Foundations of Secure Computation Arpita Patra Arpita Patra

- Slides: 19

Foundations of Secure Computation Arpita Patra © Arpita Patra

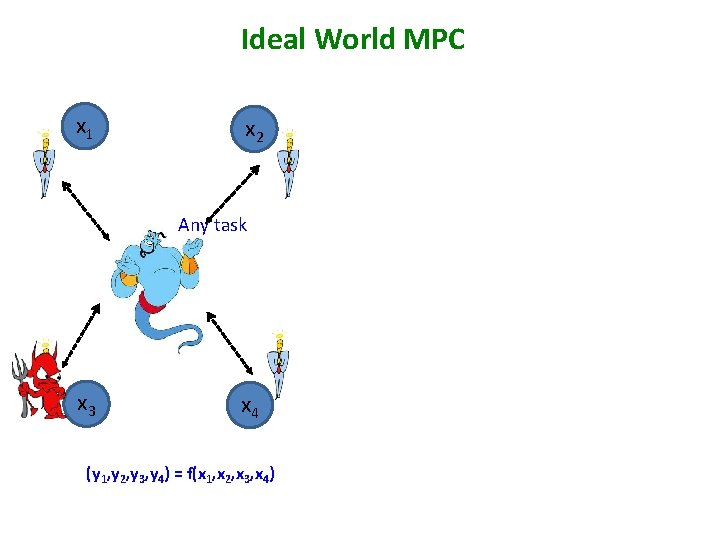
Ideal World MPC x 1 x 2 Any task x 3 x 4 (y 1, y 2, y 3, y 4) = f(x 1, x 2, x 3, x 4)

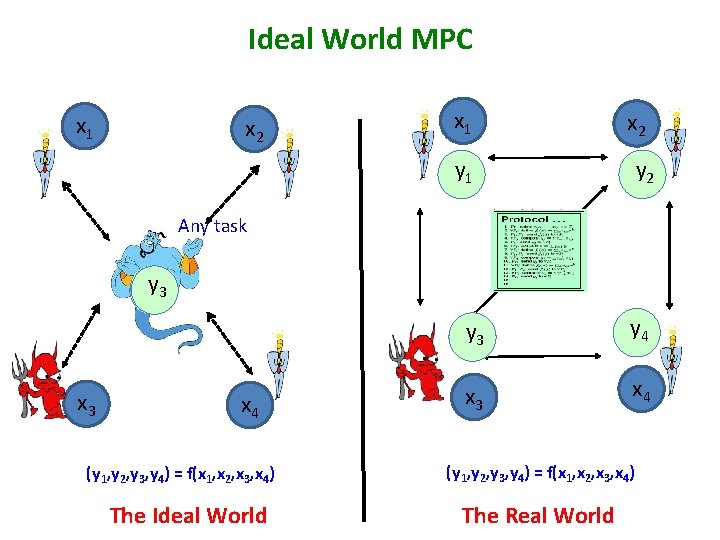
Ideal World MPC x 1 x 2 y 2 y 1 Any task y 2134 x 3 x 4 (y 1, y 2, y 3, y 4) = f(x 1, x 2, x 3, x 4) The Ideal World y 3 y 4 x 3 x 4 (y 1, y 2, y 3, y 4) = f(x 1, x 2, x 3, x 4) The Real World

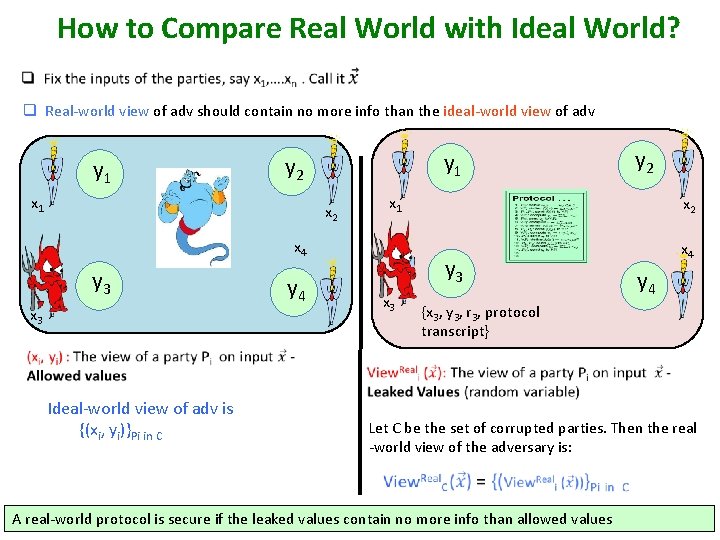
How to Compare Real World with Ideal World? q Real-world view of adv should contain no more info than the ideal-world view of adv y 1 y 2 x 1 x 2 x 4 y 3 x 3 y 2 x 2 y 3 y 4 x 3 x 4 y 4 {x 3, y 3, r 3, protocol transcript} Ideal-world view of adv is {(xi, yi)}Pi in C Let C be the set of corrupted parties. Then the real -world view of the adversary is: A real-world protocol is secure if the leaked values contain no more info than allowed values

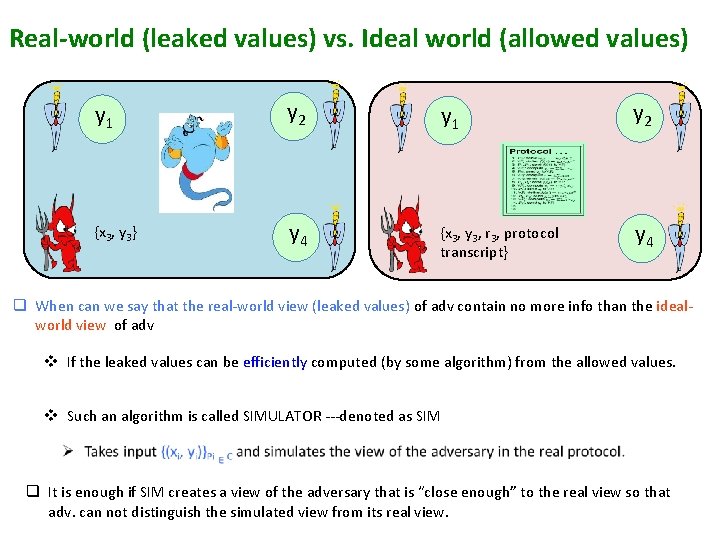
Real-world (leaked values) vs. Ideal world (allowed values) y 1 y 2 {x 3, y 3} y 4 {x 3, y 3, r 3, protocol transcript} y 4 q When can we say that the real-world view (leaked values) of adv contain no more info than the idealworld view of adv v If the leaked values can be efficiently computed (by some algorithm) from the allowed values. v Such an algorithm is called SIMULATOR ---denoted as SIM q It is enough if SIM creates a view of the adversary that is “close enough” to the real view so that adv. can not distinguish the simulated view from its real view.

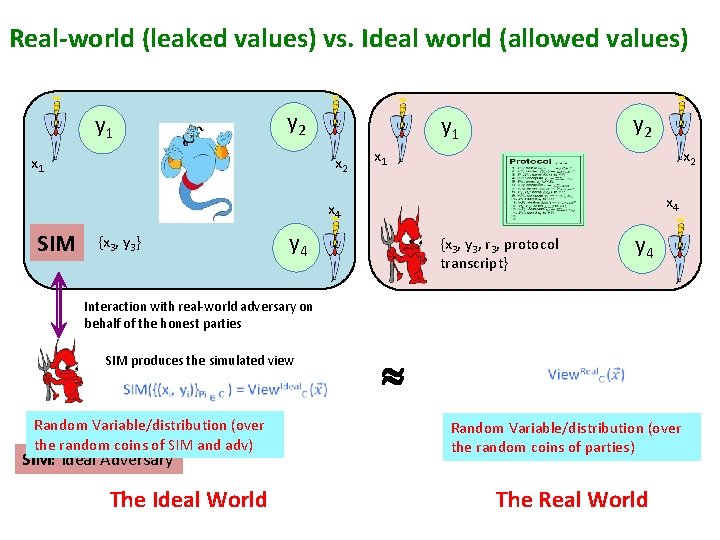
Real-world (leaked values) vs. Ideal world (allowed values) y 2 y 1 x 1 y 2 y 1 x 2 x 4 x 4 SIM {x 3, y 3} y 4 {x 3, y 3, r 3, protocol transcript} y 4 Interaction with real-world adversary on behalf of the honest parties SIM produces the simulated view Random Variable/distribution (over the random coins of SIM and adv) SIM: Ideal Adversary The Ideal World Random Variable/distribution (over the random coins of parties) The Real World

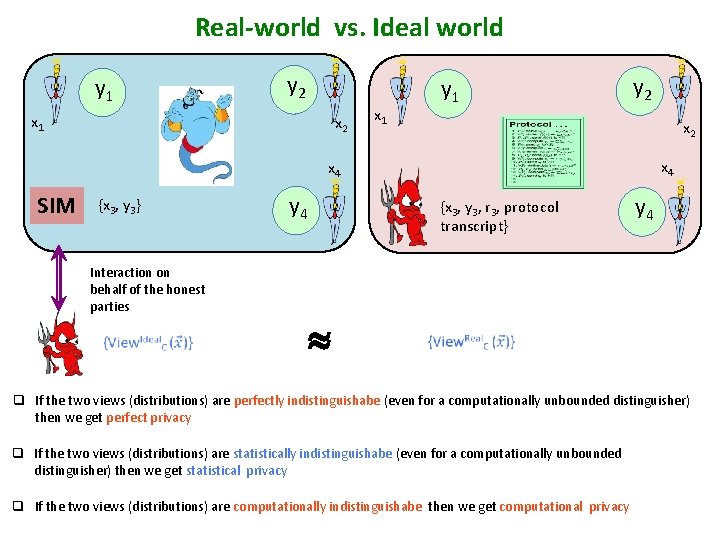
Real-world vs. Ideal world y 1 y 2 x 1 x 2 y 1 x 1 y 2 x 4 x 4 SIM {x 3, y 3} Interaction on behalf of the honest parties y 4 {x 3, y 3, r 3, protocol transcript} y 4 q If the two views (distributions) are perfectly indistinguishabe (even for a computationally unbounded distinguisher) then we get perfect privacy q If the two views (distributions) are statistically indistinguishabe (even for a computationally unbounded distinguisher) then we get statistical privacy q If the two views (distributions) are computationally indistinguishabe then we get computational privacy

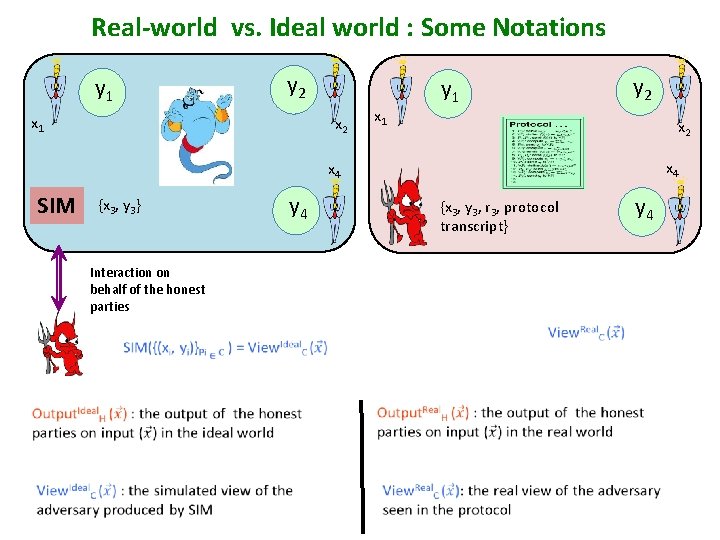
Real-world vs. Ideal world : Some Notations y 2 y 1 x 2 x 1 y 2 y 1 x 2 x 4 SIM {x 3, y 3} y 4 {x 3, y 3, r 3, protocol transcript} Interaction on behalf of the honest parties y 4

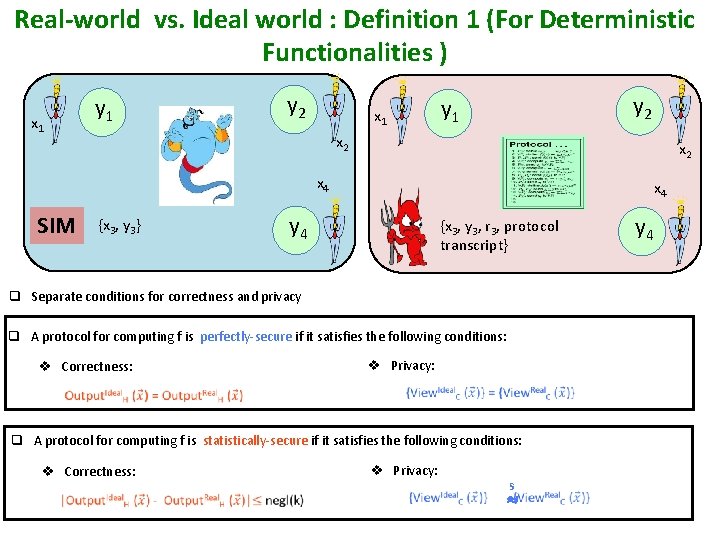
Real-world vs. Ideal world : Definition 1 (For Deterministic Functionalities ) y 1 x 1 y 2 y 1 x 2 x 4 SIM {x 3, y 3} x 4 y 4 {x 3, y 3, r 3, protocol transcript} q Separate conditions for correctness and privacy q A protocol for computing f is perfectly-secure if it satisfies the following conditions: v Correctness: v Privacy: q A protocol for computing f is statistically-secure if it satisfies the following conditions: v Correctness: v Privacy: s y 4

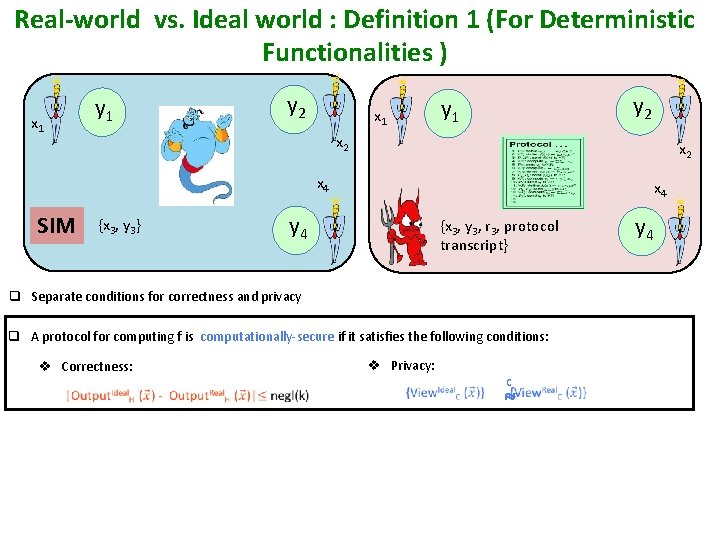
Real-world vs. Ideal world : Definition 1 (For Deterministic Functionalities ) y 1 x 1 y 2 y 1 x 2 x 4 SIM {x 3, y 3} x 4 y 4 {x 3, y 3, r 3, protocol transcript} q Separate conditions for correctness and privacy q A protocol for computing f is computationally-secure if it satisfies the following conditions: v Correctness: v Privacy: c y 4

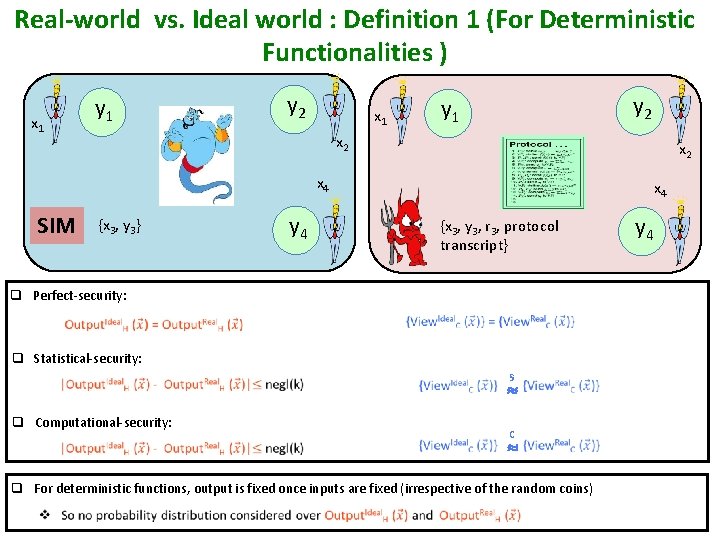
Real-world vs. Ideal world : Definition 1 (For Deterministic Functionalities ) y 1 x 1 y 2 y 1 x 2 x 4 SIM {x 3, y 3} x 4 y 4 {x 3, y 3, r 3, protocol transcript} q Perfect-security: q Statistical-security: q Computational-security: s c q For deterministic functions, output is fixed once inputs are fixed (irrespective of the random coins) y 4

Making “Very Small/Negligible” Precise– Asymptotic Approach >> “ Very Small / negligible in n” means those f(n) : - for every polynomial in n, p(n), there exists some positive integer N, such that f(n) < 1/p(n) , for all n > N - “grows slower than any inverse poly” >> Example: 1/2 n , 1/2 n/2 >> How about 1/n 10 ? For 1/n 20 n: Security A parameter. ter e m a r a p le tunab how that tunes is<to 1/n 20 it 10 icult 1/n there is NOd. N iffs. t. break a m cryptosyste - The more the value of n, the tougher the life of the adversary is.

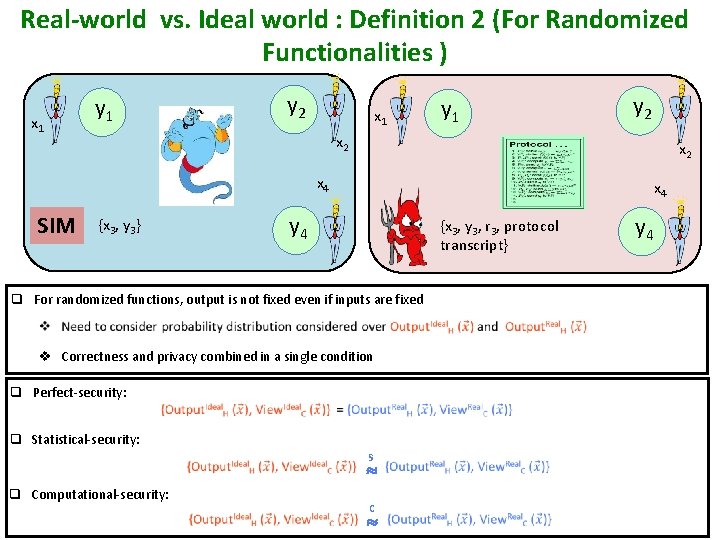
Real-world vs. Ideal world : Definition 2 (For Randomized Functionalities ) x 1 y 2 y 1 x 1 y 2 x 2 x 4 SIM x 4 y 4 {x 3, y 3} {x 3, y 3, r 3, protocol transcript} q For randomized functions, output is not fixed even if inputs are fixed v Correctness and privacy combined in a single condition q Perfect-security: q Statistical-security: s q Computational-security: c y 4

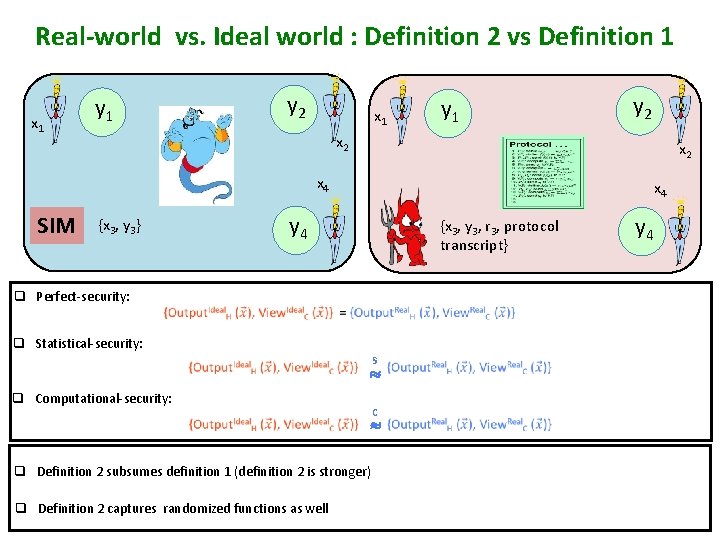
Real-world vs. Ideal world : Definition 2 vs Definition 1 x 1 y 2 y 1 x 1 y 2 x 2 x 4 SIM y 4 {x 3, y 3} q Perfect-security: x 4 {x 3, y 3, r 3, protocol transcript} q Statistical-security: s q Computational-security: q Definition 2 subsumes definition 1 (definition 2 is stronger) q Definition 2 captures randomized functions as well c y 4

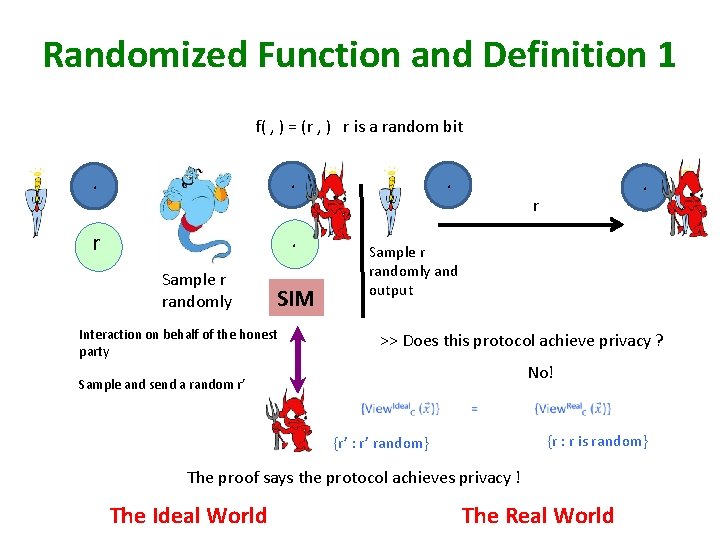
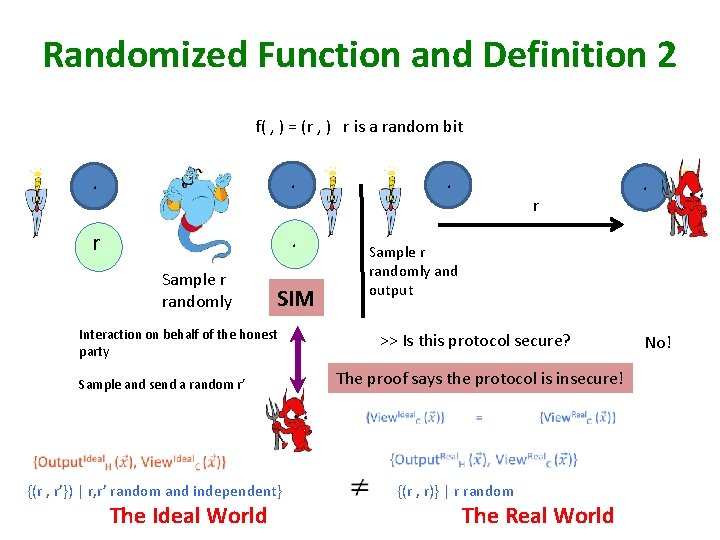
Randomized Function and Definition 1 f( , ) = (r , ) r is a random bit . . r Sample r randomly and output SIM Interaction on behalf of the honest party >> Does this protocol achieve privacy ? No! Sample and send a random r’ {r : r is random} {r’ : r’ random} The proof says the protocol achieves privacy ! The Ideal World The Real World

Randomized Function and Definition 2 f( , ) = (r , ) r is a random bit . . r . . r Sample r randomly and output SIM Interaction on behalf of the honest party Sample and send a random r’ >> Is this protocol secure? The proof says the protocol is insecure! {(r , r’}) | r, r’ random and independent} The Ideal World . {(r , r)} | r random The Real World No!

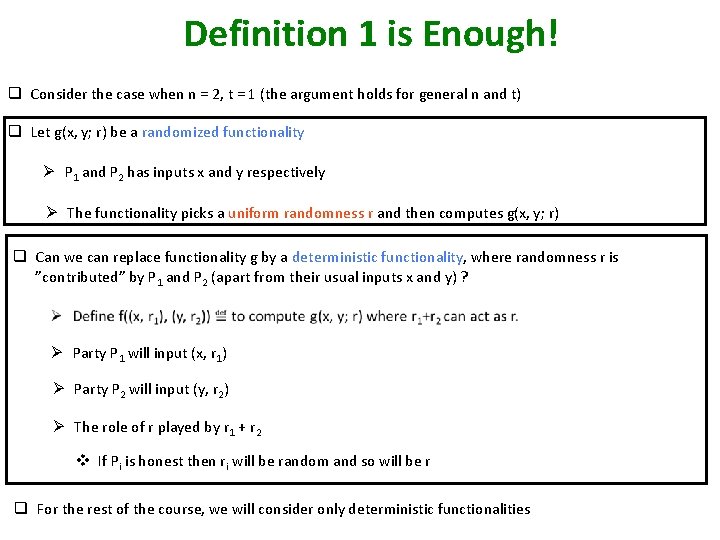
Definition 1 is Enough! q Consider the case when n = 2, t = 1 (the argument holds for general n and t) q Let g(x, y; r) be a randomized functionality Ø P 1 and P 2 has inputs x and y respectively Ø The functionality picks a uniform randomness r and then computes g(x, y; r) q Can we can replace functionality g by a deterministic functionality, where randomness r is ”contributed” by P 1 and P 2 (apart from their usual inputs x and y) ? Ø Party P 1 will input (x, r 1) Ø Party P 2 will input (y, r 2) Ø The role of r played by r 1 + r 2 v If Pi is honest then ri will be random and so will be r q For the rest of the course, we will consider only deterministic functionalities

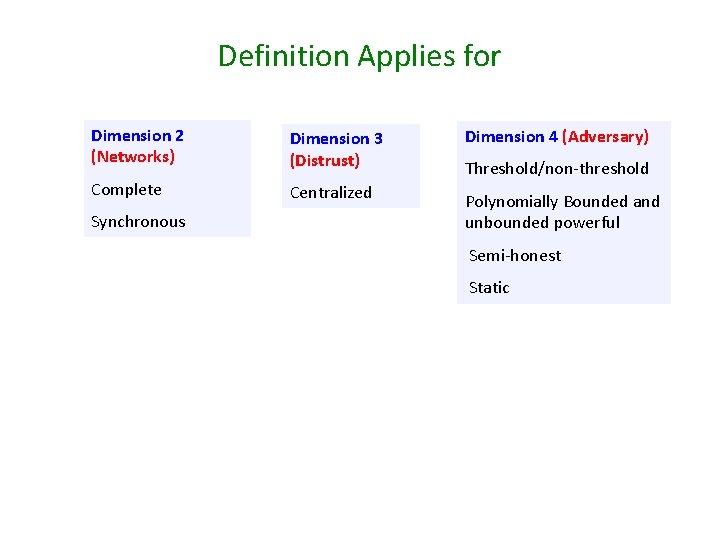
Definition Applies for Dimension 2 (Networks) Dimension 3 (Distrust) Dimension 4 (Adversary) Complete Centralized Polynomially Bounded and unbounded powerful Synchronous Threshold/non-threshold Semi-honest Static

 Arpita choudhury age
Arpita choudhury age Recallcrypto.com
Recallcrypto.com Binary search in secure computation
Binary search in secure computation Compute
Compute Secure foundations
Secure foundations Era of quality at the akshaya patra foundation
Era of quality at the akshaya patra foundation Cipher patra
Cipher patra Cipher patra
Cipher patra Sudhakar patra
Sudhakar patra Akshaya patra donation online
Akshaya patra donation online Sudhakar patra
Sudhakar patra Mechové patro
Mechové patro Goutam patra
Goutam patra Rostlinná patra
Rostlinná patra Pragyapan patra nepal
Pragyapan patra nepal Fertilizer computation examples
Fertilizer computation examples Diagonalization method in theory of computation
Diagonalization method in theory of computation Pda
Pda The purpose of computing is insight not numbers meaning
The purpose of computing is insight not numbers meaning The pagerank citation ranking: bringing order to the web
The pagerank citation ranking: bringing order to the web