Attacks on Mixes R Newman Topics Defining anonymity

























- Slides: 36

Attacks on Mixes R. Newman

Topics Defining anonymity Need for anonymity Defining privacy Threats to anonymity and privacy Mechanisms to provide anonymity Metrics for Anonymity Applications of anonymity technology

Attackers Passive Attacker Local – only detect traffic to/from one node Global – detect all messages Still, can only see src and dest (assume lengths all same, contents disguised) Active Attacker Delay Destroy Modify Replay Fabricate

Attackers Active Attacker – targetting a specific msg Trickle Attack Inject attacker messages Blending Attacks Delay or drop most msgs (timed Mix) Flood Attack Can manipulate batch of msgs entering Mix Trickle or flood Aim: Only one unknown message in batch

Attackers GAAs Can treat as two separate, cooperating attackers Global Inserting Attacker Global delaying Attacker GIA Can insert any number of messages anywhere Can do this in constant time Models unauthenticated systems (what else? ) GDA Treat deleting message as infinite delay

N-1 Attack Threshold Mix Threshold = N Inject N-1 messages into batch Only the one message under attack is unknown Know where the N-1 go See where the other one goes Repeat at each Mix until true destination known

Attack Classes Exact Attacker knows destination exactly Attacker knows when attack succeeds Anonymity is 0 Certain Attack always has the power to do this Attack always works in finite time

Mix Classes By resistance to Blending Attacks Strongly Resistant No blending attack can reduce anonymity of any message at all Blending attack anonymity k No blending attack can reduce the anonymity of any message below a constant k (AS size)

Mix Classes By resistance to Blending Attacks Vulnerable to non-exact, uncertain BAs Vulnerable to exact, uncertain BAs GAA can always reduce anonymity, but never to zero GAA can always reduce anonymity to 0, but may need to spend arbitrary resources (msges, time) Vulnerable to exact, certain BAs GAA can always reduce anonymity to 0, with finite resources (msges, time)

Mix Classes By resistance to Blending Attacks Note that the list may not be in order of increasing vulnerability in a practical sense Resources matter!

Threshold Mix Fires when N messages arrive Min delay is epsilon, max is infinite Mean delay is N/2 r, where r = arrival rate Min anonymity set size is N Distinct senders, distinct receivers

Threshold Mix Fires when N messages arrive Blending attack behavior Susceptible to flooding attack Min msgs is N-1, max is 2 N-2 Does not require delay

Threshold Mix Fires when N messages arrive Blending attack behavior Susceptible to flooding attack Min msgs is N-1, max is 2 N-2 Does not require delay Mix with N=5 target Mix 1 good good Can allow other good messages to arrive, or send bad messages to flush Mix 2

Threshold Mix Fires when N messages arrive Blending attack behavior Susceptible to flooding attack Min msgs is N-1, max is 2 N-2 Does not require delay good target Delay the new good messages Mix 1 bad bad Send bad messages to flush mix Mix 2

Threshold Mix Fires when N messages arrive Blending attack behavior Susceptible to flooding attack Min msgs is N-1, max is 2 N-2 Does not require delay good Mix 1 target bad bad Watch where other message goes Know where bad messages are going Mix 2

Timed Mix Fires every T seconds Min delay is epsilon e, max is T-e Mean delay is T/2 Min anonymity set size is 0, max is infinite In theory. . . In practice, limited by rate and memory Distinct senders, distinct receivers Mean AS size is r. T, where r is arrival rate

Timed Mix Fires every T seconds Blending attack behavior Susceptible to exact, certain attack Trickle Delay target message until Mix fires Delay all but target message Takes max time of 2 T-e, min of e Does not require insertions Can happen naturally in low traffic conditions!

Threshold OR Timed Mix Fires every T seconds or when N msgs arrive Min delay is epsilon e, max is T-e Mean delay is T/2 Min anonymity set size is 0, max is N Mean AS size is. . . min(N, r. T), where r is arrival rate

Threshold OR Timed Mix Fires every T seconds or when N msgs arrive Blending attack behavior Worst of both worlds!!! Susceptible to exact, certain attack Trickle or Flood! Min of 0 insertions with max time of 2 T-e, min of e Max of 2(N-1) insertions in e seconds

Threshold AND Timed Mix Waits for at least T seconds and N msgs Min delay is epsilon e, max is infinite Mean delay is T/2 Min anonymity set size is N, max is infinite Mean AS size is. . . max(N, r. T), where r is arrival rate

Threshold AND Timed Mix Waits for at least T seconds and N msgs Blending attack behavior Combined blending attack is exact and certain Trickle and Flood! Must delay non-target messages Must insert dummy messages Max time of 2 T-e, min of e Max of 2(N-1) insertions and min of N-1 insertions

Pool Mixes Maintains a pool of F messages Initializes pool With dummy messages or. . . Waits for F initial messages before normal ops May be timed, threshold, or combination Make attacks uncertain, increase cost

Threshold Pool Mix Fires when N new messages arrive Sends uniform random selection of N, keeps F Min delay is epsilon, max is infinite Infinite even if Mix fires infinitely many times! Mean delay is 1 + F/(N+F) rounds Mean round rate is N/r where r is arrival rate Mean delay is (N/r)(1 + F/(N+F)) Anonymity set size – must resort to info theory Amax = -(1 -F/N) lg (N+F) + (F/N) lg F Min AS size is N (assumes distinct senders)

Threshold Pool Mix Blending attack behavior Generally have two phases: Flush good messages out of Mix Insert bad messages into Mix Problem: Can never be sure good message is flushed! Attack becomes uncertain! Is still exact (attacker knows when Mix is clean)

Threshold Pool Mix Blending attack behavior Exact but uncertain Prob(msg still in Mix after r rounds) = [F/(N+F)]r If there were G good messages in Mix at start, Exp(# good msgs in Mix) = G [F/(N+F)]r Prob(all good messages have left Mix by round r) = [1 – (F/(N+F))r ]M M ranges between F and N+F

Threshold Pool Mix Blending attack behavior Prob(all good messages have left Mix by round r) = [1 – (F/(N+F))r ]M Example: N = 100, F = 60 Average delay = 1. 6 rounds If M = 60 (i. e. , Mix just fired) Expected number of good messages in Mix is < 1 after 5 rounds, or 500 attacker messages Prob(all M gone) > 0. 5 after 5 rounds, and Prob(all M gond) > 0. 99 after 9 rounds

Timed Pool Mix Fires every T seconds Always retains F messages in pool If <= F in pool, it does not fire (hence Threshold AND Timed mix, technically) Min delay is epsilon e, max is infinity Min anonymity set size is F+1, max is infinite Compute effective A similar to Threshold Pool Mix

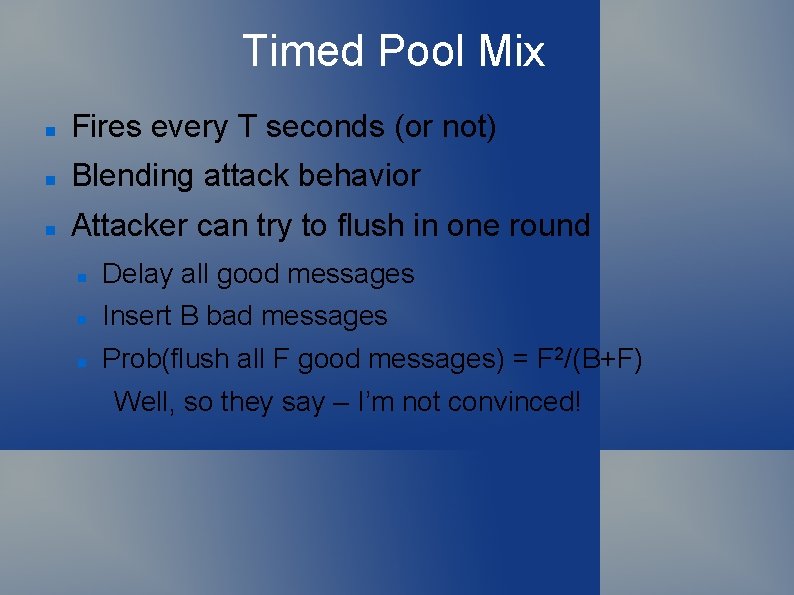
Timed Pool Mix Fires every T seconds (or not) Blending attack behavior Attacker can try to flush in one round Delay all good messages Insert B bad messages Prob(flush all F good messages) = F 2/(B+F) Well, so they say – I’m not convinced!

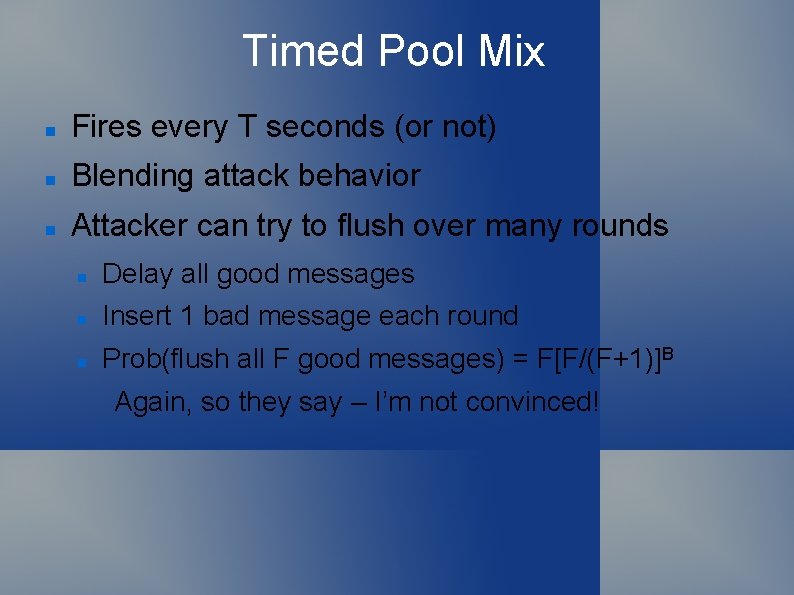
Timed Pool Mix Fires every T seconds (or not) Blending attack behavior Attacker can try to flush over many rounds Delay all good messages Insert 1 bad message each round Prob(flush all F good messages) = F[F/(F+1)]B Again, so they say – I’m not convinced!

Dynamic Timed Mix Fires every T seconds with threshold N Min pool size Fmin, f = fraction of msgs to send Must have at least N + Fmin msgs to fire Sends max(1, mf) messages If N=1, this is Cottrell Mix m = number of messages in Mix when firing Used in Mixmaster remailer Size of pool may change over time If constant arrival rate then equivalent to constant pool mix

Dynamic Timed Mix Message delay: Min is e, max is infinite Mean delay depends on future arrival rates At least as high as constant-pool mix, usually higher Anonymity Same properties as constant pool mix Anonymity higher since prob(stay in pool) is constant, rather than decreasing with increasing m

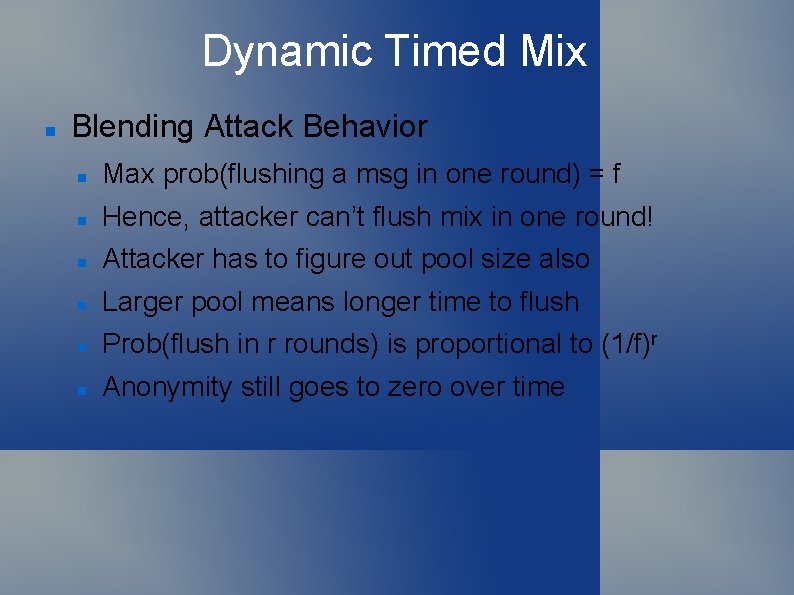
Dynamic Timed Mix Blending Attack Behavior Max prob(flushing a msg in one round) = f Hence, attacker can’t flush mix in one round! Attacker has to figure out pool size also Larger pool means longer time to flush Prob(flush in r rounds) is proportional to (1/f)r Anonymity still goes to zero over time

Resisting Exact Attacks All prior mixes subject to exact attacks Attacker knows when good messages are flushed Some provide uncertainty – don’t know how long it will take Binomial Mix Flush each message with some probability Hard to determine size of pool now Target specific goals: Certainty Exactness

Resisting Exact Attacks Use same tools as attacker Uncertainty Don’t let attacker know when target msg leaves pool Use dummy messages Intermix link encryption – hard to recognize chaff Intermix detours – reroute outgoing messages Stop-and-Go Mixes Inexactness Don’t let attacker know size of current pool Dynamic pool fractional approach Binomial approach

Resisting Exact Attacks Stop-and-Go (SG) Mixes Estimate arrival time of good msg at each Mix If msg is outside of window, discard it Frustrates arbitrary delay attacks But seems attacker can still manipulate system Reputation systems Prevent or diminish insertion attacks Only known senders can participate Seems hard to be both known and anonymous!

Next Up Defining anonymity Need for anonymity Defining privacy Threats to anonymity and privacy Mechanisms to provide anonymity Metrics for Anonymity Applications of anonymity technology Voting Ecash