Policy Management An Overview Marco Casassa Mont marco




![Examples of (High-Level) Policies [1/3] The UK Data Protection Act (1998) requires that Personal Examples of (High-Level) Policies [1/3] The UK Data Protection Act (1998) requires that Personal](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-8.jpg)
![Examples of Policies (Refinement) [2/3] “Every financial institution has an affirmative and continuing obligation Examples of Policies (Refinement) [2/3] “Every financial institution has an affirmative and continuing obligation](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-9.jpg)
![Examples of Policies (Categories) [3/3] Enterprise Information Lifecycle Management Policies Service Level Agreements Change Examples of Policies (Categories) [3/3] Enterprise Information Lifecycle Management Policies Service Level Agreements Change](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-10.jpg)



![Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [1/2] Information Lifecycle Management Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [1/2] Information Lifecycle Management](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-21.jpg)
![Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [2/2] Policy-driven Information Lifecycle Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [2/2] Policy-driven Information Lifecycle](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-22.jpg)






![Privacy Policy Authoring [1/2] 42 1/3/2022 Privacy Policy Authoring [1/2] 42 1/3/2022](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-42.jpg)
![Privacy Policy Authoring [2/2] Checking Intent against Purpose Define Data Filtering Criteria 43 1/3/2022 Privacy Policy Authoring [2/2] Checking Intent against Purpose Define Data Filtering Criteria 43 1/3/2022](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-43.jpg)




![Identity Capable Platforms (ICP) [1/2] 55 1/3/2022 Identity Capable Platforms (ICP) [1/2] 55 1/3/2022](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-55.jpg)
![Identity Capable Platforms (ICP) [2/2] Liberty Alliance Initiative (http: //www. projectliberty. org) • Focus Identity Capable Platforms (ICP) [2/2] Liberty Alliance Initiative (http: //www. projectliberty. org) • Focus](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-56.jpg)

![Policy Management: Hard Problems and Future Research Areas [1/5] A) Policy Refinement Process Human Policy Management: Hard Problems and Future Research Areas [1/5] A) Policy Refinement Process Human](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-62.jpg)
![Policy Management: Hard Problems and Future Research Areas [2/5] B) “Federated Policy Management” in Policy Management: Hard Problems and Future Research Areas [2/5] B) “Federated Policy Management” in](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-63.jpg)
![Policy Management: Hard Problems and Future Research Areas [3/5] C) Management of “Sticky Policies” Policy Management: Hard Problems and Future Research Areas [3/5] C) Management of “Sticky Policies”](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-64.jpg)
![Policy Management: Hard Problems and Future Research Areas [4/5] D) Content-aware Access Control in Policy Management: Hard Problems and Future Research Areas [4/5] D) Content-aware Access Control in](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-65.jpg)
![Policy Management: Hard Problems and Future Research Areas [5/5] E) Other Research Areas • Policy Management: Hard Problems and Future Research Areas [5/5] E) Other Research Areas •](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-66.jpg)







- Slides: 73

Policy Management: An Overview Marco Casassa Mont marco. casassa-mont@hp. com Trusted Systems Lab Hewlett-Packard Labs © 2006 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

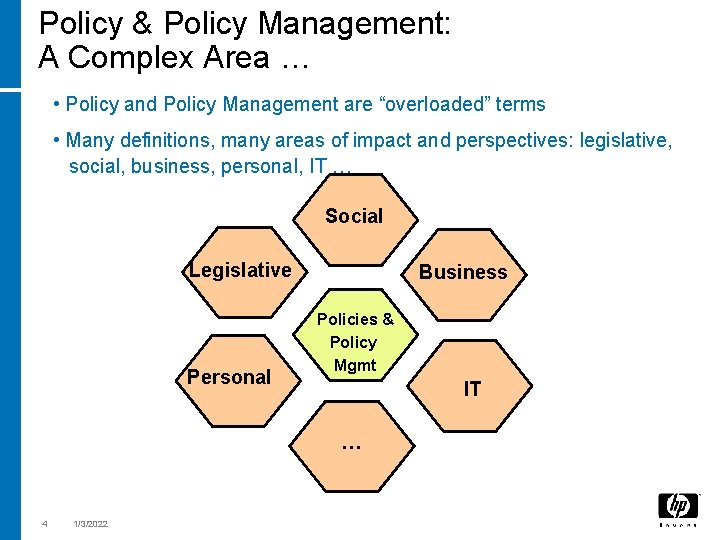
Policy & Policy Management: A Complex Area … • Policy and Policy Management are “overloaded” terms • Many definitions, many areas of impact and perspectives: legislative, social, business, personal, IT … Social Legislative Personal Business Policies & Policy Mgmt IT … 4 1/3/2022

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

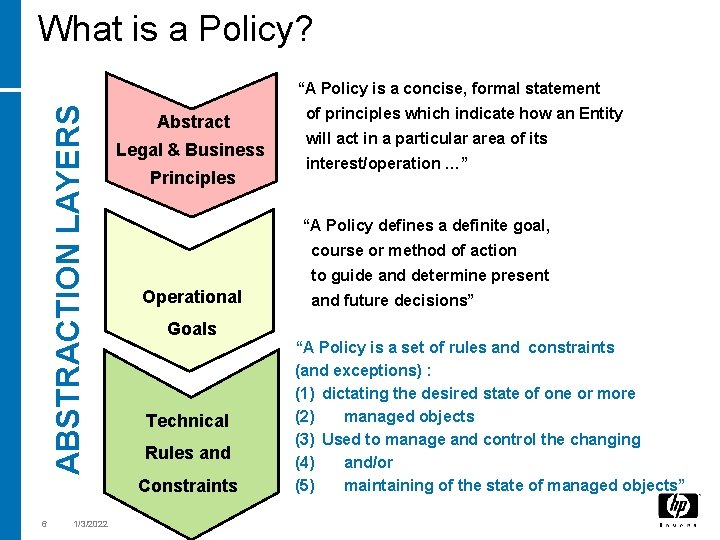
What is a Policy? ABSTRACTION LAYERS “A Policy is a concise, formal statement Abstract Legal & Business Principles 1/3/2022 will act in a particular area of its interest/operation …” “A Policy defines a definite goal, course or method of action to guide and determine present Operational Goals Technical Rules and Constraints 6 of principles which indicate how an Entity and future decisions” “A Policy is a set of rules and constraints (and exceptions) : (1) dictating the desired state of one or more (2) managed objects (3) Used to manage and control the changing (4) and/or (5) maintaining of the state of managed objects”

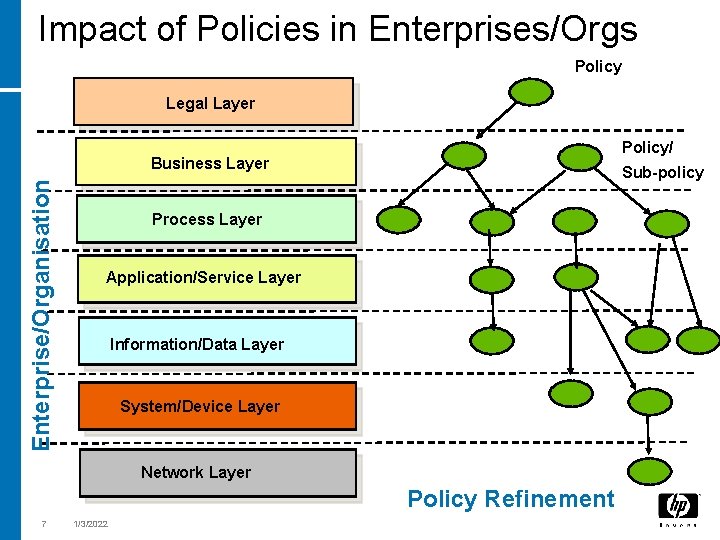
Impact of Policies in Enterprises/Orgs Policy Legal Layer Policy/ Enterprise/Organisation Business Layer Sub-policy Process Layer Application/Service Layer Information/Data Layer System/Device Layer Network Layer Policy Refinement 7 1/3/2022
![Examples of HighLevel Policies 13 The UK Data Protection Act 1998 requires that Personal Examples of (High-Level) Policies [1/3] The UK Data Protection Act (1998) requires that Personal](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-8.jpg)
Examples of (High-Level) Policies [1/3] The UK Data Protection Act (1998) requires that Personal Data shall: 1. Be processed fairly and lawfully and shall not be processed unless certain conditions are met; 2. Be obtained for a specified and lawful purpose and shall not be processed in any manner incompatible with that purpose; 3. Be adequate, relevant and not excessive for those purposes; 4. Be accurate and, where necessary, kept up to date; 5. Not be kept for longer than is necessary for that purpose; 6. Be processed in accordance with the data subject’s rights; 7. Be kept secure from unauthorised or unlawful processing and protected against accidental loss, destruction or damage by using the appropriate technical and organisational measures; 8. And not be transferred to a country or territory outside the European Economic Area, unless that country or territory ensures an adequate level of protection for the rights and freedoms of data subjects in relation to the processing of personal data. Other Legislation: SOX, GLB, HIPAA, COPPA, EU Data Protection Law, etc 8 1/3/2022
![Examples of Policies Refinement 23 Every financial institution has an affirmative and continuing obligation Examples of Policies (Refinement) [2/3] “Every financial institution has an affirmative and continuing obligation](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-9.jpg)
Examples of Policies (Refinement) [2/3] “Every financial institution has an affirmative and continuing obligation to respect customer privacy and protect the security and confidentiality of customer information” Gramm-Leach-Bliley (GLB) Act All Financial, Personal and The CEO has the Confidential Information duty to demonstrate must be secured Organisational … Compliance to GLB All Processes, Applications and services Only People with Information has Financial Data Role X To be retained must not be only Can Access Data Y In Data Storage Z All Critical Systems Ifdeleted there areunless well Storing Data Need If explicitly Defined reasons & authorised by CFO purposes to be Periodically Scanned Against 9 1/3/2022 Viruses need to be auditable All Critical MS Applications and Services Must have the Audit Log Feature Turned-on
![Examples of Policies Categories 33 Enterprise Information Lifecycle Management Policies Service Level Agreements Change Examples of Policies (Categories) [3/3] Enterprise Information Lifecycle Management Policies Service Level Agreements Change](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-10.jpg)
Examples of Policies (Categories) [3/3] Enterprise Information Lifecycle Management Policies Service Level Agreements Change Control Policies Availability and 10 Recovery Time Security Policies 1/3/2022 IT Governance Policies

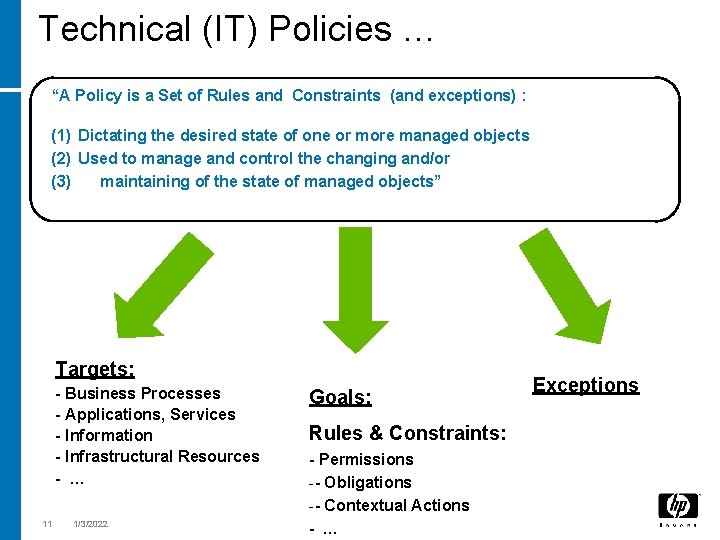
Technical (IT) Policies … “A Policy is a Set of Rules and Constraints (and exceptions) : (1) Dictating the desired state of one or more managed objects (2) Used to manage and control the changing and/or (3) maintaining of the state of managed objects” Targets: - Business Processes - Applications, Services - Information - Infrastructural Resources - … 11 1/3/2022 Goals: Rules & Constraints: - Permissions -- Obligations -- Contextual Actions - … Exceptions

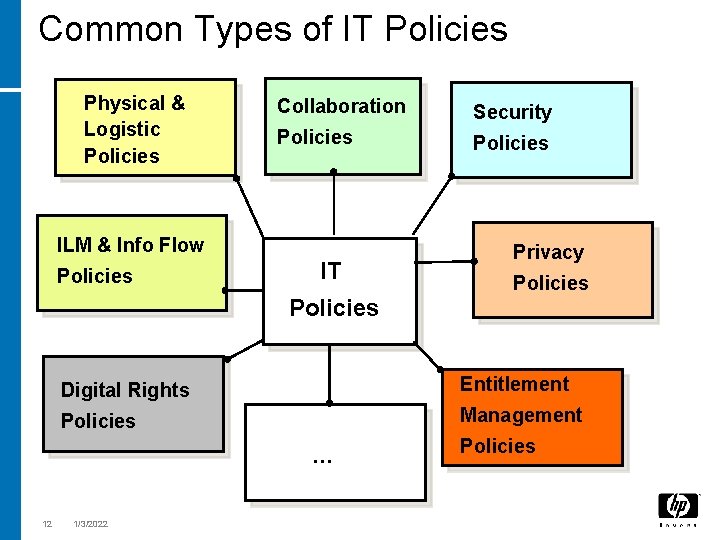
Common Types of IT Policies Physical & Logistic Policies Collaboration Security Policies ILM & Info Flow Policies IT Privacy Policies Digital Rights Entitlement Policies Management … 12 1/3/2022 Policies

IT Policy Representation Policy Languages • Formal representation of Policy Rules, Constraints and Exceptions • Reasoning • Automation of Policy Decisions, Enforcement and Monitoring Many Standards and/or Proposals • Security/Access Control: OASIS XACML, Ponder (IC), … • Privacy: W 3 C P 3 P, EPAL, Extended XACML, EU PRIME, … • Assertions/Rights: OASIS SAML, … • … 13 1/3/2022

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

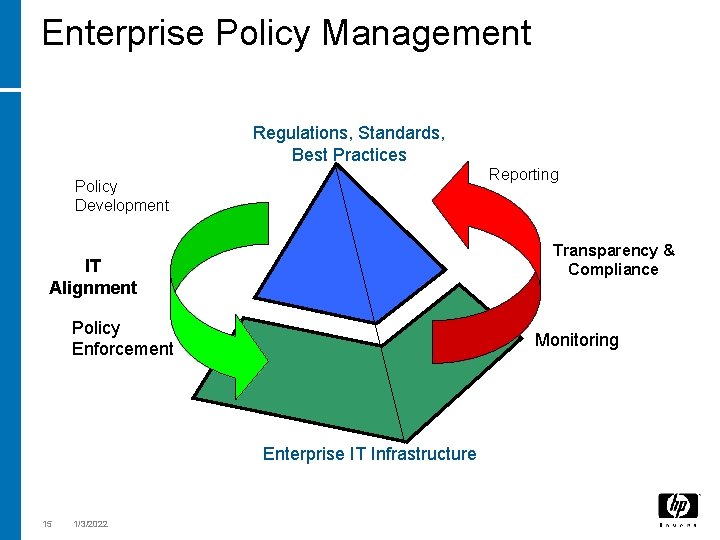
Enterprise Policy Management Regulations, Standards, Best Practices Reporting Policy Development Transparency & Compliance IT Alignment Policy Enforcement Monitoring Enterprise IT Infrastructure 15 1/3/2022

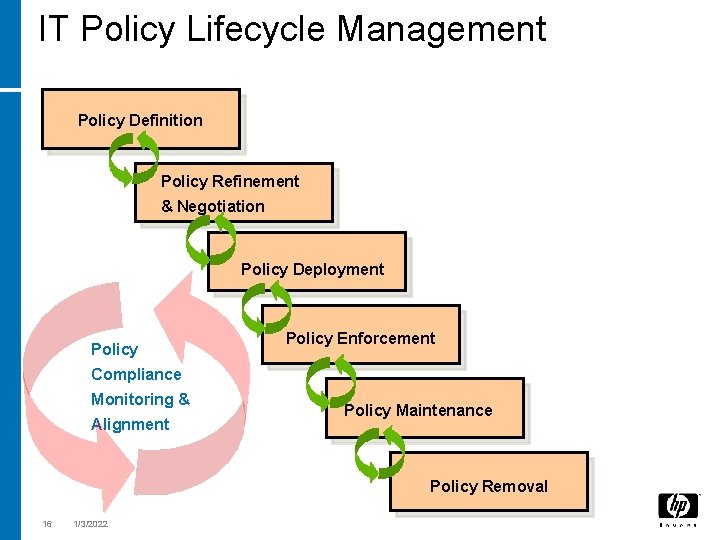
IT Policy Lifecycle Management Policy Definition Policy Refinement & Negotiation Policy Deployment Policy Enforcement Compliance Monitoring & Alignment Policy Maintenance Policy Removal 16 1/3/2022

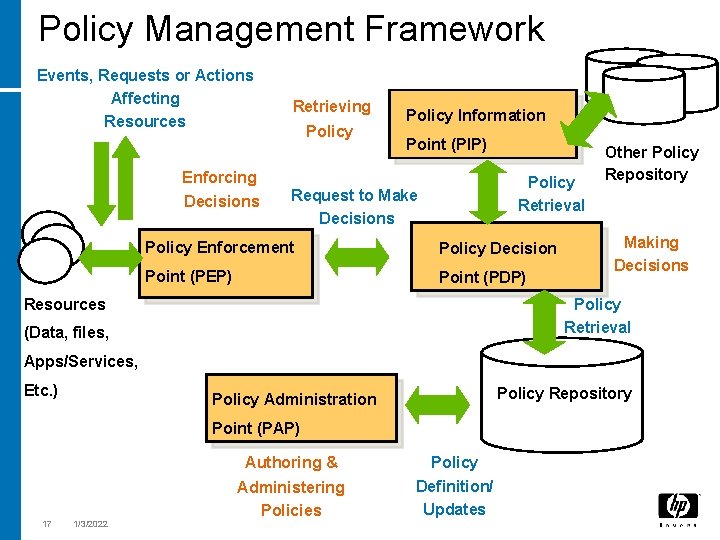
Policy Management Framework Events, Requests or Actions Affecting Resources Enforcing Decisions Retrieving Policy Information Point (PIP) Policy Retrieval Request to Make Decisions Policy Enforcement Policy Decision Point (PEP) Point (PDP) Resources Other Policy Repository Making Decisions Policy Retrieval (Data, files, Apps/Services, Etc. ) Policy Repository Policy Administration Point (PAP) Authoring & 17 1/3/2022 Administering Policies Policy Definition/ Updates

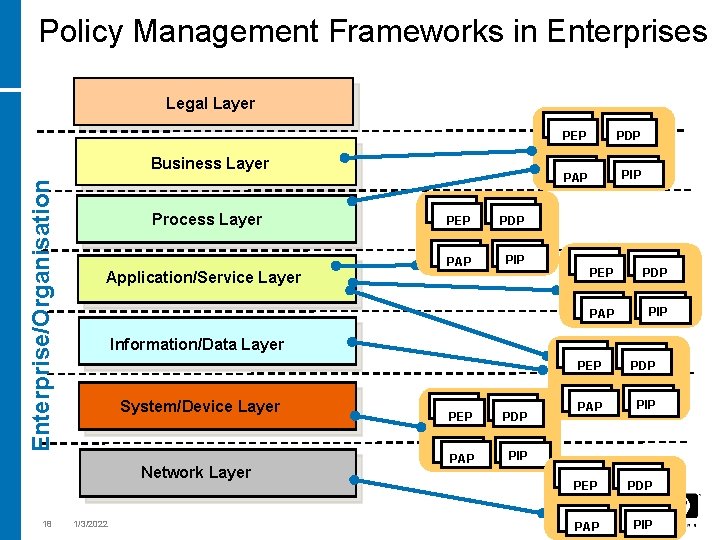
Policy Management Frameworks in Enterprises Legal Layer Enterprise/Organisation Business Layer Process Layer Application/Service Layer PDP PAP PIP PEP PDP PAP PIP Information/Data Layer System/Device Layer Network Layer 18 PEP 1/3/2022 PEP PDP PAP PIP

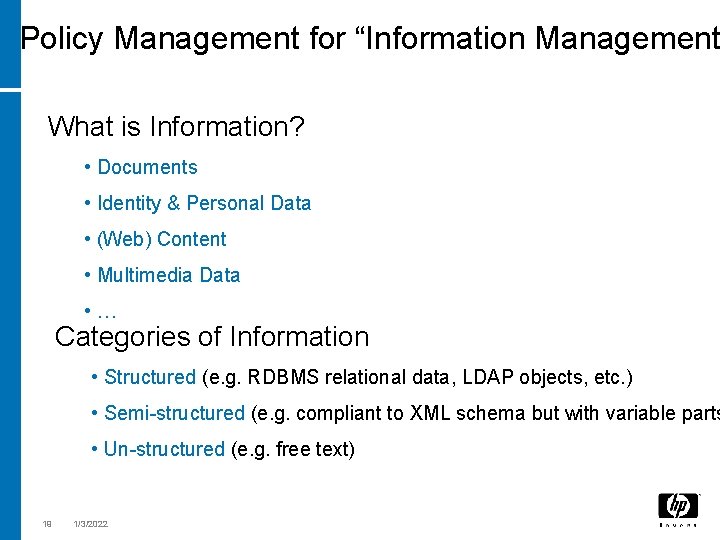
Policy Management for “Information Management What is Information? • Documents • Identity & Personal Data • (Web) Content • Multimedia Data • … Categories of Information • Structured (e. g. RDBMS relational data, LDAP objects, etc. ) • Semi-structured (e. g. compliant to XML schema but with variable parts • Un-structured (e. g. free text) 19 1/3/2022

Policies for “Information Management” Some Relevant Policies • Security Policies e. g. Only Person/Role X can Read and Modify Information I • Privacy Policies e. g. Data X can only be Accessed for Purpose P under the Explicit Consent of Data Subject (Owner) U • Retention/Disposal Policies e. g. Medical Information X can be disposed after 7 years • Availability and Retrieval (Qo. S) Policies e. g. Information of Type X must always be retrievable and accessible in not more than T seconds • Information Flow Policies e. g. Personal Data generated in EU can only be transferred to EU countries • … 20 1/3/2022
![Role of Policies in Classic Enterprise Information Lifecycle Management Scenario 12 Information Lifecycle Management Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [1/2] Information Lifecycle Management](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-21.jpg)
Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [1/2] Information Lifecycle Management (ILM) provides degrees of support for the following Information/Data Management Phases: Assessment Data Analysis Classification Automation Review 21 1/3/2022
![Role of Policies in Classic Enterprise Information Lifecycle Management Scenario 22 Policydriven Information Lifecycle Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [2/2] Policy-driven Information Lifecycle](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-22.jpg)
Role of Policies in Classic Enterprise “Information Lifecycle Management” Scenario [2/2] Policy-driven Information Lifecycle Management (ILM) Automation Technologies: ILM Policy Engine Search and Classify ILM Policy Audit Information/ Document Mover Source: “Data Protection and Information Lifecycle Management Ed. Prentice Hall, Author: Petrocelli” 22 1/3/2022 Secure Access

Role of Policies in other Important Scenarios • Enterprise Identity and Privacy Management of Identity and Confidential Information driven by Security and Privacy Policies • Federated Service Scenarios Policy-driven Information Flows across boundaries in Federate Contexts • Collaborative Scenarios Policy-driven Content Management • Management of Confidential Content in Devices Policy-driven management of Sensitive Information stored in Devices • … 23 1/3/2022

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

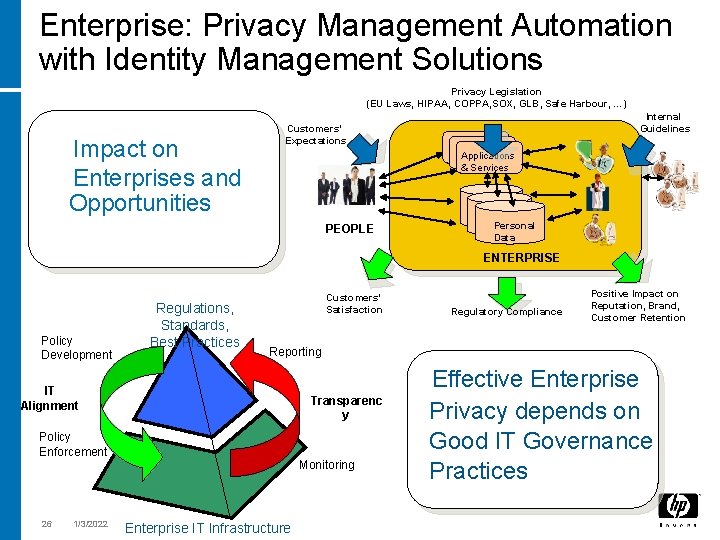
Enterprise: Privacy Management Automation with Identity Management Solutions Privacy Legislation (EU Laws, HIPAA, COPPA, SOX, GLB, Safe Harbour, …) Impact on Enterprises and Opportunities Internal Guidelines Customers’ Expectations Applications & Services PEOPLE Personal Data ENTERPRISE Policy Development Regulations, Standards, Best Practices Customers’ Satisfaction Reporting IT Alignment Transparenc y Policy Enforcement Monitoring 26 1/3/2022 Regulatory Compliance Positive Impact on Reputation, Brand, Customer Retention Enterprise IT Infrastructure Effective Enterprise Privacy depends on Good IT Governance Practices

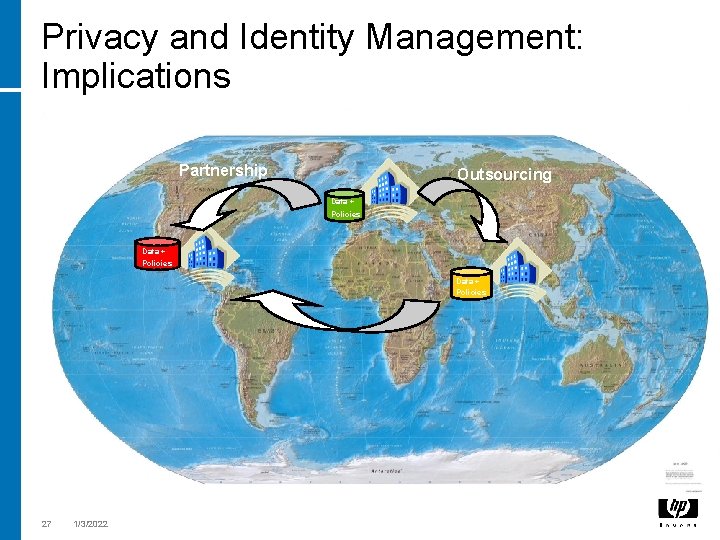
Privacy and Identity Management: Implications Partnership Outsourcing Data + Policies 27 1/3/2022

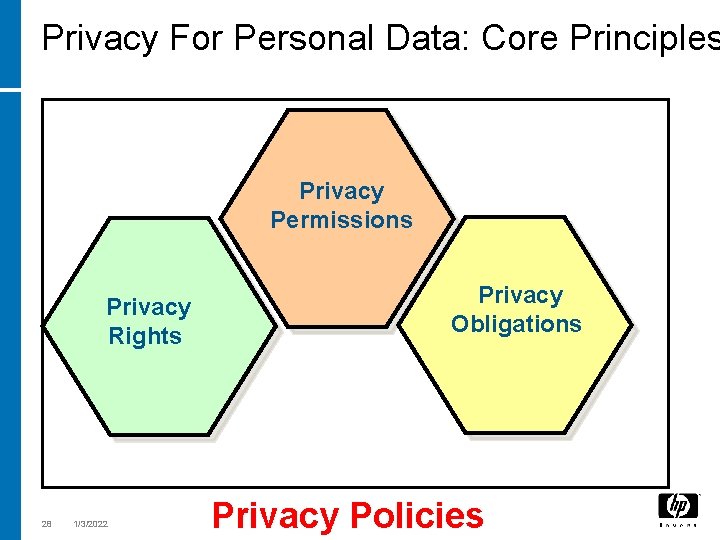
Privacy For Personal Data: Core Principles Privacy Collection Limitation Privacy Permissions Individual Participation Security Safeguards Privacy Rights OECD Principles Data Quality Privacy Obligations Purpose Specification Openness Use Limitation 28 1/3/2022 Privacy Policies

Addressed Problems • How to Automate Privacy Management within Enterprises: − How to Automate Privacy-Aware Access Control − How to Automate Privacy-Aware Information Lifecycle • How to Do this in a Systematic Way • How to Leverage Current Identity Management Solutions 29 1/3/2022

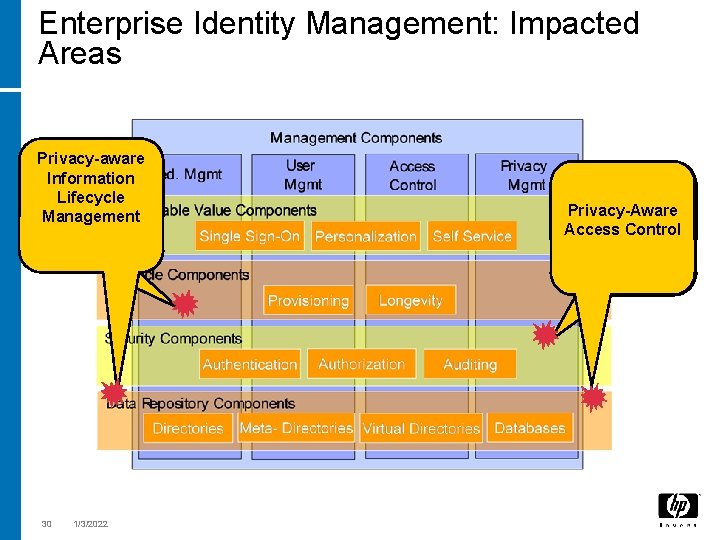
Enterprise Identity Management: Impacted Areas Privacy-aware Information Lifecycle Management 30 1/3/2022 Privacy-Aware Access Control

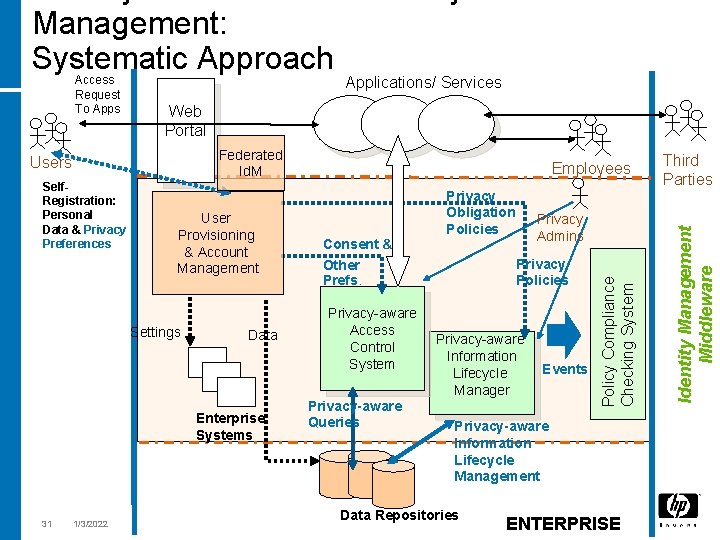
Management: Systematic Approach Web Portal Self. Registration: Personal Data & Privacy Preferences User Provisioning & Account Management Settings Data Enterprise Systems 1/3/2022 Employees Consent & Other Prefs. Privacy-aware Access Control System Privacy-aware Queries Privacy Obligation Policies Privacy Admins Privacy Policies Privacy-aware Information Lifecycle Manager Events Privacy-aware Information Lifecycle Management Data Repositories ENTERPRISE Third Parties Identity Management Middleware Federated Id. M Users 31 Applications/ Services Policy Compliance Checking System Access Request To Apps

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

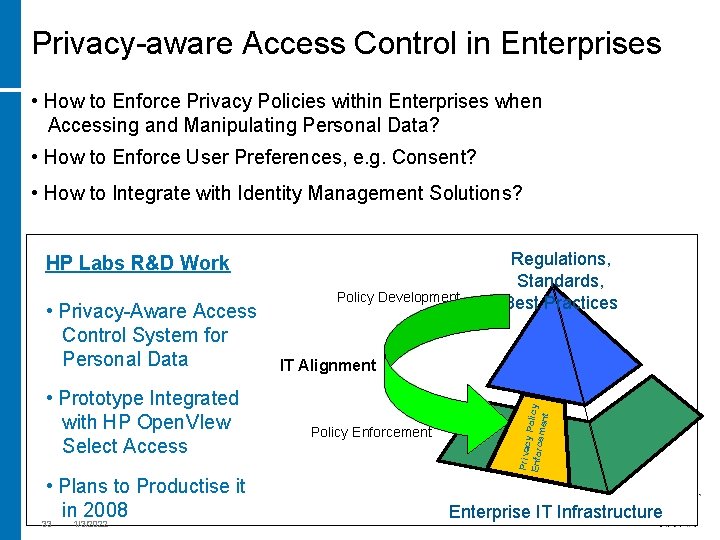
Privacy-aware Access Control in Enterprises • How to Enforce Privacy Policies within Enterprises when Accessing and Manipulating Personal Data? • How to Enforce User Preferences, e. g. Consent? • How to Integrate with Identity Management Solutions? HP Labs R&D Work • Prototype Integrated with HP Open. VIew Select Access • Plans to Productise it in 1/3/2022 2008 33 IT Alignment Policy Enforcement Privac y Polic y Enforc ement • Privacy-Aware Access Control System for Personal Data Policy Development Regulations, Standards, Best Practices Enterprise IT Infrastructure

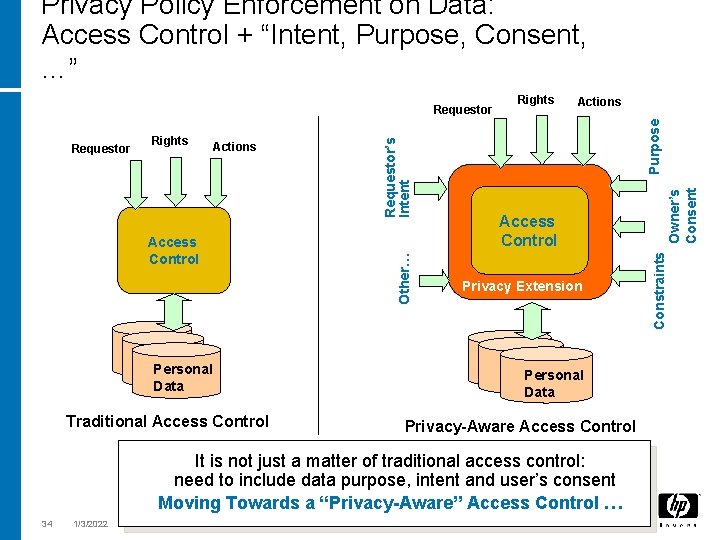
Privacy Policy Enforcement on Data: Access Control + “Intent, Purpose, Consent, …” Personal Data Traditional Access Control Privacy Extension Personal Data Privacy-Aware Access Control It is not just a matter of traditional access control: need to include data purpose, intent and user’s consent Moving Towards a “Privacy-Aware” Access Control … 34 1/3/2022 Owner’s Consent Access Control Actions Purpose Actions Rights Constraints Rights Other… Requestor’s Intent Requestor

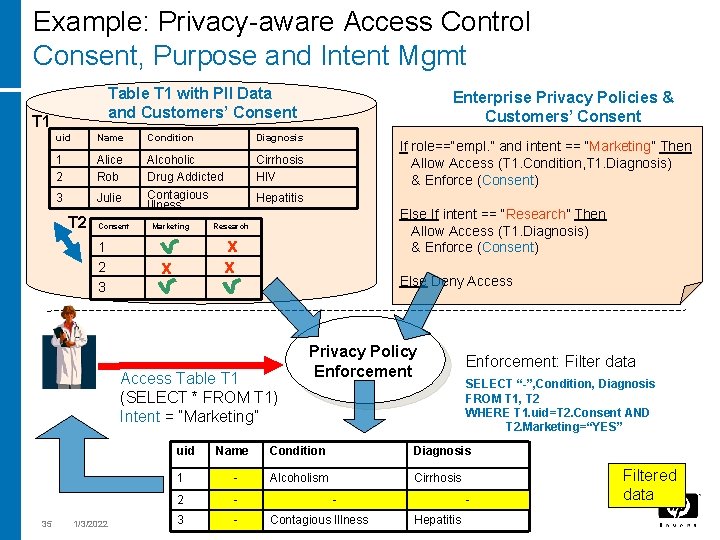
Example: Privacy-aware Access Control Consent, Purpose and Intent Mgmt Table T 1 with PII Data and Customers’ Consent T 1 uid Name Condition Diagnosis 1 2 Alice Rob Cirrhosis HIV 3 Julie Alcoholic Drug Addicted Contagious Illness T 2 Consent 1 2 3 Marketing Else If intent == “Research” Then Allow Access (T 1. Diagnosis) & Enforce (Consent) Research x x x uid 1/3/2022 If role==“empl. ” and intent == “Marketing” Then Allow Access (T 1. Condition, T 1. Diagnosis) & Enforce (Consent) Hepatitis Else Deny Access Table T 1 (SELECT * FROM T 1) Intent = “Marketing” 35 Enterprise Privacy Policies & Customers’ Consent Privacy Policy Enforcement: Filter data SELECT “-”, Condition, Diagnosis FROM T 1, T 2 WHERE T 1. uid=T 2. Consent AND T 2. Marketing=“YES” Name Condition Diagnosis 1 - Alcoholism Cirrhosis 2 - 3 - Contagious Illness Hepatitis Filtered data

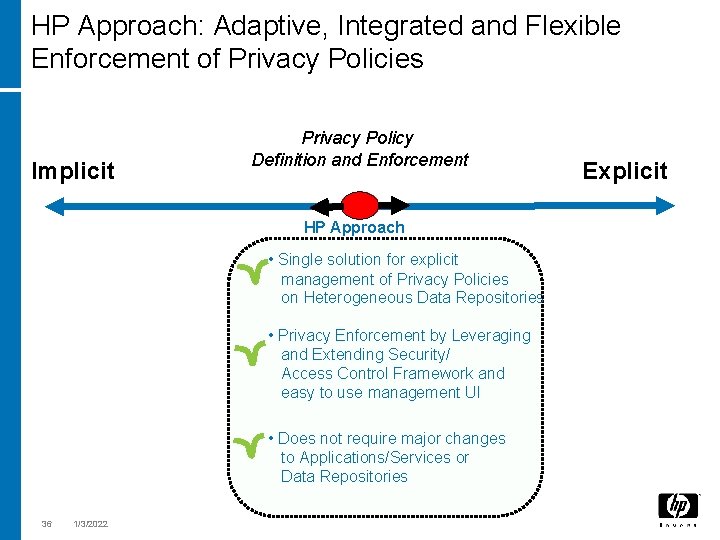
HP Approach: Adaptive, Integrated and Flexible Enforcement of Privacy Policies Implicit Privacy Policy Definition and Enforcement HP Approach • Single solution for explicit management of Privacy Policies on Heterogeneous Data Repositories • Privacy Enforcement by Leveraging and Extending Security/ Access Control Framework and easy to use management UI • Does not require major changes to Applications/Services or Data Repositories 36 1/3/2022 Explicit

Key Requirements • Modeling of Personal data • Explicit Definition, Authoring and Management of Privacy Policies • Extensible Privacy Policies • Explicit Deployment and Enforcement of Privacy Policies • Integration with traditional Access Control Systems • Simplicity of Usage • Support for Audit 37 1/3/2022

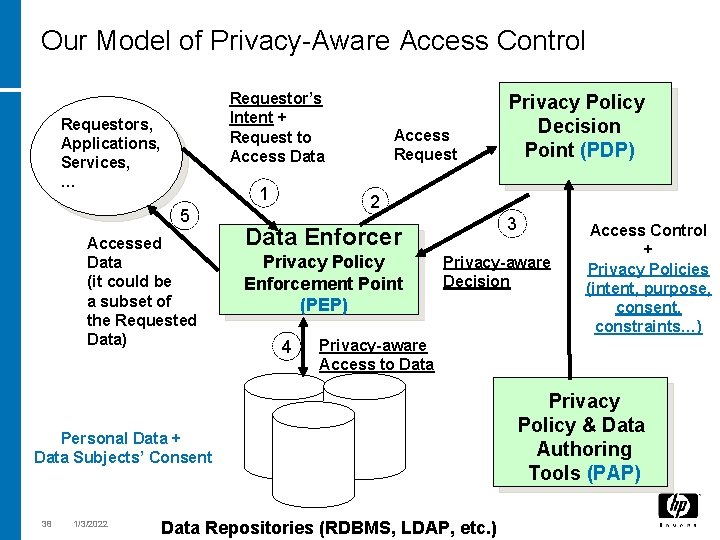
Our Model of Privacy-Aware Access Control Requestor’s Intent + Request to Access Data Requestors, Applications, Services, … 1 5 Accessed Data (it could be a subset of the Requested Data) Access Request 2 3 Data Enforcer Privacy Policy Enforcement Point (PEP) 4 Privacy-aware Decision 1/3/2022 Access Control + Privacy Policies (intent, purpose, consent, constraints…) Privacy-aware Access to Data Personal Data + Data Subjects’ Consent 38 Privacy Policy Decision Point (PDP) Data Repositories (RDBMS, LDAP, etc. ) Privacy Policy & Data Authoring Tools (PAP)

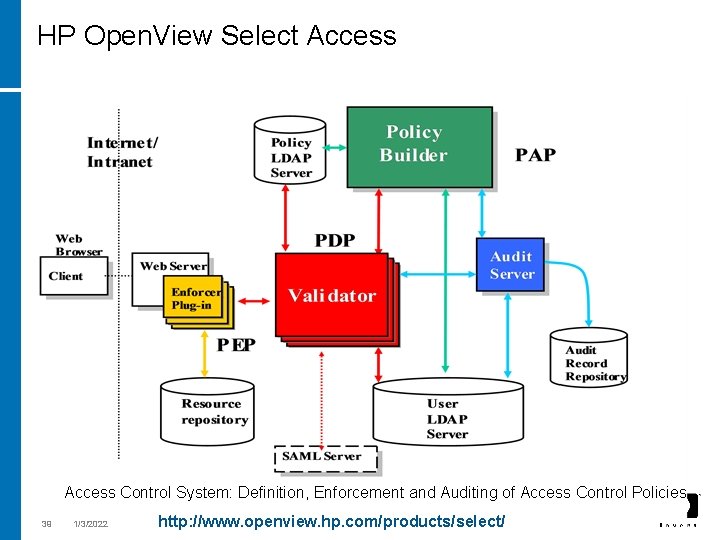
HP Open. View Select Access Control System: Definition, Enforcement and Auditing of Access Control Policies 39 1/3/2022 http: //www. openview. hp. com/products/select/

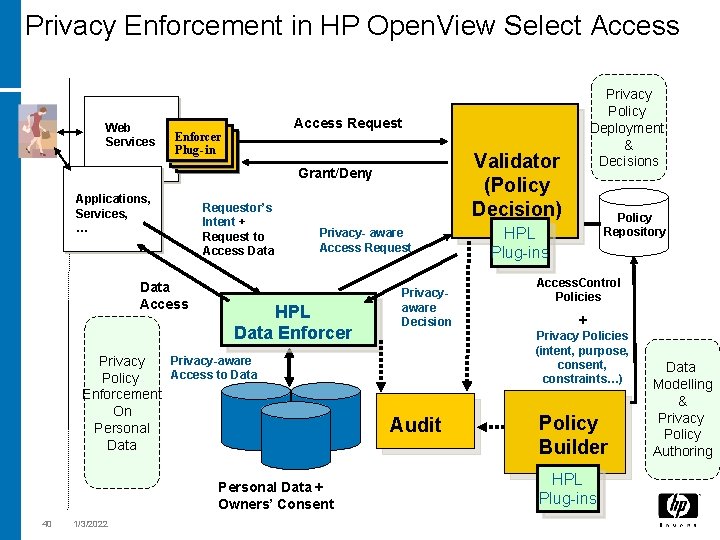
Privacy Enforcement in HP Open. View Select Access Web Services Access Request Enforcer Plug -in Plug-in Applications, Services, … Data Access Requestor’s Intent + Request to Access Data Privacy- aware Access Request HPL Data Enforcer Personal Data + Owners’ Consent 1/3/2022 Validator (Policy Decision) Grant/Deny Privacy-aware Privacy Access to Data Policy Enforcement On Personal Data 40 Privacy Policy Deployment & Decisions Privacyaware Decision Policy Repository HPL Plug-ins Access. Control Policies + Privacy Policies (intent, purpose, consent, constraints…) Audit Policy Builder HPL Plug-ins Data Modelling & Privacy Policy Authoring

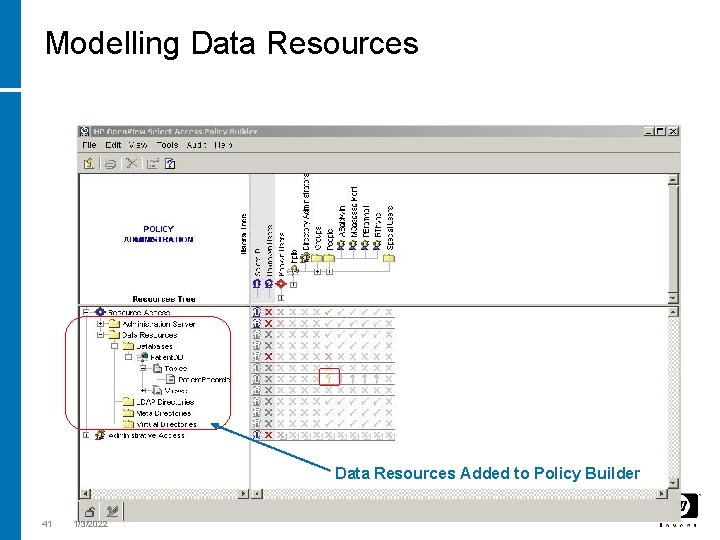
Modelling Data Resources Added to Policy Builder 41 1/3/2022
![Privacy Policy Authoring 12 42 132022 Privacy Policy Authoring [1/2] 42 1/3/2022](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-42.jpg)
Privacy Policy Authoring [1/2] 42 1/3/2022
![Privacy Policy Authoring 22 Checking Intent against Purpose Define Data Filtering Criteria 43 132022 Privacy Policy Authoring [2/2] Checking Intent against Purpose Define Data Filtering Criteria 43 1/3/2022](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-43.jpg)
Privacy Policy Authoring [2/2] Checking Intent against Purpose Define Data Filtering Criteria 43 1/3/2022 Define How to Handle Consent

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

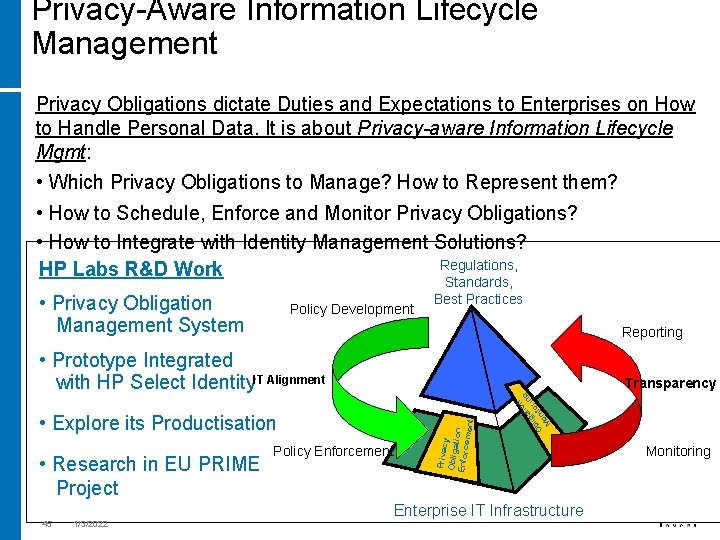
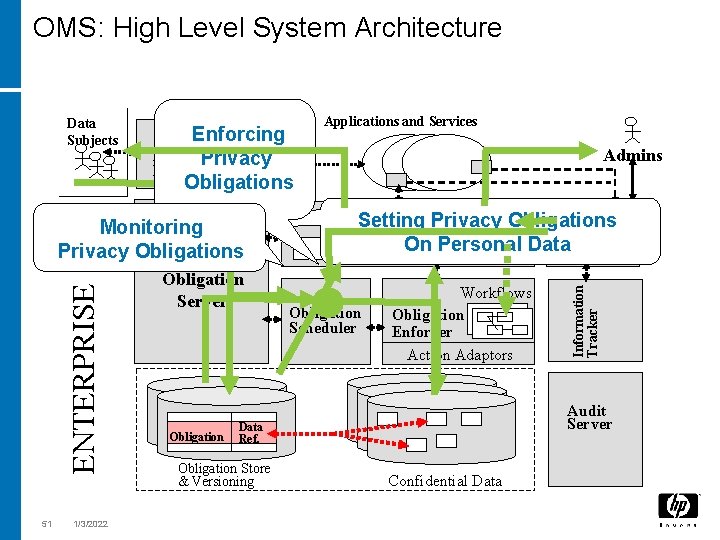
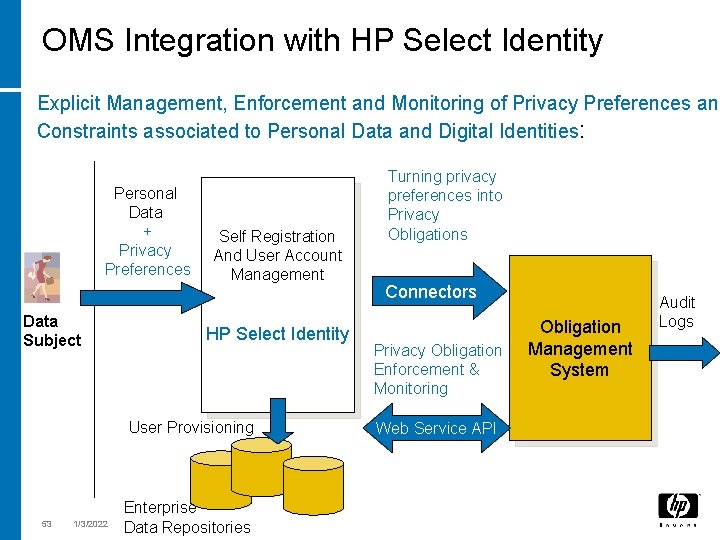
Privacy-Aware Information Lifecycle Management Privacy Obligations dictate Duties and Expectations to Enterprises on How to Handle Personal Data. It is about Privacy-aware Information Lifecycle Mgmt: • Which Privacy Obligations to Manage? How to Represent them? • How to Schedule, Enforce and Monitor Privacy Obligations? • How to Integrate with Identity Management Solutions? Regulations, HP Labs R&D Work • Privacy Obligation Management System Policy Development Standards, Best Practices Reporting • Prototype Integrated with HP Select Identity. IT Alignment • Research in EU PRIME Project Policy Enforcement n io g at il g orin Ob onit M Privac y Obliga tion Enforc ement • Explore its Productisation Transparency Enterprise IT Infrastructure 45 1/3/2022 Monitoring

Privacy Obligation Refinement: Abstract vs. Refined Obligations can be very abstract: “Every financial institution has an affirmative and continuing obligation to respect customer privacy and protect the security and confidentiality of customer information” Gramm-Leach-Bliley Act More refined Privacy Obligations dictate Duties, Expectations and Responsibilities on How to Handle Personal Data: • Notice Requirements • Enforcement of opt-in/opt-out options • Limits on reuse of Information and Information Sharing • Data Retention limitations … 46 1/3/2022

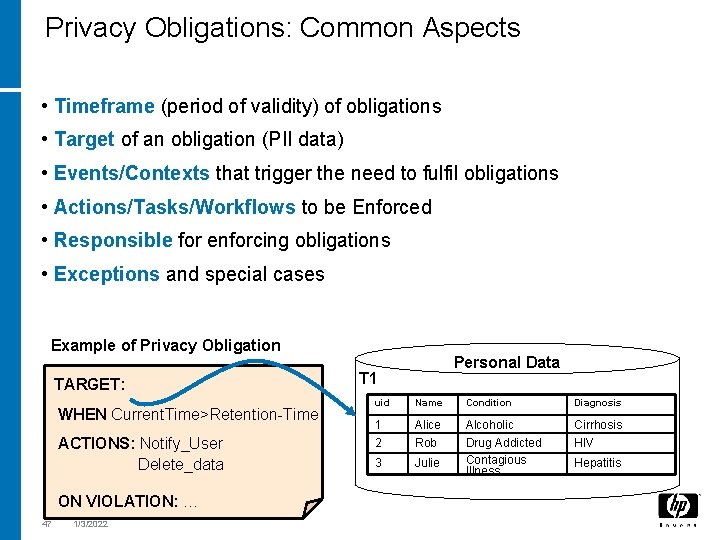
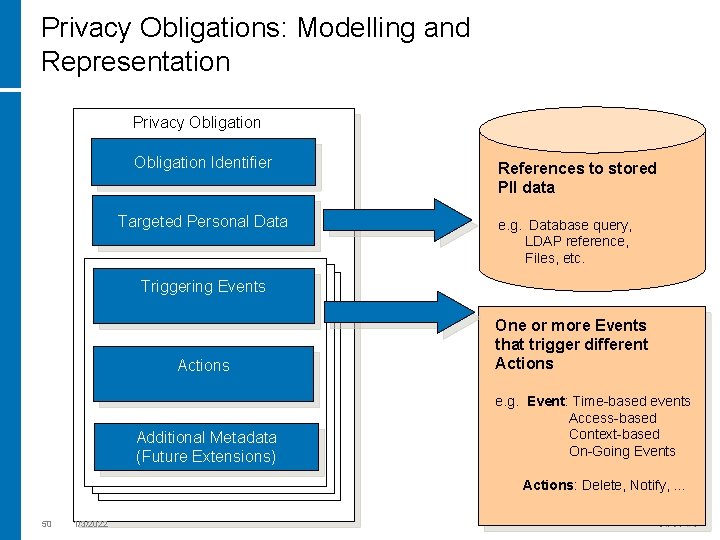
Privacy Obligations: Common Aspects • Timeframe (period of validity) of obligations • Target of an obligation (PII data) • Events/Contexts that trigger the need to fulfil obligations • Actions/Tasks/Workflows to be Enforced • Responsible for enforcing obligations • Exceptions and special cases Example of Privacy Obligation TARGET: WHEN Current. Time>Retention-Time ACTIONS: Notify_User Delete_data ON VIOLATION: … 47 1/3/2022 Personal Data T 1 uid Name Condition Diagnosis 1 2 Alice Rob Cirrhosis HIV 3 Julie Alcoholic Drug Addicted Contagious Illness Hepatitis

Key Requirements • Explicit Modeling and Representation of privacy obligations • (Strong) Association of obligations to data • Mapping obligations into enforceable actions • Compliance of refined obligations to high-level policies • Tracking the evolution of obligation policies • Dealing with Long-term Obligation aspects • Accountability management and auditing • Monitoring obligations • User involvement • Handling Complexity and Cost of instrumenting Apps and Services 48 1/3/2022

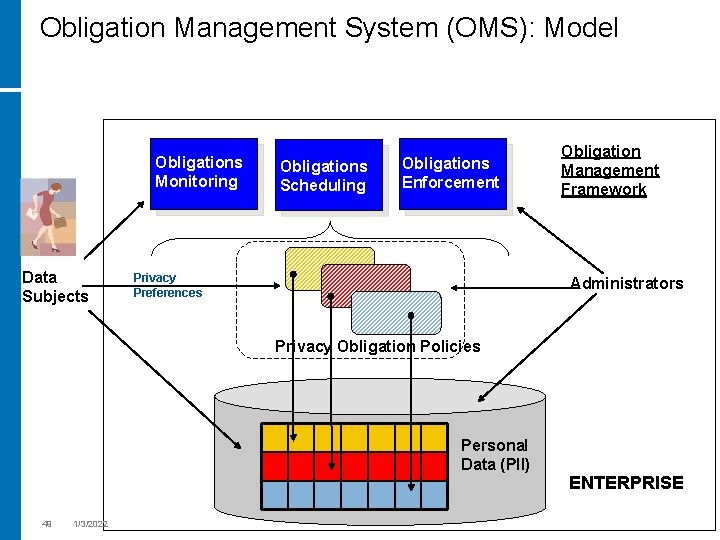
Obligation Management System (OMS): Model Obligations Monitoring Data Subjects Obligations Scheduling Obligations Enforcement Privacy Preferences Obligation Management Framework Administrators Privacy Obligation Policies Personal Data (PII) 49 1/3/2022 ENTERPRISE

Privacy Obligations: Modelling and Representation Privacy Obligation Identifier Targeted Personal Data References to stored PII data e. g. Database query, LDAP reference, Files, etc. Triggering Events Actions Additional Metadata (Future Extensions) One or more Events that trigger different Actions e. g. Event: Time-based events Access-based Context-based On-Going Events Actions: Delete, Notify, … 50 1/3/2022

OMS: High Level System Architecture Enforcing Privacy-enabled Privacy Portal Obligations ENTERPRISE Monitoring Privacy Obligations Admins 51 1/3/2022 Obligation Server Obligation Applications and Services Admins Events Obligation Monitoring Service. Obligations Setting Privacy Handler Data Monitoring. On Task. Personal Handler Obligation Scheduler Workflows Obligation Enforcer Action Adaptors Audit Server Data Ref. Obligation Store & Versioning Information Tracker Data Subjects Confidential Data

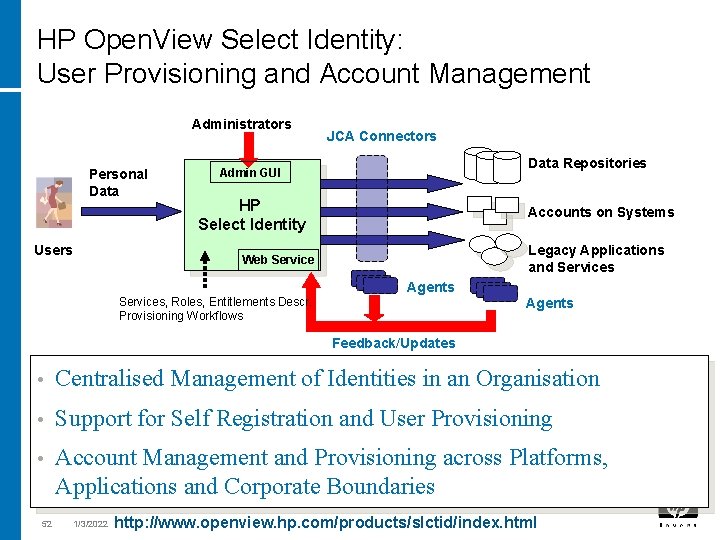
HP Open. View Select Identity: User Provisioning and Account Management Administrators Personal Data Users JCA Connectors Data Repositories Admin GUI HP Select Identity Accounts on Systems Legacy Applications and Services Web Services, Roles, Entitlements Descr. Provisioning Workflows Agents Feedback/Updates • Centralised Management of Identities in an Organisation • Support for Self Registration and User Provisioning • Account Management and Provisioning across Platforms, Applications and Corporate Boundaries 52 1/3/2022 http: //www. openview. hp. com/products/slctid/index. html

OMS Integration with HP Select Identity Explicit Management, Enforcement and Monitoring of Privacy Preferences and Constraints associated to Personal Data and Digital Identities: Personal Data + Privacy Preferences Data Subject Self Registration And User Account Management HP Select Identity User Provisioning 53 1/3/2022 Enterprise Data Repositories Turning privacy preferences into Privacy Obligations Connectors Privacy Obligation Enforcement & Monitoring Web Service API Obligation Management System Audit Logs

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)
![Identity Capable Platforms ICP 12 55 132022 Identity Capable Platforms (ICP) [1/2] 55 1/3/2022](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-55.jpg)
Identity Capable Platforms (ICP) [1/2] 55 1/3/2022
![Identity Capable Platforms ICP 22 Liberty Alliance Initiative http www projectliberty org Focus Identity Capable Platforms (ICP) [2/2] Liberty Alliance Initiative (http: //www. projectliberty. org) • Focus](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-56.jpg)
Identity Capable Platforms (ICP) [2/2] Liberty Alliance Initiative (http: //www. projectliberty. org) • Focus on Federated Identity Management, involving Identity Providers (Id. P) and Service Providers (SPs) • Aiming at specifying: − Identity Capable Platforms (ICP) to allow users to engage in a safe and transparent way • into federated Id. M. Store “Identity Tokens” in a secure and trustworthy environment along with Policies and Manage them − Provisioning Services: extend Liberty Alliance Federated Id. M Standards to safely delegate and provision “Identity Tokens” to ICP • Technology Pilot: HP/HP Labs, BT, Intel • Current Status: Full working prototype and demonstrator (Po. Cv 1) shown at RSA 2007. Moving towards a Po. Cv 2 and technology trial. 56 1/3/2022

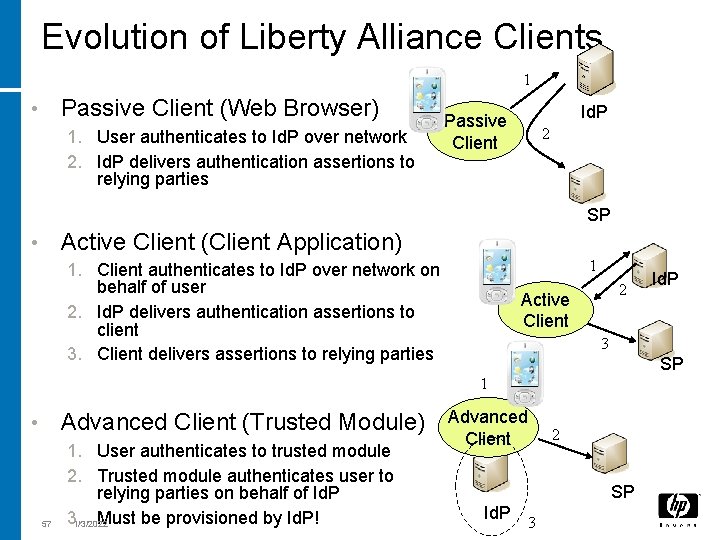
Evolution of Liberty Alliance Clients 1 Passive Client (Web Browser) • 1. User authenticates to Id. P over network 2. Id. P delivers authentication assertions to relying parties Id. P Passive Client 2 SP Active Client (Client Application) • 1 1. Client authenticates to Id. P over network on behalf of user 2. Id. P delivers authentication assertions to client 3. Client delivers assertions to relying parties 2 Active Client 3 SP 1 Advanced Client (Trusted Module) • 57 1. User authenticates to trusted module 2. Trusted module authenticates user to relying parties on behalf of Id. P 3. Must be provisioned by Id. P! 1/3/2022 Id. P Advanced Client 2 SP Id. P 3

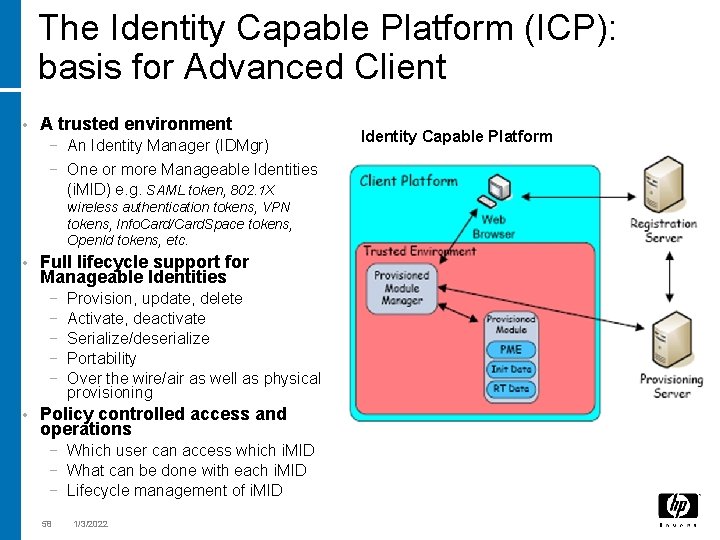
The Identity Capable Platform (ICP): basis for Advanced Client • A trusted environment − An Identity Manager (IDMgr) − One or more Manageable Identities (i. MID) e. g. SAML token, 802. 1 X wireless authentication tokens, VPN tokens, Info. Card/Card. Space tokens, Open. Id tokens, etc. • Full lifecycle support for Manageable Identities − − − • Provision, update, delete Activate, deactivate Serialize/deserialize Portability Over the wire/air as well as physical provisioning Policy controlled access and operations − Which user can access which i. MID − What can be done with each i. MID − Lifecycle management of i. MID 58 1/3/2022 Identity Capable Platform

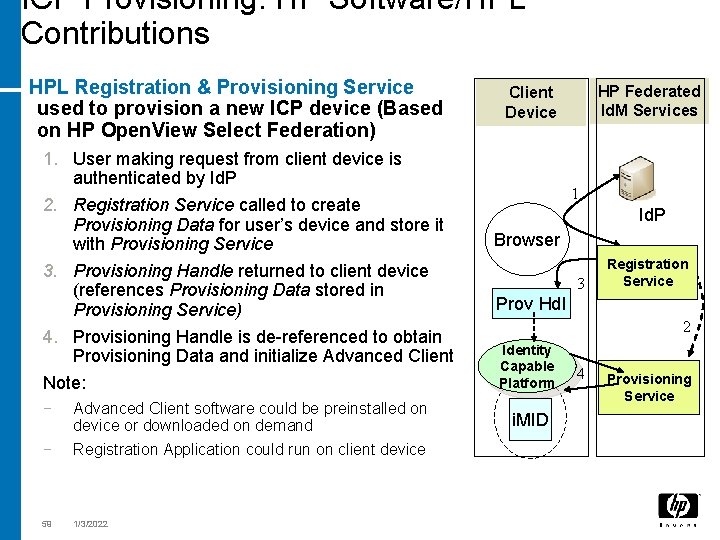
ICP Provisioning: HP Software/HPL Contributions HPL Registration & Provisioning Service used to provision a new ICP device (Based on HP Open. View Select Federation) 1. User making request from client device is authenticated by Id. P 2. Registration Service called to create Provisioning Data for user’s device and store it with Provisioning Service 3. Provisioning Handle returned to client device (references Provisioning Data stored in Provisioning Service) 4. Provisioning Handle is de-referenced to obtain Provisioning Data and initialize Advanced Client Note: − − Advanced Client software could be preinstalled on device or downloaded on demand Registration Application could run on client device 59 1/3/2022 HP Federated Id. M Services Client Device 1 Id. P Browser 3 Registration Service Prov Hdl 2 Identity Capable Platform i. MID 4 Provisioning Service

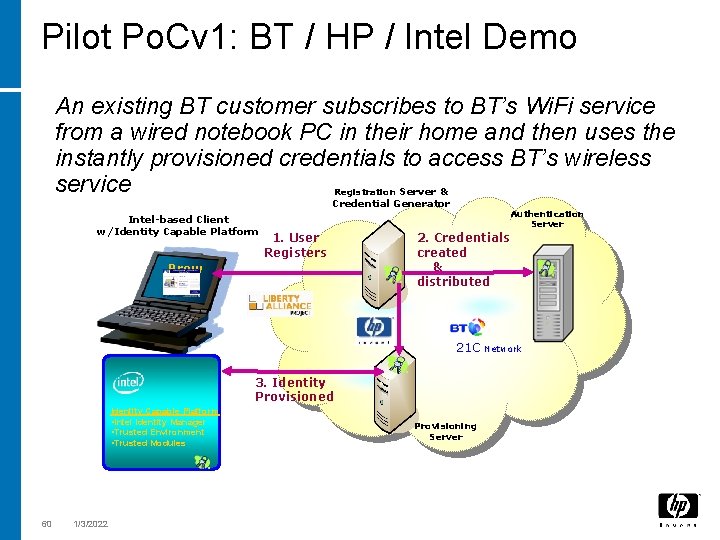
Pilot Po. Cv 1: BT / HP / Intel Demo An existing BT customer subscribes to BT’s Wi. Fi service from a wired notebook PC in their home and then uses the instantly provisioned credentials to access BT’s wireless service Server & Registration Credential Generator Intel-based Client w/Identity Capable Platform 1. User Registers Brow ser+ Authentication Server 2. Credentials created & distributed 21 C 3. Identity Provisioned Identity Capable Platform • Intel Identity Manager • Trusted Environment • Trusted Modules 60 1/3/2022 Provisioning Server Network

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)
![Policy Management Hard Problems and Future Research Areas 15 A Policy Refinement Process Human Policy Management: Hard Problems and Future Research Areas [1/5] A) Policy Refinement Process Human](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-62.jpg)
Policy Management: Hard Problems and Future Research Areas [1/5] A) Policy Refinement Process Human vs. Technological approach to Policies and Policy Management Not Always Policies can be refined to IT Policies/Automated Policies Policy Legal Layer Business Layer Process Layer Application/ Service Layer Information/ Data Layer System/ Device Layer Network Layer 62 1/3/2022 Policy/ Sub-policy • How to achieve Policy Refinement by Balancing Human Processes and Technologies? • How to Address this with a right “blend” of Automation, Decision Support Systems, Collaboration Support Tools, Processes, Feedback Management?
![Policy Management Hard Problems and Future Research Areas 25 B Federated Policy Management in Policy Management: Hard Problems and Future Research Areas [2/5] B) “Federated Policy Management” in](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-63.jpg)
Policy Management: Hard Problems and Future Research Areas [2/5] B) “Federated Policy Management” in Organisations Too many different types of Policies and Policy Management Frameworks Too many controls, inconsistencies, misalignment s negative impact on IT Governance PEP Legal Layer PAP Business Layer Process Layer Application/ Service Layer PEP PDP PAP PIP Information/ Data Layer System/ Device Layer Network Layer 63 1/3/2022 • How to “Federate” various Policy Management ? PDP PEP PIP PDP PAP PIP PEP PDP PAP PIP • How to ensure better IT Governance and compliance to high-level goals? • How, for example, to achieve this in a context of Information Management (so many different types of Data/Information, managed with different tools and solutions)?
![Policy Management Hard Problems and Future Research Areas 35 C Management of Sticky Policies Policy Management: Hard Problems and Future Research Areas [3/5] C) Management of “Sticky Policies”](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-64.jpg)
Policy Management: Hard Problems and Future Research Areas [3/5] C) Management of “Sticky Policies” for Information Flow Information and Data Moves around, within and across organisations. Associated Policies might be lost during this flow or misinterpreted ENTERPRISE • How to Ensure that Policies Stick to data and can be Enforced? • How to provide Assurance? Applications & Services Data PEOPLE • Need for Standards in terms of Policies and Policy Frameworks? Data/Information + “Sticky” Policies ENTERPRISE Applications & Services PEOPLE 64 1/3/2022 Data • Need for Rich Semantic and Upfront Negotiation?
![Policy Management Hard Problems and Future Research Areas 45 D Contentaware Access Control in Policy Management: Hard Problems and Future Research Areas [4/5] D) Content-aware Access Control in](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-65.jpg)
Policy Management: Hard Problems and Future Research Areas [4/5] D) Content-aware Access Control in Collaborative Environments driven by Policies (e. g. Enterprise Web 2. 0) Collaborative content creation and management needs adequate, fine grained access control. Associated Policies might be lost during this flow or misinterpreted • How to deal with fine-grained Request access for parts of a document access control for semi-structured and unstructured data? Injecting data Collaborative Tool Storage (docs & policies) 65 1/3/2022 Request access for entire document • How to factor in Enterprise constraints in terms of confidentiality? • How to provide dynamics, fine-grained views on content?
![Policy Management Hard Problems and Future Research Areas 55 E Other Research Areas Policy Management: Hard Problems and Future Research Areas [5/5] E) Other Research Areas •](https://slidetodoc.com/presentation_image_h2/4f72f8b59fc5aefea26749819d3e00c4/image-66.jpg)
Policy Management: Hard Problems and Future Research Areas [5/5] E) Other Research Areas • Interoperability between Policy Languages • Policy Conflict Detection and Resolution • Policy Violation Detection and Remediation • Rich Semantic for Policies and “Deep” Reasoning • … 66 1/3/2022

Overview • Background on Policy and Policy Management § Policies § Policy Management • Some HPL/TSL R&D in the Policy/Policy Management Space § Enterprise Privacy Management with Id. M Solutions Ø Privacy-Aware Access Control Ø Privacy-Aware Information Lifecycle Management § Identity Capable Platforms (ICP) and Provisioning Services • Some Future R&D Opportunities in the Policy/Policy Management Space • W 3 C Policy Languages Interest Group (PLING)

W 3 C Policy Languages Interest Group (PLING) It is a W 3 C Interest Group on Policies: http: //www. w 3. org/Policy/pling/ Scope: • It is NOT about defining new Policy Languages Too many languages are already there. How to make sense of them? • Explore what the main requirements, obstacles and issues are to have a “joint” deployment of them, to achieve security, privacy, identity management, obligation management, compliance, etc. 68 1/3/2022

W 3 C Policy Languages Interest Group (PLING) It is a W 3 C Interest Group on Policies: http: //www. w 3. org/Policy/pling/ Approach: • Start from real use-cases and requirements (and issues) • Discuss about policy approaches, architectures and frameworks • explore the use of relevant technologies toward delivering interoperability frameworks for policy languages. Deliverables: Discussions, new Requirements and Proposals, Reports and Workshops. No Language Specifications. Next Steps: Start Discussions in mailing list, WWW 2008 Panel (proposal) 69 1/3/2022

W 3 C Policy Languages Interest Group (PLING) It is a W 3 C Interest Group on Policies: http: //www. w 3. org/Policy/pling/ co-Chairs: • Marco Casassa Mont (HPL) • Renato Iannella (NICTA, Australia) How to Get Involved: Subscribe to PLING mailing list (http: //lists. w 3. org/Archives/Public/public-pling/) Opportunity: Steer discussions and outcome in the context of policies and policy management in a way that is relevant to your needs!!! PLEASE SUBSCRIBE AND GET INVOLVED 70 1/3/2022

Additional Material • HPL Projects and Documents on Research on Privacy, Identity Management and Policy Management (see Projects section): http: //www. hpl. hp. com/personal/mcm/ • My Blogs on “Research on Identity Management”: http: //h 20325. www 2. hp. com/blogs/mcm http: //research-on-identitymanagement. blogspot. com/ 71 1/3/2022

Any Question? 72 1/3/2022

 Gerlachovský štít svetadiel
Gerlachovský štít svetadiel Mont godinne ophtalmologie
Mont godinne ophtalmologie Mont saint michel merveille du monde
Mont saint michel merveille du monde Gömlek giyme beceri analizi
Gömlek giyme beceri analizi Mont 107
Mont 107 Patrick evrard mont godinne
Patrick evrard mont godinne Zweideutige logos
Zweideutige logos Prade haute mont dore
Prade haute mont dore Mont hua
Mont hua Samsung mont blanc air conditioner
Samsung mont blanc air conditioner çatalla yemek yeme beceri analizi
çatalla yemek yeme beceri analizi Mont blanc
Mont blanc Moodle mont perdut
Moodle mont perdut Seven hill mont
Seven hill mont 1 mont ago
1 mont ago Tunnel du mont blanc
Tunnel du mont blanc Diferencia de marco conceptual y marco teorico
Diferencia de marco conceptual y marco teorico Introduction to content management systems
Introduction to content management systems Intro to human resource management
Intro to human resource management Management topics for project
Management topics for project Gym management system
Gym management system Rtim real time interaction management
Rtim real time interaction management Management overview
Management overview Peta konsep manajemen ekonomi
Peta konsep manajemen ekonomi Overview of financial management
Overview of financial management What is multinational financial management
What is multinational financial management Chapter 1 an overview of financial management
Chapter 1 an overview of financial management An overview of financial management
An overview of financial management Hse risk management framework
Hse risk management framework Advanced group policy management
Advanced group policy management Environmental management system in tcs
Environmental management system in tcs Sipdm
Sipdm Policy based network management
Policy based network management Public policy and management corvinus
Public policy and management corvinus Enterprise policy management
Enterprise policy management Ibrahim askar
Ibrahim askar Fmom
Fmom What is hr policies
What is hr policies Dividend policy decision in financial management
Dividend policy decision in financial management Emos os
Emos os Dividend policy decision in financial management
Dividend policy decision in financial management Change management proposal template
Change management proposal template Top management middle management first line management
Top management middle management first line management Management pyramid
Management pyramid Top management and middle management
Top management and middle management Www overview
Www overview Maximo overview
Maximo overview Universal modeling language
Universal modeling language Uml overview
Uml overview Vertical retail
Vertical retail Figure 12-1 provides an overview of the lymphatic vessels
Figure 12-1 provides an overview of the lymphatic vessels Major veins of the body
Major veins of the body Texas recapture districts
Texas recapture districts Walmart company overview
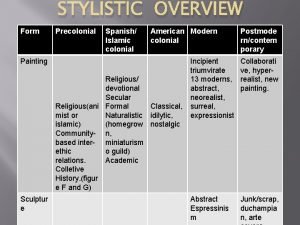
Walmart company overview Stylistic overview of painting
Stylistic overview of painting Sa/sd
Sa/sd Spring framework overview
Spring framework overview Nagios tactical overview
Nagios tactical overview Market overview managed file transfer solutions
Market overview managed file transfer solutions Nfv vs sdn
Nfv vs sdn Sbic program overview
Sbic program overview Quota sap
Quota sap Ariba registration process
Ariba registration process Safe overview
Safe overview Rfid technology overview
Rfid technology overview Overview in research example
Overview in research example Perbedaan replikasi virus dna dan rna
Perbedaan replikasi virus dna dan rna Example of a project overview
Example of a project overview Venous drainage of the abdomen
Venous drainage of the abdomen Is abstract a summary
Is abstract a summary Solvency 2 pillar 2
Solvency 2 pillar 2 What is physical storage
What is physical storage Overview of education in health care
Overview of education in health care Marcus scheuren
Marcus scheuren