Cryptography Lecture 9 Arpita Patra Arpita Patra Recall







- Slides: 22

Cryptography Lecture 9 Arpita Patra © Arpita Patra

Recall >> cpa-security to cca-security o Padding Oracle Attack on CBC mode o Attack on cpa-secure scheme from PRF >> MAC o Definitions- cma, scma, cmva, scmva

Today’s Goal - Recall of security definitions of MAC - Construction from PRF - Domain Extension: How to find a tag for long message o CBC-MAC - Authenticated Encryption (AE)- message privacy + integrity o Definition o Any AE is cca-secure. Stronger than cca-security. Nontrivial proof o Construction of AE from- cpa-secure SKE + cma-secure MAC

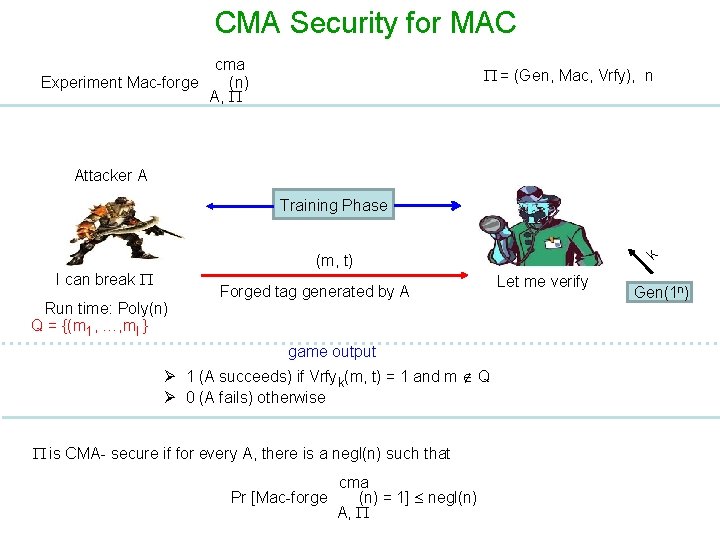
Security for MAC - - Randomized PPT Chosen Message Attack (CMA) Randomized PPT Chosen Message and Verification Attack (CMVA) It is not possible to come up with (m, t) if no tag on m is seen before It is not possible to come up with (m, t) if (m, t) has not been seen before.

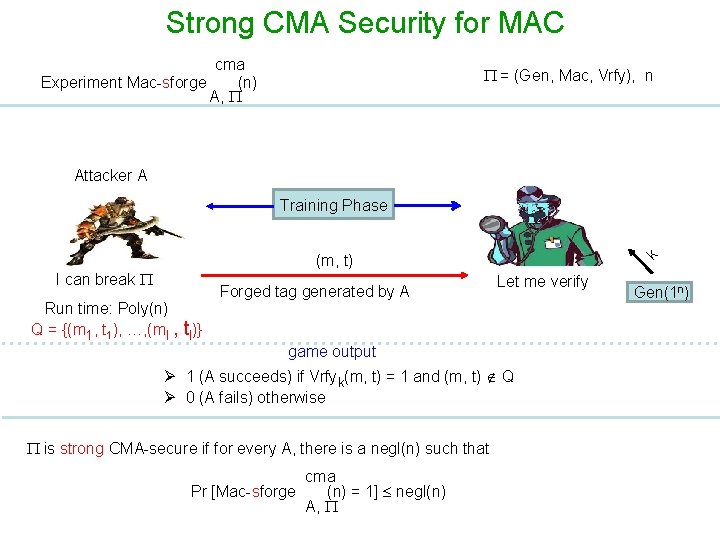
CMA Security for MAC cma Experiment Mac-forge (n) A, = (Gen, Mac, Vrfy), n Attacker A Training Phase I can break Run time: Poly(n) Q = {(m 1, …, ml } Forged tag generated by A game output Ø 1 (A succeeds) if Vrfyk(m, t) = 1 and m Q Ø 0 (A fails) otherwise is CMA- secure if for every A, there is a negl(n) such that cma Pr [Mac-forge (n) = 1] negl(n) A, k (m, t) Let me verify Gen(1 n)

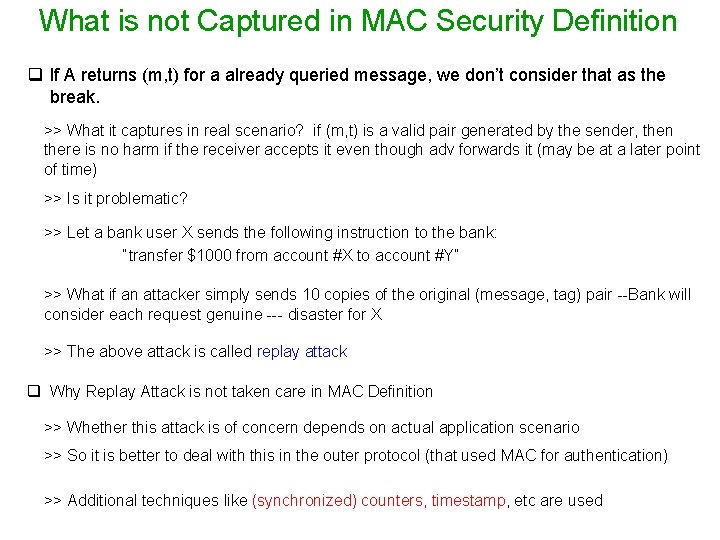
Strong CMA Security for MAC cma Experiment Mac-sforge (n) A, = (Gen, Mac, Vrfy), n Attacker A Training Phase I can break Run time: Poly(n) Q = {(m 1, t 1), …, (ml , tl)} Forged tag generated by A k (m, t) Let me verify game output Ø 1 (A succeeds) if Vrfyk(m, t) = 1 and (m, t) Q Ø 0 (A fails) otherwise is strong CMA-secure if for every A, there is a negl(n) such that cma Pr [Mac-sforge (n) = 1] negl(n) A, Gen(1 n)

What is not Captured in MAC Security Definition q If A returns (m, t) for a already queried message, we don’t consider that as the break. >> What it captures in real scenario? if (m, t) is a valid pair generated by the sender, then there is no harm if the receiver accepts it even though adv forwards it (may be at a later point of time) >> Is it problematic? >> Let a bank user X sends the following instruction to the bank: “transfer $1000 from account #X to account #Y“ >> What if an attacker simply sends 10 copies of the original (message, tag) pair --Bank will consider each request genuine --- disaster for X >> The above attack is called replay attack q Why Replay Attack is not taken care in MAC Definition >> Whether this attack is of concern depends on actual application scenario >> So it is better to deal with this in the outer protocol (that used MAC for authentication) >> Additional techniques like (synchronized) counters, timestamp, etc are used

Fixed-length MAC from PRF q Let F: {0, 1}n x {0, 1}n be a PRF Then = (Gen, Mac, Vrfy) is a fixed-length MAC for n-bit strings where : k 1 n Gen k R {0, 1}n m {0, 1}n Mac k t: = Fk(m) m, t Vrfy 0, if t Fk(m) 1, if t = Fk(m) (Deterministic Mac) Theorem: If F is a PRF then is a cma-secure MAC. Ø Show that if is not cma-secure then F is not a PRF by designing a distinguisher for F Ø If instead a TRF f was used to compute tag then an attacker can guess f(m) for a “new” m with probability at most 2 -n Ø The same should hold even if a PRF is used (as key is unknown)

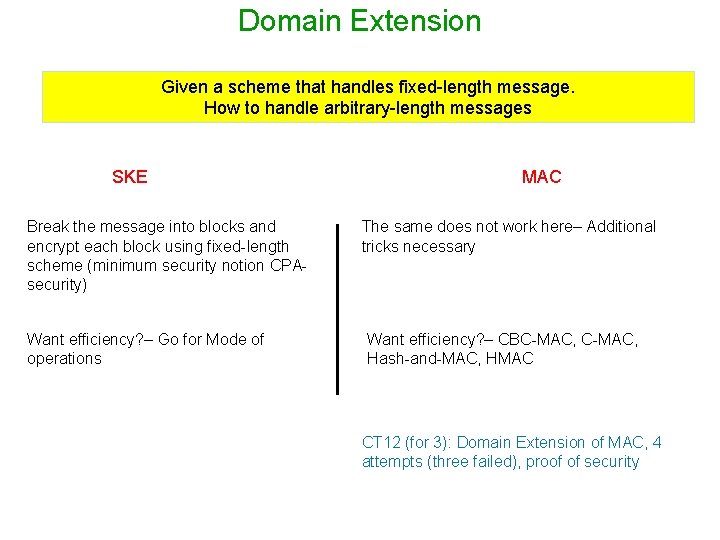
Domain Extension Given a scheme that handles fixed-length message. How to handle arbitrary-length messages SKE Break the message into blocks and encrypt each block using fixed-length scheme (minimum security notion CPAsecurity) Want efficiency? – Go for Mode of operations MAC The same does not work here– Additional tricks necessary Want efficiency? – CBC-MAC, Hash-and-MAC, HMAC CT 12 (for 3): Domain Extension of MAC, 4 attempts (three failed), proof of security

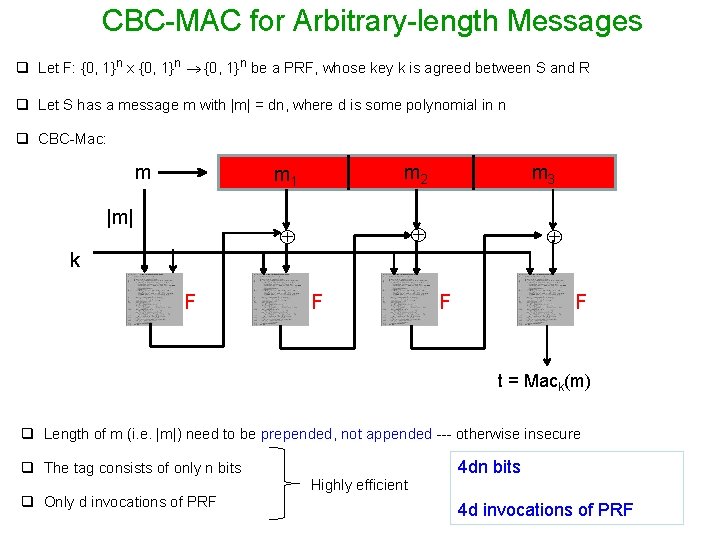
CBC-MAC for Arbitrary-length Messages q Let F: {0, 1}n x {0, 1}n be a PRF, whose key k is agreed between S and R q Let S has a message m with |m| = dn, where d is some polynomial in n q CBC-Mac: m |m| m 1 m 2 m 3 k F F t = Mack(m) q Length of m (i. e. |m|) need to be prepended, not appended --- otherwise insecure q The tag consists of only n bits q Only d invocations of PRF Highly efficient 4 dn bits 4 d invocations of PRF

Information-theoretic MAC CT 13 (for 3): Definition (restriction on key usage/one-time) Construction from Universal Function Proof of security CT 14 (for 1): Limitations of i. t MAC

The Picture Till Now SKE MAC q Privacy q Integrity & Authentication q Not necessarily provide integrity and authentication; q Not necessarily provide privacy; >> easy to come of with a valid ciphertext >> easy to manipulate known ciphertext >> Easy to distinguish tags of two different messag Authenticated Encryption Jonathan Katz, Moti Yung: Unforgeable Encryption and Chosen Ciphertext Secure Modes of Operation. FSE 2000: 284 -299 Mihir Bellare, Chanathip Nampre: Authenticated Encryption: Relations among Notions and Analysis of the Generic Composition Paradigm. ASIACRYPT 2000: 531 -545

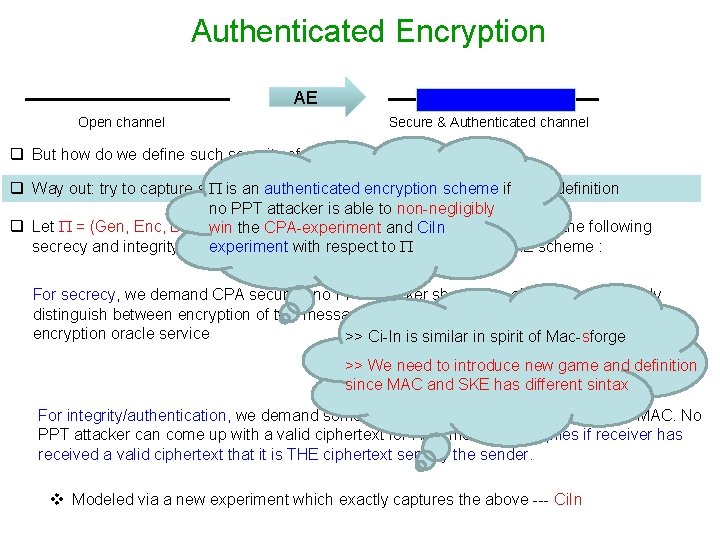
Authenticated Encryption AE Open channel Secure & Authenticated channel q But how do we define such security of such a primitive ? q Way out: try to capture secrecy authenticity/integrity is anand authenticated encryptionseparately scheme if in the definition no PPT attacker is able to non-negligibly q Let = (Gen, Enc, Dec) be symmetric-key cipher. Intuitively we demand the following winathe CPA-experiment and Ci. In secrecy and integrity property to be satisfied by toto qualify it as an AE scheme : experiment with respect For secrecy, we demand CPA security: no PPT attacker should be able to non-negligibly distinguish between encryption of two messages of its choice, even if it has access to encryption oracle service >> Ci-In is similar in spirit of Mac-sforge >> We need to introduce new game and definition since MAC and SKE has different sintax For integrity/authentication, we demand something similar to strong cma-security for MAC. No PPT attacker can come up with a valid ciphertext for ANY message). Implies if receiver has received a valid ciphertext that it is THE ciphertext sent by the sender. v Modeled via a new experiment which exactly captures the above --- Ci. In

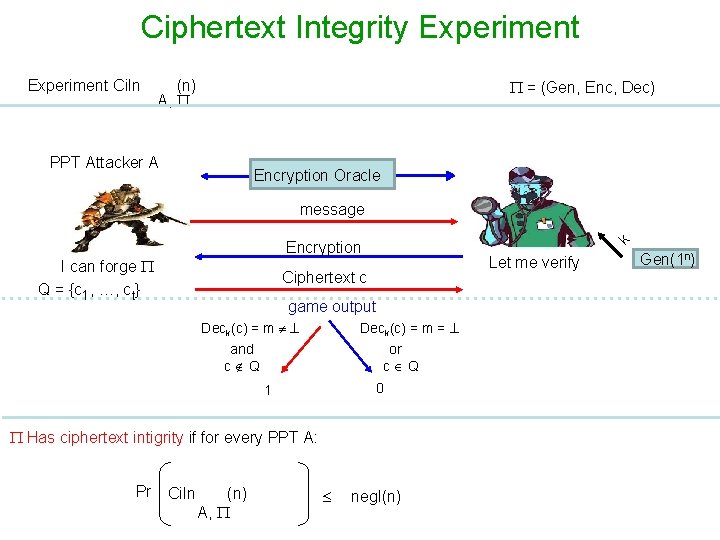
Ciphertext Integrity Experiment Ci. In (n) A, = (Gen, Enc, Dec) PPT Attacker A Encryption Oracle message I can forge Q = {c 1, …, ct} k Encryption Let me verify Ciphertext c game output Deck(c) = m = and c Q or c Q 0 1 Has ciphertext intigrity if for every PPT A: Pr Ci. In (n) A, negl(n) Gen(1 n)

Ingredients for Authenticated Encryption >> cpa-secure SKE >> scma-secure MAC >> How to combine them– crux of AE

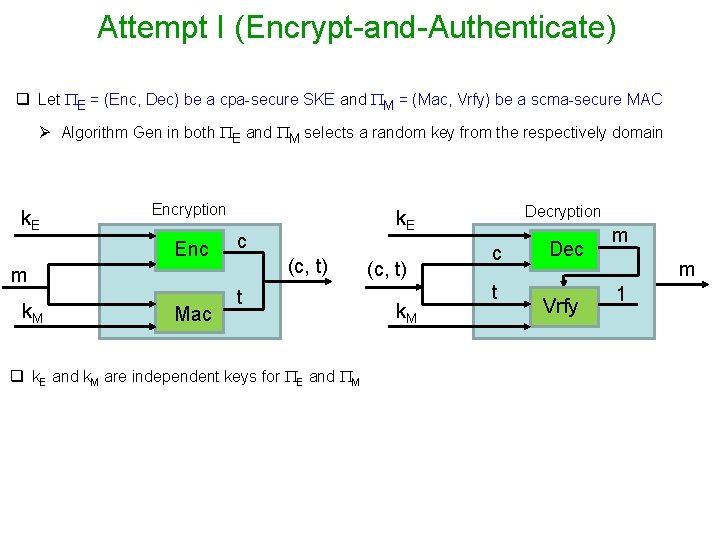
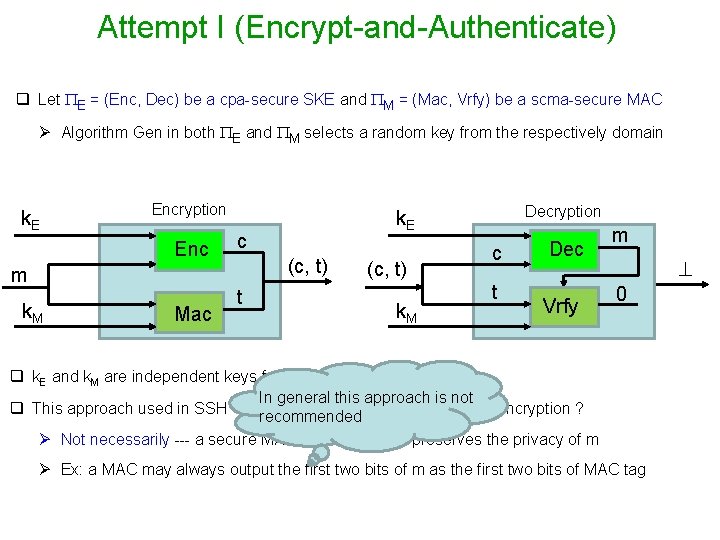
Attempt I (Encrypt-and-Authenticate) q Let E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E Encryption Enc c (c, t) m k. M Mac Decryption k. E t q k. E and k. M are independent keys for E and M (c, t) k. M c t Dec Vrfy m m 1

Attempt I (Encrypt-and-Authenticate) q Let E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E Encryption Enc c (c, t) m k. M Mac t Decryption k. E (c, t) k. M c t Dec Vrfy m 0 q k. E and k. M are independent keys for E and M In general this approach is not q This approach used in SSH --- does this guarantee authenticated encryption ? recommended Ø Not necessarily --- a secure MAC not necessarily preserves the privacy of m Ø Ex: a MAC may always output the first two bits of m as the first two bits of MAC tag

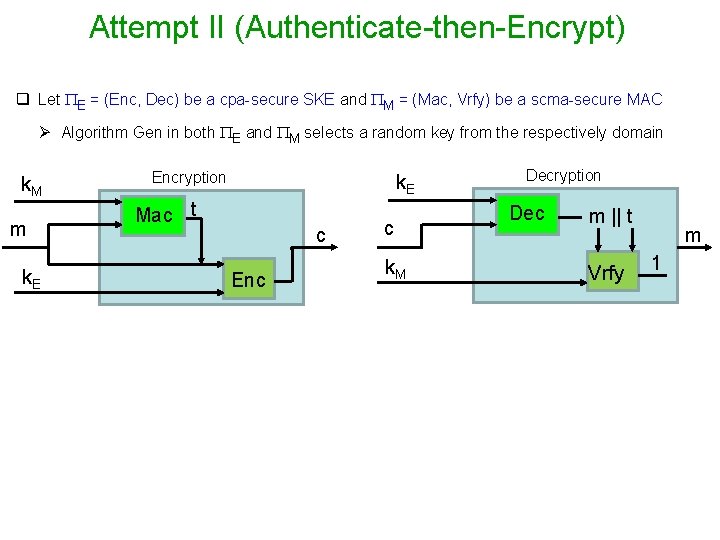
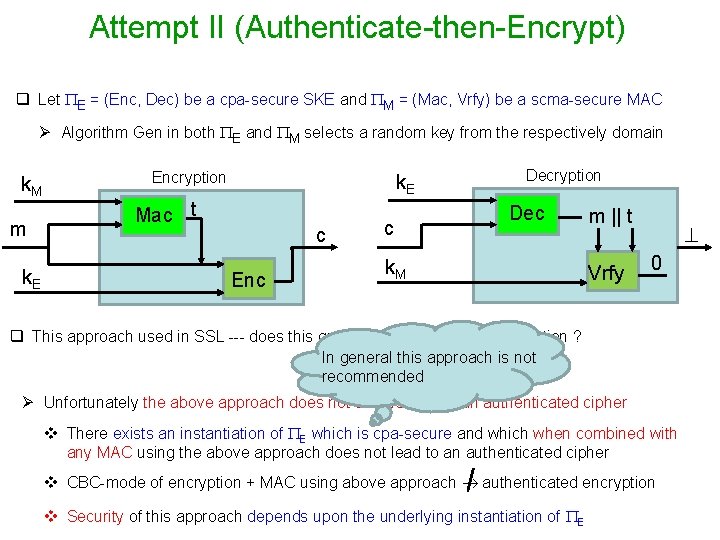
Attempt II (Authenticate-then-Encrypt) q Let E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. M m k. E Encryption k. E Mac t c Enc c k. M Decryption Dec m || t Vrfy m 1

Attempt II (Authenticate-then-Encrypt) q Let E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. M m k. E Encryption k. E Mac t c Enc c Decryption Dec k. M m || t Vrfy 0 q This approach used in SSL --- does this guarantee authenticated encryption ? In general this approach is not recommended Ø Unfortunately the above approach does not always lead to an authenticated cipher v There exists an instantiation of E which is cpa-secure and which when combined with any MAC using the above approach does not lead to an authenticated cipher v CBC-mode of encryption + MAC using above approach authenticated encryption v Security of this approach depends upon the underlying instantiation of E

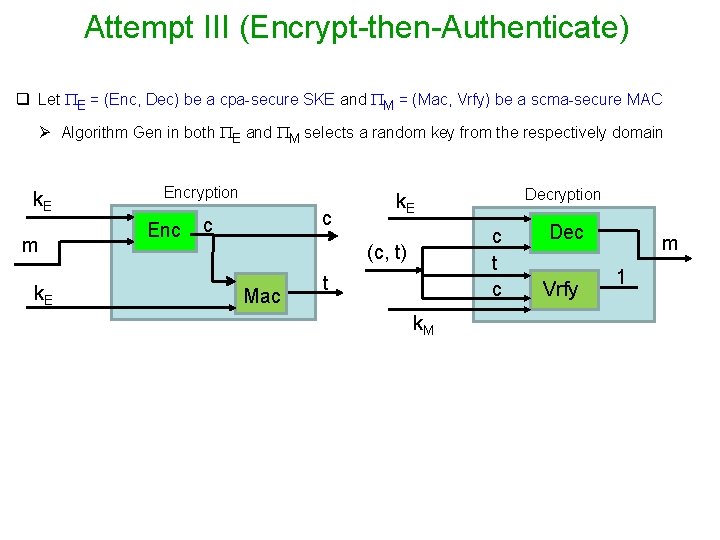
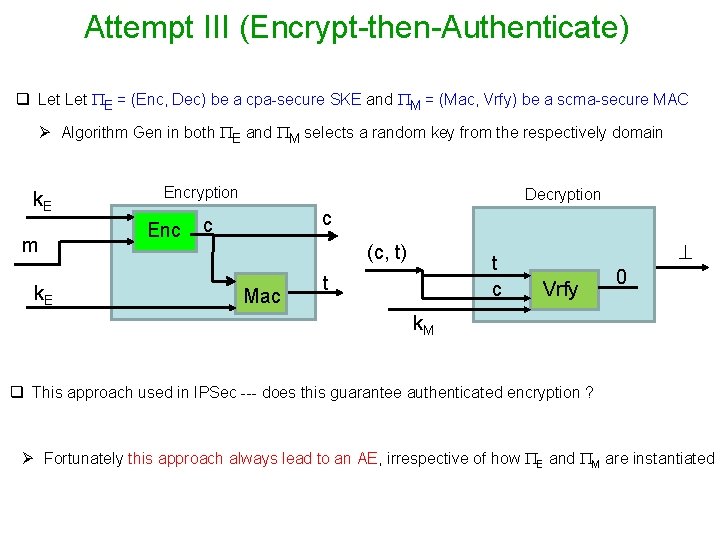
Attempt III (Encrypt-then-Authenticate) q Let E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E m k. E Encryption Enc c t c (c, t) Mac Decryption k. E t k. M Dec Vrfy m 1

Attempt III (Encrypt-then-Authenticate) q Let E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC Ø Algorithm Gen in both E and M selects a random key from the respectively domain k. E m k. E Encryption Enc Decryption c c (c, t) Mac t Vrfy 0 k. M q This approach used in IPSec --- does this guarantee authenticated encryption ? Ø Fortunately this approach always lead to an AE, irrespective of how E and M are instantiated

 Arpita patra iisc
Arpita patra iisc Cipher patra
Cipher patra 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Cipher patra
Cipher patra Cipher patra
Cipher patra Sudhakar patra
Sudhakar patra Akshaya patra donation online
Akshaya patra donation online Sudhakar patra
Sudhakar patra Patra lesa
Patra lesa Goutam patra
Goutam patra Rostlinná patra
Rostlinná patra Pragyapan patra nepal
Pragyapan patra nepal Era of quality at the akshaya patra foundation
Era of quality at the akshaya patra foundation Difference between recall and recognition
Difference between recall and recognition Gianttoby
Gianttoby Wj iv word reading fluency description
Wj iv word reading fluency description Aviane recall
Aviane recall Concept map marketing
Concept map marketing Let us reflect
Let us reflect Recall coordinator
Recall coordinator Recall column
Recall column Tip of the tongue phenomenon
Tip of the tongue phenomenon Active recall
Active recall








































