Wireless EE 122 Intro to Communication Networks Fall



























- Slides: 85

Wireless EE 122: Intro to Communication Networks Fall 2010 (MW 4 -5: 30 in 101 Barker) Scott Shenker TAs: Sameer Agarwal, Sara Alspaugh, Igor Ganichev, Prayag Narula http: //inst. eecs. berkeley. edu/~ee 122/ Materials with thanks to Jennifer Rexford, Ion Stoica, Vern Paxson and other colleagues at Princeton and UC Berkeley

Review of Last Lecture • Peer-to-peer: – Design paradigm: No central contol – Economic model: leverage user nodes • As an economic model: – Latest step in war over control – Grassroots way to build large-scale system – But need good coordination mechanism 2

P 2 P Tasks • Search: general keyword/wildcard search – Controlled flooding • Lookup: given name, get IP address of location – DHT or similar structure • Download: – Chunking is used because of asymmetric bandwidth – Self-scaling depends on an incentive mechanism o Prevent free-riders 3

Wireless Networks 4

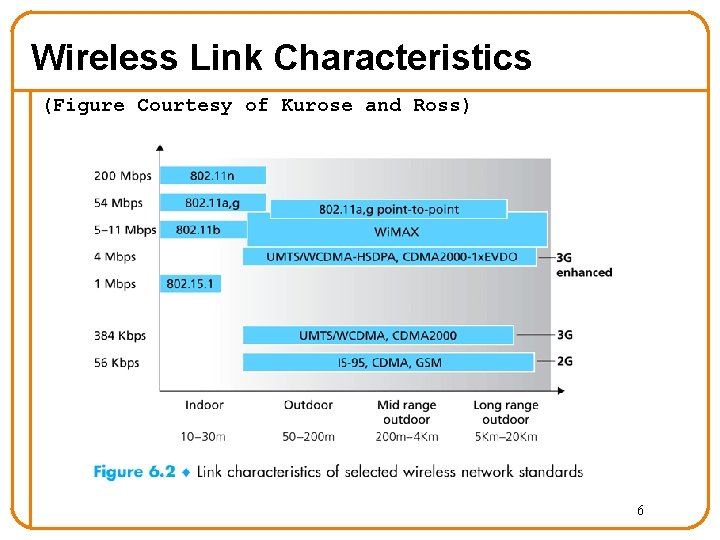
Wireless Communication Standards • Cellular – 2 G: GSM (Global System for Mobile communication), CDMA (Code Division Multiple Access) – 3 G: CDMA 2000 • IEEE 802. 11 – A: 5. 0 Ghz band, 54 Mbps (25 Mbps operating rate) – B: 2. 4 Ghz band, 11 Mbps (4. 5 Mbps operating rate) – G: 2. 4 Ghz, 54 Mbps (19 Mbps operating rate) – N: 2. 4/5 Ghz, 150 Mbps • IEEE 802. 15 – lower power wireless – 802. 15. 1: 2. 4 Ghz, 2. 1 Mbps (Bluetooth) – 802. 15. 4: 2. 4 Ghz, 250 Kbps (Sensor Networks) 5

Wireless Link Characteristics (Figure Courtesy of Kurose and Ross) 6

What Makes Wireless Different? • Signals sent by sender don’t always end up at receiver intact – Complicated physics involved, which we won’t discuss – But what can go wrong? • Two quantities we care about: – Signal-to-noise ratio (SNR) o Signal Power/Noise Power – Bit-Error Rate (BER) 7

Path Loss • Signal power attenuates by about ~r 2 factor for omni-directional antennas in free space – r is the distance between the sender and the receiver • The exponent depends on placement of antennas • Less than 2 for directional antennas • Greater than 2 when antennas are placed on the ground – Signal bounces off the ground and reduces the power of the signal 8

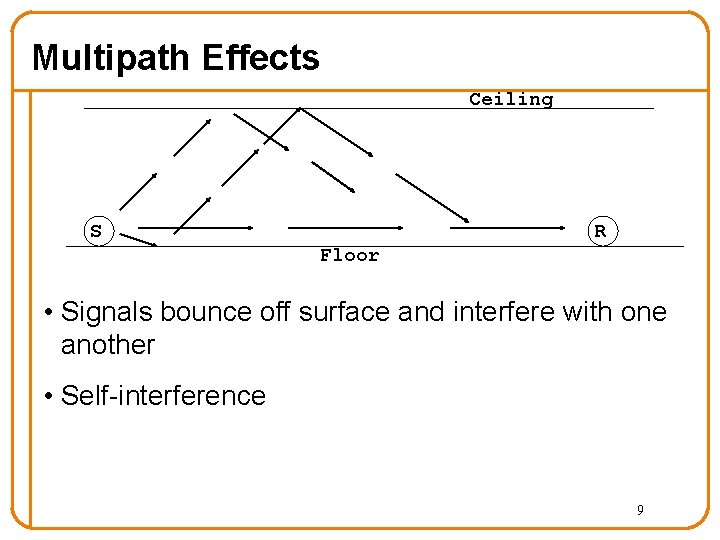
Multipath Effects Ceiling S R Floor • Signals bounce off surface and interfere with one another • Self-interference 9

Interference from Other Sources • External Interference – Microwave is turned on and blocks your signal • Internal Interference – Hosts within range of each other collide with one another’s transmission (remember Aloha) • We have to tolerate path loss, multipath, etc. , but we can try to avoid internal interference • This is what makes 802. 11 interesting…. 10

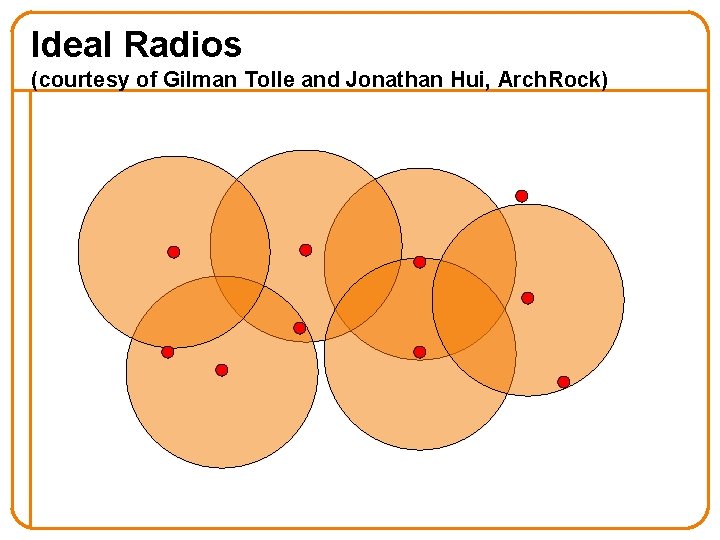
Ideal Radios (courtesy of Gilman Tolle and Jonathan Hui, Arch. Rock)

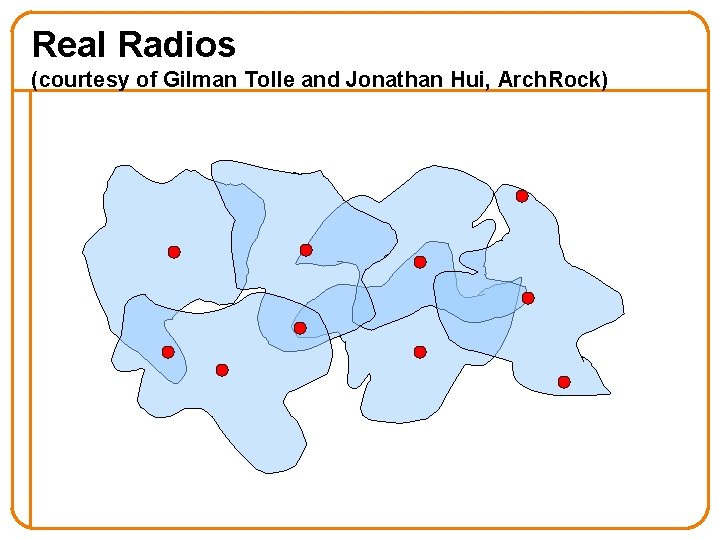
Real Radios (courtesy of Gilman Tolle and Jonathan Hui, Arch. Rock)

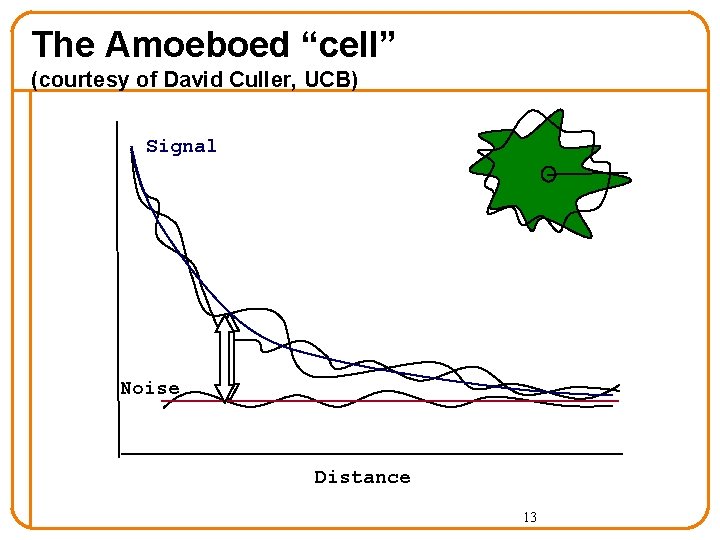
The Amoeboed “cell” (courtesy of David Culler, UCB) Signal Noise Distance 13

Wireless Bit Errors • The lower the SNR (Signal/Noise) the higher the Bit Error Rate (BER) • We could make the signal stronger… • Why is this not always a good idea? – Increased signal strength requires more power – Increases the interference range of the sender, so you interfere with more nodes around you o And then they increase their power……. • Error Correction schemes can correct some problems 14

802. 11 15

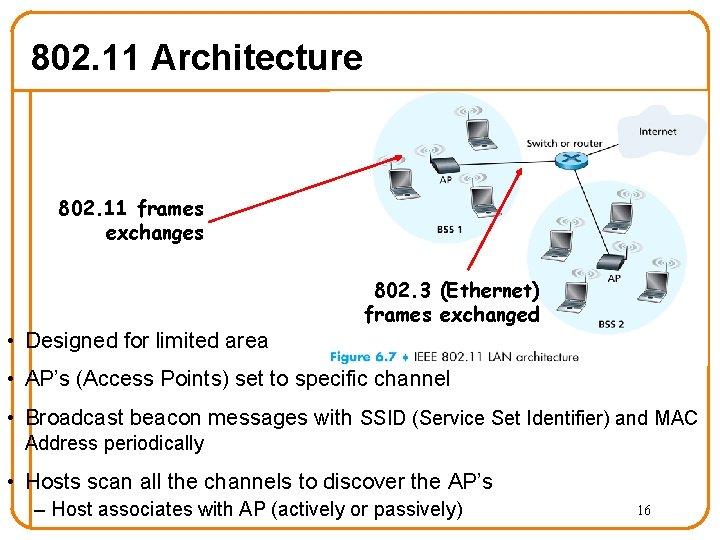
802. 11 Architecture 802. 11 frames exchanges 802. 3 (Ethernet) frames exchanged • Designed for limited area • AP’s (Access Points) set to specific channel • Broadcast beacon messages with SSID (Service Set Identifier) and MAC Address periodically • Hosts scan all the channels to discover the AP’s – Host associates with AP (actively or passively) 16

Wireless Multiple Access Technique? • Carrier Sense? – Sender can listen before sending – What does that tell the sender? • Collision Detection? – Where do collisions occur? – How can you detect them? 17

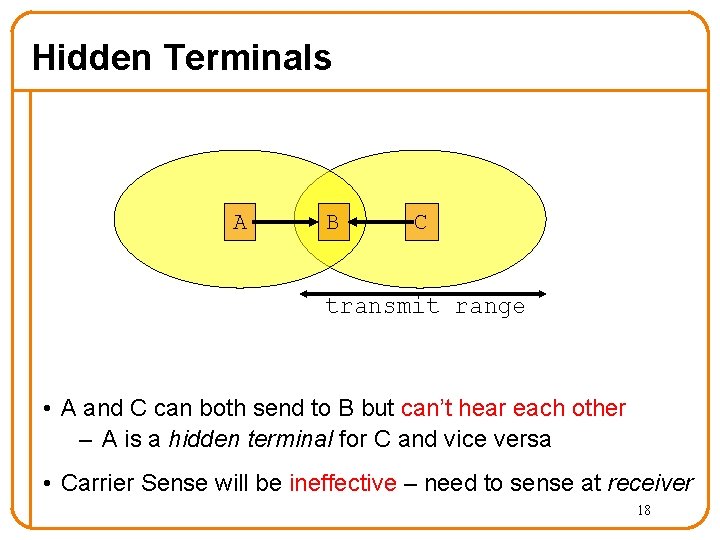
Hidden Terminals A B C transmit range • A and C can both send to B but can’t hear each other – A is a hidden terminal for C and vice versa • Carrier Sense will be ineffective – need to sense at receiver 18

Exposed Terminals A B C D • Exposed node: B sends a packet to A; C hears this and decides not to send a packet to D (despite the fact that this will not cause interference)! • Carrier sense would prevent a successful transmission – But we do carrier sense anway (why? ) 19

Key Points • No concept of a global collision – Different receivers hear different signals – Different senders reach different receivers • Collisions are at receiver, not sender – Only care if receiver can hear the sender clearly – It does not matter if sender can hear someone else – As long as that signal does not interfere with receiver • Goal of protocol: – Detect if receiver can hear sender – Tell senders who might interfere with receiver to shut 20 up

Basic Collision Avoidance • Since can’t detect collisions, we try to avoid them • Carrier sense: – When medium busy, choose random interval – Wait that many idle timeslots to pass before sending • When a collision is inferred, retransmit with binary exponential backoff (like Ethernet) – Use ACK from receiver to infer “no collision” – Use exponential backoff to adapt contention window • How would we get ACKs if we didn’t do carrier sense? 21

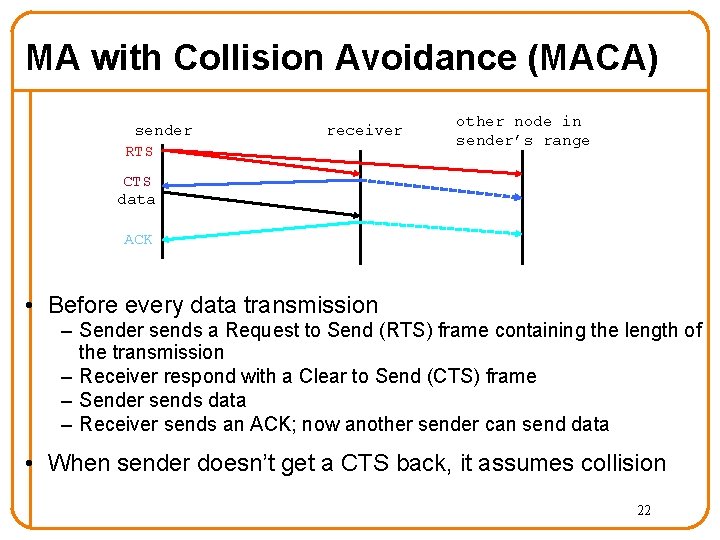
MA with Collision Avoidance (MACA) sender RTS receiver other node in sender’s range CTS data ACK • Before every data transmission – Sender sends a Request to Send (RTS) frame containing the length of the transmission – Receiver respond with a Clear to Send (CTS) frame – Sender sends data – Receiver sends an ACK; now another sender can send data • When sender doesn’t get a CTS back, it assumes collision 22

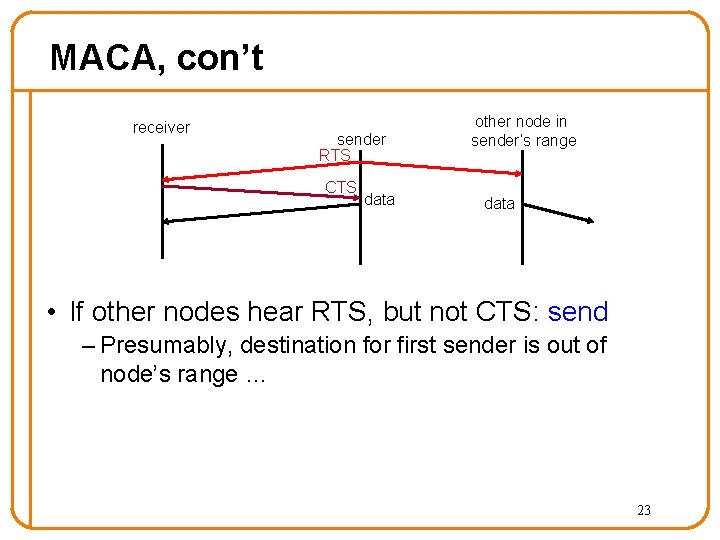
MACA, con’t receiver sender RTS CTS data other node in sender’s range data • If other nodes hear RTS, but not CTS: send – Presumably, destination for first sender is out of node’s range … 23

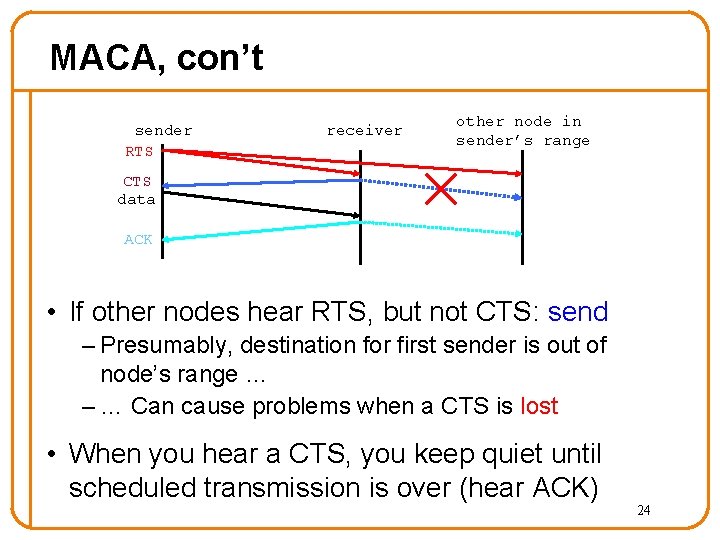
MACA, con’t sender RTS receiver other node in sender’s range CTS data ACK • If other nodes hear RTS, but not CTS: send – Presumably, destination for first sender is out of node’s range … – … Can cause problems when a CTS is lost • When you hear a CTS, you keep quiet until scheduled transmission is over (hear ACK) 24

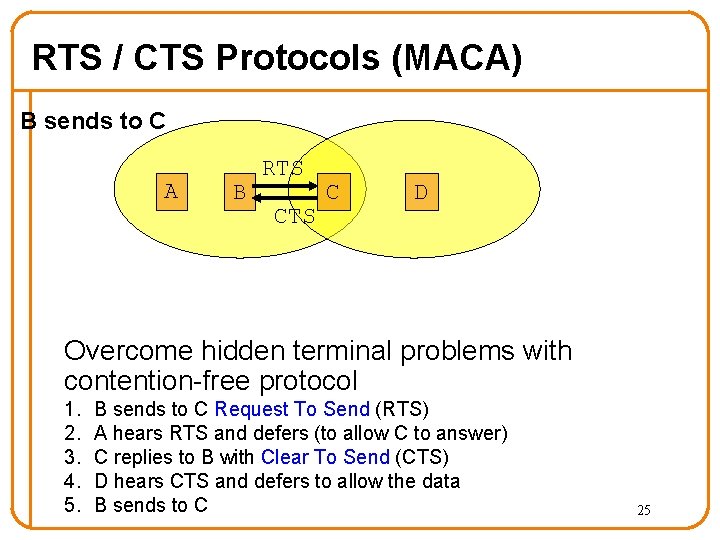
RTS / CTS Protocols (MACA) B sends to C A B RTS C D Overcome hidden terminal problems with contention-free protocol 1. 2. 3. 4. 5. B sends to C Request To Send (RTS) A hears RTS and defers (to allow C to answer) C replies to B with Clear To Send (CTS) D hears CTS and defers to allow the data B sends to C 25

5 Minute Break Questions Before We Proceed? 26

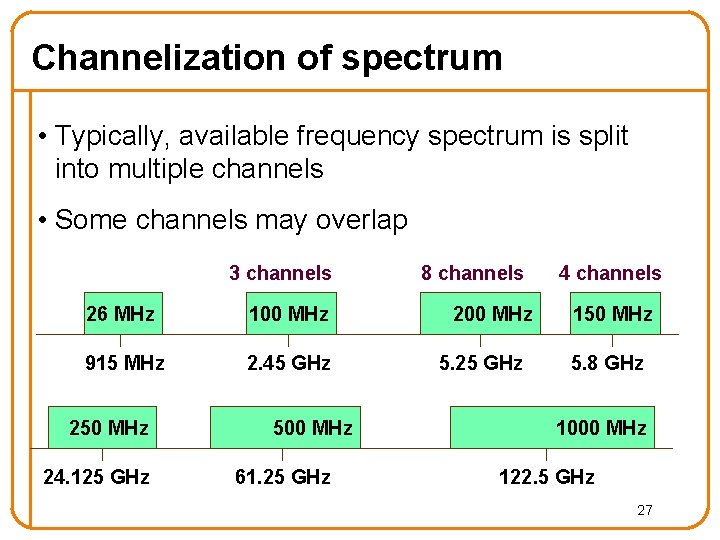
Channelization of spectrum • Typically, available frequency spectrum is split into multiple channels • Some channels may overlap 3 channels 26 MHz 100 MHz 915 MHz 2. 45 GHz 250 MHz 24. 125 GHz 500 MHz 61. 25 GHz 8 channels 200 MHz 5. 25 GHz 4 channels 150 MHz 5. 8 GHz 1000 MHz 122. 5 GHz 27

Preventing Collisions Altogether • Frequency Spectrum partitioned into several channels – Nodes within interference range can use separate channels A B D C – Now A and C can send without any interference! – Aggregate Network throughput doubles 28

Using Multiple Channels • 802. 11: AP’s on different channels – Usually manually configured by administrator – Automatic Configuration may cause problems • Most cards have only 1 transceiver – Not Full Duplex: Cannot send and receive at the same time • Multichannel MAC Protocols – Automatically have nodes negotiate channels o Channel coordination amongst nodes is necessary o Introduces negotiation and channel-switching latency that reduce throughput 29

Wireless Multihop Networks • Vehicular Networks – Delay Tolerant (batch) sending over several hops carry data to a base station • Common in Sensor Network for periodically transmitting data – Infrastructure Monitoring o E. g. , structural health monitoring of the Golden Gate Bridge • Multihop networking for Internet connection sharing – Routing traffic over several hops to base station connected to Internet – E. g. , Meraki Networks 30

Large Multihop Network (courtesy of Sanjit Biswas, MIT) 1 kilometer

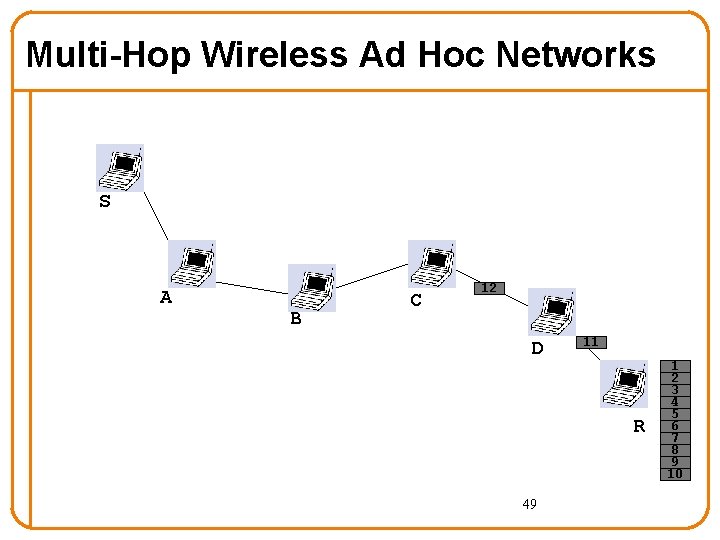
Multi-Hop Wireless Ad Hoc Networks (Courtesy of Tianbo Kuang and Carey Williamson University of Calgary) S A B C D R

Multi-Hop Wireless Ad Hoc Networks S A B C D R 33

Multi-Hop Wireless Ad Hoc Networks (Assume ideal world…) 1 2 3 4 5 6 7 8 9 10 11 12 S A B C D R 34

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S 1 A B C D R 35

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S 2 1 A B C D R 36

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 3 1 2 A B C D R 37

Multi-Hop Wireless Ad Hoc Networks 5 6 7 8 9 10 11 12 S 4 2 3 A B 1 C D R 38

Multi-Hop Wireless Ad Hoc Networks 6 7 8 9 10 11 12 S 5 A 3 4 B C 2 D 1 R 39

Multi-Hop Wireless Ad Hoc Networks S 7 8 9 10 11 12 6 A 4 5 B 3 C D 2 1 R 40

Multi-Hop Wireless Ad Hoc Networks S 8 9 10 11 12 7 A 5 6 B C 4 D 3 1 2 R 41

Multi-Hop Wireless Ad Hoc Networks S 9 10 11 12 8 A 6 7 B C 5 D 4 1 2 3 R 42

Multi-Hop Wireless Ad Hoc Networks S 10 11 12 9 7 A 8 B C 6 D 5 1 2 3 4 R 43

Multi-Hop Wireless Ad Hoc Networks S 11 12 10 A 8 9 B C 7 D 6 R 44 1 2 3 4 5

Multi-Hop Wireless Ad Hoc Networks S 12 11 A 9 10 B 8 C D 7 R 45 1 2 3 4 5 6

Multi-Hop Wireless Ad Hoc Networks S 12 A 10 11 B C 9 D 8 R 46 1 2 3 4 5 6 7

Multi-Hop Wireless Ad Hoc Networks S A 11 12 B 10 C D 9 R 47 1 2 3 4 5 6 7 8

Multi-Hop Wireless Ad Hoc Networks S 12 A B C 11 D 10 R 48 1 2 3 4 5 6 7 8 9

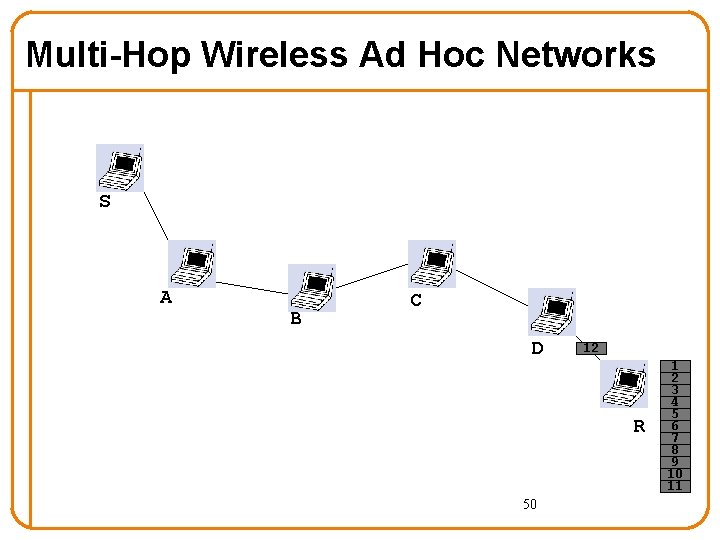
Multi-Hop Wireless Ad Hoc Networks S A B C 12 D 11 R 49 1 2 3 4 5 6 7 8 9 10

Multi-Hop Wireless Ad Hoc Networks S A B C D 12 R 50 1 2 3 4 5 6 7 8 9 10 11

Multi-Hop Wireless Ad Hoc Networks S A B C D R 51 1 2 3 4 5 6 7 8 9 10 11 12

What Do YOU Think Really Happens? 52

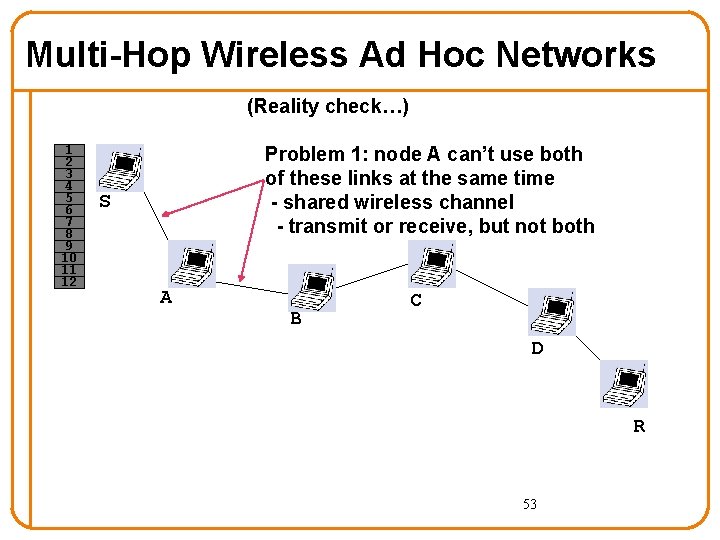
Multi-Hop Wireless Ad Hoc Networks (Reality check…) 1 2 3 4 5 6 7 8 9 10 11 12 Problem 1: node A can’t use both of these links at the same time - shared wireless channel - transmit or receive, but not both S A B C D R 53

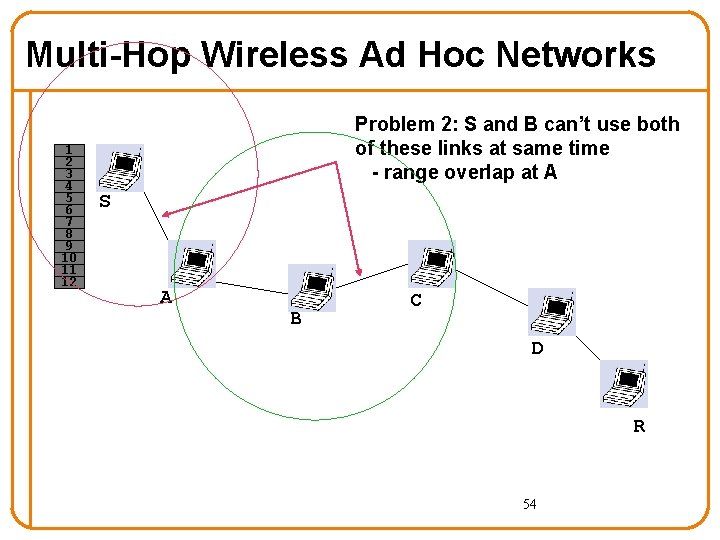
Multi-Hop Wireless Ad Hoc Networks 1 2 3 4 5 6 7 8 9 10 11 12 Problem 2: S and B can’t use both of these links at same time - range overlap at A S A B C D R 54

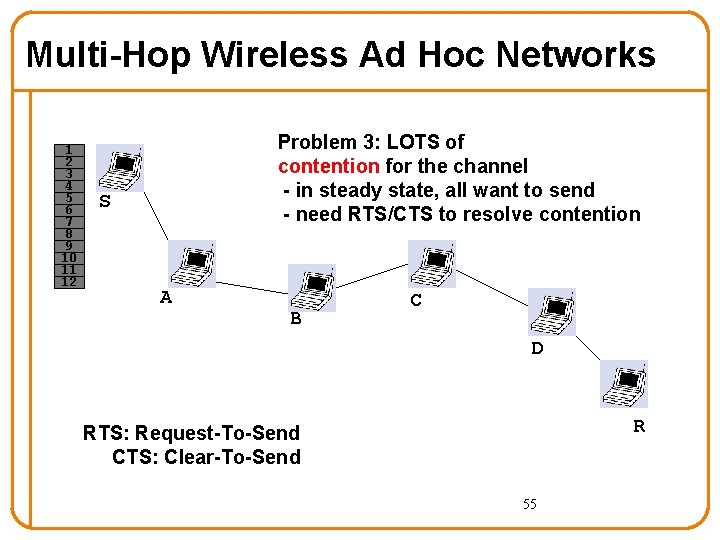
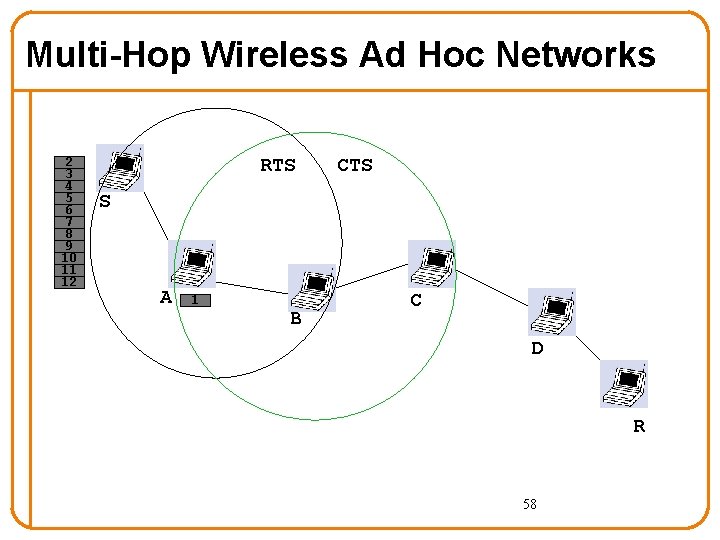
Multi-Hop Wireless Ad Hoc Networks 1 2 3 4 5 6 7 8 9 10 11 12 Problem 3: LOTS of contention for the channel - in steady state, all want to send - need RTS/CTS to resolve contention S A B C D R RTS: Request-To-Send CTS: Clear-To-Send 55

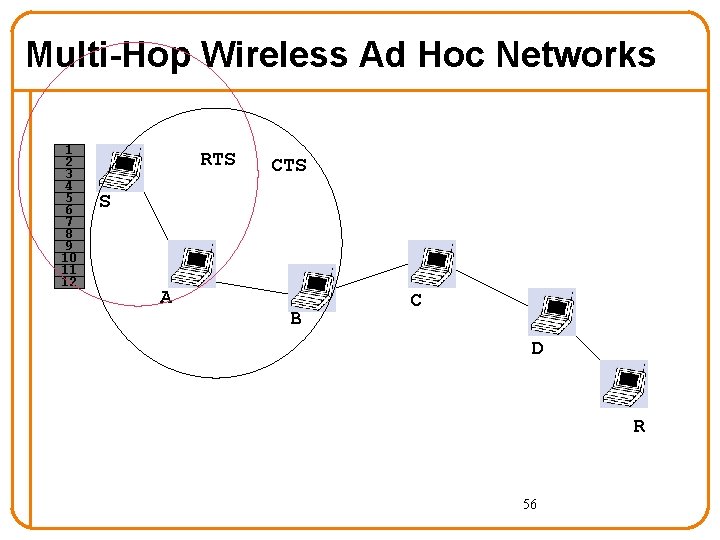
Multi-Hop Wireless Ad Hoc Networks 1 2 3 4 5 6 7 8 9 10 11 12 RTS CTS S A B C D R 56

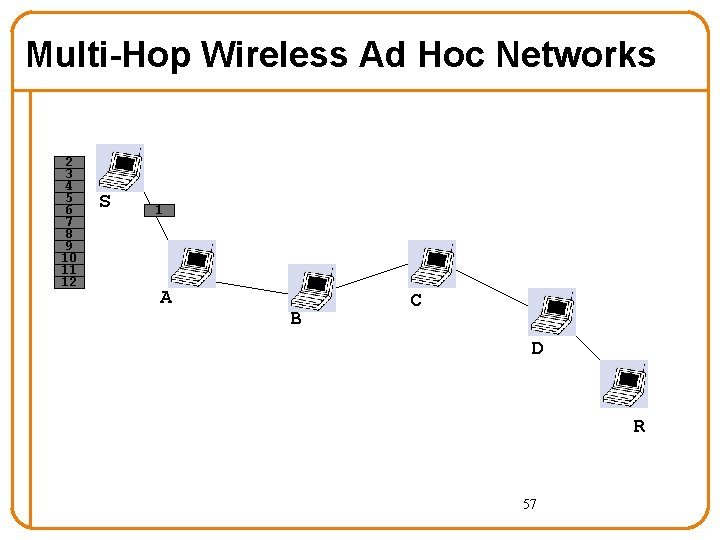
Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S 1 A B C D R 57

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 RTS CTS S A 1 B C D R 58

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S A 1 B C D R 59

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S 1 A B C D R 60

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S 2 A B C 1 D R 61

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S A 2 B C D 1 R 62

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S 2 A B C D 1 R 63

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 3 A B C 2 D 1 R 64

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S A 3 B C D 2 1 R 65

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 3 A B C D 1 2 R 66

Multi-Hop Wireless Ad Hoc Networks 5 6 7 8 9 10 11 12 S 4 A B C 3 D 1 2 R 67

Multi-Hop Wireless Ad Hoc Networks 5 6 7 8 9 10 11 12 S A 4 B C D 3 1 2 R 68

Multi-Hop Wireless Ad Hoc Networks 5 6 7 8 9 10 11 12 S 4 A B C D 1 2 3 R 69

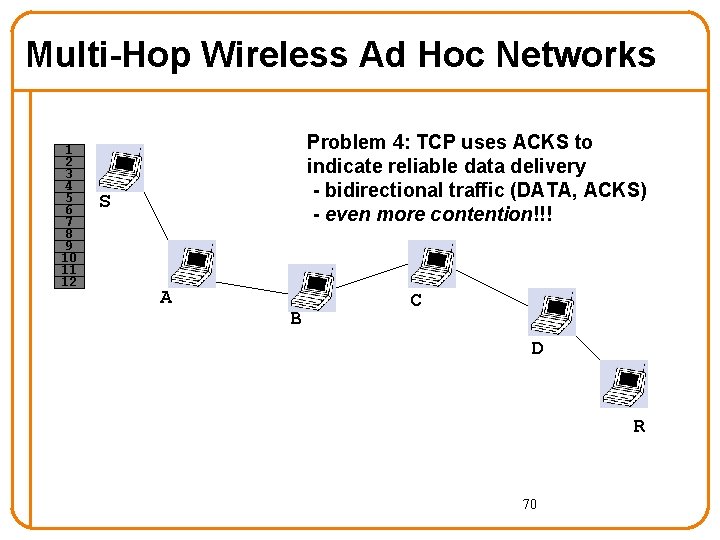
Multi-Hop Wireless Ad Hoc Networks 1 2 3 4 5 6 7 8 9 10 11 12 Problem 4: TCP uses ACKS to indicate reliable data delivery - bidirectional traffic (DATA, ACKS) - even more contention!!! S A B C D R 70

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S 1 A B C D R 71

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S A 1 B C D R 72

Multi-Hop Wireless Ad Hoc Networks 2 3 4 5 6 7 8 9 10 11 12 S 1 A B C D R 73

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S 2 A B C 1 D R 74

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S A 2 B C D 1 R 75

Multi-Hop Wireless Ad Hoc Networks 3 4 5 6 7 8 9 10 11 12 S 2 1 2 A B 2 C D 1 1 1 R 76

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 3 A B C 1 2 D 1 R 77

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 1 A 3 B C D 2 1 R 78

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S A 3 B C 1 D 2 1 R 79

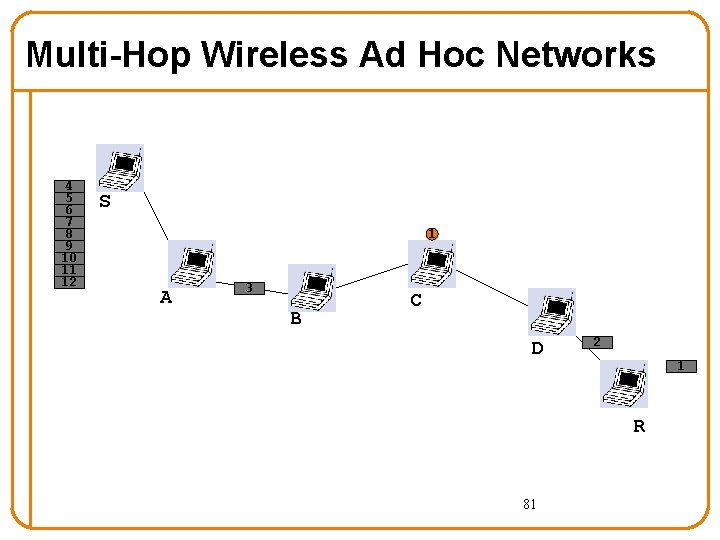
Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 1 A 3 B C D 2 1 R 80

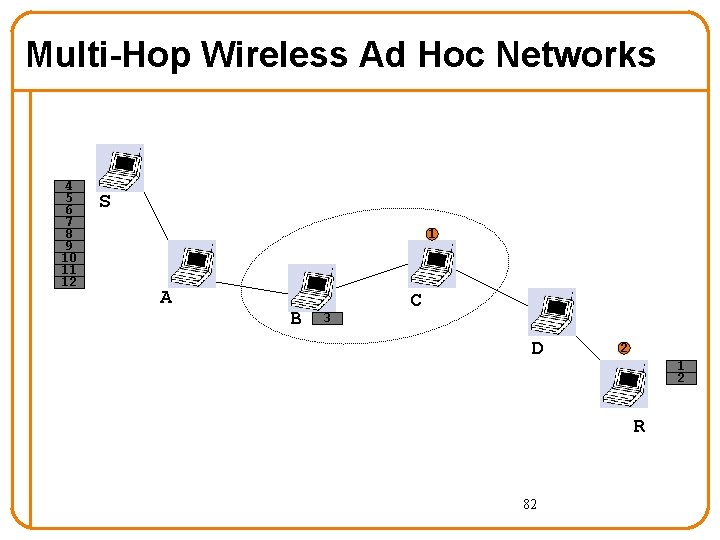
Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 1 A 3 B C D 2 1 R 81

Multi-Hop Wireless Ad Hoc Networks 4 5 6 7 8 9 10 11 12 S 1 A B 3 C D 2 1 2 R 82

Lesson • Multihop wireless is hard to make efficient 83

Summary • Wireless is a tricky beast – Distributed multiple access problem – Hidden terminals – Exposed terminals – Current protocols sufficient, given overprovisioning • Multihop even more complicated 84

Rest of Course • Next lecture: Security • After that: Future of Networking – Why things will look completely different in ten years • Review 85