Todays Quiz 1 The most popular social networking














































- Slides: 50

Today’s Quiz 1. The most popular social networking site among young people is Twitter. 2. Nothing is private once it is posted on the Internet. 3. Teens should share passwords with their best friends in case they forget them. 4. About half of teens text around 60 messages a day, or 1, 800 messages a month. 5. It’s ok to write embarrassing things about someone on the Internet if it’s just a joke.

What is the Internet? The large network of millions of computers around the world that are connected to each other through smaller networks. It is a very public place!

The Nature of the Internet Once something is posted on the Internet, it is no longer private.

Once something is posted on the Internet: you cannot get it back, you lose control over where it goes, you lose control over who sees it, and whatever you post is permanent.

Who’s Looking? • Parents • Principal, Teachers, Coaches • Colleges and Universities • Future employers • Friends (Friends of Friends? ) • Strangers (Everyone? )

Strangers Online Not everyone on the Internet is who they say they are!

Predators go through social networking sites and chat rooms like catalogs, looking for information and photos that children and teens post.

Predators • Are both genders, but mostly males • All ages (recently - from 31 to 77) • All races • All levels of income • All professions (Attorney, Time Warner employee, BMW executive, Lowe’s employee, former military, psychiatrist)

The Predator Isolates victim from family and friends. Promises victim money, clothes, etc. Wants victim to keep everything a secret. Wants victim to meet them offline.

Can you be certain?


Let a trusted adult know if anyone you first met on the Internet asks you to meet them in real life.

Risky Online Behaviors

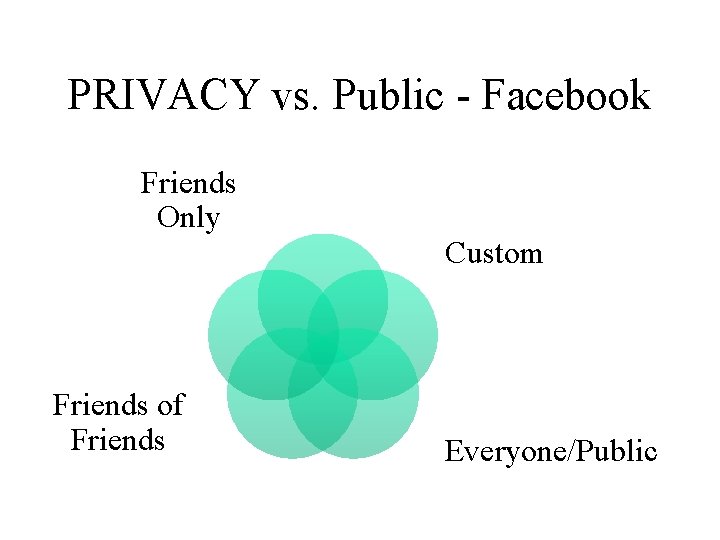
Private vs. Public Most sites are on PUBLIC settings by default.

PRIVACY vs. Public - Facebook Friends Only Friends of Friends Custom Everyone/Public




Posting personal information online such as full name, age, address, school, etc.

Identity Theft

Phishing Definition: Theft of sensitive personal information. (credit card numbers, bank account information, SSN, passwords, etc. ) • UPDATE • VALIDATE • CONFIRM Federal Trade Commission




Steps to Avoid Getting Phished: 1. Don’t reply to email or pop-up messages that ask for personal or financial information. 2. Don’t email personal or financial information. 3. Review credit card and bank account statements as soon as you receive them. 4. Be cautious about opening attachments or downloading files from emails you receive. 5. Never provide passwords over the phone or in response to an unsolicited Internet request. Federal Trade Commission, Federal Deposit Insurance Corporation

Sharing passwords with friends.

Accepting anyone and everyone as “friends. ”

Agreeing to meet in real life Agreeing to meet with someone with s(he) meets on the Internet. someone you first met on the Internet.

TEXTING AND DRIVING

Texting and Driving City of Columbia has banned texting while driving. Fine: $100 (up to $237 with fees) Police are on board: “The distractions are so apparent, almost to the extent of being a DUI, ” Chief Randy Scott said in late March.


Sexting

Sexting Youth taking nude or semi-nude photos of themselves or their peers, and sending the photos to their friends, usually by cell phones.

Photos sent by cell phones: Leave your control the second you send them. Can be copied and sent to anyone and everyone. You cannot get them back.

The Good News! The majority of teens DO NOT participate in sexting. If you choose not to participate, you are not alone!

The Bad News If you choose to participate in sexting, you can be charged with: Unlawful Communication (Use of a telephone or electronic means) or Sexual Exploitation of a Minor (Child Pornography)

A Shadow Resume s Job s r e y o l p m E Colleg es and Univer sities What type of reputation is represented by your online messages and photos?

Cyberbullying (Digital Abuse)

Definition: When the internet is used to intentionally and repeatedly hurt, embarrass, threaten or humiliate another person.

Roles Involved In Cyberbullying • Cyberbully • Victim • Bystander • Upstander

Cyberbullying can be: • Threats of doing some type of harm • Mean, negative comments • Spreading gossip, rumors • A fake profile of another person • Embarrassing photos spread online • Online polls, surveys

Cyberbullies Feel that they are anonymous. Will say things online that they wouldn’t say face to face. Want others to pile on. Victims Feel frustrated, isolated, depressed. Some commit suicide.


Tips for Handling Cyberbullying

First, try to ignore the messages. Don’t respond or retaliate. Save evidence such as emails, text messages, pictures, etc. from the cyberbully. Delete your account. Report it!

The Good News! The majority of teens DO NOT participate in Cyberbullying! If you choose not to participate, you are not alone.

The Bad News In S. C. , persons who are cyberbullies can be charged with Harassment or Stalking.


Where are you? Your friends? + _

R r e b m e e s the : s rd o w 4 THINK BEFORE YOU POST!
 Sdn vs traditional network
Sdn vs traditional network Drupal modules for social networking
Drupal modules for social networking Types of social networking sites
Types of social networking sites Social networking advantage and disadvantage
Social networking advantage and disadvantage Aol founded
Aol founded Social networking sites
Social networking sites Facebook social networking website
Facebook social networking website The beatles became the most popular
The beatles became the most popular Most popular religion
Most popular religion The most popular lan standard.
The most popular lan standard. Popular sports in austria
Popular sports in austria Most popular sports in lithuania
Most popular sports in lithuania Internet is the world's largest public lan
Internet is the world's largest public lan Plotter is a storage device
Plotter is a storage device Multimedia product examples
Multimedia product examples Most popular religion in italy
Most popular religion in italy Shifting cultivation and taungya system
Shifting cultivation and taungya system Sports in poland
Sports in poland Kien thuc ngay nay is one of the most popular
Kien thuc ngay nay is one of the most popular Social thinking and social influence in psychology
Social thinking and social influence in psychology Social thinking social influence social relations
Social thinking social influence social relations Generations
Generations How was today's class
How was today's class Multiple choice comma quiz
Multiple choice comma quiz Todays worldld
Todays worldld What is todays temperature
What is todays temperature Todays globl
Todays globl Whats todays wordlw
Whats todays wordlw Chapter 13 marketing in todays world
Chapter 13 marketing in todays world Todays plan
Todays plan Todays sabbath lesson
Todays sabbath lesson Todays sabbath school lesson
Todays sabbath school lesson Midlands 2 west north
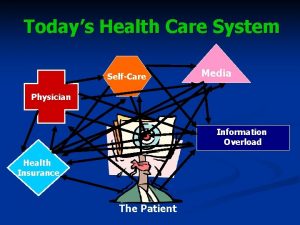
Midlands 2 west north Todays health
Todays health Todays objective
Todays objective No thats not it
No thats not it Today's objective
Today's objective Todays whether
Todays whether Todays vision
Todays vision Todays objective
Todays objective Todays planetary position
Todays planetary position Mla cover page format
Mla cover page format Todays final jeopardy answer
Todays final jeopardy answer Handcuffing positions
Handcuffing positions Todays weather hull
Todays weather hull Todays objective
Todays objective Wat is todays date
Wat is todays date Todays objective
Todays objective Digestive system of ruminant
Digestive system of ruminant Todays objective
Todays objective Todays objective
Todays objective