CSCE 201 Introduction to Information Security Fall 2015

















- Slides: 24

CSCE 201 Introduction to Information Security Fall 2015 Data Protection

Sensitive Files l Must be protected from – Hackers – Other users to protect and at what level security policy l How to protect security policy l What CSCE 201 - Farkas 2

Security Mechanism Several alternatives l Which one to choose? l – Level of assurance – User’s preferences (familiarity, ease of use, – – recommendations, etc. ) User’s technical knowledge Availability Financial considerations Etc. CSCE 201 - Farkas 3

Data Protection l Operating System’s Data protection – File encryption, e. g. , MS Window’s support for encryption, https: //msdn. microsoft. com/enus/library/windows/desktop/aa 364223(v=vs. 85). aspx l Best Practices CSCE 201 - Farkas 4

What is Encryption? How secure it is? Can you decrypt the followings? HAY? OROWEU How are you? Hello

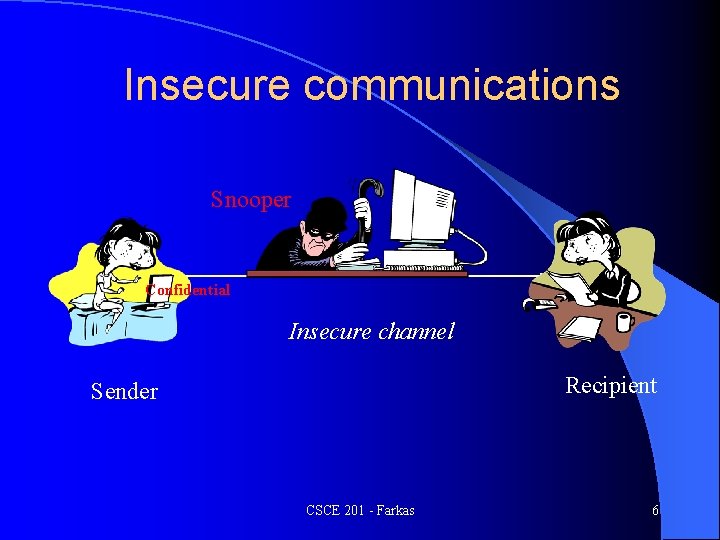
Insecure communications Snooper Confidential Insecure channel Recipient Sender CSCE 201 - Farkas 6

Terminology § Plaintext (cleartext): a message in its original § § § form Ciphertext (cyphertext): an encrypted message Encryption: transformation of a message to hide its meaning Cipher: cryptographic algorithm. A mathematical function used for encryption (encryption algorithm) and decryption (decryption algorithm). CSCE 201 - Farkas 7

Terminology §Decryption: recovering meaning from ciphertext §Cryptography: art and science of keeping messages secure §Cryptanalysis: art and science of breaking ciphertext §Cryptology: study of both cryptography and cryptanalysis CSCE 201 - Farkas 8

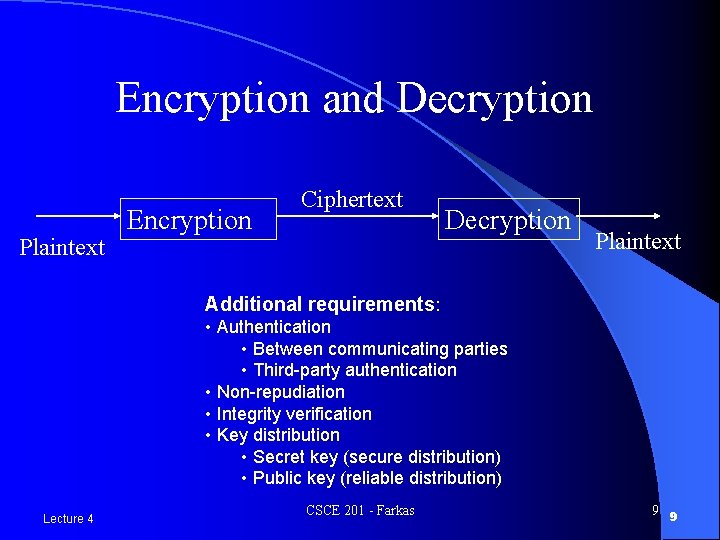
Encryption and Decryption Plaintext Encryption Ciphertext Decryption Plaintext Additional requirements: • Authentication • Between communicating parties • Third-party authentication • Non-repudiation • Integrity verification • Key distribution • Secret key (secure distribution) • Public key (reliable distribution) Lecture 4 CSCE 201 - Farkas 9 9

Cryptanalysis Cryptanalyst’s goal: – Break message – Break key – Break algorithm Lecture 4 CSCE 201 - Farkas 10 10

Secret Key Encryption (Symmetric key, Traditional)

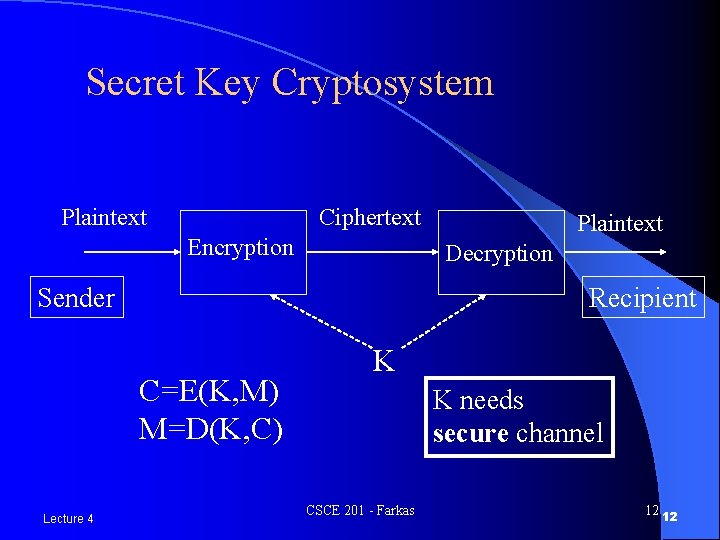
Secret Key Cryptosystem Plaintext Ciphertext Encryption Decryption Sender Recipient C=E(K, M) M=D(K, C) Lecture 4 Plaintext K K needs secure channel CSCE 201 - Farkas 12 12

Basic Encryption Techniques Substitution (confusion) n Permutation (diffusion) n Combinations and iterations of these n Lecture 4 CSCE 201 - Farkas 13 13

Simple Alphabetic Substitution n Assign a new symbol to each plain text symbol randomly or by key, e. g. , C k, A h, B l M=CAB C =k h l §Advantages: large key space 26! §Disadvantages: trivially broken for known plaintext attack, repeated pattern, letter frequency distributions unchanged Lecture 4 CSCE 201 - Farkas 14 14

Transposition n n Letters of the message are rearranged Break patterns, e. g. , columnar transposition Plaintext: this is a test this isat est! n n Lecture 4 tiehssiatst! Advantages: easy to implement Disadvantages: ¨ Trivially broken for known plaintext attack ¨ Easily broken for cipher only attack CSCE 201 - Farkas 15 15

Symmetric Key Encryption Algorithms l Data Encryption Standard (DES) l Advanced Encryption Standard (AES) CSCE 201 - Farkas 16

Public-Key Encryption l Two keys – one is private one is public l Solves the key distribution problem (but need reliable channel) l Provides electronic signatures l Slower than secret-key encryption CSCE 201 - Farkas 17

Public-Key Encryption l Needed for security: – One of the keys must be kept secret – Impossible (at least impractical) to decipher message if no other information is available – Knowledge of algorithm, one of the keys, and samples of ciphertext must be insufficient to determine the other key CSCE 201 - Farkas 18

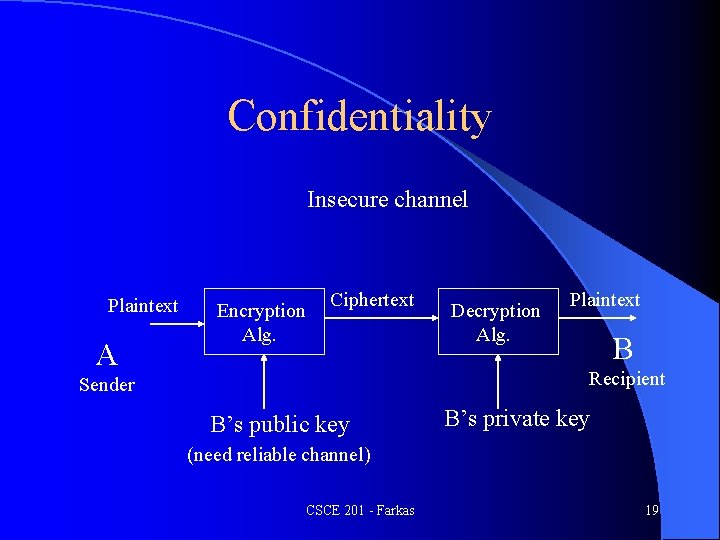
Confidentiality Insecure channel Plaintext A Encryption Alg. Ciphertext Decryption Alg. Plaintext B Recipient Sender B’s public key B’s private key (need reliable channel) CSCE 201 - Farkas 19

Public Key Cryptosystem Concept conceived by Diffie and Hellman in 1976 l Rivest, Shamir, and Adleman (RSA) describe a public key system in 1978 l Many proposals have been broken e. g. , Merkle-Hellman proposal broken by Shamir l Serious candidates (public domain) l – RSA – El Gamal CSCE 201 - Farkas 20

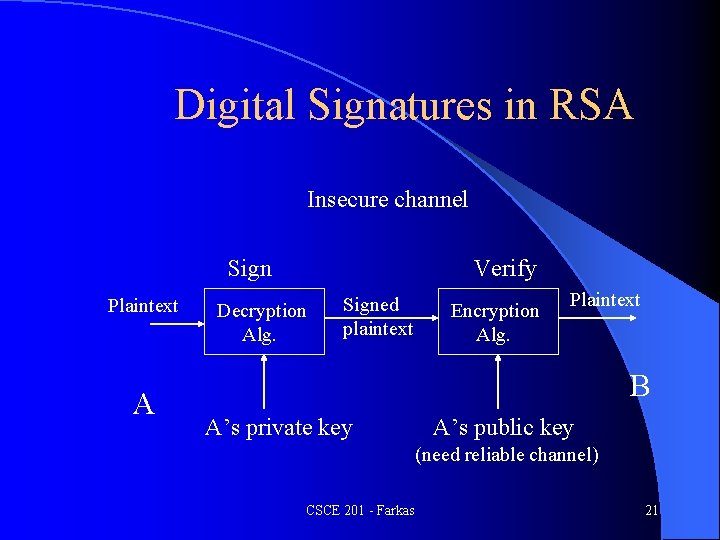
Digital Signatures in RSA Insecure channel Sign Plaintext A Verify Decryption Alg. Signed plaintext Encryption Alg. Plaintext B A’s private key A’s public key (need reliable channel) CSCE 201 - Farkas 21

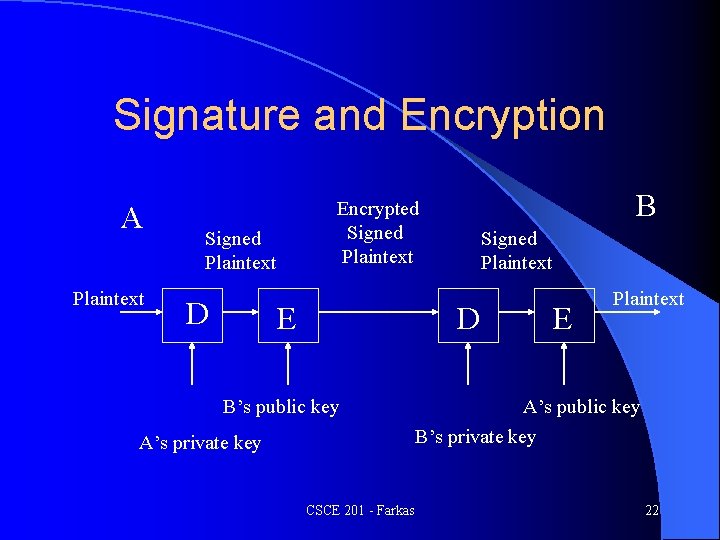
Signature and Encryption A Plaintext Signed Plaintext D B Encrypted Signed Plaintext E Signed Plaintext D B’s public key A’s private key CSCE 201 - Farkas E Plaintext A’s public key B’s private key 22

Hash Functions l Hash function h maps an input x of arbitrary length to a fixed length output h(x) (compression) l Accidental or intentional change to the data will change the hash value l Given h and x, h(x) is easy to compute (ease of computation) CSCE 201 - Farkas 23

Hash functions l Collision resistant (strong collision resistant): if it is computationally infeasible to find any two distinct inputs that has the same output CSCE 201 - Farkas 24