Anatomy of an Attack Patti Sauder Senior Security




















- Slides: 42

Anatomy of an Attack Patti Sauder Senior Security Engineer October 4, 2012

Agenda § § 2 hreats T & s n io t a iv t o M k c a t t A n a f o y m Anato Hacker Tools Live Demo - CONFIDENTIAL -

Imperva Overview Our mission. Protect the data that drives business Our market segment. Enterprise Data Security Our global business. • Founded in 2002; • • • Global operations; HQ in Redwood Shores, CA 375+ employees Customers in 50+ countries Our customers. 1, 700+ direct; Thousands cloud-based • • • 3 4 of the top 5 global financial data service firms 4 of the top 5 global telecommunications firms 4 of the top 5 global computer hardware companies 3 of the top 5 US commercial banks 150+ government agencies and departments

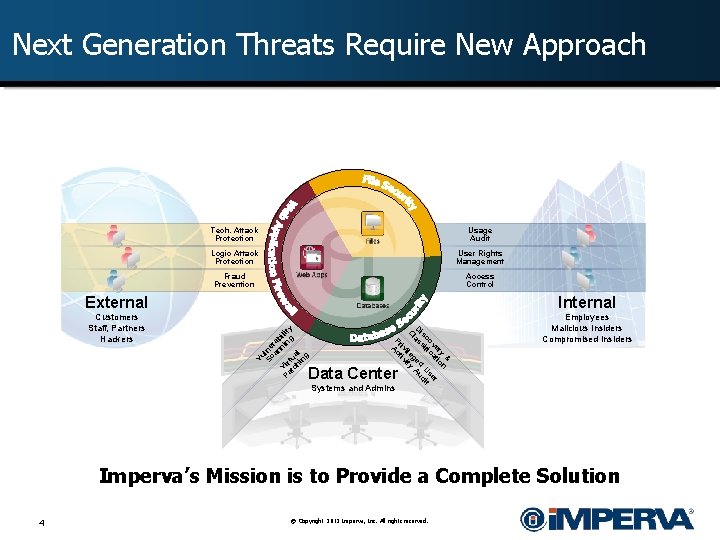
Next Generation Threats Require New Approach Tech. Attack Protection Usage Audit Logic Attack Protection User Rights Management Fraud Prevention Access Control Employees Malicious Insiders Compromised Insiders Vu Sc lne an rab ni ili Pa Vir ng ty tc tua hi l ng Internal Customers Staff, Partners Hackers & ry on r i ve at se co fic U it is si d ud D as l ge A C ile ity iv tiv Pr Ac External Data Center Systems and Admins Imperva’s Mission is to Provide a Complete Solution 4 © Copyright 2012 Imperva, Inc. All rights reserved.

“Never been easier” …to become a cybercriminal. Hacking - Foreign Secretary William Hague reported to an international conference that it has “never been easier” to become a cybercriminal. -- BBC News October 4, 2012 5

Motivation Hacking • Hacking for reputation, military or financial gain. Typically underground or secretive teams and organizations using significant effort to hide their nefarious activities. • Often an income source for organized crime. • Significant steps to hid their activities Social Hacktivism • Combination of hacking and activism, often powered by the use of social media • Usually political or ethical opinion drivers. • Proven to be quite effective • Verizon Data Breach report states that 58% of stolen records in 2011 were due to hacktivism. With zero losses were attributed to hacktivism in previous years. 6

Types of Threats Malicious Insiders According to the Verizon 2011 Data Breach Investigations Report, the number of incidents implicating malicious insiders doubled in 2011. Example: Wikileaks and Zappos Compromised Insiders According to the Office of the Director of National Intelligence, almost half of all computers in the United States have been compromised in some manner and ~60, 000 new pieces of malware identified per day. Automated Attacks 7 “External agents have created economies of scale by refining standardized, automated, and highly repeatable attacks directed at smaller, vulnerable, and largely homogenous targets. ” – Verizon 2011 Data Breach Investigations Report

Industrialization of Hacking and Automation Roles Researching Vulnerabilities Developing Exploits Growing Botnets Exploiting Targets Creating Tools Consumers Optimization Direct Value – i. e. IP, CC# Command & Control Malware Distribution Phishing & spam DDo. S Use & Rent Resources Great at using information/tools already in place 8 Automation Growing Botnets and Exploiting Vulnerabilities Selecting Targets via Search Engines Templates & Kits Centralized Management Service & Support Department

Situation Today # of websites (estimated: July 2011) : 357, 292, 065 x 230 But which will be 1% exploited? # of vulnerabilities : 821, 771, 600 vulnerabilities in active circulation http: //news. netcraft. com/archives/2011/07/08/july-2011 -web-server-survey. html https: //www. whitehatsec. com/home/resource/stats. html

Data is hacker currency Canadian credit cards: Visa: $3 Master. Card: $3 American Express: $6 Discover: $6 US credit cards: Visa: $2 Master. Card: $3 American Express: $5 Discover: $6 EU credit cards: Visa: $6 Master. Card: $6 American Express: $8 Discover: $8

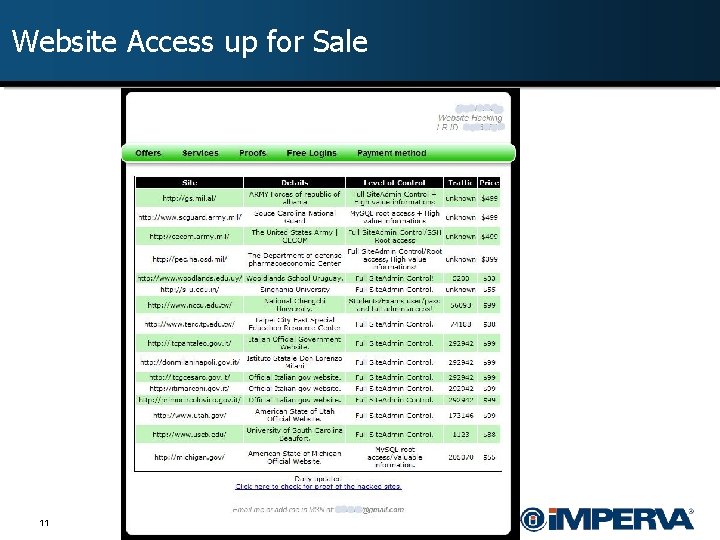
Website Access up for Sale 11 - CONFIDENTIAL -

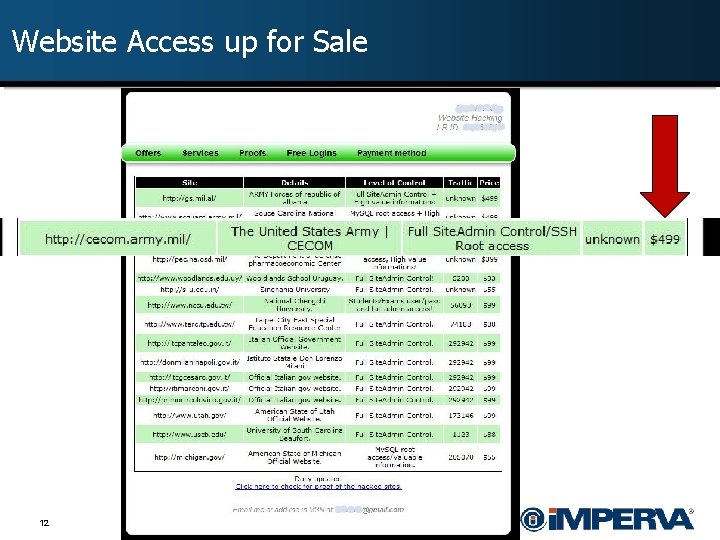
Website Access up for Sale 12 - CONFIDENTIAL -

Automation Makes It Easy § In one hacker forum, it was boasted that one hacker had found 5012 websites vulnerable to SQLi through automation tools. Note: • Due to automation, hackers can be effective in small groups – i. e. Lulzsec. • Automation also means that attacks are equal opportunity offenders. They don’t discriminate between well-known and unknown sites.

The Story

Understanding the Threat Landscape - Sources § Hacking data source + Categorized attacks across 40 web applications + Reviewed all HTTP & HTTPS traffic + 6 months: June to November 2011 § Social hacktivism data source + Imperva mitigated attack in 2011 + Activity lasted 25 days + Defensive line was network firewall, IDS, WAF, web servers and anti-virus.

Types of Attackers Both Hacking and Social Hacktivism Skilled hackers—This group have genuine hacking experience and are quite savvy with web application exploitation. Nontechnical—This group can be quite large, ranging from a Social few dozen to a few hundred volunteers. Directed by the skilled Hacktivism Only hackers, their role is primarily to conduct DDo. S attacks by either downloading and using special software or visiting websites designed to flood victims with excessive traffic. 16

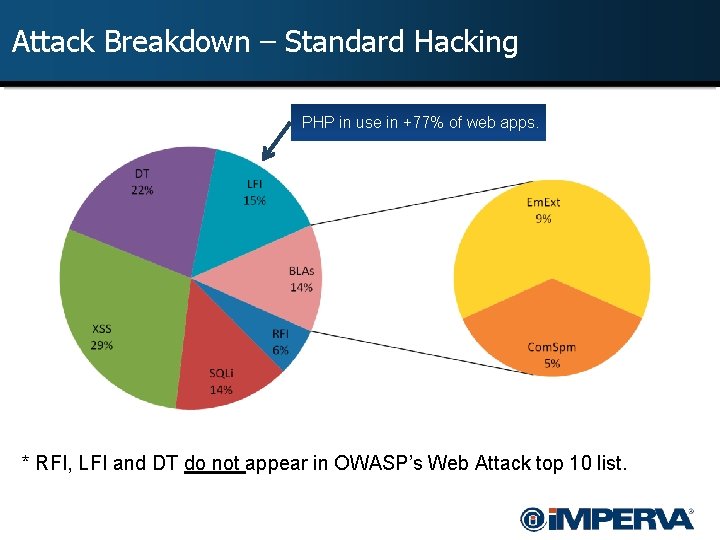
Attack Breakdown – Standard Hacking PHP in use in +77% of web apps. * RFI, LFI and DT do not appear in OWASP’s Web Attack top 10 list.

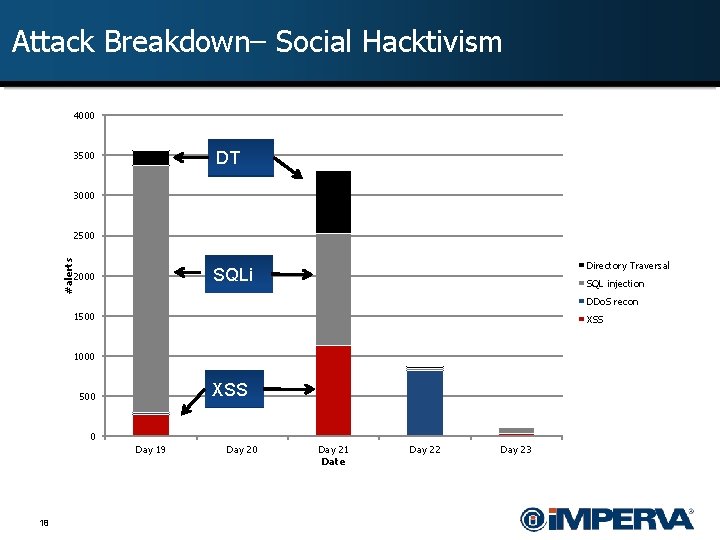
Attack Breakdown– Social Hacktivism 4000 DT 3500 3000 #alerts 2500 Directory Traversal SQLi 2000 SQL injection DDo. S recon 1500 XSS 1000 XSS 500 0 Day 19 18 Day 20 Day 21 Date Day 22 Day 23

Anatomy of an Attack eeds c c u S s u o m y n o § How An § Recruitment § Methodology 19 - CONFIDENTIAL -

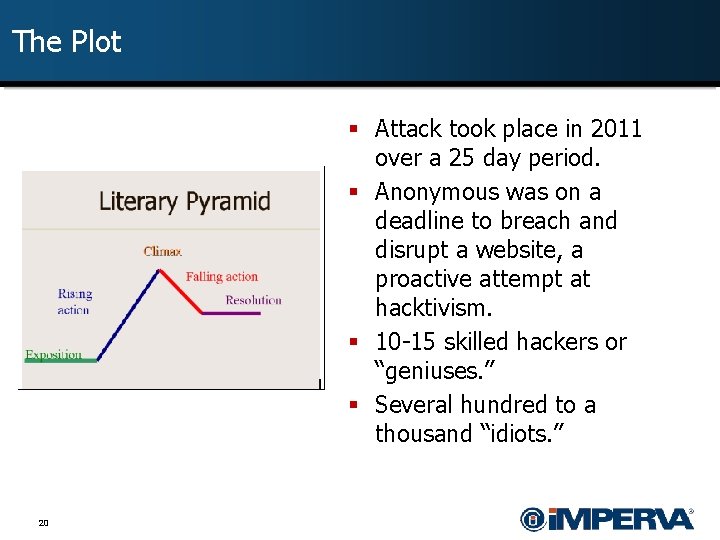
The Plot § Attack took place in 2011 over a 25 day period. § Anonymous was on a deadline to breach and disrupt a website, a proactive attempt at hacktivism. § 10 -15 skilled hackers or “geniuses. ” § Several hundred to a thousand “idiots. ” 20

Recruiting and Communications 21

An “Inspirational” Video 22

Social Media Helps Recruit 23

Setting Up An Early Warning System 24

Example 25

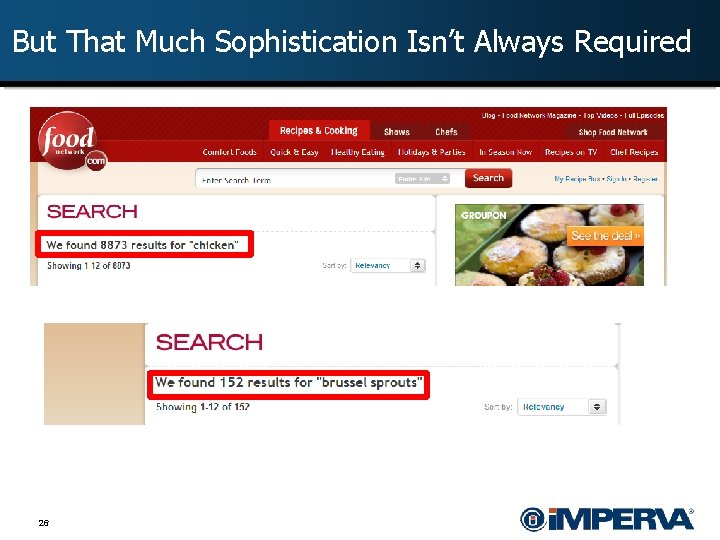
But That Much Sophistication Isn’t Always Required 26

Hacker Tools “Avoid strength, attack weakness: Striking where the enemy is most vulnerable. ” —Sun Tzu 27

Automation is Prevailing § Tools and kits exist for everything

Finding Vulnerabilities § § Tool #1: Vulnerability Scanners Purpose: Rapidly find application vulnerabilities. Cost: $0 -$1000 per license. The specific tools: + Acunetix (named a “Visionary” in a Gartner 2011 MQ) + Nikto (open source) 29

Industrial vs. Social DDOS § Traditional Application DDOS – Traditional application DDOS requires a significant effort on the part of the hacker, buying or building C&C tools, discovering exploits on target systems and expanding a large enough botnet to execute the DDOS. The advantage is that the hacker can attack targets at will without the need to publicly ‘ask’ others for help or meet a specific timeline. But it requires significant effort upfront. § Social DDOS – Supporter run DDOS requires far less effort on the behalf of the attacker, but requires enough supporters ‘willing’ to assist in the attack before it can be executed. The only effort is in creating easy to use DDOS tools and providing them to the ‘supporters’. For more: http: //blog. imperva. com/2011/12/top-cyber-security-trends-for-2012 -7. html 30

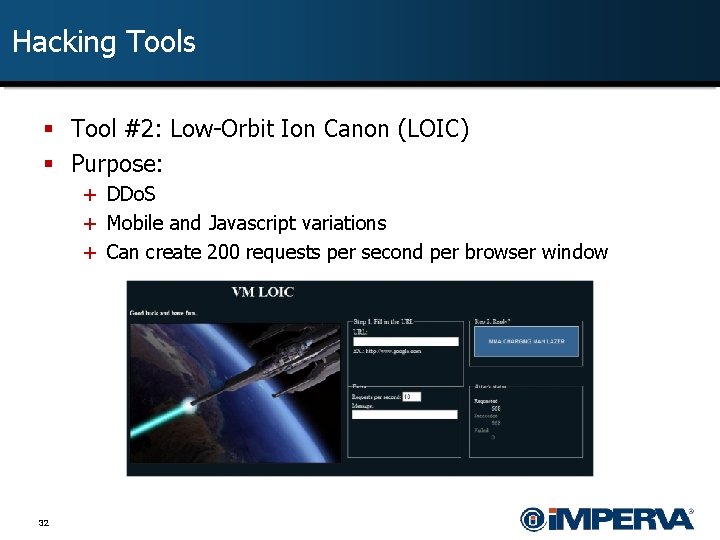
Hacking Tools § Tool #2: Low-Orbit Ion Canon (LOIC) § Purpose: + DDo. S + Mobile and Javascript variations + Can create 200 requests per second per browser window 32

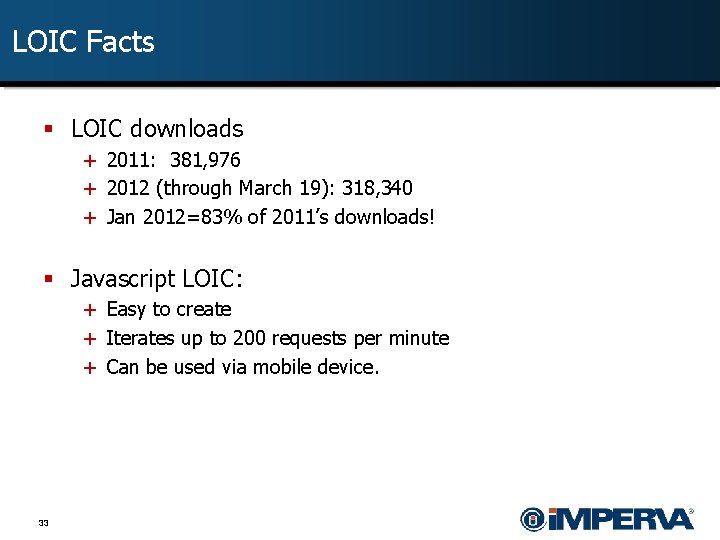
LOIC Facts § LOIC downloads + 2011: 381, 976 + 2012 (through March 19): 318, 340 + Jan 2012=83% of 2011’s downloads! § Javascript LOIC: + Easy to create + Iterates up to 200 requests per minute + Can be used via mobile device. 33

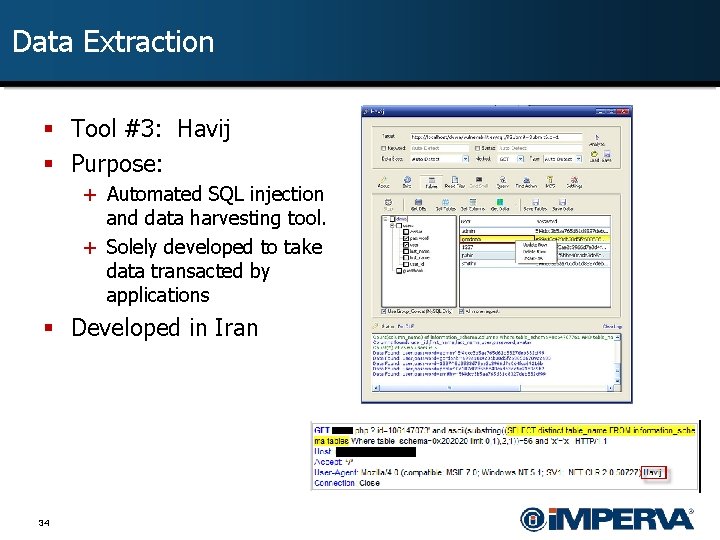
Data Extraction § Tool #3: Havij § Purpose: + Automated SQL injection and data harvesting tool. + Solely developed to take data transacted by applications § Developed in Iran 34

Mitigation Techniques Dork Yourself Blacklist WAF + VA WAF Anti-DDOS IP Reputation Code Fixing

Protect Your Organization’s Data Given all the billions spent on security, why the prolific rate of data breaches? 36

Recent attacker targets…. US Department of Justice Church of Scientology US Copyright Office Muslim Brotherhood FBI Zappos. com MPAA Military. Singles. com Warner Brothers Amazon RIAA Austria Federal Chancellor HADOPI HBGary Federal BMI Mexican Interior Ministry SOHH Mexican Senate Office of the AU Prime Minister Mexican Chamber of Deputies How many of these organizations have AV, IPS and AU House of Parliament Irish Department of Justice AU Department of Communications Irish Department of Finance Next Generations Firewalls? Swiss bank Post. Finance Greek Department of Justice Fine Gael Egyptian National Democratic Party New Zealand Parliament Spanish Police Why are the attacks successful when these technologies claim Tunisia Government Orlando Chamber of Commerce to prevent them? Zimbabwe Government Catholic Diocese of Orlando Egyptian Government Bay Area Rapid Transit Itau Pay. Pal Banco de Brazil Mastercard US Senate Visa Caixa 37

Traditional Security Doesn’t Stop Today’s Threats What helped get us secure… isn’t keeping us secure • • • Router ACLs Network Firewalls IDS and IPS VPNs Anti-Virus • • • SQL Injection (XSS) Cross-site Scripting Remote File Inclusion Cross-site Request Forgery Business Logic Attacks Insider Abuse

I have IPS and NGFW, am I safe? § IPS and NGFWs can’t prevent all web application attacks. + Don’t confuse “application aware marketing” with Web Application Security. § To prevent, WAFs at a minimum must include the following to protect web applications: • • 39 Web-App Profile Web-App Signatures Web-App Protocol Security Web-App DDOS Security Web-App Cookie Protection Anonymous Proxy/TOR IP Security HTTPS (SSL) visibility Security Policy Correlation

I have IPS and NGFW, am I safe? § IPS and NGFWs are not web application firewalls. + Don’t confuse “application aware marketing” with Web Application Security. § However, IPS and NGFWs at best only partially support the items in Red: • • 40 Web-App Profile Web-App Signatures Web-App Protocol Security Web-App DDOS Security Web-App Cookie Protection Anonymous Proxy/TOR IP Security HTTPS (SSL) visibility Security Policy Correlation

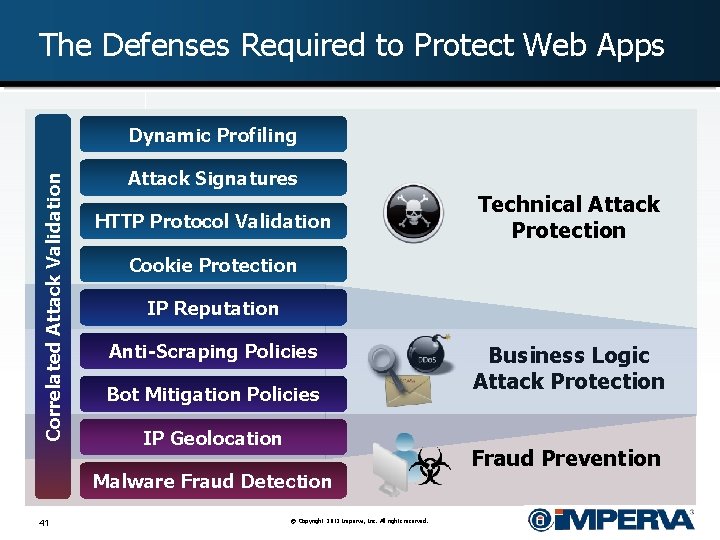
The Defenses Required to Protect Web Apps Correlated Attack Validation Dynamic Profiling Attack Signatures HTTP Protocol Validation Cookie Protection IP Reputation Anti-Scraping Policies Bot Mitigation Policies IP Geolocation Malware Fraud Detection 41 Technical Attack Protection © Copyright 2012 Imperva, Inc. All rights reserved. Business Logic Attack Protection Fraud Prevention

Anonymous Attack Demo § Live Attack D 42 - CONFIDENTIAL -

References • http: //news. netcraft. com/archives/2011/07/08/july-2011 -web-server-survey. html • https: //www. whitehatsec. com/home/resource/stats. html • http: //www. verizonbusiness. com/resources/reports/rp_data-breach-investigationsreport-2011_en_xg. pdf • http: //blog. imperva. com/2011/06/analyzing-the-lulzsec-attacks-. html • http: //www. imperva. com/docs/HI_Search_Engine_Poisoning_SEP. pdf • http: //www. imperva. com/docs/HII_The_Anatomy_of_an_Anonymous_Attack. pdf • http: //www. imperva. com/docs/HII_Remote_and_Local_File_Inclusion_Vulnerabiliti es. pdf
 Lhcca
Lhcca Sauder family
Sauder family Sauder unlimited
Sauder unlimited Active attack and passive attack
Active attack and passive attack Active attack and passive attack
Active attack and passive attack Private security
Private security Ph patti
Ph patti Patti ippoliti
Patti ippoliti Sponge billy bob
Sponge billy bob Susie roundpants
Susie roundpants Il simposio patti
Il simposio patti Dr patti giebink
Dr patti giebink Sc discus login
Sc discus login Clara abbott smart simple
Clara abbott smart simple Patti familiari
Patti familiari Patti hamilton
Patti hamilton Abskessit
Abskessit Computer security attack
Computer security attack Salami attack example
Salami attack example What is the osi security architecture?
What is the osi security architecture? Security guide to network security fundamentals
Security guide to network security fundamentals Wireless security in cryptography
Wireless security in cryptography Visa international security model diagram
Visa international security model diagram Electronic mail security in network security
Electronic mail security in network security Nstissc security model in information security
Nstissc security model in information security Security policy and integrated security in e-commerce
Security policy and integrated security in e-commerce Seven touchpoints for software security
Seven touchpoints for software security Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
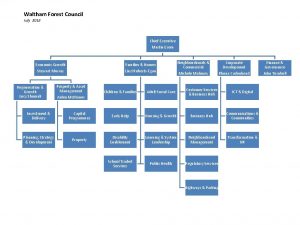
Security guide to network security fundamentals Waltham forest senior management structure
Waltham forest senior management structure Senior design ucf
Senior design ucf Concept of personality
Concept of personality Martha senior year
Martha senior year Simone sheehan
Simone sheehan Senior youth leadership portfolio
Senior youth leadership portfolio Westchester senior services
Westchester senior services Senior project template
Senior project template Senior project outline
Senior project outline Ashlynn campbell
Ashlynn campbell Senior geography project
Senior geography project Senior will example
Senior will example Senior class mottos
Senior class mottos Scarborough senior high school
Scarborough senior high school