Cryptography Lecture 7 Arpita Patra Arpita Patra Recall







- Slides: 30

Cryptography Lecture 7 Arpita Patra © Arpita Patra

Recall >> New definitions for SKE o cpa, cpa-security & cpa-mult-security >> New assumptions o PRF, PRP, SPRP

Today’s Goal - cpa-secure scheme from PRF - Proof of security - Practical cpa-secure schemes from PRF/PRP/SPRP for long messages o SSL (Secure Sockets Layer) 3. 0, o TLS (Transport Layer Security) 1. 0

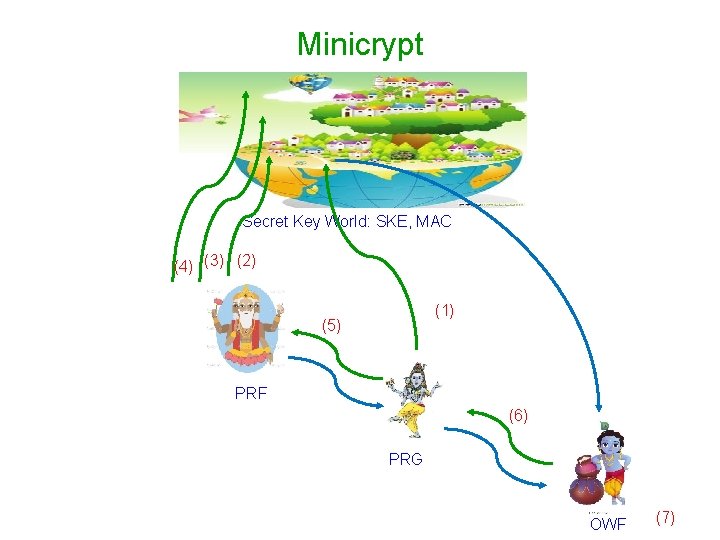
Minicrypt Secret Key World: SKE, MAC (4) (3) (2) (1) (5) PRF (6) PRG OWF (7)

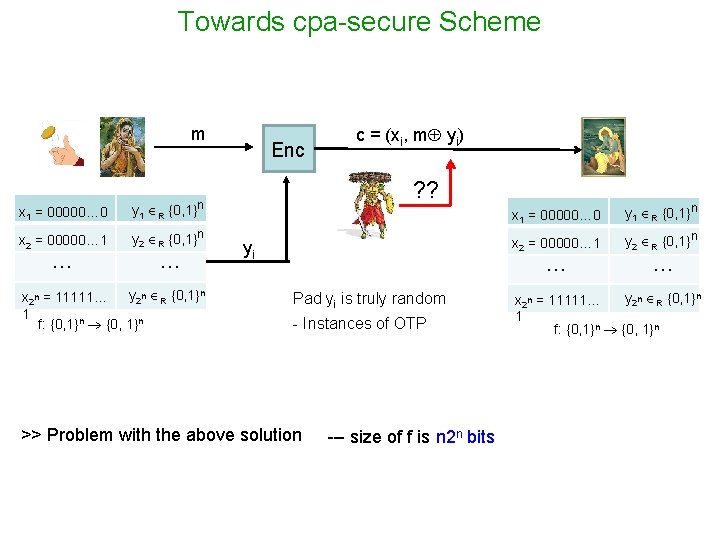
Towards cpa-secure Scheme m x 1 = 00000… 0 y 1 R {0, 1}n x 2 = 00000… 1 y 2 R {0, 1}n … … y 2 n R {0, 1}n x 2 n = 11111… 1 f: {0, 1}n Enc c = (xi, m yi) ? ? yi x 1 = 00000… 0 y 1 R {0, 1}n x 2 = 00000… 1 y 2 R {0, 1}n … Pad yi is truly random - Instances of OTP >> Problem with the above solution --- size of f is n 2 n bits … y 2 n R {0, 1}n x 2 n = 11111… 1 f: {0, 1}n

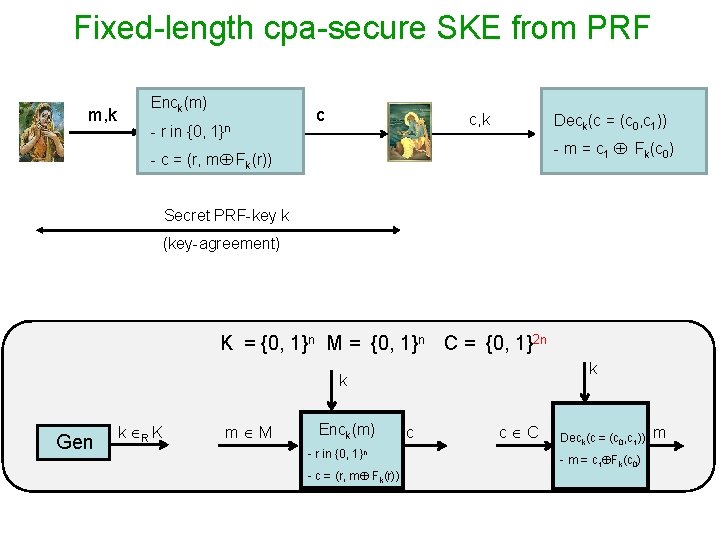
Fixed-length cpa-secure SKE from PRF m, k Enck(m) - r in {0, 1}n c c, k Deck(c = (c 0, c 1)) - m = c 1 Fk(c 0) - c = (r, m Fk(r)) Secret PRF-key k (key-agreement) K = {0, 1}n M = {0, 1}n C = {0, 1}2 n k k Gen k R K m M Enck(m) - r in {0, 1}n - c = (r, m Fk(r)) c c C Deck(c = (c 0, c 1)) - m = c 1 Fk(c 0) m

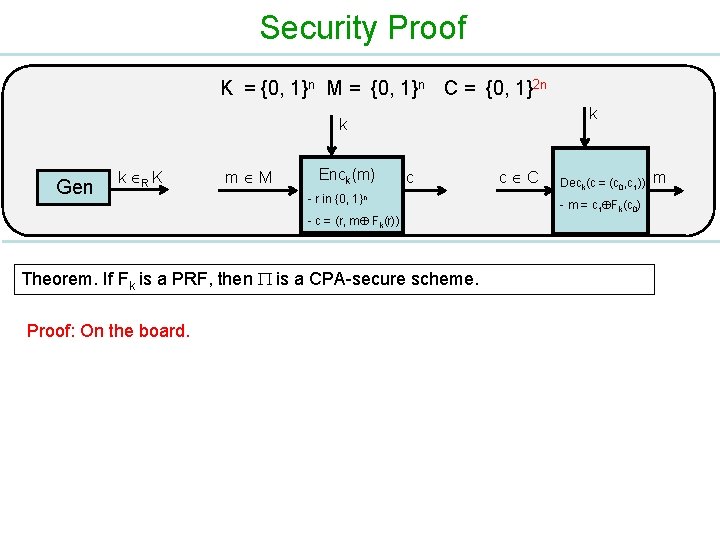
Security Proof K = {0, 1}n M = {0, 1}n C = {0, 1}2 n k k Gen k R K m M Enck(m) c - r in {0, 1}n - c = (r, m Fk(r)) Theorem. If Fk is a PRF, then is a CPA-secure scheme. Proof: On the board. c C Deck(c = (c 0, c 1)) - m = c 1 Fk(c 0) m

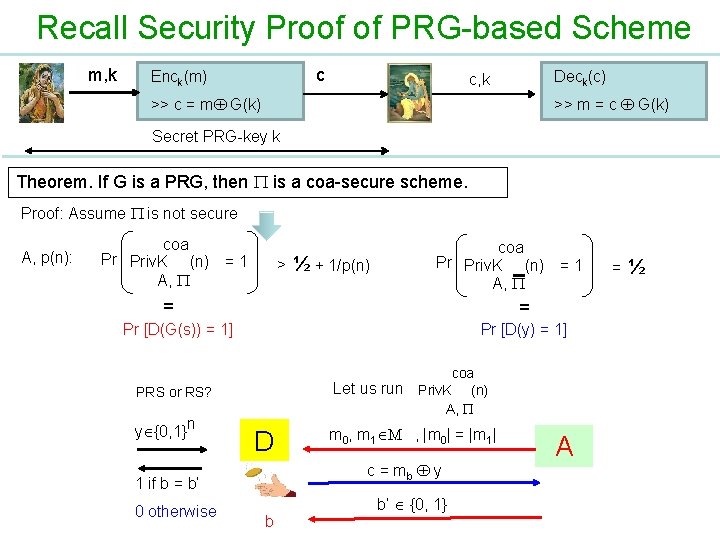
Recall Security Proof of PRG-based Scheme m, k c Enck(m) Deck(c) c, k >> m = c G(k) >> c = m G(k) Secret PRG-key k Theorem. If G is a PRG, then is a coa-secure scheme. Proof: Assume is not secure A, p(n): coa Pr Priv. K (n) = 1 A, > ½ + 1/p(n) coa Pr Priv. K (n) = 1 A, = = Pr [D(G(s)) = 1] Pr [D(y) = 1] coa Let us run Priv. K (n) A, PRS or RS? y {0, 1}n D c = mb y 1 if b = b’ 0 otherwise m 0, m 1 M , |m 0| = |m 1| b b’ {0, 1} A = ½

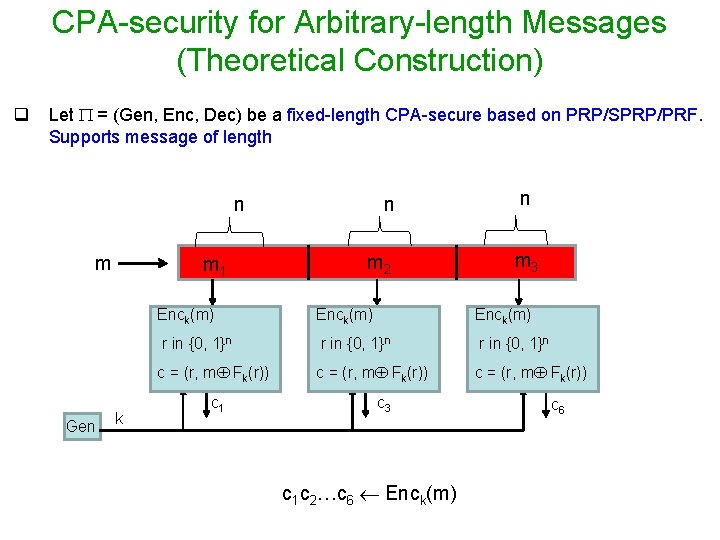
CPA-security for Arbitrary-length Messages (Theoretical Construction) q Let = (Gen, Enc, Dec) be a fixed-length CPA-secure based on PRP/SPRP/PRF. Supports message of length n m Gen m 1 k n m 2 n m 3 Enck(m) r in {0, 1}n c = (r, m Fk(r)) c 1 c 3 c 1 c 2…c 6 Enck(m) c 6

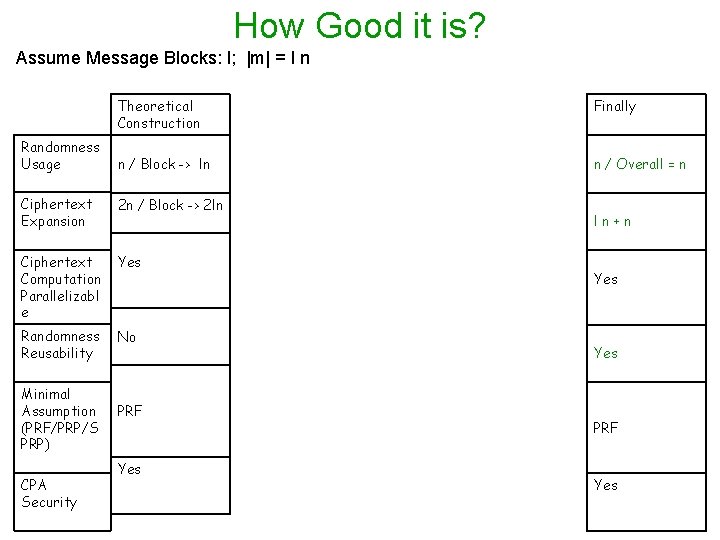
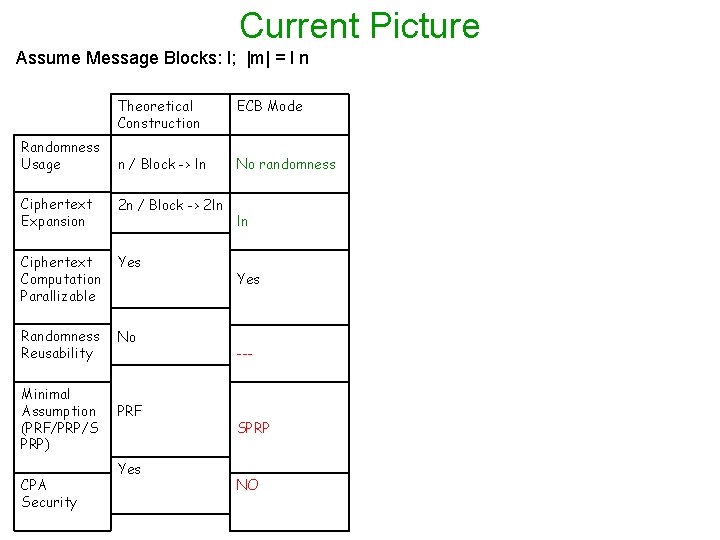
How Good it is? Assume Message Blocks: l; |m| = l n Randomness Usage Theoretical Construction Finally n / Block -> ln n / Overall = n Ciphertext Expansion 2 n / Block -> 2 ln Ciphertext Computation Parallelizabl e Yes Randomness Reusability No Minimal Assumption (PRF/PRP/S PRP) CPA Security PRF Yes ln+n Yes PRF Yes

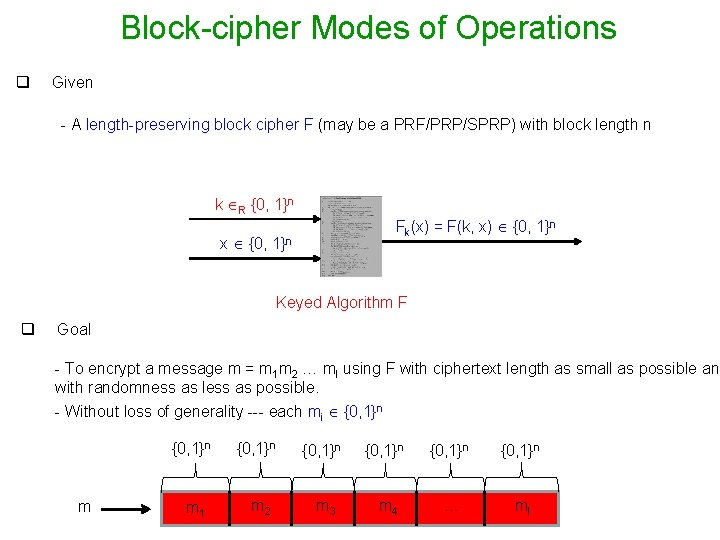
Block-cipher Modes of Operations q Given - A length-preserving block cipher F (may be a PRF/PRP/SPRP) with block length n k R {0, 1}n Fk(x) = F(k, x) {0, 1}n x {0, 1}n Keyed Algorithm F q Goal - To encrypt a message m = m 1 m 2 … ml using F with ciphertext length as small as possible and with randomness as less as possible. - Without loss of generality --- each mi {0, 1}n m {0, 1}n {0, 1}n m 1 m 2 m 3 m 4 … ml

Electronic Code Book (ECB) Mode m m 2 m 1 m 3 k Gen F c 1 = Fk(m 1) F c 2 = Fk(m 2) F c 3 = Fk(m 3) q Encryption: compute ci = Fk(mi) – No randomness used at all ! q Decryption: compute mi = Fk-1(ci) q Parallelizable! q CPA Security ? |c| = |m| >> Assumes Fk is SPRP. >> Deterministic Encryption >> No. not even coa security for multi message

Current Picture Assume Message Blocks: l; |m| = l n Randomness Usage Theoretical Construction ECB Mode n / Block -> ln No randomness Ciphertext Expansion 2 n / Block -> 2 ln Ciphertext Computation Parallizable Yes Randomness Reusability No Minimal Assumption (PRF/PRP/S PRP) CPA Security PRF Yes ln Yes --- SPRP NO

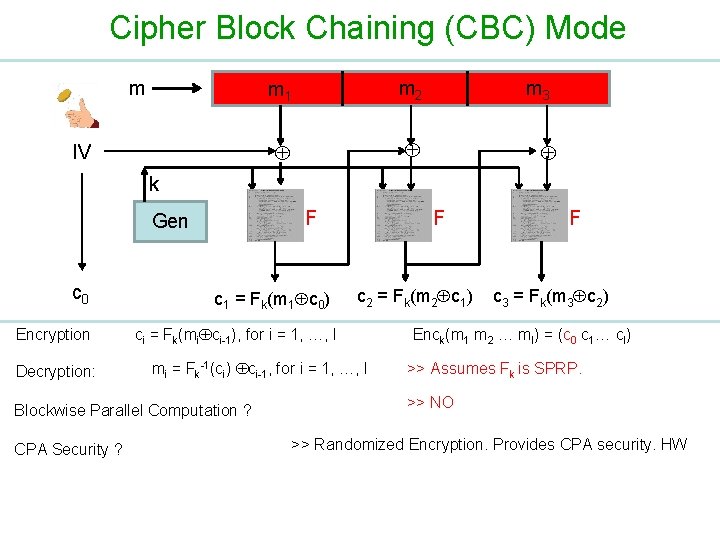
Cipher Block Chaining (CBC) Mode m IV m 1 m 2 m 3 k F Gen c 0 Encryption Decryption: c 1 = Fk(m 1 c 0) c 2 = Fk(m 2 c 1) ci = Fk(mi ci-1), for i = 1, …, l mi = Fk-1(ci) ci-1, for i = 1, …, l Blockwise Parallel Computation ? CPA Security ? F F c 3 = Fk(m 3 c 2) Enck(m 1 m 2 … ml) = (c 0 c 1… cl) >> Assumes Fk is SPRP. >> NO >> Randomized Encryption. Provides CPA security. HW

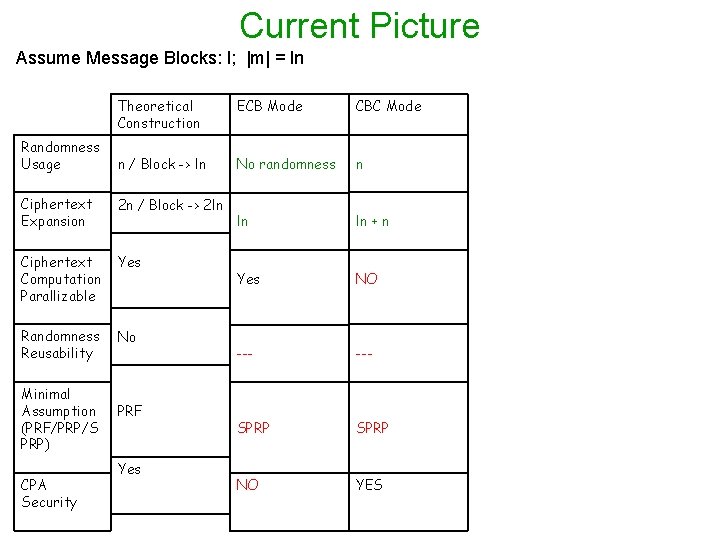
Current Picture Assume Message Blocks: l; |m| = ln Randomness Usage Theoretical Construction ECB Mode CBC Mode n / Block -> ln No randomness n ln ln + n Yes NO --- SPRP NO YES Ciphertext Expansion 2 n / Block -> 2 ln Ciphertext Computation Parallizable Yes Randomness Reusability No Minimal Assumption (PRF/PRP/S PRP) CPA Security PRF Yes

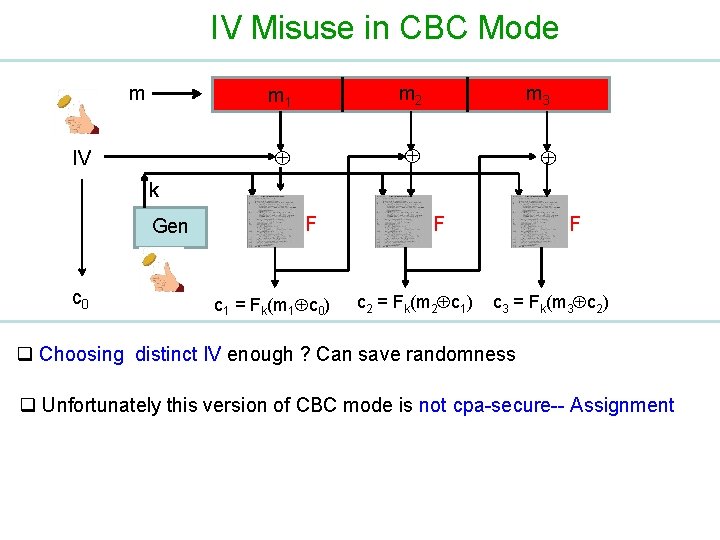
IV Misuse in CBC Mode m IV m 1 m 2 m 3 k Gen c 0 F c 1 = Fk(m 1 c 0) F c 2 = Fk(m 2 c 1) F c 3 = Fk(m 3 c 2) q Choosing distinct IV enough ? Can save randomness q Unfortunately this version of CBC mode is not cpa-secure-- Assignment

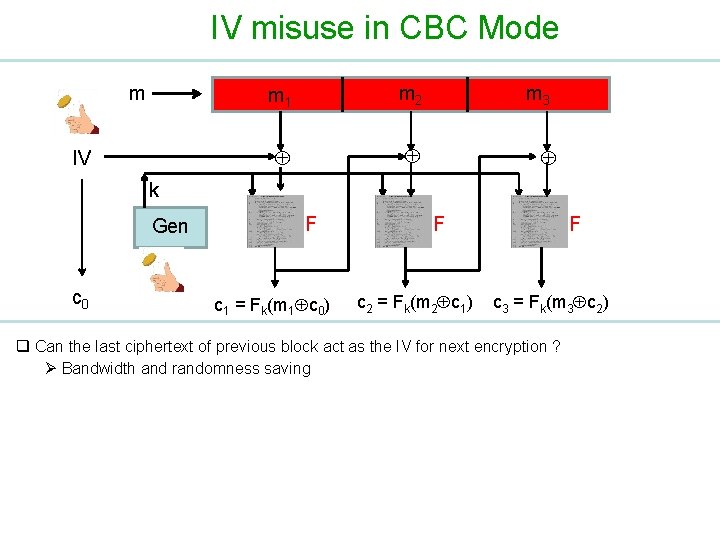
IV misuse in CBC Mode m IV m 1 m 2 m 3 k Gen c 0 F c 1 = Fk(m 1 c 0) F c 2 = Fk(m 2 c 1) F c 3 = Fk(m 3 c 2) q Can the last ciphertext of previous block act as the IV for next encryption ? Ø Bandwidth and randomness saving

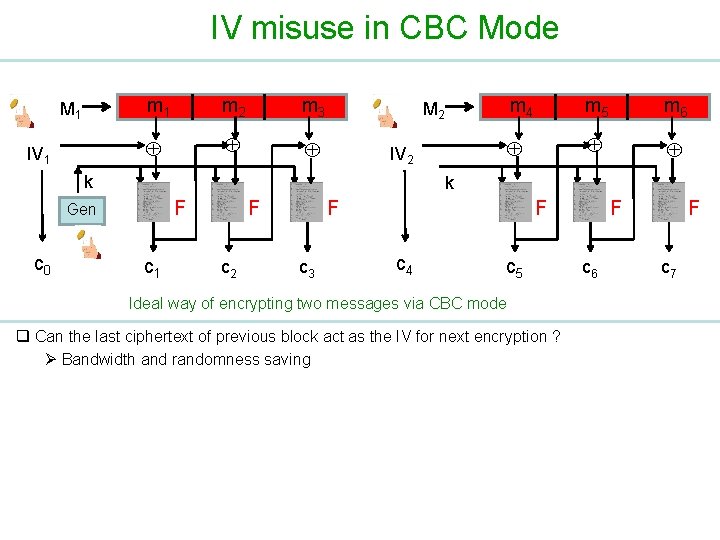
IV misuse in CBC Mode M 1 IV 1 m 2 m 3 M 2 IV 2 k m 5 m 6 k F Gen c 0 m 4 c 1 F c 2 F c 3 F c 4 c 5 Ideal way of encrypting two messages via CBC mode q Can the last ciphertext of previous block act as the IV for next encryption ? Ø Bandwidth and randomness saving F c 6 F c 7

IV misuse in CBC Mode- Chained CBC M 1 IV 1 m 2 m 3 M 2 k F Gen c 0 c 1 F c 2 F c 3 m 4 m 5 m 6 k F c 4 F c 5 F c 6 Chained CBC mode q Can the last ciphertext of previous block act as the IV for next encryption ? BEAST on SSL/TSL >> Bandwidth and attack randomness saving No modifications to crypto schemes even if the q Chained CBC mode --- used in SSL 3. 0 and TLS 1. 0 modifications look benign >> Stateful variant of CBC q CPA security? >> It is “equivalent” to encrypting a single large message M = M 1 || M 2 via CBC mode >> Yet Not CPA-secure

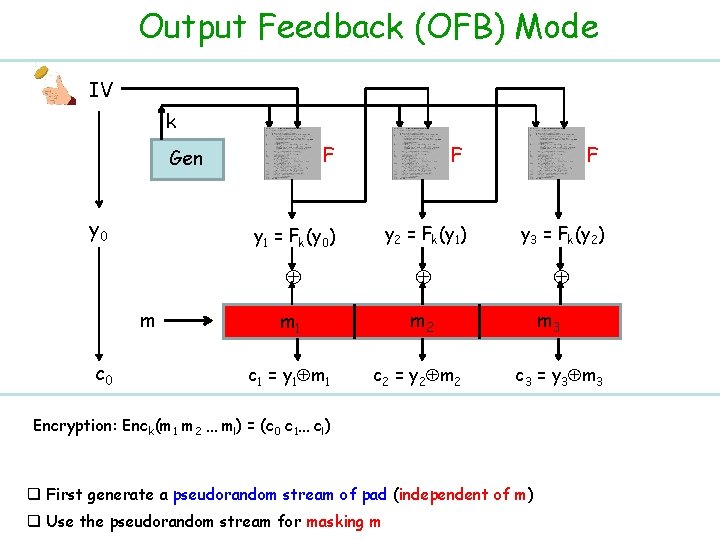
Output Feedback (OFB) Mode IV k F F y 1 = Fk(y 0) y 2 = Fk(y 1) y 3 = Fk(y 2) m 1 m 2 c 1 = y 1 m 1 c 2 = y 2 m 2 Gen y 0 m c 0 F m 3 c 3 = y 3 m 3 Encryption: Enck(m 1 m 2 … ml) = (c 0 c 1… cl) q First generate a pseudorandom stream of pad (independent of m) q Use the pseudorandom stream for masking m

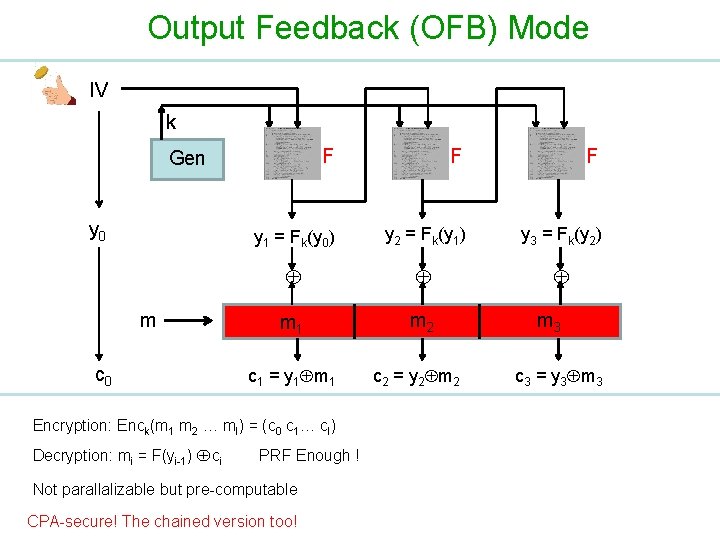
Output Feedback (OFB) Mode IV k F F F y 1 = Fk(y 0) y 2 = Fk(y 1) y 3 = Fk(y 2) m 1 m 2 Gen y 0 m c 0 c 1 = y 1 m 1 Encryption: Enck(m 1 m 2 … ml) = (c 0 c 1… cl) Decryption: mi = F(yi-1) ci PRF Enough ! Not parallalizable but pre-computable CPA-secure! The chained version too! c 2 = y 2 m 3 c 3 = y 3 m 3

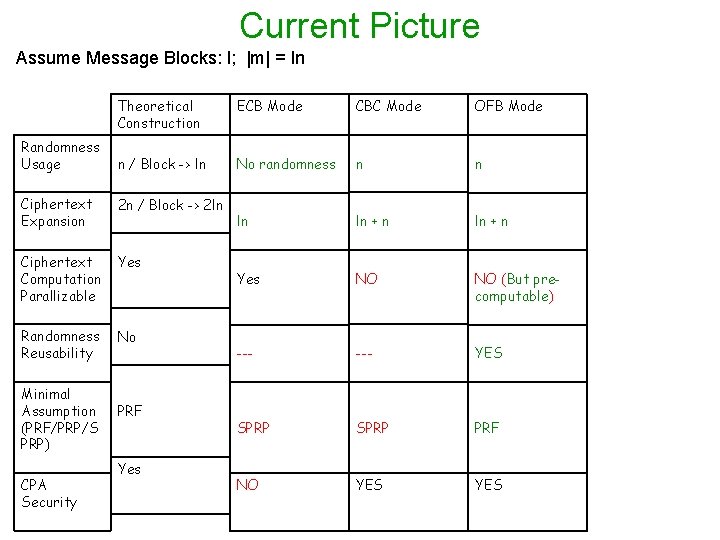
Current Picture Assume Message Blocks: l; |m| = ln Randomness Usage Theoretical Construction ECB Mode CBC Mode OFB Mode n / Block -> ln No randomness n n ln ln + n Yes NO NO (But precomputable) --- YES SPRP PRF NO YES Ciphertext Expansion 2 n / Block -> 2 ln Ciphertext Computation Parallizable Yes Randomness Reusability No Minimal Assumption (PRF/PRP/S PRP) CPA Security PRF Yes

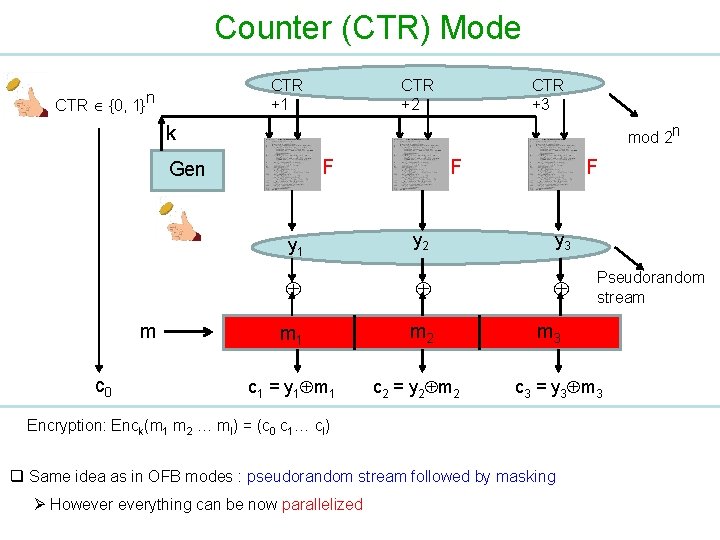
Counter (CTR) Mode CTR +1 CTR {0, 1}n CTR +2 CTR +3 k mod 2 n F Gen m c 0 F F y 1 y 2 y 3 m 1 m 2 c 1 = y 1 m 1 c 2 = y 2 m 3 c 3 = y 3 m 3 Encryption: Enck(m 1 m 2 … ml) = (c 0 c 1… cl) q Same idea as in OFB modes : pseudorandom stream followed by masking Ø Howeverything can be now parallelized Pseudorandom stream

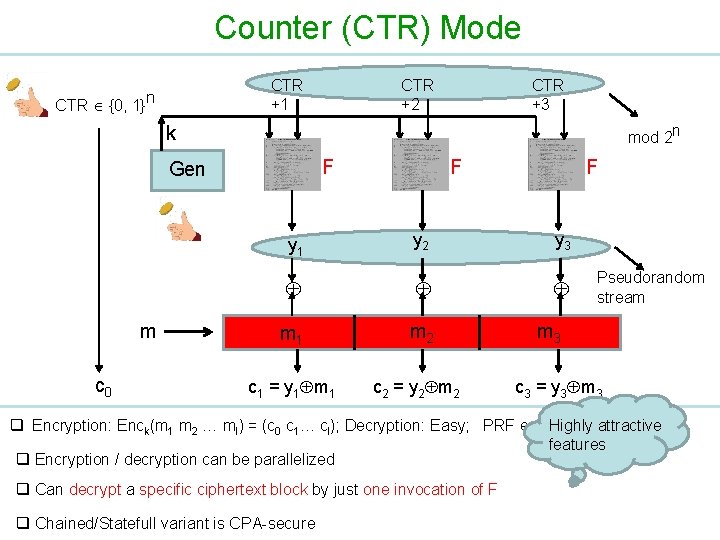
Counter (CTR) Mode CTR +1 CTR {0, 1}n CTR +2 CTR +3 k mod 2 n F Gen m c 0 F F y 1 y 2 y 3 m 1 m 2 c 1 = y 1 m 1 c 2 = y 2 m 2 Pseudorandom stream m 3 c 3 = y 3 m 3 q Encryption: Enck(m 1 m 2 … ml) = (c 0 c 1… cl); Decryption: Easy; PRF enough! Highly attractive features q Encryption / decryption can be parallelized q Can decrypt a specific ciphertext block by just one invocation of F q Chained/Statefull variant is CPA-secure

Current Picture Assume Message Blocks: l; |m| = ln Randomness Usage Theoretical Construction ECB Mode CBC Mode OFB Mode CTR Mode n / Block -> ln No randomness n n n ln ln + n Yes NO NO (But precomputable) YES --- YES SPRP PRF NO YES YES Ciphertext Expansion 2 n / Block -> 2 ln Ciphertext Computation Parallizable Yes Randomness Reusability No Minimal Assumption (PRF/PRP/S PRP) CPA Security PRF Yes

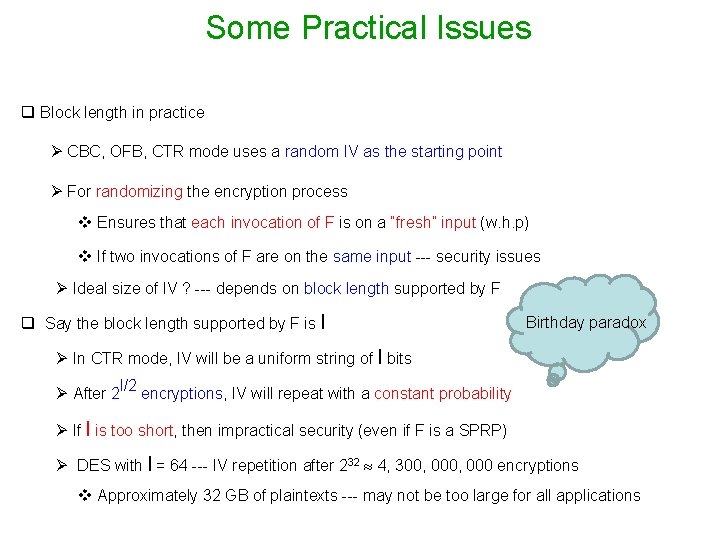
Some Practical Issues q Block length in practice Ø CBC, OFB, CTR mode uses a random IV as the starting point Ø For randomizing the encryption process v Ensures that each invocation of F is on a “fresh” input (w. h. p) v If two invocations of F are on the same input --- security issues Ø Ideal size of IV ? --- depends on block length supported by F q Say the block length supported by F is l Birthday paradox Ø In CTR mode, IV will be a uniform string of l bits Ø After 2 l/2 encryptions, IV will repeat with a constant probability Ø If l is too short, then impractical security (even if F is a SPRP) Ø DES with l = 64 --- IV repetition after 232 4, 300, 000 encryptions v Approximately 32 GB of plaintexts --- may not be too large for all applications

Some Practical Issues q IV misuse Ø Assumption made: a uniform IV selected as the starting point Ø What if the assumption goes wrong (say due to poor randomness generation, incorrect implementation, etc) ? Ø Problems if IV is repeated q In the CTR and OFB modes, the same pseudorandom stream will be generated v Two messages XORed with the same stream --- serious security breach q In the CBC mode, the effect is not that serious v After few blocks, inputs to F will “diverge” (blocks of m are also part of the input) q Solution against IV misuse Ø Use CBC mode Ø Or stateful OFB / CTR mode


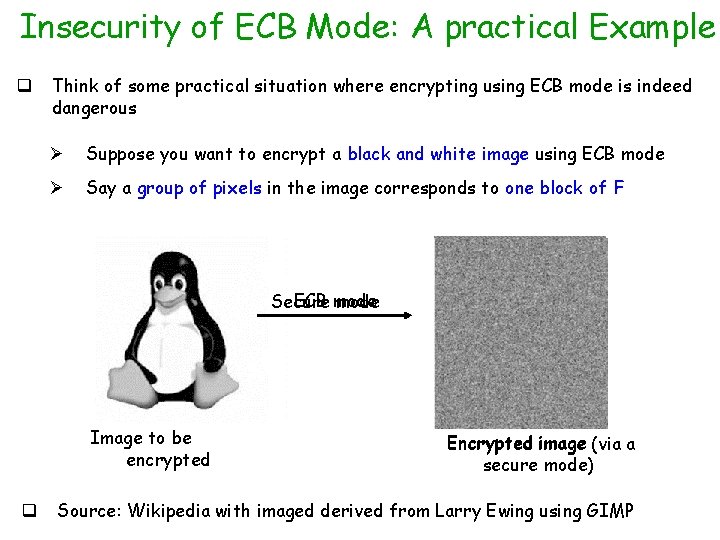
Insecurity of ECB Mode: A practical Example q Think of some practical situation where encrypting using ECB mode is indeed dangerous Ø Suppose you want to encrypt a black and white image using ECB mode Ø Say a group of pixels in the image corresponds to one block of F ECB mode Secure mode Image to be encrypted q Encrypted image (via a secure mode) Source: Wikipedia with imaged derived from Larry Ewing using GIMP

Block-cipher Modes of Operations : Some Practical Issues q Message transmission errors (non-adversarial) Ø Dropped packets, changed bits, etc Ø Different modes of operations have different effect Ø Standard solutions --- error-correction, re-transmission q Message transmission errors (adversarial) Ø What if the adversary “changes” ciphertext contents ? Ø Issue of message integrity / authentication v Will be discussed in detail later
 Arpita choudhury age
Arpita choudhury age Recallcrypto com
Recallcrypto com 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Akshaya patra donation online
Akshaya patra donation online Yamane formula for sample size
Yamane formula for sample size Patra v lese
Patra v lese Goutam patra
Goutam patra Rostlinná patra
Rostlinná patra Pragyapan patra
Pragyapan patra Era of quality at the akshaya patra foundation
Era of quality at the akshaya patra foundation Cipher patra
Cipher patra Cipher patra
Cipher patra Sudhakar patra
Sudhakar patra Neocate formula recall
Neocate formula recall Recall bias
Recall bias Fdt statistics
Fdt statistics Can hypnosis force people to act against their will
Can hypnosis force people to act against their will Recall the rules of probability.
Recall the rules of probability. Beef recall
Beef recall Difference between recall and recognition
Difference between recall and recognition Recall column
Recall column Woodcock johnson basal and ceiling examples
Woodcock johnson basal and ceiling examples Aviane recall
Aviane recall Product mapping definition
Product mapping definition Moment of recall
Moment of recall Recall column
Recall column Intermediate processing psychology example
Intermediate processing psychology example Fda district recall coordinator
Fda district recall coordinator Active recall studying
Active recall studying Precision and recall in information retrieval
Precision and recall in information retrieval Recall what an atom is.
Recall what an atom is.