Field Supervisor First Supervisor Outline 1 2 3














![Main Reference n [Brunelli et al, 1995] R. Brunelli, and D. Falavigna, "Personal identification Main Reference n [Brunelli et al, 1995] R. Brunelli, and D. Falavigna, "Personal identification](https://slidetodoc.com/presentation_image_h/a4d952d752e9d6a411c4a8ccdb916ac2/image-41.jpg)
- Slides: 41

Field Supervisor First Supervisor

Outline 1. 2. 3. 4. 5. The Basics Biometric Technologies Multi-model Biometrics Performance Metrics Biometric Applications

Section I: The Basics n n n Why Biometric Authentication? Frauds in industry Identification vs. Authentication

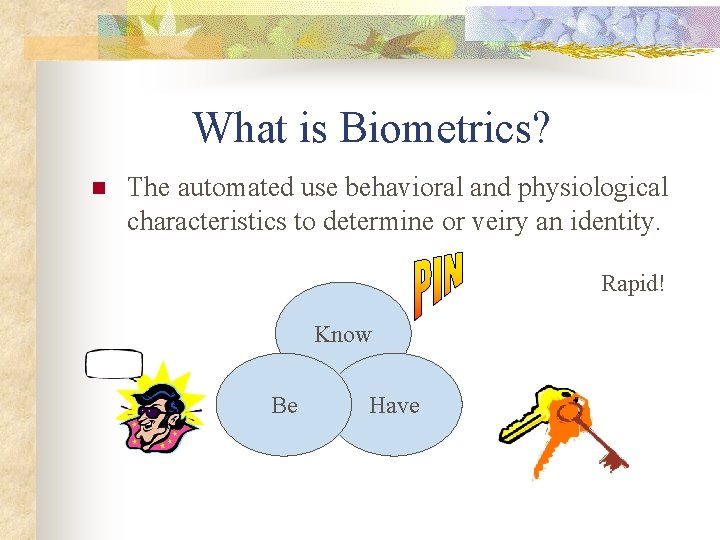
What is Biometrics? n The automated use behavioral and physiological characteristics to determine or veiry an identity. Rapid! Know Be Have

Frauds in industry happens in the following situations: n n n n n Safety deposit boxes and vaults Bank transaction like ATM withdrawals Access to computers and emails Credit Card purchase Purchase of house, car, clothes or jewellery Getting official documents like birth certificates or passports Obtaining court papers Drivers licence Getting into confidential workplace writing Checks

Why Biometric Application? n n n To prevent stealing of possessions that mark the authorised person's identity e. g. security badges, licenses, or properties To prevent fraudulent acts like faking ID badges or licenses. To ensure safety and security, thus decrease crime rates

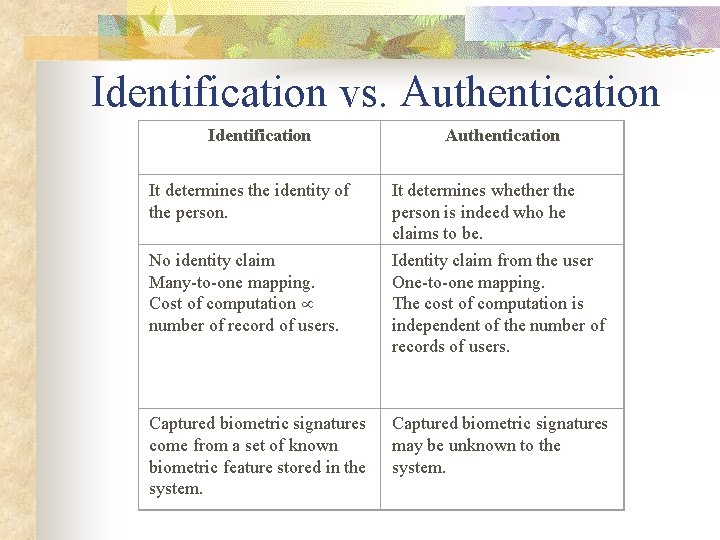
Identification vs. Authentication Identification It determines the identity of the person. No identity claim Many-to-one mapping. Cost of computation number of record of users. Captured biometric signatures come from a set of known biometric feature stored in the system. Authentication It determines whether the person is indeed who he claims to be. Identity claim from the user One-to-one mapping. The cost of computation is independent of the number of records of users. Captured biometric signatures may be unknown to the system.

Section II: Biometric Technologies n n n Several Biometric Technologies Desired Properties of Biometrics Comparisons

Types of Biometrics n n n n Fingerprint Face Recognition Session III Hand Geometry Iris Scan Voice Scan Session II Signature Retina Scan Infrared Face and Body Parts Keystroke Dynamics Gait Odour Ear DNA

Biometrics 2 D Biometrics (CCD, IR, Laser, Scanner) 1 D Biometrics

Fingerprint

Fingerprint Extraction and Matching

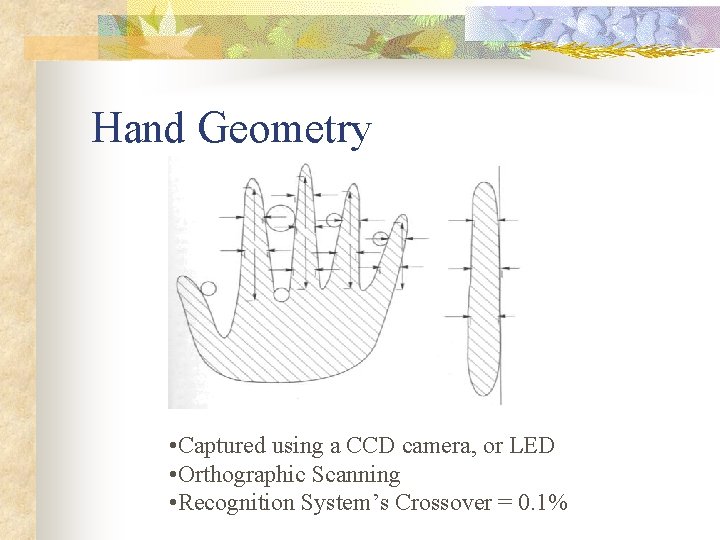
Hand Geometry • Captured using a CCD camera, or LED • Orthographic Scanning • Recognition System’s Crossover = 0. 1%

Iris. Code

Face Principal Component Analysis

Desired Properties n n n n Universality Uniqueness Permanence Collectability Performance User’s Accpetability Robustness against Circumvention

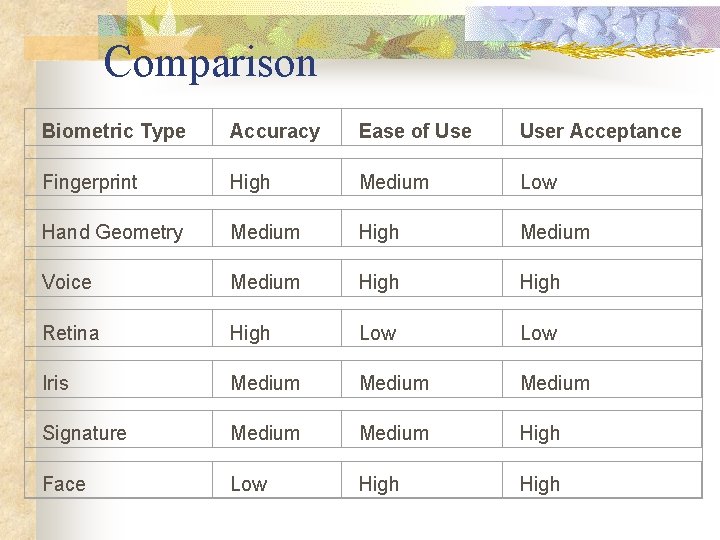
Comparison Biometric Type Accuracy Ease of User Acceptance Fingerprint High Medium Low Hand Geometry Medium High Medium Voice Medium High Retina High Low Iris Medium Signature Medium High Face Low High

Section III: A Multi-model Biometrics n n n Multi-modal Biometrics Pattern Recognition Concept A Prototype

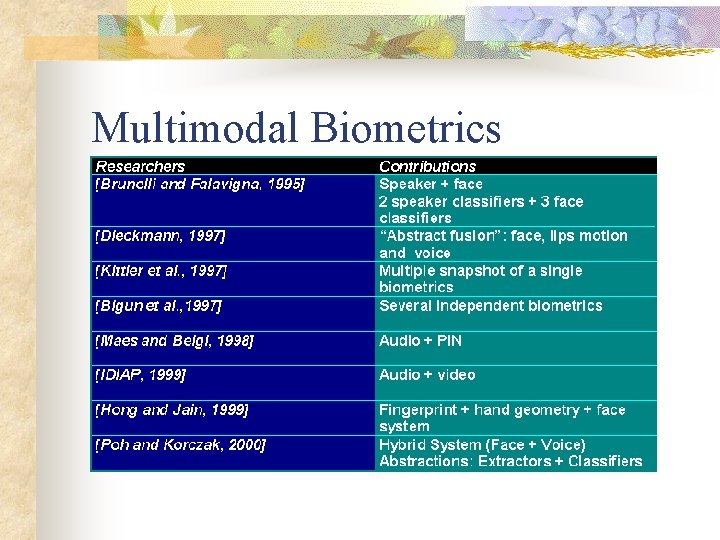
Multimodal Biometrics

Pattern Recognition Concept Sensors Extractors Image- and signal- pro. algo. Biometrics Data Rep. Voice, signature acoustics, face, fingerprint, iris, hand geometry, etc 1 D (wav), 2 D (bmp, tiff, png) Classifiers Negotiator Threshold Feature Vectors Enrolment Scores Training Submission Decision: Match, Non-match, Inconclusive

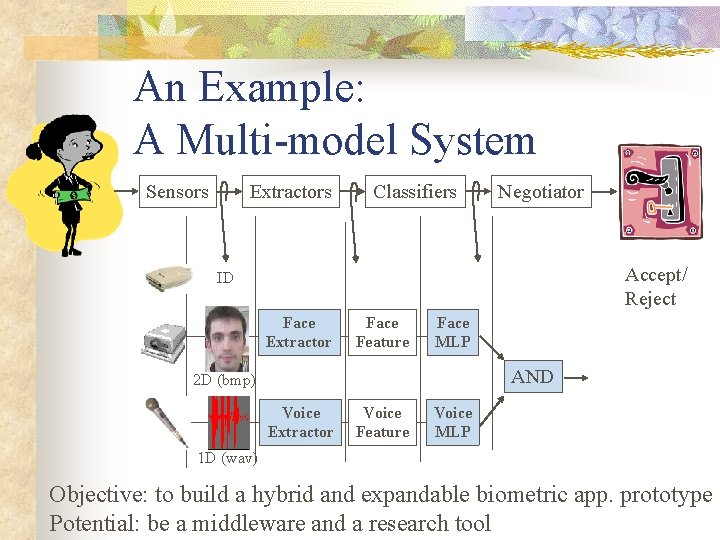
An Example: A Multi-model System Sensors Extractors Classifiers Negotiator Accept/ Reject ID Face Extractor Face Feature Face MLP AND 2 D (bmp) Voice Extractor Voice Feature Voice MLP 1 D (wav) Objective: to build a hybrid and expandable biometric app. prototype Potential: be a middleware and a research tool

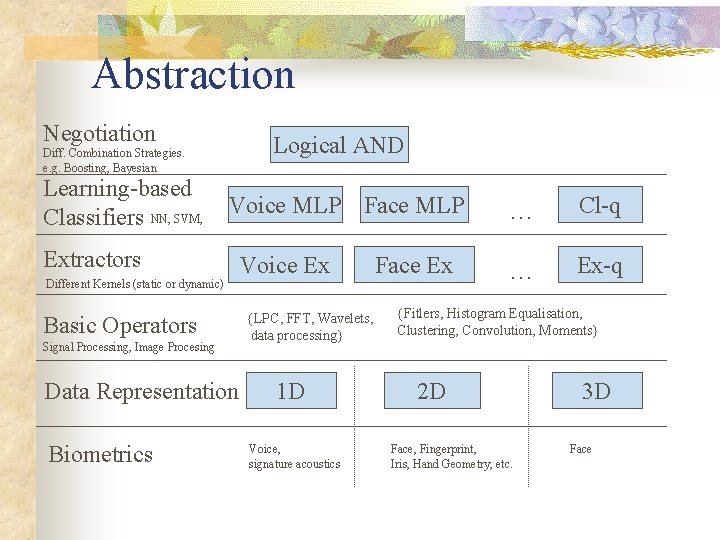
Abstraction Negotiation Logical AND Diff. Combination Strategies. e. g. Boosting, Bayesian Learning-based Classifiers NN, SVM, Voice MLP Face MLP Extractors Different Kernels (static or dynamic) Basic Operators Signal Processing, Image Procesing Data Representation Biometrics Voice Ex {LPC, FFT, Wavelets, data processing} 1 D Voice, signature acoustics Face Ex … Cl-q … Ex-q {Fitlers, Histogram Equalisation, Clustering, Convolution, Moments} 2 D Face, Fingerprint, Iris, Hand Geometry, etc. 3 D Face

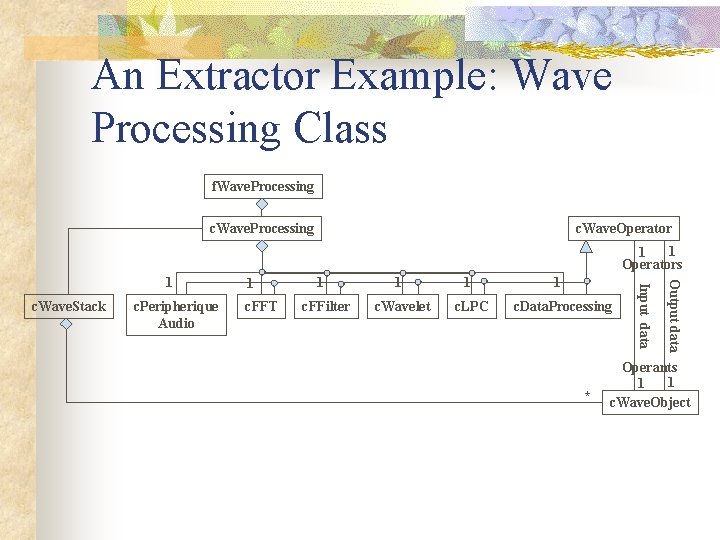
An Extractor Example: Wave Processing Class f. Wave. Processing c. Wave. Operator 1 1 Operators c. Peripherique Audio c. FFT 1 c. FFilter 1 c. Wavelet 1 c. LPC 1 c. Data. Processing * Output data c. Wave. Stack 1 Input data 1 Operants 1 1 c. Wave. Object

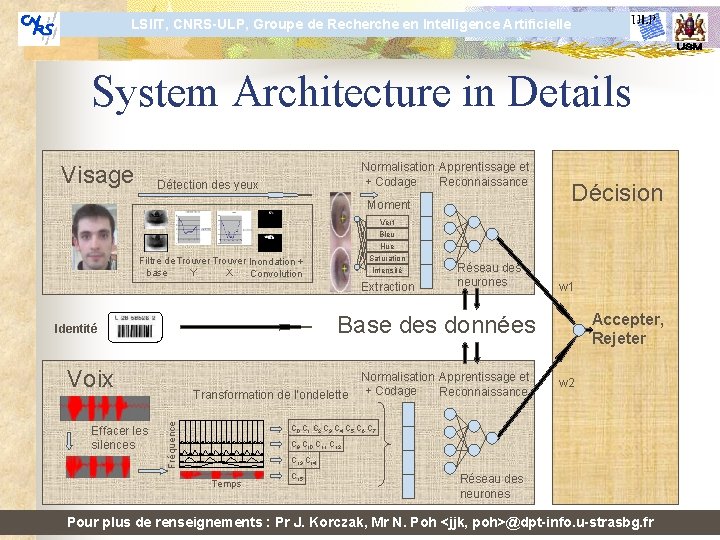
LSIIT, CNRS-ULP, Groupe de Recherche en Intelligence Artificielle System Architecture in Details Visage Normalisation Apprentissage et + Codage Reconnaissance Détection des yeux Moment Décision Vert Bleu Hue Saturation Filtre de Trouver Inondation + base Y X Convolution Intensité Extraction w 1 Accepter, Rejeter Base des données Identité Voix Transformation de l’ondelette Fréquence Effacer les silences Réseau des neurones Normalisation Apprentissage et + Codage Reconnaissance w 2 C 0 C 1 C 2 C 3 C 4 C 5 C 6 C 7 C 9 C 10 C 11 C 12 C 13 C 14 Temps C 15 Réseau des neurones Pour plus de renseignements : Pr J. Korczak, Mr N. Poh <jjk, poh>@dpt-info. u-strasbg. fr

Section IV: Performance Metrics n n n Confusion Matrix FAR and FRR Distributed Analysis Threshold Analysis Receiver Operating Curve

Testing and Evaluation: Confusion Matrix ID-1 ID-2 ID-3 0. 98 0. 01 0. 05 Correct 0. 01 0. 90 0. 78 Wrong Cl-2 … … … Threshold = 0. 50 Cl-3 … … … Cl-1 False Accepts False Rejects

A Few Definitions EER is where FAR=FRR Crossover = 1 : x Where x = round(1/EER) Failure to Enroll, FTE Ability to Verify, ATV = 1 - (1 -FTE) (1 -FRR)

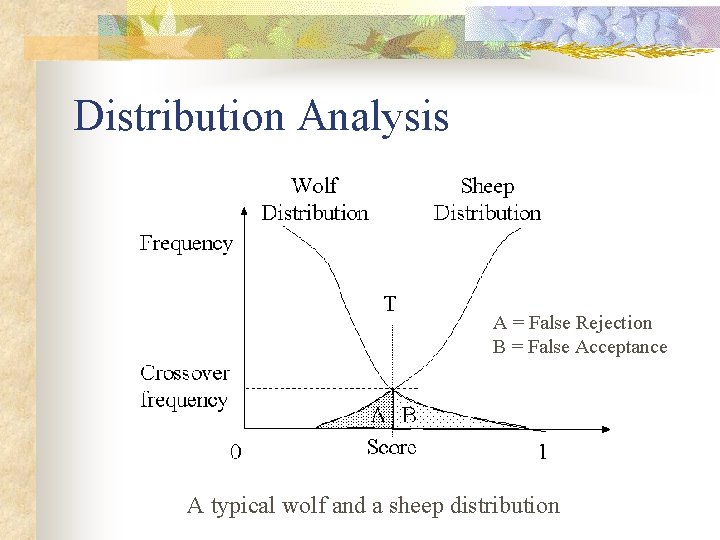
Distribution Analysis A = False Rejection B = False Acceptance A typical wolf and a sheep distribution

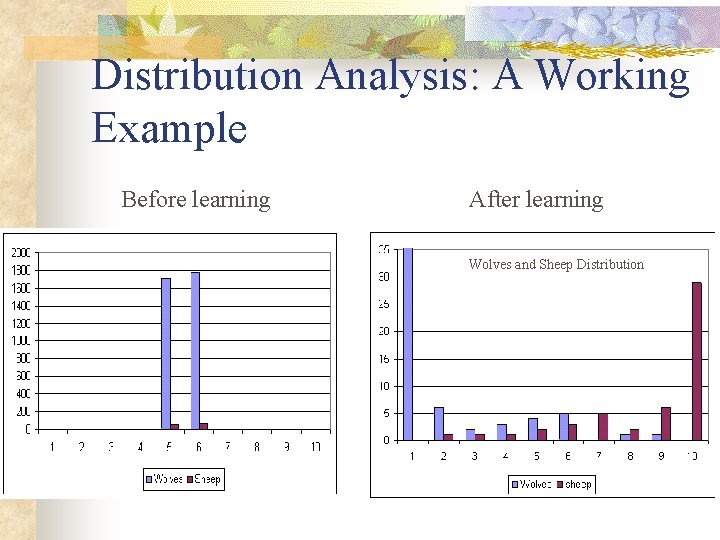
Distribution Analysis: A Working Example Before learning After learning Wolves and Sheep Distribution

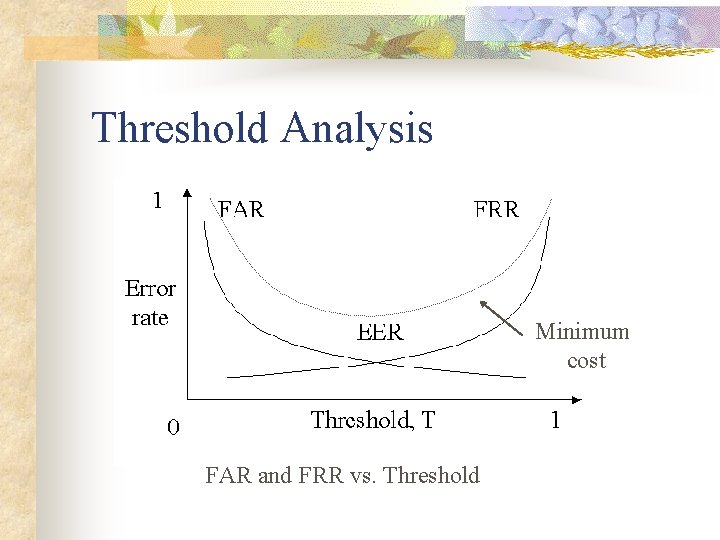
Threshold Analysis Minimum cost FAR and FRR vs. Threshold

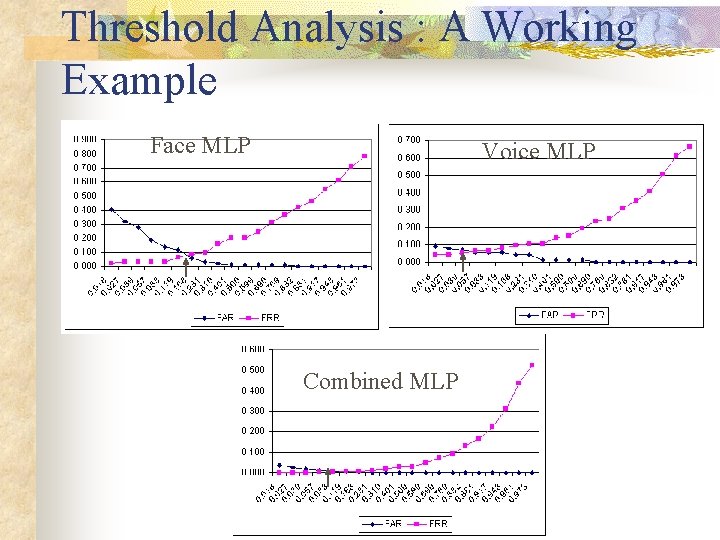
Threshold Analysis : A Working Example Face MLP Voice MLP Combined MLP

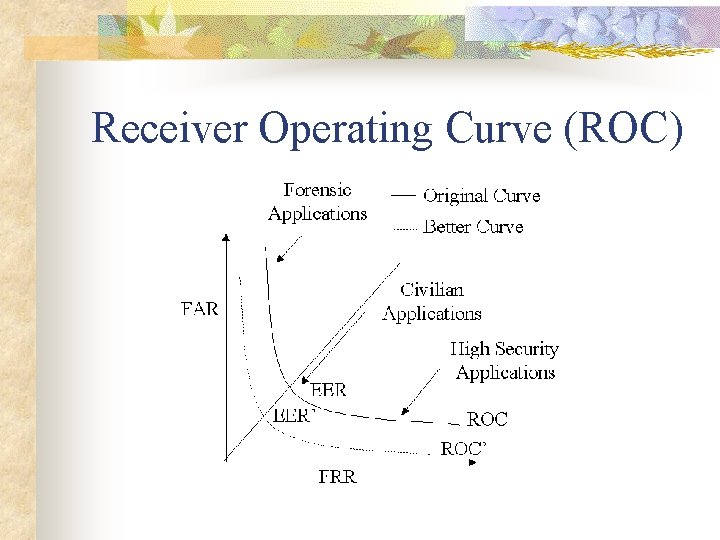
Receiver Operating Curve (ROC)

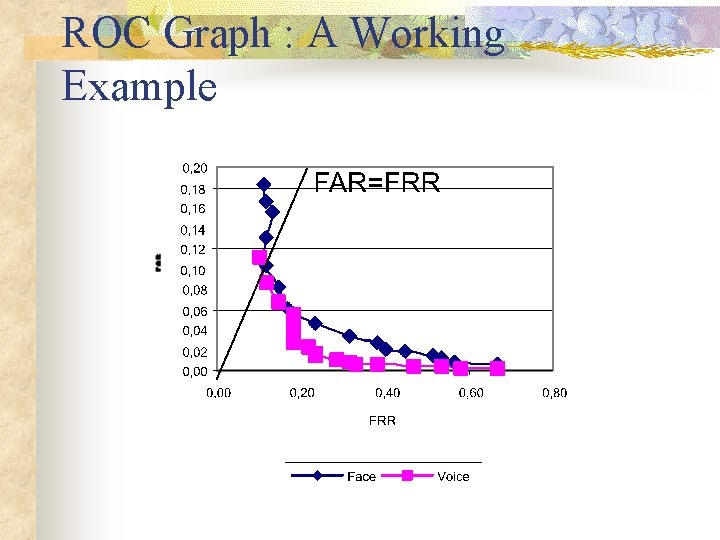
ROC Graph : A Working Example

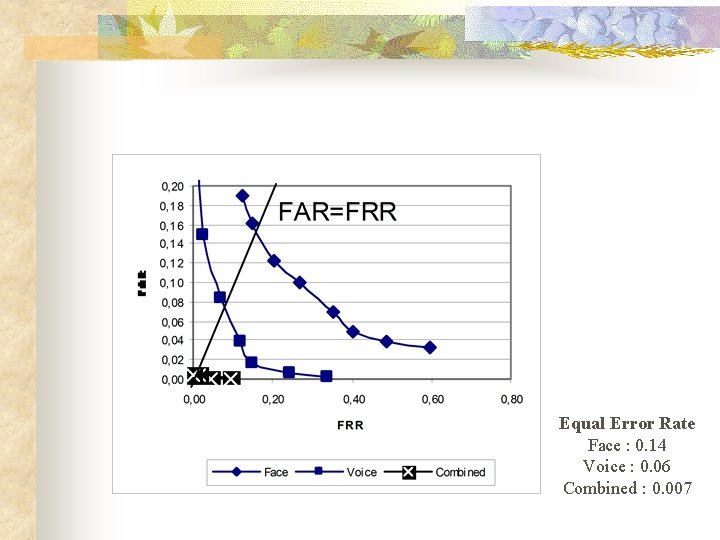
Equal Error Rate Face : 0. 14 Voice : 0. 06 Combined : 0. 007

Section V: Applications n n Authentication Applications Identification Applications Application by Technologies Commercial Products

Biometric Applications Ø Identification or Authentication (Scalability)? Ø Semi-automatic or automatic? Ø Subjects cooperative or not? Ø Storage requirement constraints? Ø User acceptability?

Biometrics-enabled Authentication Applications 1. Cell phones, Laptops, Work Stations, PDA & Handheld device set. 2. 2. Door, Car, Garage Access 3. 3. ATM Access, Smart card Image Source : http: //www. voice-security. com/Apps. html

Biometrics-enabled Identification Applications 1. Forensic : Criminal Tracking 1. e. g. Fingerprints, DNA Matching 2. Car park Surveillance 3. Frequent Customers Tracking

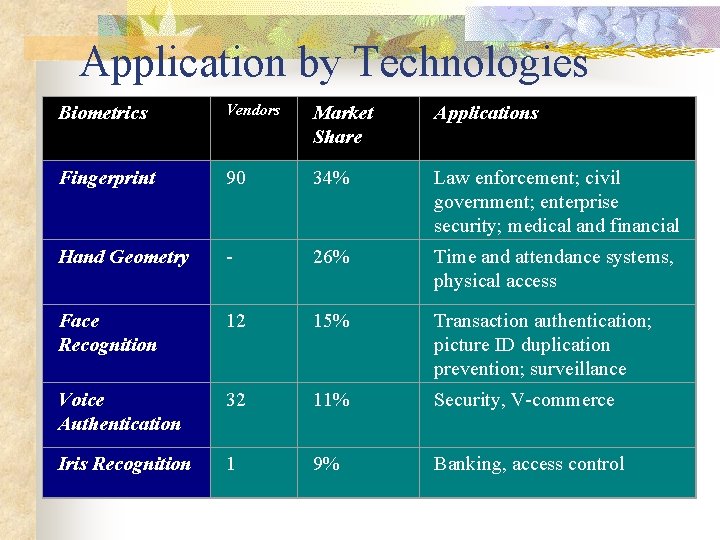
Application by Technologies Biometrics Vendors Market Share Applications Fingerprint 90 34% Hand Geometry - 26% Law enforcement; civil government; enterprise security; medical and financial transactions Time and attendance systems, physical access Face Recognition 12 15% Transaction authentication; picture ID duplication prevention; surveillance Voice Authentication 32 11% Security, V-commerce Iris Recognition 1 9% Banking, access control

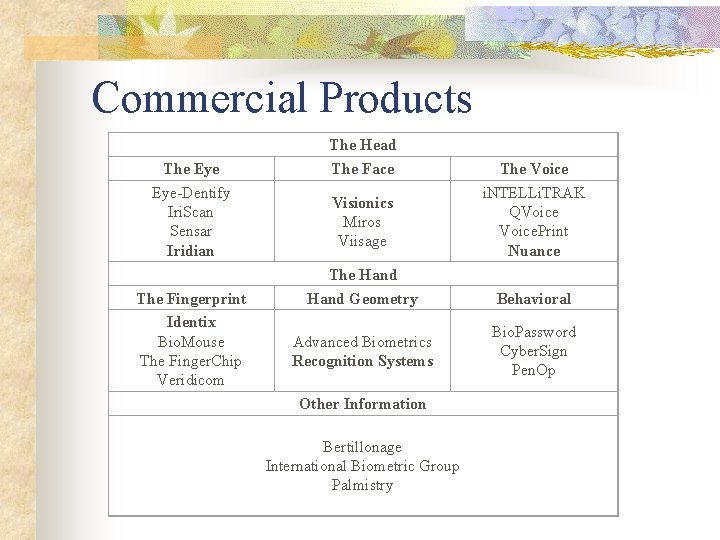
Commercial Products The Eye-Dentify Iri. Scan Sensar Iridian The Fingerprint Identix Bio. Mouse The Finger. Chip Veridicom The Head The Face Visionics Miros Viisage The Hand Geometry Advanced Biometrics Recognition Systems Other Information Bertillonage International Biometric Group Palmistry The Voice i. NTELLi. TRAK QVoice. Print Nuance Behavioral Bio. Password Cyber. Sign Pen. Op
![Main Reference n Brunelli et al 1995 R Brunelli and D Falavigna Personal identification Main Reference n [Brunelli et al, 1995] R. Brunelli, and D. Falavigna, "Personal identification](https://slidetodoc.com/presentation_image_h/a4d952d752e9d6a411c4a8ccdb916ac2/image-41.jpg)
Main Reference n [Brunelli et al, 1995] R. Brunelli, and D. Falavigna, "Personal identification using multiple cues, " IEEE Trans. on Pattern Analysis and Machine Intelligence, Vol. 17, No. 10, pp. 955 -966, 1995 n [Bigun, 1997] Bigun, E. S. , J. Bigun, Duc, B. : “Expert conciliation for multi modal person authentication systems by Bayesian statistics, ” In Proc. 1 st Int. Conf. On Audio Video-Based Personal Authentication, pp. 327 -334, Crans-Montana, Switzerland, 1997 n [Dieckmann et al, 1997] Dieckmann, U. , Plankensteiner, P. , and Wagner, T. : “SESAM: A biometric person identification system using sensor fusion, ” In Pattern Recognition Letters, Vol. 18, No. 9, pp. 827 -833, 1997 n [Kittler et al, 1997] Kittler, J. , Li, Y. , Matas, J. and Sanchez, M. U. : “Combining evidence in multi-modal personal identity recognition systems, ” In Proc. 1 st International Conference On Audio Video-Based Personal Authentication, pp. 327 -344, Crans-Montana, Switzerland, 1997 n [Maes and Beigi, 1998] S. Maes and H. Beigi, "Open sesame! Speech, password or key to secure your door? ", In Proc. 3 rd Asian Conference on Computer Vision, pp. 531 -541, Hong Kong, China, 1998 n [Jain et al, 1999] Jain, A. , Bolle, R. , Pankanti, S. : “BIOMETRICS: Personal identification in networked society, ” 2 nd Printing, Kluwer Academic Publishers (1999) n [Gonzalez, 1993] Gonzalez, R. , and Woods, R. : "Digital Image Processing", 2 nd edition, Addison-Wesley, 1993.