CSCE 201 Intrusion Detection Fall 2015 Historical Research


















- Slides: 33

CSCE 201 Intrusion Detection Fall 2015

Historical Research - Prevention It is better to prevent something than to plan for loss. CSCE 201 - Farkas 2

Misuse Prevention l Prevention techniques: first line of defense l Secure local and network resources l Techniques: cryptography, identification, authentication, authorization, access control, security filters, etc. Problem: Losses occur! CSCE 201 - Farkas 3

Contributing Factors for Misuse l Many security flaws in systems l Secure systems are expensive l Secure systems are not user-friendly l “Secure systems” still have flaws l Insider Threat l Hackers’ skills and tools improve CSCE 201 - Farkas 4

Need: l Intrusion Prevention: protect system resources l Intrusion Detection: (second line of defense) discriminate intrusion attempts from normal system usage l Intrusion Recovery: cost effective recovery models CSCE 201 - Farkas 5

Why Intrusion Detection? l Second line of defense l Deter intruders l Catch intruders l Prevent threats to occur (real-time IDS) l Improve prevention/detection techniques CSCE 201 - Farkas 6

Intrusion Detection - Milestones l 1980: Deviation from historical system usage (Anderson) l 1987: framework for general-purpose intrusion detection system (Denning) l 1988: intrusion detection research splits – Attack signatures based detection (MIDAS) – Anomaly detection based detection (IDES) CSCE 201 - Farkas 7

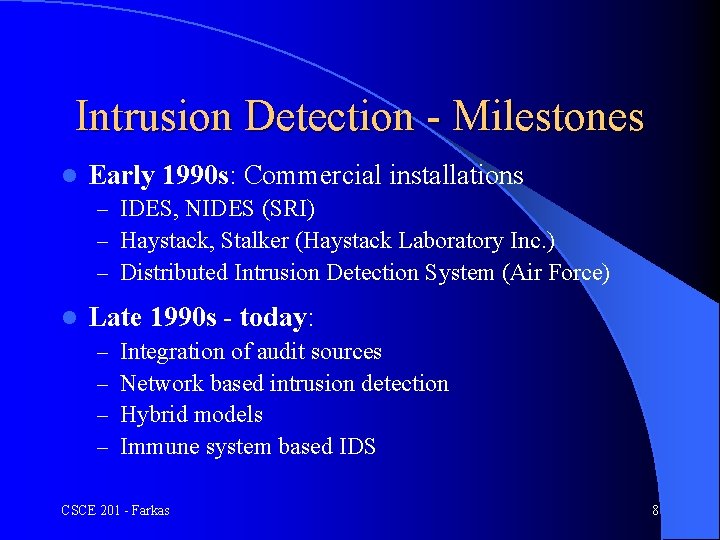
Intrusion Detection - Milestones l Early 1990 s: Commercial installations – IDES, NIDES (SRI) – Haystack, Stalker (Haystack Laboratory Inc. ) – Distributed Intrusion Detection System (Air Force) l Late 1990 s - today: – – Integration of audit sources Network based intrusion detection Hybrid models Immune system based IDS CSCE 201 - Farkas 8

Terminology l l l l Audit: activity of looking at user/system behavior, its effects, or the collected data Profiling: looking at users or systems to determine what they usually do Anomaly: abnormal behavior Misuse: activity that violates the security policy Outsider: someone without access right to the system Insider: someone with access right to the system Intrusion: misuse by outsiders and insiders CSCE 201 - Farkas 9

Phases of Intrusion l Intelligence gathering: attacker observes the system to determine vulnerabilities l Planning: attacker decide what resource to attack (usually least defended component) l Attack: attacker carries out the plan l Hiding: attacker covers tracks of attack l Future attacks: attacker installs backdoors for future entry points CSCE 201 - Farkas 10

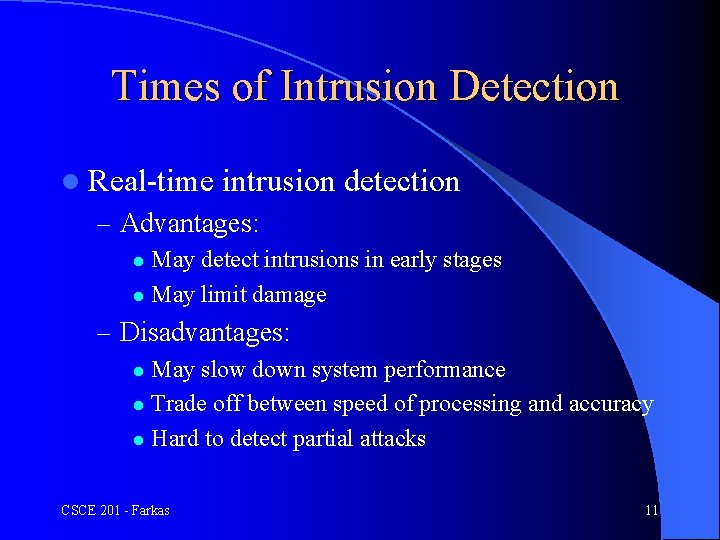
Times of Intrusion Detection l Real-time intrusion detection – Advantages: May detect intrusions in early stages l May limit damage l – Disadvantages: May slow down system performance l Trade off between speed of processing and accuracy l Hard to detect partial attacks l CSCE 201 - Farkas 11

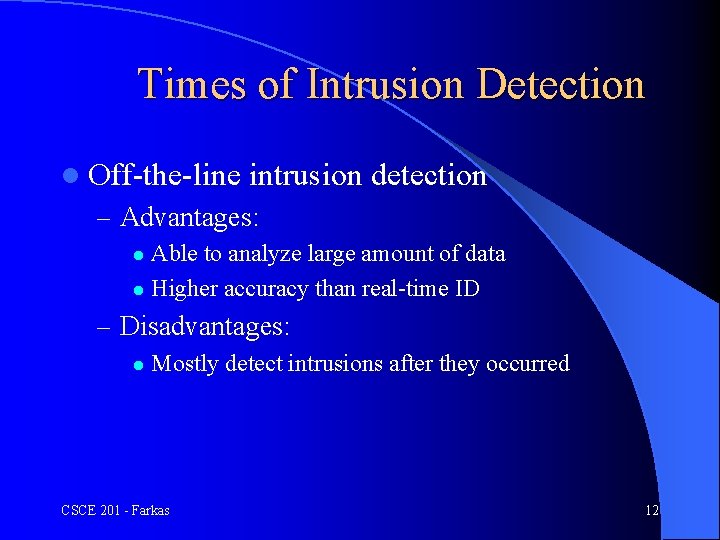
Times of Intrusion Detection l Off-the-line intrusion detection – Advantages: Able to analyze large amount of data l Higher accuracy than real-time ID l – Disadvantages: l Mostly detect intrusions after they occurred CSCE 201 - Farkas 12

Audit Data Format, granularity and completeness depend on the collecting tool l Examples l – – l System tools collect data (login, mail) Additional collection of low system level “Sniffers” as network probes Application auditing Needed for – Establishing guilt of attackers – Detecting subversive user activity CSCE 201 - Farkas 13

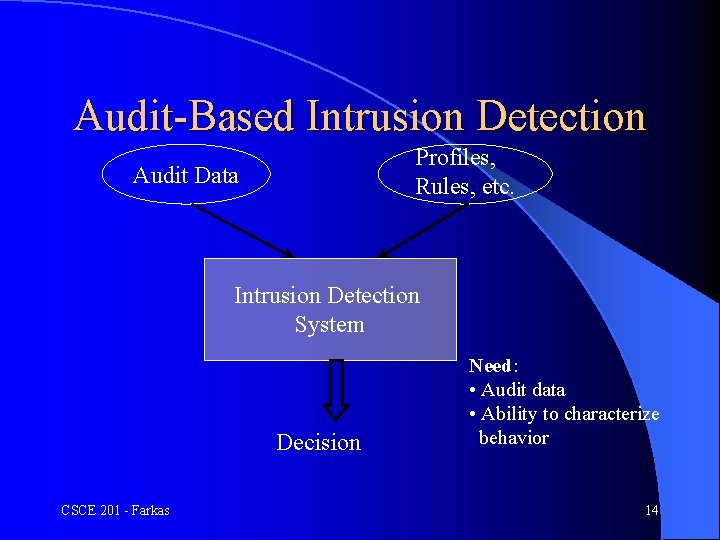
Audit-Based Intrusion Detection Profiles, Rules, etc. Audit Data Intrusion Detection System Decision CSCE 201 - Farkas Need: • Audit data • Ability to characterize behavior 14

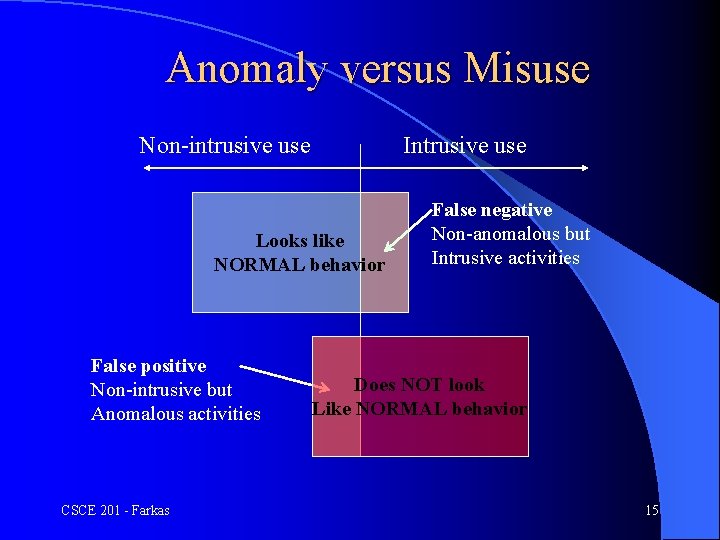
Anomaly versus Misuse Non-intrusive use Intrusive use Looks like NORMAL behavior False positive Non-intrusive but Anomalous activities CSCE 201 - Farkas False negative Non-anomalous but Intrusive activities Does NOT look Like NORMAL behavior 15

False Positive vs. False Negative l False positive: non-intrusive but anomalous activity – Security policy is not violated – Cause unnecessary interruption – May cause users to become unsatisfied l False negative: non-anomalous but intrusive activity – Security policy is violated – Undetected intrusion CSCE 201 - Farkas 16

Intrusion Detection Techniques Anomaly Detection 2. Misuse Detection 3. Hybrid Misuse/Anomaly Detection 4. Immune System Based IDS 1. CSCE 201 - Farkas 17

Rules and Profiles l Statistical techniques: – Collect usage data to statistically analyze data – Good for both anomaly-based and misuse-based detection: l l Anomaly-based: standards for normal behavior. Warning when deviation is detected Misuse-based: standards for misuse. Warning when phases of an identified attack are detected – Threshold detection l E. g. , number of failed logins, number of accesses to resources, size of downloaded files, etc. CSCE 201 - Farkas 18

Rules and Profiles l Rule-based techniques: – Define rules to describe normal behavior or known attacks – Good for both anomaly-based and misuse-based detection: Anomaly-based: looks for deviations from previous usage l Misuse-based: define rules to represent known attacks l CSCE 201 - Farkas 19

Anomaly Detection Techniques Assume that all intrusive activities are necessarily anomalous flag all system states that very from a “normal activity profile”. CSCE 201 - Farkas 20

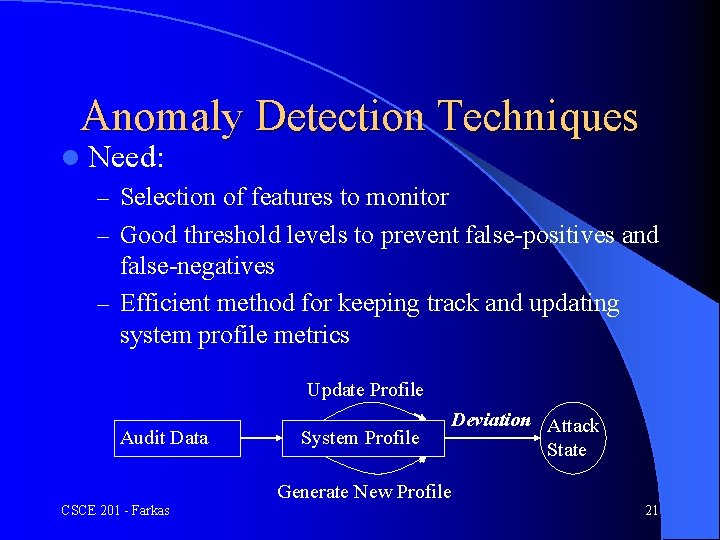
Anomaly Detection Techniques l Need: – Selection of features to monitor – Good threshold levels to prevent false-positives and false-negatives – Efficient method for keeping track and updating system profile metrics Update Profile Audit Data System Profile Deviation Attack State Generate New Profile CSCE 201 - Farkas 21

Misuse Detection Techniques Represent attacks in the form of pattern or a signature (variations of same attack can be detected) Problem! Cannot represent new attacks CSCE 201 - Farkas 22

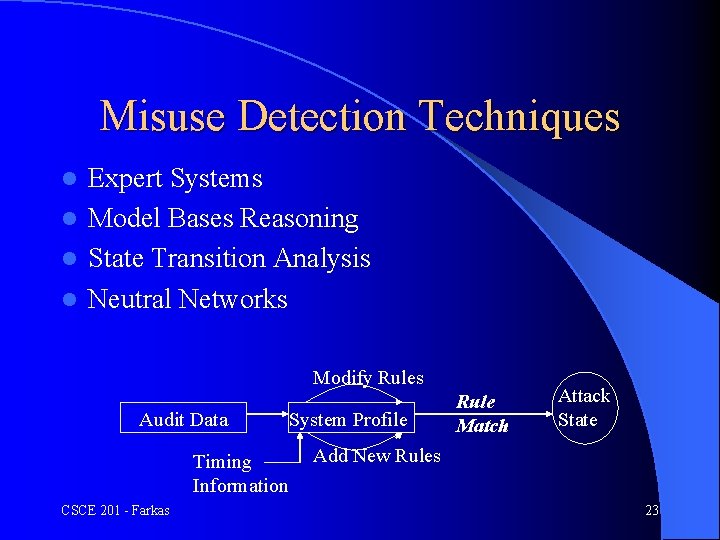
Misuse Detection Techniques Expert Systems l Model Bases Reasoning l State Transition Analysis l Neutral Networks l Modify Rules Audit Data Timing Information CSCE 201 - Farkas System Profile Rule Match Attack State Add New Rules 23

Hybrid Misuse / Anomaly Detection Anomaly and misuse detection approaches together l Example: l 1. Browsing using “nuclear” is not misuse but might be anomalous 2. Administrator accessing sensitive files is not anomalous but might be misuse CSCE 201 - Farkas 24

Immune System Based ID l Detect intrusions by identifying suspicious changes in system-wide activities. l System health factors: – Performance – Use of system resources l Need: CSCE 201 - Farkas identify system-wide measurements 25

Immune System Based ID l Principal features of human immune system that are relevant to construct robust computer systems: 1. Multi-layered protection 2. Distributed detection 3. Diversity of detection 4. Inexact matching ability 5. Detection of unseen attacks CSCE 201 - Farkas 26

Intrusion Types l l l Doorknob rattling Masquerade attacks Diversionary Attack Coordinated attacks Chaining Loop-back CSCE 201 - Farkas 27

Doorknob Rattling Attack on activity that can be audited by the system (e. g. , password guessing) l Number of attempts is lower than threshold l Attacks continue until l – All targets are covered or – Access is gained CSCE 201 - Farkas 28

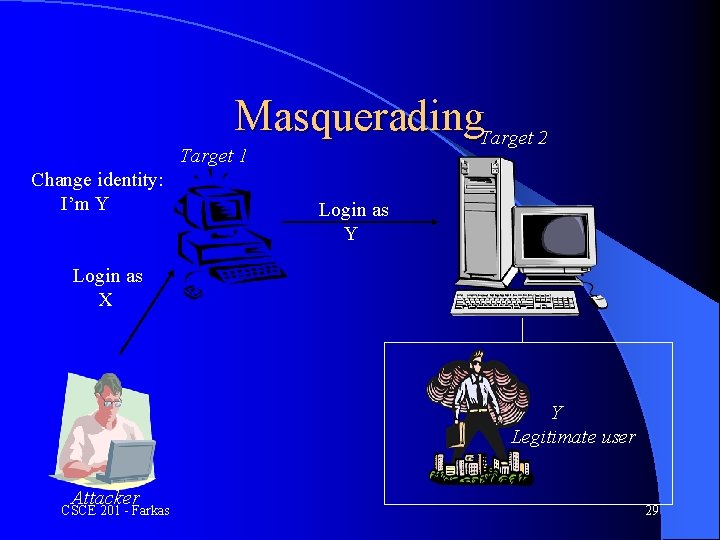
Masquerading. Target 2 Target 1 Change identity: I’m Y Login as X Y Legitimate user Attacker CSCE 201 - Farkas 29

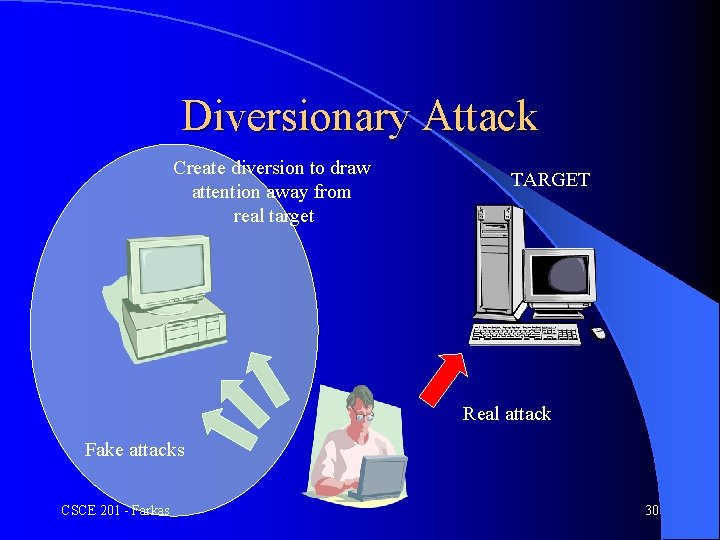
Diversionary Attack Create diversion to draw attention away from real target TARGET Real attack Fake attacks CSCE 201 - Farkas 30

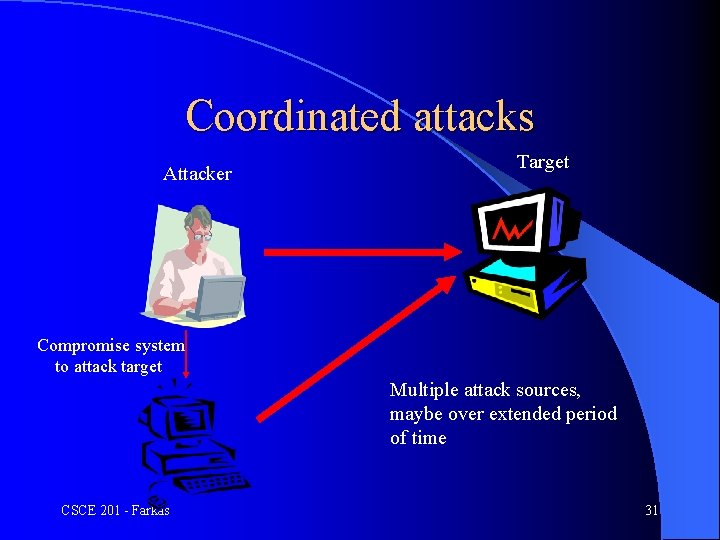
Coordinated attacks Attacker Target Compromise system to attack target Multiple attack sources, maybe over extended period of time CSCE 201 - Farkas 31

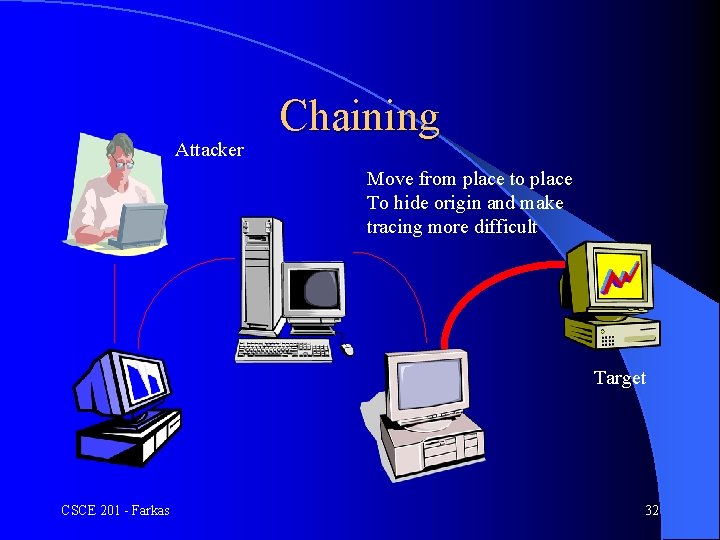
Attacker Chaining Move from place to place To hide origin and make tracing more difficult Target CSCE 201 - Farkas 32

Intrusion Recovery Actions to avoid further loss from intrusion. l Terminate intrusion and protect against reoccurrence. l Reconstructive methods based on: l – Time period of intrusion – Changes made by legitimate users during the effected period – Regular backups, audit trail based detection of effected components, semantic based recovery, minimal rollback for recovery. CSCE 201 - Farkas 33