Cryptography Lecture 12 Arpita Patra Arpita Patra Recall





- Slides: 18

Cryptography Lecture 12 Arpita Patra © Arpita Patra

Recall - Security definitions of MAC- cma, strong cma, cmva, strong cmva - Construction from PRF - Domain Extension: How to find a tag for long message o CBC-MAC - Authenticated Encryption (AE)- message privacy + integrity o Definition o Construction of AE from- cpa-secure SKE + scma-secure MAC

Today’s Goal - Authenticated Encryption (AE) o Construction of AE from- cpa-secure SKE + scma-secure MAC o Proof - Looking back and ahead

Authenticated Encryption = (Gen, Enc, Dec) is an authenticated encryption if - = (Gen, Enc, Dec) is cpa-secure AND - = (Gen, Enc, Dec) has ciphertext integrity (hard to come up with a ciphertext that has valid decryption even after sufficient training )

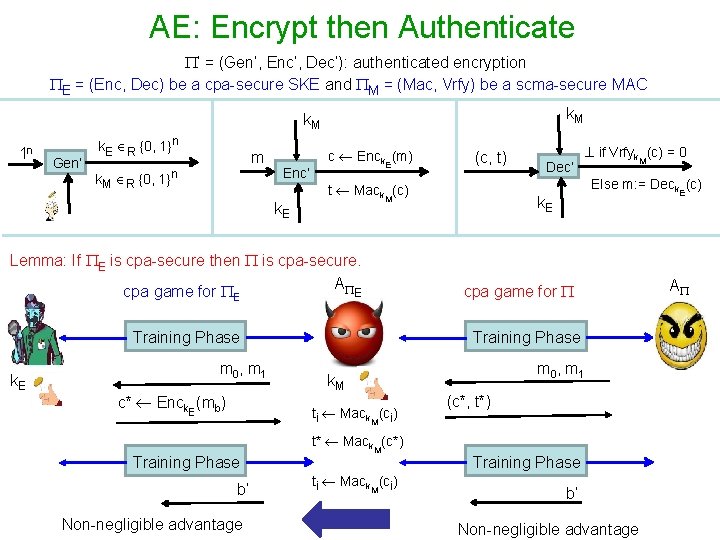
AE: Encrypt then Authenticate ’ = (Gen’, Enc’, Dec’): authenticated encryption E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC k. M 1 n Gen’ k. E R {0, 1}n m k. M R {0, 1}n Enc’ k. E c Enck (m) E t Mack (c) M Lemma: If E is cpa-secure then is cpa-secure. A cpa game for Training Phase m 0 , m 1 c* Enck. E(mb) Dec’ if Vrfyk (c) = 0 M Else m: = Deck (c) E k. E cpa game for E E k. E (c, t) Training Phase m 0 , m 1 k. M ti Mack (ci) M (c*, t*) t* Mack (c*) Training Phase b’ Non-negligible advantage M ti Mack (ci) M Training Phase b’ Non-negligible advantage A

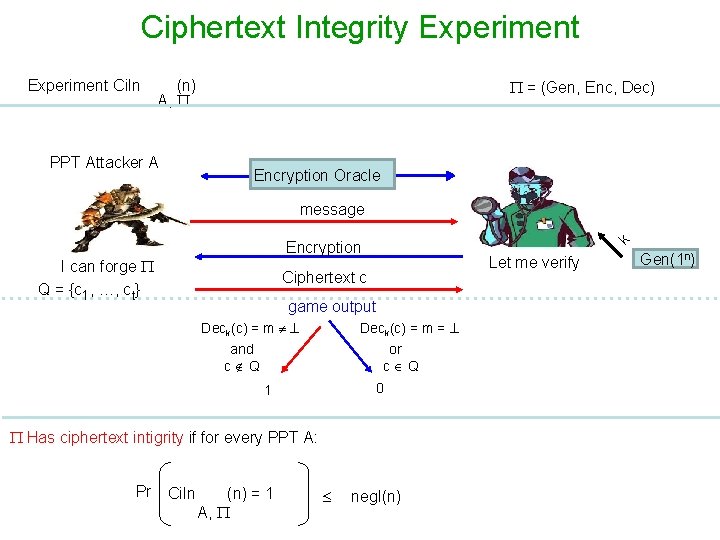
Ciphertext Integrity Experiment Ci. In (n) A, PPT Attacker A = (Gen, Enc, Dec) Encryption Oracle message I can forge Q = {c 1, …, ct} k Encryption Let me verify Ciphertext c game output Deck(c) = m = and c Q or c Q 0 1 Has ciphertext intigrity if for every PPT A: Pr Ci. In (n) = 1 A, negl(n) Gen(1 n)

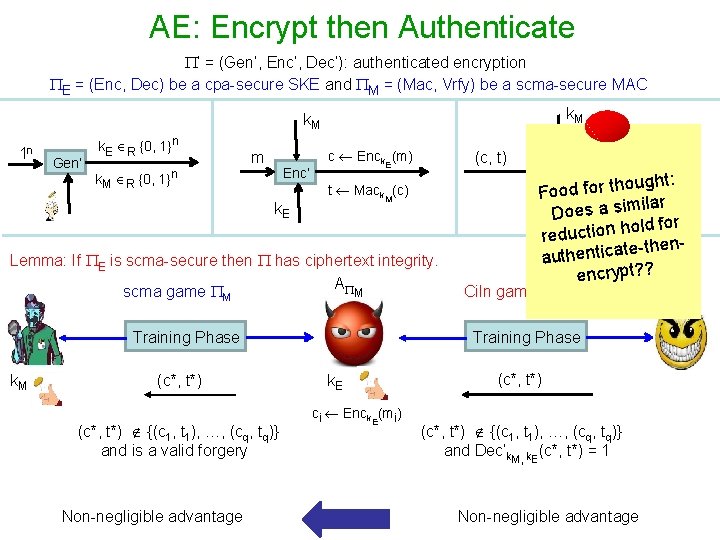
AE: Encrypt then Authenticate ’ = (Gen’, Enc’, Dec’): authenticated encryption E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC k. M 1 n Gen’ k. E R {0, 1}n m k. M R {0, 1}n Enc’ k. E c Enck (m) (c, t) E t Mack (c) M Lemma: If E is scma-secure then has ciphertext integrity. A scma game M M Training Phase k. M (c*, t*) {(c 1, t 1), …, (cq, tq)} and is a valid forgery Non-negligible advantage Dec’ if Vrfyk (c) = 0 M ht: k (c) ug. Dec Else m: = E ood for tho F r k. E ila Does a sim ld for o h n io t c u red te-thena ic t n e h t u a encrypt? ? Ci. In game for Training Phase k. E ci Enck (mi) E (c*, t*) {(c 1, t 1), …, (cq, tq)} and Dec’k. M, k. E(c*, t*) = 1 Non-negligible advantage A

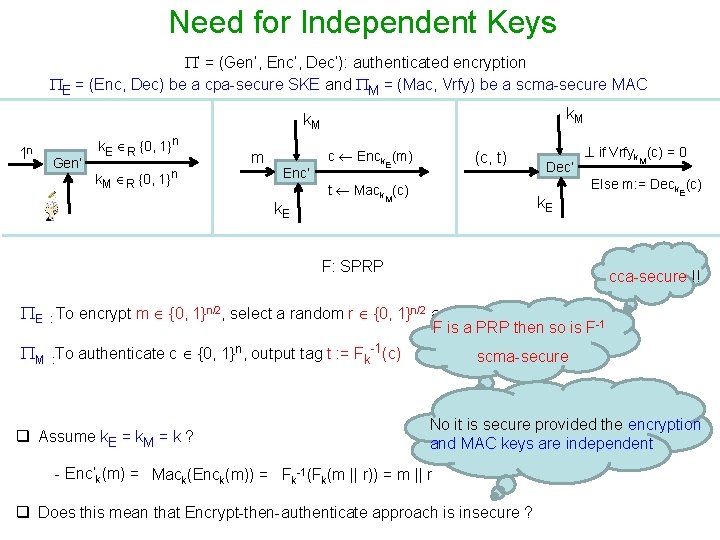
Need for Independent Keys ’ = (Gen’, Enc’, Dec’): authenticated encryption E = (Enc, Dec) be a cpa-secure SKE and M = (Mac, Vrfy) be a scma-secure MAC k. M 1 n Gen’ k. E R {0, 1}n k. M R {0, 1}n m Enc’ k. E c Enck (m) (c, t) E t Mack (c) M Dec’ k. E if Vrfyk (c) = 0 M Else m: = Deck (c) F: SPRP E cca-secure !! E : To encrypt m {0, 1}n/2, select a random r {0, 1}n/2 and output c Fk(m || r). F is a PRP then so is F-1 M : To authenticate c {0, 1}n, output tag t : = Fk-1(c) q Assume k. E = k. M = k ? scma-secure No it is secure provided the encryption and MAC keys are independent - Enc’k(m) = Mack(Enck(m)) = Fk-1(Fk(m || r)) = m || r q Does this mean that Encrypt-then-authenticate approach is insecure ?

Every AE is cca-secure Theorem: Every Authenticated Encryption is cca-secure Proof: On the board.

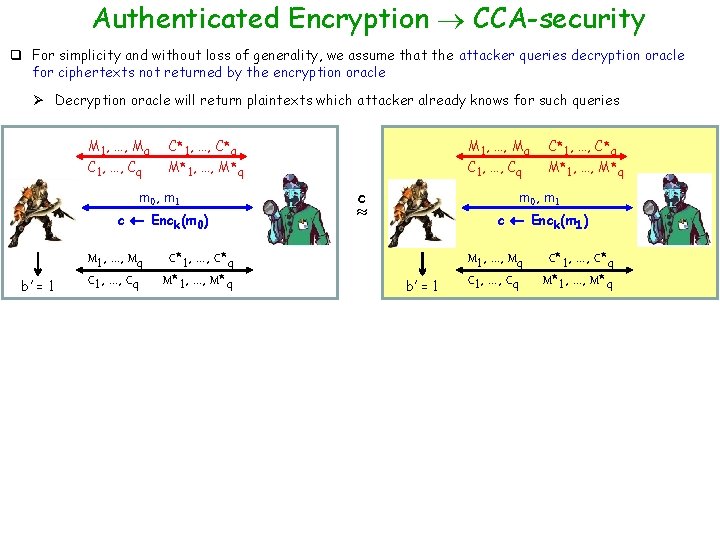
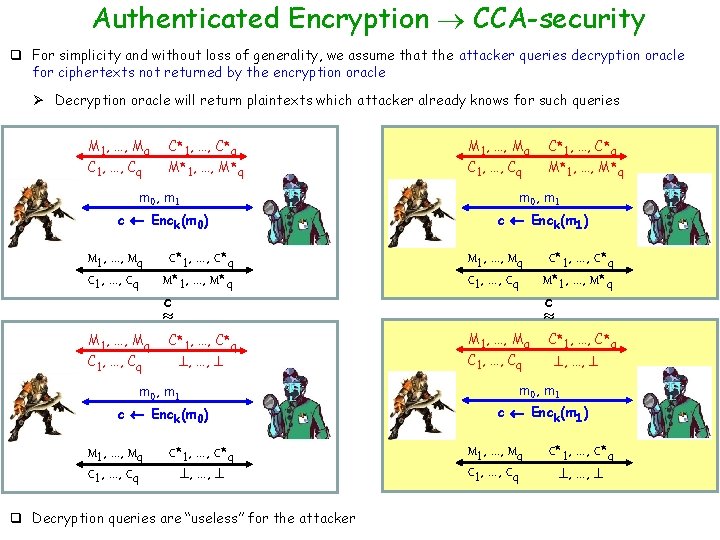
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) b’ = 1 M 1, …, Mq C 1, …, Cq M 1, …, Mq C*1, …, C*q M*1, …, M*q C 1, …, Cq c C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 1) b’ = 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q

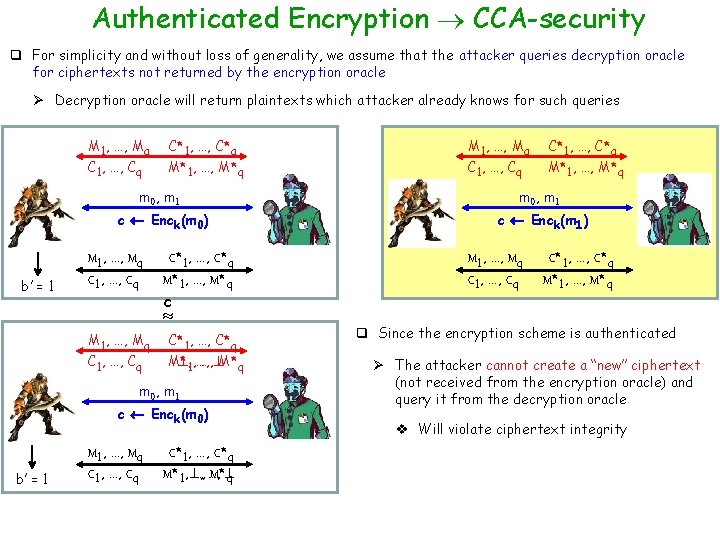
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq b’ = 1 C*1, …, C*q M*1, …, M*q C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q c M 1, …, Mq C 1, …, Cq C*1, …, C*q M* , 1, …, …, M*q m 0, m 1 c Enck(m 0) b’ = 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, , …, …, M* q M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q q Since the encryption scheme is authenticated Ø The attacker cannot create a “new” ciphertext (not received from the encryption oracle) and query it from the decryption oracle v Will violate ciphertext integrity

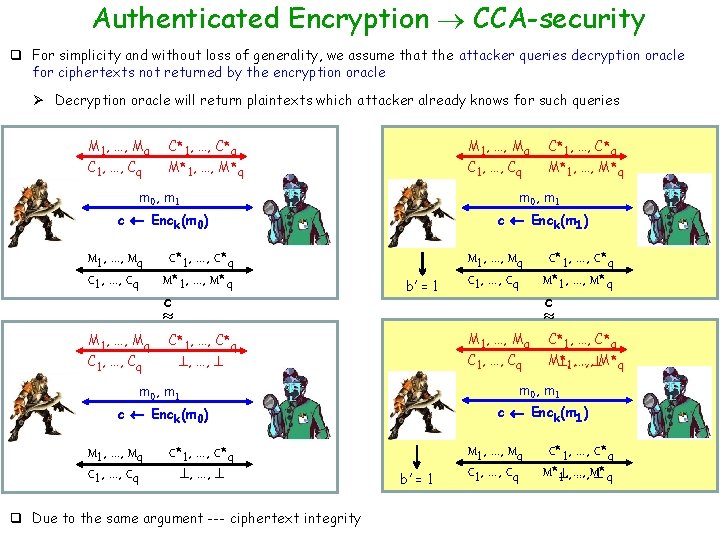
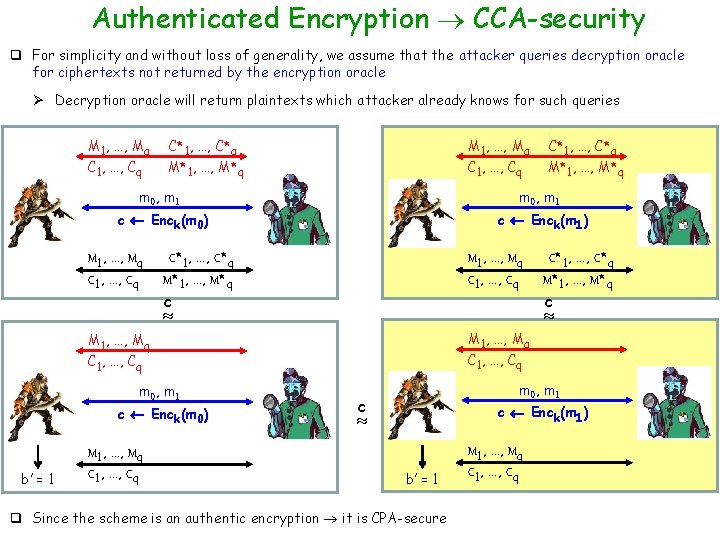
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M 1, …, Mq M*1, …, M*q C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q c b’ = 1 M 1, …, Mq C 1, …, Cq c M 1, …, Mq C*1, …, C*q C 1, …, Cq , …, q Due to the same argument --- ciphertext integrity M* …, M*q , 1, …, c Enck(m 1) c Enck(m 0) C*1, …, C*q , …, C*1, …, C*q m 0, m 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q b’ = 1 M 1, …, Mq C 1, …, Cq C*1, …, C*q M* , …, M* q 1, …,

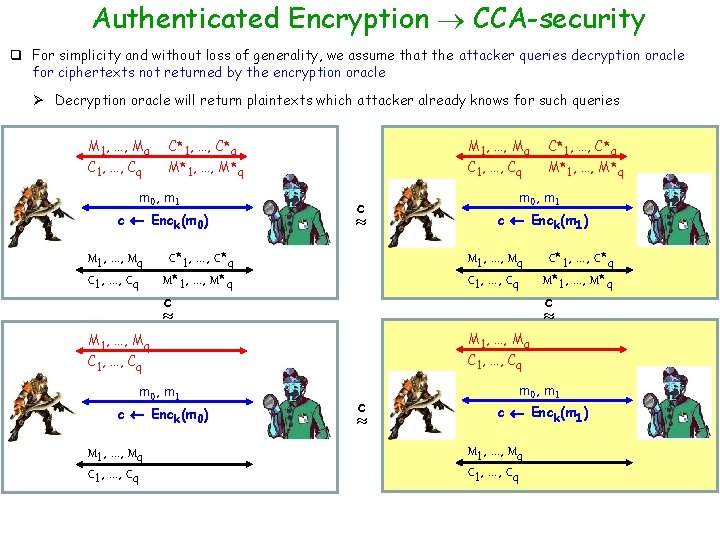
Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q c M 1, …, Mq C 1, …, Cq c C*1, …, C*q , …, m 0, m 1 c Enck(m 0) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q C*1, …, C*q , …, q Decryption queries are “useless” for the attacker M 1, …, Mq C 1, …, Cq C*1, …, C*q , …, m 0, m 1 c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q , …,

Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M 1, …, Mq M*1, …, M*q C 1, …, Cq M*1, …, M*q m 0, m 1 c Enck(m 0) c Enck(m 1) M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q M 1, …, Mq C 1, …, Cq c c Enck(m 0) M 1, …, Mq C 1, …, Cq c M 1, …, Mq C 1, …, Cq m 0, m 1 C*1, …, C*q M*1, …, M*q M 1, …, Mq b’ = 1 C*1, …, C*q m 0, m 1 c c Enck(m 1) b’ = 1 q Since the scheme is an authentic encryption it is CPA-secure M 1, …, Mq C 1, …, Cq

Authenticated Encryption CCA-security q For simplicity and without loss of generality, we assume that the attacker queries decryption oracle for ciphertexts not returned by the encryption oracle Ø Decryption oracle will return plaintexts which attacker already knows for such queries M 1, …, Mq C 1, …, Cq C*1, …, C*q M*1, …, M*q m 0, m 1 c Enck(m 0) M 1, …, Mq C 1, …, Cq c C*1, …, C*q M*1, …, M*q c Enck(m 1) M 1, …, Mq C 1, …, Cq c Enck(m 0) C*1, …, C*q M*1, …, M*q M 1, …, Mq m 0, m 1 M*1, …, M*q m 0, m 1 M 1, …, Mq C 1, …, Cq c C*1, …, C*q c m 0, m 1 c Enck(m 1) M 1, …, Mq C 1, …, Cq

CCA-security vs Authenticated Encryption q Every authenticated encryption scheme is also a cca-secure cipher Ø What about the converse ? Ø There are encryption schemes which are only cca-secure (Assignment problem) q Conceptually the goal of CCA-security and authenticated encryption are different Ø CCA-security : aim to achieve only privacy even if an attacker disrupts the communication Ø Authenticated encryption: aim is to achieve both privacy as well as integrity q Which is more efficient ? Ø In the symmetric-key world both are almost equivalent Ø No reason to just use a cca-secure scheme (instead of an authenticated encryption) if the major concern is efficiency Ø In the public-key world, the difference is more pronounced v Depending upon the application need to determine whether to go for CCA-security or authenticated encryption

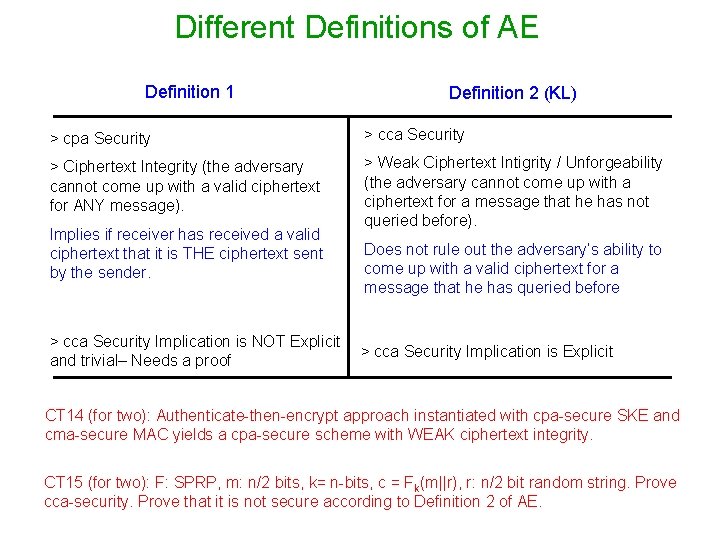
Different Definitions of AE Definition 1 Definition 2 (KL) > cpa Security > cca Security > Ciphertext Integrity (the adversary cannot come up with a valid ciphertext for ANY message). > Weak Ciphertext Intigrity / Unforgeability (the adversary cannot come up with a ciphertext for a message that he has not queried before). Implies if receiver has received a valid ciphertext that it is THE ciphertext sent by the sender. > cca Security Implication is NOT Explicit and trivial– Needs a proof Does not rule out the adversary’s ability to come up with a valid ciphertext for a message that he has queried before > cca Security Implication is Explicit CT 14 (for two): Authenticate-then-encrypt approach instantiated with cpa-secure SKE and cma-secure MAC yields a cpa-secure scheme with WEAK ciphertext integrity. CT 15 (for two): F: SPRP, m: n/2 bits, k= n-bits, c = Fk(m||r), r: n/2 bit random string. Prove cca-security. Prove that it is not secure according to Definition 2 of AE.

 Arpita patra iisc
Arpita patra iisc Recallcrypto com
Recallcrypto com 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Rostlinná patra
Rostlinná patra Pragyapan patra nepal
Pragyapan patra nepal Era of quality at the akshaya patra foundation
Era of quality at the akshaya patra foundation Cipher patra
Cipher patra Cipher patra
Cipher patra Sudhakar patra
Sudhakar patra Akshaya patra donation online
Akshaya patra donation online Sudhakar patra
Sudhakar patra Patra v lese
Patra v lese Goutam patra
Goutam patra 24 hodinový recall
24 hodinový recall Ido recall
Ido recall Toyota public relations crisis
Toyota public relations crisis Completion of the accounting cycle
Completion of the accounting cycle Recall vs recognition
Recall vs recognition What is feature article
What is feature article
































