Information Security Management Information Security Management Goal The


















- Slides: 26

Information Security Management

Information Security Management- Goal The goal of the Information Security process is to align IT security with business security and ensure that information security is effectively managed in all service and Service Management activities. This goal is divided between: • Meeting external security requirements • Meeting internal security requirements

Scope To ensure that the confidentiality, integrity and availability of an organization’s assets, information, data and IT services is maintained, Information Security Management must consider the following four perspectives: Organizational Physical Procedural Technical

Value ISM ensures that an Information Security Policy is maintained and enforced that fulfils the needs of the Business Security Policy and the requirements of corporate governance. ISM raises awareness of the need for security within all IT services and assets throughout the organization, ensuring that the policy is appropriate for the needs of the organization.

Basic Concepts - Terminology confidentiality integrity availability security baseline security incident

Information Security Management Security • ensure such a level of security, that the agreed availability of the infrastructure is not compromised. • study the security demand • study the security possibilities • security regarding 3 rd parties (e. g. suppliers) • study the risks of security • draw up a security strategy CRAMM

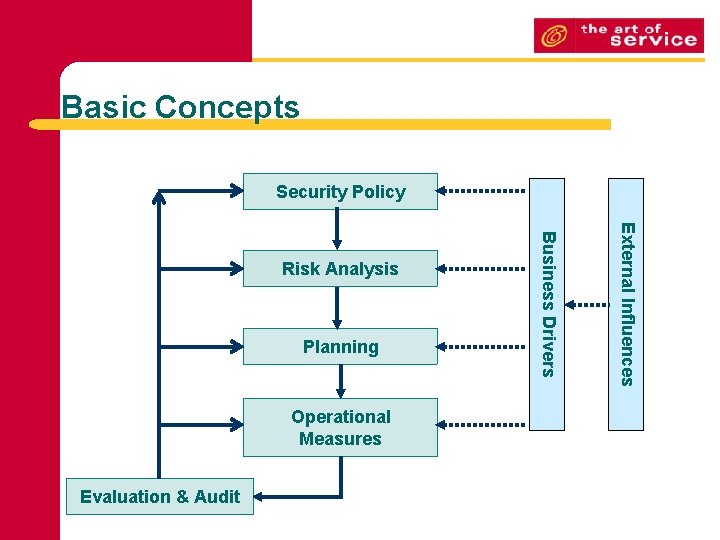
Basic Concepts Security Policy Operational Measures Evaluation & Audit External Influences Planning Business Drivers Risk Analysis

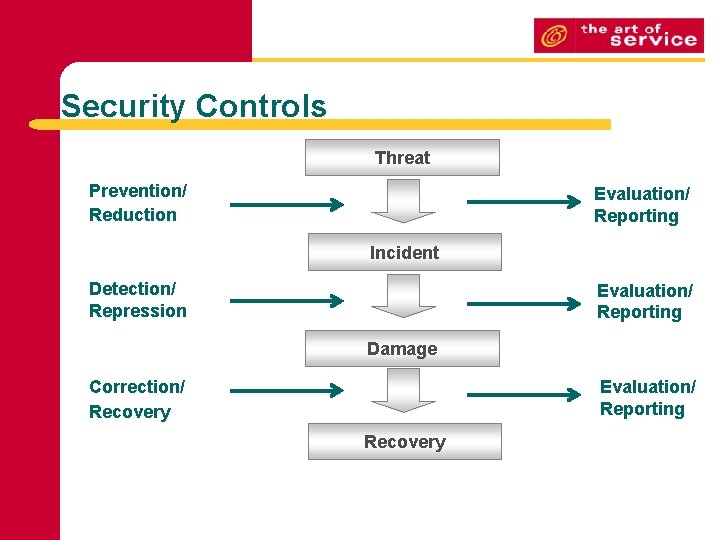
Security Controls Threat Prevention/ Reduction Evaluation/ Reporting Incident Detection/ Repression Evaluation/ Reporting Damage Correction/ Recovery Evaluation/ Reporting Recovery

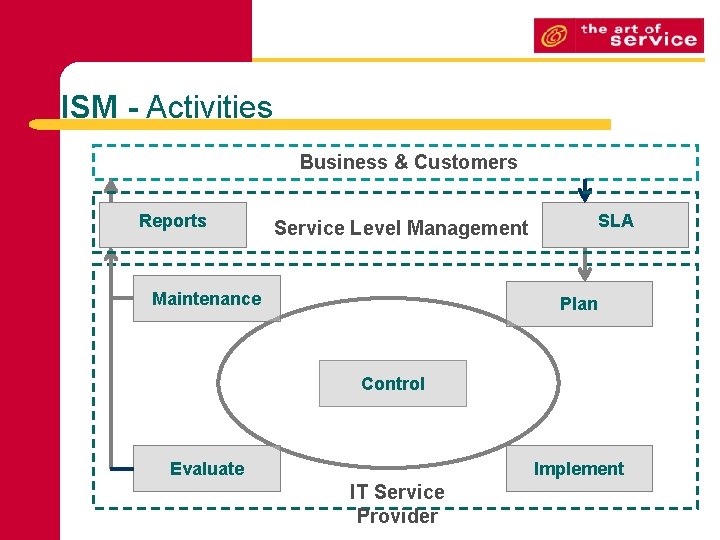
ISM - Activities Business & Customers Reports Service Level Management Maintenance SLA Plan Control Evaluate Implement IT Service Provider

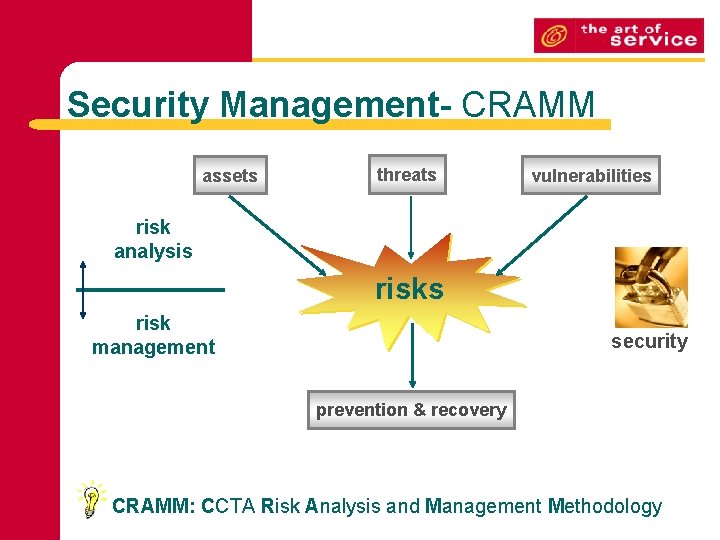
Security Management- CRAMM assets threats vulnerabilities risk analysis risk management security prevention & recovery CRAMM: CCTA Risk Analysis and Management Methodology

Information Security Management Steering: policy and organization of securing information • Policy • develop and implement policy • awareness campaign: the goal, the common principles and the importance placed on security • determine the sub processes • determine responsibilities and authorities • determine the relationships with other ITIL-processes • how to deal with security incidents

Information Security Management Steering: policy and organization of securing information • organization • set up organization structure and management frame • allocate responsibilities and authorities • choose tools (for e. g. risk analysis) • implement the “Taskforce Information Security” TIS • coordination of securing information (and providing specialist advice) • ensure independent audits (EDP-audits) • ensure information security in 3 rd party contracts • ensure physical and logical access security regarding 3 rd parties

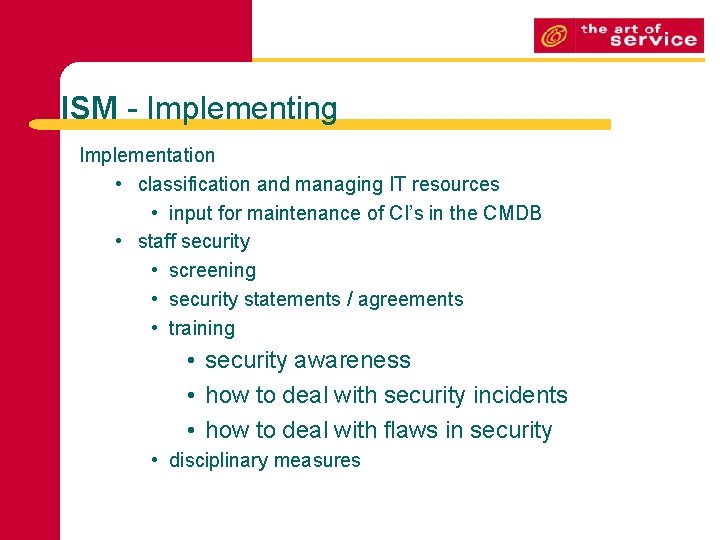
ISM - Implementing Implementation • classification and managing IT resources • input for maintenance of CI’s in the CMDB • staff security • screening • security statements / agreements • training • security awareness • how to deal with security incidents • how to deal with flaws in security • disciplinary measures

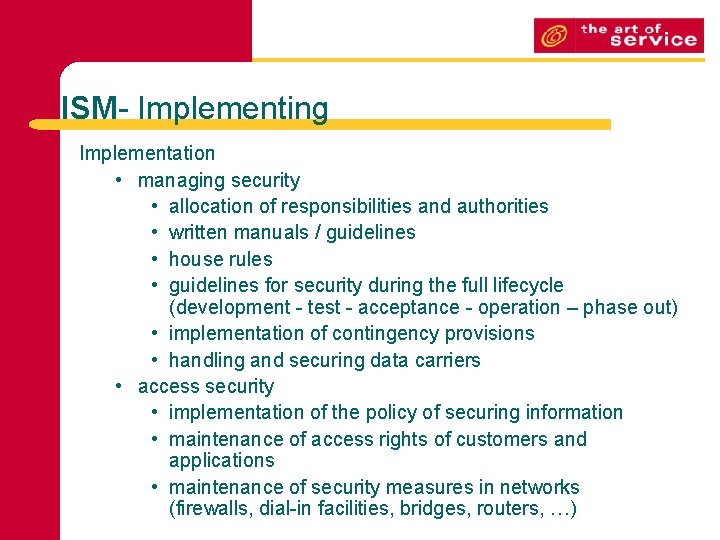
ISM- Implementing Implementation • managing security • allocation of responsibilities and authorities • written manuals / guidelines • house rules • guidelines for security during the full lifecycle (development - test - acceptance - operation – phase out) • implementation of contingency provisions • handling and securing data carriers • access security • implementation of the policy of securing information • maintenance of access rights of customers and applications • maintenance of security measures in networks (firewalls, dial-in facilities, bridges, routers, …)

ISM - Evaluation (audit & evaluation) • self assessments • are mainly carried out by the business processes themselves • internal audits • by internal EDP-auditors • external audits • by external (independent) EDP-auditors • verification of the security policy • verification of security plans • evaluate security incidents • detect and react to unwanted use of IT resources

ISM - Maintenance • of both the SLA (the security paragraph) as well as the OLAs • is based on the results of the sub process “Evaluate” and insight in changing risks • proposes changes to be carried out: • in the sub process “Plan” • in the regular SLA maintenance • the changes go through Change Management !!!

ISM - Reporting • on sub process “Plan” • degree of confirmation to SLAs (including CPIs on security) • status of (and possible problems with): - OLAs - Underpinning Contracts - security year plans / action plans • on sub process “Implementation” • status accounting • regarding the implementation of securing information • regarding the awareness campaign on securing information • account of security incidents and the reactions • trend analysis regarding security incidents

ISM - Reporting • on sub process “Evaluation” • results of audits, reviews and internal assessments • warnings about and identification of new threats • specific reports • with the individual customer agreed SLA-reports • procedures regarding communication in special (unforseen) situations

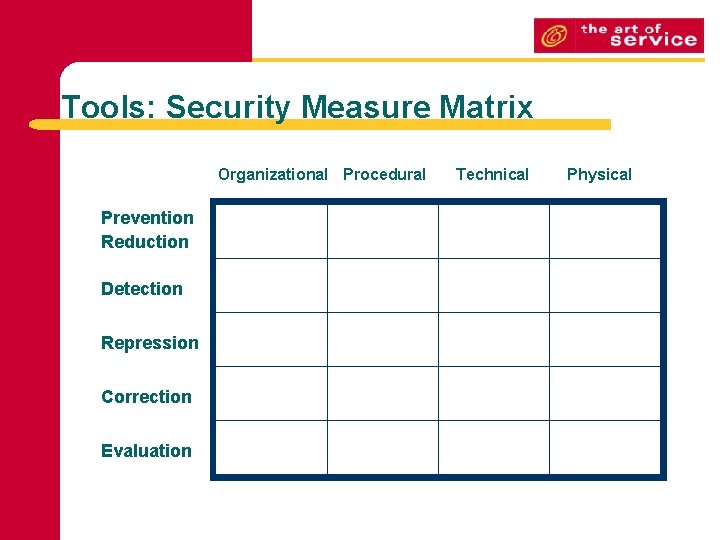
Tools: Security Measure Matrix Organizational Procedural Prevention Reduction Detection Repression Correction Evaluation Technical Physical

ISM - Roles, Responsibilities and Skills Security Manager § Responsibilities: - Manage entire security process, - consult with senior management § Skills: - Strategic, - sense of PR, tactical Security Officer § Responsibilities: - Day to day operational duties, - advise staff on security policy & measures § Skills: - analytical, eye for detail, consultancy

Inputs & Outputs Inputs: • Business information • Corporate governance and business security policy • IT information • Service information • Risk analysis processes and reports • Details of all security events and breaches • Change information • Details of partner and supplier access.

Inputs & Outputs: • Overall ISM policy • Security Management Information System • Revised security risk assessments • Set of security controls • Security audits and audit reports • Security test schedules and plans • Security classifications • Review and reports of security breaches and major incidents • Policies, processes and procedures for managing partners and suppliers and their access to services and information.

KPI’s § § § Business protected against security violations Determination of clear and agreed policy Security procedures are justified A mechanism for improvement Integral part of all IT and ITSM processes Effective marketing and education

ISM - Challenges • Management commitment • Staff commitment • Low priority compared to current work issues • Weak or non-existing Business Security Management (& Plan) • Conducting thorough testing of countermeasures

CSF’s • Business protected against security violations • Determination of a clear and agreed policy, integrated with the needs of the business • Security procedures that are justified • Effective marketing and education in security requirements • Mechanism for improvement • Information security is an integral part of all IT services and all ITSM processes • Availability of services is not compromised by security incidents • Clear ownership and awareness of the security policies amongst the customer community.

Risks • Lack of commitment from the business to the ISM processes and procedures • Lack of commitment from the business and lack of of appropriate information on future plans and strategies • Lack of senior management commitment or lack of resources and/or budget for the ISM process • The process focus too much on the technology issues and not enough on the IT services and the needs and priorities of the business. • Risk assessment and management is conducted in isolation and not in conjunction with Availability Management and ITSCM. • ISM policies, plans, risks and information become