Traffic Matrix Approach R Newman Topics Defining anonymity





![Traffic Matrix TM has all diagonal entries zero No self-traffic T[i, j] = # Traffic Matrix TM has all diagonal entries zero No self-traffic T[i, j] = #](https://slidetodoc.com/presentation_image_h2/6ca549f877e3ad24c98a1ab98f28cbdd/image-10.jpg)


![Traffic Matrix Routes, flow assignments Actual TM requires Tact[i, j] message be sent from Traffic Matrix Routes, flow assignments Actual TM requires Tact[i, j] message be sent from](https://slidetodoc.com/presentation_image_h2/6ca549f877e3ad24c98a1ab98f28cbdd/image-13.jpg)


![Cost of Neutrality Padding only: Load Cost = (N 2 -N)max{Tact[i, j]} –Load(Tact) In Cost of Neutrality Padding only: Load Cost = (N 2 -N)max{Tact[i, j]} –Load(Tact) In](https://slidetodoc.com/presentation_image_h2/6ca549f877e3ad24c98a1ab98f28cbdd/image-27.jpg)










- Slides: 44

Traffic Matrix Approach R. Newman

Topics Defining anonymity Need for anonymity Defining privacy Threats to anonymity and privacy Mechanisms to provide anonymity Metrics for Anonymity Applications of anonymity technology

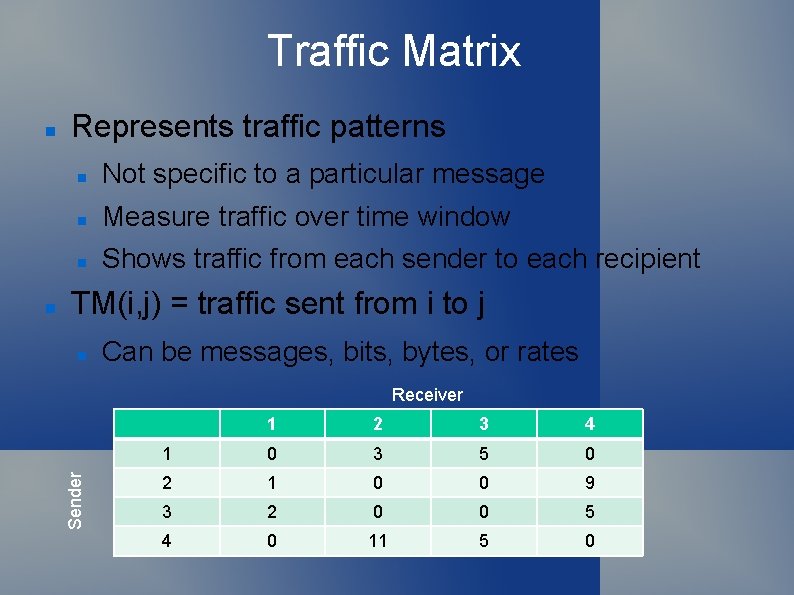
Traffic Matrix Represents traffic patterns Not specific to a particular message Measure traffic over time window Shows traffic from each sender to each recipient TM(i, j) = traffic sent from i to j Can be messages, bits, bytes, or rates Receiver Sender 1 2 3 4 1 0 3 5 0 2 1 0 0 9 3 2 0 0 5 4 0 11 5 0

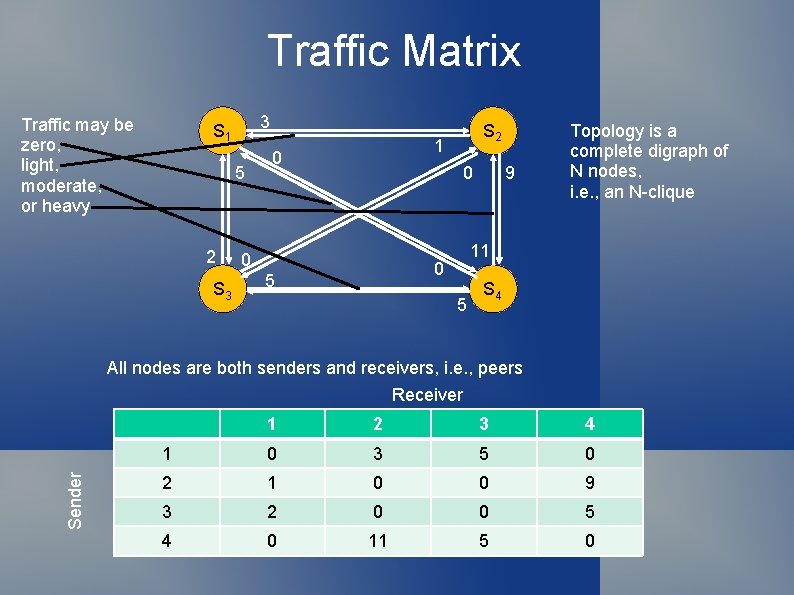
Traffic Matrix Traffic may be zero, light, moderate, or heavy 3 S 1 5 2 S 3 S 2 1 0 0 0 11 0 5 9 Topology is a complete digraph of N nodes, i. e. , an N-clique 5 S 4 All nodes are both senders and receivers, i. e. , peers Sender Receiver 1 2 3 4 1 0 3 5 0 2 1 0 0 9 3 2 0 0 5 4 0 11 5 0

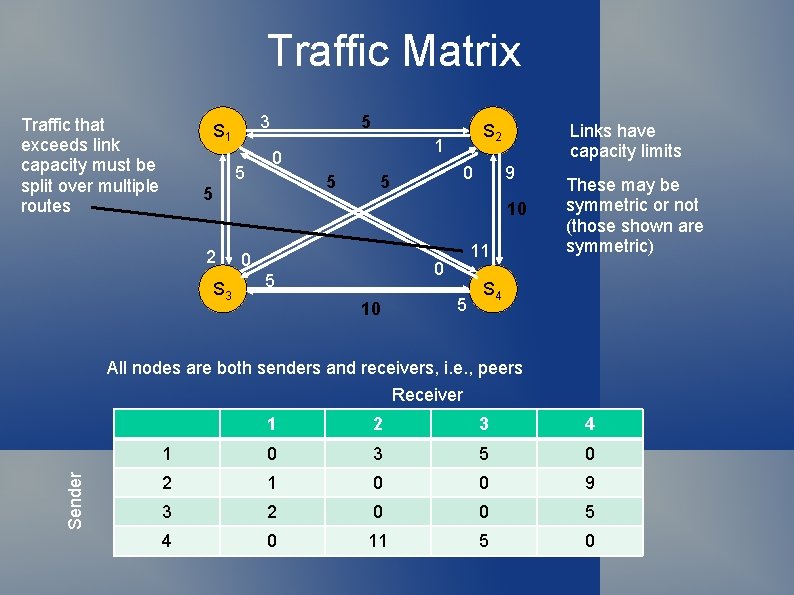
Traffic Matrix Traffic that exceeds link capacity must be split over multiple routes 3 S 1 5 5 1 0 5 5 S 2 0 5 Links have capacity limits 9 10 2 S 3 0 11 0 5 10 5 These may be symmetric or not (those shown are symmetric) S 4 All nodes are both senders and receivers, i. e. , peers Sender Receiver 1 2 3 4 1 0 3 5 0 2 1 0 0 9 3 2 0 0 5 4 0 11 5 0

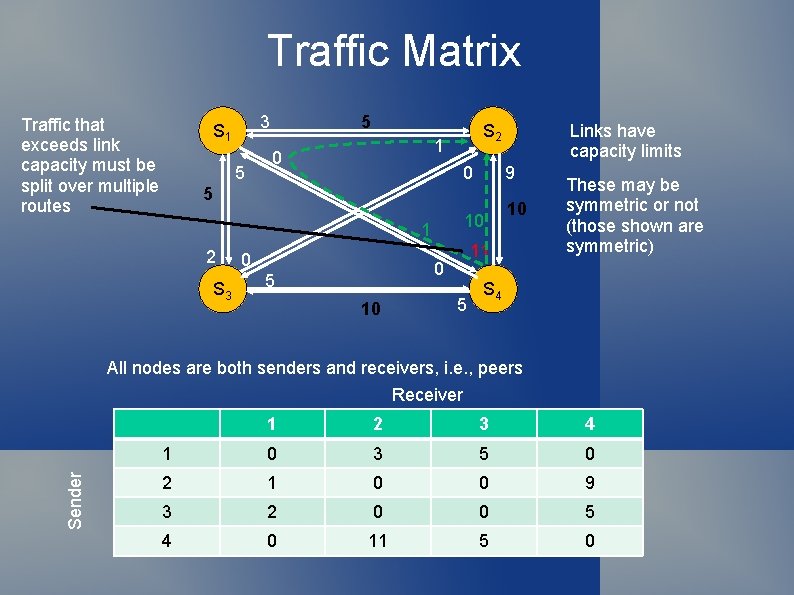
Traffic Matrix Traffic that exceeds link capacity must be split over multiple routes 3 S 1 5 5 S 2 1 0 0 9 5 10 1 2 S 3 0 10 10 11 0 5 Links have capacity limits 5 These may be symmetric or not (those shown are symmetric) S 4 All nodes are both senders and receivers, i. e. , peers Sender Receiver 1 2 3 4 1 0 3 5 0 2 1 0 0 9 3 2 0 0 5 4 0 11 5 0

Traffic Matrix Takes the approach that attacker wants to know traffic patterns Not specific to a particular message Measure traffic over time window Global passive adversary Sees source & destination for all msgs ”Observed TM” = what attacker observes If no countermeasures, then observed TM is the actual TM Assumes nodes are peers Assumes nodes are not compromised

TAP Countermeasures All messages are padded to same length Prevent linking messages Only (visible) source and destination are not encrypted Prevent linking messages Prevent source/destination linkage

TAP Countermeasures Node may send dummy messages Node may re-route messages Adds to observed traffic Changes observed traffic pattern Node may delay messages Helps obscure message linkage Can smooth out flows
![Traffic Matrix TM has all diagonal entries zero No selftraffic Ti j Traffic Matrix TM has all diagonal entries zero No self-traffic T[i, j] = #](https://slidetodoc.com/presentation_image_h2/6ca549f877e3ad24c98a1ab98f28cbdd/image-10.jpg)
Traffic Matrix TM has all diagonal entries zero No self-traffic T[i, j] = # messages from i to j TM T dominates T’ iff for all i and j T[i, j] >= T’[i, j] Neutral TM – all traffic is uniform All non-diagonal values are equal For all i <> j and i’ <> j’, T[i, j] = T[i’, j’] Unit Neutral TM: all non-diagonal values = 1 Magnitude of Neutral TM is non-zero values in TM

Neutral Traffic Matrix All traffic between all pairs is equal Observer cannot distinguish pairs that are engaged in much interaction from those that are engaged in none What information does Neutral TM give? Only an upper bound on the actual possible traffic But traffic between a pair can exceed observed traffic between the pair, due to rerouting May be overkill

Traffic Matrix Actual TM, Tact End-to-end TM not including any countermeasures No dummy messages No re-routing through intermediaries Observed TM, Tobs End-to-end traffic as observed from addresses Includes dummy traffic Includes changes due to re-routed traffic
![Traffic Matrix Routes flow assignments Actual TM requires Tacti j message be sent from Traffic Matrix Routes, flow assignments Actual TM requires Tact[i, j] message be sent from](https://slidetodoc.com/presentation_image_h2/6ca549f877e3ad24c98a1ab98f28cbdd/image-13.jpg)
Traffic Matrix Routes, flow assignments Actual TM requires Tact[i, j] message be sent from i to j in time period Each message must either be sent directly from node i to node j Or it must follow a longer path from i to j Flow assignment dictates how many message from i to j take each particular route Sk Tact[i, j] = 10 5 5 Tobs[i, j] = 5 10 Si 5 Sj

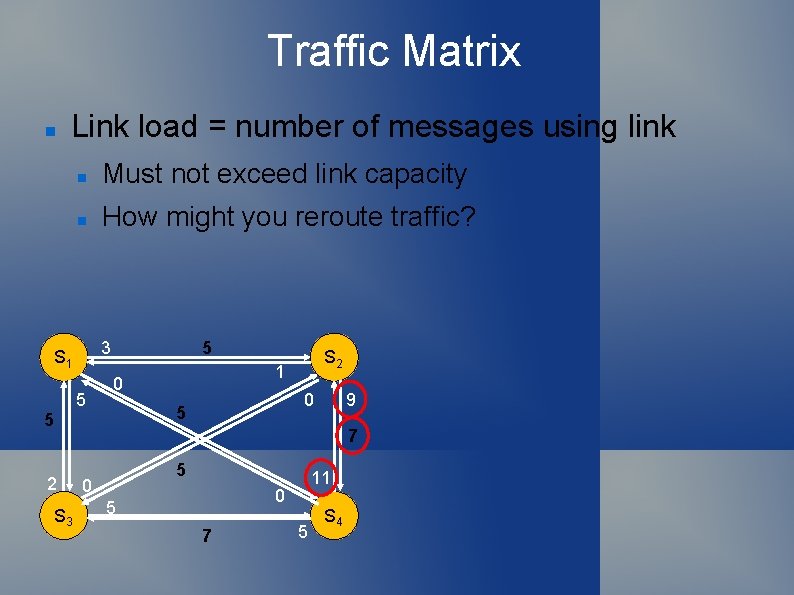
Traffic Matrix Link load = number of messages using link Must not exceed link capacity How might you reroute traffic? 3 S 1 5 5 1 0 0 5 5 S 2 9 7 2 S 3 5 0 11 0 5 7 5 S 4

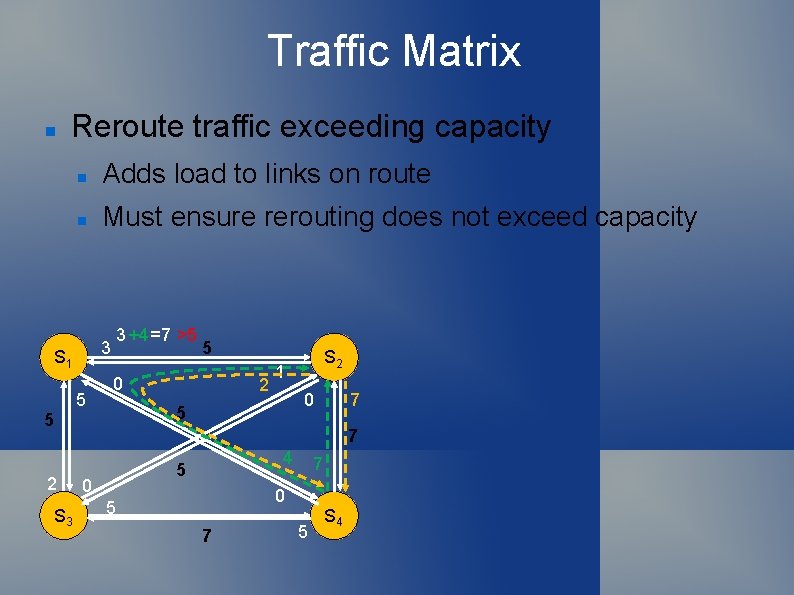
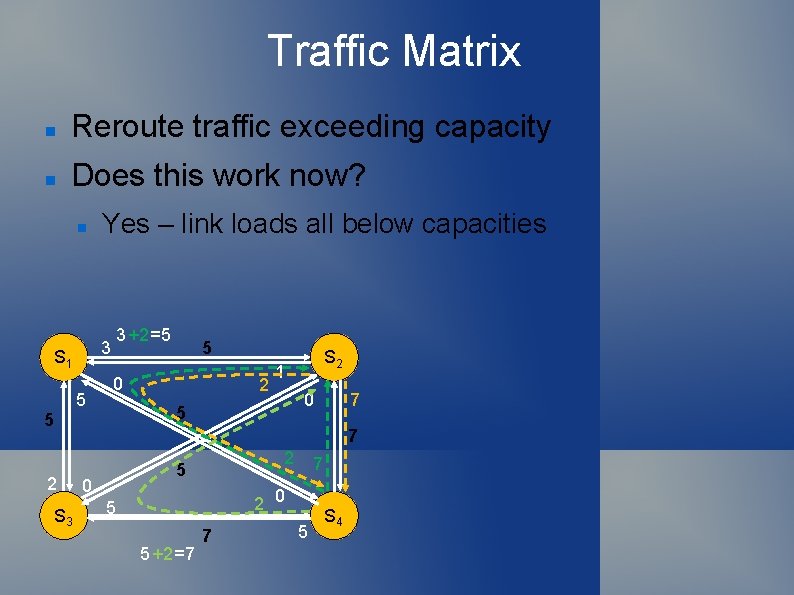
Traffic Matrix Reroute traffic exceeding capacity Adds load to links on route Must ensure rerouting does not exceed capacity 3 S 1 5 3 +4=7 >5 5 0 2 1 0 5 5 S 2 7 7 2 S 3 4 5 0 7 0 5 7 5 S 4

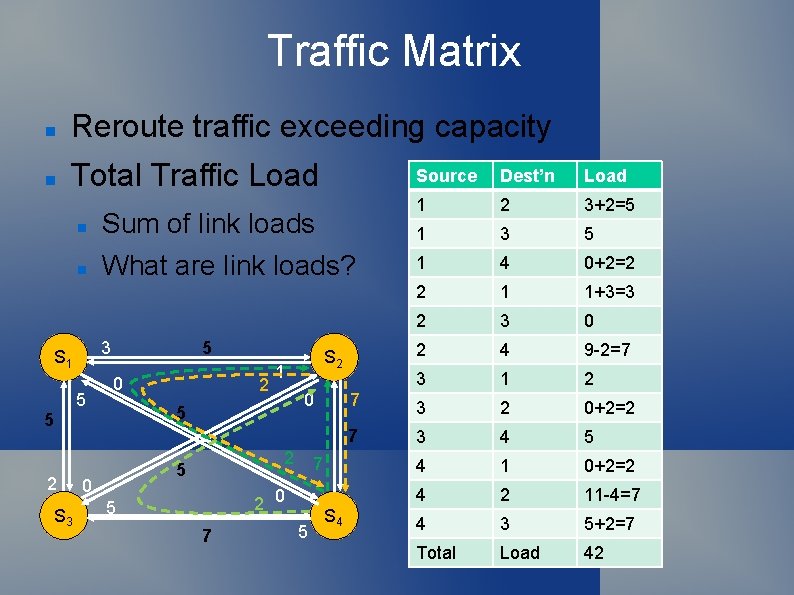
Traffic Matrix Reroute traffic exceeding capacity Does this work now? Yes – link loads all below capacities 3 S 1 5 3 +2=5 5 0 2 1 0 5 5 S 2 7 7 2 S 3 2 5 0 7 2 0 5 5 +2=7 7 5 S 4

Traffic Matrix Reroute traffic exceeding capacity Total Traffic Load 1 2 3+2=5 1 3 5 1 4 0+2=2 2 1 1+3=3 2 3 0 2 4 9 -2=7 3 1 2 7 3 2 0+2=2 7 3 4 5 4 1 0+2=2 4 2 11 -4=7 4 3 5+2=7 Total Load 42 Sum of link loads What are link loads? 3 5 5 0 2 5 0 S 2 1 5 5 S 3 Dest’n S 1 2 Source 7 2 0 5 7 5 S 4

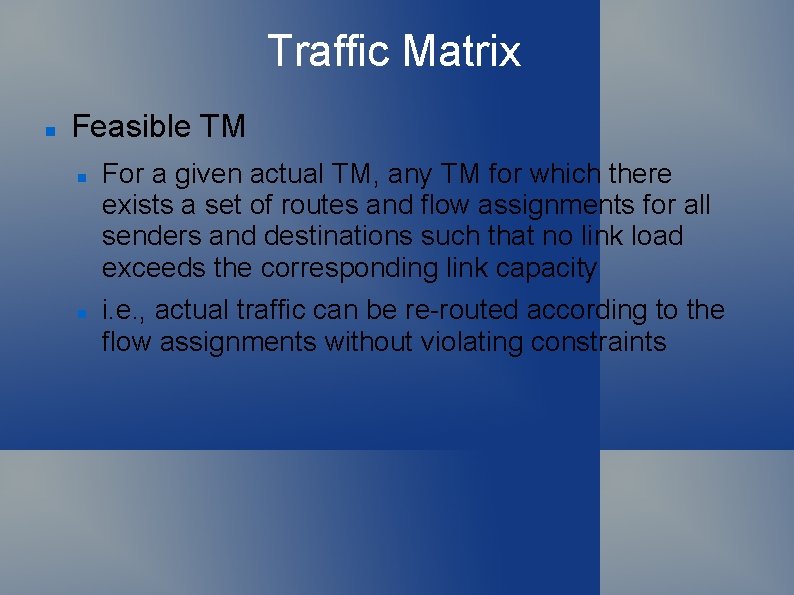
Traffic Matrix Feasible TM For a given actual TM, any TM for which there exists a set of routes and flow assignments for all senders and destinations such that no link load exceeds the corresponding link capacity i. e. , actual traffic can be re-routed according to the flow assignments without violating constraints

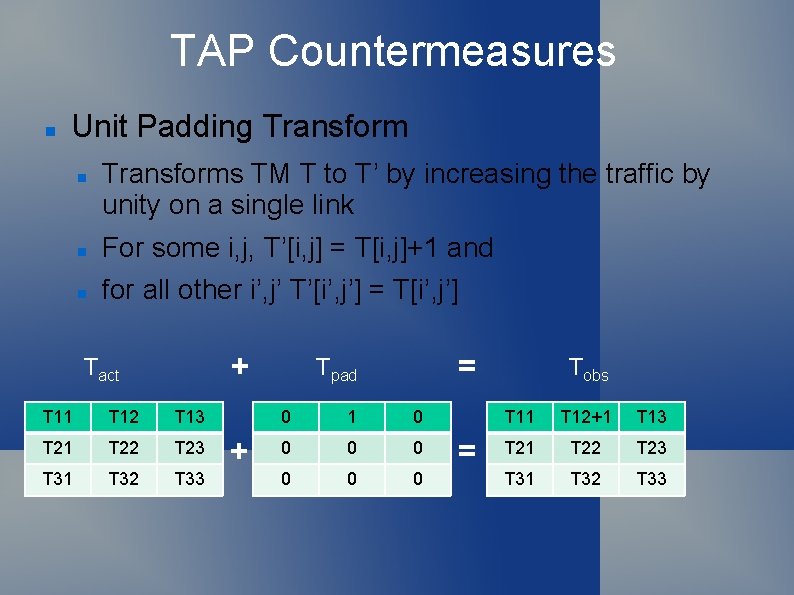
TAP Countermeasures Unit Padding Transforms TM T to T’ by increasing the traffic by unity on a single link For some i, j, T’[i, j] = T[i, j]+1 and for all other i’, j’ T’[i’, j’] = T[i’, j’] + Tact T 11 T 12 T 13 T 21 T 22 T 23 T 31 T 32 T 33 + = Tpad 0 1 0 0 0 0 = Tobs T 11 T 12+1 T 13 T 21 T 22 T 23 T 31 T 32 T 33

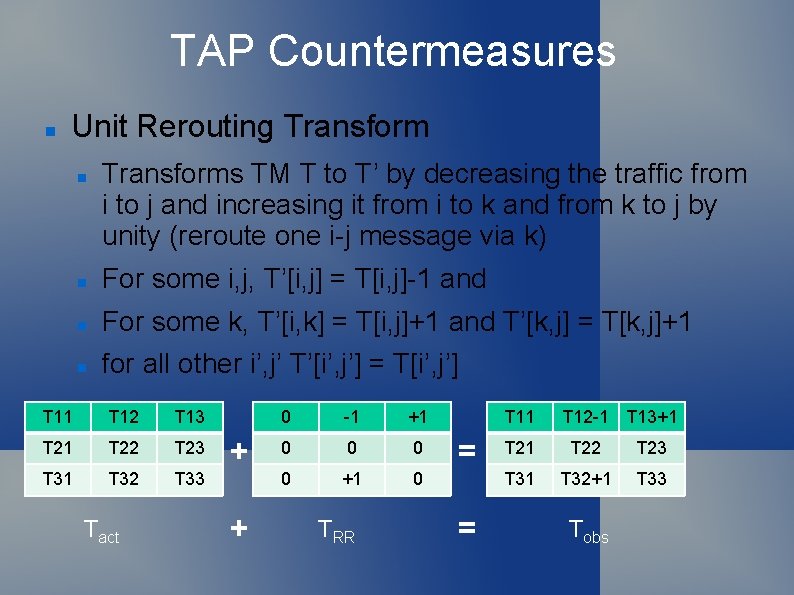
TAP Countermeasures Unit Rerouting Transforms TM T to T’ by decreasing the traffic from i to j and increasing it from i to k and from k to j by unity (reroute one i-j message via k) For some i, j, T’[i, j] = T[i, j]-1 and For some k, T’[i, k] = T[i, j]+1 and T’[k, j] = T[k, j]+1 for all other i’, j’ T’[i’, j’] = T[i’, j’] T 11 T 12 T 13 T 21 T 22 T 23 T 31 T 32 T 33 Tact + + 0 -1 +1 0 0 +1 0 TRR T 11 = = T 12 -1 T 13+1 T 22 T 23 T 31 T 32+1 T 33 Tobs

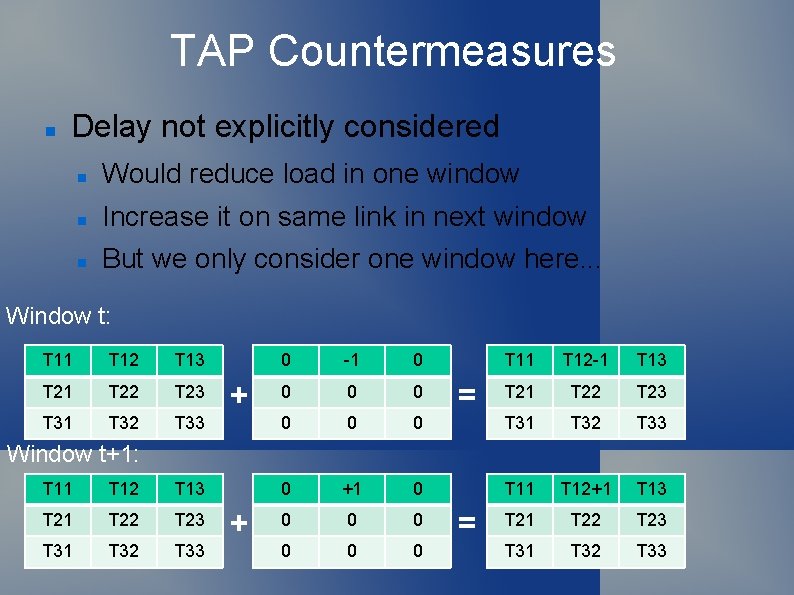
TAP Countermeasures Delay not explicitly considered Would reduce load in one window Increase it on same link in next window But we only consider one window here. . . Window t: T 11 T 12 T 13 0 -1 0 T 21 T 22 T 23 0 0 0 T 31 T 32 T 33 0 0 0 + T 11 T 12 -1 T 13 T 21 T 22 T 23 0 T 31 T 32 T 33 +1 0 T 11 T 12+1 T 13 0 0 0 T 21 T 22 T 23 0 0 0 T 31 T 32 T 33 = Window t+1: T 11 T 12 T 13 T 21 T 22 T 23 T 31 T 32 T 33 + =

Achieving Neutrality Padding Pad matrix is sum of scaled unit pad matrices One unit pad per i, j pair (where i <> j) N(N-1) scaling multipliers Rerouting Reroute matrix is sum of scaled unit reroutes One unit reroute matrix per triple (i, j, k) N(N-1)(N-2) non-zero scaling multipliers

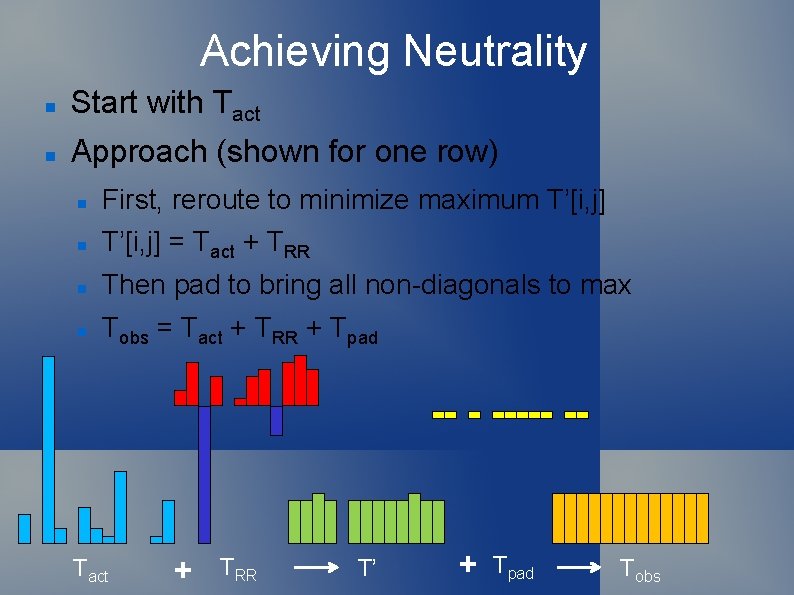
Achieving Neutrality Start with Tact Approach (shown for one row) First, reroute to minimize maximum T’[i, j] = Tact + TRR Then pad to bring all non-diagonals to max Tobs = Tact + TRR + Tpad Tact + TRR T’ + Tpad Tobs

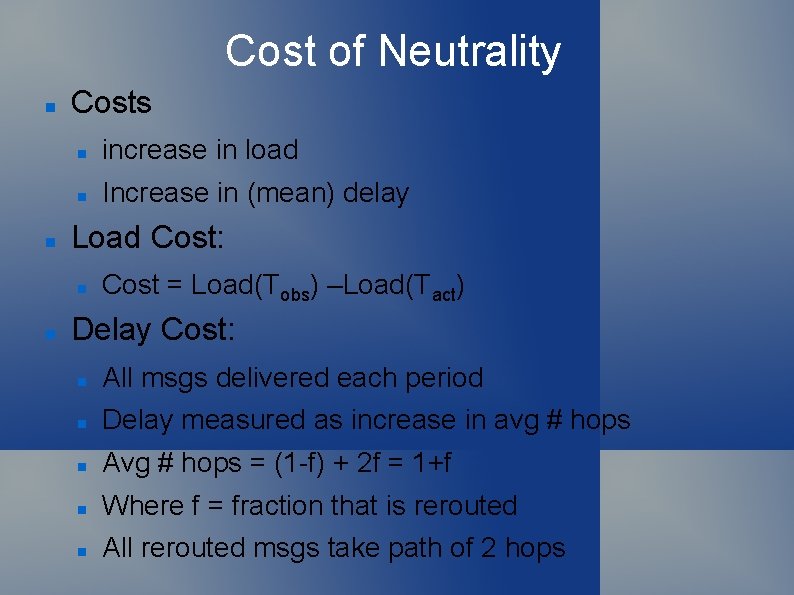
Cost of Neutrality Costs increase in load Increase in (mean) delay Load Cost: Cost = Load(Tobs) –Load(Tact) Delay Cost: All msgs delivered each period Delay measured as increase in avg # hops Avg # hops = (1 -f) + 2 f = 1+f Where f = fraction that is rerouted All rerouted msgs take path of 2 hops

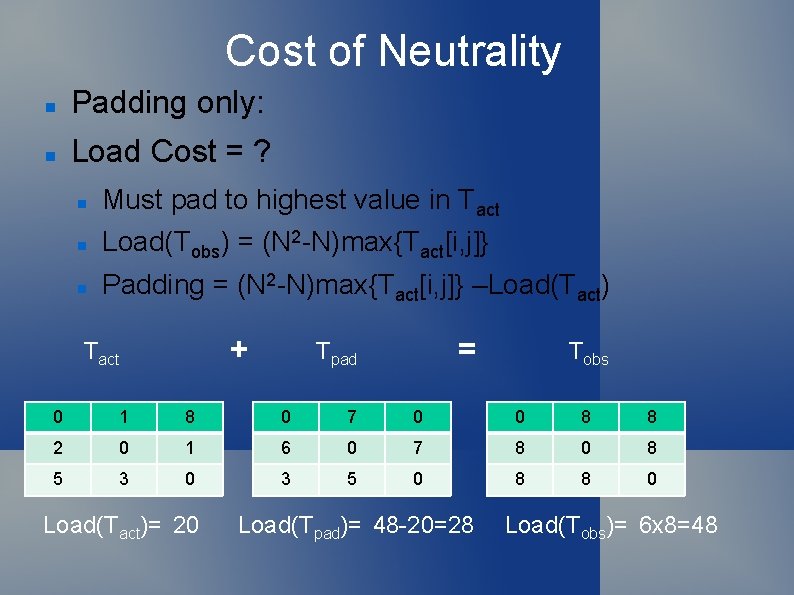
Cost of Neutrality Padding only: Delay cost = ? None (f = 1) Load Cost = ? = Load(Tobs) –Load(Tact) = [Load(Tact)+Padding] –Load(Tact) = Padding i. e, cost = exactly number of dummy messages Which is just the sum of the padding multipliers

Cost of Neutrality Padding only: Load Cost = ? Must pad to highest value in Tact Load(Tobs) = (N 2 -N)max{Tact[i, j]} Padding = (N 2 -N)max{Tact[i, j]} –Load(Tact) + Tact = Tpad Tobs 0 1 8 0 7 0 0 8 8 2 0 1 6 0 7 8 0 8 5 3 0 3 5 0 8 8 0 Load(Tact)= 20 Load(Tpad)= 48 -20=28 Load(Tobs)= 6 x 8=48
![Cost of Neutrality Padding only Load Cost N 2 NmaxTacti j LoadTact In Cost of Neutrality Padding only: Load Cost = (N 2 -N)max{Tact[i, j]} –Load(Tact) In](https://slidetodoc.com/presentation_image_h2/6ca549f877e3ad24c98a1ab98f28cbdd/image-27.jpg)
Cost of Neutrality Padding only: Load Cost = (N 2 -N)max{Tact[i, j]} –Load(Tact) In practice, the distribution of values in Tact is long-tailed, with many 0’s and small numbers This leads to very high costs for padding only Problem gets worse with larger N! Larger proportion of non-communicating pairs

Cost of Neutrality Rerouting only: Let T’ be TM after rerouting T’ may not be neutral (pad later) Delay cost = ? f = ? (average, or per pair) f = (#rerouted msgs)/(#actual msgs) = [Load(T’) – Load(Tact)] / Load(Tact) = Load(TRR) / Load(Tact) Where TRR is reroute matrix T’ = Tact + TRR Load(TRR) = sum of RR scaling multipliers

Cost of Neutrality Rerouting only: Load Cost = ? = Load(T’) – Load(Tact) = [Load(T’)+Load(TRR)] –Load(Tact) = Load(TRR) i. e, cost = exactly number of rerouted messages Which is the sum of the reroute multipliers Approach: Reroute first to minimize variance Then pad to bring up to neutrality

Cost of Neutrality Approach: Reroute first to minimize variance Then pad to bring up to neutrality In practice This approach leads to about a doubling of load How to find TRR that minimizes cost? Want to minimize the maximum value in T’ Turn into a system of linear inequalities

Linearization of Problem ”Flatten” operator Takes a matrix and turns it into a vector Row-major order (or column-major by transpose) f(M) = <M[1, 1], M[1, 2], . . . , M[1, N], M[2, 1], . . . , M[N, N]> f

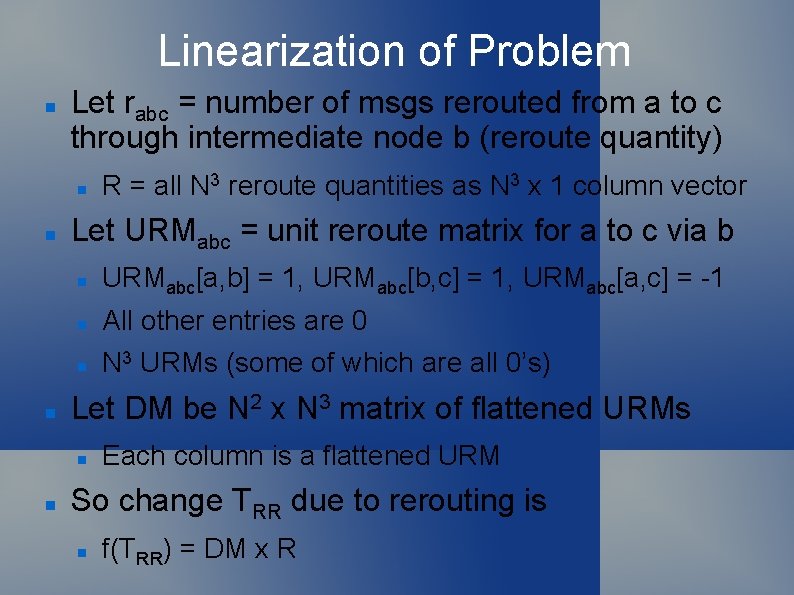
Linearization of Problem Let rabc = number of msgs rerouted from a to c through intermediate node b (reroute quantity) Let URMabc = unit reroute matrix for a to c via b URMabc[a, b] = 1, URMabc[b, c] = 1, URMabc[a, c] = -1 All other entries are 0 N 3 URMs (some of which are all 0’s) Let DM be N 2 x N 3 matrix of flattened URMs R = all N 3 reroute quantities as N 3 x 1 column vector Each column is a flattened URM So change TRR due to rerouting is f(TRR) = DM x R

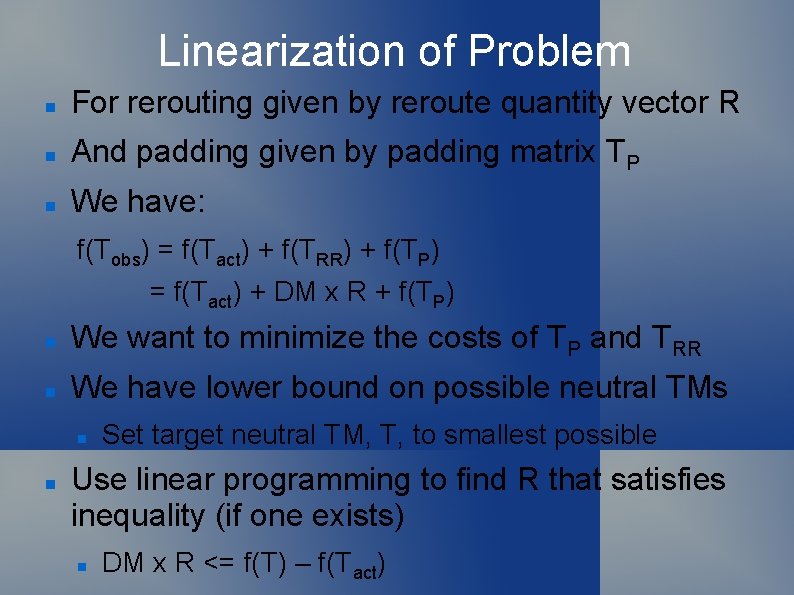
Linearization of Problem For rerouting given by reroute quantity vector R And padding given by padding matrix TP We have: f(Tobs) = f(Tact) + f(TRR) + f(TP) = f(Tact) + DM x R + f(TP) We want to minimize the costs of TP and TRR We have lower bound on possible neutral TMs Set target neutral TM, T, to smallest possible Use linear programming to find R that satisfies inequality (if one exists) DM x R <= f(T) – f(Tact)

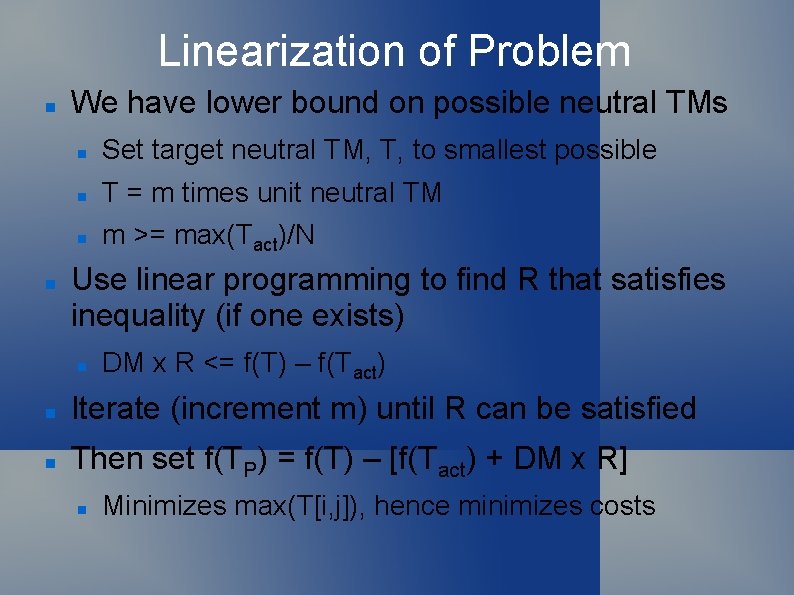
Linearization of Problem We have lower bound on possible neutral TMs Set target neutral TM, T, to smallest possible T = m times unit neutral TM m >= max(Tact)/N Use linear programming to find R that satisfies inequality (if one exists) DM x R <= f(T) – f(Tact) Iterate (increment m) until R can be satisfied Then set f(TP) = f(T) – [f(Tact) + DM x R] Minimizes max(T[i, j]), hence minimizes costs

Network Covert Channels Can treat the information ”leaked” by TMs as covert channel Mix-type packets (only src, dest show, all packets are uniform in size, rest encrypted) How can CC ”sender” convey information? Sender is a single node Sends to ”Eve” – a local eavesdropper Relative traffic volume, absolute volume, order of transmission are still visible How to minimize (or eliminate) CC? Neutral TM eliminates relative volume as signal

Network Covert Channels How to minimize (or eliminate) CC? Neutral TM eliminates relative volume as signal Every node always sends indistinguishable packet to every other node every ”round” Each node always sends to destinations in same order Only signal is change in round time intervals But how to determine reroute quantities? Not practical for all nodes to exchange traffic levels Want a local decision

Network Covert Channels Message Sending Policy Maintain Tx queues for each destination High priority = from other node Medium priority = from this node Low priority = dummy packet (generated) Send packet every period Message arrival policies If dummy from other node, discard If rerouted from other node, put into High queue If local origin, reroute if dest Med queue occupied Traffic volume changes

Network Covert Channels Traffic volume changes Negotiate shorter period length if queues stay full Negotiate longer period length if queues mostly empty All nodes must arrive at consensus Single node must dramatically change traffic to force change in period This can be audited Mode-based security Don’t allow arbitrary period changes Only allow particular modes – reduces CC capacity Only allow change at end of cycle – lower CC

Network Covert Channels Mode-based security Don’t allow arbitrary period changes Only allow particular modes M modes define allowed period durations Only allow change at end of cycle Cycle is duration spanning one or more periods Capacity is now lg(M)/Tcycle Maximum capacity is known Attempts to exercise CC can be audited

Generalizations Given an observed TM, there are limits on possible actual TMs The sum of the traffic coming into a node j in Tact cannot exceed the sum of the traffic coming in to node j in Tobs. The sum of the traffic coming out of a node i in Tact cannot exceed the sum of the traffic coming out of node i in Tobs. Although the graphs considered are cliques, the total traffic from node i to node j may exceed the capacity of the (direct) link from i to j due to some traffic being routed through other nodes

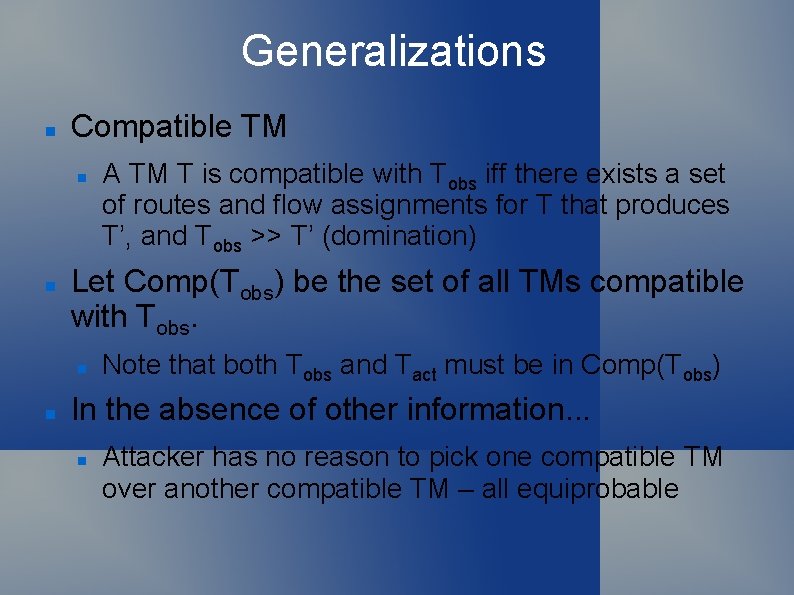
Generalizations Compatible TM Let Comp(Tobs) be the set of all TMs compatible with Tobs. A TM T is compatible with Tobs iff there exists a set of routes and flow assignments for T that produces T’, and Tobs >> T’ (domination) Note that both Tobs and Tact must be in Comp(Tobs) In the absence of other information. . . Attacker has no reason to pick one compatible TM over another compatible TM – all equiprobable

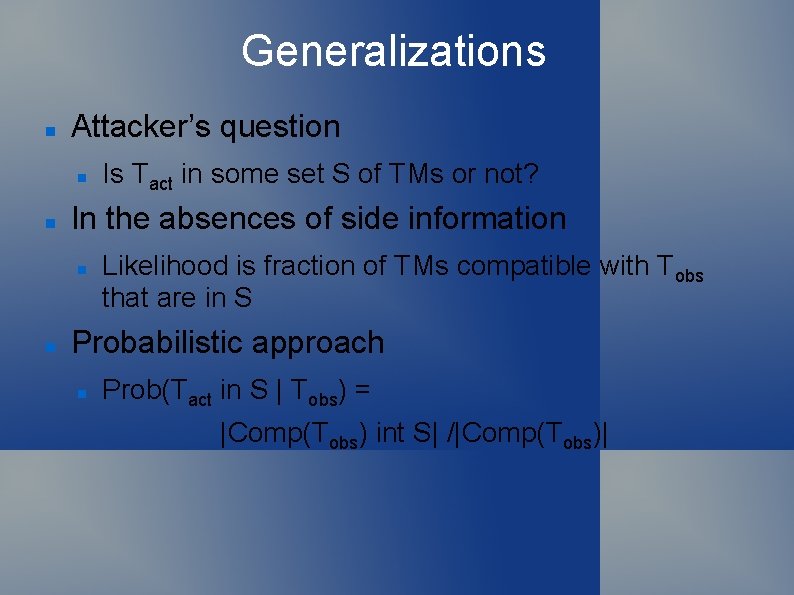
Generalizations Attacker’s question In the absences of side information Is Tact in some set S of TMs or not? Likelihood is fraction of TMs compatible with Tobs that are in S Probabilistic approach Prob(Tact in S | Tobs) = |Comp(Tobs) int S| /|Comp(Tobs)|

Summary Neutral TM Approach Aims to give nothing to GPA except upper bounds All traffic is equal Can decide reroute and pad quantities from actual traffic and desired TM Can minimize costs associated with achieving neutrality May be overkill Probabilistic TM approach Maximize uncertainty of actual TM Large number of compatible TMs with various properties

Summary Anonymity Metrics Anonymity Set Plausible Deniability Crowds approach Probability of ”guessing right” Consistent TM Set size Per message receiver and/or sender Possibilistic Subsets corresponding to property of interest can lead to probability approach also Covert Channel approach Capacity of channel = info leak rate
 Definig clause
Definig clause Relative clauses defining and non defining
Relative clauses defining and non defining Defining non defining relative clauses
Defining non defining relative clauses Defining relative clause meaning in telugu
Defining relative clause meaning in telugu Defining non defining farkı
Defining non defining farkı Defining and non defining relative clause
Defining and non defining relative clause Effrontery definition the crucible
Effrontery definition the crucible Blender torrent
Blender torrent K anonymity
K anonymity K anonymity
K anonymity Stanley mark rifkin
Stanley mark rifkin K anonymity
K anonymity Is unknown an adjective
Is unknown an adjective Inbound traffic vs outbound traffic
Inbound traffic vs outbound traffic All traffic solutions
All traffic solutions Approaches to measuring performance
Approaches to measuring performance Defining performance and choosing a measurement approach
Defining performance and choosing a measurement approach Traffic light matrix
Traffic light matrix Decalin newman projection
Decalin newman projection Persona trabajando en fabrica
Persona trabajando en fabrica Newman projection practice
Newman projection practice What shapes internal structure
What shapes internal structure Margaret newman theory in practice
Margaret newman theory in practice Francis drake halls
Francis drake halls Hsc geography notes
Hsc geography notes Gauche interaction
Gauche interaction Cardinal newman cedar
Cardinal newman cedar Batasan perencanaan
Batasan perencanaan Gerald levey and mark newman
Gerald levey and mark newman Newman projection generator
Newman projection generator Barnett newman abraham
Barnett newman abraham Robert c newman ii
Robert c newman ii Colgajo de widman modificado dibujo
Colgajo de widman modificado dibujo Conformazione sfalsata butano
Conformazione sfalsata butano Gerald levey and mark newman
Gerald levey and mark newman Gerald levey and mark newman
Gerald levey and mark newman Alcanos formula desarrollada
Alcanos formula desarrollada Carrot dude
Carrot dude Plastic bag theme american beauty
Plastic bag theme american beauty Barnett newman vir heroicus sublimis
Barnett newman vir heroicus sublimis One and three chairs
One and three chairs Newman college
Newman college Robert c newman ii
Robert c newman ii Girvan newman algorithm
Girvan newman algorithm Cognitive apprenticeship collins brown and newman
Cognitive apprenticeship collins brown and newman