Data Security and Cryptology V Traditional PreComputer Cryptography





























- Slides: 44

Data Security and Cryptology, V Traditional (Pre-Computer) Cryptography September 30 th, 2015 Valdo Praust mois@mois. ee Lecture Course in Estonian IT College Autumn 2015

Standard Model of Security Harming 1. Threats (ohud) influence the data (via IT assets) 2. Threats use the vulnerabilities (nõrkused, turvaaugud) of IT assets or components of IT system 3. Threats with co-influence the vulnerabilites will determine the risk or security risk (risk, turvarisk) 4. When a certain risk realises, there will appear a security loss or security breach or security incident (turvakadu, turvarike, turvaintsident) 5. In order to minimize the risks there’s necessary to minimise vulnerabilities using safeguards of security measures (turvameetmeid)

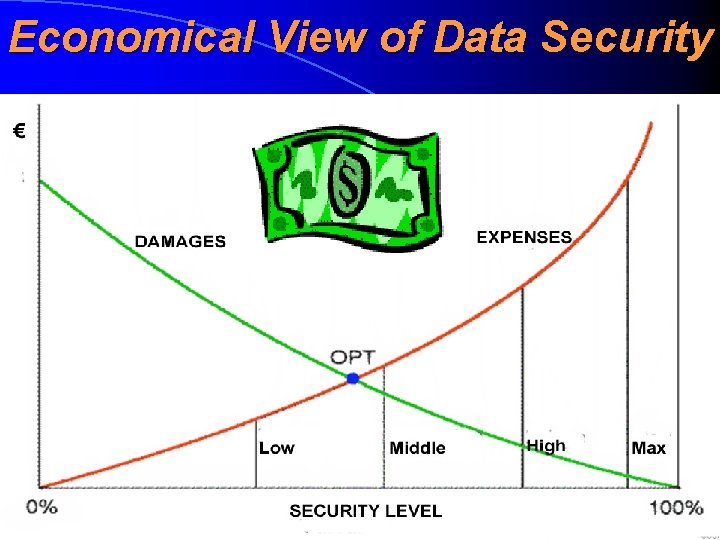
Economical View of Data Security

Essence of Risk Management Main goal of risk management: to implement exactly such a set of safeguards, which lead a security risk (the significance of theats + and its realising probability through vulnerabilities) to the level of the accepted residual risk • risk of availability loss, risk of integrity loss and risk of confidentiality loss must all be taken into account • typically these acceptable risks are determined by the business process and given to IT specialists (IT security specialists) as existing values

Main Alternatives of Risk Management 1. Detailed risk analysis (detailne riskianalüüs). An ideal case 2. Baseline approach (etalonturve metoodika). A convenient way in a lot of practical cases 3. Mixed approach (segametoodika). Takes the best elements from both baseline and detailed risk analysis combining them 4. Informal approach (mitteformaalne metoodika). A real practical alternative to systematic (formal) approaches

Detailed Risk Analysis 1. Residual risk evaluating with the using of either qualitative or quantitative risk analysis methodology 2. Founding areas where it’s necessary to reduce the residual risk 3. Implementing appropriate safeguards in these areas 4. Finding new residual risks with the comparing them to accepted residual risk 5. Repeating the above-mentioned procedure until we fit to the accepted residual risk limits

Essence of Baseline Approach In the case of baseline methodology (etalonturbe metoodika) we have a given (fixed) set of mandatory safeguards for a certain (early determined) security level and we assume that implementing these safeguards is sufficient to reach the mentioned security level (to reach to the limits of accepted residual risk) Baseline approach is a main alternative of detailed security analysis for the casees of limited resources (used in 99% situations in practice)

Main Idea of Baseline Approach 1. All typical components of the typical information system (buildings, office, servers, hardware, software, communications, users, organization, access control, etc. ) was taken into account as an hypothetical system 2. The certain level of security was predefined 3. The detailed risk analysis was implemented (once!) for above-mentioned circumstances. The result is a certain set of safeguards 4. It is assumed that for any other information system the same security level needs to implement the same set of safeguards. Therefore, these safeguards can be considered as a baseline safeguards (etalonturvameetmed)

Essence of Mixed Approach Overtakes the advantages from both, detailed risk analysis and baseline approach combining them in order to find a reasonable compromize Two main branches of mixed approach (segametoodika): 1. Sets of baseline safeguards are prepared not only for a certain (single) security level but for different security levels (for different pre-defined availability, integrity and confidentiality levels) 2. In mission-critcal and/or unique architecture components the detailed risk analysis was implemented (in other components the baseline approach)

Informal Apporoach Informal approach (mitteformaalne riskihaldusmetoodika) is based on risk assessment by non-abstract methods using the existing experience of specialists (own employees, external consultants) It is a useful method when: • risk analysis has to be performed very fast • we havn’t any suitable abstract risk assessment approaches or we can’t use them for some reasons • existing risk management methods are too resource -consumable for us • we have suitable experienced (IT) professionals

Two Stages of Cryptography • Pre-computer cryptography or traditional cryptography (arvutieelne ehk traditsiooniline krüptograafia). Uses paper-pencil or some simple mechanical devices (until 1940 s). Was a tool only for military, diplomacy and intelligence areas (until 1970 -80 s). Uses empirical tehcniques (until 1949) • Contemporary cryptology or computerage cryptography, usually called only cryptography ((kaasaja) krüptograafia). Uses computers as encrypting/breaking tools (since 1940 s). Is an essential tool for each e-systems (since 1970 -80 s). Uses scientific-based algoritms(since 1949)

Essence of Traditional Cryptography Traditional or pre-computer cryptography (traditsiooniline ehk arvutieelne krüptograafia) was a discipline which aim was a hiding of information (hiding meaning of data) foreign or alien people by the way of ”strange writing” The name of the discipline comes from the Greek name (like most of other classic disciplines): • κρνπτος (kryptos) – hidden • γραπηο (graphō) – I write Cryptography means “hidden word” in Greek

Sources of Cryptography derives probably from ancient times, when the writing was invented and there also soon arises a necessity to write down the information in such a way that it will be understandable by own people but ununderstandable for others (aliens) How old it actually is? • An alphabet is some thousand years old (first used by Phoenicians), hieroglyphs are much older (at least 5000 years) • Cryptography is probably also about 30005000 years old

The Oldest Known Utilization Fact Hieroglyphs on cliff-tomb of Egyptian Pharaoh Khnumhotep, which are completly different from other knows hieroglyphs from these times About 4000 years old (1900 BC)

Main Methods of Pre. Computer Cryptography, I • substitution (substitutsioon) – replacing of original characters (letters) by another characters (letters) • transposition or permutation (transpositsioon, permutatsioon) – changing the order of characters (letters)

Main Methods of Pre. Computer Cryptography, II The simplest pre-computer (ancient) ciphers were different variants of substitution or transposition ciphers. More complex ancient ciphers were certain combinations of substitution and transposition By the way, even a lot of modern (computerage) cryptoalgorithms are still a complex combinations of substitution and transposition

Ancient Greek Cryptography: Polybios Square Used probably since 200 BC Each character was replaced by the pair of numbers of row and column. For example EESTI was replaced by 5151344442 The alphabet was usually re-arranged or mixed (25! different possibilities)

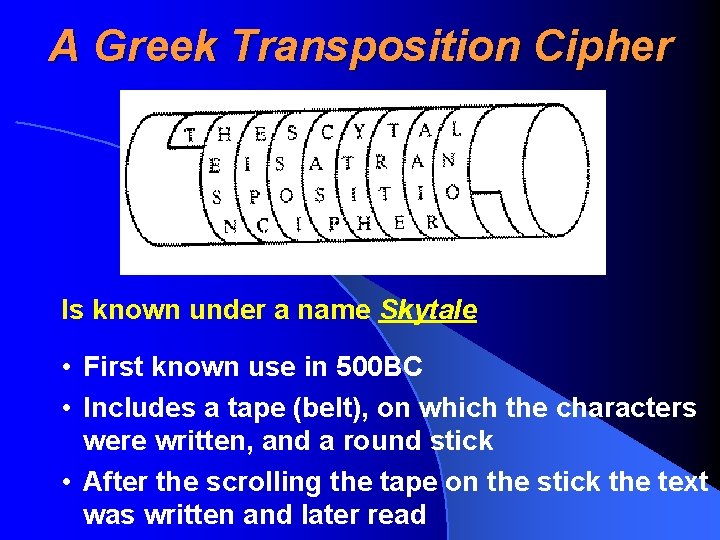
A Greek Transposition Cipher Is known under a name Skytale • First known use in 500 BC • Includes a tape (belt), on which the characters were written, and a round stick • After the scrolling the tape on the stick the text was written and later read

Caesar Cipher Was a simple substitution cipher – each letter (character) was replaced by another letter with a certain positions ahead Was used by a famous Roman Emperor Julius (Gaius) Caesar Usage time: about 50 BC Example: a word KRYPTO is encrypted to CIOHKG

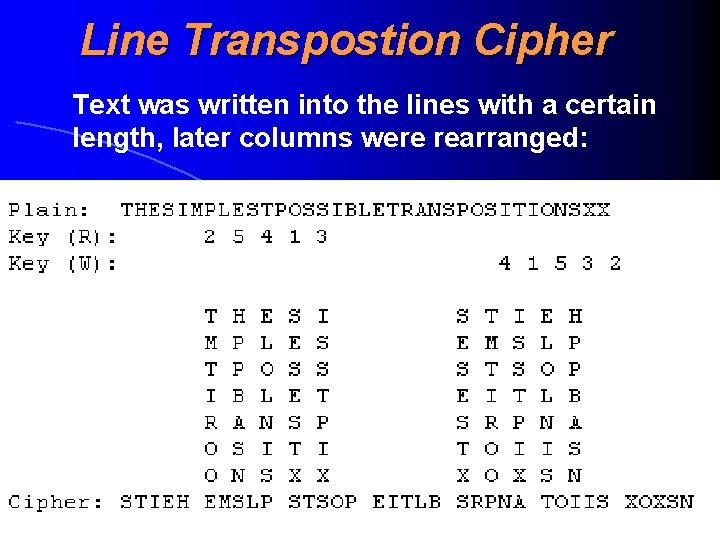
Line Transpostion Cipher Text was written into the lines with a certain length, later columns were rearranged:

Arab Cryptography Al-Khalil (Abu `Abd al-Rahman al-Khalil ibn Ahmad ibn `Amr ibn Tammam al Farahidi al. Zadi al Yahmadi), about AD 790 : • Has written the book about ciphers (lost, but used as citations in other later and remained books) • Has discussed on a different cipher systems, including the systems which were used in Byzantine Empire • Has used the complex cryptoanalytic means (by the way the known plaintext analysis which was used in 1940 for breaking ENIGMA cipher)

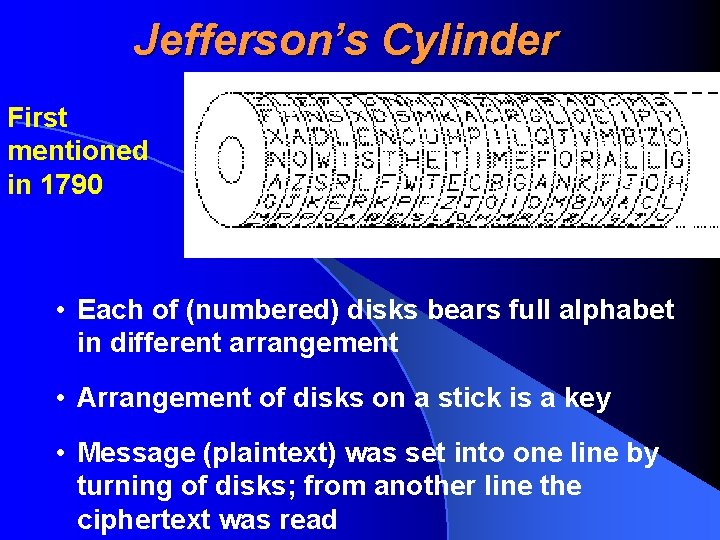
Jefferson’s Cylinder First mentioned in 1790 • Each of (numbered) disks bears full alphabet in different arrangement • Arrangement of disks on a stick is a key • Message (plaintext) was set into one line by turning of disks; from another line the ciphertext was read

Vigenére’s Table

Vigenére’s Table • Is a common rule how we calculate the ciphertext letter from a plaintext letter and key letter • The key is a portion of any text (usually from previously determined book and page) • Was very widely used between 18 th and 20 th centuries If the lenght of key is equal to the lenght of enciphered text, then such a system (Vernam’s cipher) is theoretically unbreakable It was proved by Shannon in 1949

Paper and Pencil as Essential Tools • Until the 1920 -40 s the paper and pencil were the most important tools in encryption; other tools were used only slightly • Most used cipher was a Verman cipher when certain book (certain page of book) was used as a key material During 1920 -40 s there also appeared first mechanical and/or electromechanical ciphering devices (machines)

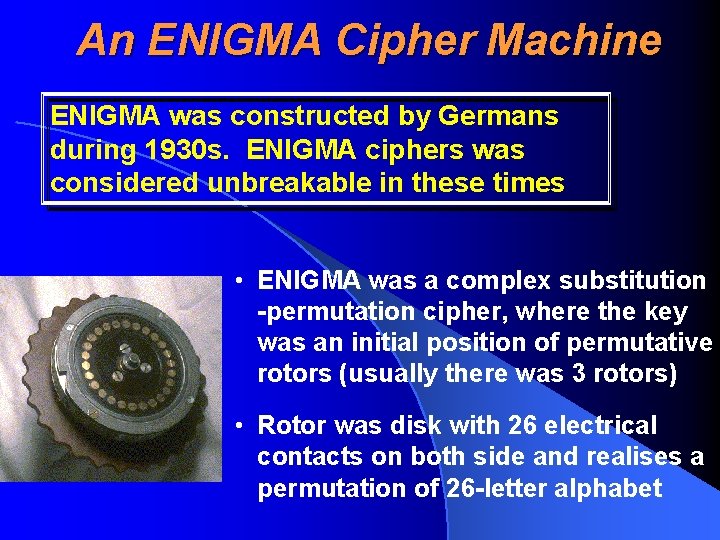
An ENIGMA Cipher Machine ENIGMA was constructed by Germans during 1930 s. ENIGMA ciphers was considered unbreakable in these times • ENIGMA was a complex substitution -permutation cipher, where the key was an initial position of permutative rotors (usually there was 3 rotors) • Rotor was disk with 26 electrical contacts on both side and realises a permutation of 26 -letter alphabet

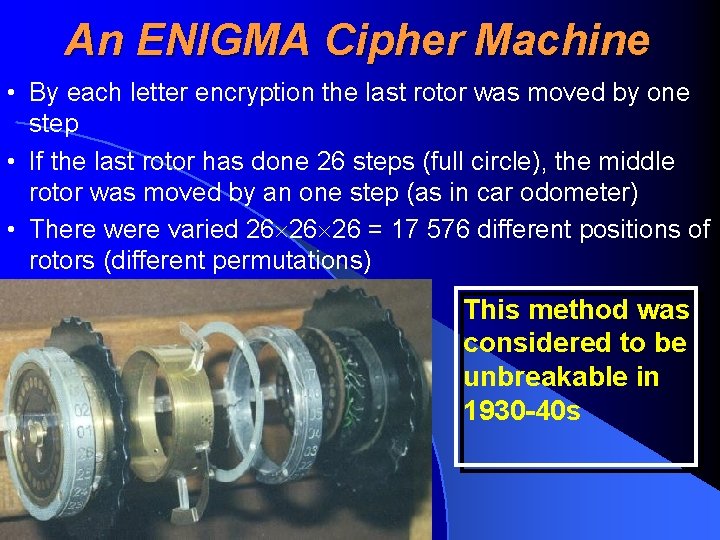
An ENIGMA Cipher Machine • By each letter encryption the last rotor was moved by one step • If the last rotor has done 26 steps (full circle), the middle rotor was moved by an one step (as in car odometer) • There were varied 26 26 26 = 17 576 different positions of rotors (different permutations) This method was considered to be unbreakable in 1930 -40 s

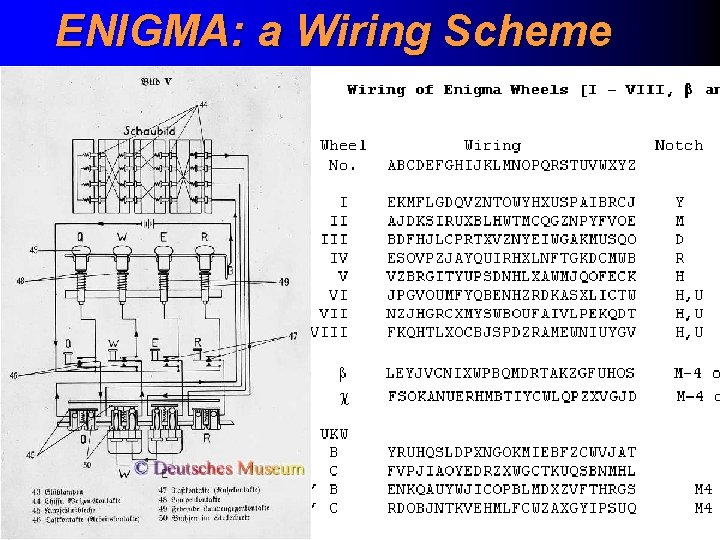
ENIGMA: a Wiring Scheme

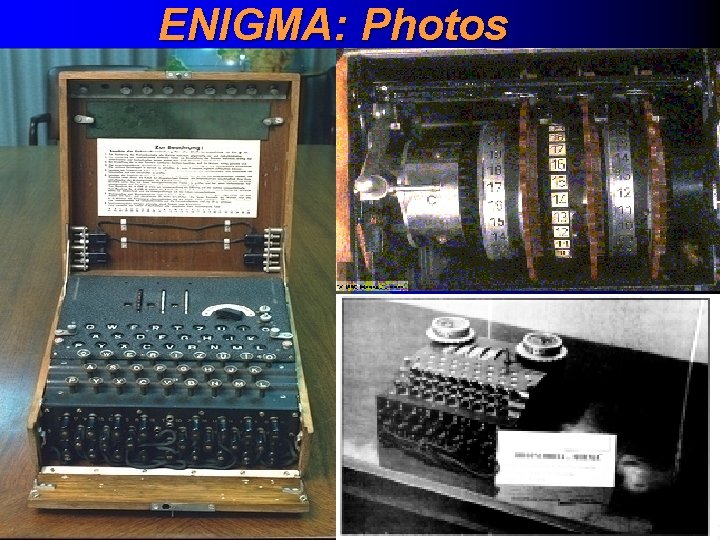
ENIGMA: Photos

ENIGMA: Photos

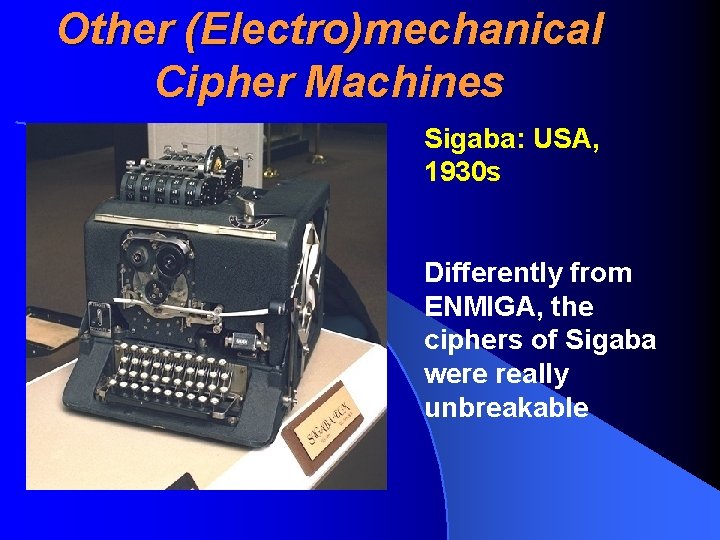
Other (Electro)mechanical Cipher Machines Sigaba: USA, 1930 s Differently from ENMIGA, the ciphers of Sigaba were really unbreakable

Other (Electro)mechanical Cipher Machines M-100: USSR, 1934 Germans were unable to decrypt the messages made by M-100 during WWII

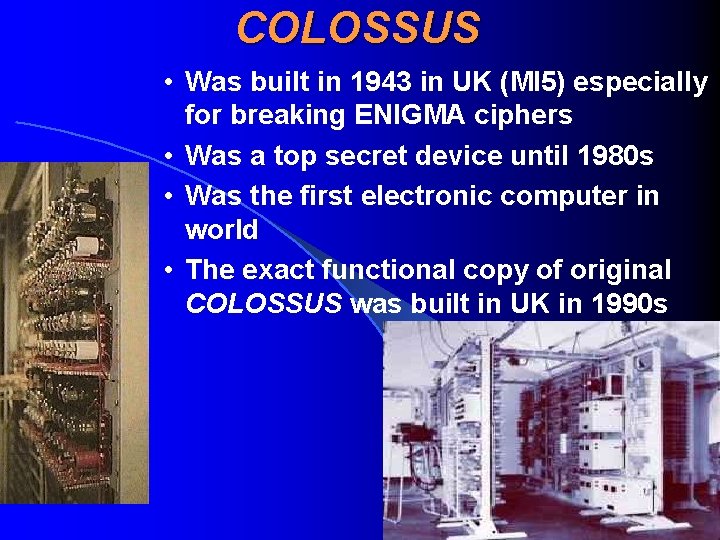
ENIGMA - A Breaking Story • ENIGMA cipher was theoretically broken by a Polish cryptographer Rejewski in 1930 s but it needed large amount of calculations (a lot of time and/or machine work) • In 1943, a British matematician Alan Turing constructed a special electronic computer (first in world!) named COLOSSUS, which only aim was breaking the ENIGMA ciphers • This fact was kept secret for a long time (until the end of cold war in late 1980 s) because COLOSSUS was made by British intelligence MI 5

COLOSSUS • Was built in 1943 in UK (MI 5) especially for breaking ENIGMA ciphers • Was a top secret device until 1980 s • Was the first electronic computer in world • The exact functional copy of original COLOSSUS was built in UK in 1990 s

End of Traditional Cryptography, I End of traditional cryptography was mainly caused by an appearing of electronic computer in 1940 s (COLOSSUS, ENIAC), which made a computational work thousands times faster than before It ended the era of pre-computer ciphers (crypotoalgorithms) and a traditional (pre-computer) cryptography Since 1940 s for both during encryption and cipher breaking processe there was used (electronical) computers

End of Traditional Cryptography, II Around the same time with the appearance of electronic computers, Shannon published his information theory (1949). It led cryptology from previous empirical basis to scientific basis Since 1949 we can speak about contemporary (modern, scientifical) cryptography. It is a branch of applied mathematics. It is used as an useful tool for data security (both confidentiality and integrity)

A Tool for Diplomats and Warriors Traditional or pre-computer cryptography was used for a narrow purposes - for diplomacy, intelligence and military purposes The transition from paper-based into computer-based encrypting during 1940 -50 s did not change these traditional usage fields In many countries until 1970 -80 s the encryption equipment/devices was considered to be handled as weapons

1970 -80 s – From Military to Commerce Use Mass-use of cryptographic means in commerce began together with the spread on wide-area computer networks (Internet) during 1970 -80 s where the transferred information confidentiality often needed a protection Additionally this process was heavily led by the invention of new types of cryptoalgorithms which do not protect the confidentiality but integity

The Essence and Role of Contemporary Cryptology The aim of contemporary cryptology is not only confidentiality. The additional aim – the avoiding of unauthorized changes (integrity) was added. Ensuring of integrity can be even considered as the main function of contemporary cryptology (ca 80% of its usage) But the classical (Greek) name cryptography (a hidden word) has stille remained as a relict (even in these cases when the aim is not confidentiality)

1990 s: Liberalizing of Cryptology The mass-usage of Internet (the early and mid 1990 s) caused the final liberalizing of cryptographical means/devices use Last essential “old relicts” were: • France - until mid-1990 s the cryptographivc devices’ usage were considered as weapons • U. S. - until 1999 there was an export ban of unbreakable algorithms (algorithms with tke keylenght more than 40 bits)

Contemporary Cryptology as a Typical Tool of IT and Data Security Without the using of cryptographical tools as an essentials tools for protecting digital data, there’s usually impossible to realize any information system. The observation of cryptotools as weapons are lost forever already for long years Contemporary cryptology is a basic mean to protecting both the integrity and confidentiality of any digital data. For protecting of availabilty it is usualy an auxiliary mean

Contemporary Cryptography — an Official Definition (Contemporary) cryptology ((kaasaja) krüptograafia) is a discipline that embodies the principles, means, and methods for the transformation of data in order to hide their semantic content, prevent their unauthorized use, or prevent their undetected modification (Source: ISO 7498 -2)

Basic Concepts of (Contemporary) Cryptology • Encryptable (convertable from readable to unreadable form) text is called plaintext (avatekst) • Encrypted text (the text which is already converted to unreadable form) is called ciphertext (krüptogramm) • The converting process from plaintext to ciphertext (from readable to unreadable form) is called encryption or encipherment (krüpteerimine, šifreerimine) • The converting process from ciphertext back to plaintext (beck to readable form) under normal circumstances is called decryption or deciphering (dešifreerimine)

Basic Concepts of (Contemporary) Cryptology • Usually both the enciphering and deciphering processes are performed by using a key or secret key (võti, salajane võti) • Deciphering is a transforming of ciphertext into a plaintext using an appropriate key • Successful transforming of ciphertext into a plaintext without a key is called breaking a cryptoalgorithm (krüptoalgoritmi murdmine) In pre-computer (traditional) cryptoalgoritms the key is often undistinguishable from an algoritm itself