Security Design for IEEE P 1687 Hejia Liu






- Slides: 26

Security Design for IEEE P 1687 Hejia Liu Major Professor: Vishwani D. Agrawal

Introduction �Part 1: Introduction of IEEE P 1687 (IJTAG) security risks in P 1687 �Part 2: Security design and expected unlocking time �Part 3: Discussion of a proposal and improvement in security Apr 8, 2014 Liu: MEE Project 2

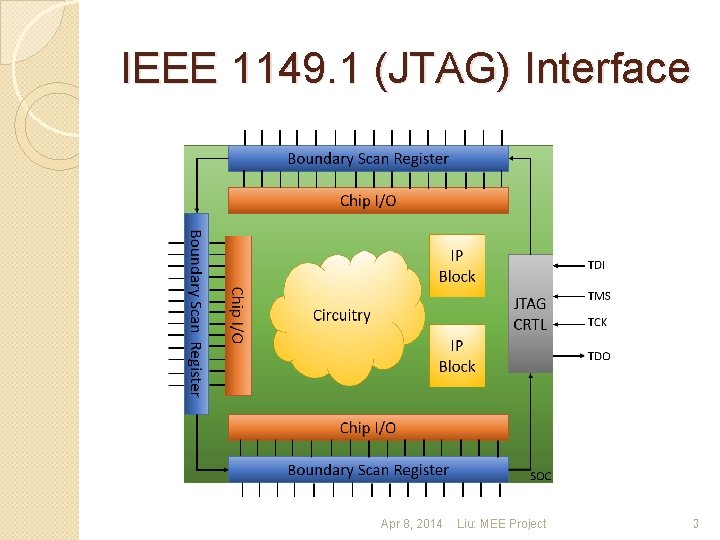
IEEE 1149. 1 (JTAG) Interface Apr 8, 2014 Liu: MEE Project 3

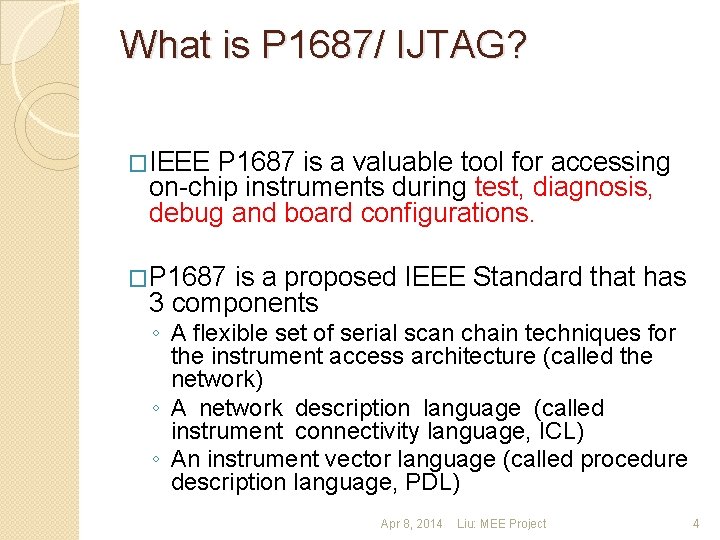
What is P 1687/ IJTAG? �IEEE P 1687 is a valuable tool for accessing on-chip instruments during test, diagnosis, debug and board configurations. �P 1687 is a proposed IEEE Standard that has 3 components ◦ A flexible set of serial scan chain techniques for the instrument access architecture (called the network) ◦ A network description language (called instrument connectivity language, ICL) ◦ An instrument vector language (called procedure description language, PDL) Apr 8, 2014 Liu: MEE Project 4

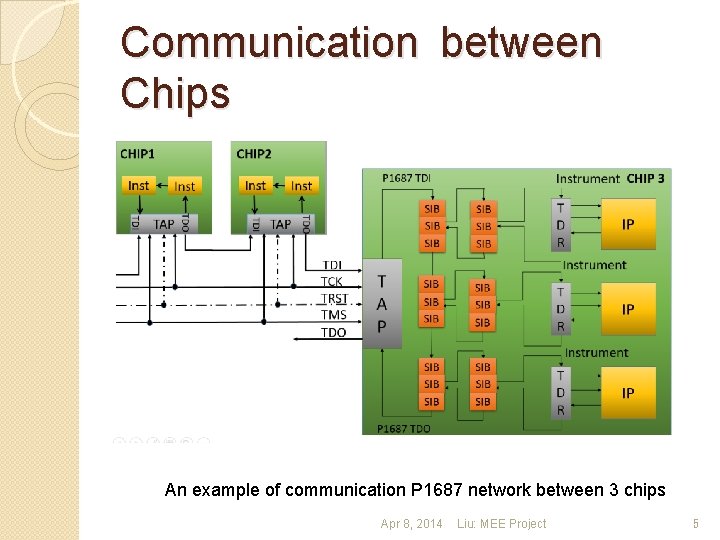
Communication between Chips An example of communication P 1687 network between 3 chips Apr 8, 2014 Liu: MEE Project 5

Instruments, IPs �An IP (Intellectual property core) with a P 1687 compliant interface is named instrument. �IPs: Analog, digital or mixed signal circuitry performing particular functions, such as a clock a generator, an interface to an external measurement probe, a radio tuner, an analog signal converter, a digital signal processor, etc. Apr 8, 2014 Liu: MEE Project 6

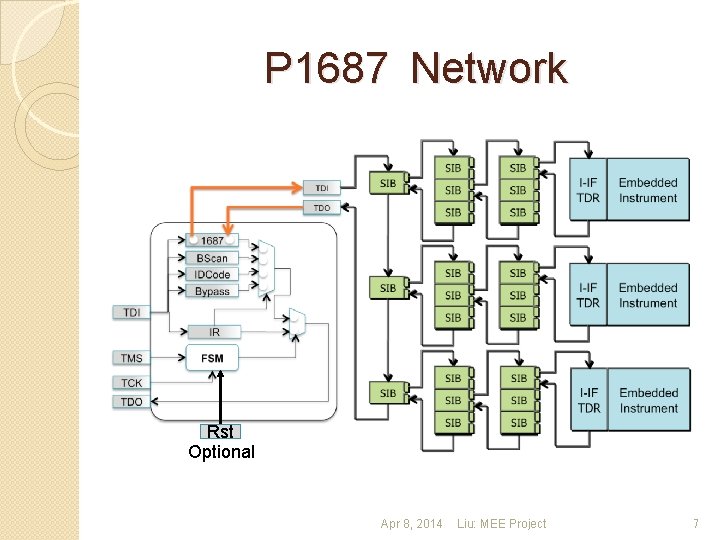
P 1687 Network Rst Optional Apr 8, 2014 Liu: MEE Project 7

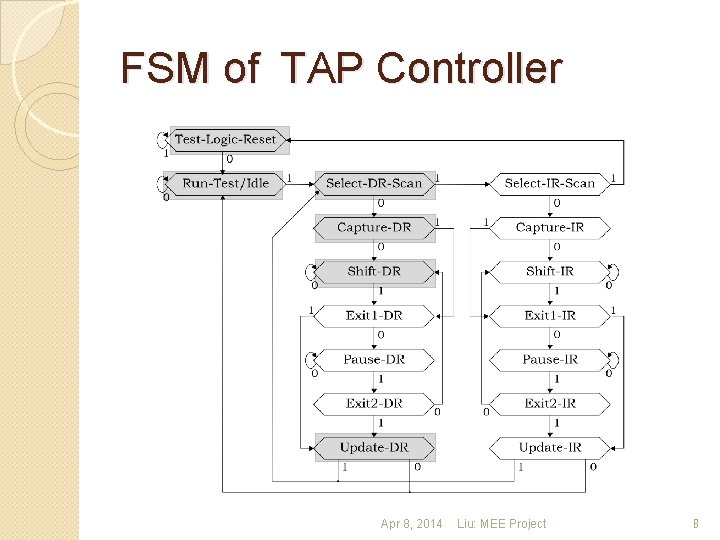
FSM of TAP Controller Apr 8, 2014 Liu: MEE Project 8

Security Risks �Depending on the application, data may be stored on-chip, including chip ID, codes, and encryption keys. � An attacker can access a targeted instrument and obtain the secret data easily. Apr 8, 2014 Liu: MEE Project 9

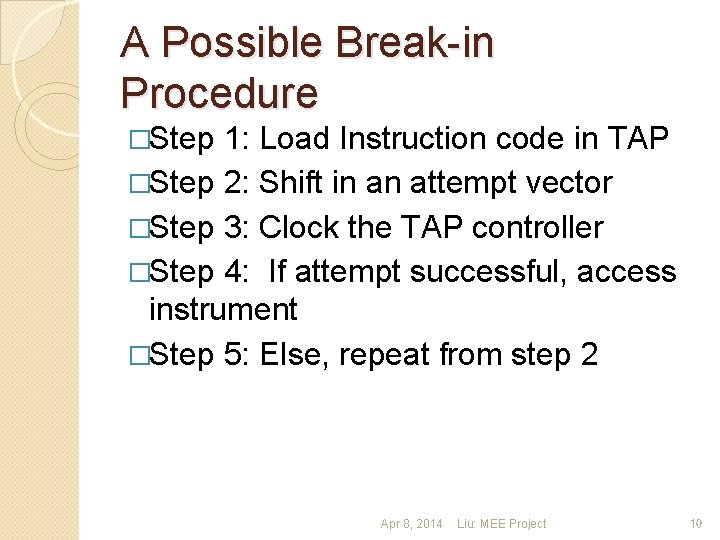
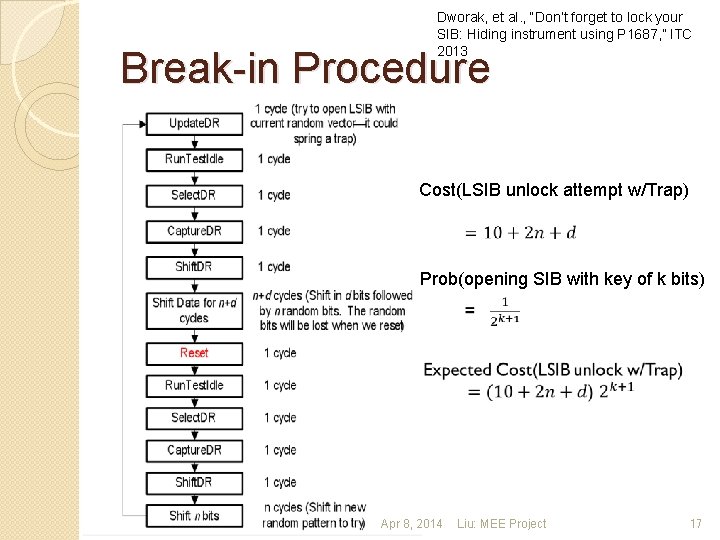
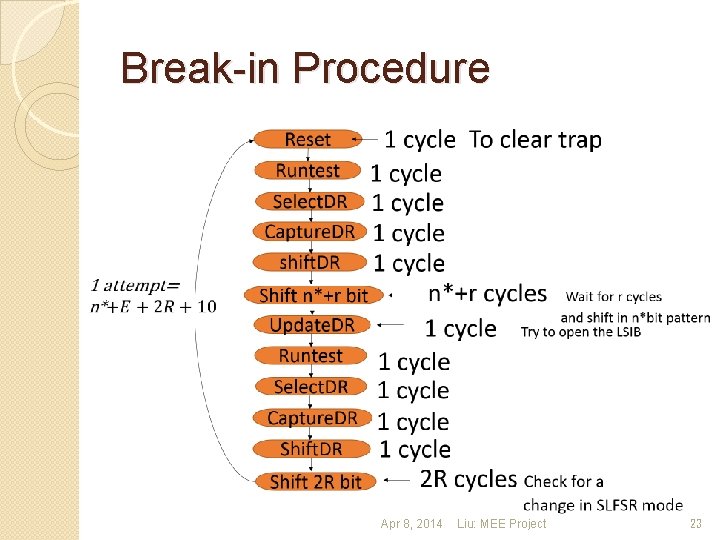
A Possible Break-in Procedure �Step 1: Load Instruction code in TAP �Step 2: Shift in an attempt vector �Step 3: Clock the TAP controller �Step 4: If attempt successful, access instrument �Step 5: Else, repeat from step 2 Apr 8, 2014 Liu: MEE Project 10

Security Levels �Insecurity: Break-in time at the level of days �Weak security: Break-in time at the level of years �Strong security: Break-in time at the level of ten years �Full Security: Break-in time in the level of thousand years Apr 8, 2014 Liu: MEE Project 11

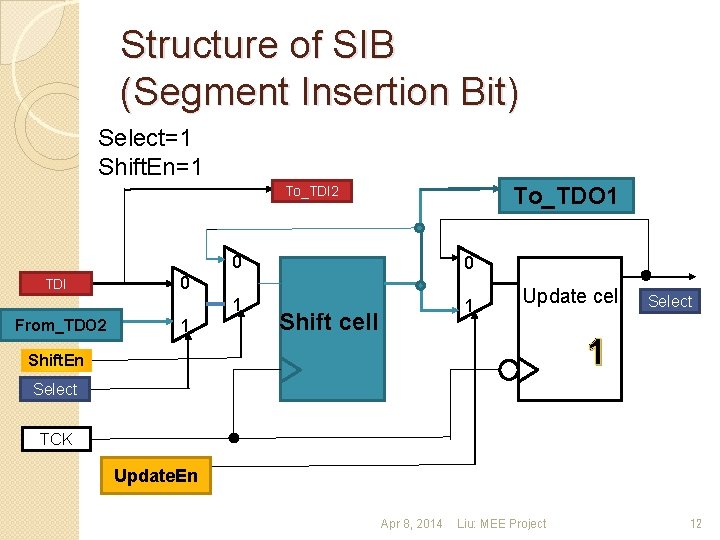
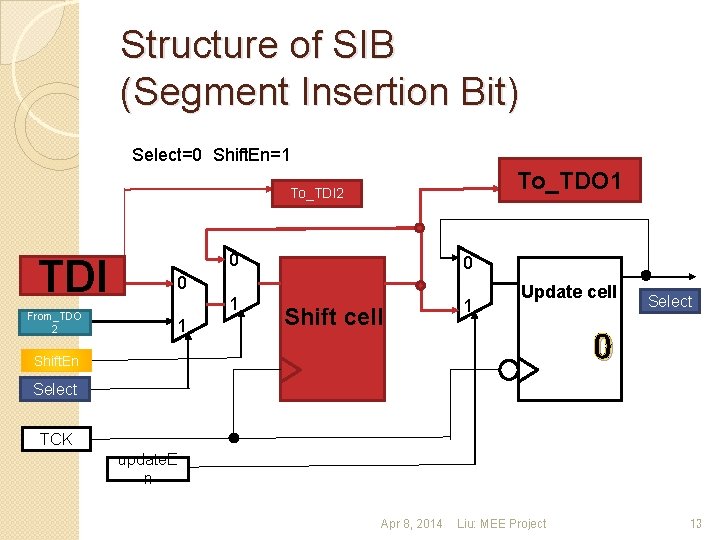
Structure of SIB (Segment Insertion Bit) Select=1 Shift. En=1 To_TDO 1 To_TDI 2 TDI From_TDO 2 0 0 1 1 0 1 Shift cell Update cell Select 1 Shift. En Select TCK Update. En Apr 8, 2014 Liu: MEE Project 12

Structure of SIB (Segment Insertion Bit) Select=0 Shift. En=1 To_TDO 1 To_TDI 2 TDI From_TDO 2 0 0 1 1 0 1 Shift cell Update cell Select 0 Shift. En Select TCK update. E n Apr 8, 2014 Liu: MEE Project 13

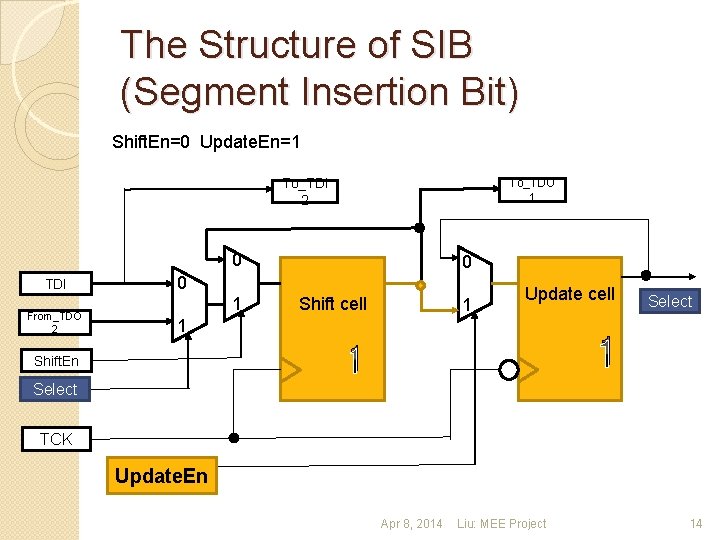
The Structure of SIB (Segment Insertion Bit) Shift. En=0 Update. En=1 To_TDI 2 To_TDO 1 0 TDI From_TDO 2 0 0 1 Shift cell 1 Update cell 1 1 1 Shift. En Select TCK Update. En Apr 8, 2014 Liu: MEE Project 14

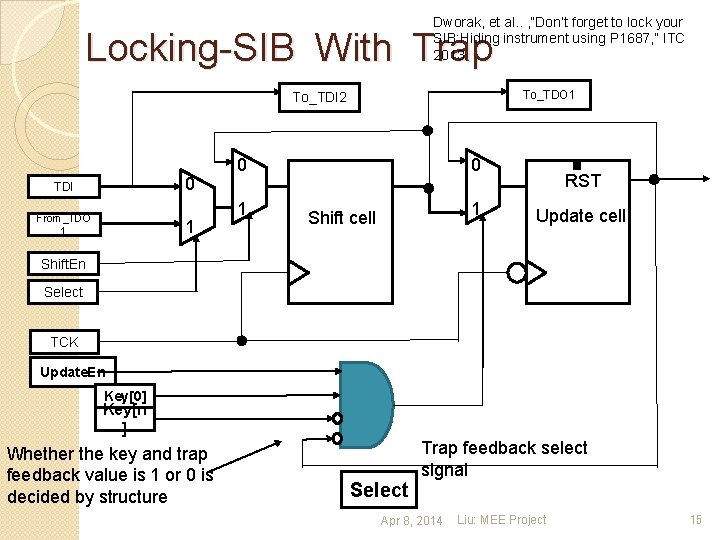
Dworak, et al. . , ”Don’t forget to lock your SIB: Hiding instrument using P 1687, ” ITC 2013 Locking-SIB With Trap To_TDO 1 To_TDI 2 0 TDI From_TDO 1 1 0 1 Shift cell RST Update cell Shift. En Select TCK Update. En Key[0] Key[n ] Whether the key and trap feedback value is 1 or 0 is decided by structure Select Trap feedback select signal Apr 8, 2014 Liu: MEE Project 15

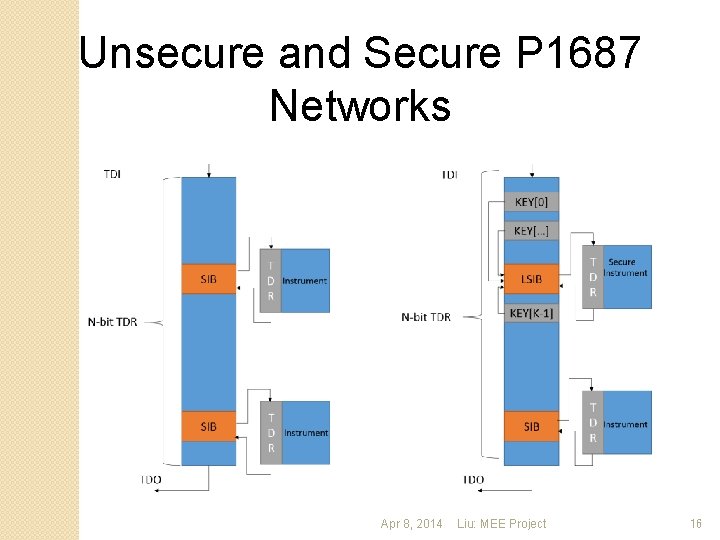
Unsecure and Secure P 1687 Networks Apr 8, 2014 Liu: MEE Project 16

Dworak, et al. , “Don’t forget to lock your SIB: Hiding instrument using P 1687, ” ITC 2013 Break-in Procedure Cost(LSIB unlock attempt w/Trap) Prob(opening SIB with key of k bits) Apr 8, 2014 Liu: MEE Project 17

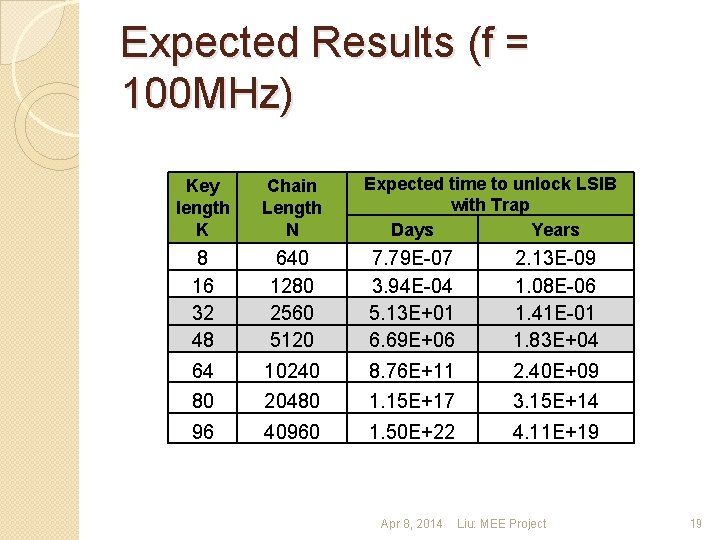
Expected Results (f = 100 MHz) Expected time to unlock LSIB with Trap Days Years Key length K Chain Length N 8 16 32 48 640 1280 2560 5120 7. 79 E-07 3. 94 E-04 5. 13 E+01 6. 69 E+06 2. 13 E-09 1. 08 E-06 1. 41 E-01 1. 83 E+04 64 10240 8. 76 E+11 2. 40 E+09 80 20480 1. 15 E+17 3. 15 E+14 96 40960 1. 50 E+22 4. 11 E+19 Apr 8, 2014 Liu: MEE Project 19

Features of Secure Structure � Apr 8, 2014 Liu: MEE Project 20

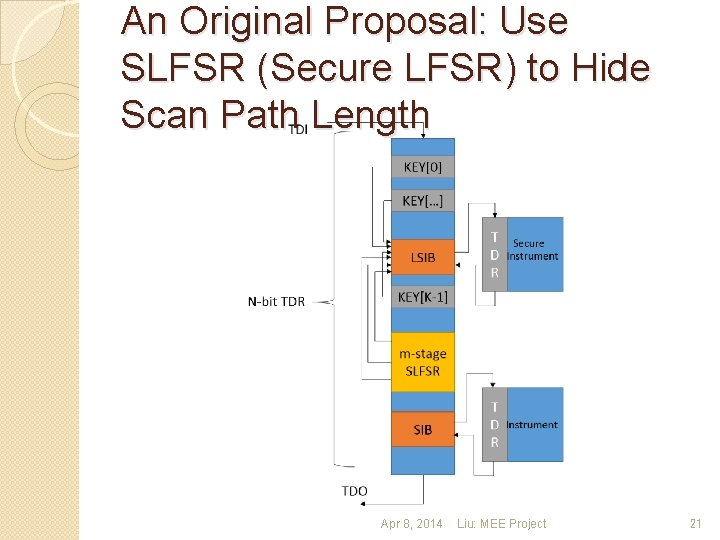
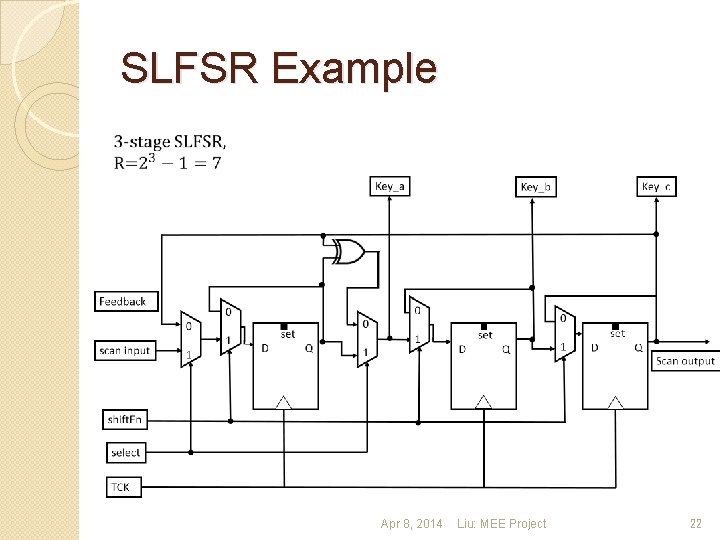
An Original Proposal: Use SLFSR (Secure LFSR) to Hide Scan Path Length Apr 8, 2014 Liu: MEE Project 21

SLFSR Example Apr 8, 2014 Liu: MEE Project 22

Break-in Procedure Apr 8, 2014 Liu: MEE Project 23

Attacker’s Strategies � Apr 8, 2014 Liu: MEE Project 24

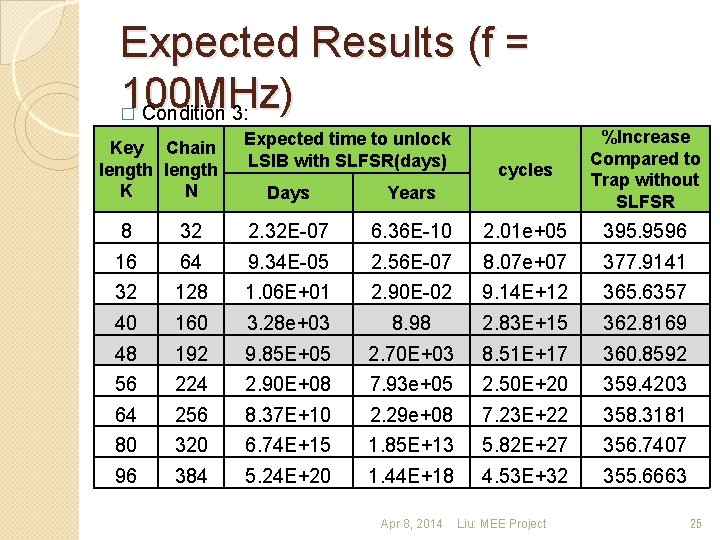
Expected Results (f = 100 MHz) Condition 3: � Key Chain length K N Expected time to unlock LSIB with SLFSR(days) Days Years cycles %Increase Compared to Trap without SLFSR 8 32 2. 32 E-07 6. 36 E-10 2. 01 e+05 395. 9596 16 64 9. 34 E-05 2. 56 E-07 8. 07 e+07 377. 9141 32 128 1. 06 E+01 2. 90 E-02 9. 14 E+12 365. 6357 40 160 3. 28 e+03 8. 98 2. 83 E+15 362. 8169 48 192 9. 85 E+05 2. 70 E+03 8. 51 E+17 360. 8592 56 224 2. 90 E+08 7. 93 e+05 2. 50 E+20 359. 4203 64 256 8. 37 E+10 2. 29 e+08 7. 23 E+22 358. 3181 80 320 6. 74 E+15 1. 85 E+13 5. 82 E+27 356. 7407 96 384 5. 24 E+20 1. 44 E+18 4. 53 E+32 355. 6663 Apr 8, 2014 Liu: MEE Project 25

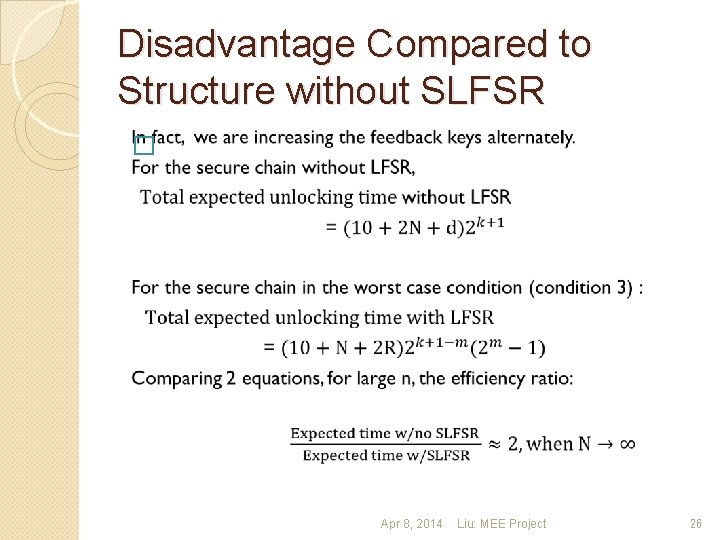
Disadvantage Compared to Structure without SLFSR � Apr 8, 2014 Liu: MEE Project 26

Conclusion �It is useful we replace the non- functional segments with SLFSR �Security SLFSR increases attacker’s effort as breaking not only depends on the structure we build up, but also the strategies that attacker chooses. �We should be concerned about the “lucky” attacker Apr 8, 2014 Liu: MEE Project 27