive packets must have arrived. Second, the set starts from the beginning of the window. 23. 41

Figure 23. 35: Flow diagram for Example 3. 10 23. 42

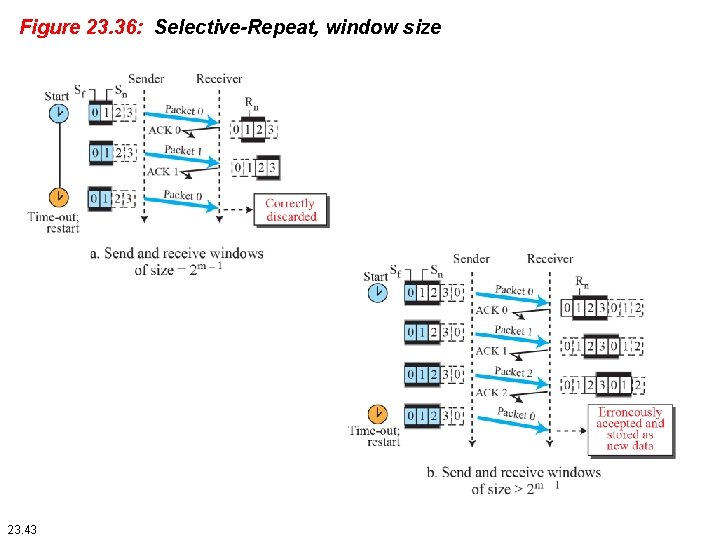
Figure 23. 36: Selective-Repeat, window size 23. 43