Introduction to Cryptology Definitions Digital encryption techniques are






- Slides: 11

Introduction to Cryptology

Definitions Digital encryption techniques are used to protect data in two ways: to maintain privacy and to prove integrity [1] Cryptography comes from the Greek words Kryptos, meaning hidden, Graphen, meaning to write. Cryptography is the art of communicating confidentially through an insecure channel Cryptanalysis is the art of deciphering those communications when one is not the legitimate receiver. Cryptology is the union of these two domains. Cryptology is actually the study of codes and ciphers.

Definitions Plaintext the original message that is to be changed into a secret form Cipher, Cryptosystem, Encryption Method is a procedure for converting the plaintext message into encrypted message – ciphertext The word cipher originates from the Hebrew word "Saphar, " meaning "to number. " Decryption - the process that conducted by the intended receiver to recover original message (plaintext) from the encrypted message (ciphertext) Key - keeps the message secret

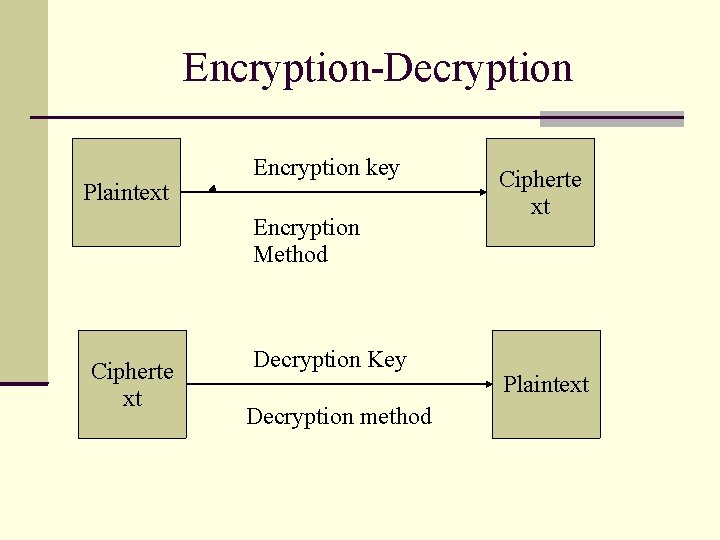
Encryption-Decryption Plaintext Encryption key Encryption Method Cipherte xt Decryption Key Decryption method Cipherte xt Plaintext

Symmetric and Asymmetric Ciphers Symmetric Cipher – knowledge of encryption key is equivalent to knowledge of the decryption key, or the same key is used for encryption and decryption. Asymmetric Cipher (Public-Key Cryptosystem) the knowledge of encryption key give little information about the decryption key and vice versa

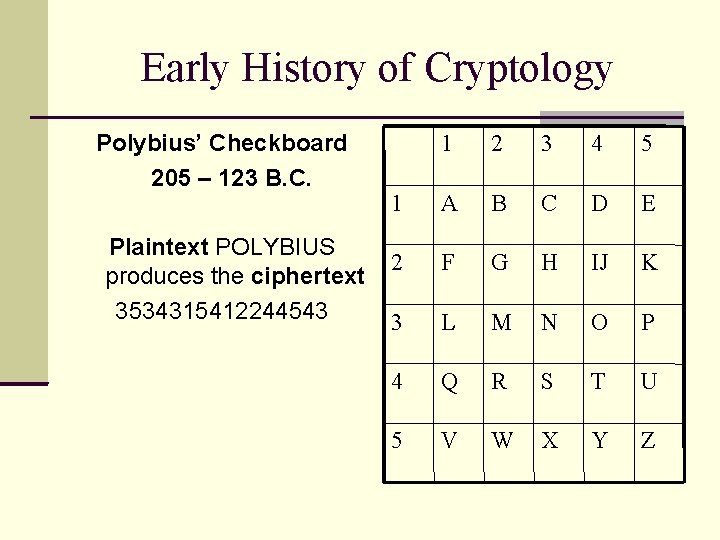
Early History of Cryptology Polybius’ Checkboard 205 – 123 B. C. Plaintext POLYBIUS produces the ciphertext 3534315412244543 1 2 3 4 5 1 A B C D E 2 F G H IJ K 3 L M N O P 4 Q R S T U 5 V W X Y Z

Julius Caesar Cipher The letters of the alphabet are coded as: A B C D. . . Z 0 1 2 3. . . 25 Caesar Cipher One of the simplest examples of a substitution or shift cipher Have been used by Julius Caesar to communicate with his army Caesar is considered to be one of the first persons to have ever employed encryption for the sake of securing messages

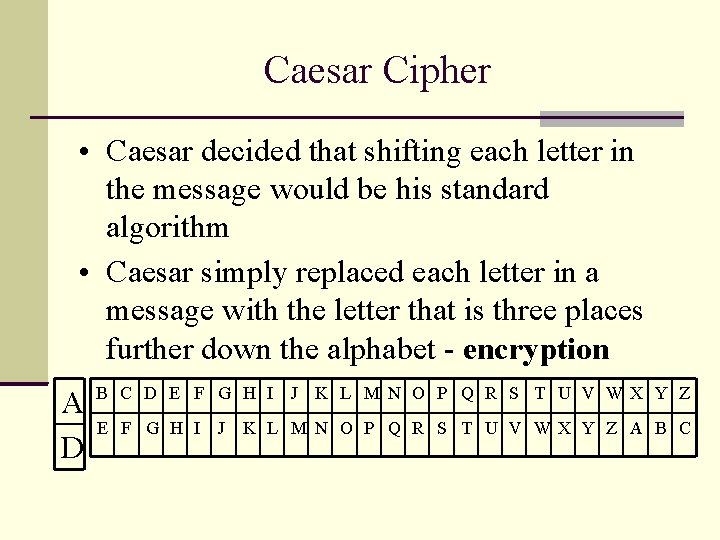
Caesar Cipher • Caesar decided that shifting each letter in the message would be his standard algorithm • Caesar simply replaced each letter in a message with the letter that is three places further down the alphabet - encryption A D B C D E F G H I J K L M N O P Q R S T U V W X Y Z J K L M N O P Q R S T U V WX Y Z A B C

Caesar Ciphertext may be deciphered or decrypted by replacing each letter by the third previous letter. Example: Plaintext: dog Ciphertext: GRJ Example: Ciphertext: BDQD Plaintext: yana

Caesar Cipher Remember: we think of each letter as corresponding to a number from 0 to 25 To encrypt, we map numbers according to C ( P + 3 )(mod 26) To decrypt, we map numbers according to P (C – 3) (mod 26)

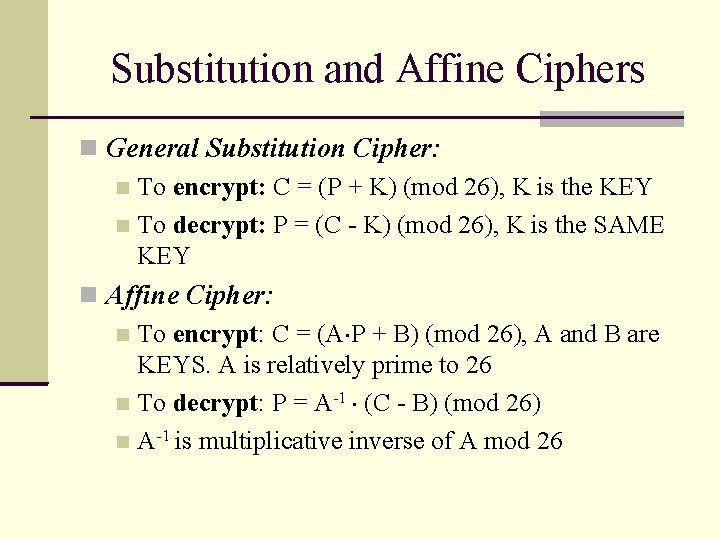
Substitution and Affine Ciphers General Substitution Cipher: To encrypt: C = (P + K) (mod 26), K is the KEY To decrypt: P = (C - K) (mod 26), K is the SAME KEY Affine Cipher: To encrypt: C = (A P + B) (mod 26), A and B are KEYS. A is relatively prime to 26 To decrypt: P = A-1 (C - B) (mod 26) A-1 is multiplicative inverse of A mod 26