CSCE 522 Lecture 12 Program Security Malicious Code






















- Slides: 31

CSCE 522 Lecture 12 Program Security Malicious Code

Reading l Reading for this lecture: Required: – Pfleeger: Ch. 3 Recommended: – USC Technology Services – Antivirus Protection, https: //www. uts. sc. edu/itsecurity/antivirus. shtml CSCE 522 - Farkas 2

Program Flaws Taxonomy of flaws: – how (genesis) – when (time) – where (location) the flaw was introduced into the system CSCE 522 - Farkas 3

Security Flaws by Genesis l Genesis – Intentional l l Malicious: Trojan Horse, Trapdoor, Logic Bomb, Worms, Virus Non-malicious – Inadvertent l l l Validation error Domain error Serialization error Identification/authentication error Other error CSCE 522 - Farkas 4

Secure Software l Software provides functionality l Functionality comes with certain risks l Software security aims to manage risk l Security is always a secondary concern l Security achievement is hard to evaluate when nothing bad happens CSCE 522 - Farkas 5

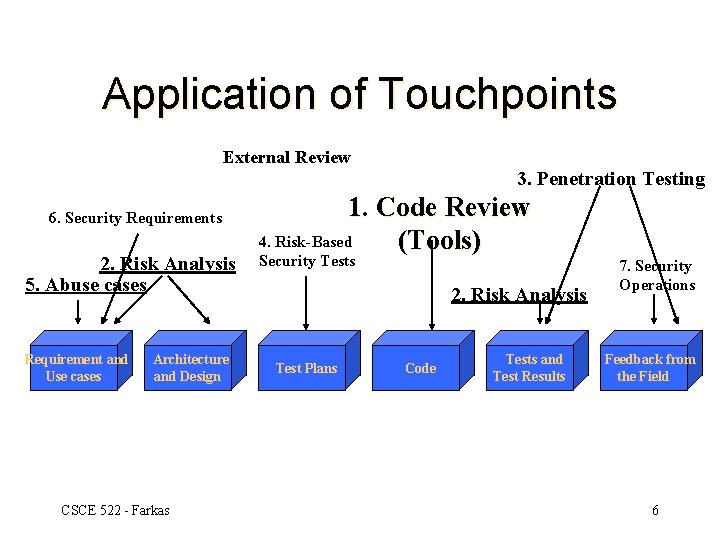
Application of Touchpoints External Review 3. Penetration Testing 6. Security Requirements 2. Risk Analysis 5. Abuse cases Requirement and Use cases Architecture and Design CSCE 522 - Farkas 1. Code Review 4. Risk-Based (Tools) Security Tests 2. Risk Analysis Test Plans Code Tests and Test Results 7. Security Operations Feedback from the Field 6

Web Applications l Attacker: – Download the site’s code for offline study – Mapping the site functionality and vulnerabilities – Experiment with site response to supplied data l Several vulnerabilities exist from corrupting sites, applications, servers, to other clients CSCE 522 - Farkas 7

OWASP Top 10 2013 Vulnerabilities l l l A 1 -Injection A 2 -Broken Authentication and Session Management A 3 -Cross-Site Scripting (XSS) A 4 -Insecure Direct Object References A 5 -Security Misconfiguration A 6 -Sensitive Data Exposure A 7 -Missing Function Level Access Control A 8 -Cross-Site Request Forgery (CSRF) A 9 -Using Components with Known Vulnerabilities A 10 -Unvalidated Redirects and Forwards https: //www. owasp. org/index. php/Category: OWASP_Top_Ten _2013_Project CSCE 522 - Farkas 8

Malware CSCE 522 - Farkas

Kinds of Malicious Codes l Virus: a program that attaches copies of itself into other programs. Propagates and performs some unwanted function. Viruses are not programs - they cannot run on their own. l Bacteria: make copies of themselves to overwhelm a computer system's resources. Denying the user access to the resources. CSCE 522 - Farkas 10

Kinds of Malicious Code l Worm: a program that propagates copies of itself through the network. Independent program. May carry other code, including programs and viruses. l Trojan Horse: secret, undocumented routine embedded within a useful program. Execution of the program results in execution of secret code. CSCE 522 - Farkas 11

Kinds of Malicious Code Logic bomb, time bomb: programmed threats that lie dormant for an extended period of time until they are triggered. When triggered, malicious code is executed. l Trapdoor: secret, undocumented entry point into a program, used to grant access without normal methods of access authentication. l Dropper: Not a virus or infected file. When executed, it installs a virus into memory, on to the disk, or into a file. l CSCE 522 - Farkas 12

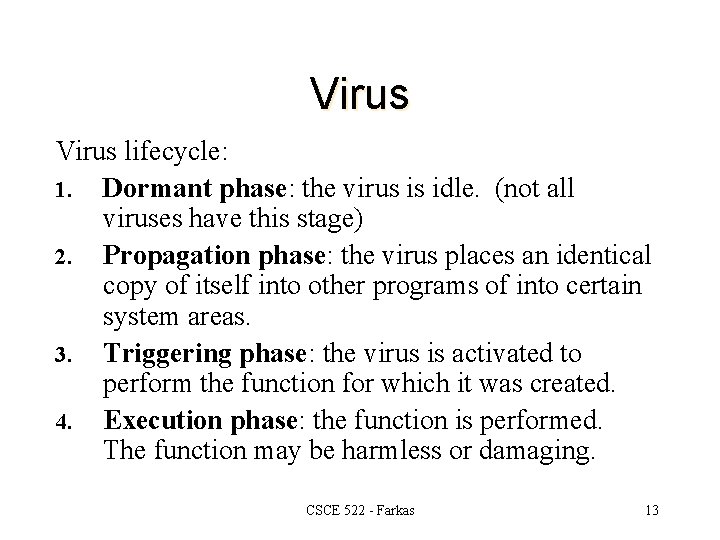
Virus lifecycle: 1. Dormant phase: the virus is idle. (not all viruses have this stage) 2. Propagation phase: the virus places an identical copy of itself into other programs of into certain system areas. 3. Triggering phase: the virus is activated to perform the function for which it was created. 4. Execution phase: the function is performed. The function may be harmless or damaging. CSCE 522 - Farkas 13

Virus Types l Parasitic virus: most common form. Attaches itself to a file and replicates when the infected program is executed. l Memory resident virus: lodged in main memory as part of a resident system program. Virus may infect every program that executes. CSCE 522 - Farkas 14

Virus Types l Boot Sector Viruses: – Infects the boot record and spreads when system is booted. – Gains control of machine before the virus detection tools. – Very hard to notice – Carrier files: AUTOEXEC. BAT, CONFIG. SYS, IO. SYS CSCE 522 - Farkas 15

Virus Types l Stealth virus: a form of virus explicitly designed to hide from detection by antivirus software. l Polymorphic virus: a virus that mutates with every infection making detection by the “signature” of the virus difficult. CSCE 522 - Farkas 16

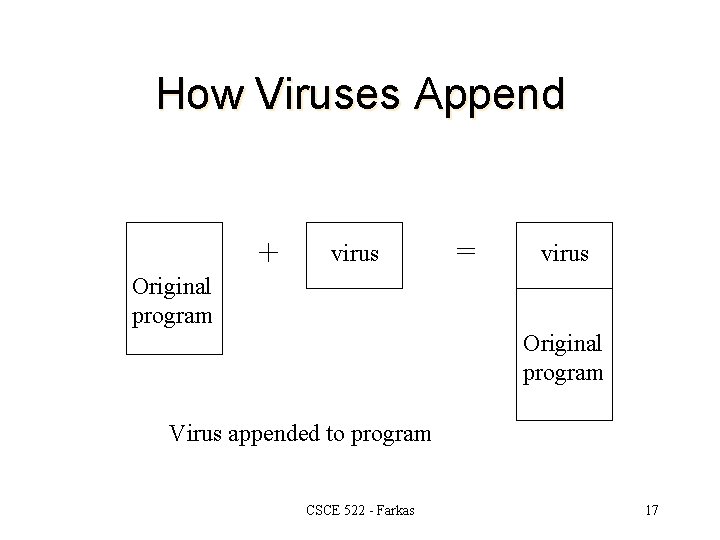
How Viruses Append + virus = virus Original program Virus appended to program CSCE 522 - Farkas 17

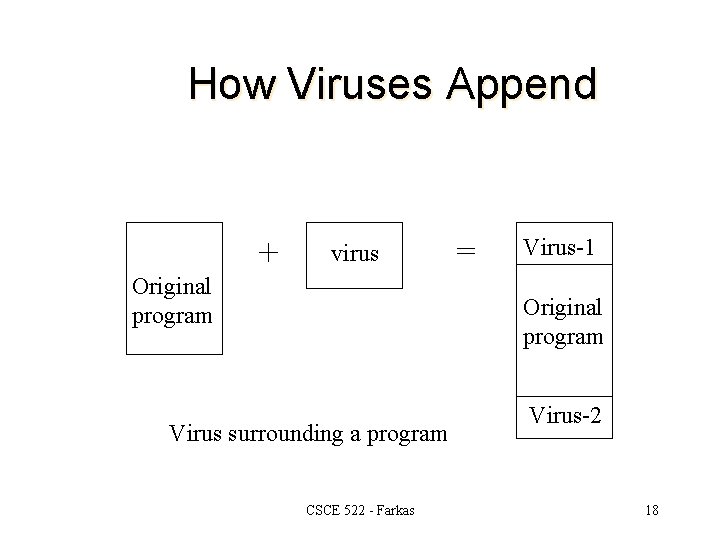
How Viruses Append + virus Original program = Virus-1 Original program Virus surrounding a program CSCE 522 - Farkas Virus-2 18

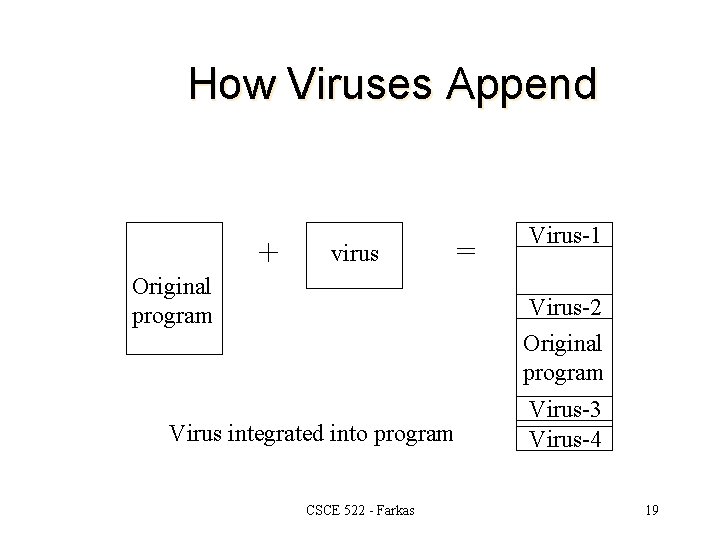
How Viruses Append + virus Original program = Virus-1 Virus-2 Original program Virus integrated into program CSCE 522 - Farkas Virus-3 Virus-4 19

How Viruses Gain Control l Virus V has to be invoked instead of target T. – V overwrites T – V changes pointers from T to V l High risk virus properties: – – – Hard to detect Hard to destroy Spread infection widely Can re-infect Easy to create Machine independent CSCE 522 - Farkas 20

Antivirus Approaches l l l Prevention: disallow the download/execution Detection: determine infection and locate the virus. Identification: identify the specific virus. Removal: remove the virus from all infected systems, so the disease cannot spread further. Recovery: restore the system to its original state. CSCE 522 - Farkas 21

Preventing Virus Infection Prevention: l Good source of software installed l Isolated testing phase l Use virus detectors Limit damage: l Make bootable diskette l Make and retain backup copies important resources CSCE 522 - Farkas 22

Virus Detection 1. l Virus Signature: needs constant update – Storage pattern Code always located on a specific address l Increased file size l – Execution pattern – Transmission pattern – Polymorphic Viruses CSCE 522 - Farkas 23

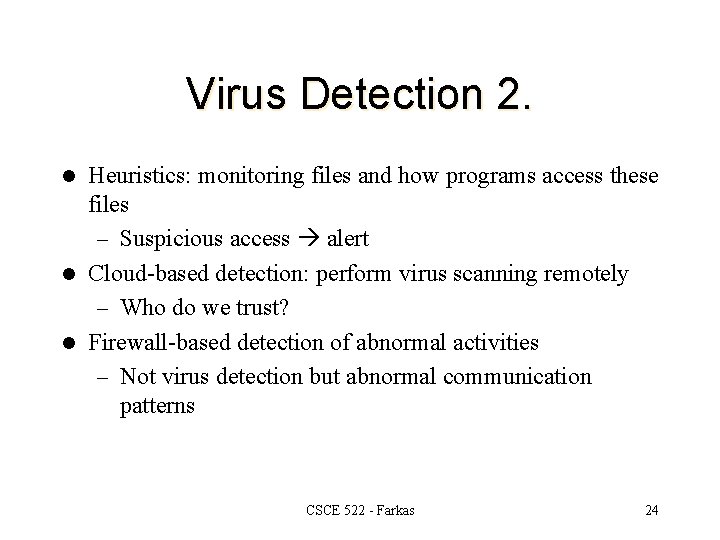
Virus Detection 2. Heuristics: monitoring files and how programs access these files – Suspicious access alert l Cloud-based detection: perform virus scanning remotely – Who do we trust? l Firewall-based detection of abnormal activities – Not virus detection but abnormal communication patterns l CSCE 522 - Farkas 24

Worm Self-replicating (like virus) l Objective: system penetration (intruder) l Phases: dormant, propagation, triggering, and execution l Propagation: l – – Searches for other systems to infect (e. g. , host tables) Establishes connection with remote system Copies itself to remote system Execute CSCE 522 - Farkas 25

Adware and Spyware l Adware: a malware designed to display advertisements in the user’s software – Maybe harmless or harmful l Spyware: a malware that spies on the user – information collected from the user’s computer and the usage – Generally creates a system performance degradatio CSCE 522 - Farkas 26

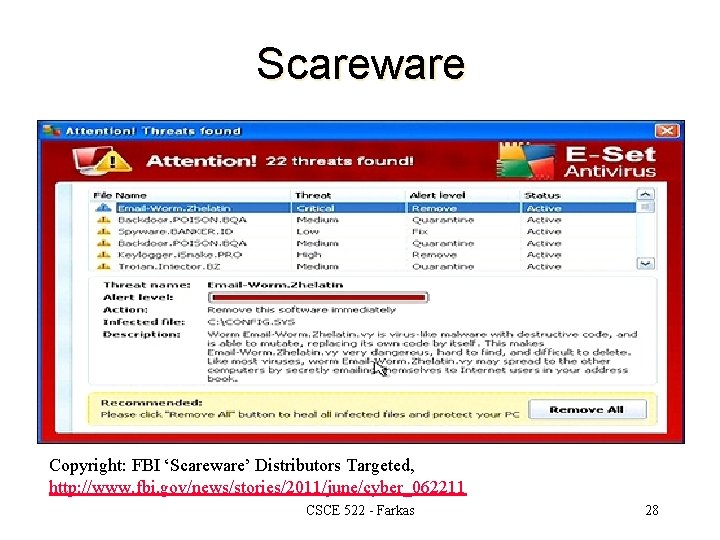
Scareware Malware: – with malicious payloads, or of limited or no benefit – Intend to cause shock, anxiety, or the perception of a threat l Rapidly increasing, high impact attacks l Scareware warnings – look like actual warnings from your system – hard to close – designed to appear legitimate l CSCE 522 - Farkas 27

Scareware Copyright: FBI ‘Scareware’ Distributors Targeted, http: //www. fbi. gov/news/stories/2011/june/cyber_062211 CSCE 522 - Farkas 28

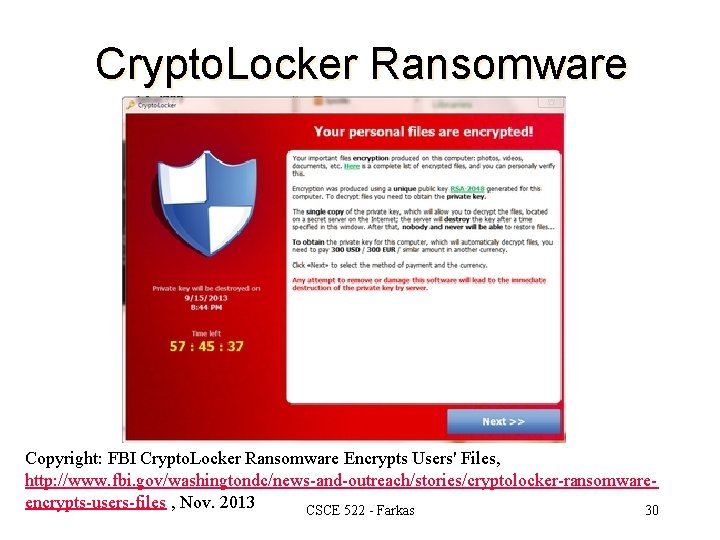
Ransomware l Holds a computer system, or the data it contains, hostage against its user by demanding a ransom. – Disable an essential system service or lock the display at system startup – Encrypt some of the user's personal files l Victim has to – enter a code obtainable only after wiring payment to the attacker or sending an SMS message – buy a decryption or removal tool CSCE 522 - Farkas 29

Crypto. Locker Ransomware Copyright: FBI Crypto. Locker Ransomware Encrypts Users' Files, http: //www. fbi. gov/washingtondc/news-and-outreach/stories/cryptolocker-ransomwareencrypts-users-files , Nov. 2013 CSCE 522 - Farkas 30

Next Class l Network Security CSCE 522 - Farkas 31