IP Addressing EE 122 Intro to Communication Networks







![Next Design: Classful Addressing – Class A: if first byte in [0. . 127], Next Design: Classful Addressing – Class A: if first byte in [0. . 127],](https://slidetodoc.com/presentation_image/5edb2c26654a382be870b128345389eb/image-20.jpg)
![Classful Addressing (cont’d) – Class D: [224. . 239] (top bits 1110) 1110******** o Classful Addressing (cont’d) – Class D: [224. . 239] (top bits 1110) 1110******** o](https://slidetodoc.com/presentation_image/5edb2c26654a382be870b128345389eb/image-21.jpg)






- Slides: 58

IP Addressing EE 122: Intro to Communication Networks Fall 2010 (MW 4 -5: 30 in 101 Barker) Scott Shenker TAs: Sameer Agarwal, Sara Alspaugh, Igor Ganichev, Prayag Narula http: //inst. eecs. berkeley. edu/~ee 122/ Materials with thanks to Jennifer Rexford, Ion Stoica, Vern Paxson and other colleagues at Princeton and UC Berkeley 1

Goals of Today’s Lecture • IP addressing • Address allocation • Brief security analysis of IP’s header design – Leftover from last lecture, will cover if have time 2

IP Addressing 3

Designing IP’s Addresses • Question #1: what should an address be associated with? – E. g. , a telephone number is associated not with a person but with a handset • Question #2: what structure should addresses have? What are the implications of different types of structure? • Question #3: who determines the particular addresses used in the global Internet? What are the implications of how this is done? 4

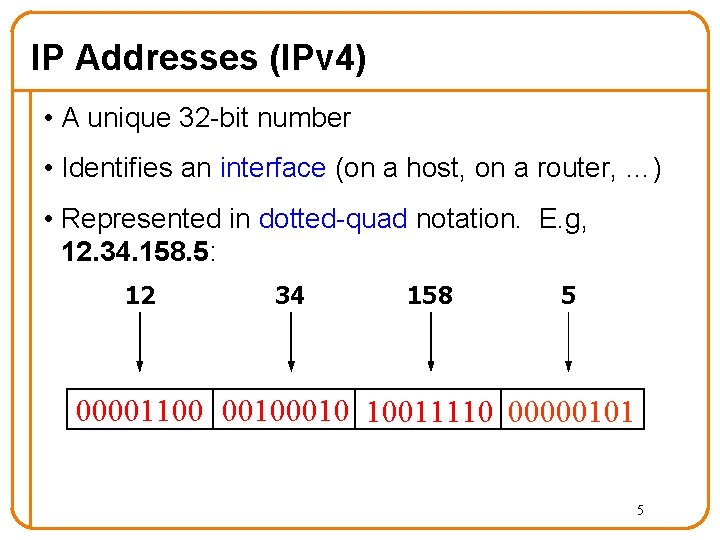
IP Addresses (IPv 4) • A unique 32 -bit number • Identifies an interface (on a host, on a router, …) • Represented in dotted-quad notation. E. g, 12. 34. 158. 5: 12 34 158 5 00001100 0010 10011110 00000101 5

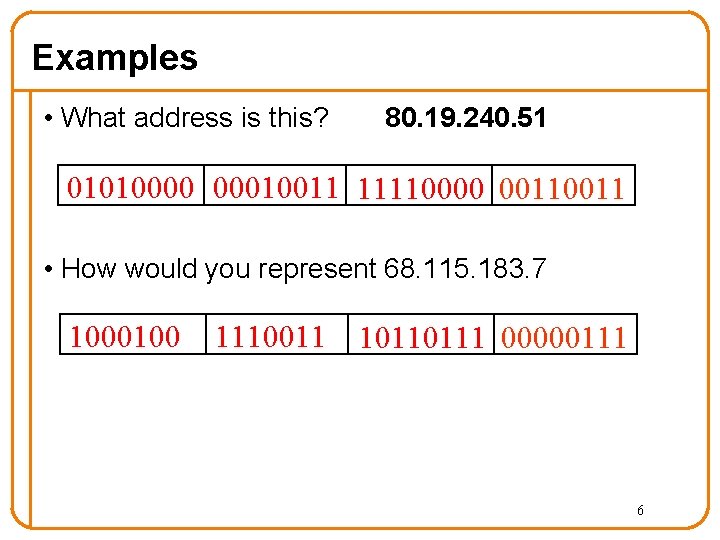
Examples • What address is this? 80. 19. 240. 51 01010000 00010011 11110000 0011 • How would you represent 68. 115. 183. 7 1000100 1110011 10110111 00000111 6

What Are Addresses Used For? • Network uses addresses to figure out where to forward packets • Routers are the network devices that forward packets based on IP addresses • What do “switches” do? – Route on Layer-2 addresses (e. g. , MAC addresses) 7

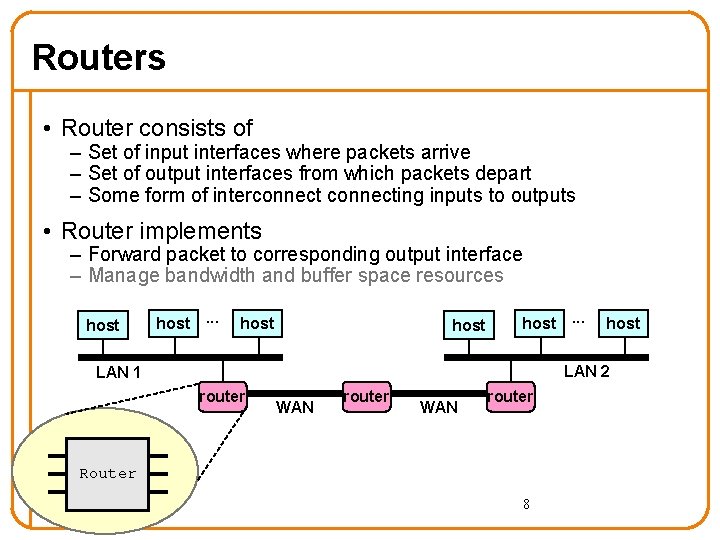
Routers • Router consists of – Set of input interfaces where packets arrive – Set of output interfaces from which packets depart – Some form of interconnecting inputs to outputs • Router implements – Forward packet to corresponding output interface – Manage bandwidth and buffer space resources host. . . host LAN 2 LAN 1 router WAN router Router 8

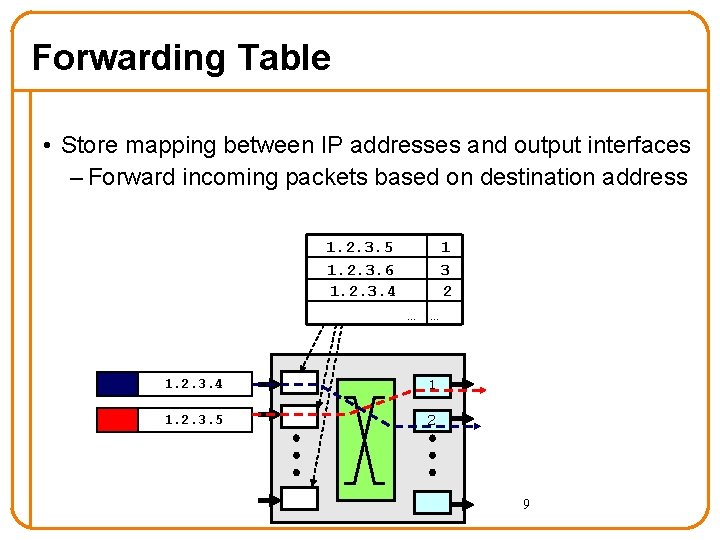
Forwarding Table • Store mapping between IP addresses and output interfaces – Forward incoming packets based on destination address 1. 2. 3. 5 1. 2. 3. 6 1. 2. 3. 4 1 3 2 … … 1. 2. 3. 4 1 1. 2. 3. 5 2 9

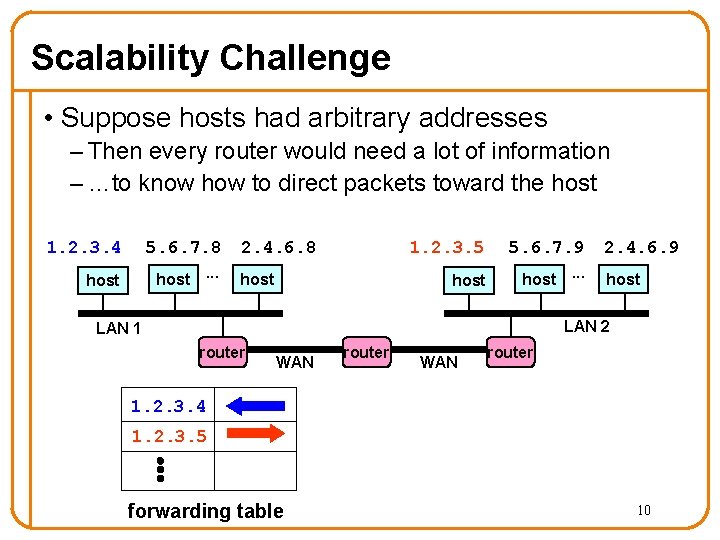
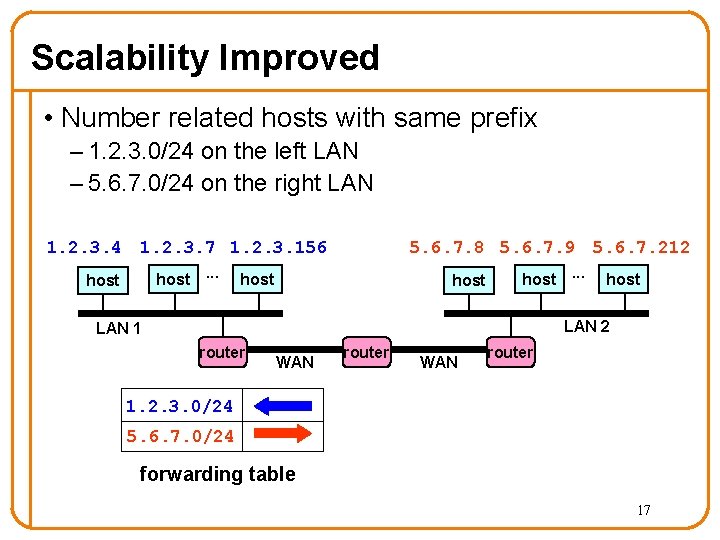
Scalability Challenge • Suppose hosts had arbitrary addresses – Then every router would need a lot of information – …to know how to direct packets toward the host 1. 2. 3. 4 5. 6. 7. 8 host. . . 2. 4. 6. 8 host 1. 2. 3. 5 5. 6. 7. 9 host. . . 2. 4. 6. 9 host LAN 2 LAN 1 router WAN router 1. 2. 3. 4 1. 2. 3. 5 forwarding table 10

Two Universal Tricks in CS • When you need more flexibility, you add… – A layer of indirection • When you need more scalability, you impose… – A hierarchical structure 11

Hierarchical Addressing in U. S. Mail • Addressing in the U. S. mail – Zip code: 94704 – Street: Center Street – Building on street: 1947 – Location in building: Suite 600 – Name of occupant: Scott Shenker ? ? ? • Forwarding the U. S. mail – Deliver letter to the post office in the zip code – Assign letter to mailman covering the street – Drop letter into mailbox for the building/room – Give letter to the appropriate person 12

Who Knows What? • Does anyone in the US Mail system know where every house is? • Separate routing tables at each level of hierarchy – Each of manageable scale 13

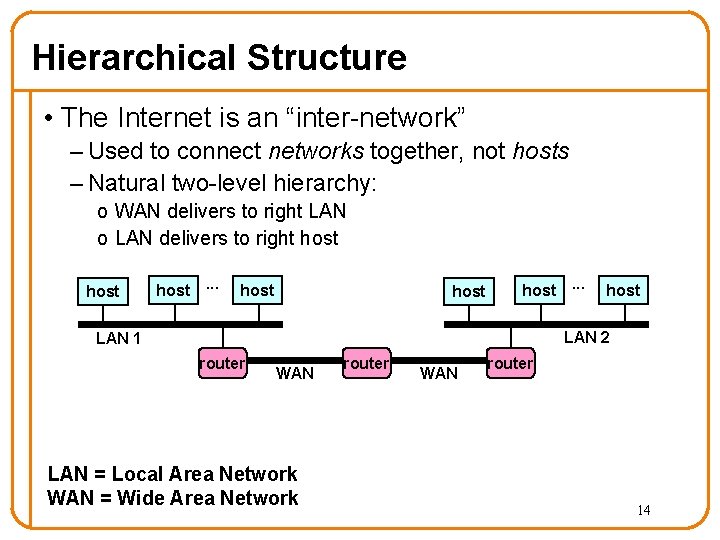
Hierarchical Structure • The Internet is an “inter-network” – Used to connect networks together, not hosts – Natural two-level hierarchy: o WAN delivers to right LAN o LAN delivers to right host. . . host LAN 2 LAN 1 router WAN LAN = Local Area Network WAN = Wide Area Network router WAN router 14

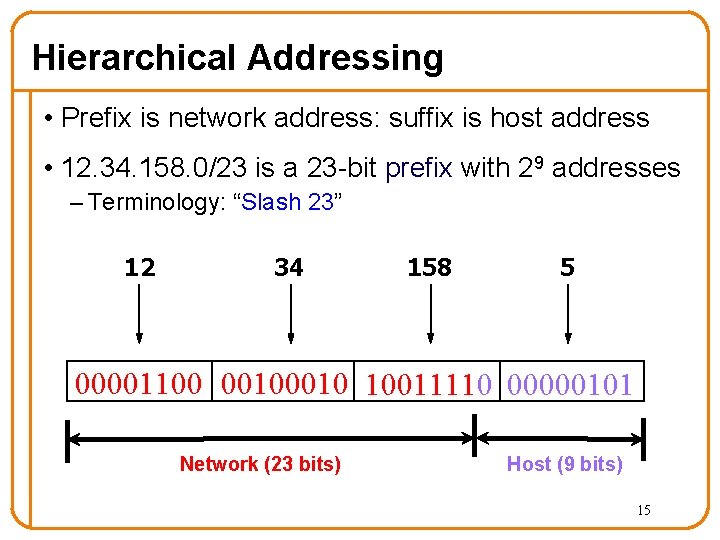
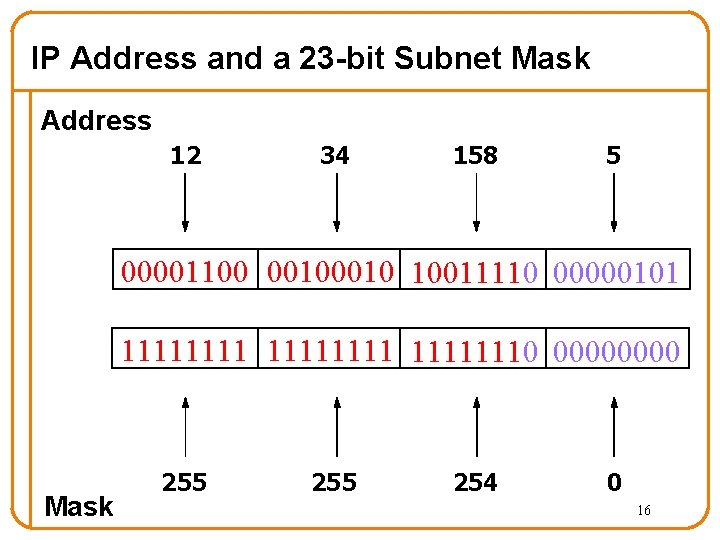
Hierarchical Addressing • Prefix is network address: suffix is host address • 12. 34. 158. 0/23 is a 23 -bit prefix with 29 addresses – Terminology: “Slash 23” 12 34 158 5 00001100 0010 10011110 00000101 Network (23 bits) Host (9 bits) 15

IP Address and a 23 -bit Subnet Mask Address 12 34 158 5 00001100 0010 10011110 00000101 111111110 0000 Mask 255 254 0 16

Scalability Improved • Number related hosts with same prefix – 1. 2. 3. 0/24 on the left LAN – 5. 6. 7. 0/24 on the right LAN 1. 2. 3. 4 1. 2. 3. 7 1. 2. 3. 156 host. . . host 5. 6. 7. 8 5. 6. 7. 9 5. 6. 7. 212 host. . . host LAN 2 LAN 1 router WAN router 1. 2. 3. 0/24 5. 6. 7. 0/24 forwarding table 17

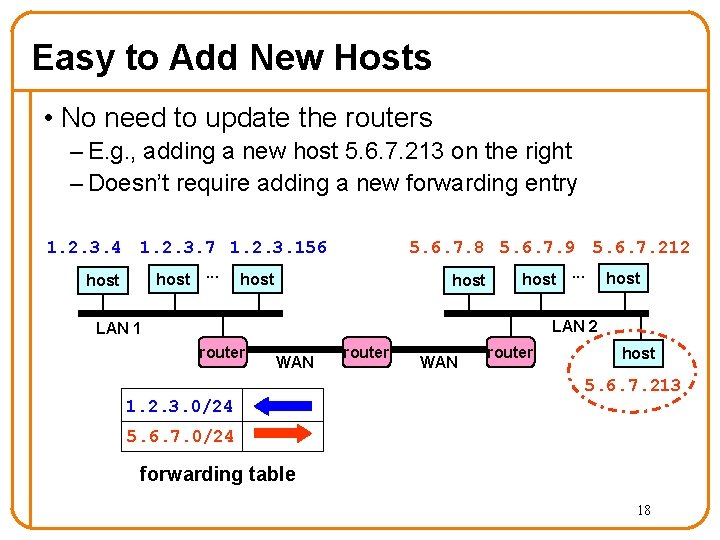
Easy to Add New Hosts • No need to update the routers – E. g. , adding a new host 5. 6. 7. 213 on the right – Doesn’t require adding a new forwarding entry 1. 2. 3. 4 1. 2. 3. 7 1. 2. 3. 156 host. . . host 5. 6. 7. 8 5. 6. 7. 9 5. 6. 7. 212 host. . . host LAN 2 LAN 1 router WAN router host 5. 6. 7. 213 1. 2. 3. 0/24 5. 6. 7. 0/24 forwarding table 18

Original Internet Addresses • First eight bits: network address (/8) • Last 24 bits: host address Assumed 256 networks were more than enough! 19
![Next Design Classful Addressing Class A if first byte in 0 127 Next Design: Classful Addressing – Class A: if first byte in [0. . 127],](https://slidetodoc.com/presentation_image/5edb2c26654a382be870b128345389eb/image-20.jpg)
Next Design: Classful Addressing – Class A: if first byte in [0. . 127], assume /8 (top bit = 0) 0******** **** o Very large blocks (e. g. , MIT has 18. 0. 0. 0/8) – Class B: first byte in [128. . 191] assume /16 (top bits = 10) 10******** **** o Large blocks (e. g, . UCB has* 128. 32. 0. 0/16) – Class C: [192. . 223] assume /24 (top bits = 110) 110******** **** o Small blocks (e. g. , ICIR has 192. 150. 187. 0/24) o (My house has a /25) 20
![Classful Addressing contd Class D 224 239 top bits 1110 1110 o Classful Addressing (cont’d) – Class D: [224. . 239] (top bits 1110) 1110******** o](https://slidetodoc.com/presentation_image/5edb2c26654a382be870b128345389eb/image-21.jpg)
Classful Addressing (cont’d) – Class D: [224. . 239] (top bits 1110) 1110******** o Multicast groups – Class E: [240. . 255] (top bits 11110) 11110*** ******** o Reserved for future use • What problems can classful addressing lead to? – Only comes in 3 sizes – Routers can end up knowing about many class C’s 21

Today’s Addressing: CIDR • CIDR = Classless Interdomain Routing • Flexible boundary between network and host addresses • Must specify both address and mask, to clarify where the network address ends and the host address begins – Classful addressing communicate this with first few bits – CIDR requires explicit mask 22

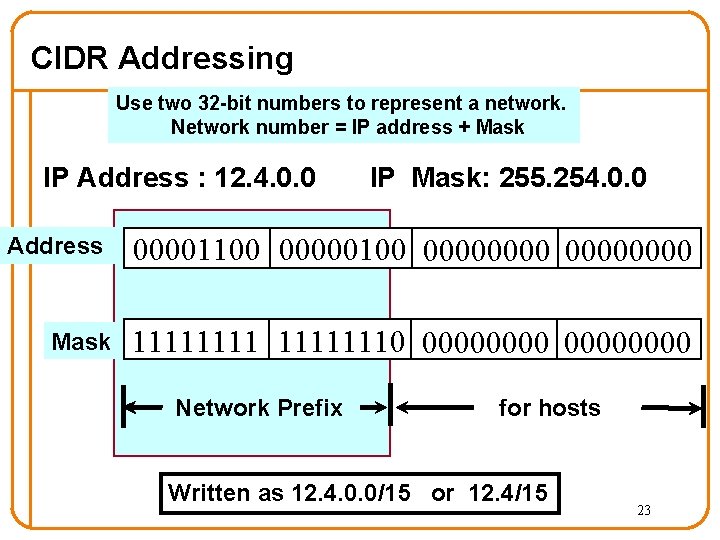
CIDR Addressing Use two 32 -bit numbers to represent a network. Network number = IP address + Mask IP Address : 12. 4. 0. 0 Address Mask IP Mask: 255. 254. 0. 0 00001100 00000000 11111110 00000000 Network Prefix for hosts Written as 12. 4. 0. 0/15 or 12. 4/15 23

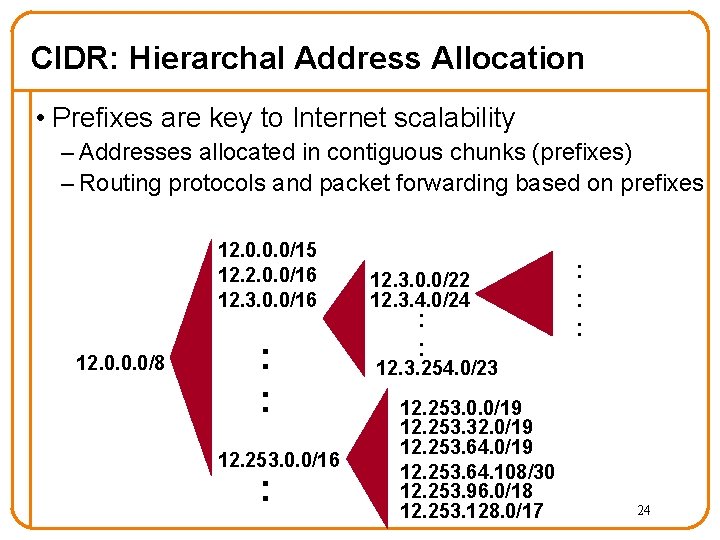
CIDR: Hierarchal Address Allocation • Prefixes are key to Internet scalability – Addresses allocated in contiguous chunks (prefixes) – Routing protocols and packet forwarding based on prefixes 12. 0. 0. 0/15 12. 2. 0. 0/16 12. 3. 0. 0/16 12. 0. 0. 0/8 : : 12. 253. 0. 0/16 : 12. 3. 0. 0/22 12. 3. 4. 0/24 : : : 12. 3. 254. 0/23 12. 253. 0. 0/19 12. 253. 32. 0/19 12. 253. 64. 108/30 12. 253. 96. 0/18 12. 253. 128. 0/17 24

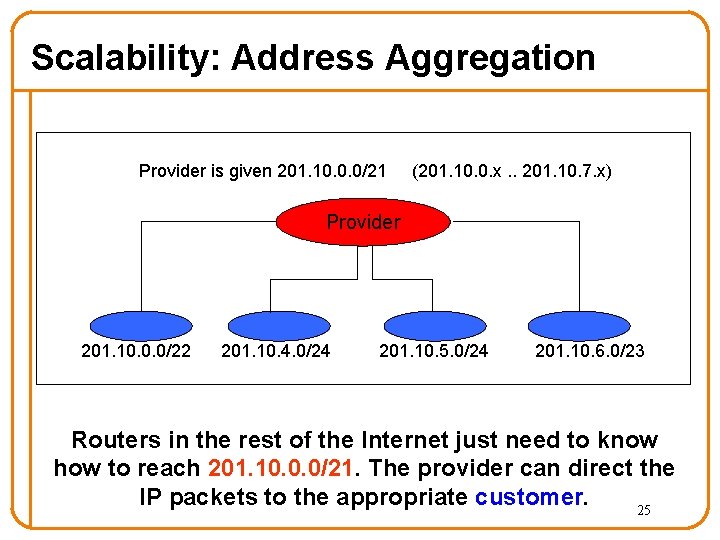
Scalability: Address Aggregation Provider is given 201. 10. 0. 0/21 (201. 10. 0. x. . 201. 10. 7. x) Provider 201. 10. 0. 0/22 201. 10. 4. 0/24 201. 10. 5. 0/24 201. 10. 6. 0/23 Routers in the rest of the Internet just need to know how to reach 201. 10. 0. 0/21. The provider can direct the IP packets to the appropriate customer. 25

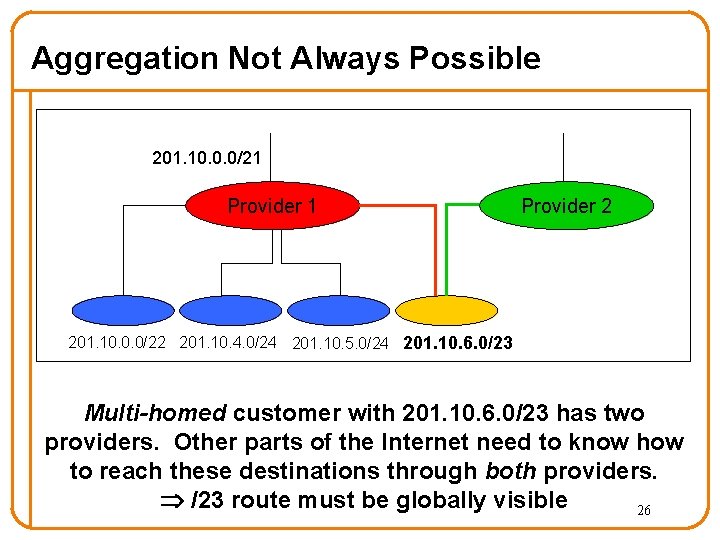
Aggregation Not Always Possible 201. 10. 0. 0/21 Provider 2 201. 10. 0. 0/22 201. 10. 4. 0/24 201. 10. 5. 0/24 201. 10. 6. 0/23 Multi-homed customer with 201. 10. 6. 0/23 has two providers. Other parts of the Internet need to know how to reach these destinations through both providers. /23 route must be globally visible 26

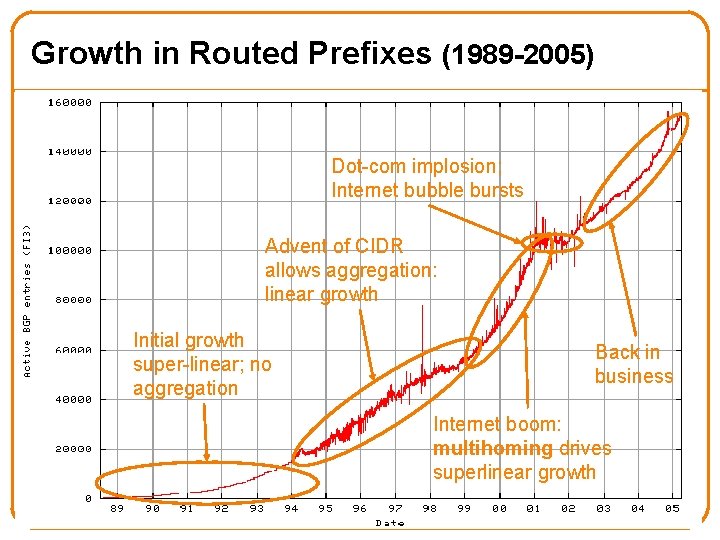
Growth in Routed Prefixes (1989 -2005) Dot-com implosion; Internet bubble bursts Advent of CIDR allows aggregation: linear growth Initial growth super-linear; no aggregation Back in business Internet boom: multihoming drives superlinear growth 27

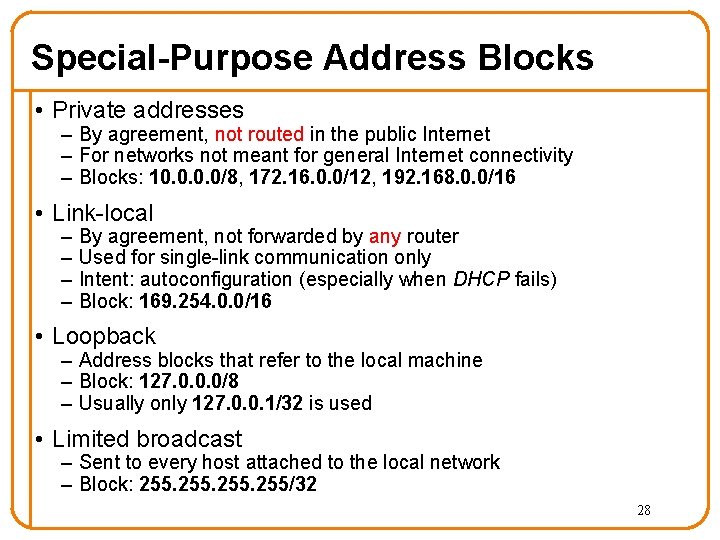
Special-Purpose Address Blocks • Private addresses – By agreement, not routed in the public Internet – For networks not meant for general Internet connectivity – Blocks: 10. 0/8, 172. 16. 0. 0/12, 192. 168. 0. 0/16 • Link-local – – By agreement, not forwarded by any router Used for single-link communication only Intent: autoconfiguration (especially when DHCP fails) Block: 169. 254. 0. 0/16 • Loopback – Address blocks that refer to the local machine – Block: 127. 0. 0. 0/8 – Usually only 127. 0. 0. 1/32 is used • Limited broadcast – Sent to every host attached to the local network – Block: 255/32 28

Summary of IP Addressing Scalability Through Non-Uniform Hierarchy • Hierarchical addressing – Critical for scalable system – Don’t require everyone to know everyone else – Reduces amount of updating when something changes • Non-uniform hierarchy – Useful for heterogeneous networks of different sizes – Class-based addressing was far too coarse – Classless Inter. Domain Routing (CIDR) more flexible 29

Editorial • Internet started with simple addressing design: – Two-layer hierarchy: network and host – Addresses in each hierarchy not tied to network topology • Address exhaustion led to a less clean design – CIDR is based on flexible aggregation – Aggregation relies on topological numbering • In “our” design, names were – Semantic-free – Verifiable • Internet addresses violate both of these conditions – Spoofing, problems with mobility, etc. 30

5 Minute Break Questions Before We Proceed? 31

Address Allocation 32

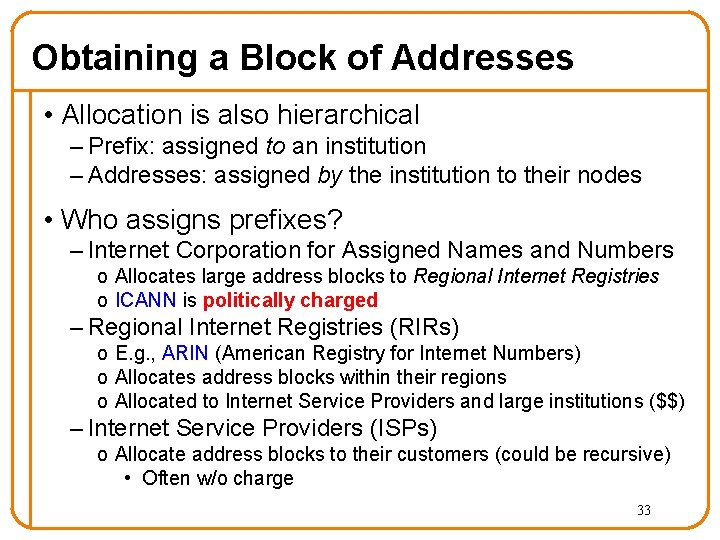
Obtaining a Block of Addresses • Allocation is also hierarchical – Prefix: assigned to an institution – Addresses: assigned by the institution to their nodes • Who assigns prefixes? – Internet Corporation for Assigned Names and Numbers o Allocates large address blocks to Regional Internet Registries o ICANN is politically charged – Regional Internet Registries (RIRs) o E. g. , ARIN (American Registry for Internet Numbers) o Allocates address blocks within their regions o Allocated to Internet Service Providers and large institutions ($$) – Internet Service Providers (ISPs) o Allocate address blocks to their customers (could be recursive) • Often w/o charge 33

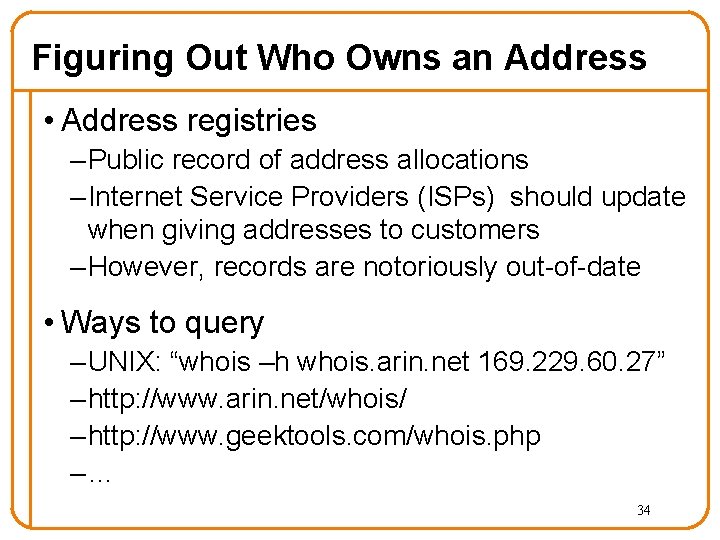
Figuring Out Who Owns an Address • Address registries – Public record of address allocations – Internet Service Providers (ISPs) should update when giving addresses to customers – However, records are notoriously out-of-date • Ways to query – UNIX: “whois –h whois. arin. net 169. 229. 60. 27” – http: //www. arin. net/whois/ – http: //www. geektools. com/whois. php –… 34

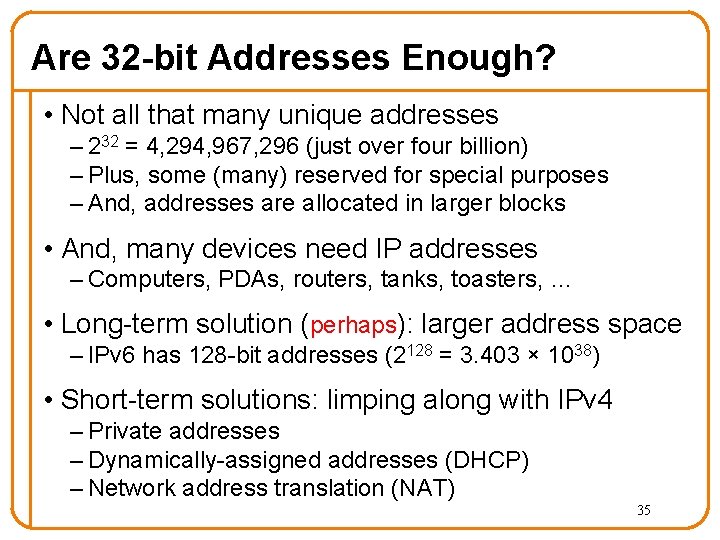
Are 32 -bit Addresses Enough? • Not all that many unique addresses – 232 = 4, 294, 967, 296 (just over four billion) – Plus, some (many) reserved for special purposes – And, addresses are allocated in larger blocks • And, many devices need IP addresses – Computers, PDAs, routers, tanks, toasters, … • Long-term solution (perhaps): larger address space – IPv 6 has 128 -bit addresses (2128 = 3. 403 × 1038) • Short-term solutions: limping along with IPv 4 – Private addresses – Dynamically-assigned addresses (DHCP) – Network address translation (NAT) 35

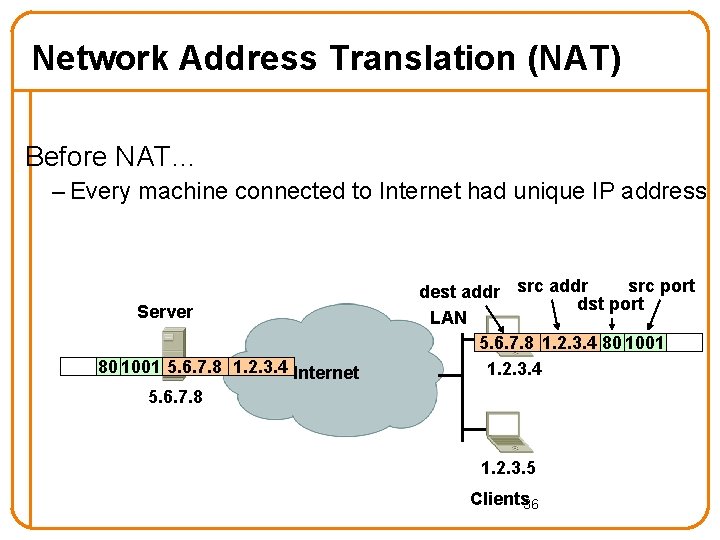
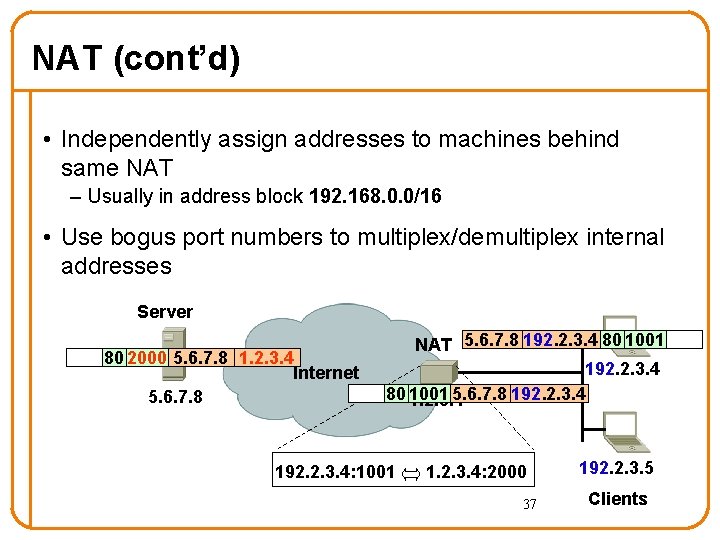
Network Address Translation (NAT) Before NAT… – Every machine connected to Internet had unique IP address Server 80 1001 5. 6. 7. 8 1. 2. 3. 4 Internet 5. 6. 7. 8 src port dest addr src addr dst port LAN 5. 6. 7. 8 1. 2. 3. 4 80 1001 1. 2. 3. 4 1. 2. 3. 5 Clients 36

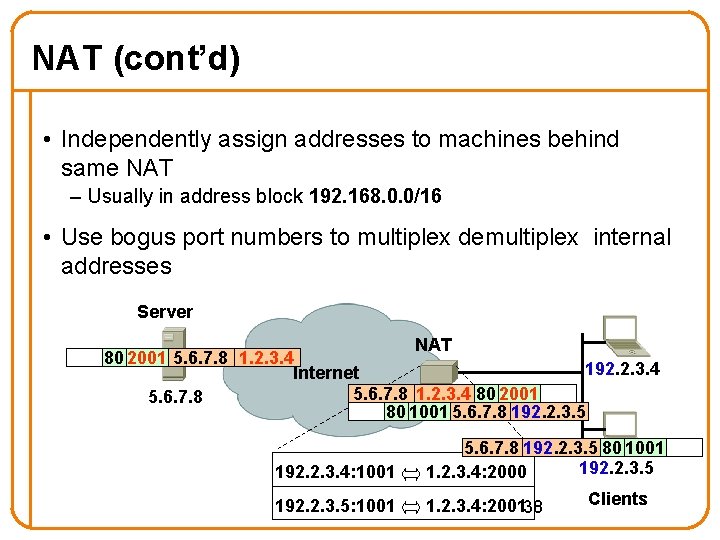
NAT (cont’d) • Independently assign addresses to machines behind same NAT – Usually in address block 192. 168. 0. 0/16 • Use bogus port numbers to multiplex/demultiplex internal addresses Server NAT 5. 6. 7. 8 192. 2. 3. 4 80 1001 80 2000 5. 6. 7. 8 1. 2. 3. 4 192. 2. 3. 4 Internet 5. 6. 7. 8 80 1001 1. 2. 3. 4 5. 6. 7. 8 80 2000 192. 2. 3. 4 5. 6. 7. 8 1. 2. 3. 4 192. 2. 3. 4: 1001 1. 2. 3. 4: 2000 37 192. 2. 3. 5 Clients

NAT (cont’d) • Independently assign addresses to machines behind same NAT – Usually in address block 192. 168. 0. 0/16 • Use bogus port numbers to multiplex demultiplex internal addresses Server NAT 80 2001 5. 6. 7. 8 1. 2. 3. 4 192. 2. 3. 4 Internet 5. 6. 7. 8 1. 2. 3. 4 80 2001 5. 6. 7. 8 80 1001 5. 6. 7. 8 192. 2. 3. 5 192. 2. 3. 4: 1001 5. 6. 7. 8 192. 2. 3. 5 80 1001 192. 2. 3. 5 1. 2. 3. 4: 2000 192. 2. 3. 5: 1001 1. 2. 3. 4: 200138 Clients

Hard Policy Questions • How much address space per geographic region? – Equal amount per country? – Proportional to the population? – What about addresses already allocated? • Address space portability? – Keep your address block when you change providers? – Pro: avoid having to renumber your equipment – Con: reduces the effectiveness of address aggregation • Keeping the address registries up to date? – What about mergers and acquisitions? – Delegation of address blocks to customers? – As a result, the registries are often out of date 39

Summary of IP Addressing • 32 -bit numbers identify interfaces • Allocated in prefixes • Non-uniform hierarchy for scalability and flexibility – Routing is based on CIDR • A number of special-purpose blocks reserved • Address allocation: – ICANN RIR ISP customer network host • Issues to be covered later – How hosts get their addresses (DHCP) – How to map from an IP address to a link address (ARP) 40

Quick Security Analysis 41

Focus on Sender Attacks • Ignore (for now) attacks by others: – Traffic analysis – Snooping payload – Denial of service • Here we look at vulnerabilities sender can exploit 42

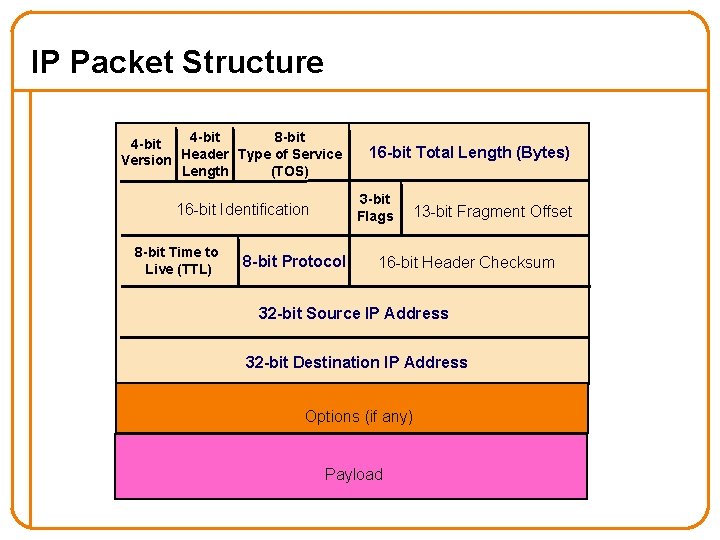
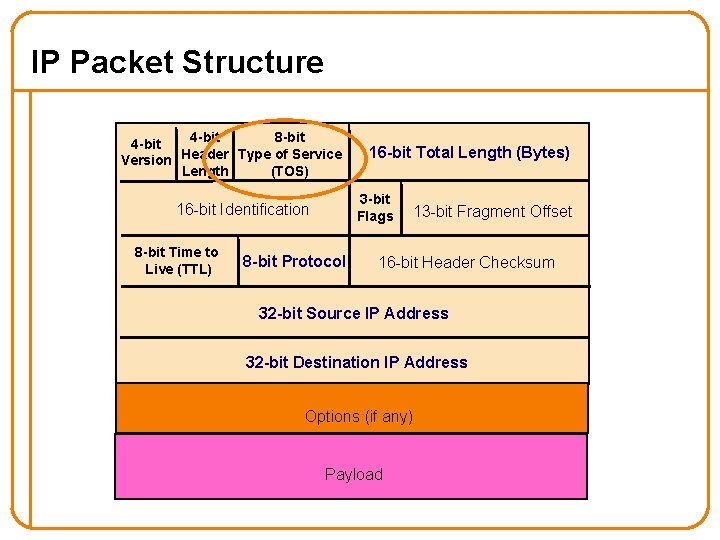
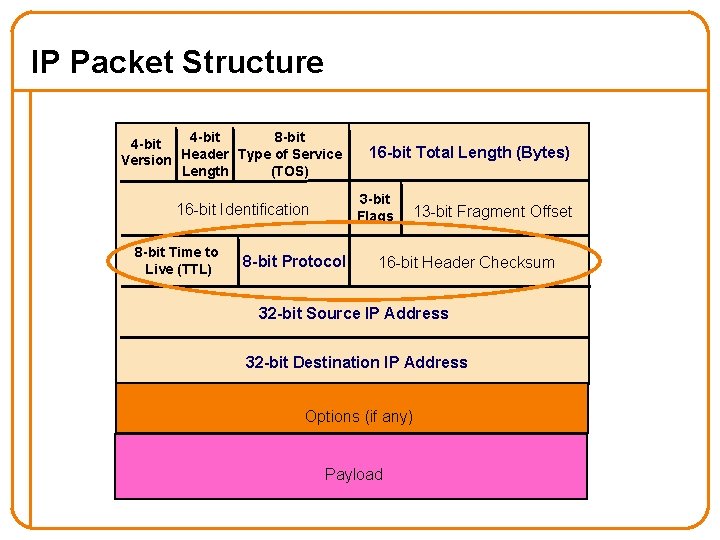
IP Packet Structure 4 -bit 8 -bit 4 -bit Version Header Type of Service Length (TOS) 3 -bit Flags 16 -bit Identification 8 -bit Time to Live (TTL) 16 -bit Total Length (Bytes) 8 -bit Protocol 13 -bit Fragment Offset 16 -bit Header Checksum 32 -bit Source IP Address 32 -bit Destination IP Address Options (if any) Payload

IP Address Integrity • Source address should be the sending host – But, who’s checking, anyway? – You could send packets with any source you want – Why is checking hard? 44

IP Address Integrity, con’t • Why would someone use a bogus source address? • Launch a denial-of-service attack – Send excessive packets to the destination – … to overload the node, or the links leading to the node – But: victim can identify/filter you by the source address • Evade detection by “spoofing” – Put someone else’s source address in the packets o Or: use a lot of different ones so can’t be filtered • Or: as a way to bother the spoofed host – Spoofed host is wrongly blamed – Spoofed host may receive return traffic from the receiver 45

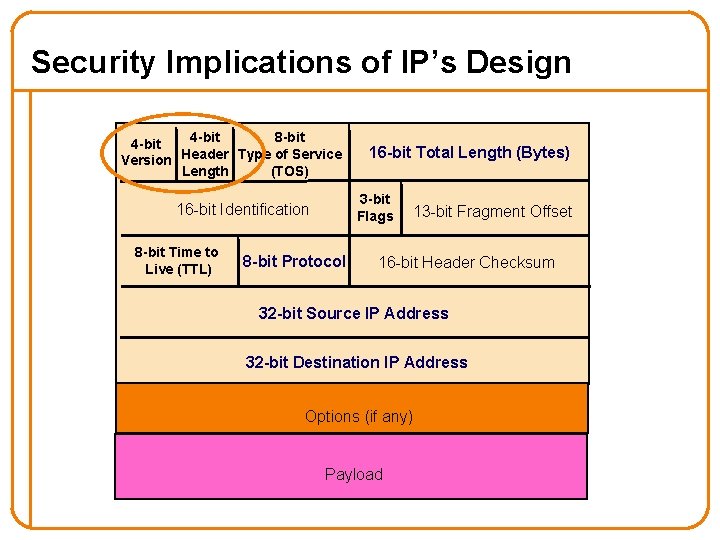
Security Implications of IP’s Design 4 -bit 8 -bit 4 -bit Version Header Type of Service Length (TOS) 3 -bit Flags 16 -bit Identification 8 -bit Time to Live (TTL) 16 -bit Total Length (Bytes) 8 -bit Protocol 13 -bit Fragment Offset 16 -bit Header Checksum 32 -bit Source IP Address 32 -bit Destination IP Address Options (if any) Payload

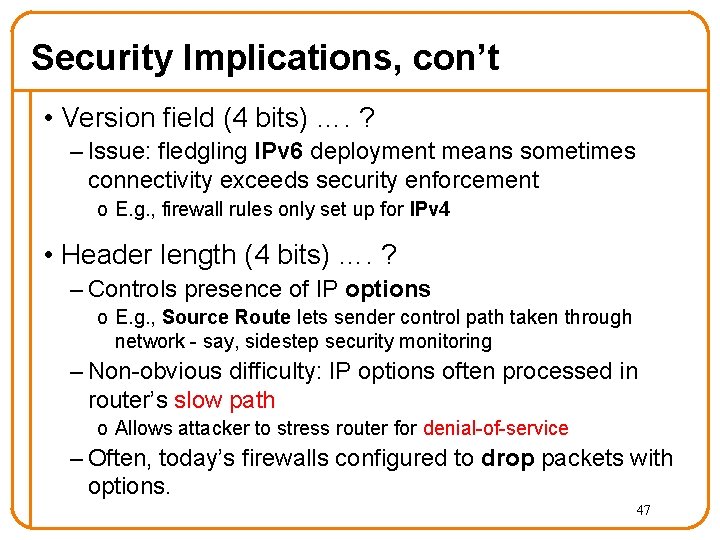
Security Implications, con’t • Version field (4 bits) …. ? – Issue: fledgling IPv 6 deployment means sometimes connectivity exceeds security enforcement o E. g. , firewall rules only set up for IPv 4 • Header length (4 bits) …. ? – Controls presence of IP options o E. g. , Source Route lets sender control path taken through network - say, sidestep security monitoring – Non-obvious difficulty: IP options often processed in router’s slow path o Allows attacker to stress router for denial-of-service – Often, today’s firewalls configured to drop packets with options. 47

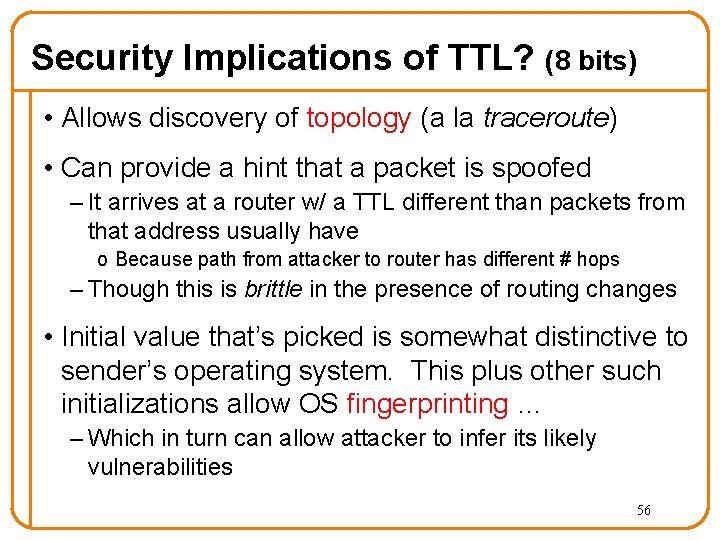
IP Packet Structure 4 -bit 8 -bit 4 -bit Version Header Type of Service Length (TOS) 3 -bit Flags 16 -bit Identification 8 -bit Time to Live (TTL) 16 -bit Total Length (Bytes) 8 -bit Protocol 13 -bit Fragment Offset 16 -bit Header Checksum 32 -bit Source IP Address 32 -bit Destination IP Address Options (if any) Payload

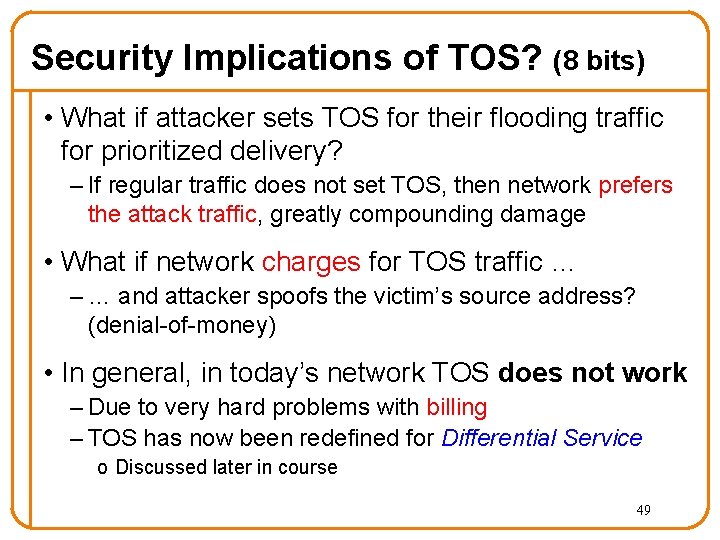
Security Implications of TOS? (8 bits) • What if attacker sets TOS for their flooding traffic for prioritized delivery? – If regular traffic does not set TOS, then network prefers the attack traffic, greatly compounding damage • What if network charges for TOS traffic … – … and attacker spoofs the victim’s source address? (denial-of-money) • In general, in today’s network TOS does not work – Due to very hard problems with billing – TOS has now been redefined for Differential Service o Discussed later in course 49

IP Packet Structure 4 -bit 8 -bit 4 -bit Version Header Type of Service Length (TOS) 3 -bit Flags 16 -bit Identification 8 -bit Time to Live (TTL) 16 -bit Total Length (Bytes) 8 -bit Protocol 13 -bit Fragment Offset 16 -bit Header Checksum 32 -bit Source IP Address 32 -bit Destination IP Address Options (if any) Payload

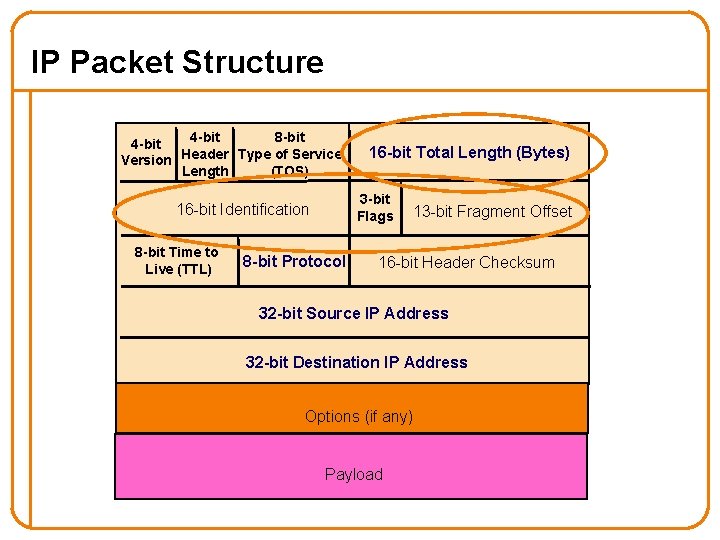
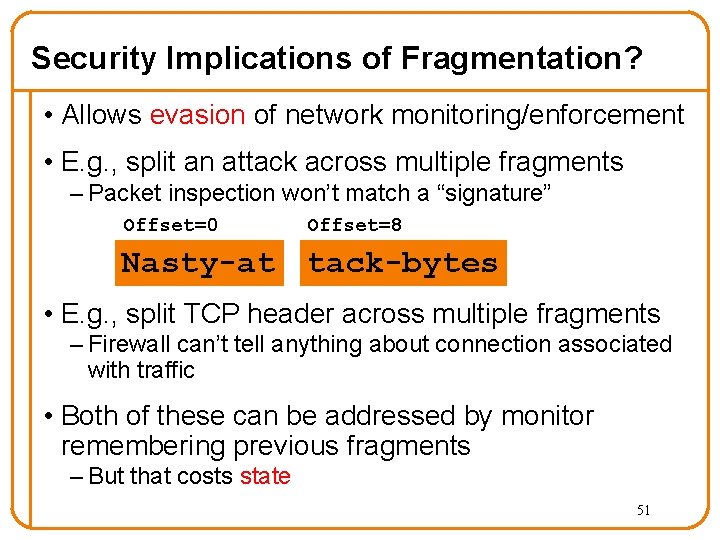
Security Implications of Fragmentation? • Allows evasion of network monitoring/enforcement • E. g. , split an attack across multiple fragments – Packet inspection won’t match a “signature” Offset=0 Offset=8 Nasty-at tack-bytes • E. g. , split TCP header across multiple fragments – Firewall can’t tell anything about connection associated with traffic • Both of these can be addressed by monitor remembering previous fragments – But that costs state 51

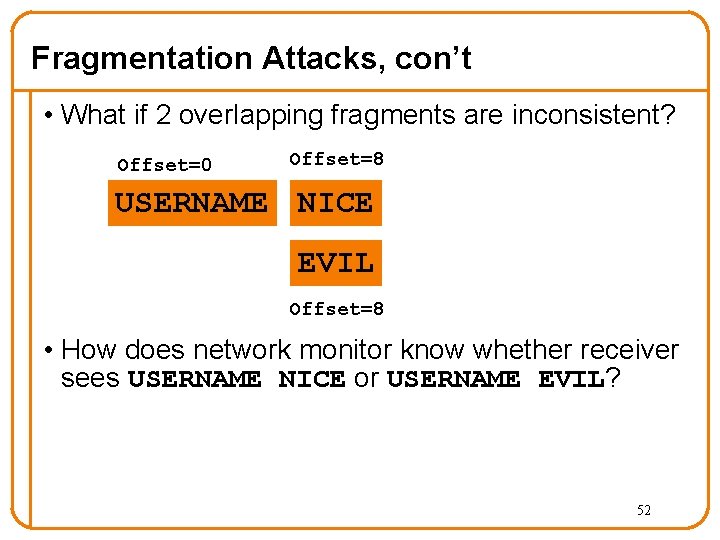
Fragmentation Attacks, con’t • What if 2 overlapping fragments are inconsistent? Offset=0 Offset=8 USERNAME NICE EVIL Offset=8 • How does network monitor know whether receiver sees USERNAME NICE or USERNAME EVIL? 52

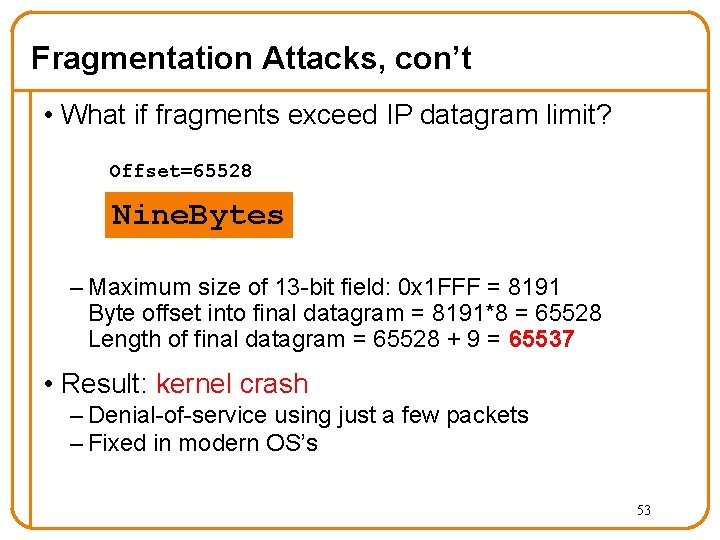
Fragmentation Attacks, con’t • What if fragments exceed IP datagram limit? Offset=65528 Nine. Bytes – Maximum size of 13 -bit field: 0 x 1 FFF = 8191 Byte offset into final datagram = 8191*8 = 65528 Length of final datagram = 65528 + 9 = 65537 • Result: kernel crash – Denial-of-service using just a few packets – Fixed in modern OS’s 53

Fragmentation Attacks, con’t • What happens if attacker doesn’t send all of the fragments in a datagram? • Receiver (or firewall) winds up holding the ones they receive for a long time – State-holding attack 54

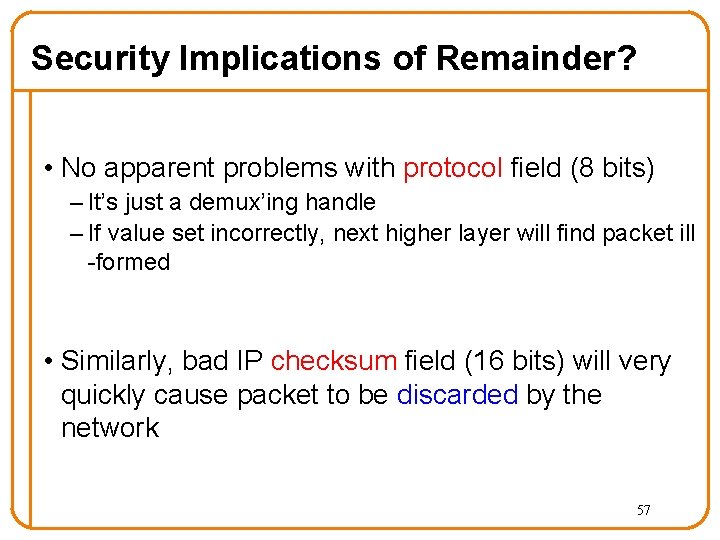
IP Packet Structure 4 -bit 8 -bit 4 -bit Version Header Type of Service Length (TOS) 3 -bit Flags 16 -bit Identification 8 -bit Time to Live (TTL) 16 -bit Total Length (Bytes) 8 -bit Protocol 13 -bit Fragment Offset 16 -bit Header Checksum 32 -bit Source IP Address 32 -bit Destination IP Address Options (if any) Payload

Security Implications of TTL? (8 bits) • Allows discovery of topology (a la traceroute) • Can provide a hint that a packet is spoofed – It arrives at a router w/ a TTL different than packets from that address usually have o Because path from attacker to router has different # hops – Though this is brittle in the presence of routing changes • Initial value that’s picked is somewhat distinctive to sender’s operating system. This plus other such initializations allow OS fingerprinting … – Which in turn can allow attacker to infer its likely vulnerabilities 56

Security Implications of Remainder? • No apparent problems with protocol field (8 bits) – It’s just a demux’ing handle – If value set incorrectly, next higher layer will find packet ill -formed • Similarly, bad IP checksum field (16 bits) will very quickly cause packet to be discarded by the network 57

Next Lecture • IP Forwarding; Transport protocols • Read K&R: 3 -3. 4 58