CSCE 201 Introduction to Information Security Fall 2010


















- Slides: 22

CSCE 201 Introduction to Information Security Fall 2010 Windows XP Access Control

Reading assignments Required: l – – An Introduction to Computer Security: The NIST Handbook, http: //csrc. nist. gov/publications/nistpubs/800 -12/handbook. pdf : Chapter 17, LOGICAL ACCESS CONTROL, pages 194 - 207 Microsoft support, Use access control to restrict who can use your files , 2001, 2005, http: //www. microsoft. com/windowsxp/using/security/learnmore/accesscontr ol. mspx Recommended: l – Sudhakar Govindavajhala and Andrew W. Appel, Windows Access Control Demystied, 2006, http: //www. cs. princeton. edu/~appel/papers/winval. pdf CSCE 201 - Farkas 2

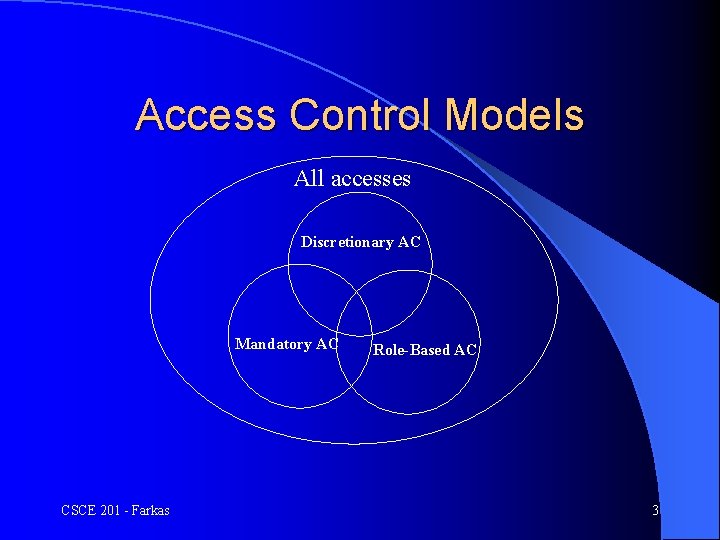
Access Control Models All accesses Discretionary AC Mandatory AC CSCE 201 - Farkas Role-Based AC 3

Windows XP professional Product Documentation Access Control – Selecting where to apply permissions – File and Folder permissions – Permissions on a file server – Changing inherited permissions – Ownership – Explicit vs. inherited permissions – How inheritance affects file and folder permissions – Permissions and security descriptors – Permissions – Security identifiers – Take ownership of a file or folder – Best practices: Access Control – Set, view, change, or remove file and folder permissions – Effective permissions – View effective permissions for files and folders – Set, view, change, or remove special permissions for files and folders – Special permissions for files and folders CSCE 201 - Farkas 4

Best Practices http: //www. microsoft. com/resources/documentation/windows/xp/all/ proddocs/en-us/acl_topnode. mspx? mfr=true l Permissions l User Rights CSCE 201 - Farkas 5

Permissions l Apply to objects l Selecting where to apply permissions – Permission Entry for File or Folder Name – Apply onto list – Check box: Apply these permissions to objects and/or containers within this container only (Default: empty check box) CSCE 201 - Farkas 6

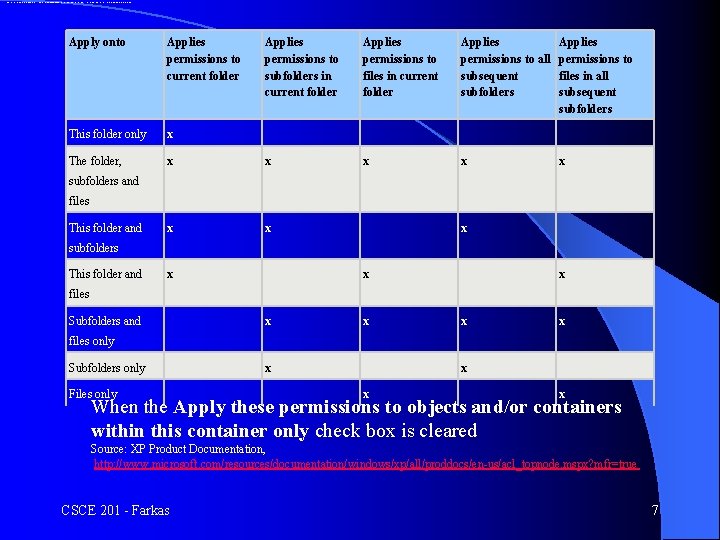
When the Apply these permissions to objects and/or containers within this container only check box is cleared Apply onto Applies permissions to current folder Applies permissions to subfolders in current folder Applies permissions to files in current folder Applies permissions to all subsequent subfolders Applies permissions to files in all subsequent subfolders This folder only x The folder, x x x x Subfolders only x x Files only x x subfolders and files This folder and subfolders This folder and files Subfolders and files only When the Apply these permissions to objects and/or containers within this container only check box is cleared Source: XP Product Documentation, http: //www. microsoft. com/resources/documentation/windows/xp/all/proddocs/en-us/acl_topnode. mspx? mfr=true CSCE 201 - Farkas 7

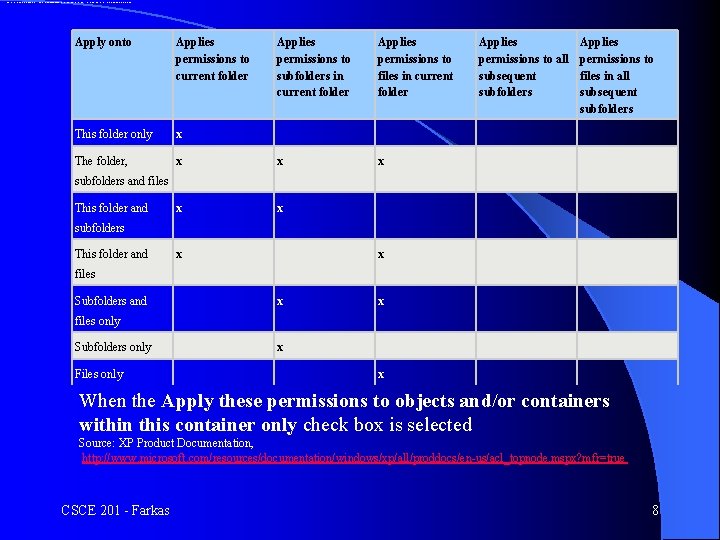
When the Apply these permissions to objects and/or containers within this container only check box is cleared Apply onto Applies permissions to current folder Applies permissions to subfolders in current folder Applies permissions to files in current folder Applies permissions to all subsequent subfolders Applies permissions to files in all subsequent subfolders This folder only x The folder, x x x Subfolders only x Files only x subfolders and files This folder and subfolders This folder and files Subfolders and files only When the Apply these permissions to objects and/or containers within this container only check box is selected Source: XP Product Documentation, http: //www. microsoft. com/resources/documentation/windows/xp/all/proddocs/en-us/acl_topnode. mspx? mfr=true CSCE 201 - Farkas 8

To set, view, change, or remove special permissions for files and folder Open Windows Explorer, and then locate the file or folder for which you want to set special permissions 2. Right-click the file or folder, click Properties, and then click the Security tab 3. Click Advanced, and then do one of the following: 1. CSCE 201 - Farkas 9

Advanced Setting To Do this Set special permissions for an additional group Click Add. In Name, type the name of the user or user or group, and then click OK. View or change special permissions for an Click the name of the group or user and then existing group or user click Edit. Remove an existing group or user and its special Click the name of the group or user and then permissions click Remove. If the Remove button is unavailable, clear the Inherit from parent the permission entries that apply to child objects. Include these with entries explicitly defined here check box, click Remove, and skip the next two steps. CSCE 201 - Farkas 10

Permission Setting 4. 5. 6. 7. In the Permissions box, select or clear the appropriate Allow or Deny check box In Apply onto, select the folders or subfolders you would like these permissions to be applied to To configure security so that the subfolders and files will not inherit these permissions, clear the Apply these permissions to objects and/or containers within this container only check box Click OK and then, in Advanced Security Settings for Folder. Name, click OK CSCE 201 - Farkas 11

Permission Assignment Assign permissions to groups rather than to users – administration l Set permission to be inheritable to child objects. l Assign Full control, if appropriate, rather than individual permissions l Deny should be used for these special cases – Exclude a subset of a group which has Allowed permissions – Exclude one special permission when you have already granted full control to a user or group l CSCE 201 - Farkas 12

User Rights l Administrators can assign specific rights to group accounts or to individual user accounts l Apply to user accounts l Define capabilities at the local level l Can apply to individual user accounts or a group account CSCE 201 - Farkas 13

Group Account Members of a group automatically inherit the rights associated with that group l Rights are applied to all members of the group while they remain members l If a user is a member of multiple groups, the user's rights are cumulative l Simplifies the task of user account administration l CSCE 201 - Farkas 14

User Rights l Types of user rights: – Privileges: specifies allowable actions on the system, e. g. , the right to back up files and directories – Logon rights: specifies the ways in which a user can log onto a system, e. g. , such as the right to log on to a system remotely In general, user rights assigned to one group do not conflict with the rights assigned to another group l Exception: Logon rights l CSCE 201 - Farkas 15

Logon Rights Control access to a system l Logon Rights and default settings for Windows XP Professional are available at http: //www. microsoft. com/resources/documentation/windows/xp/all/pr oddocs/en-us/acl_topnode. mspx? mfr=true l Examples: – Log on locally, Default setting: Administrators, Power Users, Guest, and Backup Operators – Deny access to this computer from network, Default setting: No one – Access this computer from a network, Default setting: Administrators, Everyone, Users, Power Users, and Backup Operators l CSCE 201 - Farkas 16

Privileges Act as Part of the Operating System, Add Workstations to a Domain, Back Up Files and Directories, Change the System Time, Create a Token Object, Create Permanent Shared Objects, Debug Programs, Force Shutdown from a Remote System, Generate Security Audits, etc. l Some of the privileges can override permissions set on an object – E. g. , the right to perform a backup, takes precedence over all file and directory permissions l CSCE 201 - Farkas 17

Privileges, which can override permissions set on an object l l l Take Ownership of Files or Other Object – grants Write. Owner access to an object Manage Auditing and Security Log -- provides several abilities including access to the security log, overriding access restrictions to the security log Back Up Files and Directories – grants read and write access to an object Restore Files and Directories – grants read and write access to an object Debug Programs -- grants read or open access to an object Bypass Traverse Checking -- provides the reverse access on directories CSCE 201 - Farkas 18

Assigning User Rights l 1. 2. 3. 4. 5. Assigned through the Local Policies node of Group Policy Log on using an administrator account Open the Active Directory Users and Computers tool Right-click the container holding the domain controller and click Properties Click the Group Policy tab, and then click Edit to edit the Default Domain Policy In the Group Policy window, expand Computer Configuration, navigate to Windows Settings, to Security Settings, and then to Local Policies CSCE 201 - Farkas 19

Assigning User Rights Select User Rights Assignment 7. To configure user rights assignment, double-click a user right or right-click on it and select Security. This opens a Security Policy Setting dialog box 8. Open the Security Policy Setting dialog box for the user right to be modified 9. Select Define these policy settings to define the policy. 10. To apply the right to a user or group, click Add 11. In the Add user or group dialog box, click Browse. This opens the Select Users Or Groups dialog box. The right can now be applied to users and groups 6. CSCE 201 - Farkas 20

User Rights Assign rights as high in the container tree as possible – administration l Apply inheritance to propagate rights through the tree l Administrators should – use an account with restrictive permissions to perform routine, non-administrative tasks – use an account with broader permissions only when performing specific administrative tasks l CSCE 201 - Farkas 21

Next Class l Back up procedures CSCE 201 - Farkas 22