CSCE 201 Introduction to Information Security Fall 2010






























- Slides: 35

CSCE 201 Introduction to Information Security Fall 2010

CSCE 201 Introduction to Computer Security l l l Instructor: Csilla Farkas Office: Swearingen 3 A 43 Office Hours: Monday, Wednesday 10: 00 – 11: 00 am or electronically any time or by appointment Telephone: 576 -5762 E-mail: farkas@cec. sc. edu Homepage: http: //www. cse. sc. edu/~farkas/csce 2012009/csce 201. htm CSCE 201 - Farkas 2

Course Objectives l l l Understand basic concepts and practices of information security Understand tools and techniques used by attackers to penetrate computer systems Understand tools and techniques used by defense to protect computer systems Be able to check for security updates, apply and use patches and other defense mechanisms Be able to understand follow security and privacy policies Understand the ethical implications of using attack tools on computer systems CSCE 201 - Farkas 3

Text l C. Easttom, Computer Security Fundamentals, Pearson. Prentice Hall, ISBN: 0 -13 -171129 -6 l Lecture handouts CSCE 201 - Farkas 4

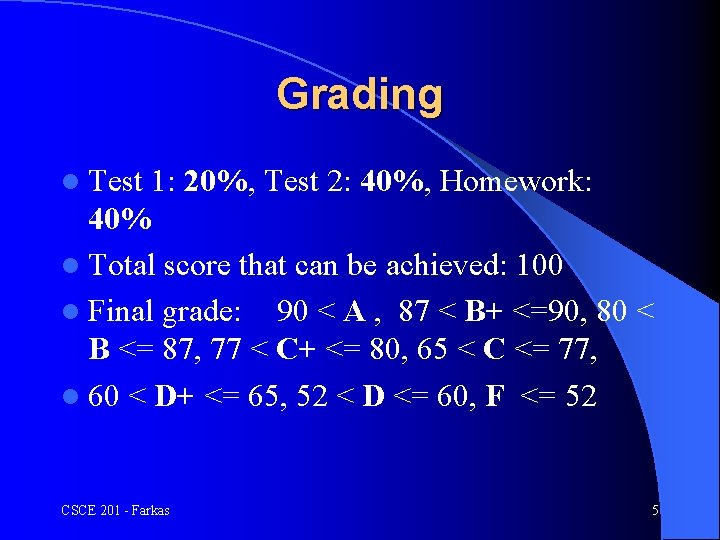
Grading l Test 1: 20%, Test 2: 40%, Homework: 40% l Total score that can be achieved: 100 l Final grade: 90 < A , 87 < B+ <=90, 80 < B <= 87, 77 < C+ <= 80, 65 < C <= 77, l 60 < D+ <= 65, 52 < D <= 60, F <= 52 CSCE 201 - Farkas 5

Tentative Schedule l Weeks 1— 5: Basic Security Concepts l Weeks 6— 10: Home Computer Security – Hardening the System l Weeks 11— 15: Let’s Have Fun – Popular applications, ethics, security and privacy CSCE 201 - Farkas 6

Security Planning CSCE 201 - Farkas 7

l Reading list: – Easttom: Chapter 1 l Other useful sites – Computer Security Institute, http: //www. gocsi. com/ – SANS Institute, http: //www. sans. org/ – Carnegie Mellon University's Computer Emergency Response Team , http: //www. cert. org/ – Information Warfare and Information Security on the Web, http: //www. fas. org/irp/wwwinfo. html – Sun Tzu on the Art of War (Lionel Giles, trans. ), http: //all. net/books/tzu. html CSCE 201 - Farkas 8

Security Objectives l Confidentiality: prevent/detect/deter improper disclosure of information l Integrity: prevent/detect/deter improper modification of information l Availability: prevent/detect/deter improper denial of access to services CSCE 201 - Farkas 9

Military Example l Confidentiality: target coordinates of a missile should not be improperly disclosed l Integrity: target coordinates of missile should be correct l Availability: missile should fire when proper command is issued CSCE 201 - Farkas 10

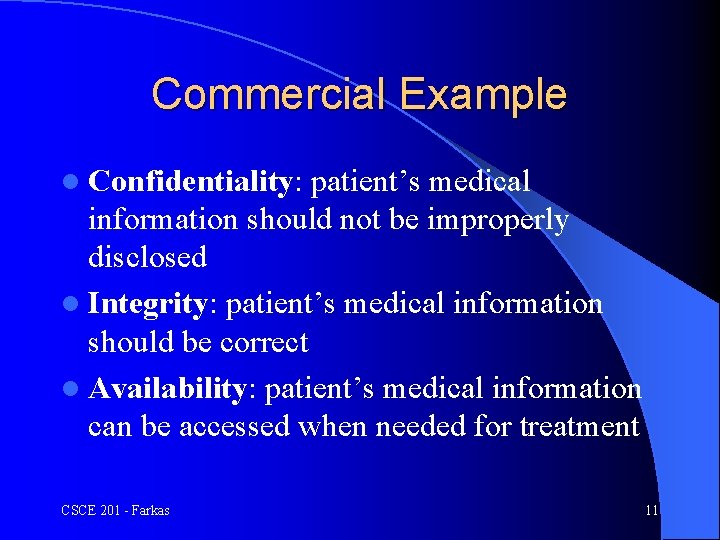
Commercial Example l Confidentiality: patient’s medical information should not be improperly disclosed l Integrity: patient’s medical information should be correct l Availability: patient’s medical information can be accessed when needed for treatment CSCE 201 - Farkas 11

Fourth Objective l Securing computing resources: prevent/detect/deter improper use of computing resources – Hardware – Software – Data – Network CSCE 201 - Farkas 12

Achieving Security l Policy – What to protect? l Mechanism – How to protect? l Assurance – How good is the protection? CSCE 201 - Farkas 13

Security Policy Organizational Policy Computerized Information System Policy CSCE 201 - Farkas 14

Security Mechanism l Prevention l Detection l Tolerance/Recovery CSCE 201 - Farkas 15

Security by Obscurity Hide inner working of the system Bad idea! Vendor independent open standard n Widespread computer knowledge n CSCE 201 - Farkas 16

Security by Legislation • Instruct users how to behave • Not good enough! n Important n Only enhance security n Targets only some of the security problems CSCE 201 - Farkas 17

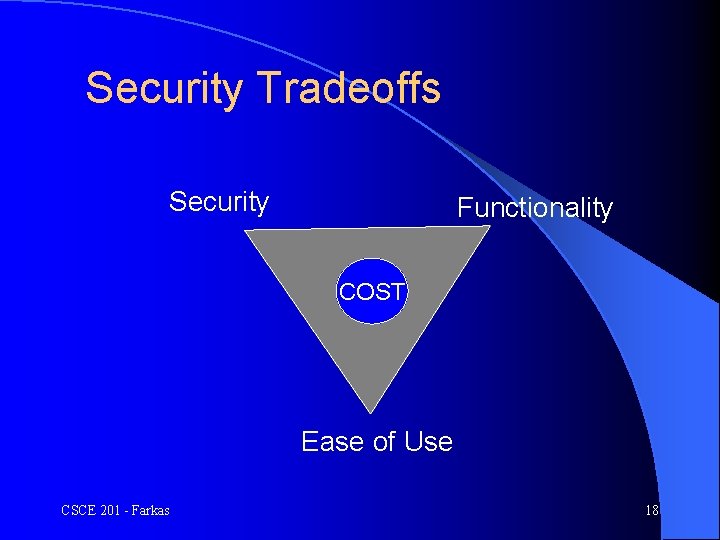
Security Tradeoffs Security Functionality COST Ease of Use CSCE 201 - Farkas 18

Threat, Vulnerability, Risk § Threat: potential occurrence that can have an § § § undesired effect on the system Vulnerability: characteristics of the system that makes is possible for a threat to potentially occur Attack: action of malicious intruder that exploits vulnerabilities of the system to cause a threat to occur Risk: measure of the possibility of security breaches and severity of the damage CSCE 201 - Farkas 19

Types of Threats § Errors of users § Natural/man-made/machine disasters § Dishonest insider § Disgruntled insider § Outsiders CSCE 201 - Farkas 20

Types of Attack § Interruption – an asset is destroyed, unavailable or § § unusable (availability) Interception – unauthorized party gains access to an asset (confidentiality) Modification – unauthorized party tampers with asset (integrity) Fabrication – unauthorized party inserts counterfeit object into the system (authenticity) Denial – person denies taking an action (authenticity) CSCE 201 - Farkas 21

Computer Crime l Any crime that involves computers or aided by the use of computers l U. S. Federal Bureau of Investigation: reports uniform crime statistics CSCE 201 - Farkas 22

Computer Criminals Amateurs: regular users, who exploit the vulnerabilities of the computer system – Motivation: easy access to vulnerable resources l Crackers: attempt to access computing facilities for which they do not have the authorization – Motivation: enjoy challenge, curiosity l Career criminals: professionals who understand the computer system and its vulnerabilities – Motivation: personal gain (e. g. , financial) l CSCE 201 - Farkas 23

Methods of Defense l l l l Prevent: block attack Deter: make the attack harder Deflect: make other targets more attractive Detect: identify misuse Tolerate: function under attack Recover: restore to correct state Documentation and reporting CSCE 201 - Farkas 24

Information Security Planning l Organization Analysis l Risk management l Mitigation approaches and their costs l Security policy and procedures l Implementation and testing l Security training and awareness CSCE 201 - Farkas 25

Risk Management 26

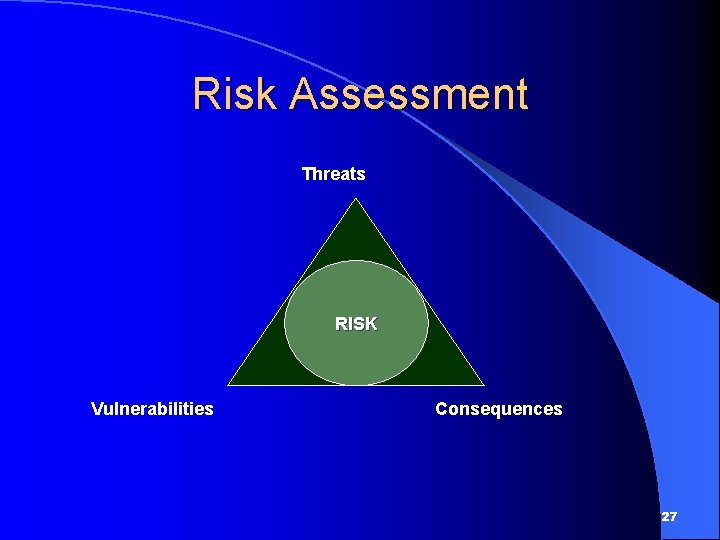
Risk Assessment Threats RISK Vulnerabilities Consequences 27

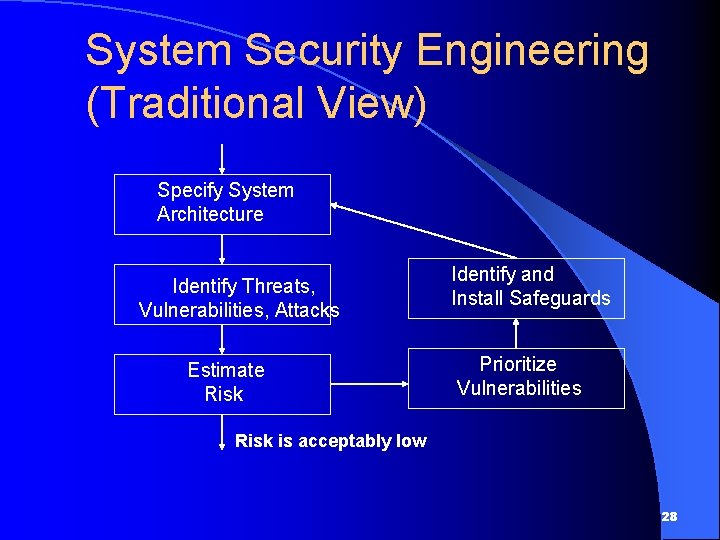
System Security Engineering (Traditional View) Specify System Architecture Identify Threats, Vulnerabilities, Attacks Estimate Risk Identify and Install Safeguards Prioritize Vulnerabilities Risk is acceptably low 28

Human Actions l Domains: – Play: hackers vs. owners – Crime: perpetrators vs. victims – Individual rights: individuals vs. individuals/organizations/government – National security: national level activities

Play l Playing pranks l Actors: hackers/crackers/phreakers l Motivation: challenge, knowledge, thrill l Culture: social/educational – “global networks” – publications – forums l Law

Crime l Intellectual Property Crimes – IT targets: research and development, manufacturing and marketing plan, customer list, etc. – Attacker: insiders, formal insiders – 1996: Economic Espionage Act (U. S. Congress) l Fraud – Telemarketing scam, identity theft, bank fraud, telecommunication fraud, computer fraud and abuse l Fighting crime

Individual Rights l Privacy – Secondary use of information l Free speech – Harmful/disturbing speech – Theft and distribution of intellectual property – Censorship

National Security l Foreign Intelligence – Peace time: protecting national interests l Open channels, human spies, electronic surveillance, electronic hacking (? ) – War time: support military operations – U. S. Intelligence Priorities: l l l Intelligence supporting military needs during operation Intelligence about hostile countries Intelligence about specific transnational threats – Central Intelligence Agency (CIA) – Primary targets in U. S. A. : high technology and defense- related industry

Terrorism l Traditional: – Intelligence collection – Psyops and perception management l New forms: – Exploitation of computer technologies Internet propaganda l Cyber attacks (electronic mail flooding, DOS, etc. ) l l Protection of national infrastructure

Next Class l Making decisions about security l Easttom: Ch. 3