CIT 480 Securing Computer Systems Firewalls CIT 480










- Slides: 33

CIT 480: Securing Computer Systems Firewalls CIT 480: Securing Computer Systems Slide #1

Topics 1. What is a firewall? 2. Types of Firewalls 1. 2. 3. 4. Packet filters (stateless) Stateful firewalls Proxy servers Application layer firewalls 3. Configuring the Linux Firewall 4. Firewall Architectures and DMZs CIT 480: Securing Computer Systems Slide #2

What is a Firewall? A software or hardware component that restricts network communication between two computers or networks. In buildings, a firewall is a fireproof wall that restricts the spread of a fire. Network firewall prevents threats from spreading from one network to another. CIT 480: Securing Computer Systems Slide #3

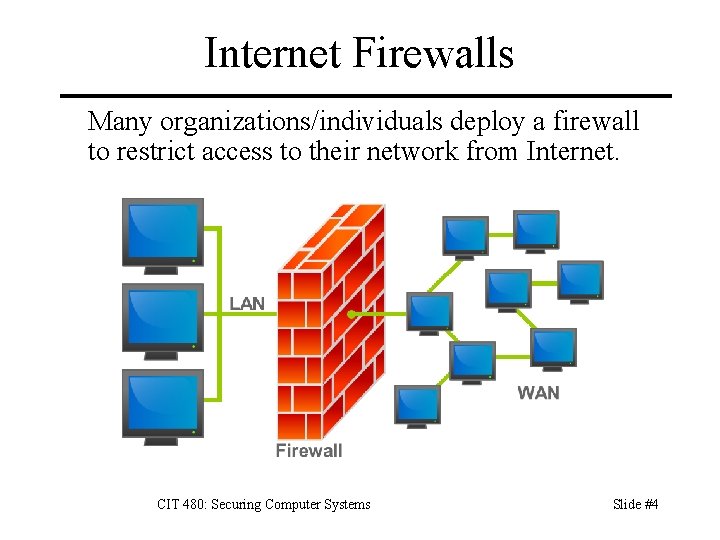
Internet Firewalls Many organizations/individuals deploy a firewall to restrict access to their network from Internet. CIT 480: Securing Computer Systems Slide #4

What is a Firewall? (2) A security control to enforce network policy – Choke point that traffic has to flow through. – ACLs on a host/network level. Policy Decisions: – What traffic should be allowed into network? • Integrity: protect integrity of internal systems. • Availability: protection from Do. S attacks. – What traffic should be allowed out? • Confidentiality: protection from data leakage. CIT 480: Securing Computer Systems Slide #5

Firewall Policies Blacklist – Specify traffic to be blocked. – Let everything else through. Whitelist – Specify traffic to be accepted. – Block everything else. CIT 480: Securing Computer Systems Slide #6

Types of Firewalls Packet Filters (Stateless) – Apply access rules to individual packets. – Most routers have this capabilities. Stateful Filters – Apply access rules to network flows or sessions. – Must maintain a table of active flows. Application Layer Firewalls – A proxy server that relays byte streams from client to server and vice versa. – Inspects application headers for undesirable sites and application data for undesirable content (malware etc. )

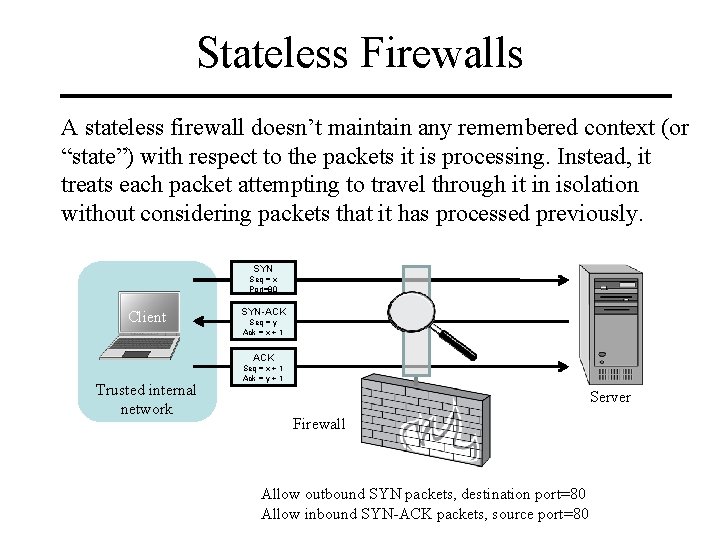
Stateless Firewalls A stateless firewall doesn’t maintain any remembered context (or “state”) with respect to the packets it is processing. Instead, it treats each packet attempting to travel through it in isolation without considering packets that it has processed previously. SYN Seq = x Port=80 Client SYN-ACK Seq = y Ack = x + 1 ACK Trusted internal network Seq = x + 1 Ack = y + 1 Server Firewall Allow outbound SYN packets, destination port=80 Allow inbound SYN-ACK packets, source port=80

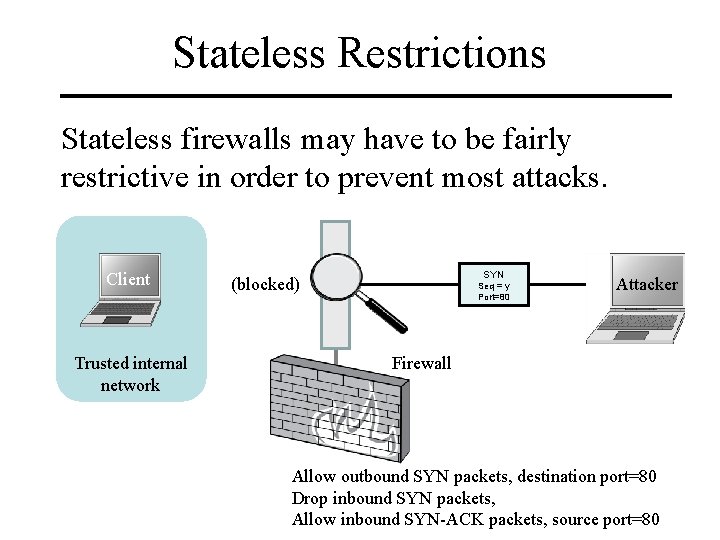
Stateless Restrictions Stateless firewalls may have to be fairly restrictive in order to prevent most attacks. Client Trusted internal network SYN (blocked) Seq = y Port=80 Attacker Firewall Allow outbound SYN packets, destination port=80 Drop inbound SYN packets, Allow inbound SYN-ACK packets, source port=80

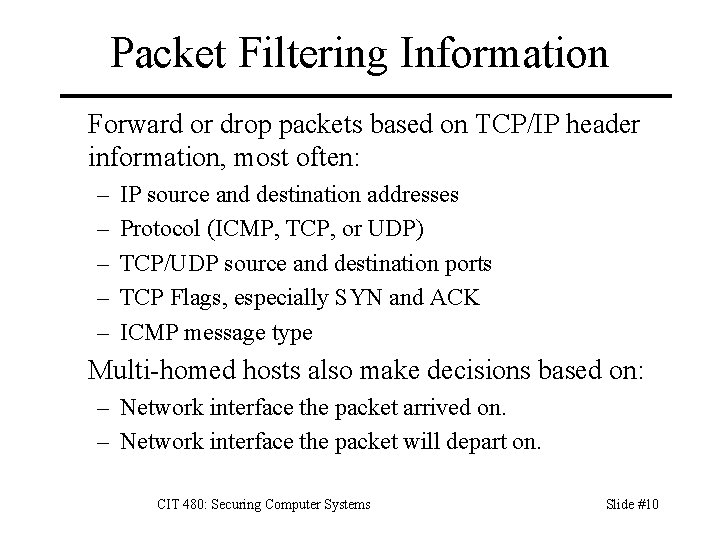
Packet Filtering Information Forward or drop packets based on TCP/IP header information, most often: – – – IP source and destination addresses Protocol (ICMP, TCP, or UDP) TCP/UDP source and destination ports TCP Flags, especially SYN and ACK ICMP message type Multi-homed hosts also make decisions based on: – Network interface the packet arrived on. – Network interface the packet will depart on. CIT 480: Securing Computer Systems Slide #10

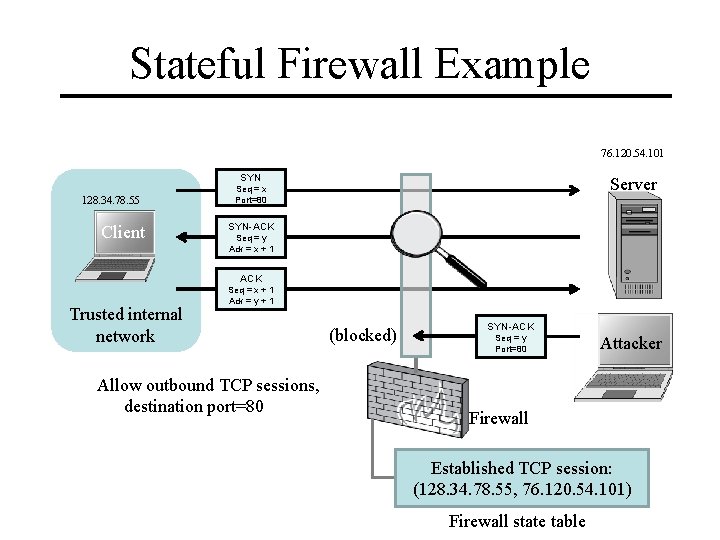
Stateful Firewall Example 76. 120. 54. 101 SYN 128. 34. 78. 55 Client Server Seq = x Port=80 SYN-ACK Seq = y Ack = x + 1 ACK Trusted internal network Seq = x + 1 Ack = y + 1 Allow outbound TCP sessions, destination port=80 (blocked) SYN-ACK Seq = y Port=80 Attacker Firewall Established TCP session: (128. 34. 78. 55, 76. 120. 54. 101) Firewall state table

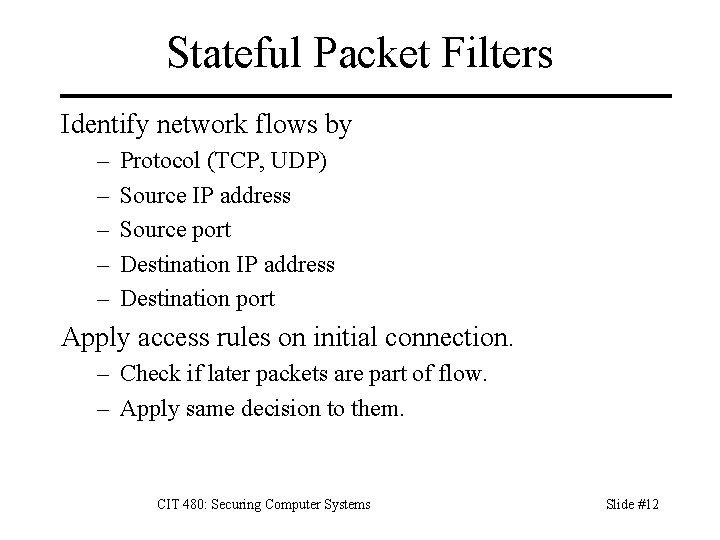
Stateful Packet Filters Identify network flows by – – – Protocol (TCP, UDP) Source IP address Source port Destination IP address Destination port Apply access rules on initial connection. – Check if later packets are part of flow. – Apply same decision to them. CIT 480: Securing Computer Systems Slide #12

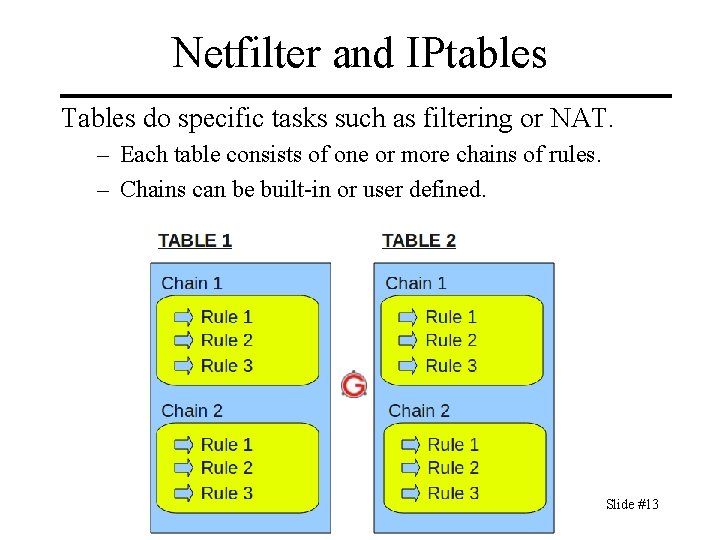
Netfilter and IPtables Tables do specific tasks such as filtering or NAT. – Each table consists of one or more chains of rules. – Chains can be built-in or user defined. Slide #13

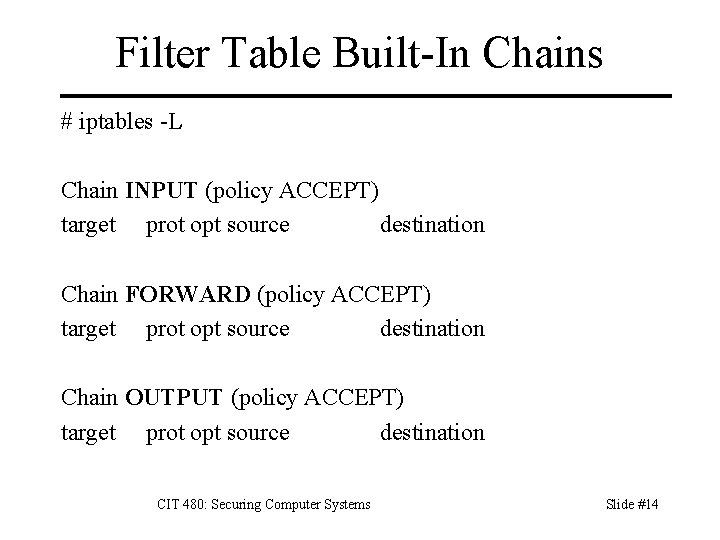
Filter Table Built-In Chains # iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination CIT 480: Securing Computer Systems Slide #14

Chains are Lists of Rules Packet traverses a chain sequentially until – A rule matches the packet and makes a final decision to ACCEPT or REJECT it. – A rule matches the packet and sends it to another chain. – The end of the chain is reached. If the end is reached, the packet either – Returns to being processed by the calling chain. – Is processed by the default policy of the chain. CIT 480: Securing Computer Systems Slide #15

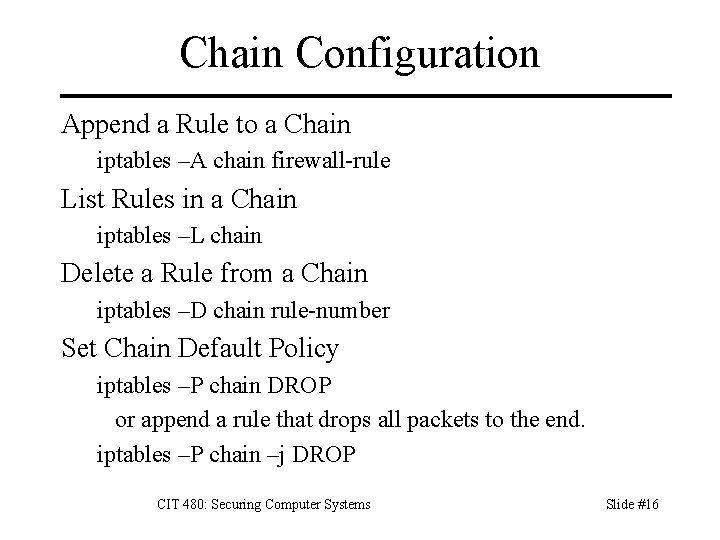
Chain Configuration Append a Rule to a Chain iptables –A chain firewall-rule List Rules in a Chain iptables –L chain Delete a Rule from a Chain iptables –D chain rule-number Set Chain Default Policy iptables –P chain DROP or append a rule that drops all packets to the end. iptables –P chain –j DROP CIT 480: Securing Computer Systems Slide #16

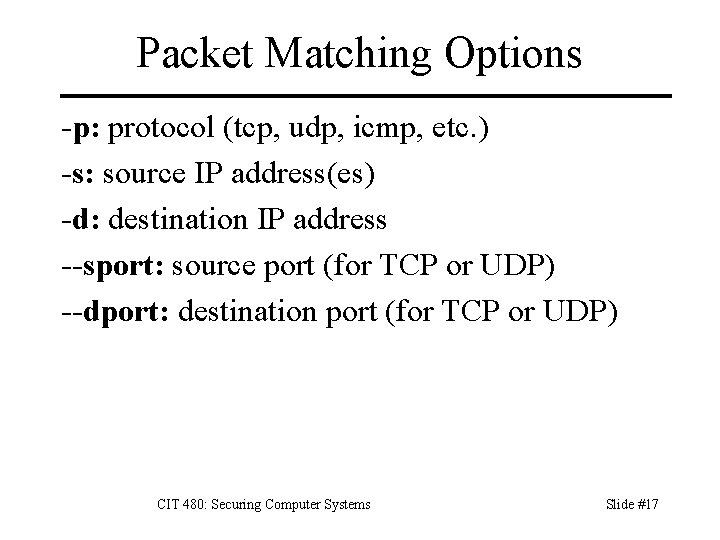
Packet Matching Options -p: protocol (tcp, udp, icmp, etc. ) -s: source IP address(es) -d: destination IP address --sport: source port (for TCP or UDP) --dport: destination port (for TCP or UDP) CIT 480: Securing Computer Systems Slide #17

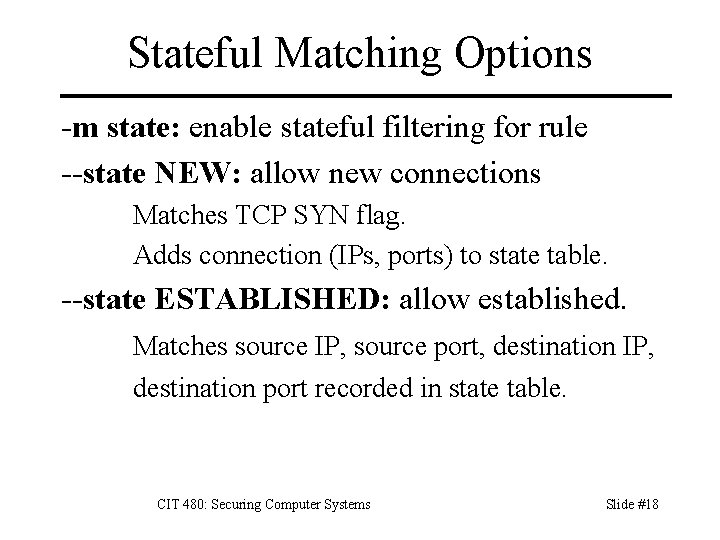
Stateful Matching Options -m state: enable stateful filtering for rule --state NEW: allow new connections Matches TCP SYN flag. Adds connection (IPs, ports) to state table. --state ESTABLISHED: allow established. Matches source IP, source port, destination IP, destination port recorded in state table. CIT 480: Securing Computer Systems Slide #18

Rule Targets ACCEPT: let the packet through. DROP: do not let the packet through. REJECT: do not allow + send ICMP error. RETURN: stop processing on this chain and return to the next rule in the calling chain: continue processing packet with the named chain. CIT 480: Securing Computer Systems Slide #19

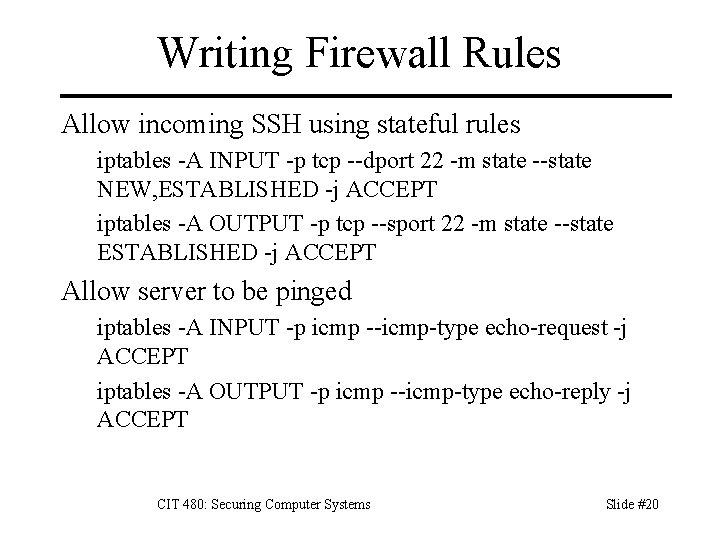
Writing Firewall Rules Allow incoming SSH using stateful rules iptables -A INPUT -p tcp --dport 22 -m state --state NEW, ESTABLISHED -j ACCEPT iptables -A OUTPUT -p tcp --sport 22 -m state --state ESTABLISHED -j ACCEPT Allow server to be pinged iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPT iptables -A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPT CIT 480: Securing Computer Systems Slide #20

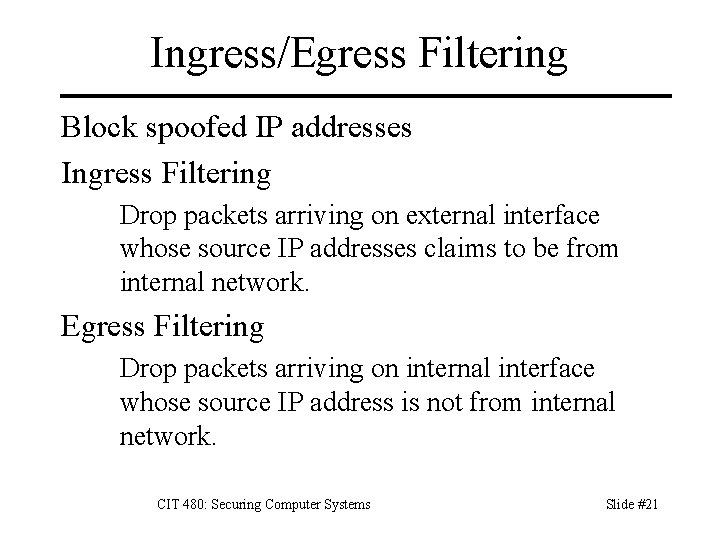
Ingress/Egress Filtering Block spoofed IP addresses Ingress Filtering Drop packets arriving on external interface whose source IP addresses claims to be from internal network. Egress Filtering Drop packets arriving on internal interface whose source IP address is not from internal network. CIT 480: Securing Computer Systems Slide #21

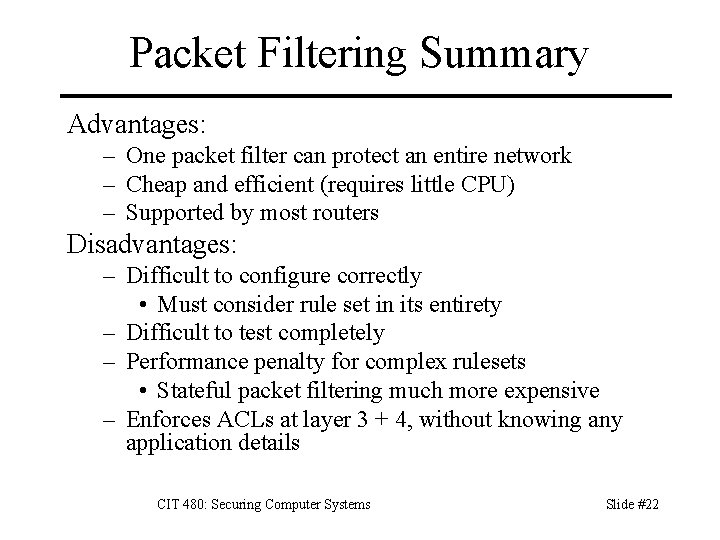
Packet Filtering Summary Advantages: – One packet filter can protect an entire network – Cheap and efficient (requires little CPU) – Supported by most routers Disadvantages: – Difficult to configure correctly • Must consider rule set in its entirety – Difficult to test completely – Performance penalty for complex rulesets • Stateful packet filtering much more expensive – Enforces ACLs at layer 3 + 4, without knowing any application details CIT 480: Securing Computer Systems Slide #22

Proxy Servers Proxy host relays Transport/App connections – Packet filter blocks direct connections. – Client makes connection to proxy. – Proxy forwards connection to server. Proxy can provide multiple security features: – Access Control – Authentication – Logging – Anonymity CIT 480: Securing Computer Systems Slide #23

Example: SOCKS v 5 • Socks Server • Socks Client Library – Clients must be linked against library. – Library offers replacements for UNIX network socket system calls. • User Authentication Protocols – Cleartext username/password. – GSS-API authentication. CIT 480: Securing Computer Systems Slide #24

Proxy Servers Advantages: – User-level authentication possible. – Efficient logging, as proxy deals with circuit connections instead of individual packets. Disadvantages: – Clients have to be recompiled or reconfigured to use proxy service. – Some services can’t be proxied. – Cannot protect you from all protocol weaknesses. CIT 480: Securing Computer Systems Slide #25

Application Layer Firewalls Application layer rules – HTTP: URLs, headers, etc. – SMTP: spam statistics More complex – Only 216 ports, but – An infinite number of URLs, HTTP headers, bodies, etc. Slide #26

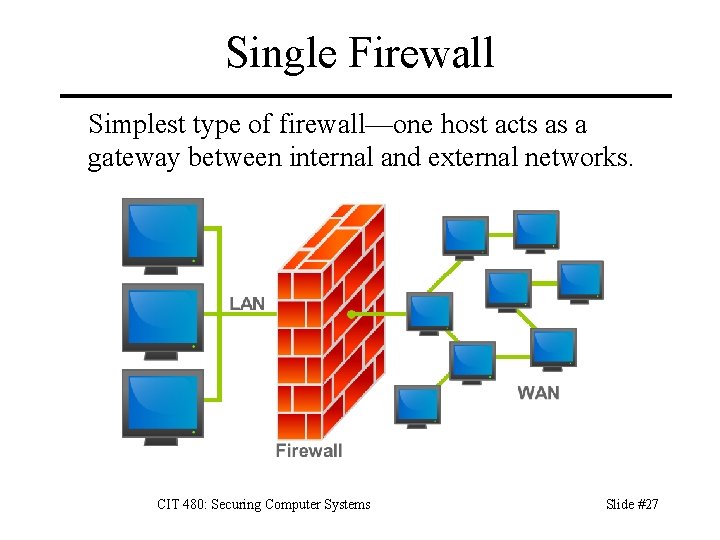
Single Firewall Simplest type of firewall—one host acts as a gateway between internal and external networks. CIT 480: Securing Computer Systems Slide #27

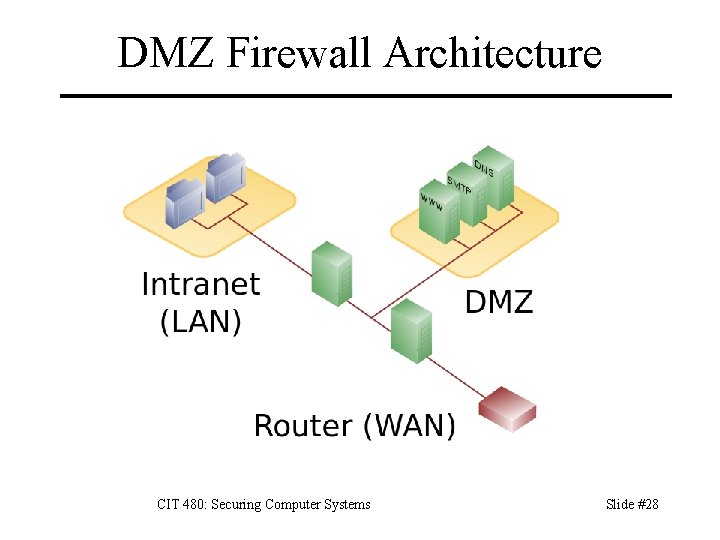
DMZ Firewall Architecture CIT 480: Securing Computer Systems Slide #28

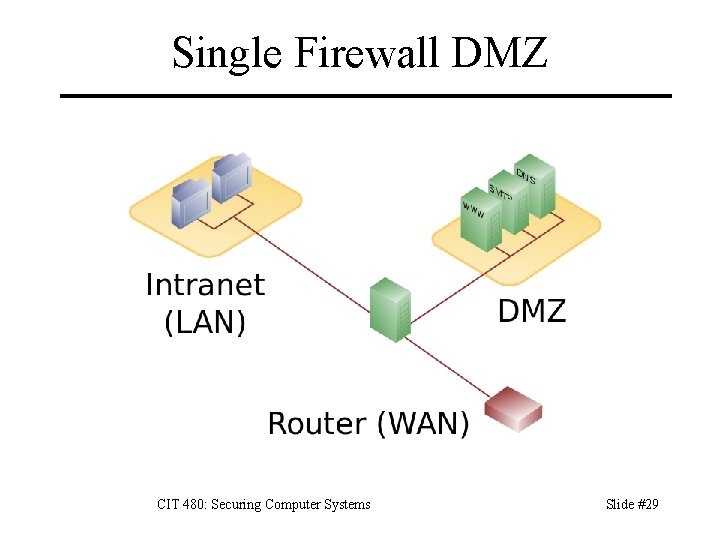
Single Firewall DMZ CIT 480: Securing Computer Systems Slide #29

DMZ Servers w/ external access isolated from internal net – Compromise of a DMZ server doesn’t directly compromise internal network. – DMZ servers also can’t sniff internal traffic, since they’re on a different subnet. No single point of failure – Attacker must compromise both exterior and interior routers to gain access to internal net. Advantages: greater security Disadvantages: higher cost and complexity CIT 480: Securing Computer Systems Slide #30

Firewall Limitations Cannot protect from internal attacks – May be able to limit access with internal firewalls to a segment of your network. Cannot protect you from user error – Users will still run trojan horses that make it past your AV scanner. – Users visiting malicious sites run malicious Javascript inside the firewalls. Firewall mechanism may not precisely enforce your security policy. CIT 480: Securing Computer Systems Slide #31

Key Points 1. Firewall types 1. 2. 3. 4. Packet filtering (stateless) Stateful firewalls Proxy servers Application layer firewalls 2. Netfilter and Iptables 1. Tables and chains 2. Rules and actions 3. Firewall Architectures 1. Single firewall 2. DMZ 3. Single firewall DMZ Slide #32

References 1. 2. 3. 4. 5. William Cheswick, Steven Bellovin, and Avriel Rubin, Firewalls and Internet Security, 2 nd edition, 2003. Simson Garfinkel, Gene Spafford, and Alan Schwartz, Practical UNIX and Internet Security, 3 rd edition, O’Reilly & Associates, 2003. Goodrich and Tammasia, Introduction to Computer Security, Pearson, 2011. Ed Skoudis, Counter Hack Reloaded, Prentice Hall, 2006. Elizabeth Zwicky, Brent Chapman, Simon Cooper, Building Internet Firewalls, 2 nd edition, O’Reilly & Associates, 2000. CIT 480: Securing Computer Systems Slide #33