Cryptology Tim Cahill Ryan Church Cryptology Cryptology Cryptography



- Slides: 6

Cryptology Tim Cahill Ryan Church

Cryptology - • Cryptology • Cryptography - • Cryptanalysis - the procedures, processes, methods, etc. , used to the science and study of cryptanalysis and cryptography. the procedures, processes, methods, etc. , of making and using secret writing, as codes or ciphers. Ex: The process where you take your message and encode it using a key you make up. your sentence = yana is awesome your key = +3 Encoded message = bdqd lv dzhvrph translate or interpret secret writings, as codes and ciphers, for which the key is unknown. Ex: encrypted segment = DEF cryptanalysis is the process where you go from the encrypted segment “DEF” to the decrypted segment “ABC” without using the key.

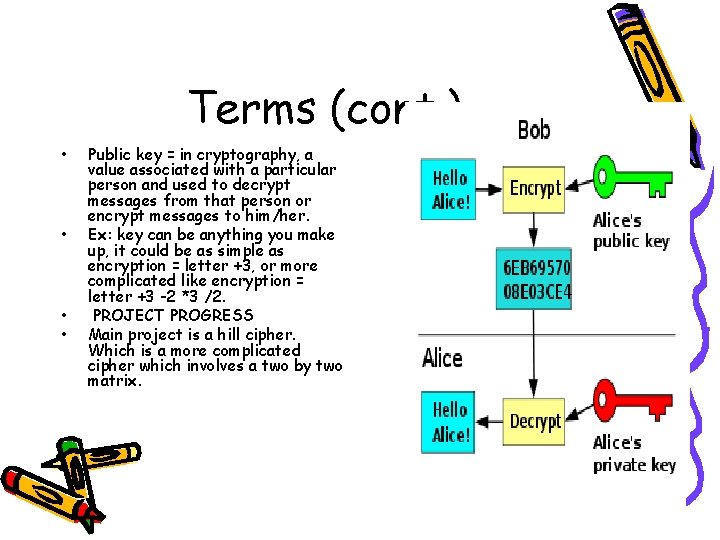
Terms (cont. ) • • Public key = in cryptography, a value associated with a particular person and used to decrypt messages from that person or encrypt messages to him/her. Ex: key can be anything you make up, it could be as simple as encryption = letter +3, or more complicated like encryption = letter +3 -2 *3 /2. PROJECT PROGRESS Main project is a hill cipher. Which is a more complicated cipher which involves a two by two matrix.

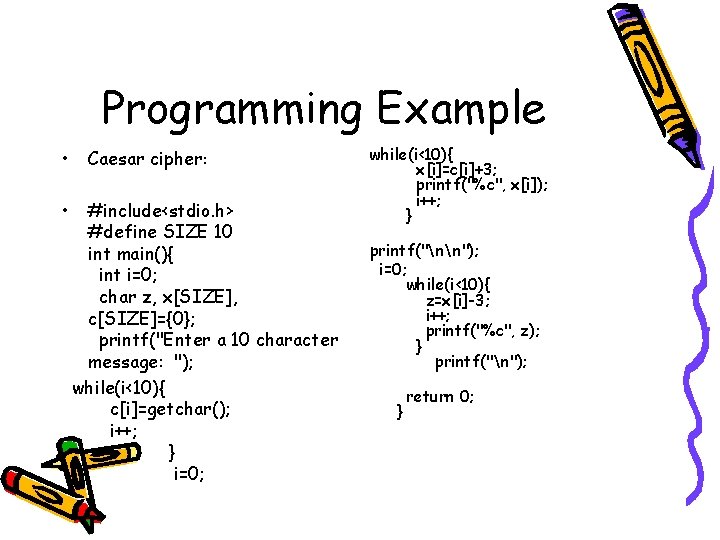
Programming Example • • Caesar cipher: #include<stdio. h> #define SIZE 10 int main(){ int i=0; char z, x[SIZE], c[SIZE]={0}; printf("Enter a 10 character message: "); while(i<10){ c[i]=getchar(); i++; } i=0; while(i<10){ x[i]=c[i]+3; printf("%c", x[i]); i++; } printf("nn"); i=0; while(i<10){ z=x[i]-3; i++; printf("%c", z); } printf("n"); } return 0;

Quiz • 1) What is the difference between cryptology and cryptography? • 2) What is the main use for cryptology? • 3) Draw how public key is used. • 4) What would the encoded message of Yana be if the key is +4?

References • Spam and the ongoing battle for the inbox. Communications of the ACM, Volume 50, #2 (2007), pages 24 -33. Joshua Goodman, Gordon V. Cormack, David Heckerman. • Textbook: Invitation to computer science java version Edition 3, Schneider, copyright 07. pages 600 -607 • An overview of cryptography. Gary C. Kessler, may 1998 (23 January 2009). (website) www. garykessler. net/library/crypto. html#purpose