Freenet Anonymity v Napster anonymity Gnutella Kazaa do











- Slides: 21

Freenet

Anonymity v Napster, anonymity Gnutella, Kazaa do not provide v. Users know who they are downloading from v. Others know who sent a query v Freenet v. Designed to provide anonymity among other features

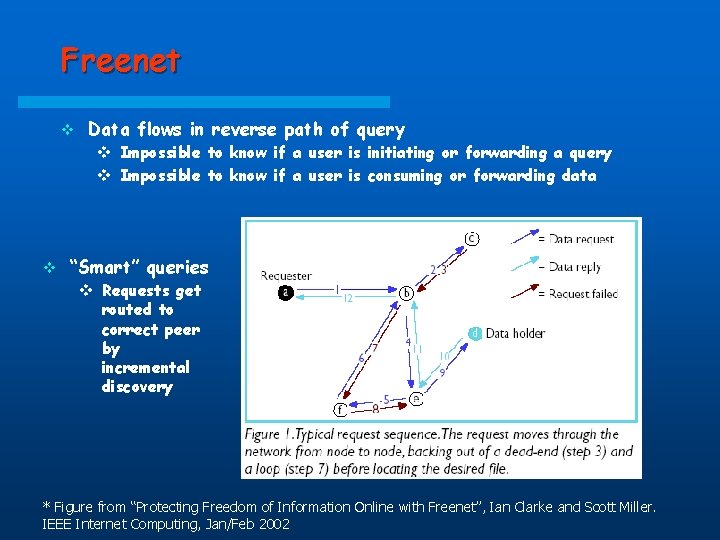
Freenet v Data flows in reverse path of query v Impossible to know if a user is initiating or forwarding a query v Impossible to know if a user is consuming or forwarding data v “Smart” queries v Requests get routed to correct peer by incremental discovery * Figure from “Protecting Freedom of Information Online with Freenet”, Ian Clarke and Scott Miller. IEEE Internet Computing, Jan/Feb 2002

Freenet Peer-to-peer indexing and searching service v Peer-to-peer file downloading v Files served use the same route as searches (not point-to-point) v v Provides for anonymity

Freenet Completely anonymous, for producers or consumers of information v Resistance to attempts by third parties to deny access to information v Goals: v v Anonymity for producers and consumers v Deniability for information storers v Resistance to denial attacks v Efficient storing and routing v Does NOT provide v Permanent file storage v Load balancing

Freenet Somewhat similar to Gnutella but… v As file passes through ‘vine-like’ framework, the file makes a copy of itself at each point along its route v Implemented encryption to hid the originating point of the file v Vision of open source project is to allow all information, copyrighted or not, to be distributed anonymously and untraceable in a p 2 p network v http: //www. freenet. org

Freenet history Final Year project Ian Clarke , Edinburgh University, Scotland, June, 1999 v Sourceforge Project, most active v V. 0. 1 (released March 2000) v Latest version(Sept, 2001): 0. 4 v

What is Freenet and Why? Distributed, Peer to Peer, file sharing system v Completely anonymous, for producers or consumers of information v Resistance to attempts by third parties to deny access to information v

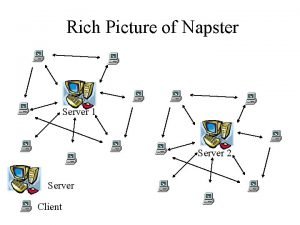
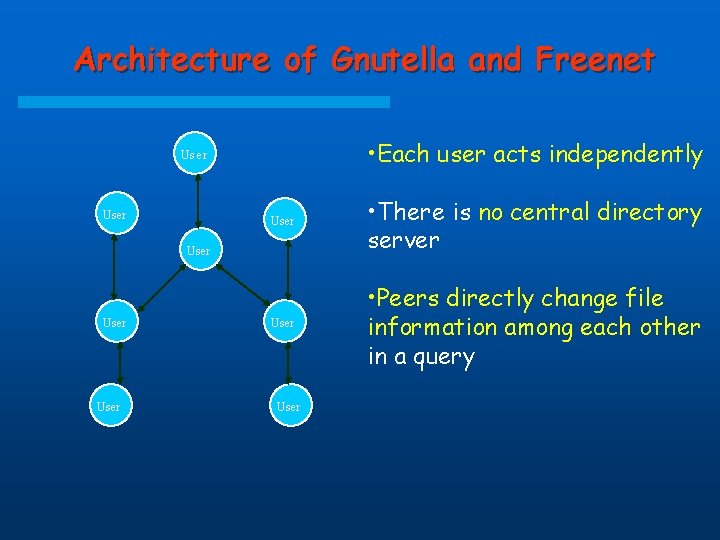
Architecture of Gnutella and Freenet • Each user acts independently Us er User • There is no central directory server User • Peers directly change file information among each other in a query User

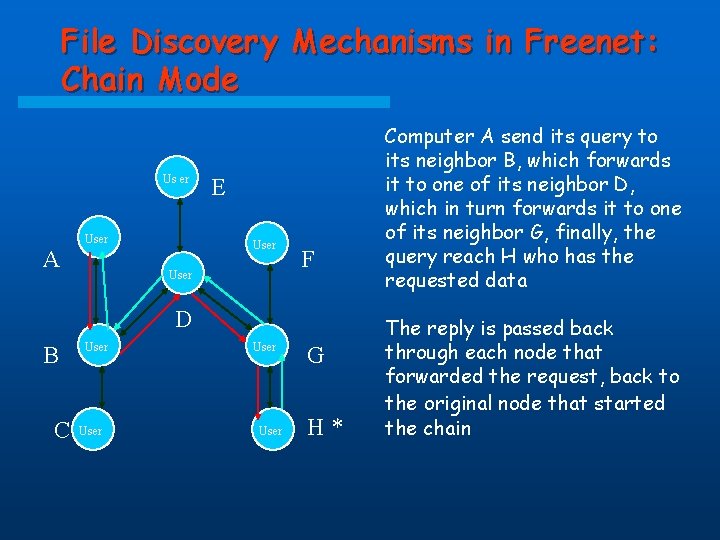
File Discovery Mechanisms in Freenet: Chain Mode A request for a file can be forwarded through many different nodes. v If a node does not have the document that the requestor is looking for, it forwards the request to one of its neighbor that is more likely to have the document v v The messages form a chain as each node forwards the request to the next node Message times out after passing through a certain number of nodes, so that huge chains don’t form. v The chain ends when the message times out or when a node replies with the data. v

File Discovery Mechanisms in Freenet: Chain Mode Us er A User E User F D B C User G H* Computer A send its query to its neighbor B, which forwards it to one of its neighbor D, which in turn forwards it to one of its neighbor G, finally, the query reach H who has the requested data The reply is passed back through each node that forwarded the request, back to the original node that started the chain

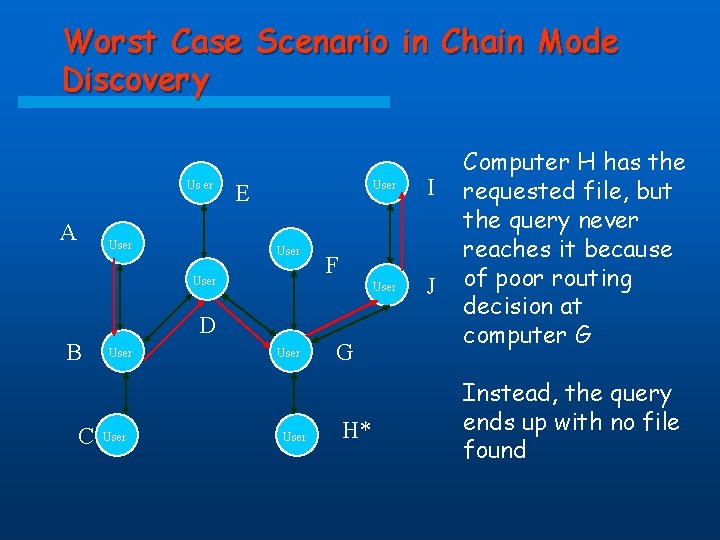
Advantages and Disadvantages of Chain Mode in Searching v Advantages: v Fast discovery with less network traffic in average case v Search stops once the requested file is found v More scalable v Disadvantages: v Slow discovery in worst case

Worst Case Scenario in Chain Mode Discovery Us er A User E User C User I User J F D B User G H* Computer H has the requested file, but the query never reaches it because of poor routing decision at computer G Instead, the query ends up with no file found

Freenet v It aims: v To allow people to distribute material anonymously. v To allow people to retrieve material anonymously. v To make the removal of material almost insuperably difficult. v To operate without central control.

operation of freenet v Searches are only passed to one other servent, which pass it on. After no positive response from that chain, another servent is tried. v But the entire document sought is passed along, unless it is too large v Servents keep caches of popular documents until no one asks for it for a long time. v popular documents frequent and close to users.

searching on freenet You basically can not search on freenet. v Each document has an identifier v v The identifier and the document can not be changed. v This will make it difficult to use it on its own as a device for people to exchange copyrighted material.

Some security and authentication issues v How to ensure anonymity: v Nodes can lie randomly about the requests and claim to be the origin or the destination of a request v Hop-To-Live values are fuzzy v Then it’s impossible to trace back a document to its original node v Similarly, it’s impossible to discover which node inserted a given document.

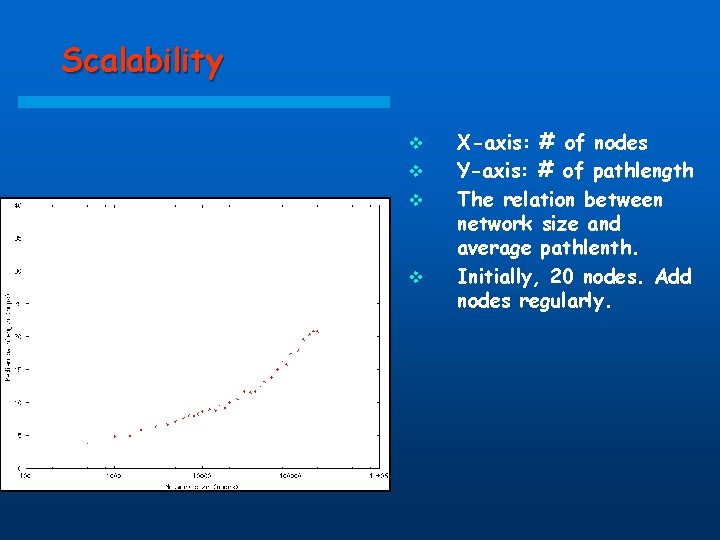
Scalability v v X-axis: # of nodes Y-axis: # of pathlength The relation between network size and average pathlenth. Initially, 20 nodes. Add nodes regularly.

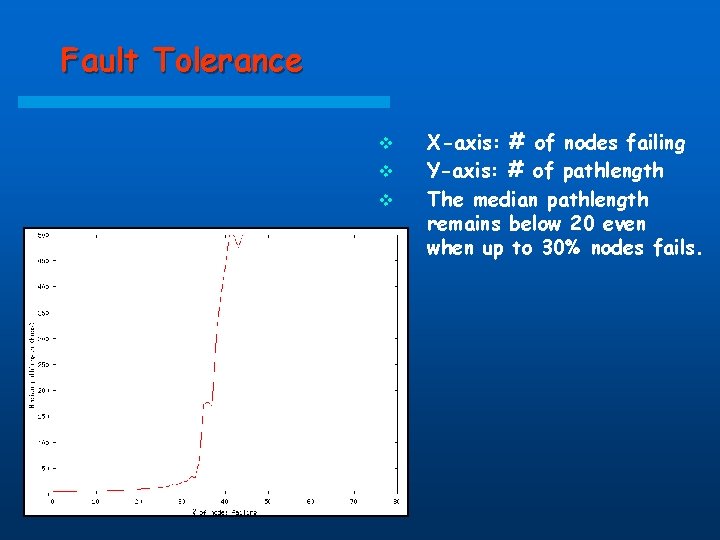
Fault Tolerance v v v X-axis: # of nodes failing Y-axis: # of pathlength The median pathlength remains below 20 even when up to 30% nodes fails.

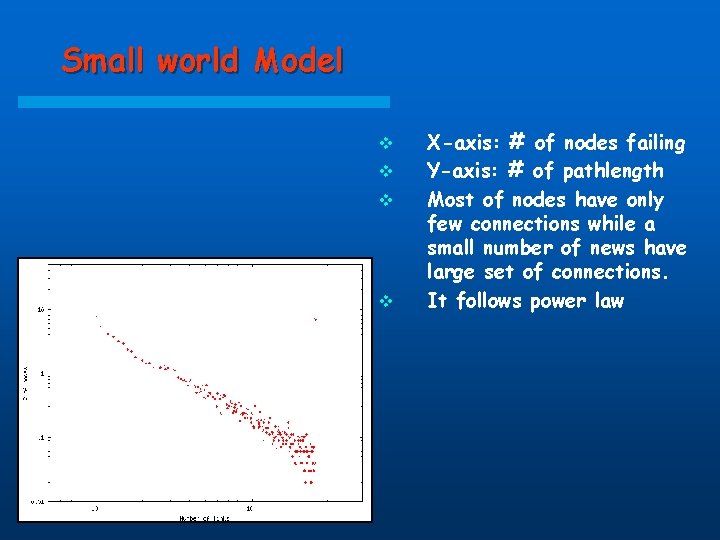
Small world Model v v X-axis: # of nodes failing Y-axis: # of pathlength Most of nodes have only few connections while a small number of news have large set of connections. It follows power law

Is it Perfect? v How long will it take to search or insert? v v v Trade off between anonymity and searching efforts: Chord vs Freenet Have no idea about if search fails due to no such document or just didn’t find it. File lifetime v Freenet doesn’t guarantee a document you submit today will exist tomorrow
 Napster and gnutella
Napster and gnutella Ian clarke freenet
Ian clarke freenet Freenet liberec
Freenet liberec Freenet jahreshauptversammlung
Freenet jahreshauptversammlung Gnutella clients
Gnutella clients What is gnutella
What is gnutella Futella
Futella Gnutella 2
Gnutella 2 A&m records v napster
A&m records v napster Napster protocol
Napster protocol Limewire history
Limewire history Napster in distributed system
Napster in distributed system Riaa vs napster
Riaa vs napster K anonymity
K anonymity K anonymity
K anonymity Anonymous adjective
Anonymous adjective Ingratiating definition the crucible
Ingratiating definition the crucible L diversity
L diversity Bitblender
Bitblender Stanley mark rifkin
Stanley mark rifkin