Universidade Federal do Rio Grande do Sul PGCC








- Slides: 18

Universidade Federal do Rio Grande do Sul PGCC - Pós-graduação em Computação Considerações sobre o algoritmo RC 4. Ricardo Goulart ragoulart@hotmail. com

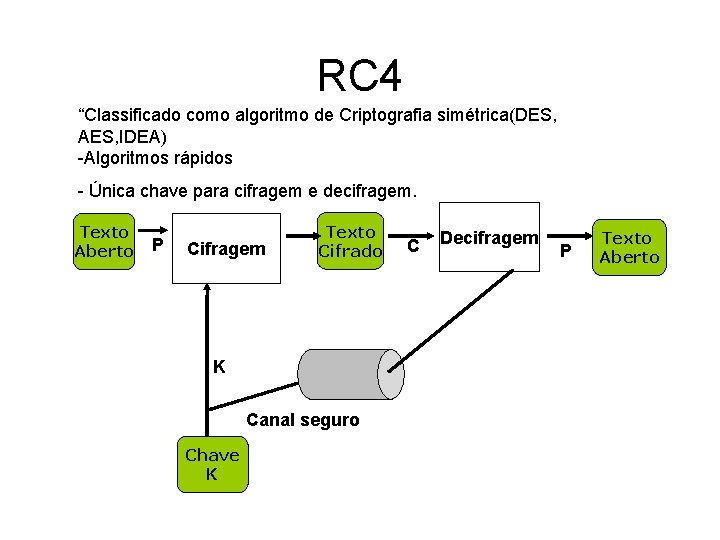
RC 4 “Classificado como algoritmo de Criptografia simétrica(DES, AES, IDEA) -Algoritmos rápidos - Única chave para cifragem e decifragem. Texto Aberto P Cifragem Texto Cifrado K Canal seguro Chave K c Decifragem P Texto Aberto

RC 4 É um Stream Cipher. Gera ilimitados bytes pseudo aleatórios Possui chave de tamanho variável. Não é considerado um dos melhores sistemas criptográficos

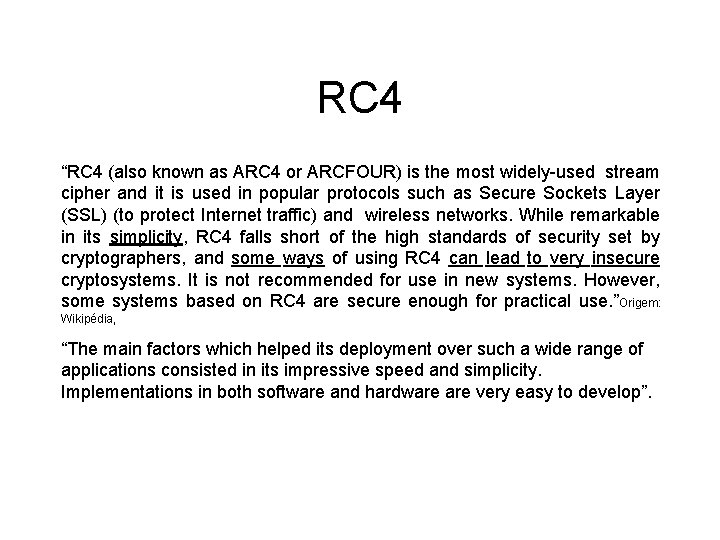
RC 4 “RC 4 (also known as ARC 4 or ARCFOUR) is the most widely-used stream cipher and it is used in popular protocols such as Secure Sockets Layer (SSL) (to protect Internet traffic) and wireless networks. While remarkable in its simplicity, RC 4 falls short of the high standards of security set by cryptographers, and some ways of using RC 4 can lead to very insecure cryptosystems. It is not recommended for use in new systems. However, some systems based on RC 4 are secure enough for practical use. ”Origem: Wikipédia, “The main factors which helped its deployment over such a wide range of applications consisted in its impressive speed and simplicity. Implementations in both software and hardware very easy to develop”.

RC 4 História 1987 Ron Rivest desenvolve o algoritmo RC 4 para RSA(Rivest, Samir and Aderman) Data Security, Inc. , Especializada em sist. encriptação. Foi, um segredo comercial bem protegido, popular, e utilizado largamente em software, como Lotus Notes, Apple Computer’s AOCE, Oracle Secure SQL, Internet Explorer, Netscape e Adobe Acrobat. [SCH 96] Em Set 1994, é postado um código fonte em uma mailing list dedicada à criptografia (Cypherpunks) supostamente equivalente ao RC 4. Espalhou-se rápido pela rede e foi confirmada a compatilidade com o RC 4.

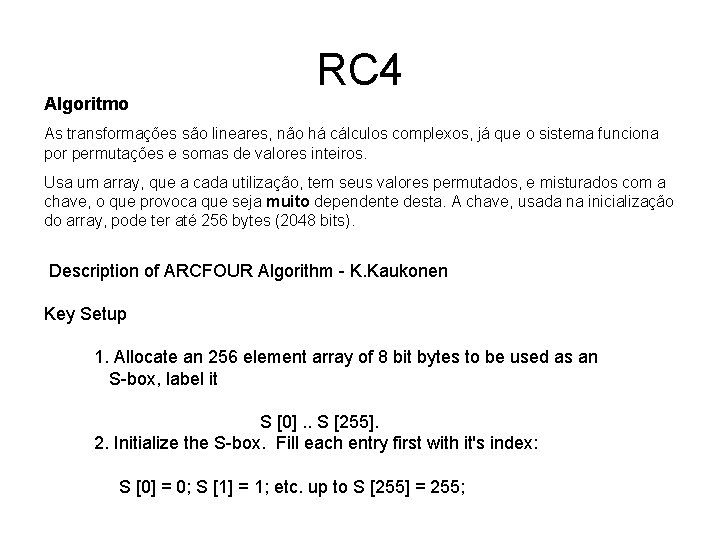
Algoritmo RC 4 As transformações são lineares, não há cálculos complexos, já que o sistema funciona por permutações e somas de valores inteiros. Usa um array, que a cada utilização, tem seus valores permutados, e misturados com a chave, o que provoca que seja muito dependente desta. A chave, usada na inicialização do array, pode ter até 256 bytes (2048 bits). Description of ARCFOUR Algorithm - K. Kaukonen Key Setup 1. Allocate an 256 element array of 8 bit bytes to be used as an S-box, label it S [0]. . S [255]. 2. Initialize the S-box. Fill each entry first with it's index: S [0] = 0; S [1] = 1; etc. up to S [255] = 255;

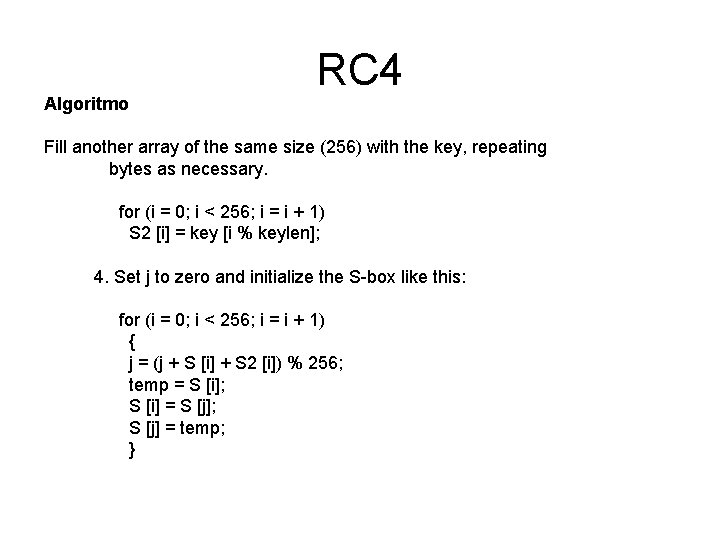
Algoritmo RC 4 Fill another array of the same size (256) with the key, repeating bytes as necessary. for (i = 0; i < 256; i = i + 1) S 2 [i] = key [i % keylen]; 4. Set j to zero and initialize the S-box like this: for (i = 0; i < 256; i = i + 1) { j = (j + S [i] + S 2 [i]) % 256; temp = S [i]; S [i] = S [j]; S [j] = temp; }

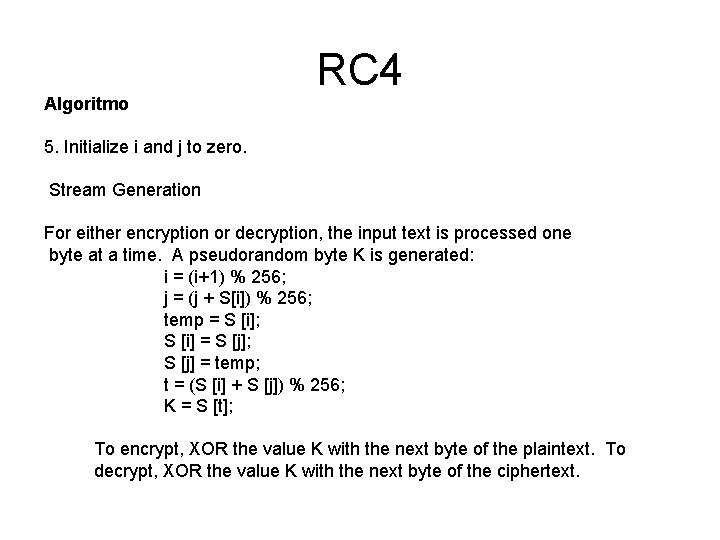
Algoritmo RC 4 5. Initialize i and j to zero. Stream Generation For either encryption or decryption, the input text is processed one byte at a time. A pseudorandom byte K is generated: i = (i+1) % 256; j = (j + S[i]) % 256; temp = S [i]; S [i] = S [j]; S [j] = temp; t = (S [i] + S [j]) % 256; K = S [t]; To encrypt, XOR the value K with the next byte of the plaintext. To decrypt, XOR the value K with the next byte of the ciphertext.

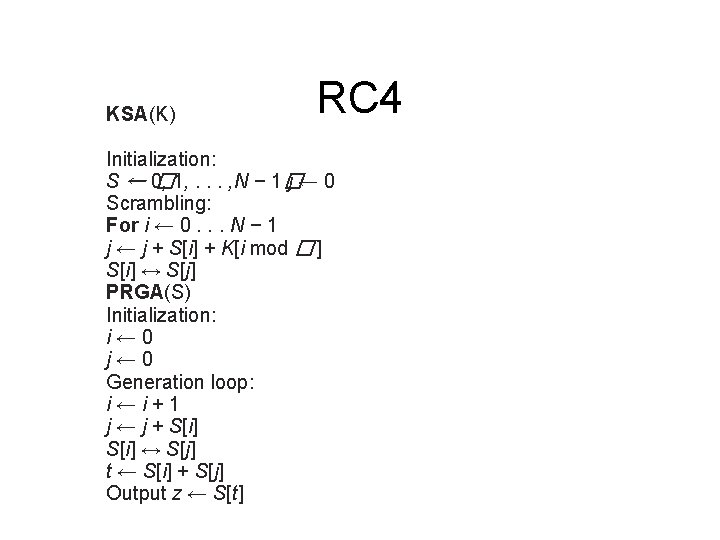
KSA(K) RC 4 Initialization: S ← 0, � 1, . . . , N − 1� j← 0 Scrambling: For i ← 0. . . N − 1 j ← j + S[i] + K[i mod � ] S[i] ↔ S[j] PRGA(S) Initialization: i← 0 j← 0 Generation loop: i←i+1 j ← j + S[i] ↔ S[j] t ← S[i] + S[j] Output z ← S[t]

RC 4 Fragilidade do RC 4 2001 - publicação de artigos sobre a fragilidade do protocolo WEP: O Intercepting Mobile Communication, UCB e o Weakness in the Key Scheduling Algorithm of RC 4, escrito pelo CISCO e Instituto Weizmann, Israel. . Esses dois artigos atacam o WEP, alegando ou dando a entender que a sua maior fragilidade é o seu algoritmo de criptografia. O primeiro artigo ensina como se consegue, sem o conhecimento prévio da chave ter acesso às informações criptografadas.

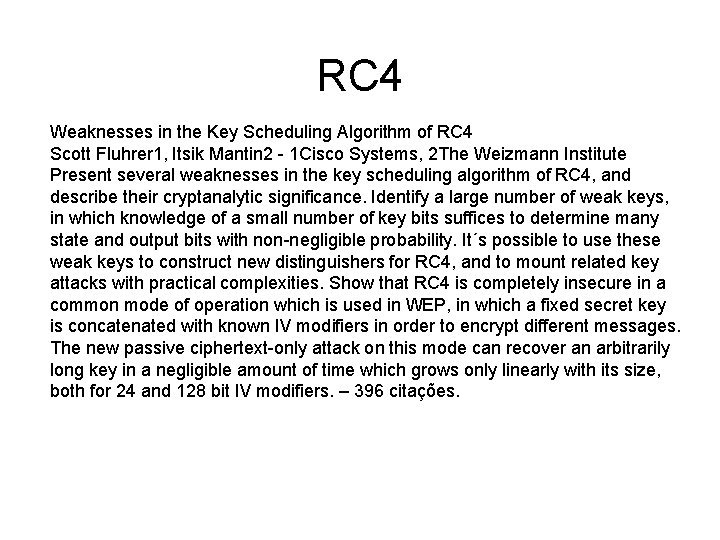
RC 4 Weaknesses in the Key Scheduling Algorithm of RC 4 Scott Fluhrer 1, Itsik Mantin 2 - 1 Cisco Systems, 2 The Weizmann Institute Present several weaknesses in the key scheduling algorithm of RC 4, and describe their cryptanalytic significance. Identify a large number of weak keys, in which knowledge of a small number of key bits suffices to determine many state and output bits with non-negligible probability. It´s possible to use these weak keys to construct new distinguishers for RC 4, and to mount related key attacks with practical complexities. Show that RC 4 is completely insecure in a common mode of operation which is used in WEP, in which a fixed secret key is concatenated with known IV modifiers in order to encrypt different messages. The new passive ciphertext-only attack on this mode can recover an arbitrarily long key in a negligible amount of time which grows only linearly with its size, both for 24 and 128 bit IV modifiers. – 396 citações.

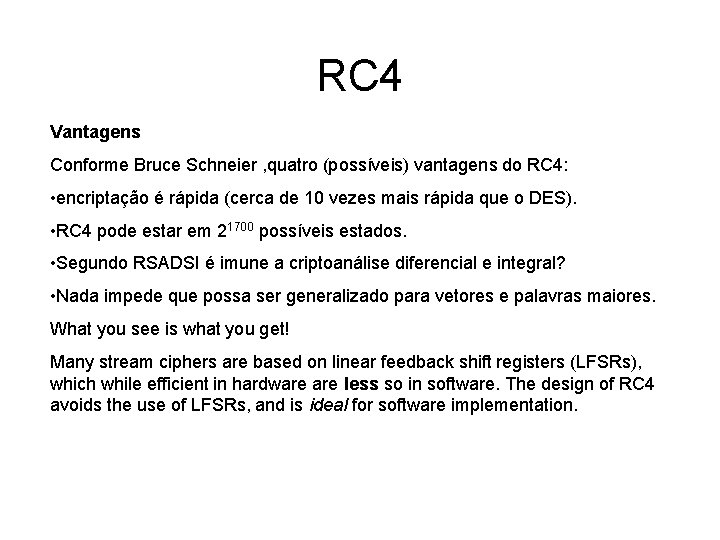
RC 4 Vantagens Conforme Bruce Schneier , quatro (possíveis) vantagens do RC 4: • encriptação é rápida (cerca de 10 vezes mais rápida que o DES). • RC 4 pode estar em 21700 possíveis estados. • Segundo RSADSI é imune a criptoanálise diferencial e integral? • Nada impede que possa ser generalizado para vetores e palavras maiores. What you see is what you get! Many stream ciphers are based on linear feedback shift registers (LFSRs), which while efficient in hardware less so in software. The design of RC 4 avoids the use of LFSRs, and is ideal for software implementation.

RC 4 Desvantagens ? Defesa do RC 4? Maior fragilidade observada é na forma que foi implementado no WEP. Implementação incorreta no Microsoft msoffice 2002/2003 In 2001 a new discovery was made by Fluhrer, Mantin and Shamir: over all possible RC 4 keys, the statistics for the first few bytes of output keystream are strongly non-random, leaking information about the key. If the long-term key and nonce are simply concatenated to generate the RC 4 key, this longterm key can be discovered by analysing large number of messages encrypted with this key. “weaknesses in the key scheduling algorithm can be prevented by discarding the first 256 output bytes of the pseudo-random generator before beginning encryption” - RSA.

RC 4 Desvantagens ? Defesa do RC 4? So far no one had found an attack on the PRGA part of RC 4 which is even close to being practical: For n = 8 and sufficiently long keys, the best known attack requires more than 2700 time to find its initial state. - RSA.

RC 4 Desvantagens ? O que diz a RSA? The "heart" of RC 4 is its exceptionally simple and extremely efficient pseudorandom generator. The recent attacks relate only to the key-scheduling algorithm, not to the generator. There at present no known practical attacks against this generator when initialized with a randomly-chosen initial state. RC 4 is likely to remain the algorithm of choice for many applications and embedded systems. (Of course, strong block ciphers like AES or RC 6 should also routinely be considered as candidates for any new application, particularly when authentication is also required, since block ciphers can utilize modes of operation, that efficiently provide both confidentiality and integrity. ) The initial key scheduling component of RC 4 should for now be routinely amended for new applications to include hashing and/or discarding the first 256 bytes of pseudo-random output. (This has in any case been RSA's routine recommendation. ).

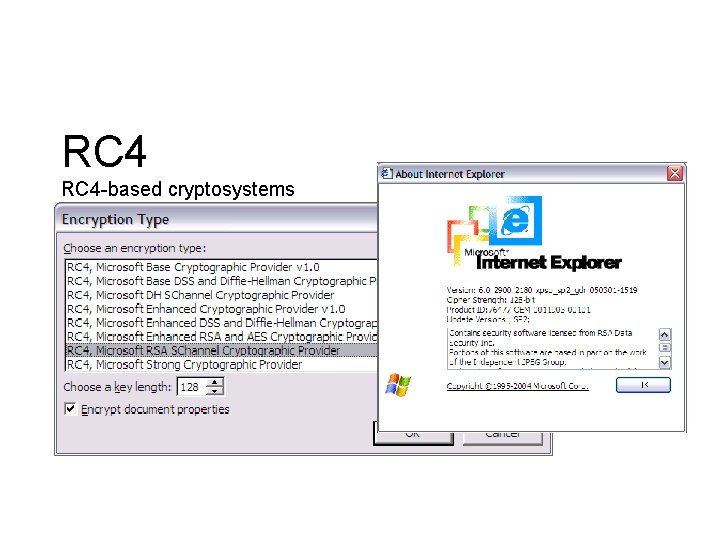
RC 4 Sistemas de criptografia baseados no RC 4 WEP e WPA Cipher. Saber Bit. Torrent protocol encryption Microsoft Point-to-Point Encryption SSL- Secure Sockets Layer (optionally) Secure shell (optionally) Kerberos (optionally) MSOffice 2002 / 2003

RC 4 -based cryptosystems

RC 4 • Bruce Schneier. Applied Criptography. 1996. P 397 -398. Chapter 17. Others Stream Ciphers and Real Random Sequence Generators. • Kaukonen, Thayer Internet Draft ARCFOUR Algorithm July, 1999. A Stream Cipher Encryption Algorithm "Arcfour“. Disponivel em • http: //www. mozilla. org/projects/security/pki/nss/draft-kaukonen-cipher-arcfour 03. txt • Mehran Misaghi - O Papel da Criptografia em Segurança da Informação SOCIESC – IST. • Wikipédia(Inglês). Abril de 2007. • RSA Security Response to weaknesses in ksa of rc 4. RSA Site. • http: //www. rsa. com/rsalabs/node. asp? id=2009 • WEBER. Raul Fernando. PEREZ, André. UFRGS. Considerações sobre segurança em redes sem fio. • PEARL Tools. Um conjunto de Ferramentas para avaliação da Eficiência de algoritmos de criptografia em dispositivos móveis. UFB. Hernandez, mateus et al. • Hongjun Wu. The misuse of RC 4 in Microsoft Word and Excel. I. I. R, Singapure. • Cryptobytes. Atacks in RC 4 and WEP. RSA Laboratories. Vol. 5 Num 2. 2002 Scott Fluhrer, Itsik Mantin, and Adi Shamir.
 Universidade federal do rio grande do norte
Universidade federal do rio grande do norte Universidade federal do rio grande do norte
Universidade federal do rio grande do norte Arenização rio grande do sul
Arenização rio grande do sul Accokeek hall pgcc
Accokeek hall pgcc Meu pergamum unifesp
Meu pergamum unifesp Universidade federal de santa catarina
Universidade federal de santa catarina Ufam
Ufam Universidade federal de santa catarina brazil
Universidade federal de santa catarina brazil Siare ufsc
Siare ufsc Universidade federal do amazonas
Universidade federal do amazonas Universidade federal de santa catarina
Universidade federal de santa catarina Universidade federal de santa catarina
Universidade federal de santa catarina Universidade federal do amazonas medicina
Universidade federal do amazonas medicina Universidade federal de santa catarina
Universidade federal de santa catarina Texto-base adaptada universidade federal de alagoas ufal
Texto-base adaptada universidade federal de alagoas ufal Zigurates
Zigurates Access rio hondo college
Access rio hondo college Rio grande river
Rio grande river Bacia hidrográfica do rio grande
Bacia hidrográfica do rio grande



































