Cryptography Lecture 2 Arpita Patra Arpita Patra Recall











- Slides: 26

Cryptography Lecture 2 Arpita Patra © Arpita Patra

Recall >> Crypto: Past and Present (aka Classical vs. Modern Cryto) o Scope o Scientific Basis (Formal Def. + Precise Assumption + Rigorous Proof) o End-users >> Secure Communication in Secret Key Setting Secret Key Encryption (SKE) >> Learn From the Blunders of Classical SKE o Algorithms of SKE (in general in crypto) must be PUBLIC o Secret Key Space Must be large enough to fail brute force o No ad-hoc algorithm without definition and proof

Today’s Goal - Do Secure Communication in a ‘modern’ way ditching the ‘classic’ approach o Formulate a formal definition (threat + break model) o Identify assumptions needed and build a construction o Prove security of the construction relative to the definition and assumption

Secure Communication in Private Key Setting m m Encryption c Decryption m ? ? k o Secret key k shared in advance (by “some” mechanism) o m is the plain-text o c is the cipher-text (scrambled message) Need: An encryption scheme (Gen, Enc, Dec) - Private (Secret) Key Encryption- Keys are private to the sender and the receiver - Symmetric Key Encryption- The same key is used for encryption and decryption k

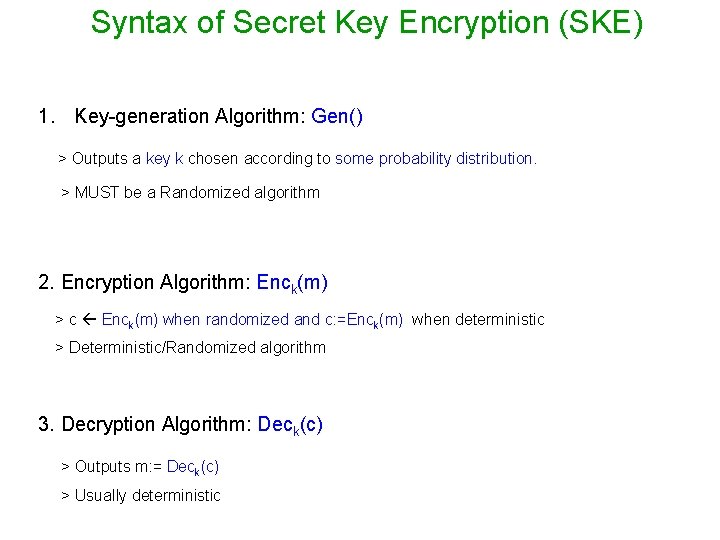
Syntax of Secret Key Encryption (SKE) 1. Key-generation Algorithm: Gen() > Outputs a key k chosen according to some probability distribution. > MUST be a Randomized algorithm 2. Encryption Algorithm: Enck(m) > c Enck(m) when randomized and c: =Enck(m) when deterministic > Deterministic/Randomized algorithm 3. Decryption Algorithm: Deck(c) > Outputs m: = Deck(c) > Usually deterministic

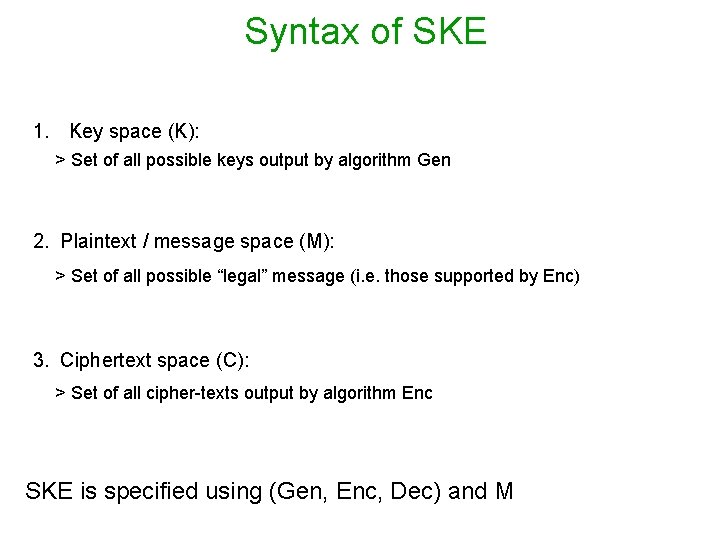
Syntax of SKE 1. Key space (K): > Set of all possible keys output by algorithm Gen 2. Plaintext / message space (M): > Set of all possible “legal” message (i. e. those supported by Enc) 3. Ciphertext space (C): > Set of all cipher-texts output by algorithm Enc SKE is specified using (Gen, Enc, Dec) and M

Formal Definition of Security Two components of a security definition: Threat: >> Who is your threat? >> Who do you want to protect from? >> Cultivate your enemy a. k. a adversary in crypto language. >> Look out in practical scenarios / be an adversary >> Unless you know your adv, no hope of defeating him Break: >> What are you afraid of losing? >> What do you want to protect? >> If you don’t know what to protect then how to do you when or if you are protecting it?

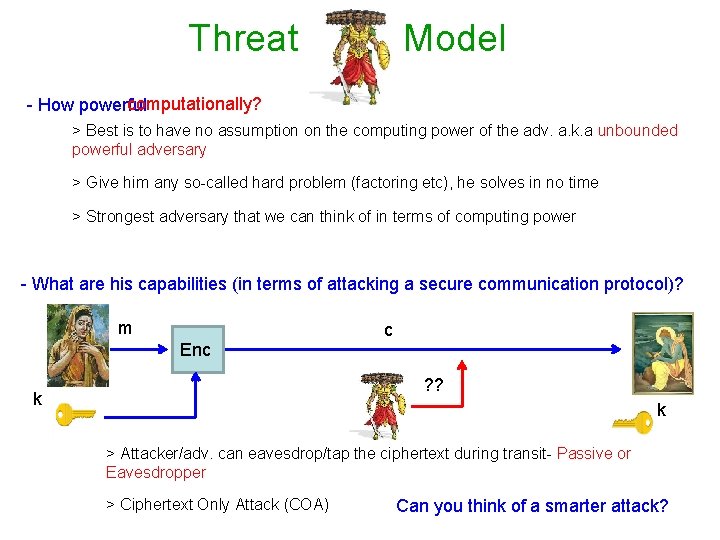
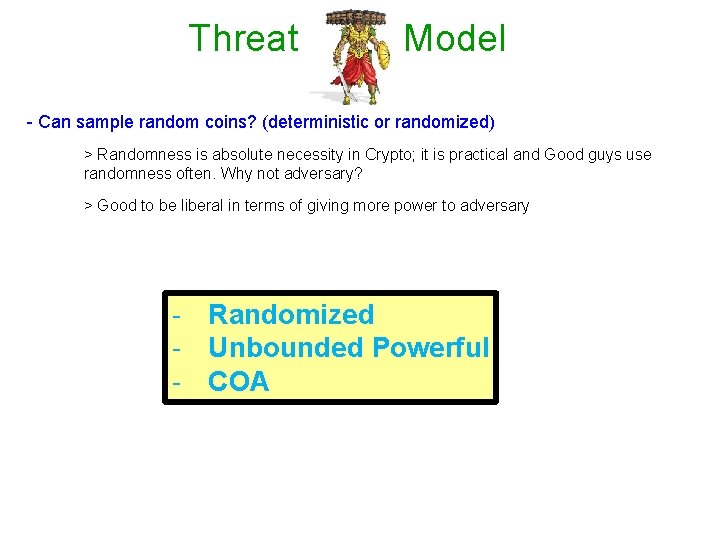
Threat Model computationally? - How powerful > Best is to have no assumption on the computing power of the adv. a. k. a unbounded powerful adversary > Give him any so-called hard problem (factoring etc), he solves in no time > Strongest adversary that we can think of in terms of computing power - What are his capabilities (in terms of attacking a secure communication protocol)? m Enc c ? ? k k > Attacker/adv. can eavesdrop/tap the ciphertext during transit- Passive or Eavesdropper > Ciphertext Only Attack (COA) Can you think of a smarter attack?

Threat Model - Can sample random coins? (deterministic or randomized) > Randomness is absolute necessity in Crypto; it is practical and Good guys use randomness often. Why not adversary? > Good to be liberal in terms of giving more power to adversary - Randomized - Unbounded Powerful - COA

Break Model Attempt I>> Secret key ? Then Enc(m) = m is secure Attempt II>> Entire Message? Then Enc(m) leaking most significant 10 bits is secure; m: bank password| amazon password| Attempt III>> No additional info about the message irrespective of prior information? Right Notion How to formalise? Need basics of Discrete Probability Theory

Discrete Probability Background > U: Finite set; e. g. {0, 1} > Probability Distribution on U specifies the probabilities of the occurrence of the elements of U - e. g Probability Distribution on U = {0, 1}: Pr(0) = ½ , Pr(1) = ½ Pr(0) = 0 , Pr(1) = 1 Probability distribution: Probability distribution Pr over U is a function Pr: U �[0, 1] such that Σ Pr(x) = 1 x in U > Uniform Probability Distribution on U: Pr(x) = 1/|U| for every x

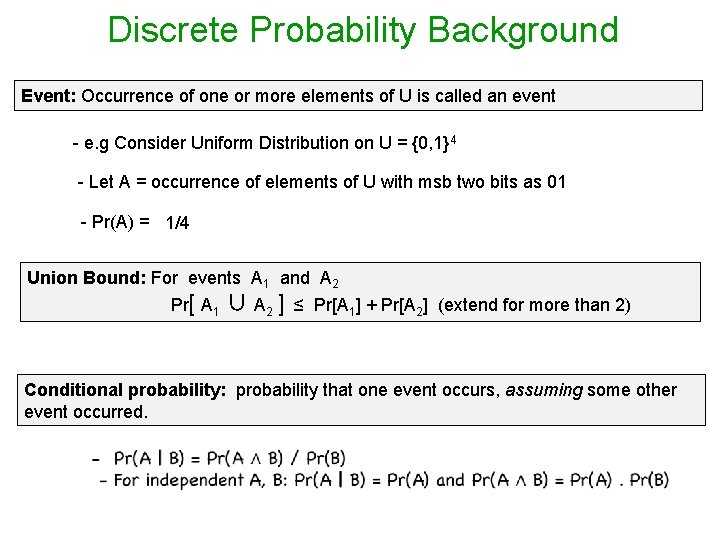
Discrete Probability Background Event: Occurrence of one or more elements of U is called an event - e. g Consider Uniform Distribution on U = {0, 1}4 - Let A = occurrence of elements of U with msb two bits as 01 - Pr(A) = 1/4 Union Bound: For events A 1 and A 2 Pr[ A 1 ∪ A 2 ] ≤ Pr[A 1] + Pr[A 2] (extend for more than 2) Conditional probability: probability that one event occurs, assuming some other event occurred.

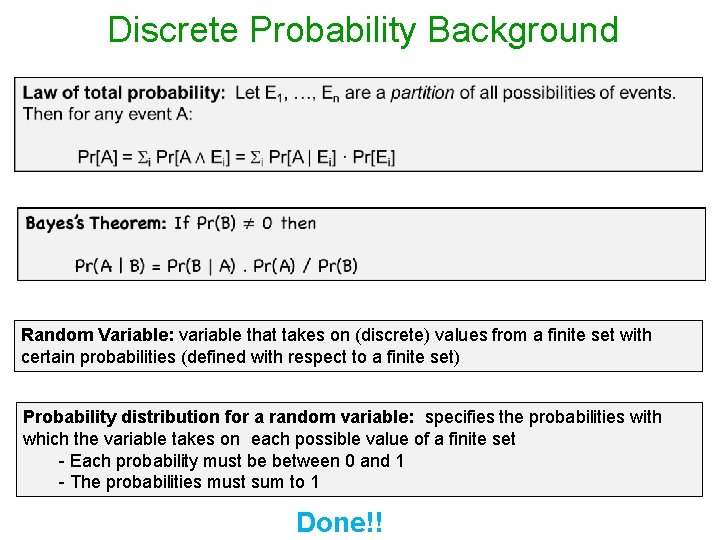
Discrete Probability Background Random Variable: variable that takes on (discrete) values from a finite set with certain probabilities (defined with respect to a finite set) Probability distribution for a random variable: specifies the probabilities with which the variable takes on each possible value of a finite set - Each probability must be between 0 and 1 - The probabilities must sum to 1 Done!!

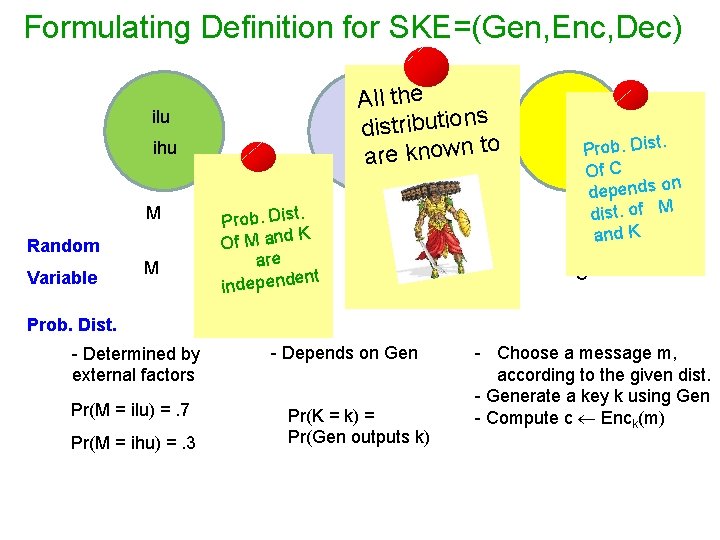
Formulating Definition for SKE=(Gen, Enc, Dec) All the s distribution o t n w o n k e ar ilu ihu M Random Variable M . Prob. Dist K Of M and are nt independe K K . Prob. Dist Of C n depends o M C dist. of and K C Prob. Dist. - Determined by external factors Pr(M = ilu) =. 7 Pr(M = ihu) =. 3 - Depends on Gen Pr(K = k) = Pr(Gen outputs k) - Choose a message m, according to the given dist. - Generate a key k using Gen - Compute c Enck(m)

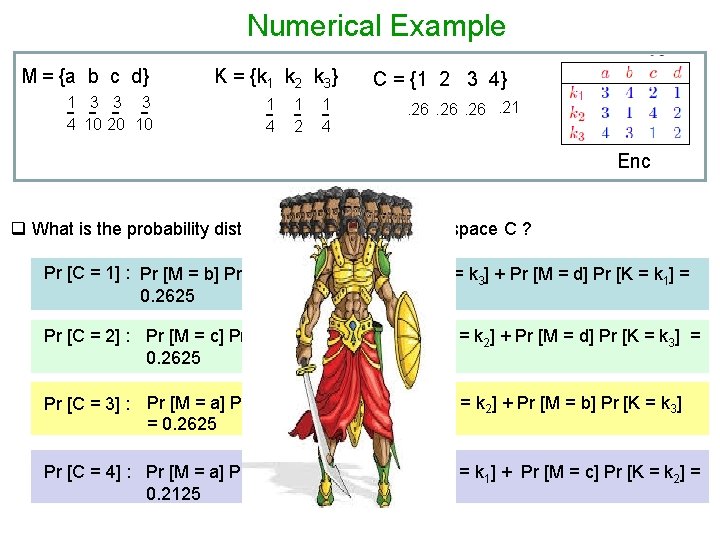
Numerical Example M = {a b c d} 1 3 3 3 -4 10 - 20 - 10 - K = {k 1 k 2 k 3} 1 -4 1 -2 1 -4 C = {1 2 3 4}. 26. 26. 21 Enc q What is the probability distribution on the cipher-text space C ? Pr [C = 1] : Pr [M = b] Pr [K = k 2] + Pr [M = c] Pr [K = k 3] + Pr [M = d] Pr [K = k 1] = 0. 2625 Pr [C = 2] : Pr [M = c] Pr [K = k 1] + Pr [M = d] Pr [K = k 2] + Pr [M = d] Pr [K = k 3] = 0. 2625 Pr [C = 3] : Pr [M = a] Pr [K = k 1] + Pr [M = a] Pr [K = k 2] + Pr [M = b] Pr [K = k 3] = 0. 2625 Pr [C = 4] : Pr [M = a] Pr [K = k 3] + Pr [M = b] Pr [K = k 1] + Pr [M = c] Pr [K = k 2] = 0. 2125

Threat & Break Model What is the point in tapping over channel. I better watch the cricket match today - Randomized Unbounded Powerful COA q No additional info about the message should be leaked from the ciphertext irrespective of the prior information that the adv has What captures the prior information of the attacker about m ? erfe. Mct - Probability distribution on the plain-text P space ! - The probability distribution {Pr[M = m]}Security!!! q Observing the cipher-text c should not change the attacker’s knowledge about the distribution of the plaintext - Mathematically, Pr[M = m | C = c] = Pr[M = m]

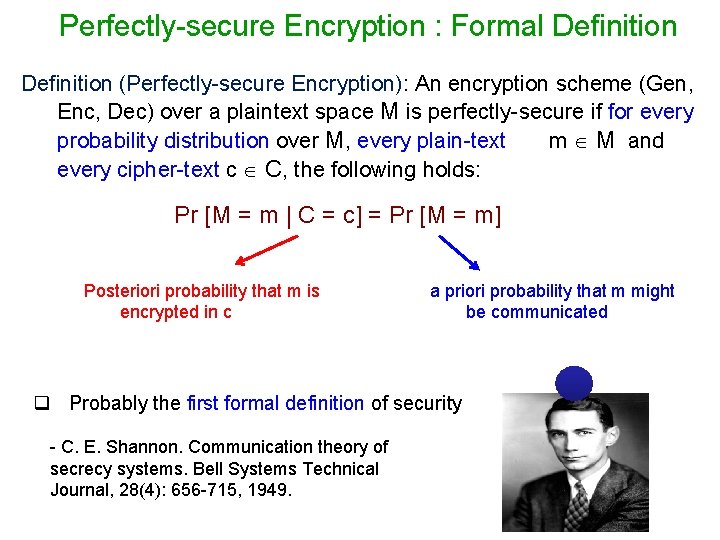
Perfectly-secure Encryption : Formal Definition (Perfectly-secure Encryption): An encryption scheme (Gen, Enc, Dec) over a plaintext space M is perfectly-secure if for every probability distribution over M, every plain-text m M and every cipher-text c C, the following holds: Pr [M = m | C = c] = Pr [M = m] Posteriori probability that m is encrypted in c a priori probability that m might be communicated q Probably the first formal definition of security - C. E. Shannon. Communication theory of secrecy systems. Bell Systems Technical Journal, 28(4): 656 -715, 1949.

What have we done so far. . o Formulate a formal definition (threat + break model) o Identify assumptions needed and build a construction o Prove security of the construction relative to the definition and assumption No assumption!!

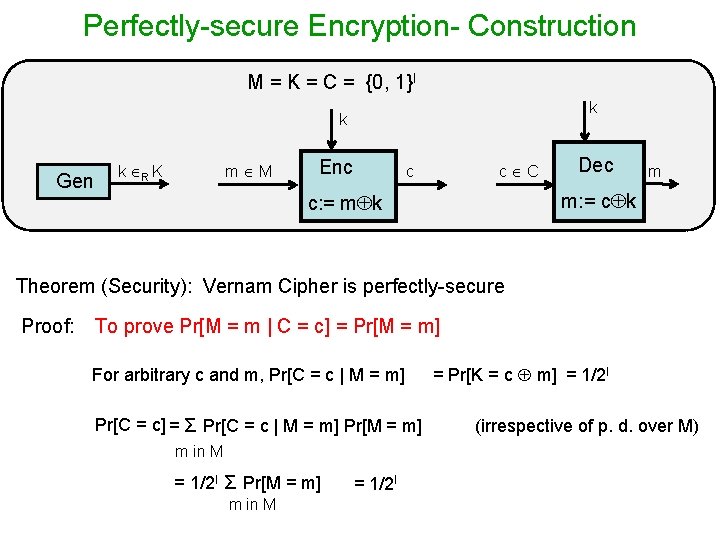
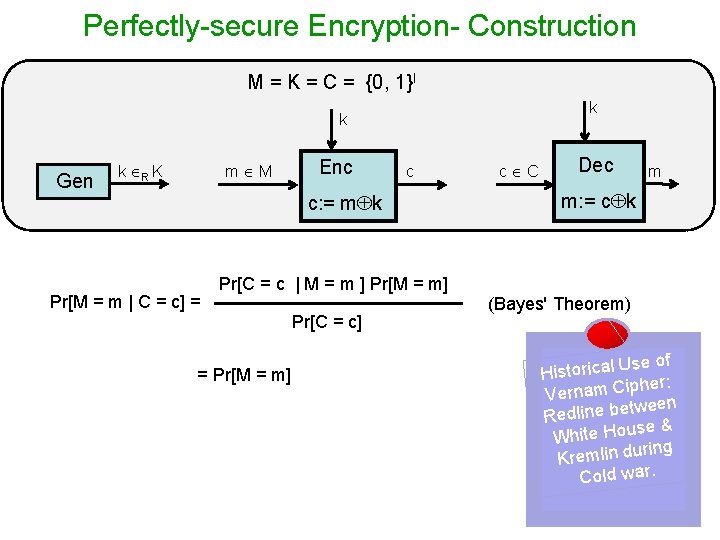
Perfectly-secure Encryption- Construction M = K = C = {0, 1}l k k Gen k R K m M Enc c c C m: = c k c: = m k Correctness: Deck( Enck(m) ) Dec =m her Vernam Cip [1917]: But roved Shannon p after its security erfect p g in t la u form security m

Perfectly-secure Encryption- Construction M = K = C = {0, 1}l k k Gen k R K m M Enc c C c Dec m m: = c k c: = m k Theorem (Security): Vernam Cipher is perfectly-secure Proof: To prove Pr[M = m | C = c] = Pr[M = m] For arbitrary c and m, Pr[C = c | M = m] Pr[C = c] = Σ Pr[C = c | M = m] Pr[M = m] m in M = 1/2 l Σ Pr[M = m] m in M = 1/2 l = Pr[K = c m] = 1/2 l (irrespective of p. d. over M)

Perfectly-secure Encryption- Construction M = K = C = {0, 1}l k k Gen k R K m M Enc c c: = m k Pr[M = m | C = c] = Pr[C = c | M = m ] Pr[M = m] = Pr[M = m] Pr[C = c] c C Dec m m: = c k (Bayes' Theorem) se of Historical U her: ip C m a n r e V tween Redline be se & White Hou ring Kremlin du Cold war.

What have we done so far. . o Formulate a formal definition (threat + break model) o Identify assumptions needed and build a construction o Prove security of the construction relative to the definition and assumption

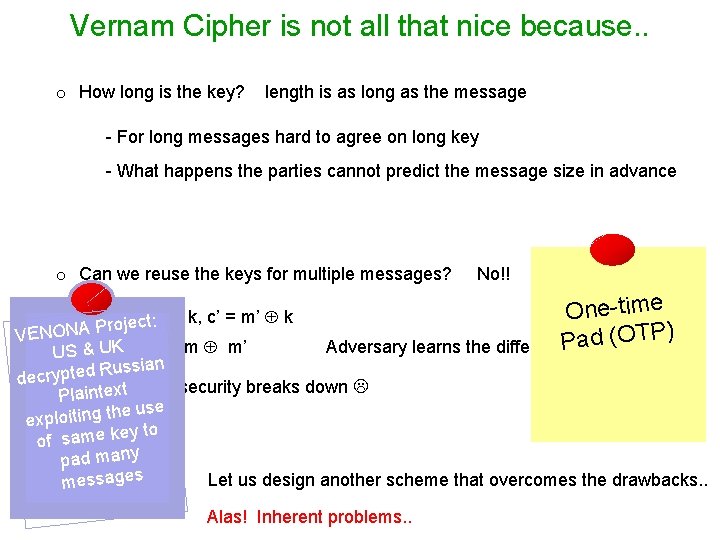
Vernam Cipher is not all that nice because. . o How long is the key? length is as long as the message - For long messages hard to agree on long key - What happens the parties cannot predict the message size in advance o Can we reuse the keys for multiple messages? No!! ime One-t -rocje=ctm k, c’ = m’ k : P) T VENONA P O ( d a P Adversary learns the difference! US & U-Kc c’ = m m’ Russian d e t p y r c e d security breaks down xt Plaint-e. Perfect he use exploiting t ey to of same k pad many Let us design another scheme that overcomes the drawbacks. . messages Alas! Inherent problems. .

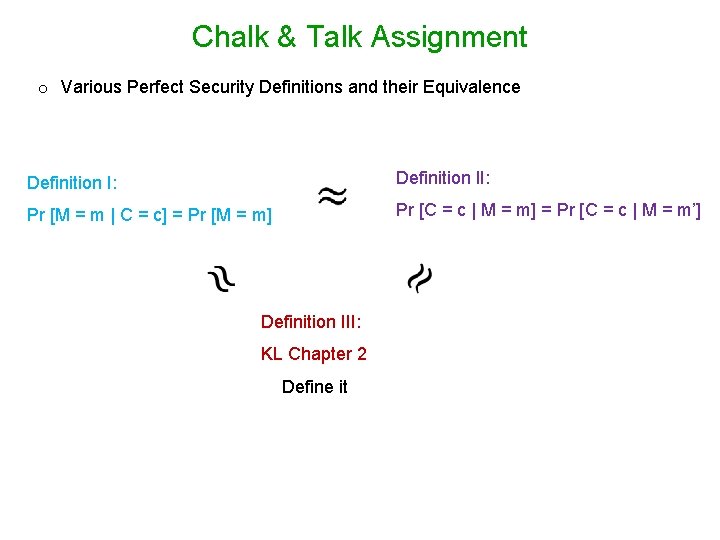
Chalk & Talk Assignment o Various Perfect Security Definitions and their Equivalence Definition I: Definition II: Pr [C = c | M = m] = Pr [C = c | M = m’] Pr [M = m | C = c] = Pr [M = m] Definition III: KL Chapter 2 Define it

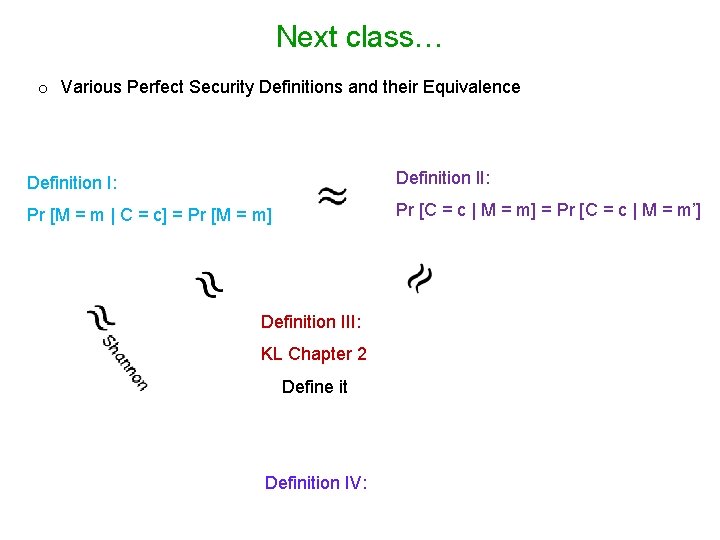
Next class… o Various Perfect Security Definitions and their Equivalence Definition I: Definition II: Pr [C = c | M = m] = Pr [C = c | M = m’] Pr [M = m | C = c] = Pr [M = m] Definition III: KL Chapter 2 Define it Definition IV:

 Arpita choudhury age
Arpita choudhury age Cipher patra
Cipher patra 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Akshaya patra donation online
Akshaya patra donation online Sudhakar patra
Sudhakar patra Mechové patro
Mechové patro Goutam patra
Goutam patra Rostlinná patra
Rostlinná patra Pragyapan patra nepal
Pragyapan patra nepal Era of quality at the akshaya patra foundation
Era of quality at the akshaya patra foundation Cipher patra
Cipher patra Cipher patra
Cipher patra Sudhakar patra
Sudhakar patra Ionic recall
Ionic recall Recall bias
Recall bias Brute recall
Brute recall Beef recall
Beef recall High precision vs high recall
High precision vs high recall Serial recall
Serial recall High precision vs high recall
High precision vs high recall Circumference of an area
Circumference of an area Recall lesson 6
Recall lesson 6 Beef recall
Beef recall Supernaturalao3
Supernaturalao3 An inspector calls recall questions
An inspector calls recall questions 24 hodinový recall
24 hodinový recall Skip pointers in information retrieval
Skip pointers in information retrieval