CSCE 522 Network Security CSCE 522 Farkas 1

















- Slides: 31

CSCE 522 Network Security CSCE 522 - Farkas 1

Reading l Pfleeger and Pfleeger: Chapter 6 CSCE 522 - Farkas 2

Overview of TCP/IP Layers CSCE 522 - Farkas 3

Internet Challenge Interconnected networks differ (protocols, interfaces, services, etc. ) l Solutions: l Reengineer and develop one global packet switching network standard: not economically feasible 2. Have every host implement the protocols of every network it wants to communicate with: too complex, very high engineering cost 3. Add an extra layer: internetworking layer l Hosts: one higher-level protocol l Connecting networks use the same protocol l Interface between the new protocol and network 1. CSCE 522 - Farkas 4

Layering l Organize a network system into logically distinct entities – the service provided by one entity is based only on the service provided by the lower level entity CSCE 522 - Farkas 5

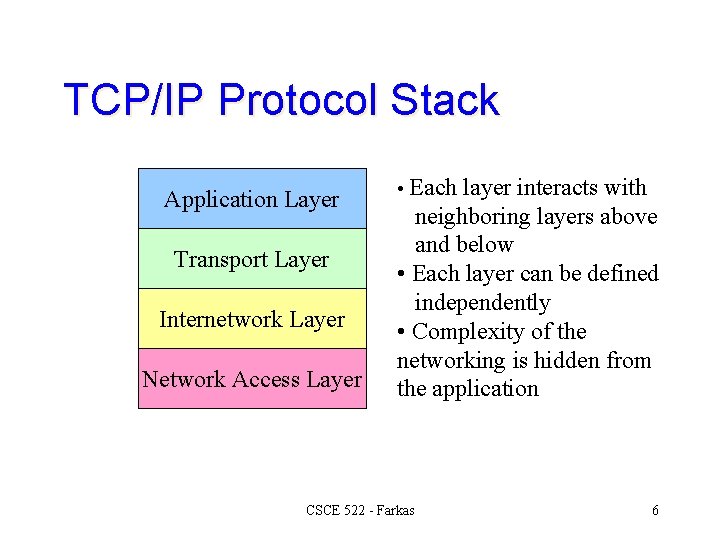
TCP/IP Protocol Stack Application Layer Transport Layer Internetwork Layer Network Access Layer • Each layer interacts with neighboring layers above and below • Each layer can be defined independently • Complexity of the networking is hidden from the application CSCE 522 - Farkas 6

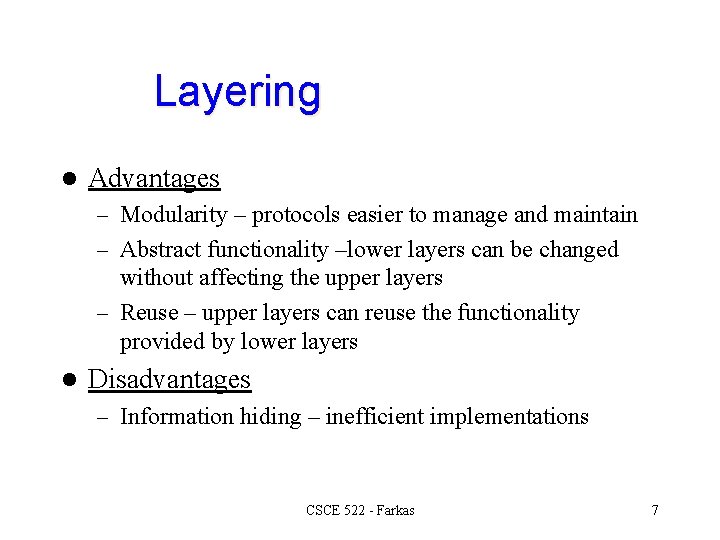
Layering l Advantages – Modularity – protocols easier to manage and maintain – Abstract functionality –lower layers can be changed without affecting the upper layers – Reuse – upper layers can reuse the functionality provided by lower layers l Disadvantages – Information hiding – inefficient implementations CSCE 522 - Farkas 7

ISO OSI Reference Model l ISO – International Standard Organization l OSI – Open System Interconnection l Goal: a general open standard – allow vendors to enter the market by using their own implementation and protocols CSCE 522 - Farkas 8

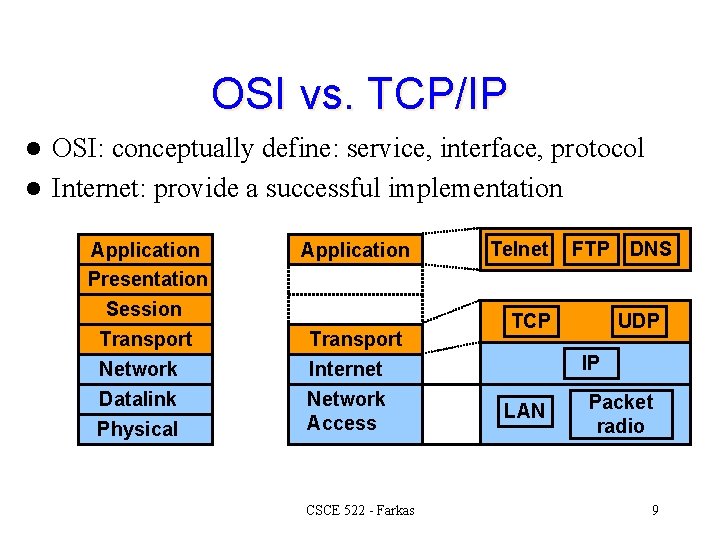
OSI vs. TCP/IP OSI: conceptually define: service, interface, protocol l Internet: provide a successful implementation l Application Presentation Session Transport Network Datalink Physical Application Transport Internet Network Access CSCE 522 - Farkas Telnet FTP TCP DNS UDP IP LAN Packet radio 9

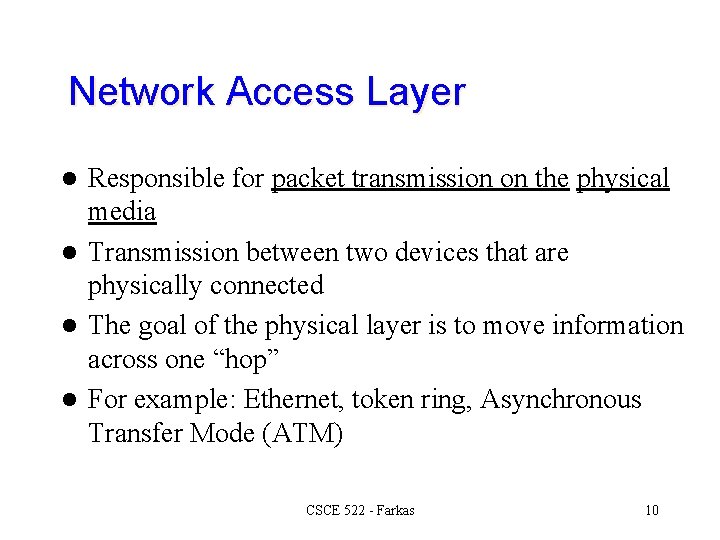
Network Access Layer Responsible for packet transmission on the physical media l Transmission between two devices that are physically connected l The goal of the physical layer is to move information across one “hop” l For example: Ethernet, token ring, Asynchronous Transfer Mode (ATM) l CSCE 522 - Farkas 10

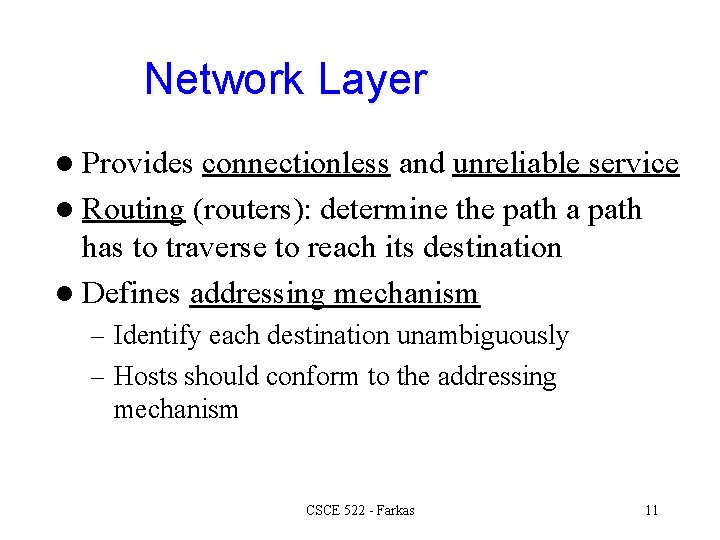
Network Layer l Provides connectionless and unreliable service l Routing (routers): determine the path a path has to traverse to reach its destination l Defines addressing mechanism – Identify each destination unambiguously – Hosts should conform to the addressing mechanism CSCE 522 - Farkas 11

IP Addresses – Network layer IP provides logical address space and a corresponding addressing schema l IP address is a globally unique or private number associated with a host network interface l Every system which will send packets directly out across the Internet must have a unique IP address l IP addresses are based on where the hosts are connected l IP addresses are controlled by a single organization address ranges are assigned l They are running out of space! l CSCE 522 - Farkas 12

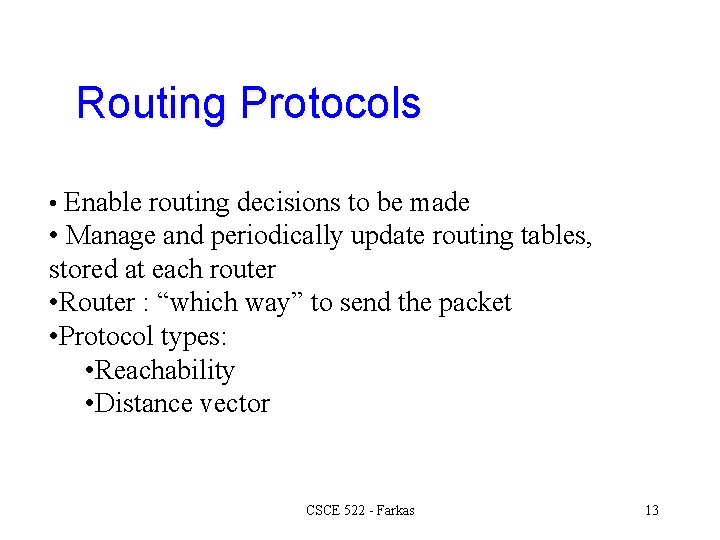
Routing Protocols • Enable routing decisions to be made • Manage and periodically update routing tables, stored at each router • Router : “which way” to send the packet • Protocol types: • Reachability • Distance vector CSCE 522 - Farkas 13

The Domain Name System l Each system connected to the Internet also has one or more logical addresses. l Unlike IP addresses, the domain address have no routing information - they are organized based on administrative units l There are no limitations on the mapping from domain addresses to IP addresses CSCE 522 - Farkas 14

Domain Name Resolution l Domain Name Resolution: looking up a logical name and finding a physical IP address l There is a hierarchy of domain name servers l Each client system uses one domain name server which in turn queries up and down the hierarchy to find the address l If your server does not know the address, it goes up the hierarchy possibly to the top and works its way back down CSCE 522 - Farkas 15

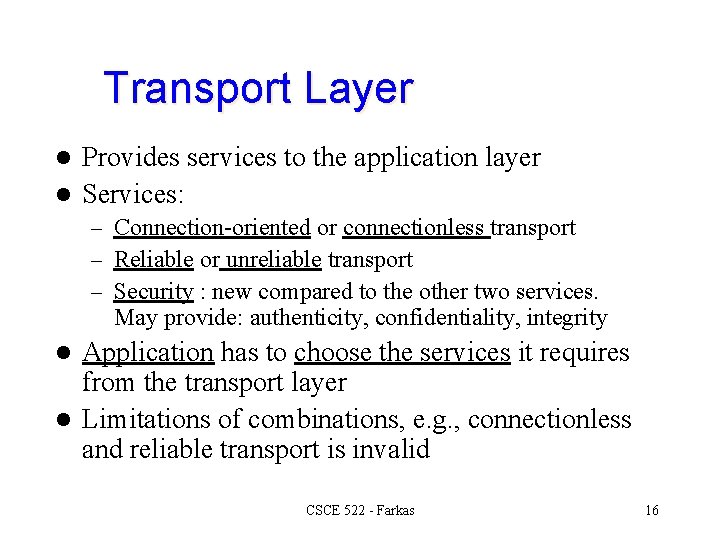
Transport Layer Provides services to the application layer l Services: l – Connection-oriented or connectionless transport – Reliable or unreliable transport – Security : new compared to the other two services. May provide: authenticity, confidentiality, integrity Application has to choose the services it requires from the transport layer l Limitations of combinations, e. g. , connectionless and reliable transport is invalid l CSCE 522 - Farkas 16

Application Layer l Provides services for an application to send and recieve data over the network, e. g. , telnet (port 23), mail (port 25), finger (port 79) l Interface to the transport layer – Operating system dependent – Socket interface – most popular CSCE 522 - Farkas 17

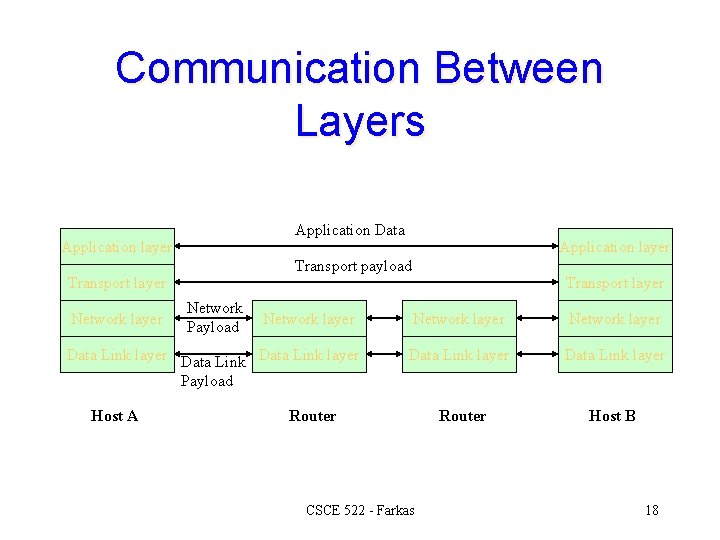
Communication Between Layers Application Data Application layer Transport payload Transport layer Network layer Application layer Network Payload Transport layer Network layer Data Link layer Payload Data Link layer Router Host B Host A Router CSCE 522 - Farkas 18

Networks Threats CSCE 522 - Farkas 19

Network Threats 1. l Reconnaissance – Port scan: which ports and services are running, which OS is installed, applications and their versions – Social engineering: can access sensitive information up to login credentials – Intelligence: open source vs. espionage – Bulletin boards, chats, documentations, etc. CSCE 522 - Farkas 20

Threats in Transit Passive attacks: wiretap, traffic monitoring, packet sniffer, etc. l Protocol Flaws: RFC number used to report new vulnerabilities l Impersonation – Nonexistent authentication, guessing authentication information, well-known authentication – Eavesdropping and wiretapping – Spoofing and masquerading – Session hijacking, man-in-the-middle l CSCE 522 - Farkas 21

Message Confidentiality Threats l Mis-delivery – Target not available, promiscuous-mode l Exposure – Eavesdropping – Traffic analysis CSCE 522 - Farkas 22

Message Integrity Threats l Falsification of Messages l Noise l Malformed Packets l Protocol failures CSCE 522 - Farkas 23

Denial of Service Threats Transmission failure – Multiple reasons, intentional accidental l Connection flooding: attacker sends as much data as the victim can handle, preventing other from acess – E. g. , ping of death, smurf, syn flooding, etc. l Traffic redirection: routers forward packets to wrong address – Corrupted router, incorrect DNS entry, etc. l CSCE 522 - Farkas 24

How to address these threats? CSCE 522 - Farkas 25

Security -- At What Level? Secure traffic at various levels in the network l Where to implement security? -- Depends on the security requirements of the application and the user l Basic services that need to be implemented: l Key management l Confidentiality l Nonrepudiation l Integrity/authentication l Authorization l CSCE 522 - Farkas 26

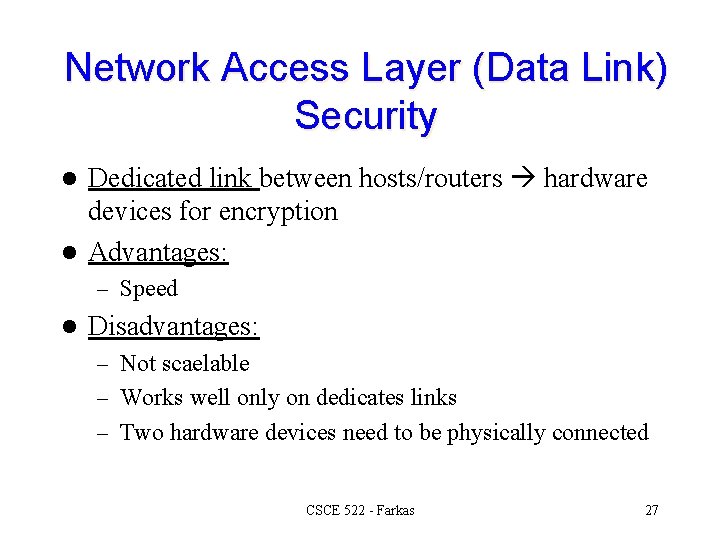
Network Access Layer (Data Link) Security Dedicated link between hosts/routers hardware devices for encryption l Advantages: l – Speed l Disadvantages: – Not scaelable – Works well only on dedicates links – Two hardware devices need to be physically connected CSCE 522 - Farkas 27

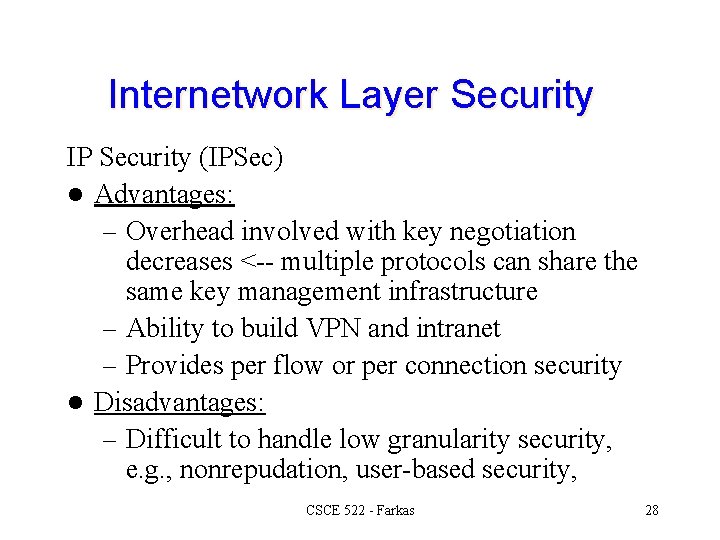
Internetwork Layer Security IP Security (IPSec) l Advantages: – Overhead involved with key negotiation decreases <-- multiple protocols can share the same key management infrastructure – Ability to build VPN and intranet – Provides per flow or per connection security l Disadvantages: – Difficult to handle low granularity security, e. g. , nonrepudation, user-based security, CSCE 522 - Farkas 28

Transport Layer Security Advantages: – Does not require enhancement to each application l Disadvantages: – Difficult to obtain user context – Implemented on an end system (Transport Layer Security) – Protocol specific l Implemented for each protocol l Must maintain context for a connection l CSCE 522 - Farkas 29

Application Layer Security l Advantages: – Executing in the context of the user --> easy access to user’s credentials – Complete access to data --> easier to ensure nonrepudation – Application can be extended to provide security (do not depend on the operating system) – Application understand data --> fine tune security l Disadvantages: – Implemented in end hosts – Security mechanisms have to be implemented for each application --> – expensive – greated probability of making mistake CSCE 522 - Farkas 30

Application Example l E-mail client using PGP l Extended capabilities – Ability to look up public keys of the users – Ability to provide securiy services such as encryption/decrytion, nonrepudation, and authentication for e-mail messages CSCE 522 - Farkas 31