CS 591 Introduction to Computer Security Lecture 3

















































- Slides: 59

CS 591: Introduction to Computer Security Lecture 3: Voting Machine Study Access Control James Hook 6/4/2021 9: 00 PM

Discussion • Feldman, Halderman, and Felten, Security Analysis of the Diebold Accu. Vote-TS Voting Machine, September 2006 – Reaction to the paper? 6/4/2021 9: 00 PM

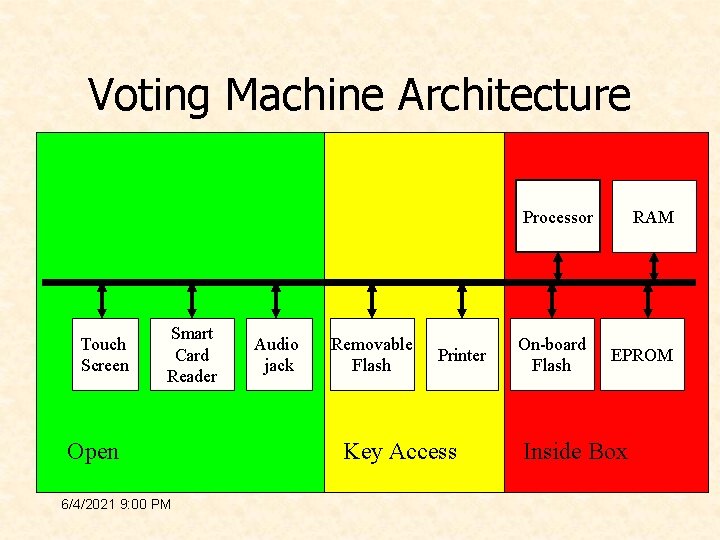
Group Tasks 1. Sketch the architecture – Identify physical security domains – Identify critical logical and/or physical components 2. 3. 4. 5. How How 6/4/2021 9: 00 PM is it supposed to work? does FHF malware steal votes? did FHF insert the malware? did the malware propagate?

Discussion Questions • Is the analysis credible? • Is the threat model credible? • Is this representative of commercial systems today? • Did Diebold follow best practices? • Are the FHF results reproducible? • Did Felton’s lab follow a sound methodology in analyzing the machine? 6/4/2021 9: 00 PM

Discussion Questions • Having read the analysis of the Diebold machine, are you surprised that Sequoia used a threat of law suit to prevent Felten’s lab from analyzing their machine? • Having seen this analysis of a fielded commercial system, are you more or less concerned about the discrepencies observed in Union County elections? 6/4/2021 9: 00 PM

Access Control Model 6/4/2021 9: 00 PM

Basic Concepts of AC • What are three basic concepts of Access Control? 6/4/2021 9: 00 PM

Access Control in Case Study • Individuals and Roles • Actions • Logical and Physical Entities • How can these be mapped onto subjects, objects, and rights? 6/4/2021 9: 00 PM

Articulating Policy • How do we articulate a security policy? • How do we provide mechanisms to enforce policy? 6/4/2021 9: 00 PM

Ad hoc policies • Discus – Only voters should vote – Only poll workers should start and start elections 6/4/2021 9: 00 PM

Access Control Matrix Model – Lampson ‘ 71, refined by Graham and Denning (‘ 71, ‘ 72) – Concepts – Objects, the protected entities, O – Subjects, the active entities acting on the objects, S – Rights, the controlled operations subjects can perform on objects, R – Access Control Matrix, A, maps Objects and Subjects to sets of Rights – State: (S, O, A) 6/4/2021 9: 00 PM

Voting: Subjects, Objects, Rights • Subjects: (Roles) – Voter, Poll worker, … • Rights: (Actions) – Vote, define ballot, start and stop election, … • Objects: (Logical and physical entities) – Ballot, stored tally, final tally, voting machine, removable flash, on-board flash, … • Question: Is every voter a subject? Or is the role of voter a subject? One-person-one-vote? 6/4/2021 9: 00 PM

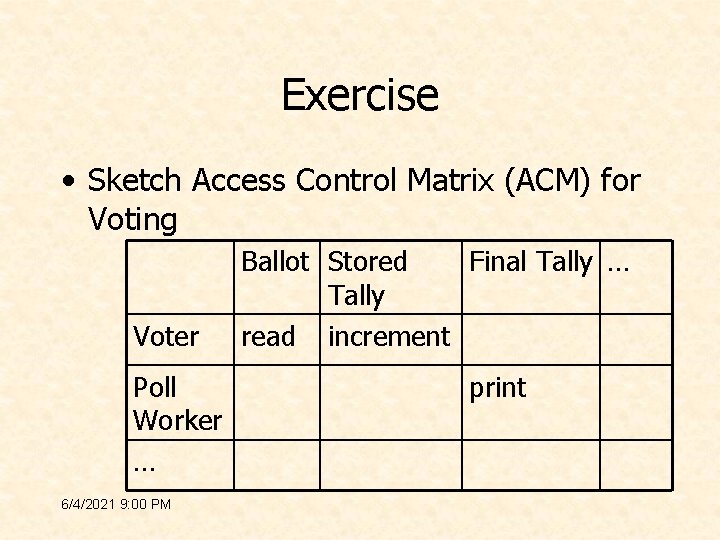
Exercise • Sketch Access Control Matrix (ACM) for Voting Voter Poll Worker … 6/4/2021 9: 00 PM Ballot Stored Final Tally … Tally read increment print

Questions • What about modes? – Once the election starts the ballot should not change – Voters should only vote when the election is happening 6/4/2021 9: 00 PM

Questions • Levels of abstraction – Some objects are physical, some are logical – When considering the programming model you now have processes and files (and possibly modes of operation) • Exercise: – Sketch ACMs with processes as subjects and files as objects for voting and postelection modes 6/4/2021 9: 00 PM

Exercise • Compare the ACMs for files and processes with the original ACM • Is every operation specified in the original feasible in the refined ACMs? • Is every feasible operation in the refined ACMs allowed in the original? 6/4/2021 9: 00 PM

Mechanisms • Policy specifies abstract goals • Mechanisms are concrete devices, algorithms, or processes that assist in implementing a policy • For example, passwords are a mechanism that can support an authentication policy – Mechanisms are not always perfect! 6/4/2021 9: 00 PM

Mechanisms • • Hardware? Operating System? Middleware? Application level? 6/4/2021 9: 00 PM

Access Control Mechanisms • Most operating systems provide some mechanisms for supporting access control • Typically: – Processes are associated with users (or user identification numbers), which are the subjects – Files are objects – Rights are: read, write, append, execute, search, . . . 6/4/2021 9: 00 PM

Applying the Mechanism • Can a file-system level Access Control mechanism help make the Voting machine more trustworthy? • What about modes? – Mode is not part of typical AC mechanisms – However rights can be changed • A typical right is “own” which in discretionary access control generally allows the subject to change rights – Analysis of systems that actively change rights is potentially difficult 6/4/2021 9: 00 PM

Limitations on Mechanisms • Simple mechanisms are preferred • All computational mechanisms must be decidable • In general, useful mechanisms must be computationally cheap 6/4/2021 9: 00 PM

Access Control • Is Access Control biased to – Confidentiality – Integrity – Availability • Exercise – Develop scenarios in which a confidentiality (integrity, availability) property is expressed using an access control matrix 6/4/2021 9: 00 PM

Model vs. Mechanism • Earlier I presented the model of the AC Matrix • Does UNIX implement the full AC Matrix? – What key simplifications does UNIX adopt? – Why? • Is the full ACM mechanism a good idea? – Is it a good model? 6/4/2021 9: 00 PM

Code Insertion • Anderson identifies code insertion attacks as access control failures. – What are they? – Why does he put consider this an Access Control problem? 6/4/2021 9: 00 PM

A Good Model • ACM is a good model because any mechanism of compatible granularity can be described in terms of how it approximates the ACM model 6/4/2021 9: 00 PM

Next Lecture: • Anderson Chapter 8 (first edition Chapter 7) • Bishop Chapter 5 6/4/2021 9: 00 PM

Access Control Policies • Discretionary Access Control (DAC) – An individual user can set allow or deny access to an object • Mandatory Access Control (MAC) – System mechanism controls access – User cannot alter that access • Originator Controlled Access Control (ORCON) – Access control set by creator of information – Owner (if different) can’t alter AC • Like copyright 6/4/2021 9: 00 PM

Background • Clearance levels – Top Secret • In-depth background check; highly trusted individual – Secret • Routine background check; trusted individual – For Official Use Only/Sensitive • No background check, but limited distribution; minimally trusted individuals • May be exempt from disclosure – Unclassified • Unlimited distribution • Untrusted individuals 6/4/2021 9: 00 PM

Background • Clearance levels are only half the story – They give a level of trust of the subject • The “need to know” policy provides an orthogonal structure called compartmentalization • A category (or compartment) is a designation related to the “need to know” policy • Examples: – NUC: Nuclear – EUR: Europe – ASI: Asia 6/4/2021 9: 00 PM

Categories and Coalitions • Categories can be critical in complex coalitions • The US may have two allies that do not wish to share information (perhaps Israel and Saudi Arabia) • Policy must support: – Top Secret, Israel – Top Secret, Saudi Arabia – Top Secret, Israel and Saudi Arabia • (probably very few people in this set) 6/4/2021 9: 00 PM

Classification Systems • Both notions of classification induce a partial order – TS is more trusted that S – You can only see information if you are cleared to access all categories that label it • Mathematicians Bell and La. Padula picked a lattice structure as a natural model for security levels 6/4/2021 9: 00 PM

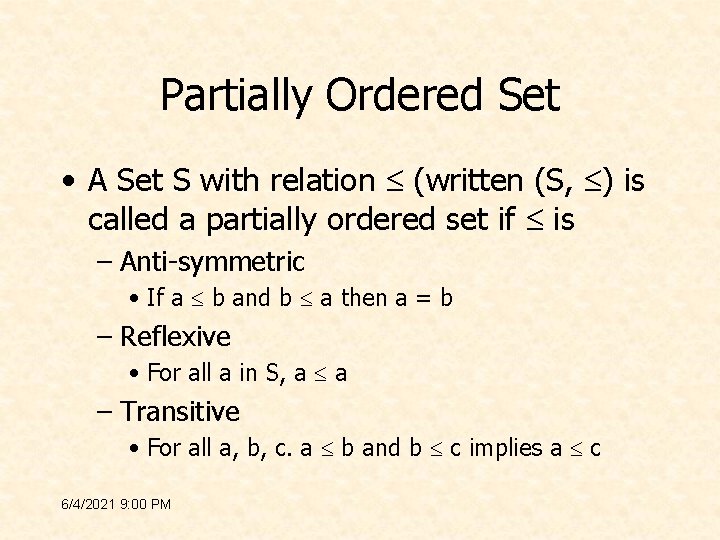
Partially Ordered Set • A Set S with relation (written (S, ) is called a partially ordered set if is – Anti-symmetric • If a b and b a then a = b – Reflexive • For all a in S, a a – Transitive • For all a, b, c. a b and b c implies a c 6/4/2021 9: 00 PM

Poset examples • Natural numbers with less than (total order) • Sets under the subset relation (not a total order) • Natural numbers ordered by divisibility 6/4/2021 9: 00 PM

Lattice • Partially ordered set (S, ) and two operations: – greatest lower bound (glb X) • Greatest element less than all elements of set X – least upper bound (lub X) • Least element greater than all elements of set X • Every lattice has – bottom (glb L) a least element – top (lub L) a greatest element 6/4/2021 9: 00 PM

Lattice examples • Natural numbers in an interval (0. . n) with less than – Also the linear order of clearances (U FOUO S TS) • The powerset of a set of generators under inclusion – E. g. Powerset of security categories {NUC, Crypto, ASI, EUR} • The divisors of a natural number under divisibility 6/4/2021 9: 00 PM

New lattices from old • The opposite of a lattice is a lattice • The product of two lattices is a lattice • The lattice of security classifications used by Bishop is the product of the lattice of clearances and the lattice of sets generated from the categories (compartments) 6/4/2021 9: 00 PM

Mandatory Access Control • In a MAC system all documents are assigned labels by a set of rules • Documents can only be relabeled under defined special circumstances • Violations of the policy are considered very serious offenses (criminal or treasonous acts) 6/4/2021 9: 00 PM

Bell La. Padula Context • Pre “MLS” policy was not to mix data of different classifications on a single system • Still a good idea if it meets your needs • “on-line multi-level secure operation” as a goal of computer security in early 1970 s 6/4/2021 9: 00 PM

From Paper to Computers • How to apply MAC to computers? • Documents are analogous to objects in Lampson’s Access Control model – Every object can be labeled with a classification • Cleared personnel are analogous to subjects – Every subject can be labeled with a clearance • What about processes? 6/4/2021 9: 00 PM

Note on subject labels • A person is generally cleared “up to” a level • Cross level communication requires that a person be able to interact below their level of clearance • Subjects are given two labels: – The maximum level – The current level • Current never exceeds maximum • We will focus on static labelings – A subject will not dynamically change their current level 6/4/2021 9: 00 PM

Bell La. Padula • Task was to propose a theory of multilevel security – supported by a mechanism implemented in an Anderson-style reference monitor – prevents unwanted information flow 6/4/2021 9: 00 PM

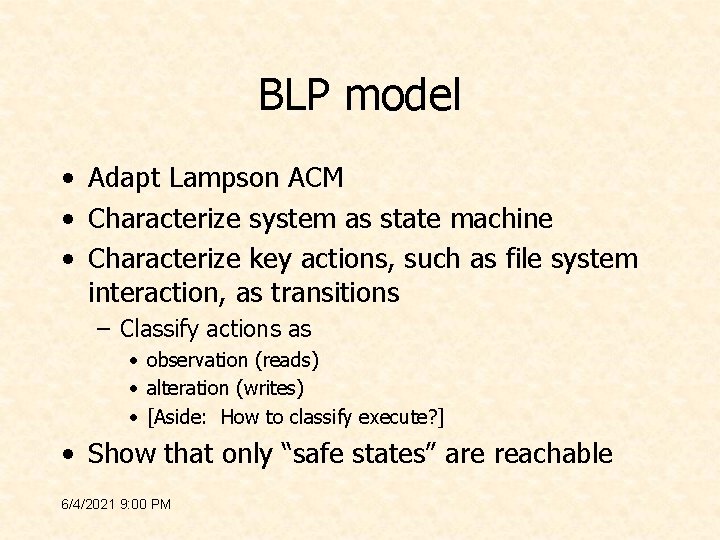
BLP model • Adapt Lampson ACM • Characterize system as state machine • Characterize key actions, such as file system interaction, as transitions – Classify actions as • observation (reads) • alteration (writes) • [Aside: How to classify execute? ] • Show that only “safe states” are reachable 6/4/2021 9: 00 PM

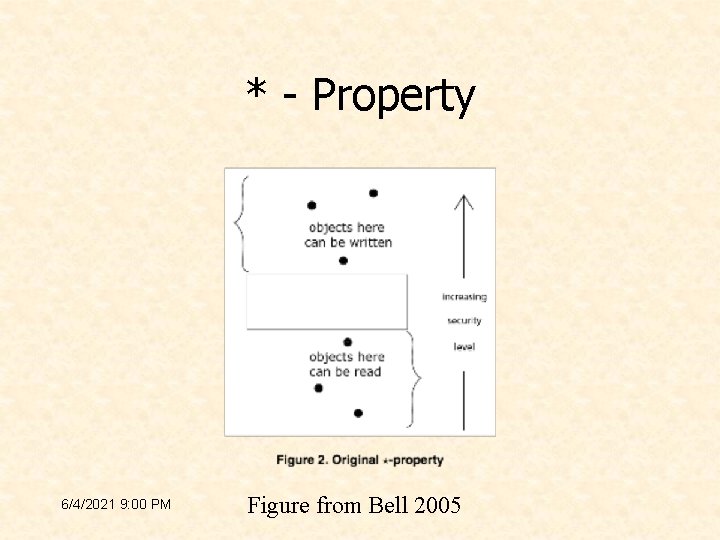
Simple Security • The simple security property – The current level of a subject dominates the level of every object that it observes • This property strongly analogous to paper systems • It is referred to by the slogan “no read up” 6/4/2021 9: 00 PM

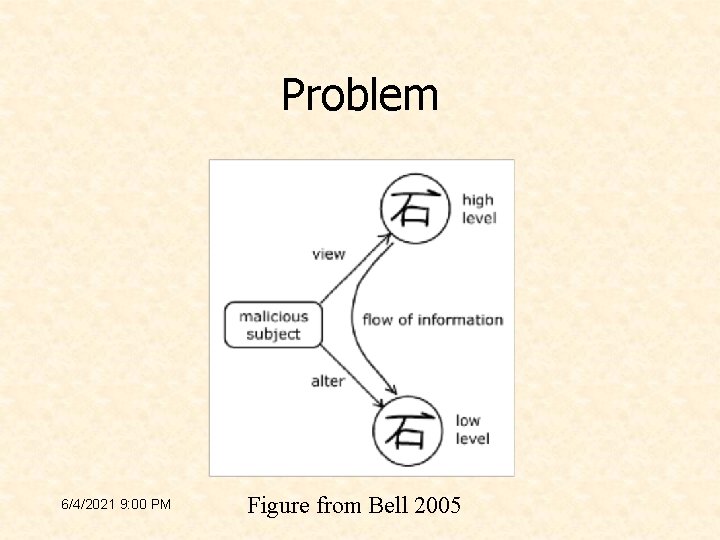
Problem 6/4/2021 9: 00 PM Figure from Bell 2005

Problem • Simple Security does not account for alterations (writes) • Another property is needed to characterize alterations 6/4/2021 9: 00 PM

* - Property 6/4/2021 9: 00 PM Figure from Bell 2005

*- Property • In any state, if a subject has simultaneous “observe” access to object -1 and “alter” access to object-2, then level (object-1) is dominated by level (object-2). – From BLP 1976, Unified Exposition • Slogan: “No write down” 6/4/2021 9: 00 PM

Discretionary • In addition to the MAC mechanisms of the simple security and *-properties, the BLP model also has a discretionary component – All accesses must be allowed by both the MAC and discretionary rules 6/4/2021 9: 00 PM

BLP Basic Security Theorem • If all transitions (consdiered individually) satisfy – simple security property – * - property – discretionary security property • Then system security is preserved inductively (that is, all states reached from a “secure” state are “secure”) 6/4/2021 9: 00 PM

Next Lecture • Discussion – Tibet • NY Times article http: //www. nytimes. com/2009/03/29/technolog y/29 spy. html? emc=eta 1 • Nagaraja and Anderson tech report http: //www. cl. cam. ac. uk/techreports/UCAM-CLTR-746. html 6/4/2021 9: 00 PM

Backup Slides 6/4/2021 9: 00 PM

Case Study • We will use the FHF paper as a case study • As we encounter concepts we will attempt to instantiate them in the context of the voting machine domain 6/4/2021 9: 00 PM

Voting Machine Architecture Processor Touch Screen Smart Card Reader Open 6/4/2021 9: 00 PM Audio jack Removable Flash Printer Key Access On-board Flash RAM EPROM Inside Box

Boot Process • Boot device specified by hardware jumpers (inside box) – EPROM – on-board flash (default) – ext flash • On Boot: – Copy bootloader into RAM; init hardware – Scan Removable flash for special files • “fboot. nb 0” => replace bootloader in on-board flash • “nk. bin” => replace OS in on-board flash • “Erase. FFX. bsq” => erase file system on on-board flash – If no special files uncompress OS image – Jump to entry point of OS 6/4/2021 9: 00 PM

Boot (continued) • On OS start up: – run Filesys. exe • unpacks registry • runs programs in HKEY_LOCAL_MACHINEInit – – shell. exe (debug shell) device. exe (Device manager) gwes. exe (graphics and event) taskman. exe (Task Manager) – Device. exe mounts file systems • (root): RAM only • FFX: mount point for on-board flash • Storage Card: mount point for removable flash 6/4/2021 9: 00 PM

Boot (continued) • Customized taskman. exe – Check removable flash • explorer. glb => launch windows explorer • *. ins => run proprietary scripts – (script language has buffer overflow vulnerabilities) – used to configure election data • default => launch “Ballot. Station” – FFXBinBallot. Station. exe 6/4/2021 9: 00 PM

Ballot. Station • Four modes: pre-download, preelection testing, election, post-election • Mode recorded in election results file – Storage CardCurrent. Electionelection. brs 6/4/2021 9: 00 PM

Stealing Votes • Malicious processes runs in parallel with Ballot. Station • Polls election results file every 15 seconds – If election mode and new results – temporarily suspend Ballot Station – steal votes – resume Ballot Station 6/4/2021 9: 00 PM

Viral propagation • Malicious bootloader – Infects host by replacing existing bootloader in on-board flash – subsequent bootloader updates print appropriate messages but do nothing • fboot. nb 0 – package contains malicious boot loader – and vote stealing software 6/4/2021 9: 00 PM