CIT 480 Securing Computer Systems Passwords CIT 480













- Slides: 40

CIT 480: Securing Computer Systems Passwords CIT 480: Securing Computer Systems Slide #1

Topics 1. 2. 3. 4. 5. 6. 7. Password Systems Threat Models: Online, Offline, Side Channel Storing Passwords: Hashing and Salting Example Password Systems Password Selection Graphical Passwords One-Time Passwords Slide #2

Authentication System A: set of authentication information – information used by entities to prove identity C: set of complementary information – information stored by system to validate A F: set of complementation functions f : A → C – generate C from A L: set of authentication functions l: A C→{T, F} – verify identity S: set of selection functions – enable entity to create or alter A or C CIT 480: Securing Computer Systems Slide #3

Password System Example Authenticate with 8 -character alphanumeric password. System compares against stored cleartext password. A = [A-Za-z 0 -9]{8} C=A F={I} L={=} Security problem: a threat who gains access to password file knows password for every user. CIT 480: Securing Computer Systems Slide #4

Password Storage Solution: We should store complementary information instead of passwords, so threat doesn’t get every password by stealing one file. Idea #1: Encrypt passwords. – Encrypt passwords with secret key. – Store ciphertext. – Problem: what if attacker finds secret key? Idea #2: Hash passwords. – Store hash value of password. – No Problem: hashes can’t be turned back into passwords. Slide #5

Password System Example #2 Authenticate with 8 -character alphanumeric password. System compares with stored MD 5 hash of password. A = [A-Za-z 0 -9]{8} C = 128 -bit numbers F = { MD 5 } L = { MD 5(a)=c } CIT 480: Securing Computer Systems Slide #6

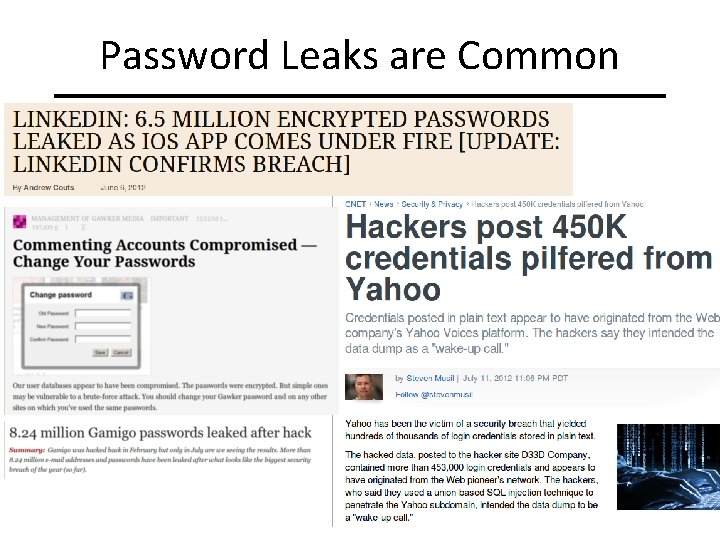
Password Leaks are Common Slide #7

Threat Models 1. Online Attacks – Threat has access to login user interface. – Attack is attempts to guess passwords using the normal UI (slow). 2. Offline Attacks – Threat has access to hashed passwords. – Attack is to guess words, hash words, then compare with hashed passwords (fast). 3. Side Channel Attacks – Threat has access to account management UI. – Attack by using password reset functionality. Slide #8

Online Password Cracking CIT 480: Securing Computer Systems

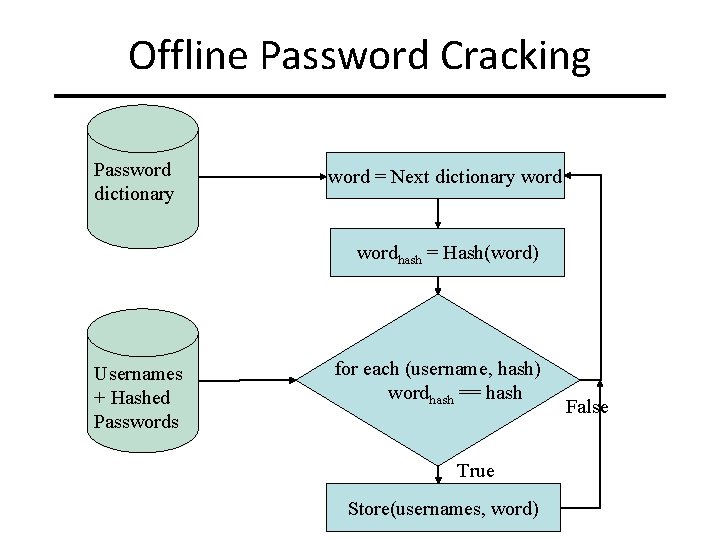
Offline Password Cracking Password dictionary word = Next dictionary wordhash = Hash(word) Usernames + Hashed Passwords for each (username, hash) wordhash == hash True Store(usernames, word) False

Side Channel Attacks Web sites will e-mail you password if you answer a simple “secret” question: 1. What is your favorite color? 2. What is your pet’s name? 3. What is your mother’s maiden name? Violation of fail-safe defaults Failover to less secure protocol. How many favorite colors are there? CIT 480: Securing Computer Systems Slide #11

Cracking Methods 1. List of candidate passwords 2. Permutation rules – Append or prepend symbols or numbers – Substitute numbers/symbols for letters – Change case, pluralize, reverse words, character shifts, joining words 3. Brute force – Try all possible passwords in length range – Only feasible for offline cracking of passwords less than 10 characters long. CIT 480: Securing Computer Systems Slide #12

Cracking Tools Online Tools – – Hydra Medusa NSE brute force scripts Brutus (Windows) Offline Tools – – John the Ripper ocl. Hashcat (GPU) Cain and Abel (Windows) Ophcrack (rainbow table) CIT 480: Securing Computer Systems Slide #13

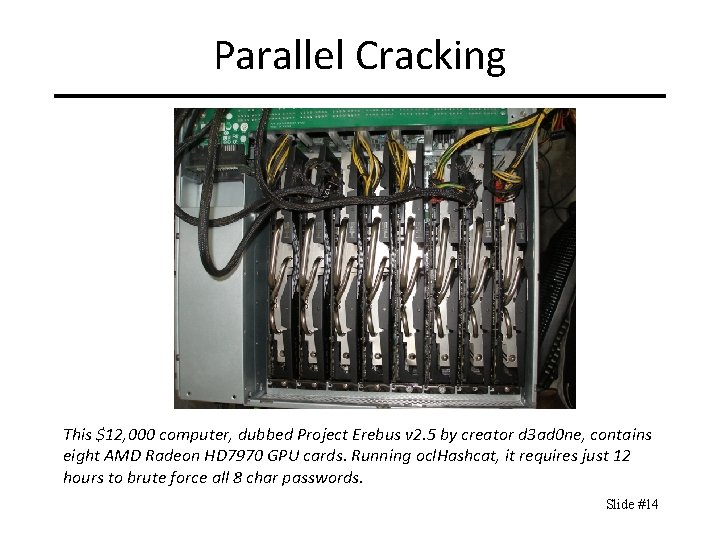
Parallel Cracking This $12, 000 computer, dubbed Project Erebus v 2. 5 by creator d 3 ad 0 ne, contains eight AMD Radeon HD 7970 GPU cards. Running ocl. Hashcat, it requires just 12 hours to brute force all 8 char passwords. Slide #14

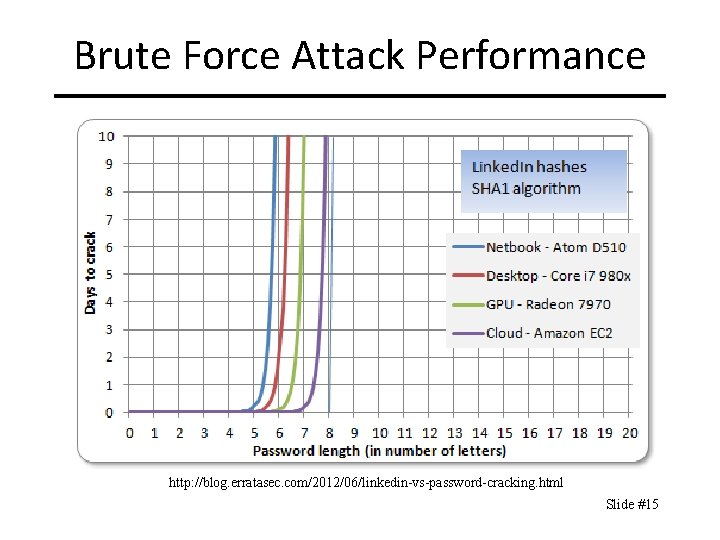
Brute Force Attack Performance http: //blog. erratasec. com/2012/06/linkedin-vs-password-cracking. html Slide #15

Countering Password Guessing Choose A, C, and F to select suitably low probability P(T) of guessing in time T. P(T) >= TG / N – G is number of guess per time unit T – T is number of time units in attack – N is number of possible passwords CIT 480: Securing Computer Systems Slide #16

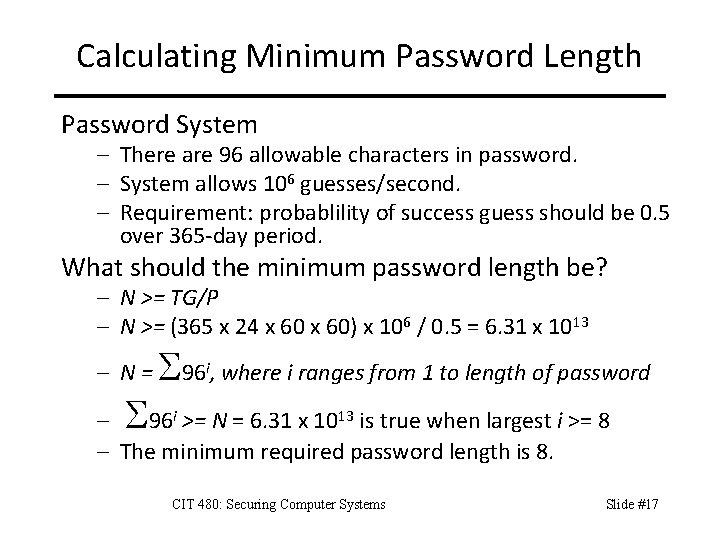
Calculating Minimum Password Length Password System – There are 96 allowable characters in password. – System allows 106 guesses/second. – Requirement: probablility of success guess should be 0. 5 over 365 -day period. What should the minimum password length be? – N >= TG/P – N >= (365 x 24 x 60) x 106 / 0. 5 = 6. 31 x 1013 – N= S S 96 , where i ranges from 1 to length of password i – 96 i >= N = 6. 31 x 1013 is true when largest i >= 8 – The minimum required password length is 8. CIT 480: Securing Computer Systems Slide #17

Password Aging Requirement that password be changed after a period of time or after an event has occurred If expected time to guess is 180 days, should change password more frequently than 180 days 1. If change time too short, users have difficulty recalling passwords. 2. Cannot allow users to change password to current one. 3. Also prevent users from changing passwords too soon. 4. Give notice of impending password change requirement. CIT 480: Securing Computer Systems Slide #18

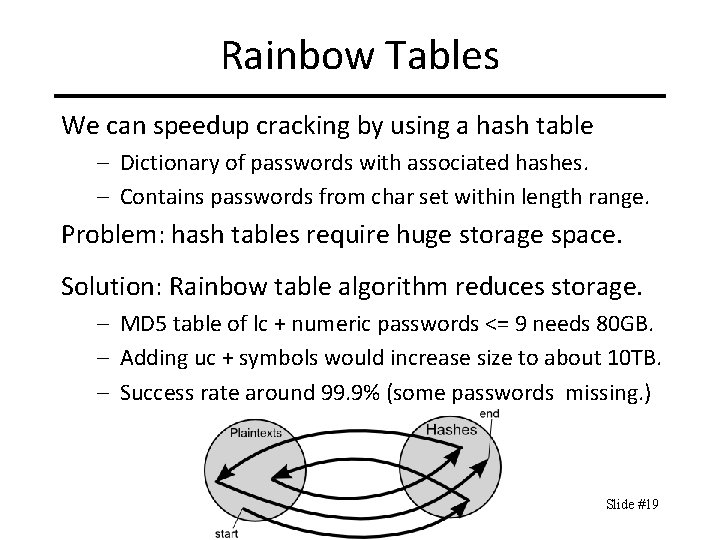
Rainbow Tables We can speedup cracking by using a hash table – Dictionary of passwords with associated hashes. – Contains passwords from char set within length range. Problem: hash tables require huge storage space. Solution: Rainbow table algorithm reduces storage. – MD 5 table of lc + numeric passwords <= 9 needs 80 GB. – Adding uc + symbols would increase size to about 10 TB. – Success rate around 99. 9% (some passwords missing. ) Slide #19

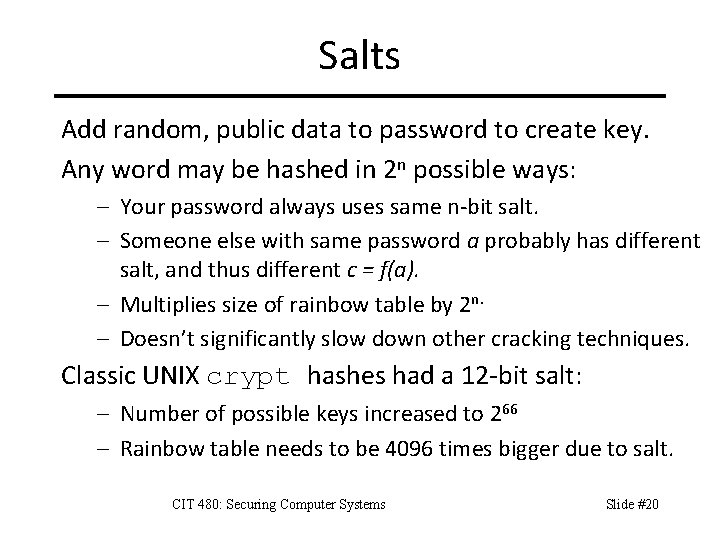
Salts Add random, public data to password to create key. Any word may be hashed in 2 n possible ways: – Your password always uses same n-bit salt. – Someone else with same password a probably has different salt, and thus different c = f(a). – Multiplies size of rainbow table by 2 n. – Doesn’t significantly slow down other cracking techniques. Classic UNIX crypt hashes had a 12 -bit salt: – Number of possible keys increased to 266 – Rainbow table needs to be 4096 times bigger due to salt. CIT 480: Securing Computer Systems Slide #20

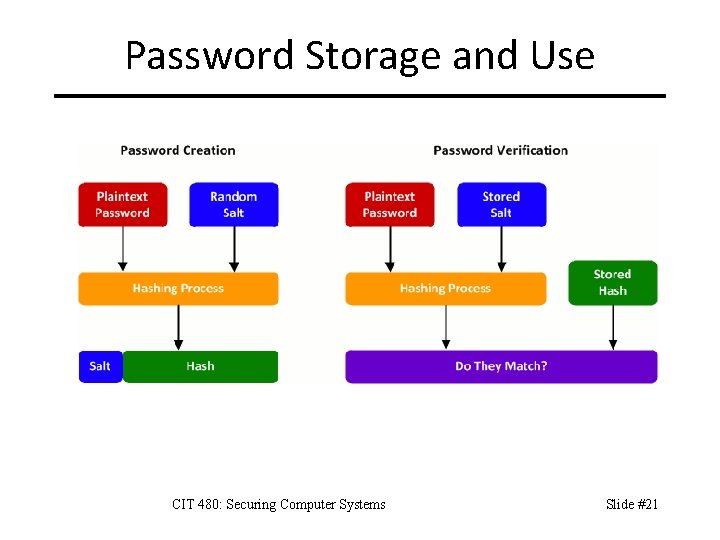
Password Storage and Use CIT 480: Securing Computer Systems Slide #21

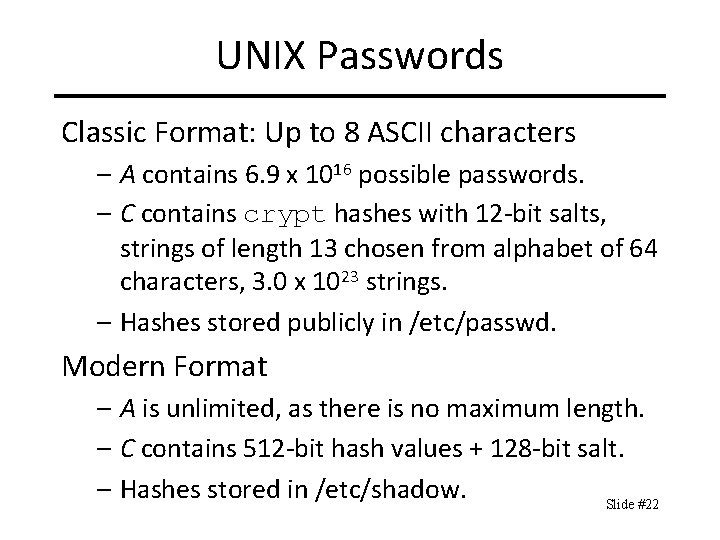
UNIX Passwords Classic Format: Up to 8 ASCII characters – A contains 6. 9 x 1016 possible passwords. – C contains crypt hashes with 12 -bit salts, strings of length 13 chosen from alphabet of 64 characters, 3. 0 x 1023 strings. – Hashes stored publicly in /etc/passwd. Modern Format – A is unlimited, as there is no maximum length. – C contains 512 -bit hash values + 128 -bit salt. – Hashes stored in /etc/shadow. Slide #22

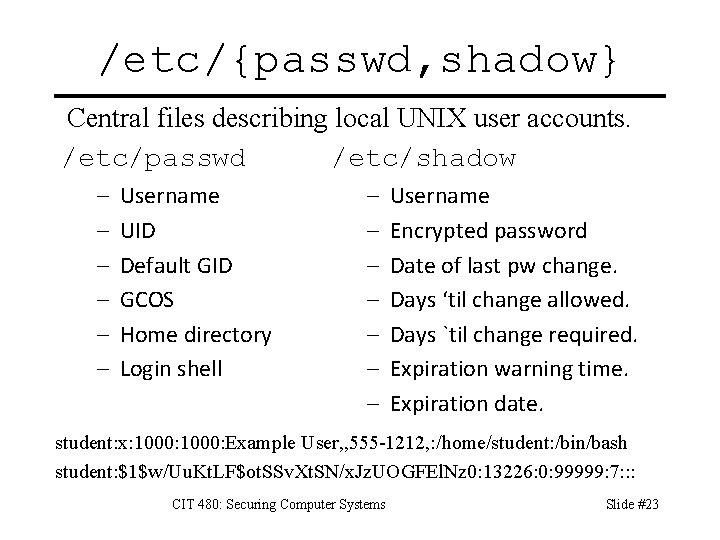
/etc/{passwd, shadow} Central files describing local UNIX user accounts. /etc/passwd /etc/shadow – – – Username UID Default GID GCOS Home directory Login shell – – – – Username Encrypted password Date of last pw change. Days ‘til change allowed. Days `til change required. Expiration warning time. Expiration date. student: x: 1000: Example User, , 555 -1212, : /home/student: /bin/bash student: $1$w/Uu. Kt. LF$ot. SSv. Xt. SN/x. Jz. UOGFEl. Nz 0: 13226: 0: 99999: 7: : : CIT 480: Securing Computer Systems Slide #23

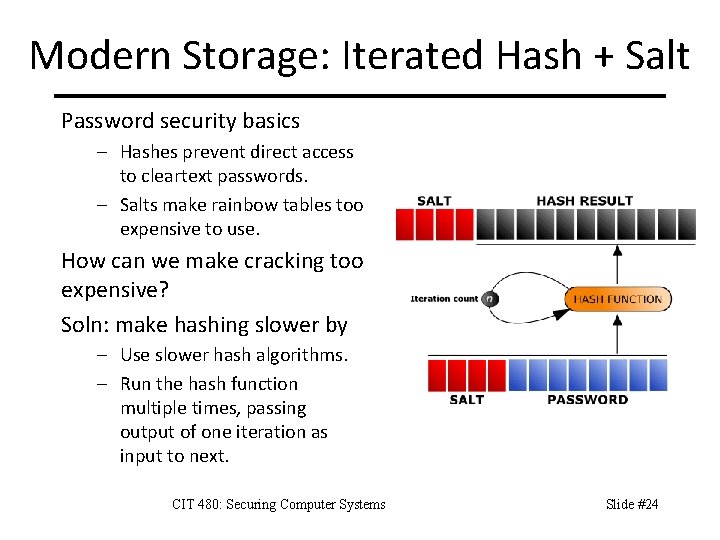
Modern Storage: Iterated Hash + Salt Password security basics – Hashes prevent direct access to cleartext passwords. – Salts make rainbow tables too expensive to use. How can we make cracking too expensive? Soln: make hashing slower by – Use slower hash algorithms. – Run the hash function multiple times, passing output of one iteration as input to next. CIT 480: Securing Computer Systems Slide #24

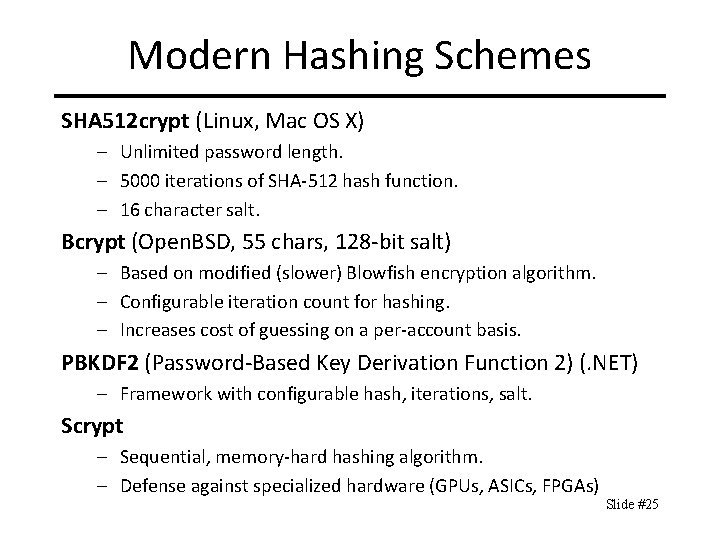
Modern Hashing Schemes SHA 512 crypt (Linux, Mac OS X) – Unlimited password length. – 5000 iterations of SHA-512 hash function. – 16 character salt. Bcrypt (Open. BSD, 55 chars, 128 -bit salt) – Based on modified (slower) Blowfish encryption algorithm. – Configurable iteration count for hashing. – Increases cost of guessing on a per-account basis. PBKDF 2 (Password-Based Key Derivation Function 2) (. NET) – Framework with configurable hash, iterations, salt. Scrypt – Sequential, memory-hard hashing algorithm. – Defense against specialized hardware (GPUs, ASICs, FPGAs) Slide #25

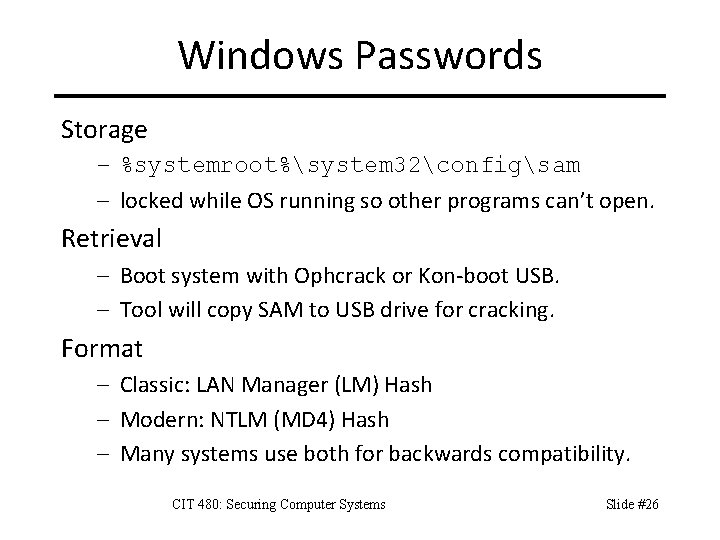
Windows Passwords Storage – %systemroot%system 32configsam – locked while OS running so other programs can’t open. Retrieval – Boot system with Ophcrack or Kon-boot USB. – Tool will copy SAM to USB drive for cracking. Format – Classic: LAN Manager (LM) Hash – Modern: NTLM (MD 4) Hash – Many systems use both for backwards compatibility. CIT 480: Securing Computer Systems Slide #26

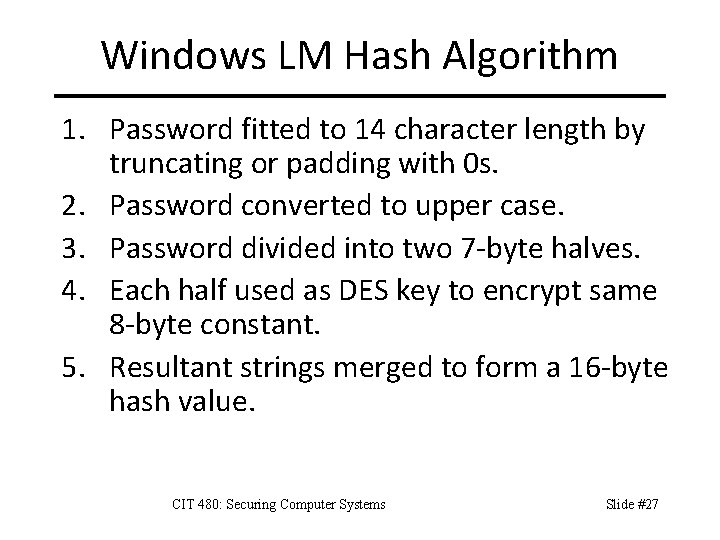
Windows LM Hash Algorithm 1. Password fitted to 14 character length by truncating or padding with 0 s. 2. Password converted to upper case. 3. Password divided into two 7 -byte halves. 4. Each half used as DES key to encrypt same 8 -byte constant. 5. Resultant strings merged to form a 16 -byte hash value. CIT 480: Securing Computer Systems Slide #27

Windows LM Hash Problems Last 8 bytes of c known if password < 7 chars. Dividing password into halves reducing problem of breaking 14 -character password to breaking two 7 character passwords. Conversion to upper case reduces character set. Dictionary of password hashes can be prebuilt – Number of possible passwords much smaller than DES space. – No salt is used. CIT 480: Securing Computer Systems Slide #28

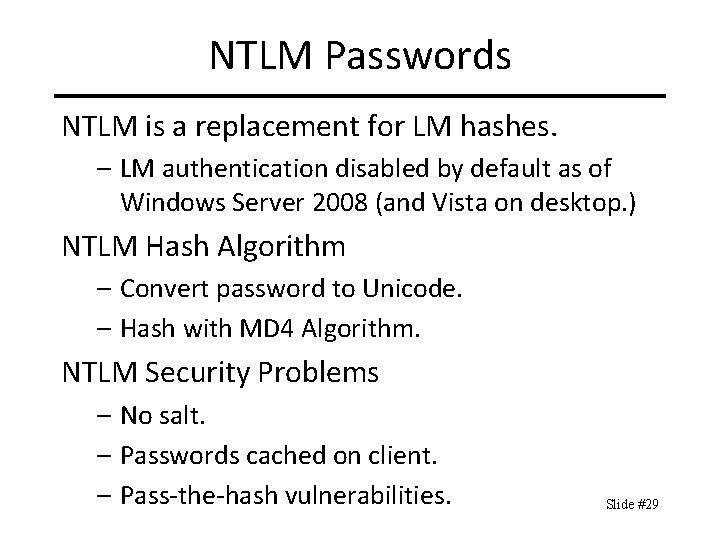
NTLM Passwords NTLM is a replacement for LM hashes. – LM authentication disabled by default as of Windows Server 2008 (and Vista on desktop. ) NTLM Hash Algorithm – Convert password to Unicode. – Hash with MD 4 Algorithm. NTLM Security Problems – No salt. – Passwords cached on client. – Pass-the-hash vulnerabilities. Slide #29

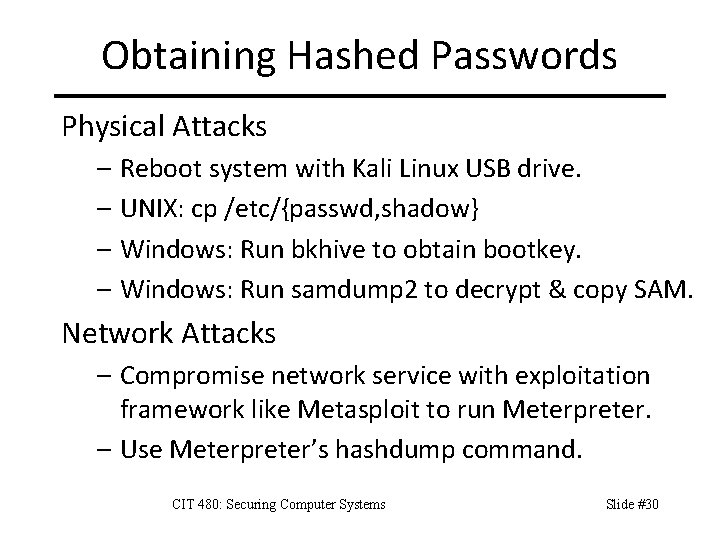
Obtaining Hashed Passwords Physical Attacks – Reboot system with Kali Linux USB drive. – UNIX: cp /etc/{passwd, shadow} – Windows: Run bkhive to obtain bootkey. – Windows: Run samdump 2 to decrypt & copy SAM. Network Attacks – Compromise network service with exploitation framework like Metasploit to run Meterpreter. – Use Meterpreter’s hashdump command. CIT 480: Securing Computer Systems Slide #30

Kerberos is a challenge/response protocol – Passwords are never sent over network. – Passwords are never stored on client. – Users authenticate via tickets, not passwords or hashes. Open standard based on symmetric cryptography – Created by MIT for internal use. – Open source and commercial versions exist. – Microsoft Active Directory = Kerberos + LDAP. Password storage – Multiple allowed hashing techniques. CIT 480: Securing Computer Systems Slide #31

Random Password Selection Yields equal distribution of passwords for maximum difficulty in cracking. Random passwords aren’t easy to remember – Short term memory holds 7 +/- 2 items – People have multiple passwords – Principle of Psychological Acceptability Requires a secure PRNG to be effective. CIT 480: Securing Computer Systems Slide #32

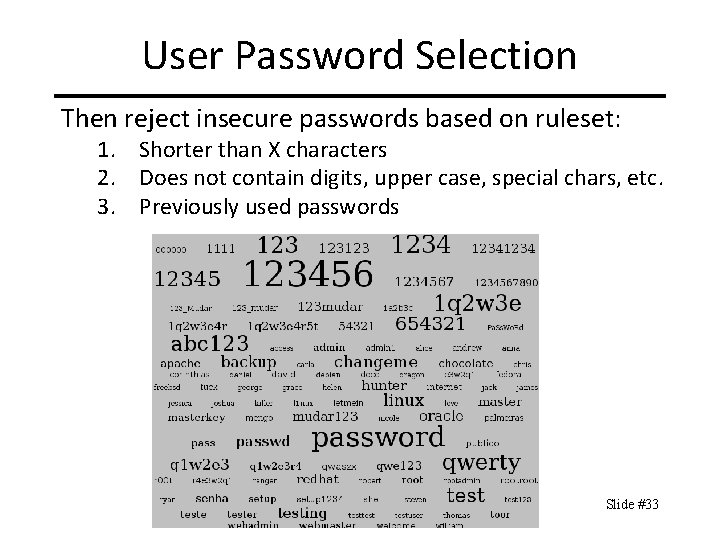
User Password Selection Then reject insecure passwords based on ruleset: 1. Shorter than X characters 2. Does not contain digits, upper case, special chars, etc. 3. Previously used passwords CIT 480: Securing Computer Systems Slide #33

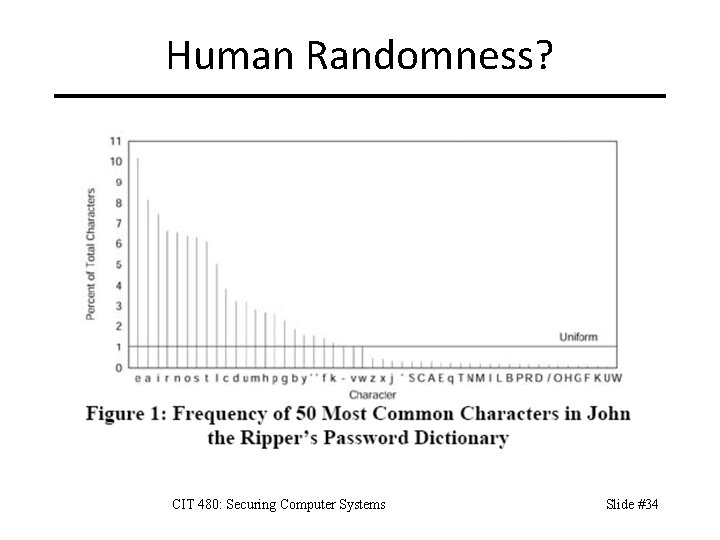
Human Randomness? CIT 480: Securing Computer Systems Slide #34

Online Cracking Defenses If complements (hashes) not accessible, attacker must use authentication functions to do an online attack. You can’t stop threats from trying to login. To increase difficulty of online attacks: Backoff: add wait time before asking for username and password again, increasing with each login failure. Disconnection: disconnect after n failures. Disabling: disable account after n failures. CIT 480: Securing Computer Systems Slide #35

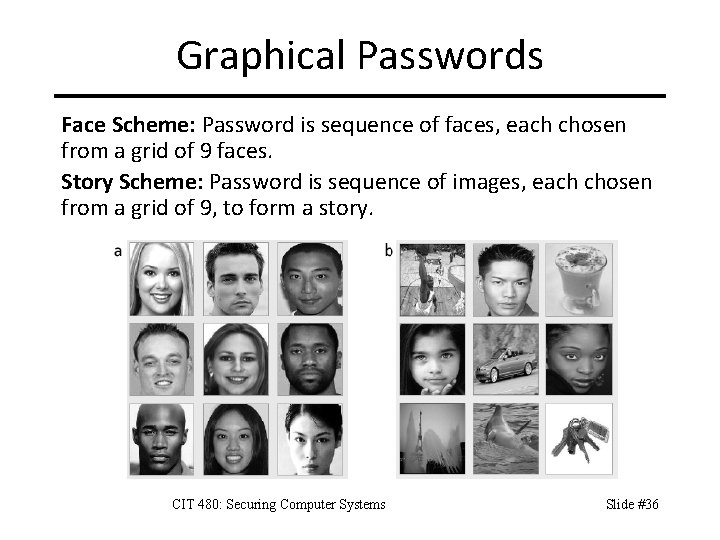
Graphical Passwords Face Scheme: Password is sequence of faces, each chosen from a grid of 9 faces. Story Scheme: Password is sequence of images, each chosen from a grid of 9, to form a story. CIT 480: Securing Computer Systems Slide #36

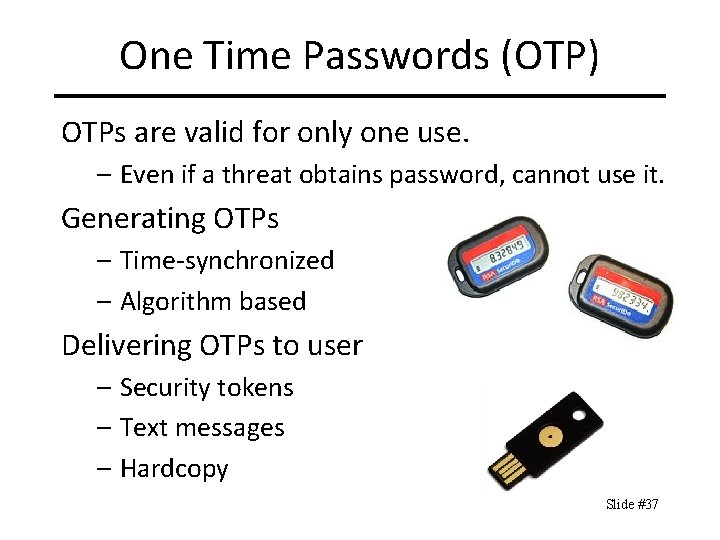
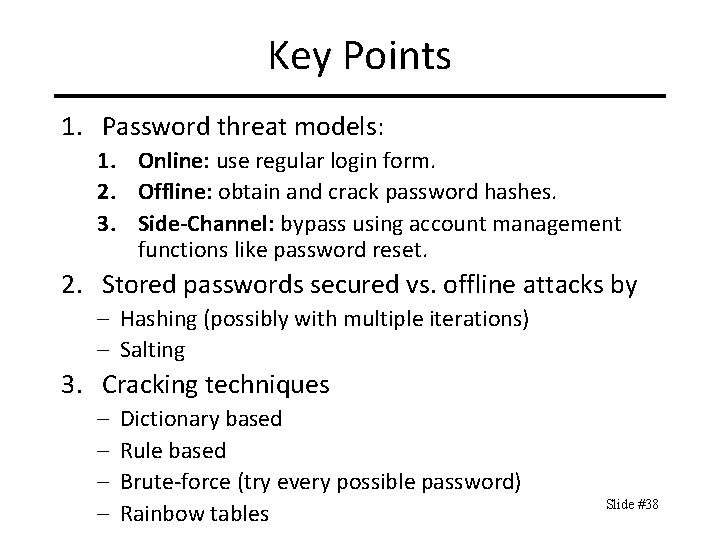
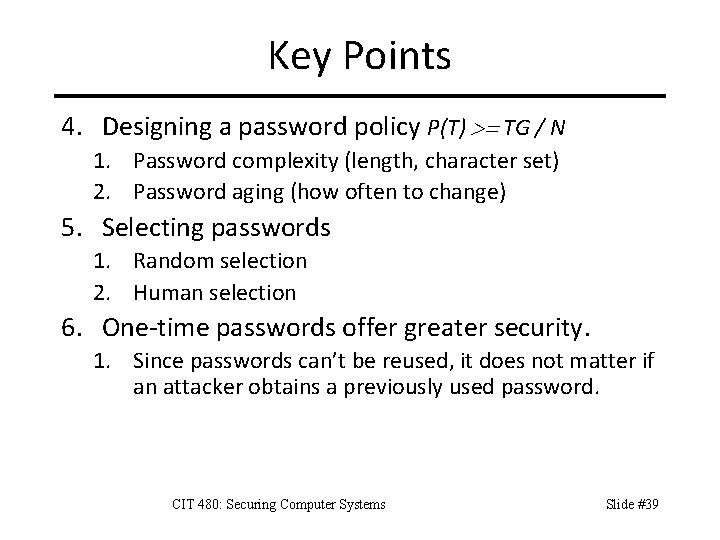
One Time Passwords (OTP) OTPs are valid for only one use. – Even if a threat obtains password, cannot use it. Generating OTPs – Time-synchronized – Algorithm based Delivering OTPs to user – Security tokens – Text messages – Hardcopy Slide #37

Key Points 1. Password threat models: 1. Online: use regular login form. 2. Offline: obtain and crack password hashes. 3. Side-Channel: bypass using account management functions like password reset. 2. Stored passwords secured vs. offline attacks by – Hashing (possibly with multiple iterations) – Salting 3. Cracking techniques – – Dictionary based Rule based Brute-force (try every possible password) Rainbow tables Slide #38

Key Points 4. Designing a password policy P(T) >= TG / N 1. Password complexity (length, character set) 2. Password aging (how often to change) 5. Selecting passwords 1. Random selection 2. Human selection 6. One-time passwords offer greater security. 1. Since passwords can’t be reused, it does not matter if an attacker obtains a previously used password. CIT 480: Securing Computer Systems Slide #39

References 1. 2. 3. 4. 5. 6. 7. 8. Ross Anderson, Security Engineering, 2 nd edition, Wiley, 2008. Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. Mark Burnett and Dave Kleiman, Perfect Passwords, Syngress, 2006. Lorie Faith Cranor and Simson Garfinkel, Security and Usability, O’Reilly, 2005. Dan Goodin, Why passwords have never been weaker—and crackers have never been stronger, Ars Technica, http: //arstechnica. com/security/2012/08/passwords-under-assault/, 2012. Goodrich and Tammasia, Introduction to Computer Security, Pearson, 2011. Cynthia Kuo et. al. , Human Selection of Mnemonic Phrase-based Passwords. SOUPS 2006, http: //cups. cmu. edu/soups/2006/proceedings/p 67_kuo. pdf. Solar Designer, Password hashing at scale, Ya. C 2012, http: //www. openwall. com/presentations/Ya. C 2012 -Password. Hashing-At-Scale/, 2012. Slide #40