How to Avoid Hiring Unauthorized Workers Protecting Vital





















- Slides: 38

How to Avoid Hiring Unauthorized Workers: Protecting Vital Interests with Absolute Validation of Personal Identifiers Chuck Salvia Computer Information Development LLC

Why Worry? • I-9 errors and employment of unauthorized workers can lead to massive liability • You need to be aware of ways to minimize risk © 2011 Computer Information Development, LLC

Recent ICE enforcement trends • Recent ICE (Immigration and Customs Enforcement ) Investigations ►Not hesitant to fine for minor errors ►Less willing to negotiate/settle than in past ►Large inspection center allows for large-scale audits • 2, 200+ I-9 inspections in FY 2010 (up from 500 in 2008) • Civil penalties exceeded $5 M in FY 2010 (up from less than $700 K in 2008) © 2011 Computer Information Development, LLC

Potential fines, criminal sanctions, and other liability I-9 Related (Civil) Penalties Paperwork (I-9) Violations $110 - $1, 100 per I-9, depending on the company’s history of violations Knowingly hiring, recruiting, referring for a fee, or continuing to employ an unauthorized worker $375 - $16, 000 per worker, depending on the company’s history of violations Document Abuse $110 - $1, 100 per employee Unfair immigration-related employment practices (discrimination based on national origin or citizenship status) $375 - $16, 000 per employee, depending on the history of violations, plus back pay Document Fraud (knowingly forging, counterfeiting, altering, using, possessing, obtaining, accepting, or receiving a falsely made document for purposes of satisfying I-9 requirements) $275 - $6, 500 per violation, depending on the history of violations. © 2011 Computer Information Development, LLC

Criminal Penalties • Pattern or practice of “knowingly” hiring or continuing to employ unauthorized workers – Fines of up to $3, 000 per individual – Up to 6 months in prison – This is in addition to, not instead of, civil penalties • Harboring/trafficking also carry criminal penalties © 2011 Computer Information Development, LLC

Options to Avoid Hiring Unauthorized Workers • Form I-9 • E-Verify • SSNVS (Social Security Number Verification Service) • CBSV (Consent Based Social Security Number Verification) © 2011 Computer Information Development, LLC

Options to Avoid Hiring Unauthorized Workers • Form I-9 • Administered by Department of Homeland Security / U. S. Citizenship and Immigration Service – “Free” – Legal requirement – Remains on file unless requested by government – Electronic I-9 s can provide additional peace of mind… and additional risks, depending on the vendor • Limit errors • Complex regulations © 2011 Computer Information Development, LLC

Options to Avoid Hiring Unauthorized Workers • E-Verify • Operated by Dept of Homeland Security in partnership with SSA – “Free” – Optional for most employers, required for some – Only to be used for new hires (some exceptions for federal government contractors/subcontractors) – Sends I-9 information to government – Checks for inconsistencies with government databases

Options to Avoid Hiring Unauthorized Workers • SSNVS (Social Security Number Verification Service) • Administered by the Social Security Administration – “Free” – Optional – Only to be used for post-hire wage reporting purposes – Matches SSN and certain bio information with SSA databases © 2011 Computer Information Development, LLC

Options to Avoid Hiring Unauthorized Workers • CBSV (Consent Based SSN Verification Service) • Administered by the Social Security Administration – Fee-based – Optional – May be used for any purpose, so long as the individual consents to the query and the purpose therefore – Matches name, SSN, DOB, gender and death indicator with SSA Master File © 2011 Computer Information Development, LLC

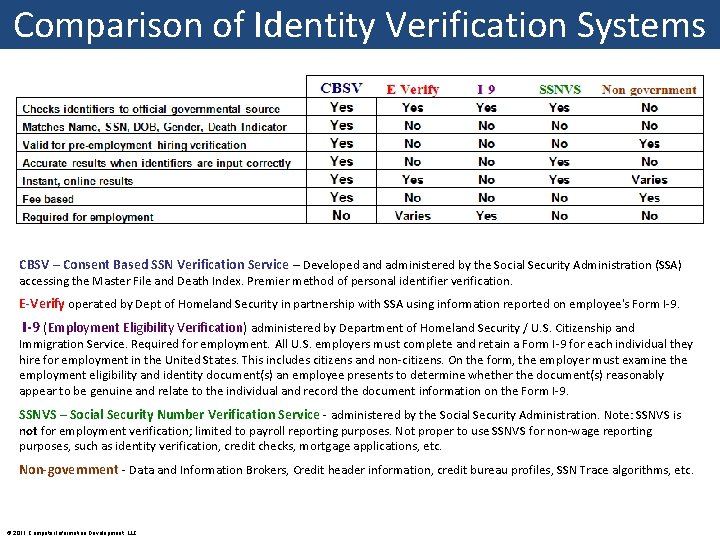
Comparison of Identity Verification Systems CBSV – Consent Based SSN Verification Service – Developed and administered by the Social Security Administration (SSA) accessing the Master File and Death Index. Premier method of personal identifier verification. E-Verify operated by Dept of Homeland Security in partnership with SSA using information reported on employee's Form I-9 (Employment Eligibility Verification) administered by Department of Homeland Security / U. S. Citizenship and Immigration Service. Required for employment. All U. S. employers must complete and retain a Form I-9 for each individual they hire for employment in the United States. This includes citizens and non-citizens. On the form, the employer must examine the employment eligibility and identity document(s) an employee presents to determine whether the document(s) reasonably appear to be genuine and relate to the individual and record the document information on the Form I-9. SSNVS – Social Security Number Verification Service - administered by the Social Security Administration. Note: SSNVS is not for employment verification; limited to payroll reporting purposes. Not proper to use SSNVS for non-wage reporting purposes, such as identity verification, credit checks, mortgage applications, etc. Non-government - Data and Information Brokers, Credit header information, credit bureau profiles, SSN Trace algorithms, etc. © 2011 Computer Information Development, LLC

What is CBSV? • Developed and administered by the Social Security Administration • Matches a Name, SSN, Date of Birth, Gender and Death Indicator to data in SSA’s Master File and Death Index • Pilot began in 2002; current version launched November 2008 • Real-time online verification and handles large volume requests • Used for all business verification purposes and compliance requirements Employment (both pre- and post-hire), Applicants of all sorts (customers, patients, students, tenants), Loan originations, Fraud investigations, Collections, Risk Management, Reduction of losses and net charge-offs • Requires signed consent of Applicant/SSN holder on Form SSA-89 • Used for the specific business purpose designated on the SSA-89 © 2011 Computer Information Development, LLC

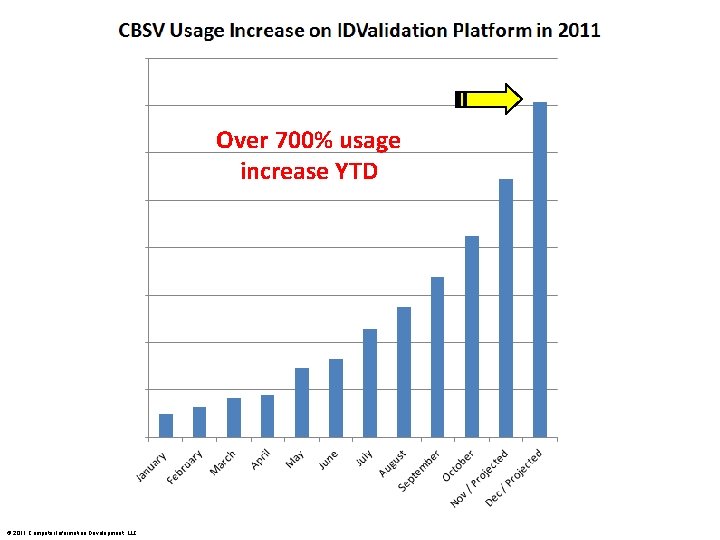
Over 700% usage increase YTD © 2011 Computer Information Development, LLC

Protecting Vital Interests CBSV validates to SSA source records It safeguards your company by shielding losses as it mitigates the risks of fraud and identity theft It strengthens, enhances, and purifies your verification due diligence processes with direct access to SSA Master File and Death Index as it validates personal identifiers © 2011 Computer Information Development, LLC

Ways to Access CBSV • Use the service of a CBSV enrolled company • Avoid costs and burdens of direct enrollment • Direct enrollment through SSA • $5, 000. 00 non-refundable enrollment fee • Required annual CPA audit (SSA estimated at $8, 000. 00) • Upfront payment for the estimated number of CBSV searches for the entire year at the current SSA $1. 05 per search fee • Safeguarding and storage of the documents • Other various duties and liabilities • Optional: Build interface to SSA Master File (SSA estimated $200, 000. 00) © 2011 Computer Information Development, LLC

Who Uses CBSV? • HR Departments for employment verification (both pre and post-hire) • Creditors (Lenders, Banks, Credit Unions, Insurance companies, Retail) • Landlords for tenant screening • Health Care providers to verify patient identity • Higher Education to verify student applicants • Any and all other legitimate verification purposes © 2011 Computer Information Development, LLC

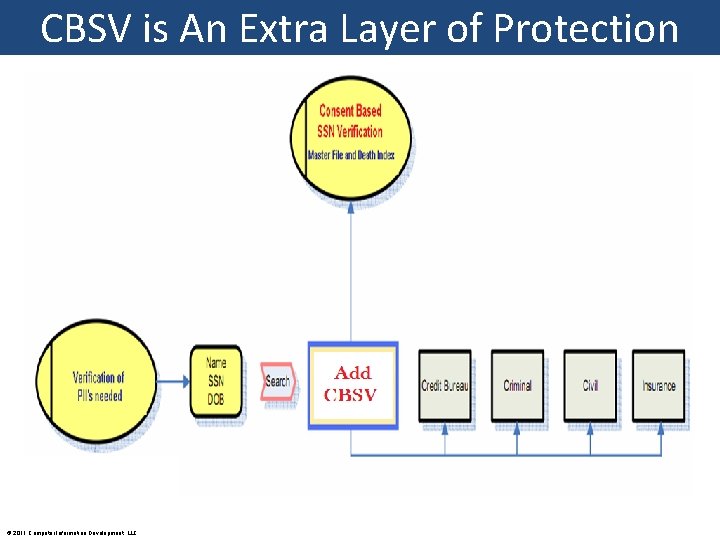
CBSV is An Extra Layer of Protection © 2011 Computer Information Development, LLC

Why is CBSV so Important? Bottom line: It thwarts fraud and identity theft where other verification methods fail © 2011 Computer Information Development, LLC

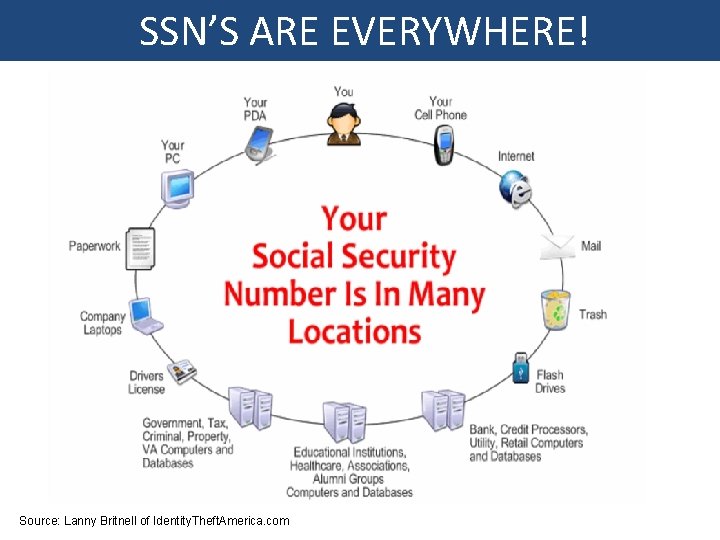
SSN’S ARE EVERYWHERE! Source: Lanny Britnell of Identity. Theft. America. com

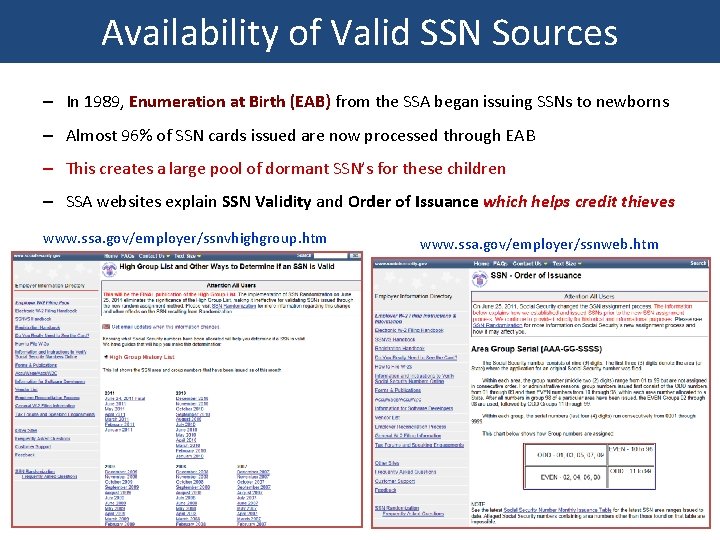
Availability of Valid SSN Sources – In 1989, Enumeration at Birth (EAB) from the SSA began issuing SSNs to newborns – Almost 96% of SSN cards issued are now processed through EAB – This creates a large pool of dormant SSN’s for these children – SSA websites explain SSN Validity and Order of Issuance which helps credit thieves www. ssa. gov/employer/ssnvhighgroup. htm www. ssa. gov/employer/ssnweb. htm

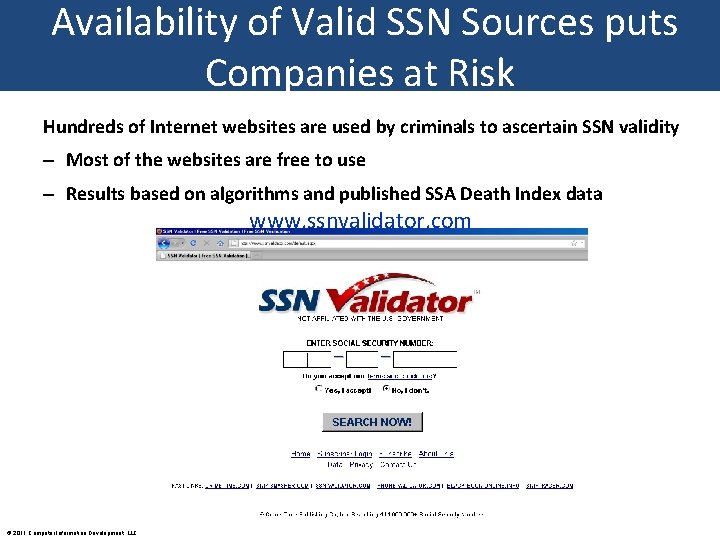
Availability of Valid SSN Sources puts Companies at Risk Hundreds of Internet websites are used by criminals to ascertain SSN validity – Most of the websites are free to use – Results based on algorithms and published SSA Death Index data www. ssnvalidator. com © 2011 Computer Information Development, LLC

Synthetic Name Fraud SSN integrity has been severely compromised in credit bureau profiles and other trusted authorities. Synthetic Name Fraud is using one’s own name, date of birth and address with another persons SSN. This creates a new, fraudulent credit profile that trusted authorities share with each other as genuine. Also known as Synthetic Identity Fraud, this threat causes “piggy-backing” in credit bureau profiles. In 2007, the Federal Trade Commission said… there are over 10 million more credit profiles in the system than there are consumers! Why attempt to "verify” in pools of polluted profile information? © 2011 Computer Information Development, LLC

How Many Minors Have Been Hired Today? This ID thief lived 14 years with a stolen SSN from a 3 year old boy slain in 1982, passed a criminal background check and worked as a sworn investigator for the Oregon Liquor Control Commission. The identity of Jason Robert Evers was stolen by Doitchin Krastev. He was sentenced in January 2011 Source: http: //www. katu. com/news/local/114718969. html Published: Jan 27, 2011 © 2011 Computer Information Development, LLC

The Elephant in the Room It’s BIG, has been ignored and gone unaddressed! Have you heard of Credit Profile Numbers? © 2011 Computer Information Development, LLC

Start a New Credit Profile with a CPN Credit thieves have re-named stolen/fabricated SSN’s by calling them Credit Profile (or Credit Privacy) Numbers (CPN) The SSA’s Enumeration at Birth (EAB) creates a large pool of dormant SSN’s for credit thieves to draw from Unsuspecting children may not need to use their SSN until they apply for a job, credit, or college and find that a credit thief has stolen their identity Have you seen the headlines? © 2011 Computer Information Development, LLC

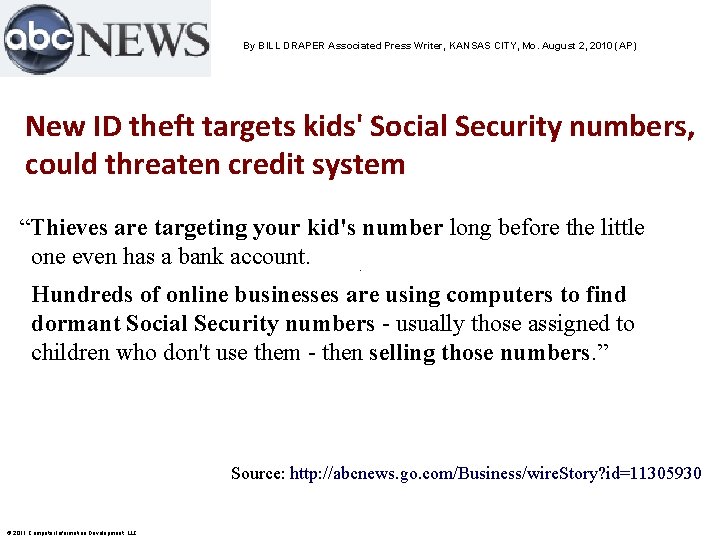
By BILL DRAPER Associated Press Writer, KANSAS CITY, Mo. August 2, 2010 (AP) New ID theft targets kids' Social Security numbers, could threaten credit system “Thieves are targeting your kid's number long before the little one even has a bank account. Hundreds of online businesses are using computers to find dormant Social Security numbers - usually those assigned to children who don't use them - then selling those numbers. ” Source: http: //abcnews. go. com/Business/wire. Story? id=11305930 © 2011 Computer Information Development, LLC

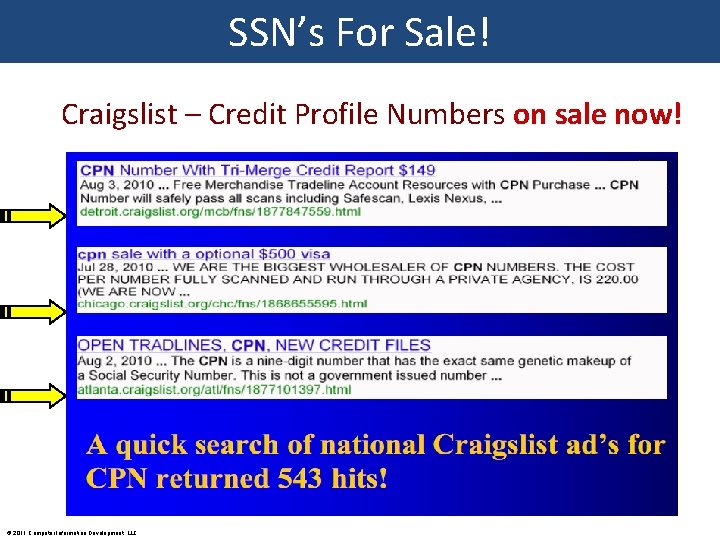
SSN’s For Sale! Craigslist – Credit Profile Numbers on sale now! © 2011 Computer Information Development, LLC

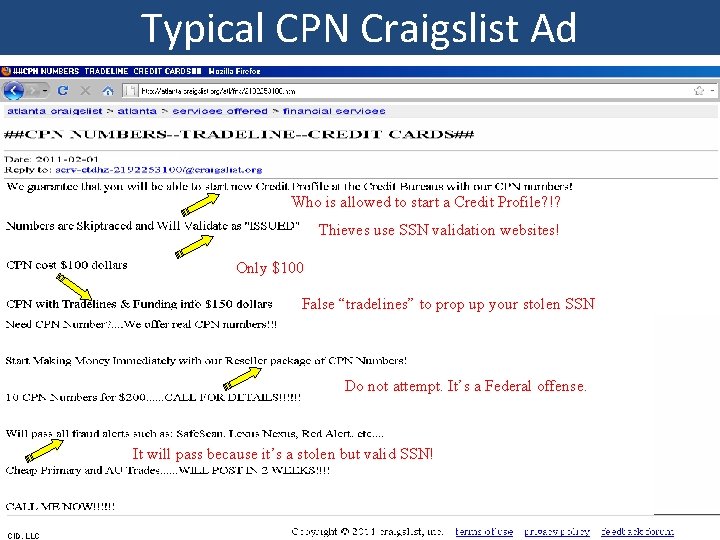
Typical CPN Craigslist Ad Who is allowed to start a Credit Profile? !? Thieves use SSN validation websites! Only $100 False “tradelines” to prop up your stolen SSN Do not attempt. It’s a Federal offense. It will pass because it’s a stolen but valid SSN! CID, LLC

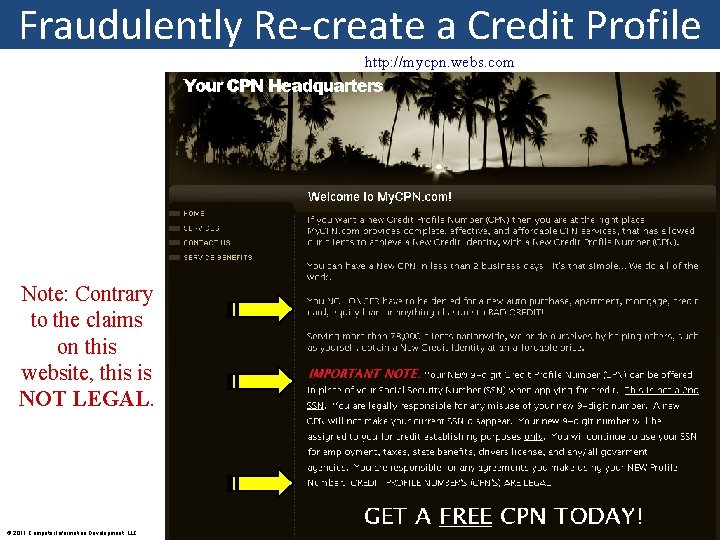
Fraudulently Re-create a Credit Profile http: //mycpn. webs. com Note: Contrary to the claims on this website, this is NOT LEGAL. © 2011 Computer Information Development, LLC

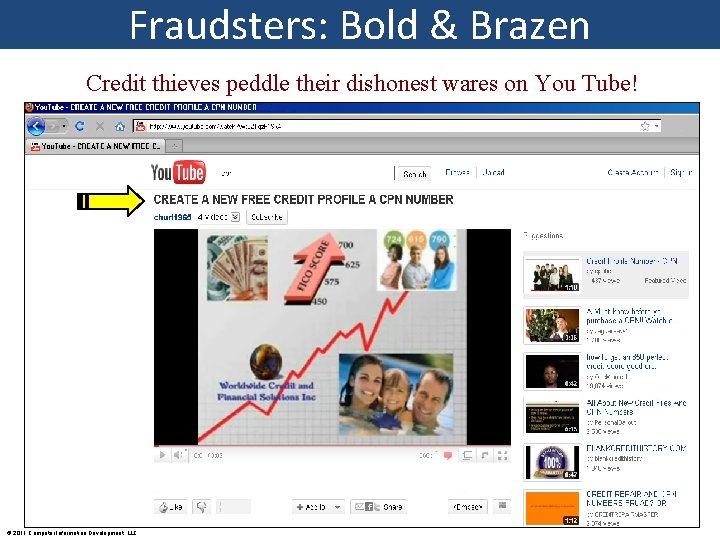
Fraudsters: Bold & Brazen Credit thieves peddle their dishonest wares on You Tube! © 2011 Computer Information Development, LLC

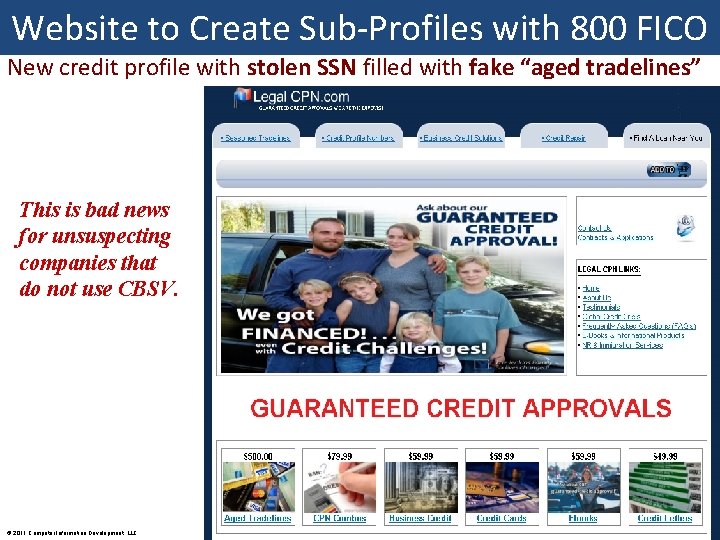
Website to Create Sub-Profiles with 800 FICO New credit profile with stolen SSN filled with fake “aged tradelines” This is bad news for unsuspecting companies that do not use CBSV. © 2011 Computer Information Development, LLC

SSN Randomization – Changing SSN’s

SSN Randomization Has Changed Everything • Random SSNs began June 25, 2011 to extend the longevity in all states • SSN no longer linked to “State of Issuance” or High Group list (frozen) • Eliminates geographical significance of the first three digits of the SSN • SSN Trace algorithms will no longer be useful for SSNs issued after June 25, 2011 • Not just for Enumeration At Birth; legal immigrants, domestic violence victims, and in extremely rare cases, victims of identity theft • Previously unassigned area numbers will be introduced for assignment excluding area numbers 000, 666 and 900 -999 • Criminals will attempt to exploit this situation • SSN Randomization is having an impact on U. S. businesses © 2011 Computer Information Development, LLC http: //www. ssa. gov/employer/randomization. html

Complacency - The Real Threat § 45 Million people in the U. S. deliberately manipulate their identities That’s 16 Percent of U. S. population engage in improper Identity Manipulation says ID Analytics § Carnegie Mellon University reports vulnerabilities of being able to properly “guess” an SSN § Over 20 million Americans have multiple SSN’s associated with their names. 40 Million SSN’s associated with multiple people, 6. 1% have at least 2 SSN’s associated with their name (ID Analytics) § FTC says 500, 000 people under the age of 18 are victims of ID theft every year - many more cases go unreported © 2011 Computer Information Development, LLC

In Compliance with Internal, State and Federal Requirements • FTC’s Red Flags Rule for creditors (FACTA) • Patriot Act - Know Your Customer Section 326 • CIP and Identity Theft Prevention Program (ITPP) • Dodd-Frank Wall Street Reform and Consumer Protection Act • And other requirements The use of CBSV strengthens all compliance policies © 2011 Computer Information Development, LLC

FACTA Regulation 315 Some businesses are responsible for ensuring the transmittal of accurate data! © 2011 Computer Information Development, LLC

CBSV: Absolute Validation Methodology False credit profiles and “cross pollution” of personal identifier data within trusted authorities requires extreme caution in the use of these resources to validate customer identities Current methodologies have exposed vulnerabilities which has led to major increases in Synthetic Name Fraud Absolute Validation can only be obtained from the source with the identifiers of Name, SSN, Date of Birth, Gender, and Death Indicator The Absolute Validation Methodology is Consent Based SSN Verification © 2011 Computer Information Development, LLC

Thank you for attending! Questions? Chuck Salvia csalvia@IDValidation. net (956) 457 -4116 Computer Information Development LLC http: //www. IDValidation. net © 2011 Computer Information Development, LLC