Introduction Class Information Introduction to Security CSCE 522


















- Slides: 26

Introduction Class Information Introduction to Security CSCE 522 - Eastman - Fall 2006

Class Information n Class Homepage: http: //www. cse. sc. edu/~eastman/CSCE 522 Fall 2006/Root 522. html n Instructor: Caroline Eastman n Office: Swearingen 3 A 44 n Telephone: 777 -8103 n Office Hours: TBA n E-mail: eastman@cse. sc. edu; eastman@engr. sc. edu 12/16/2021 CSCE 522 - Eastman - Fall 2006 2

Course Approach n Understanding of Information Security n Industry + Academics n Managerial + Technical n DEFENSE! 12/16/2021 CSCE 522 - Eastman - Fall 2006 3

Course Objective 1 n. Identify common risks, threats, and countermeasures related to computing systems n. Tests and assignments 12/16/2021 CSCE 522 - Eastman - Fall 2006 4

Course Objective 2 n. Apply knowledge of computer security to personal computer use n. Tests and assignments 12/16/2021 CSCE 522 - Eastman - Fall 2006 5

Course Objective 3 n Analyze computing situations with respect to security risks, threats, and countermeasures, including the tradeoffs between security and system functionality n Tests, assignments, and projects 12/16/2021 CSCE 522 - Eastman - Fall 2006 6

Course Objective 4 n. Work with others to design and/or implement security measures n. Projects 12/16/2021 CSCE 522 - Eastman - Fall 2006 7

Course Text n Information Security Illuminated n Michael G. Solomon and Mike Chapple n Jones and Bartlett Publishers n 2005 12/16/2021 CSCE 522 - Eastman - Fall 2006 8

Reading Assignment Chapter 1: 9 Computer and Network Security Chapter 2: Access Control Methodologies Appendix A: Online Resources and Information 12/16/2021 CSCE 522 - Eastman - Fall 2006 9

Security Incident: Choice. Point n Choice. Point – Atlanta-based company that collects and maintains personal data (data aggregator) n Sold data to fraudulent “companies” n At least 145, 000 people compromised n Contacted consumers largely as a result of California law n February 2005 12/16/2021 CSCE 522 - Eastman - Fall 2006 10

Security Incident: Diebold n Manufacturer of electronic voting machines (DREs) n Accused of secrecy and fraud n HAVA – Help American Vote Act n November 2004 12/16/2021 CSCE 522 - Eastman - Fall 2006 11

Security Incidents: ACM Tech News n “Spear phishing” tests educate people about online scams n New law may tighten power plant security n E-mail authentication: Holy grail or lost cause n Electronic US passports coming in December n Johns Hopkins-led center will study, develop voting technologies n August 17, 2005 12/16/2021 CSCE 522 - Eastman - Fall 2006 12

Some Security Concerns n Monitoring and capture network traffic n Exploitation of software bugs n Unauthorized access to resources n Masquerade as authorized user of end system n E-mail forgery n Malicious attacks 12/16/2021 CSCE 522 - Eastman - Fall 2006 13

Contributing Factors n Increased Internet usage n Lack of awareness n Unencrypted network traffic n Complexity of security measures n Software bugs n Availability of cracking tools 12/16/2021 CSCE 522 - Eastman - Fall 2006 14

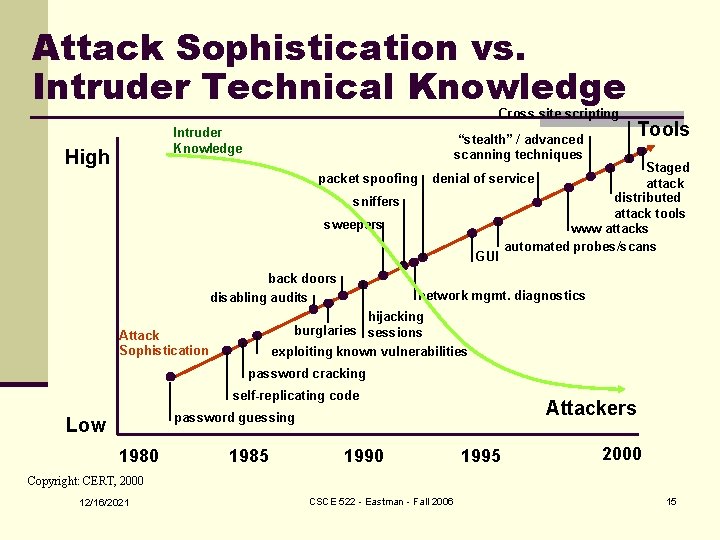
Attack Sophistication vs. Intruder Technical Knowledge Cross site scripting Intruder Knowledge High “stealth” / advanced scanning techniques packet spoofing Staged attack distributed attack tools www attacks automated probes/scans denial of service sniffers sweepers GUI back doors disabling audits Tools network mgmt. diagnostics hijacking burglaries sessions exploiting known vulnerabilities Attack Sophistication password cracking self-replicating code Attackers password guessing Low 1980 1985 1990 1995 2000 Copyright: CERT, 2000 12/16/2021 CSCE 522 - Eastman - Fall 2006 15

Two Security Triads n. CIA Confidentiality n Integrity n Accessibility n n. DAD Disclosure n Alteration n Denial n 12/16/2021 CSCE 522 - Eastman - Fall 2006 16

The Relationships Disclosure – Confidentiality Alteration – Integrity Denial – Accessibility 12/16/2021 CSCE 522 - Eastman - Fall 2006 17

Security Objectives n Confidentiality: prevent/detect/deter improper disclosure of information n Integrity: prevent/detect/deter improper modification of information n Availability: prevent/detect/deter improper denial of access to services 12/16/2021 CSCE 522 - Eastman - Fall 2006 18

Military Example n Confidentiality: target coordinates of a missile should not be improperly disclosed n Integrity: target coordinates of missile should be correct n Availability: missile should fire when proper command is issued 12/16/2021 CSCE 522 - Eastman - Fall 2006 19

Commercial Example n Confidentiality: patient’s medical information should not be improperly disclosed n Integrity: patient’s medical information should be correct n Availability: patient’s medical information can be accessed when needed for treatment 12/16/2021 CSCE 522 - Eastman - Fall 2006 20

Achieving Security n Policy n What to protect? n Mechanism n How to protect? n Assurance n How good is the protection? 12/16/2021 CSCE 522 - Eastman - Fall 2006 21

Security Policy Organizational Policy Computerized Information System Policy 12/16/2021 CSCE 522 - Eastman - Fall 2006 22

Handling Threats n. Prevention n. Detection n. Tolerance/Recovery 12/16/2021 CSCE 522 - Eastman - Fall 2006 23

Security by Obscurity n Hide inner working of the system n Bad idea! n. Vendor independent open standard n. Widespread computer knowledge 12/16/2021 CSCE 522 - Eastman - Fall 2006 24

Security by Legislation Instruct users how to behave n Provide penalties n Important but not sufficient n 12/16/2021 CSCE 522 - Eastman - Fall 2006 25

Security Tradeoffs Security Functionality COST Ease of Use 12/16/2021 CSCE 522 - Eastman - Fall 2006 26