CSC 482582 Computer Security Access Control CSC 482582











- Slides: 33

CSC 482/582: Computer Security Access Control CSC 482/582: Computer Security

Topics 1. 2. 3. 4. 5. 6. 7. What is Access Control? Access Control Matrix <<Access Control Matrix Activity>> Access Control Lists Unix Access Control SQL Access Control Hardware Protection CSC 482/582: Computer Security

Why study Access Control? Center of gravity of computer security Why do we authenticate users? 2. What security features do OSes provide? 3. What’s the purpose of cryptography? 4. Access Control is pervasive. 1. Computer Science meets Security Engineering. • We’ll start with theory (computer science) • Then examine implementations (engineering) CSC 482/582: Computer Security

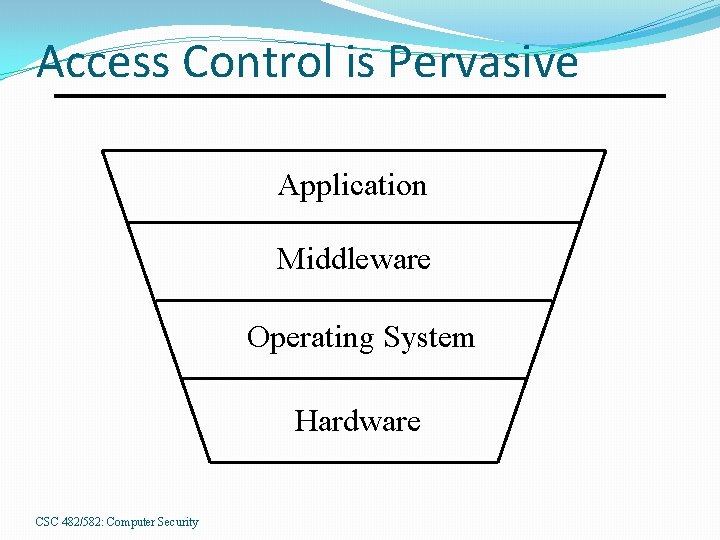
Access Control is Pervasive Application Middleware Operating System Hardware CSC 482/582: Computer Security

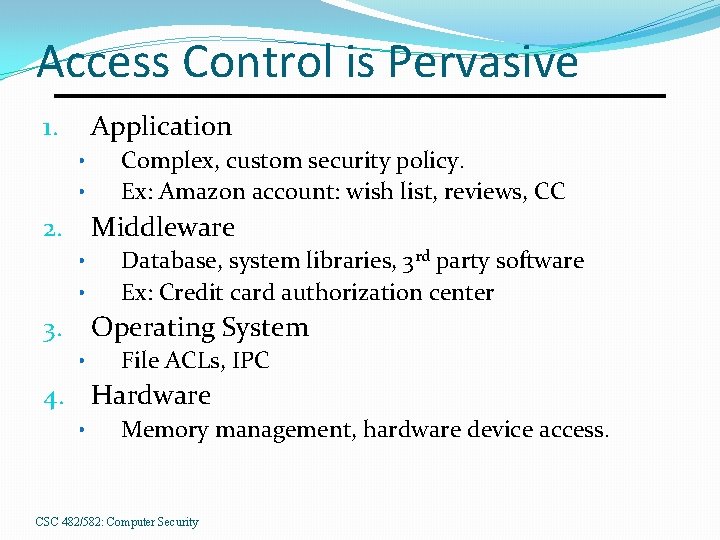
Access Control is Pervasive Application 1. • • Complex, custom security policy. Ex: Amazon account: wish list, reviews, CC Middleware 2. • • Database, system libraries, 3 rd party software Ex: Credit card authorization center Operating System 3. • File ACLs, IPC 4. Hardware • Memory management, hardware device access. CSC 482/582: Computer Security

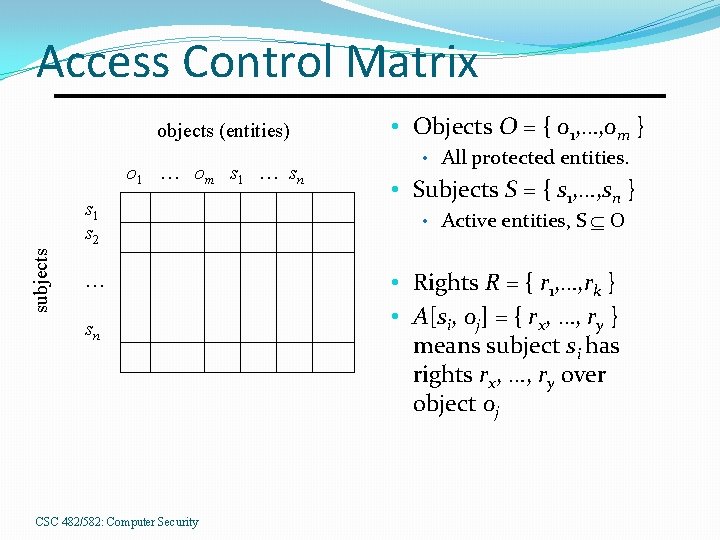
Access Control Matrix objects (entities) o 1 … om s 1 … sn subjects s 1 s 2 … sn CSC 482/582: Computer Security • Objects O = { o 1, …, om } • All protected entities. • Subjects S = { s 1, …, sn } • Active entities, S O • Rights R = { r 1, …, rk } • A[si, oj] = { rx, …, ry } means subject si has rights rx, …, ry over object oj

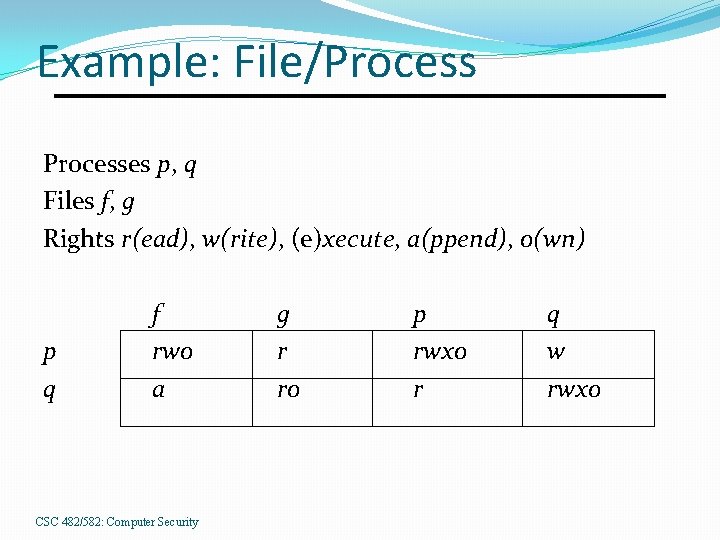
Example: File/Processes p, q Files f, g Rights r(ead), w(rite), (e)xecute, a(ppend), o(wn) p q f rwo a CSC 482/582: Computer Security g r ro p rwxo r q w rwxo

How can we implement the ACM? Problem: scale • Thousands of subjects. • Millions of objects. Solutions • Permissions only exist on containers • Buckets in Amazon S 3. • Folders in AFS. • Default permissions • Based on user (umask setting in Unix). • Based on parent directory (settable on both Unix, Windows). • Group subjects together as a single entities. CSC 482/582: Computer Security

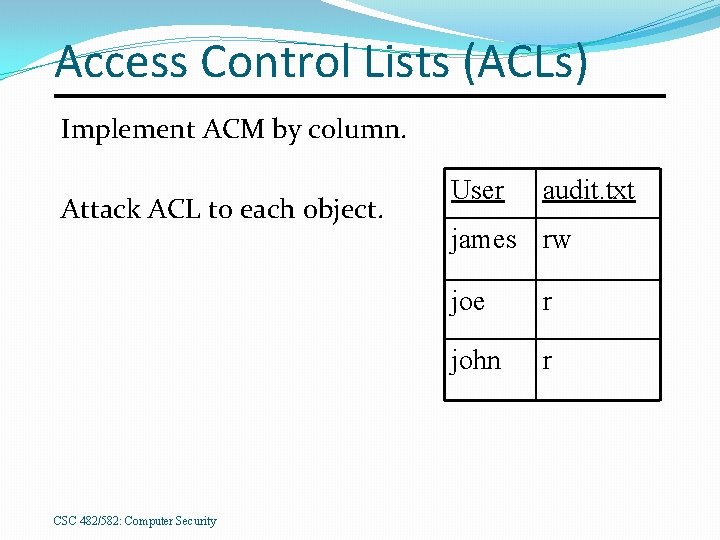
Access Control Lists (ACLs) Implement ACM by column. Attack ACL to each object. CSC 482/582: Computer Security User audit. txt james rw joe r john r

ACL Questions 1. 2. 3. 4. 5. 6. Which subjects can modify an object’s ACL? Do ACLs apply to privileged users? Do ACLs support groups and wildcards? How are ACL conflicts resolved? What are default permissions? How can a subject’s rights be revoked? CSC 482/582: Computer Security

Which subjects can modify an ACL? Create an own right for an ACL. • Only subjects with own right can modify ACL. Creating an object also creates object’s ACL. • Usually creator given own right at this time. • Other default rights may be set at creation too. CSC 482/582: Computer Security

Do ACLs apply to privileged users? Many systems have privileged users. • UNIX: root. • Windows: administrator. Should ACLs apply to privileged users? • Need read access to all objects for backups. • What security problems are produced by ignoring ACLs for privileged users? CSC 482/582: Computer Security

How are ACL conflicts resolved? What happens when multiple ACL entries give different permissions to same subject? • • • First entry wins. Last entry wins. Deny wins over allow. CSC 482/582: Computer Security

What are the default permissions? How are default ACLs determined? • Subject sets default permissions, like UNIX umask. • Inheritance • Objects in hierarchical system inherit ACLs of parent object. • Subjects inherit sets of default permissions from their parent subjects. CSC 482/582: Computer Security

How are rights revoked? From object: Removal of subject’s rights to object. • Delete entries for subject from ACL. • What about subjects that are currently using the object? From subject: Removal of subject’s rights to all objects. • Very expensive (millions of objects. ) • Most systems don’t support. • Why isn’t disabling subject’s account sufficient? CSC 482/582: Computer Security

Principle of Least Privilege • Subjects should be granted the least amount of privilege necessary to complete their tasks. • Don't run with administrative privilege unless needed. • Minimize code running in supervisor mode. • Systems must be designed to support this principle. • Desktop programs run with all user permissions — your word processor and web browser have the same access. • Android programs have their own user accounts, and are limited to accessing files accessible by that account. CSC 482/582: Computer Security

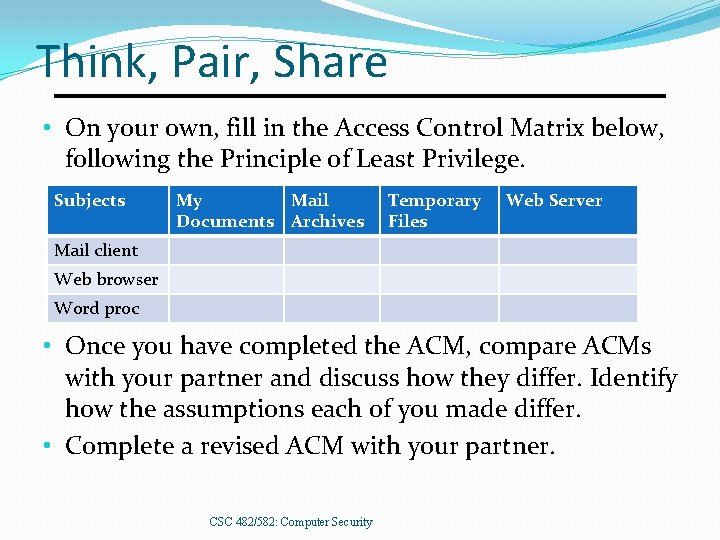
Think, Pair, Share • On your own, fill in the Access Control Matrix below, following the Principle of Least Privilege. Subjects My Mail Documents Archives Temporary Files Web Server Mail client Web browser Word proc • Once you have completed the ACM, compare ACMs with your partner and discuss how they differ. Identify how the assumptions each of you made differ. • Complete a revised ACM with your partner. CSC 482/582: Computer Security

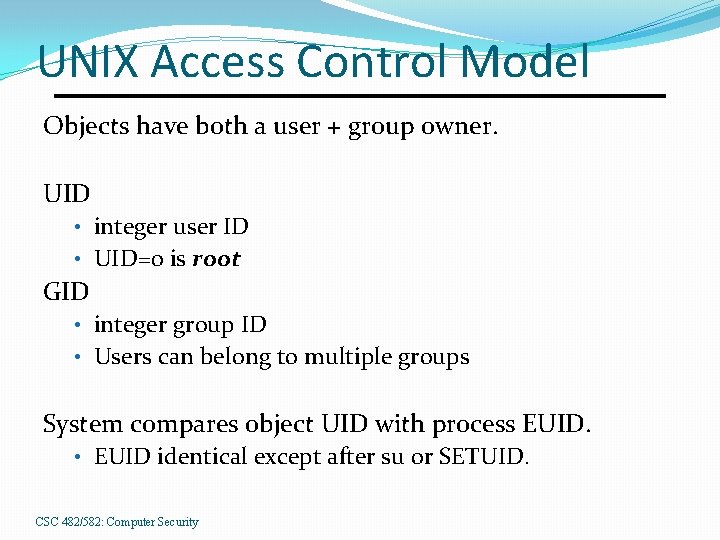
UNIX Access Control Model Objects have both a user + group owner. UID • integer user ID • UID=0 is root GID • integer group ID • Users can belong to multiple groups System compares object UID with process EUID. • EUID identical except after su or SETUID. CSC 482/582: Computer Security

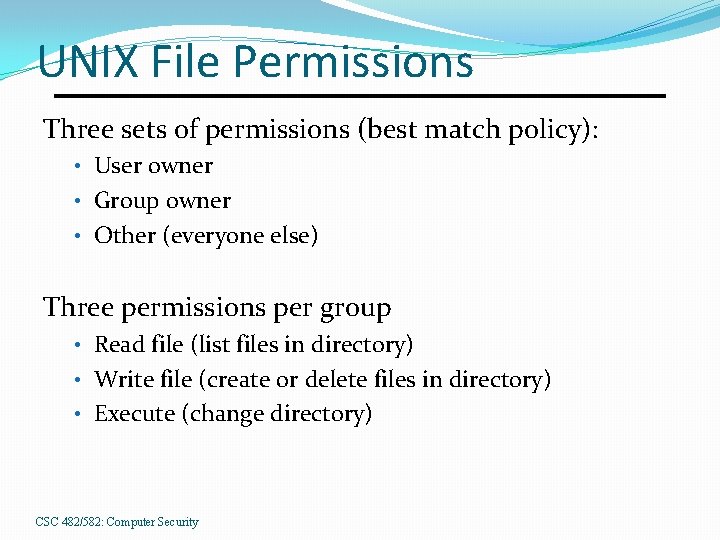
UNIX File Permissions Three sets of permissions (best match policy): • User owner • Group owner • Other (everyone else) Three permissions per group • Read file (list files in directory) • Write file (create or delete files in directory) • Execute (change directory) CSC 482/582: Computer Security

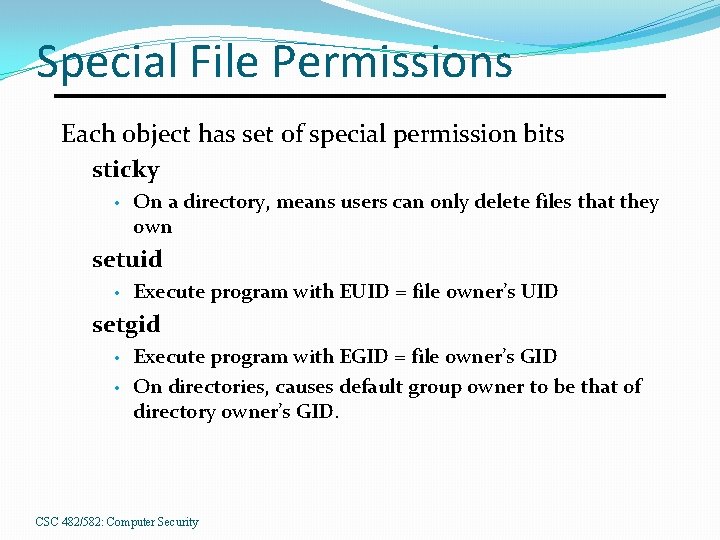
Special File Permissions Each object has set of special permission bits sticky • On a directory, means users can only delete files that they own setuid • Execute program with EUID = file owner’s UID setgid • • Execute program with EGID = file owner’s GID On directories, causes default group owner to be that of directory owner’s GID. CSC 482/582: Computer Security

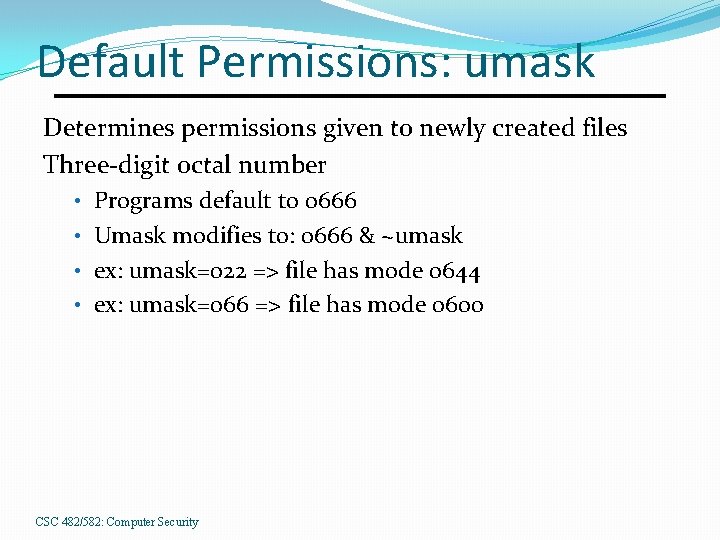
Default Permissions: umask Determines permissions given to newly created files Three-digit octal number • Programs default to 0666 • Umask modifies to: 0666 & ~umask • ex: umask=022 => file has mode 0644 • ex: umask=066 => file has mode 0600 CSC 482/582: Computer Security

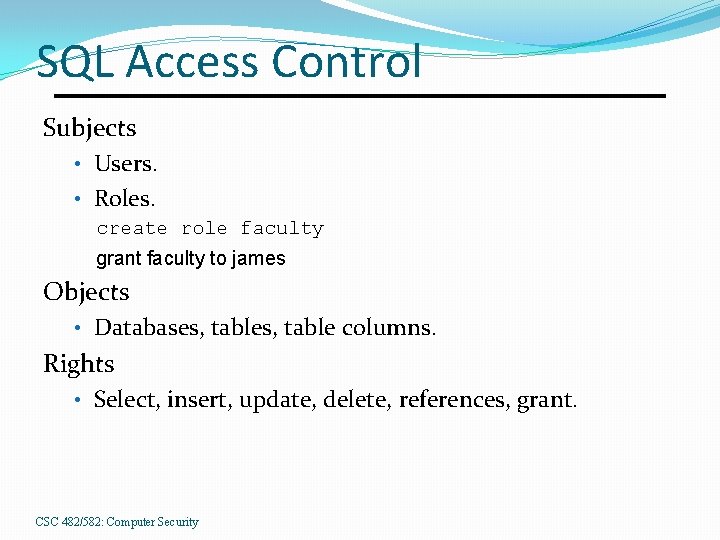
SQL Access Control Subjects • Users. • Roles. create role faculty grant faculty to james Objects • Databases, table columns. Rights • Select, insert, update, delete, references, grant. CSC 482/582: Computer Security

SQL Access Control The grant command gives access to a user grant select on students to james or a role: grant select, insert, update on grades to faculty and includes power to grant options: grant insert on students to registrar with grant option The revoke command removes access revoke insert on grades from faculty CSC 482/582: Computer Security

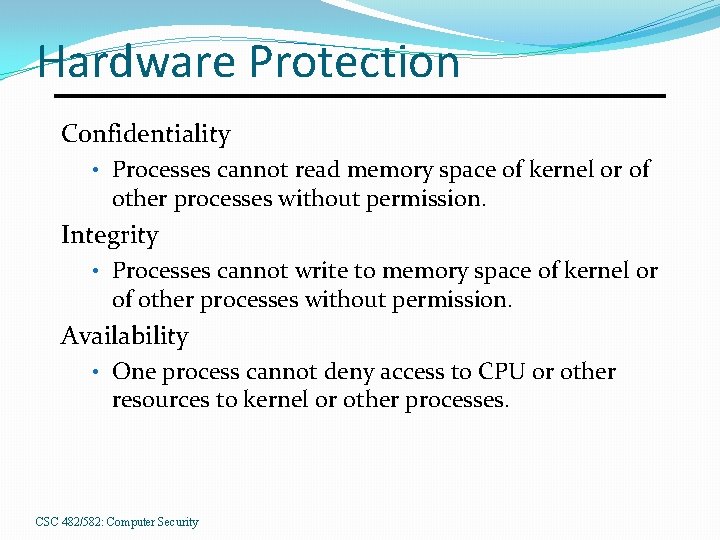
Hardware Protection Confidentiality • Processes cannot read memory space of kernel or of other processes without permission. Integrity • Processes cannot write to memory space of kernel or of other processes without permission. Availability • One process cannot deny access to CPU or other resources to kernel or other processes. CSC 482/582: Computer Security

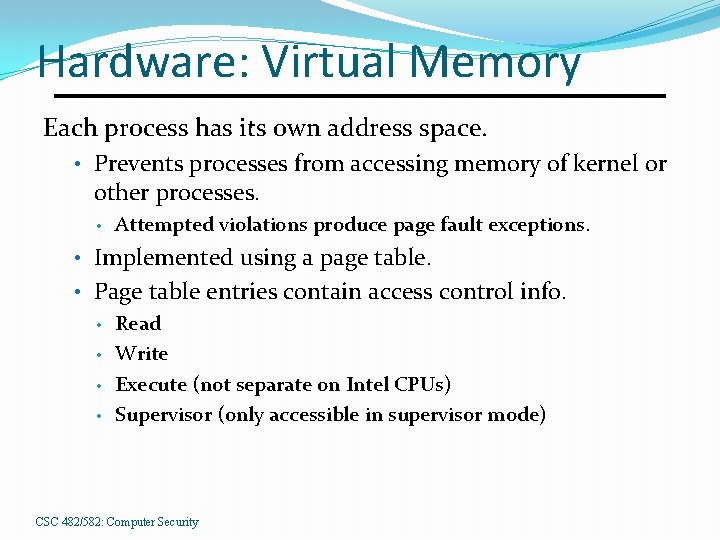
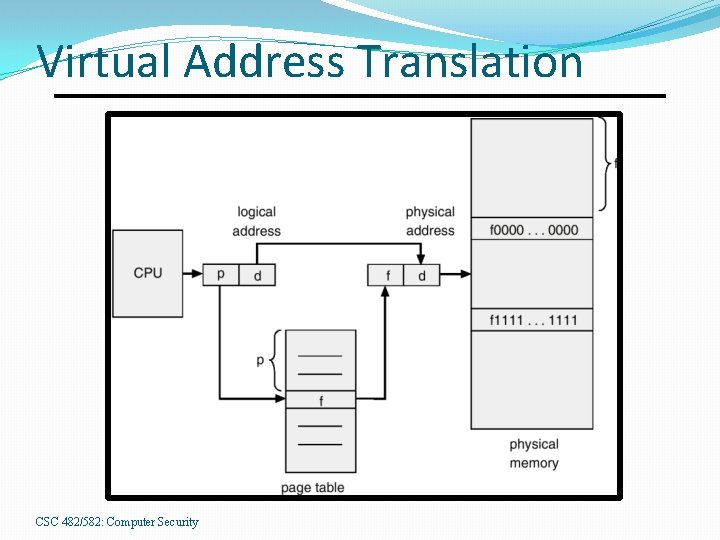
Hardware: Virtual Memory Each process has its own address space. • Prevents processes from accessing memory of kernel or other processes. • Attempted violations produce page fault exceptions. • Implemented using a page table. • Page table entries contain access control info. • Read • Write • Execute (not separate on Intel CPUs) • Supervisor (only accessible in supervisor mode) CSC 482/582: Computer Security

Virtual Address Translation CSC 482/582: Computer Security

Hardware: System Timer Processes can voluntarily give up control to OS via system calls to request OS services. • SYSENTER, INT 2 e Timer interrupt • Programmable Interval Timer chip. • Happens every 1 -100 OS, depending on OS. • Transfers control from process to OS. • Ensures no process can deny availability of machine to kernel or other processes. CSC 482/582: Computer Security

Hardware: Protection Rings CPU functionality limiting by which ring it runs in • x 86 ring 0 is supervisor mode • OS kernel runs in this mode, has access to all instructions. • x 86 ring 3 is user mode • User programs run here, no access to privileged instructions. x 86 Privileged Instructions • MOV CR 3: Set address space (page table) • IN, OUT: Read or write to hardware like disk, network, . . . • CLI, STI: Enable or disable hardware interrupts CSC 482/582: Computer Security

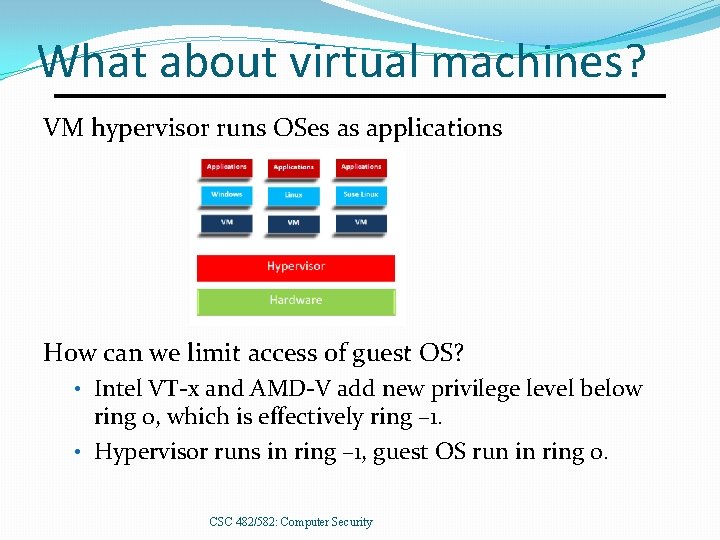
What about virtual machines? VM hypervisor runs OSes as applications How can we limit access of guest OS? • Intel VT-x and AMD-V add new privilege level below ring 0, which is effectively ring – 1. • Hypervisor runs in ring – 1, guest OS run in ring 0. CSC 482/582: Computer Security

C Activity on the VM Complete the "Compiling a C Program on the VM" inclass assignment listed under the Assignments on Canvas. CSC 482/582: Computer Security

Why is Access Control hard? Complex Objects • Identifying objects of interest. • Is your choice of objects too coarse or fine-grained? • Hierarchical structure like filesystem or XML Subjects are Complex • Identifying subjects of interest. • What are the relationships between subjects? Access Control states change. Security objectives often unclear. CSC 482/582: Computer Security

Key Points 1. Center of gravity of security; pervasive. 2. Access Control Matrix simplest abstraction mechanism for representing protection state. 3. ACM is too big, so real systems use either: 1. ACLs: columns (objects) of ACM. 2. Capabilities: rows (subjects) of ACM. 4. Access Control in Practice: Unix 5. Access control rests on hardware foundation. Virtual memory, rings, privileged instructions. CSC 482/582: Computer Security

References Anderson, Ross, Security Engineering, 2 nd edition, Wiley, 2008. 2. Bishop, Matt, Introduction to Computer Security, Addison-Wesley, 2005. 3. Bovet, Daniel and Cesati, Marco, Understanding the Linux Kernel, 2 nd edition, O’Reilly, 2003. 4. Silberschatz, et. al. , Database System Concepts, 4 th edition, Mc. Graw-Hill, 2002. 5. Silberschatz, et. al. , Operating System Concepts, 7 th edition, Wiley, 2005. 6. Viega, John, and Mc. Graw, Gary, Building Secure Software, Addison-Wesley, 2002. 1. CSC 482/582: Computer Security