CSCE 201 Identification and Authentication Fall 2015 Required























- Slides: 29

CSCE 201 Identification and Authentication Fall 2015

Required reading list: – An Introduction to Computer Security: The NIST Handbook, http: //csrc. nist. gov/publications/nistpubs/800 -12/handbook. pdf : Chapter 16, IDENTIFICATION AND AUTHENTICATION, pages 180 -192 l Recommended: – Biometrics, from Wikipedia, the free encyclopedia, http: //en. wikipedia. org/wiki/Biometrics – John the Ripper password cracker http: //www. openwall. com/john/ – Brutus the remote password cracker http: //www. hoobie. net/brutus/ l CSCE 201 - Farkas 2

CSCE 201 - Farkas 3

Identification l Something you know l Something you own l Who you are l What you are l Where you are CSCE 201 - Farkas 4

Identification l Allows an entity (a user or a system) to prove its identity to another entity l Typically, the entity whose identity is verified reveals knowledge of some secret S to the verifier l Strong authentication: the entity reveals knowledge of S to the verifier without revealing S to the verifier CSCE 201 - Farkas 5

Identification Information Must be securely maintained by the system. CSCE 201 - Farkas 6

Authentication l Authentication mechanism: verifies the identification information l Access control mechanism: grant privileges upon successful authentication l Logging: record security relevant events in an audit trail CSCE 201 - Farkas 7

Authentication Requirements l Network must ensure – Data exchange is established with addressed peer entity not with an entity that masquerades or replays previous messages l Network must ensure data source is the one claimed CSCE 201 - Farkas 8

Passwords Commonly used method l For each user, system stores (user name, F(password)), where F is some transformation (e. g. , one-way hash) in a password file l – F(password) is easy to compute – From F(password), password is difficult to compute – Password is not stored in the system l When user enters the password, system computes F(password); match provides proof of identity CSCE 201 - Farkas 9

Vulnerabilities of Passwords l Inherent vulnerabilities – Easy to guess or snoop – No control on sharing l Practical vulnerabilities – Visible if unencrypted in distributed and network environment – Susceptible for replay attacks if encrypted naively l Password advantage – Easy to modify compromised password. CSCE 201 - Farkas 10

Attacks on Password l Guessing attack/dictionary attack l Social Engineering l Sniffing l Trojan login l Van Eck sniffing CSCE 201 - Farkas 11

Social Engineering l Attacker asks for password by masquerading as somebody else (not necessarily an authenticated user) l May be difficult to detect l Protection against social engineering: strict security policy and users’ education CSCE 201 - Farkas 12

Password Management Policy l Educate users to make better choices l Define rules for good password selection and ask users to follow them l Ask or force users to change their password periodically l Actively attempt to break user’s passwords and force users to change broken ones l Screen password choices CSCE 201 - Farkas 13

One-time Password Use the password exactly once! CSCE 201 - Farkas 14

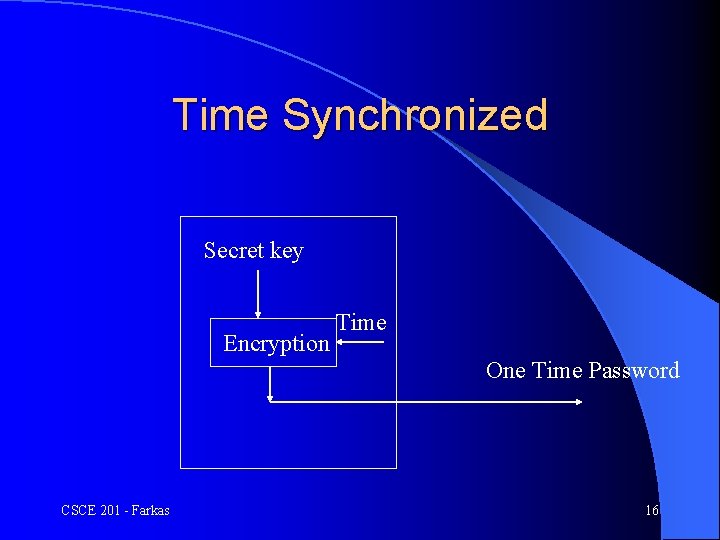
Time Synchronized l There is a hand-held authenticator – It contains an internal clock, a secret key, and a display – Display outputs a function of the current time and the key – It changes about once per minute User supplies the user id and the display value l Host uses the secret key, the function and its clock to calculate the expected output l Login is valid if the values match l CSCE 201 - Farkas 15

Time Synchronized Secret key Encryption Time One Time Password CSCE 201 - Farkas 16

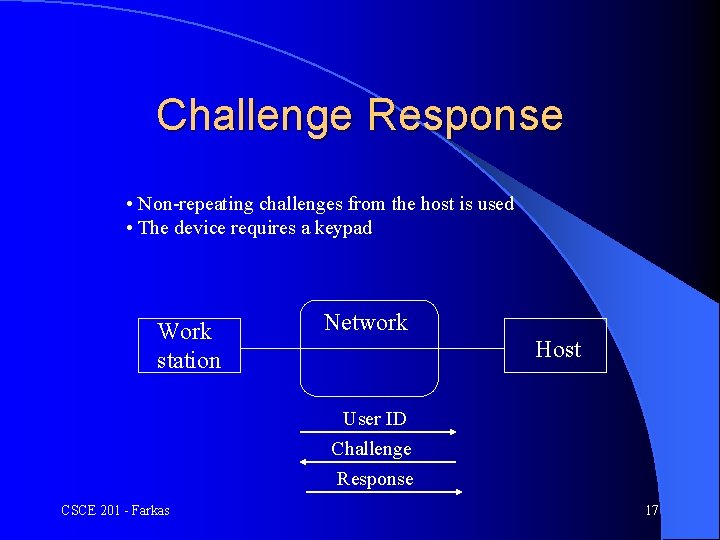
Challenge Response • Non-repeating challenges from the host is used • The device requires a keypad Work station Network Host User ID Challenge Response CSCE 201 - Farkas 17

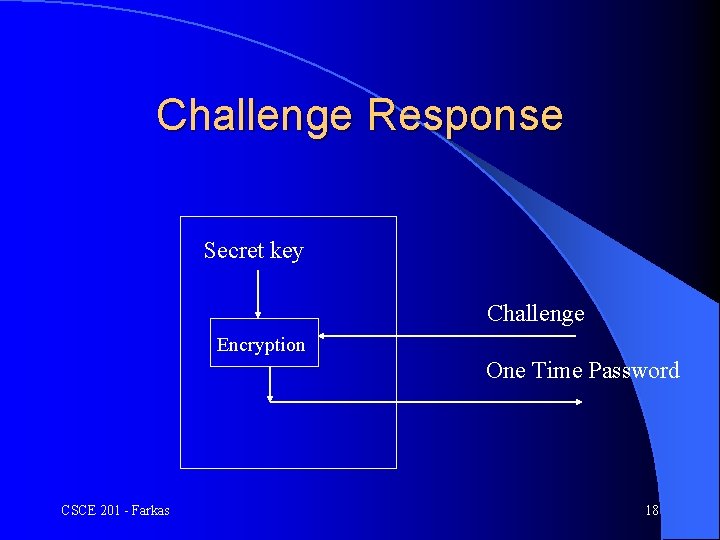
Challenge Response Secret key Challenge Encryption One Time Password CSCE 201 - Farkas 18

Devices with Personal Identification Number (PIN) l Devices are subject to theft, some devices require PIN (something the user knows) l PIN is used by the device to authenticate the user l Problems with challenge/response schemes – Key database is extremely sensitive – This can be avoided if public key algorithms are used CSCE 201 - Farkas 19

Smart Cards l Portable devices with a CPU, I/O ports, and some nonvolatile memory l Can carry out computation required by public key algorithms and transmit directly to the host l Some use biometrics data about the user instead of the PIN CSCE 201 - Farkas 20

Biometrics l Fingerprint l Retina scan l Voice pattern l Signature l Typing style CSCE 201 - Farkas 21

Problems with Biometrics l Expensive – Retina scan (min. cost) about $ 2, 200 – Voice (min. cost) about $ 1, 500 – Signature (min. cost) about $ 1, 000 l False readings – Retina scan 1/10, 000+ – Signature 1/50 – Fingerprint 1/500 l Can’t be modified when compromised CSCE 201 - Farkas 22

Home Computer Security CSCE 201 - Farkas 23

Problem: You don’t remember your password Solutions: 1. Verify that you have typed the letters of your password in the correct case 2. Access a password hint on the Welcome screen 3. Use a password reset disk 4. Log on as administrator to assign a new password to your account CSCE 201 - Farkas 24

Password Case Sensitivity l Check CAPS LOCK key Question: Why do you want to use combination of symbols for your password? CSCE 201 - Farkas 25

Using the Password Reset Disk Create a password reset disk for your user account at the earliest opportunity l How to use the password reset disk l – Microsoft Windows remembers if you have created a password reset disk. Just click use your password reset disk – Follow the instructions of the Password Reset Wizard Question: Why should you safeguard your password reset disk? CSCE 201 - Farkas 26

Use a Password Hint Create a password hint: – Log on to your computer – Click Start, and then click Control Panel – Double-click User Accounts – Click your user account, and then click Change my password – Enter your current password, enter a new password, and then enter the new password again to confirm it – Enter the password hint, and then click Change Password – The change will take effect the next time that you log on l To display the hint, click the question mark (? ) that is next to your user account l CSCE 201 - Farkas 27

Create a Password Reset Disk l l l Click Start, and then click Control Panel Double-click User Accounts Click your user account, and then click Prevent a forgotten password. The Forgotten Password Wizard starts Follow the instructions NOTE: A password reset disk is valid until you create a new one; even if you change your password CSCE 201 - Farkas 28

Next Class Cyber stalking, Fraud and Abuse CSCE 201 - Farkas 29