Cryptography Lecture 10 Arpita Patra Arpita Patra Recall








- Slides: 37

Cryptography Lecture 10 Arpita Patra © Arpita Patra

Recall >> cpa-security o PRFs o SKE from PRF o Proof of security >> Practical SKEs from PRF/PRP/SPRP (modes of operations) o ECB, CBC, OFB, CTR o Except ECB, the rest are cpa-secure o CTR is the most attractive mode RA 10: Proof of security of CTR mode RA 11: Two SKEs, one is CPA other is not, we do not know which one, construct a SKE using the above two which is cpa-secure, prove security

Today’s Goal - Chosen Chiphertext Attack (CCA)- Stronger than CPA - CCA-security - Strictly stronger than CPA-security and subsumes the later o Real life attack on CBC-mode that is proven to be CPA-secure o Attack on the PRF-based theoretical construction - Assumptions/primitives to build a cca-secure construction - Introduction to Message Authentication Code (MAC)

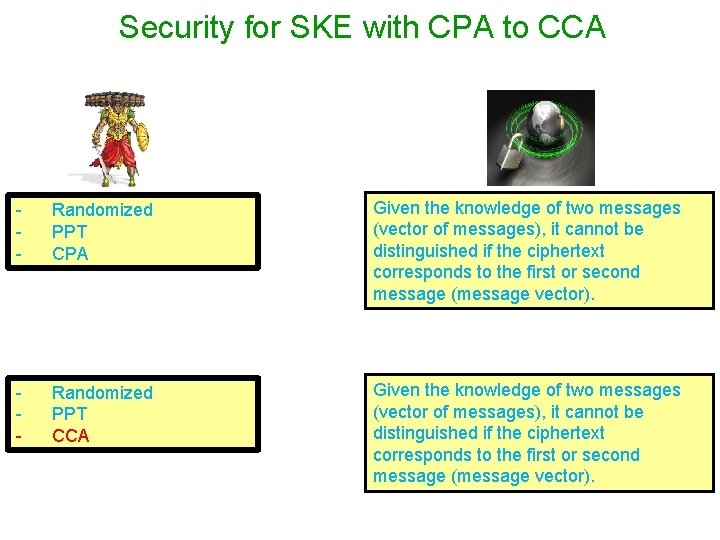
Security for SKE with CPA to CCA - Randomized PPT CPA Given the knowledge of two messages (vector of messages), it cannot be distinguished if the ciphertext corresponds to the first or second message (message vector). - Randomized PPT CCA Given the knowledge of two messages (vector of messages), it cannot be distinguished if the ciphertext corresponds to the first or second message (message vector).

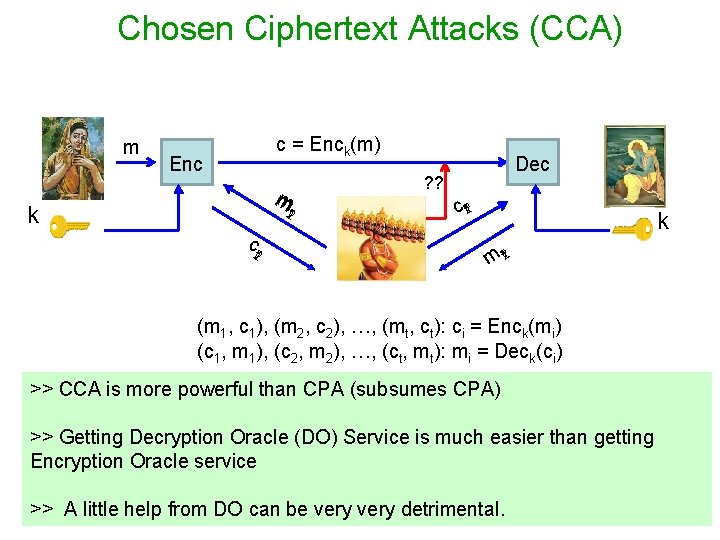
Chosen Ciphertext Attacks (CCA) m c = Enck(m) Enc m k 12 t Dec ? ? c t 21 ct 21 k m 1 t 2 (m 1, c 1), (m 2, c 2), …, (mt, ct): ci = Enck(mi) (c 1, m 1), (c 2, m 2), …, (ct, mt): mi = Deck(ci) >> CCA is more powerful than CPA (subsumes CPA) Encryption Oracle Decryption Oracle >> Adversary Getting Decryption (DO) to. Service is much easier than gettingof >> influences the. Oracle honest parties get encryption of plain-texts + decryption ciphertexts of its choice service Encryption Oracle >> Adv’s Goal: to determine the plain-text encrypted in a new cipher-text >> A little help from DO can be very detrimental.

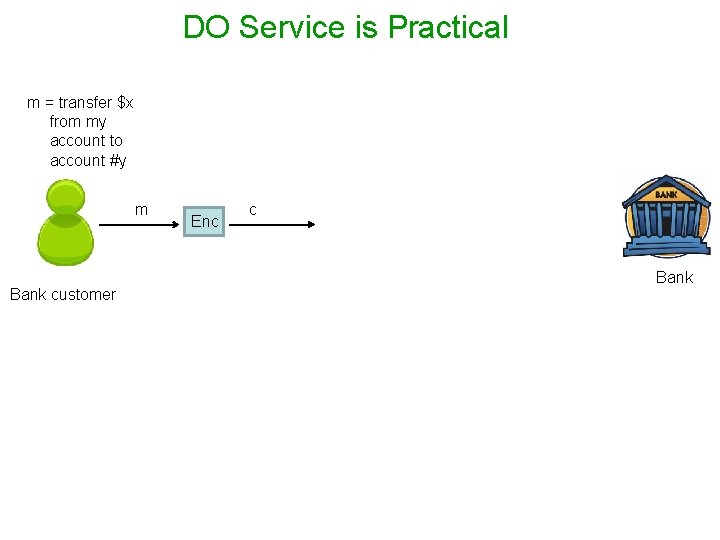
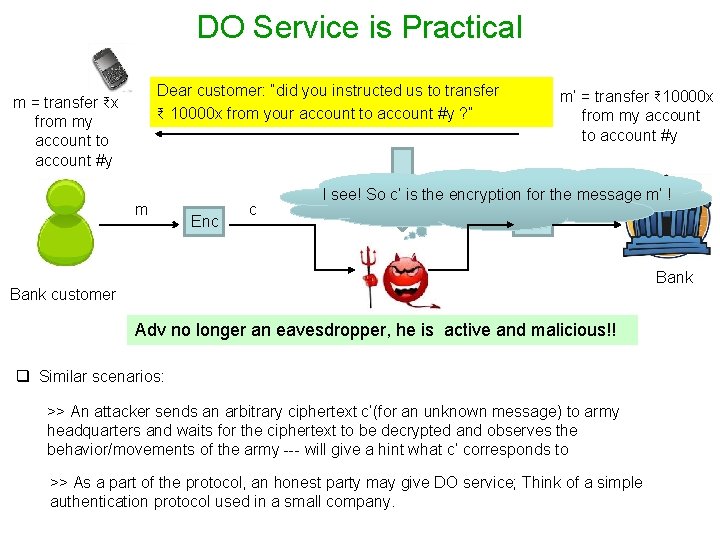
DO Service is Practical m = transfer $x from my account to account #y m Bank customer Enc c Bank

DO Service is Practical Dear customer: “did you instructed us to transfer ₹ 10000 x from your account to account #y ? ” m = transfer ₹x from my account to account #y m Enc c m’ = transfer ₹ 10000 x from my account to account #y I see! So c’ is the encryption for the message m’ ! c’ m’ Dec Bank customer Adv no longer an eavesdropper, he is active and malicious!! q Similar scenarios: >> An attacker sends an arbitrary ciphertext c’(for an unknown message) to army headquarters and waits for the ciphertext to be decrypted and observes the behavior/movements of the army --- will give a hint what c’ corresponds to >> As a part of the protocol, an honest party may give DO service; Think of a simple authentication protocol used in a small company.

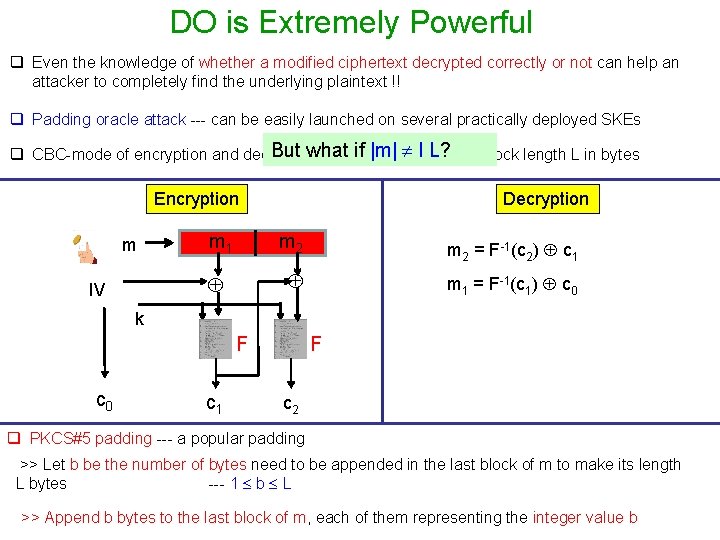
DO is Extremely Powerful q Even the knowledge of whether a modified ciphertext decrypted correctly or not can help an attacker to completely find the underlying plaintext !! q Padding oracle attack --- can be easily launched on several practically deployed SKEs But what |m|= multiple l L? of block length L in bytes q CBC-mode of encryption and decryption whenif|m| Encryption m IV Decryption m 1 m 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 k F c 0 c 1 F c 2 q PKCS#5 padding --- a popular padding >> Let b be the number of bytes need to be appended in the last block of m to make its length L bytes --- 1 b L >> Append b bytes to the last block of m, each of them representing the integer value b

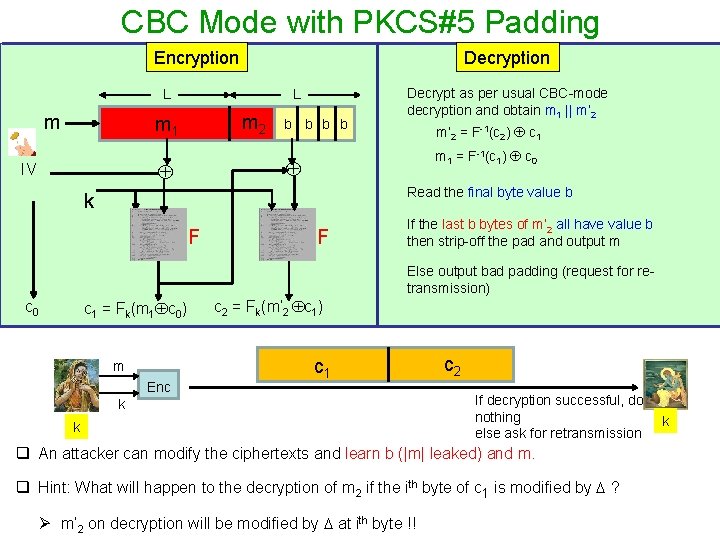
CBC Mode with PKCS#5 Padding Encryption Decryption L m 2 m 1 m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV b b Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 Read the final byte value b k F F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) m Enc c 2 = Fk(m’ 2 c 1) c 1 k k c 2 If decryption successful, do nothing else ask for retransmission q An attacker can modify the ciphertexts and learn b (|m| leaked) and m. q Hint: What will happen to the decryption of m 2 if the ith byte of c 1 is modified by ? Ø m’ 2 on decryption will be modified by at ith byte !! k

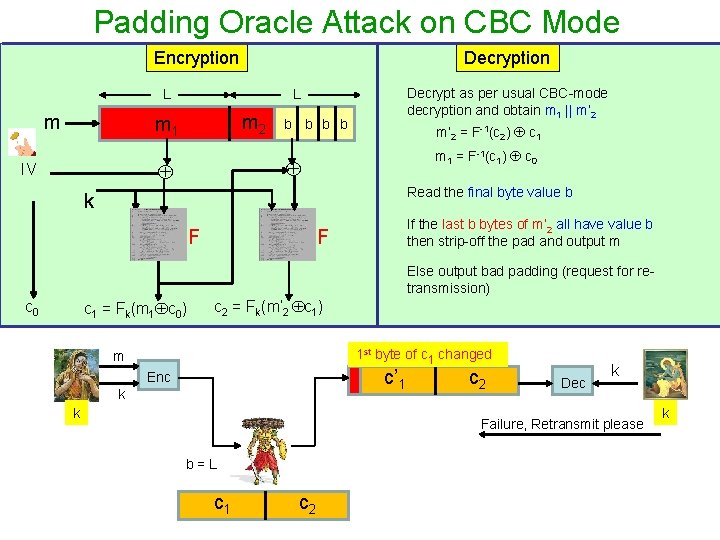
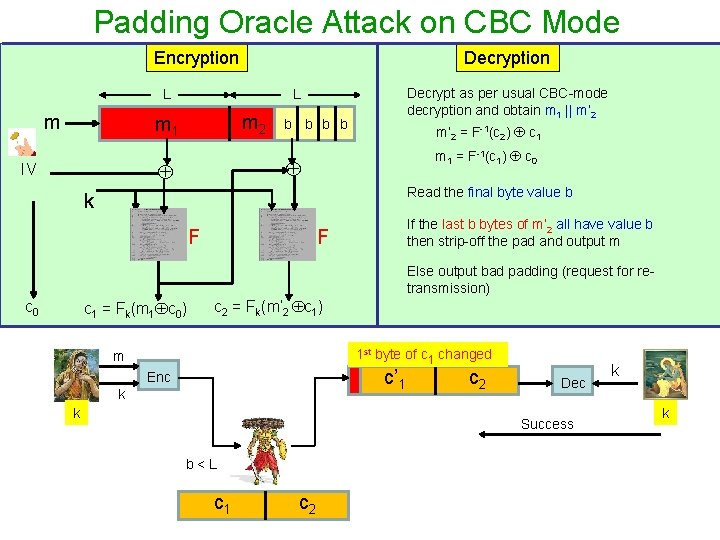
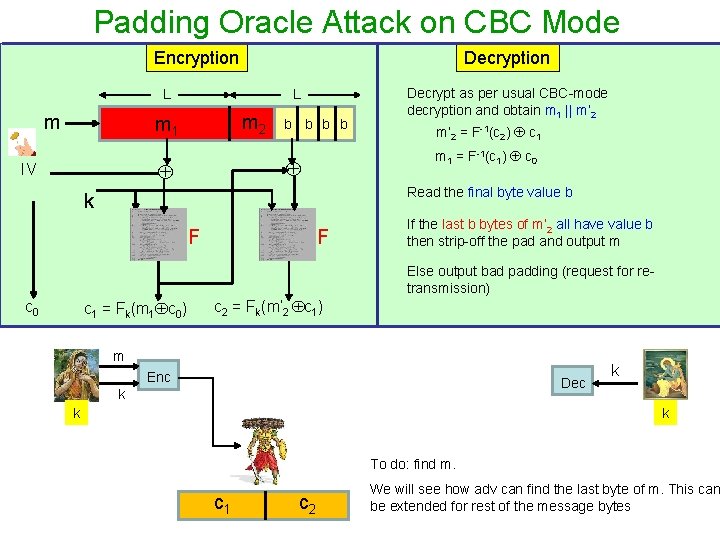
Padding Oracle Attack on CBC Mode Encryption Decryption L m m 2 m 1 b b m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 L Read the final byte value b k F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m F Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) 1 st byte of c 1 changed m c’ 1 Enc k k c 2 Dec k Failure, Retransmit please b=L c 1 c 2 k

Padding Oracle Attack on CBC Mode Encryption Decryption L m m 2 m 1 b b m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 L Read the final byte value b k F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m F Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) 1 st byte of c 1 changed m c’ 1 Enc k k c 2 Dec Success b<L c 1 c 2 k k

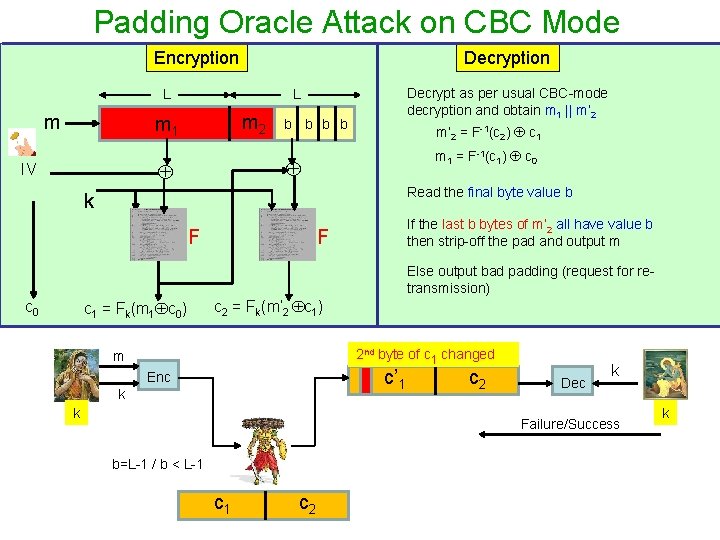
Padding Oracle Attack on CBC Mode Encryption Decryption L m m 2 m 1 b b m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 L Read the final byte value b k F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m F Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) 2 nd byte of c 1 changed m c’ 1 Enc k k c 2 Dec k Failure/Success b=L-1 / b < L-1 c 2 k

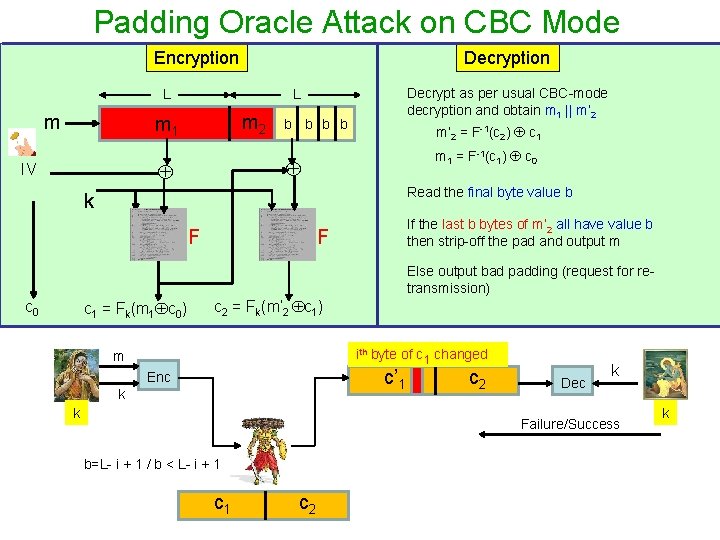
Padding Oracle Attack on CBC Mode Encryption Decryption L m m 2 m 1 b b m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 L Read the final byte value b k F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m F Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) ith byte of c 1 changed m c’ 1 Enc k k c 2 Dec k Failure/Success b=L- i + 1 / b < L- i + 1 c 2 k

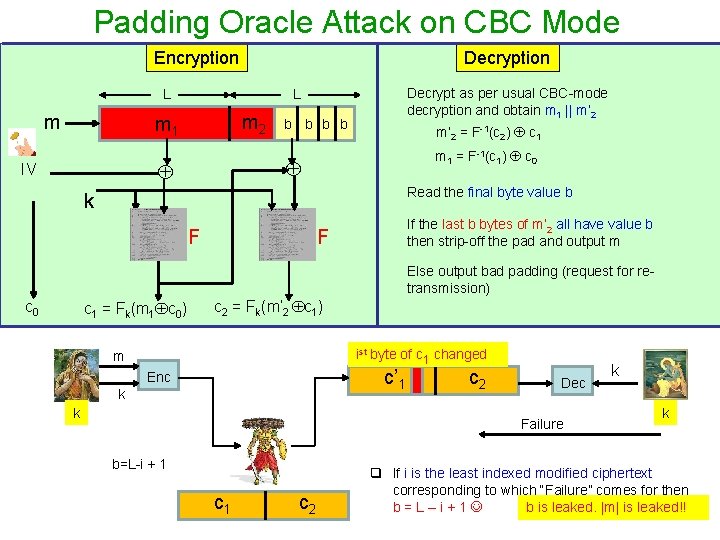
Padding Oracle Attack on CBC Mode Encryption Decryption L m m 2 m 1 b b m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 L Read the final byte value b k F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m F Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) ist byte of c 1 changed m c’ 1 Enc k k c 2 Dec Failure b=L-i + 1 c 2 k k q If i is the least indexed modified ciphertext corresponding to which “Failure” comes for then b=L–i+1 b is leaked. |m| is leaked!!

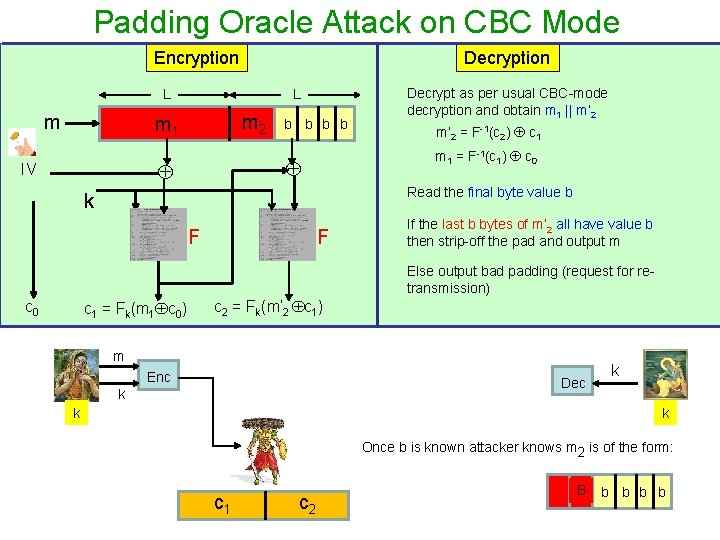
Padding Oracle Attack on CBC Mode Encryption Decryption L m 2 m 1 m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV b b Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 Read the final byte value b k F F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) m Enc Dec k k To do: find m. c 1 c 2 We will see how adv can find the last byte of m. This can be extended for rest of the message bytes

Padding Oracle Attack on CBC Mode Encryption Decryption L m 2 m 1 m’ 2 = F-1(c 2) c 1 m 1 = F-1(c 1) c 0 IV b b Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 Read the final byte value b k F F If the last b bytes of m’ 2 all have value b then strip-off the pad and output m Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) m Enc Dec k k Once b is known attacker knows m 2 is of the form: c 1 c 2 B b b

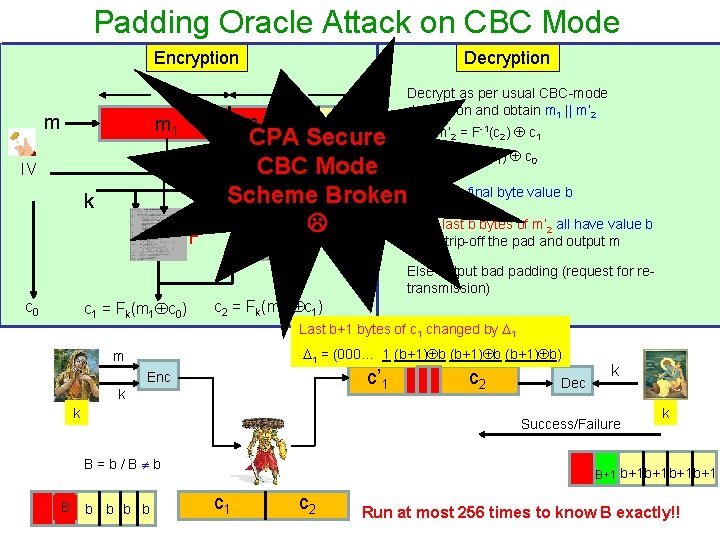
Padding Oracle Attack on CBC Mode Encryption Decryption L m m 2 m 1 b b m’ = F (c ) c CPA Secure m = F (c ) c CBC Mode Scheme Broken. Read the final byte value b If the last b bytes of m’ all have value b 2 1 IV Decrypt as per usual CBC-mode decryption and obtain m 1 || m’ 2 L k F -1 -1 2 1 1 0 2 F then strip-off the pad and output m Else output bad padding (request for retransmission) c 0 c 1 = Fk(m 1 c 0) c 2 = Fk(m’ 2 c 1) Last b+1 bytes of c 1 changed by 1 1 = (000… 1 (b+1) b) m c’ 1 Enc k k Dec k Success/Failure B=b/B b B c 2 b b k B+1 b+1 b+1 b+1 c 2 Run at most 256 times to know B exactly!!

Padding Oracle Attack Serge Vaudenay: Security Flaws Induced by CBC Padding - Applications to SSL, IPSEC, WTLS. . EUROCRYPT 2002: 534 -546

Morale of the Story q Attacker can have control over “what” is decrypted Ø Will help the attacker to break the secrecy !! q Remedy: Ø Capture CCA in the security definition. Ø Chosen-ciphertext attack (CCA) security

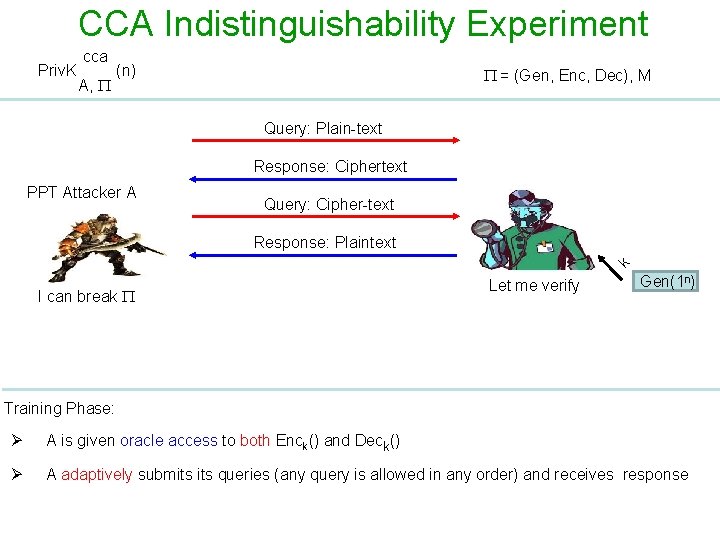
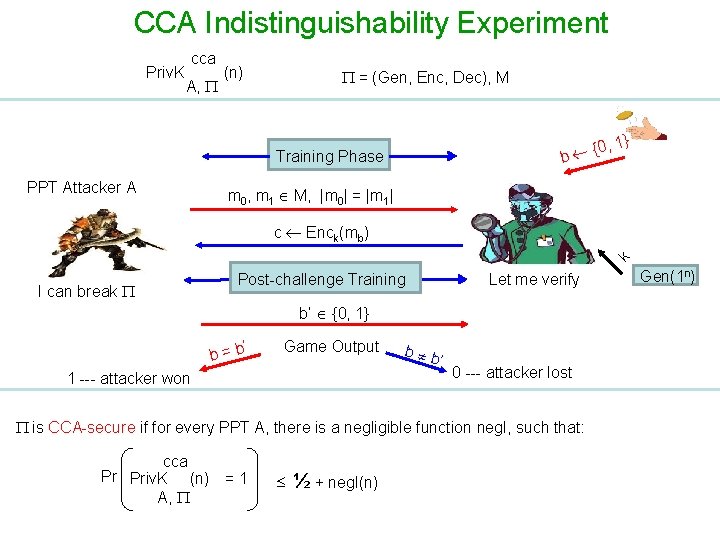
CCA Indistinguishability Experiment Priv. K cca A, (n) = (Gen, Enc, Dec), M Query: Plain-text Response: Ciphertext PPT Attacker A Query: Cipher-text k Response: Plaintext I can break Let me verify Gen(1 n) Training Phase: Ø A is given oracle access to both Enck() and Deck() Ø A adaptively submits queries (any query is allowed in any order) and receives response

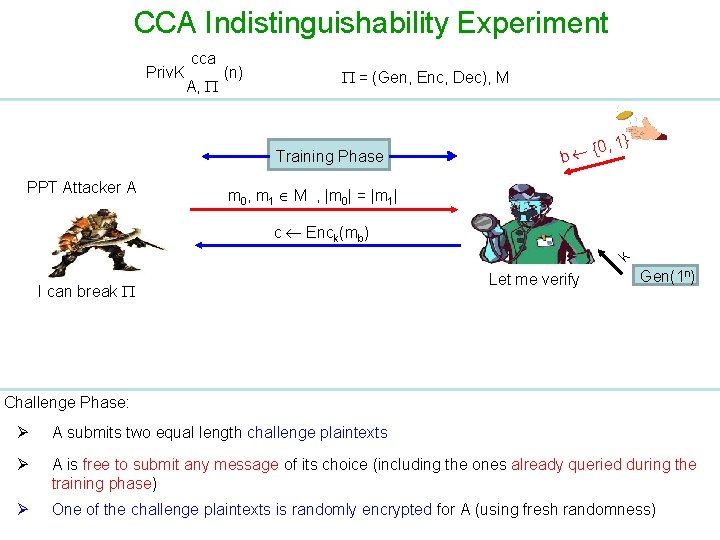
CCA Indistinguishability Experiment Priv. K cca A, (n) = (Gen, Enc, Dec), M Training Phase PPT Attacker A {0 b , 1} m 0, m 1 M , |m 0| = |m 1| k c Enck(mb) I can break Let me verify Gen(1 n) Challenge Phase: Ø A submits two equal length challenge plaintexts Ø A is free to submit any message of its choice (including the ones already queried during the training phase) Ø One of the challenge plaintexts is randomly encrypted for A (using fresh randomness)

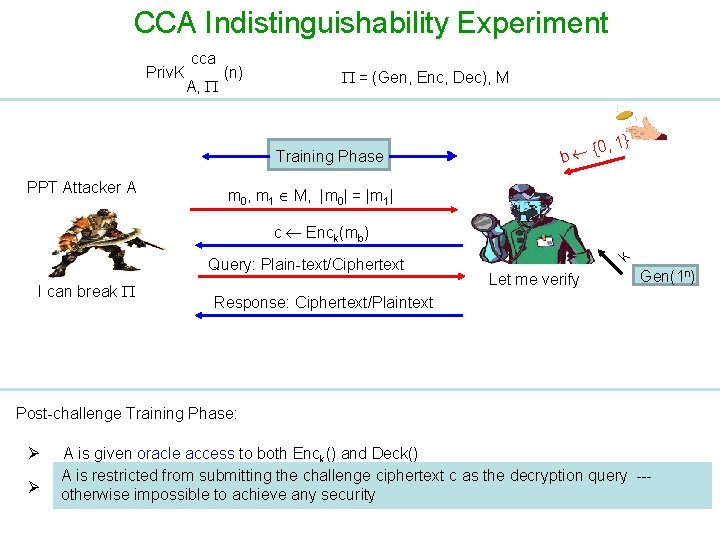
CCA Indistinguishability Experiment Priv. K cca A, (n) = (Gen, Enc, Dec), M Training Phase PPT Attacker A {0 b , 1} m 0, m 1 M, |m 0| = |m 1| Query: Plain-text/Ciphertext I can break k c Enck(mb) Let me verify Gen(1 n) Response: Ciphertext/Plaintext Post-challenge Training Phase: Ø Ø A is given oracle access to both Enck() and Deck() A is restricted from submitting the challenge ciphertext c as the decryption query --A adaptively submits to its achieve encryption/decryption otherwise impossible any security query and receives the response

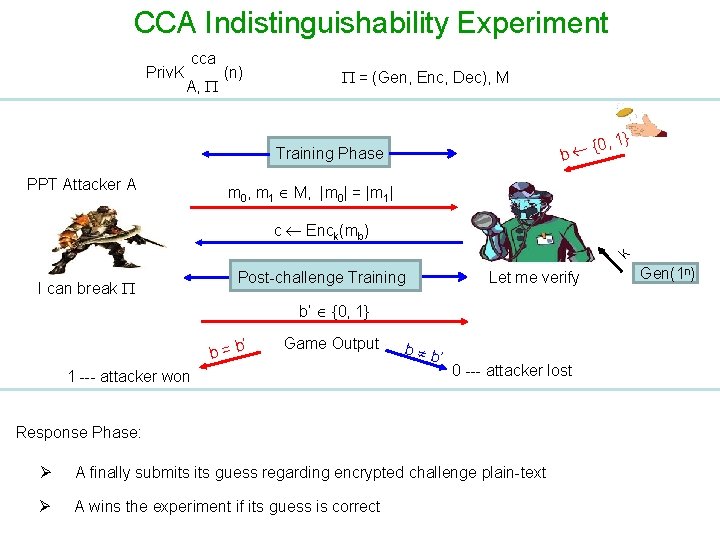
CCA Indistinguishability Experiment Priv. K cca A, (n) = (Gen, Enc, Dec), M Training Phase PPT Attacker A b , 1 {0 } m 0, m 1 M, |m 0| = |m 1| k c Enck(mb) I can break Post-challenge Training Let me verify b’ {0, 1} ’ b=b Game Output 1 --- attacker won b b ’ 0 --- attacker lost Response Phase: Ø A finally submits guess regarding encrypted challenge plain-text Ø A wins the experiment if its guess is correct Gen(1 n)

CCA Indistinguishability Experiment Priv. K cca A, (n) = (Gen, Enc, Dec), M {0 b Training Phase PPT Attacker A , 1} m 0, m 1 M, |m 0| = |m 1| k c Enck(mb) I can break Post-challenge Training Let me verify b’ {0, 1} ’ b=b Game Output 1 --- attacker won b b ’ 0 --- attacker lost is CCA-secure if for every PPT A, there is a negligible function negl, such that: cca Pr Priv. K (n) = 1 A, ½ + negl(n) Gen(1 n)

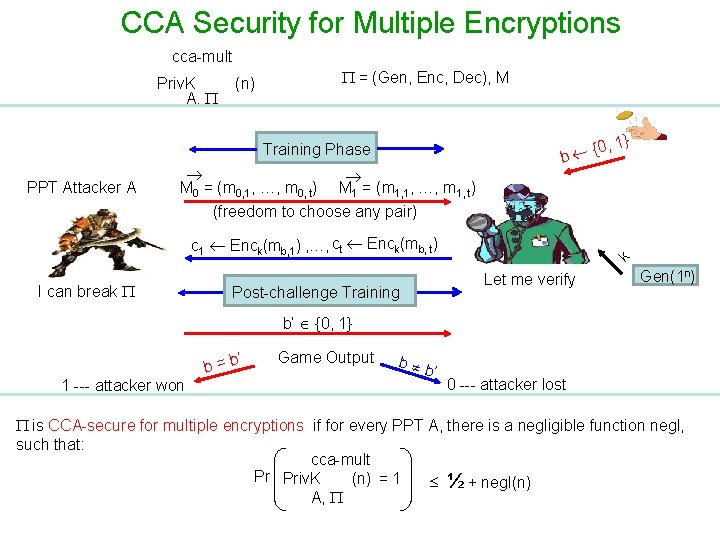
CCA Security for Multiple Encryptions cca-mult Priv. K A, = (Gen, Enc, Dec), M (n) Training Phase PPT Attacker A M 0 = (m 0, 1, …, m 0, t) M 1 = (m 1, 1, …, m 1, t) {0 b , 1} (freedom to choose any pair) I can break Post-challenge Training k c 1 Enck(mb, 1) , …, ct Enck(mb, t) Let me verify Gen(1 n) b’ {0, 1} ’ b=b 1 --- attacker won Game Output b b ’ 0 --- attacker lost is CCA-secure for multiple encryptions if for every PPT A, there is a negligible function negl, such that: cca-mult Pr Priv. K (n) = 1 ½ + negl(n) A,

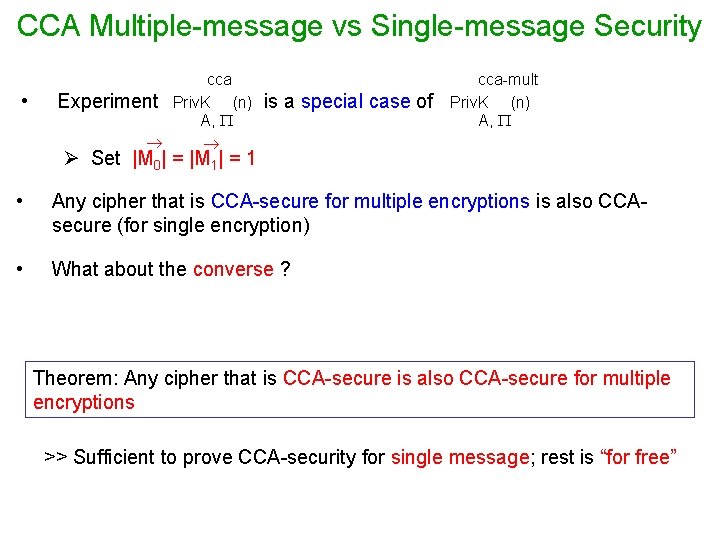
CCA Multiple-message vs Single-message Security • cca Experiment Priv. K (n) A, is a special case of cca-mult Priv. K (n) A, Ø Set |M 0| = |M 1| = 1 • Any cipher that is CCA-secure for multiple encryptions is also CCAsecure (for single encryption) • What about the converse ? Theorem: Any cipher that is CCA-secure is also CCA-secure for multiple encryptions >> Sufficient to prove CCA-security for single message; rest is “for free”

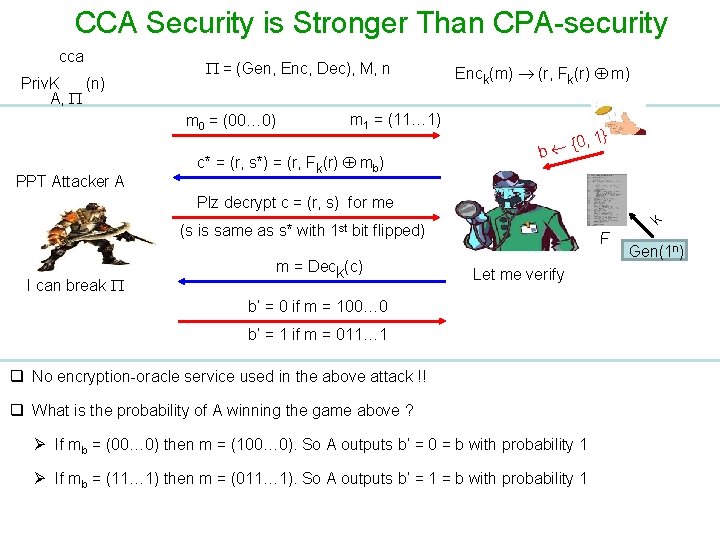
CCA Security is Stronger Than CPA-security cca Priv. K (n) A, = (Gen, Enc, Dec), M, n m 0 = (00… 0) PPT Attacker A Enck(m) (r, Fk(r) m) m 1 = (11… 1) c* = (r, s*) = (r, Fk(r) mb) {0 b , 1} k Plz decrypt c = (r, s) for me (s is same as s* with 1 st bit flipped) I can break m = Deck(c) F Let me verify b’ = 0 if m = 100… 0 b’ = 1 if m = 011… 1 q No encryption-oracle service used in the above attack !! q What is the probability of A winning the game above ? Ø If mb = (00… 0) then m = (100… 0). So A outputs b’ = 0 = b with probability 1 Ø If mb = (11… 1) then m = (011… 1). So A outputs b’ = 1 = b with probability 1 Gen(1 n)

Towards Achieving CCA-Security What capability of adv lets him win? >> Easy to manipulate known ciphertexts to obtain new ciphertexts so that the relation between the underlying messages are known to him. then he gets DO service on the changed ciphertext to get the message. . Using the relation retrieve the original message >> This is called malleability. CPA-secure scheme does not guarantee non-malleability Need a SKE so that >> Creating a new ciphertext will be nearly impossible… >> Changing a ciphertext should either result in an incorrect ciphertext or should decrypt to a plaintext which is unrelated to the original plaintext >> Together, the above two makes DO useless to the adversary. Message Authentication Codes (MAC) helps us to get such a SKE!!

Message Integrity and Authentication q In secure-communication, is it enough to keep privacy of the message? Ø What is the guarantee that a message received by R indeed originated from S and viceversa ? --- issue of message authentication Ø Even if it is confirmed that the message received by R originated from S, what is the guarantee that the message content is genuine ? --- issue of message integrity Ø Message integrity and authentication are also part of secure communication q Message authentication/integrity is important even when privacy is not a concern Ø Any kind of access control system needs them. Think of bank, institute, any organization q Encryption scheme does not help (unless designed with specific purpose of MI and MA). Ø Consider all the CPA secure schemes considered so far (PRF-based, modes of operations); none provide MI/MA Ø Spoofing attack is easy. Changing ciphertext and thereby changing the underlying message is easy!!

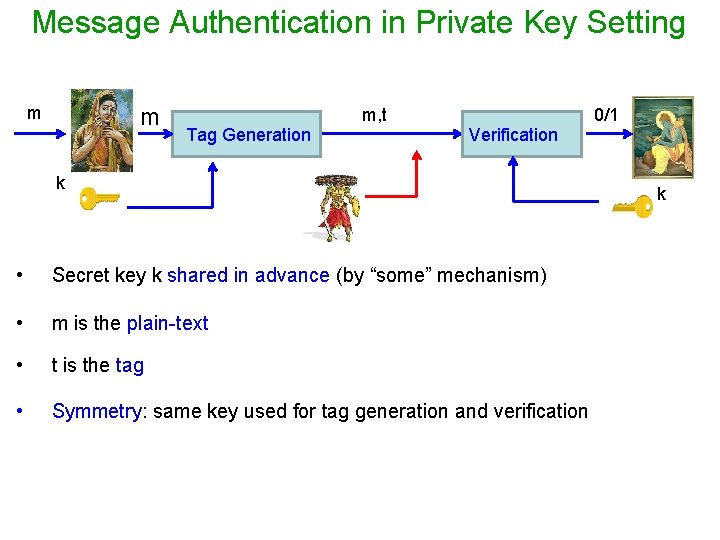
Message Authentication in Private Key Setting m m Tag Generation m, t Verification k • Secret key k shared in advance (by “some” mechanism) • m is the plain-text • t is the tag • Symmetry: same key used for tag generation and verification 0/1 k

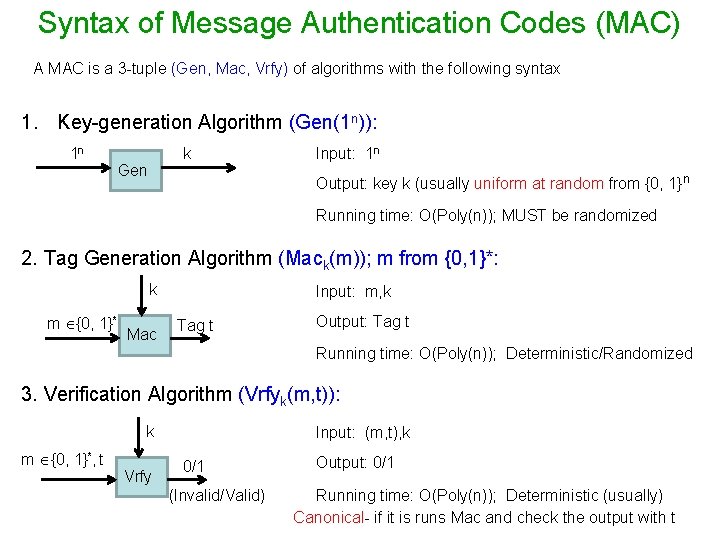
Syntax of Message Authentication Codes (MAC) A MAC is a 3 -tuple (Gen, Mac, Vrfy) of algorithms with the following syntax 1. Key-generation Algorithm (Gen(1 n)): 1 n k Gen Input: 1 n Output: key k (usually uniform at random from {0, 1}n Running time: O(Poly(n)); MUST be randomized 2. Tag Generation Algorithm (Mack(m)); m from {0, 1}*: k m {0, 1}* Mac Input: m, k Tag t Output: Tag t Running time: O(Poly(n)); Deterministic/Randomized 3. Verification Algorithm (Vrfyk(m, t)): k m {0, 1}*, t Vrfy Input: (m, t), k 0/1 (Invalid/Valid) Output: 0/1 Running time: O(Poly(n)); Deterministic (usually) Canonical- if it is runs Mac and check the output with t

Syntax of MAC • Any MAC defines the following three space (sets): 1. Key space (K): Ø Set of all possible keys output by algorithm Gen 2. Plain-text (message) space (M): Ø Set of all possible “legal” message (i. e. those supported by Mac) 3. Tag space (T): • Ø Set of all tags output by algorithm Mac Ø The sets M and K together define the set T Any MAC is defined by specifying (Gen, Mac, Vrfy) and M Correctness: For every n, every k output by Gen and every message m the following should hold : Vrfyk(m, Mack(m)) = 1

Security for MAC - Randomized PPT Chosen Message Attack (CMA) It is not possible to come up with (m, t) if no tag on m is not seen before It is not possible to come up with (m, t) if (m, t) is not seen before - Randomized PPT Chosen Message and Verification Attack (CMVA) It is not possible to come up with (m, t) if (m, t) has not been seen before. It is not possible to come up with (m, t) if (m, t) is not seen before

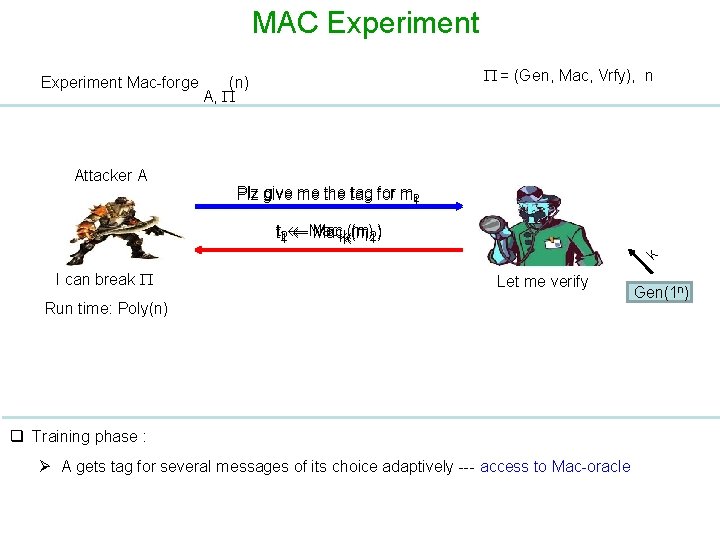
MAC Experiment Mac-forge Attacker A = (Gen, Mac, Vrfy), n (n) A, Plz give me the tag for m 21 l k t 21 l Mackk(m (ml)21) I can break Let me verify Run time: Poly(n) q Training phase : Ø A gets tag for several messages of its choice adaptively --- access to Mac-oracle Gen(1 n)

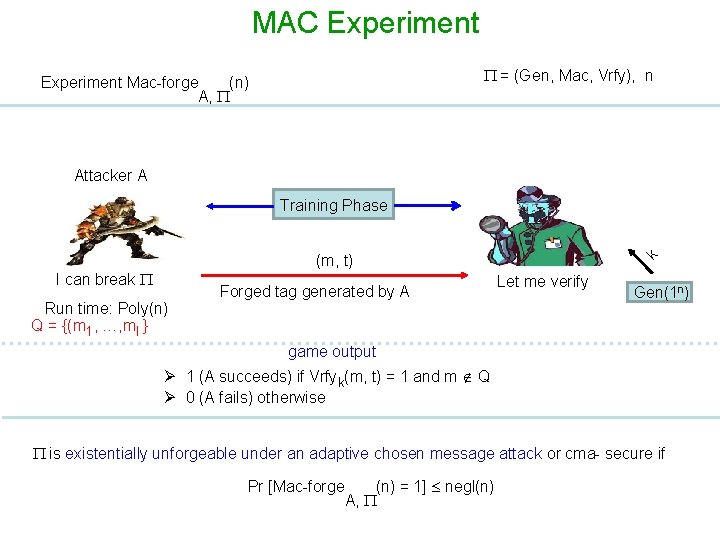
MAC Experiment = (Gen, Mac, Vrfy), n Experiment Mac-forge (n) A, Attacker A Training Phase I can break Run time: Poly(n) Q = {(m 1, …, ml } Forged tag generated by A k (m, t) Let me verify Gen(1 n) game output Ø 1 (A succeeds) if Vrfyk(m, t) = 1 and m Q Ø 0 (A fails) otherwise is existentially unforgeable under an adaptive chosen message attack or cma- secure if Pr [Mac-forge (n) = 1] negl(n) A,

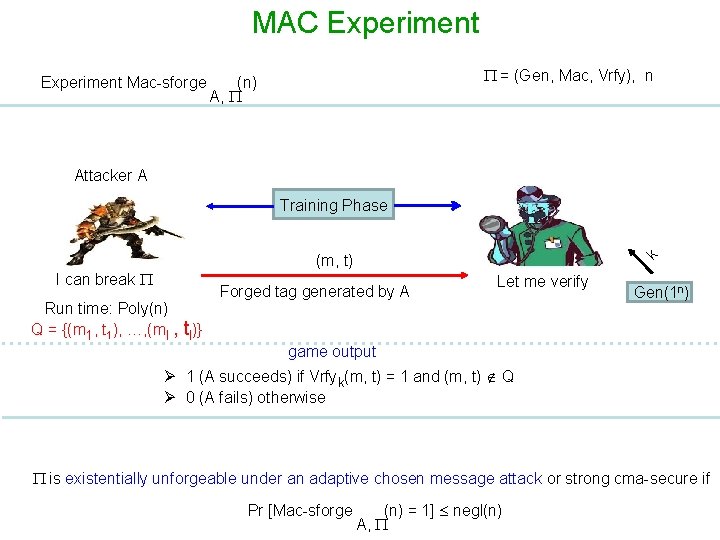
MAC Experiment Mac-sforge = (Gen, Mac, Vrfy), n (n) A, Attacker A Training Phase I can break Run time: Poly(n) Q = {(m 1, t 1), …, (ml , tl)} k (m, t) Forged tag generated by A Let me verify Gen(1 n) game output Ø 1 (A succeeds) if Vrfyk(m, t) = 1 and (m, t) Q Ø 0 (A fails) otherwise is existentially unforgeable under an adaptive chosen message attack or strong cma-secure if Pr [Mac-sforge (n) = 1] negl(n) A,
