CIT 480 Securing Computer Systems Intrusion Detection CIT








- Slides: 34

CIT 480: Securing Computer Systems Intrusion Detection CIT 480: Securing Computer Systems Slide #1

Topics 1. 2. 3. 4. 5. 6. 7. 8. Definitions and Goals Models of Intrusion Detection False Positives Architecture of an IDS Example IDS: snort Active Response (IPS) Host-based IDS and IPS IDS Evasion Techniques CIT 480: Securing Computer Systems Slide #2

IDS Terminology Intrusion – Actions aimed at compromising the security of the target (confidentiality, integrity, availability of computing/networking resources) Intrusion detection – The identification through intrusion signatures and report of intrusion activities Intrusion prevention – The process of both detecting intrusion activities and managing automatic responsive actions throughout the network CIT 480: Securing Computer Systems Slide #3

Goals of IDS 1. Detect wide variety of intrusions – Previously known and unknown attacks. – Need to adapt to new attacks or changes in behavior. 2. Detect intrusions in timely fashion – May need to be be real-time, especially when system responds to intrusion. • Problem: analyzing commands may impact response time of system. – May suffice to report intrusion occurred a few minutes or hours ago. CIT 480: Securing Computer Systems Slide #4

Goals of IDS 3. Present analysis in easy-to-understand format. – – – Ideally a binary indicator. Usually more complex, allowing analyst to examine suspected attack. User interface critical, especially when monitoring many systems. 4. Be accurate – – Minimize false positives, false negatives. Minimize time spent verifying attacks, looking for them. CIT 480: Securing Computer Systems Slide #5

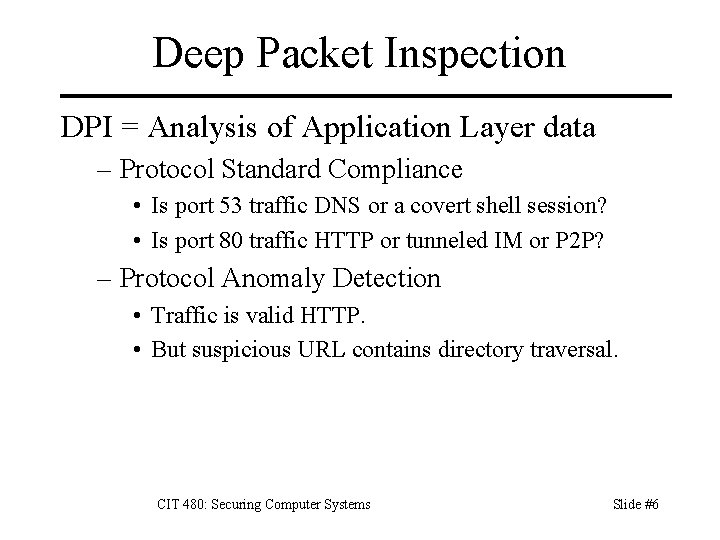
Deep Packet Inspection DPI = Analysis of Application Layer data – Protocol Standard Compliance • Is port 53 traffic DNS or a covert shell session? • Is port 80 traffic HTTP or tunneled IM or P 2 P? – Protocol Anomaly Detection • Traffic is valid HTTP. • But suspicious URL contains directory traversal. CIT 480: Securing Computer Systems Slide #6

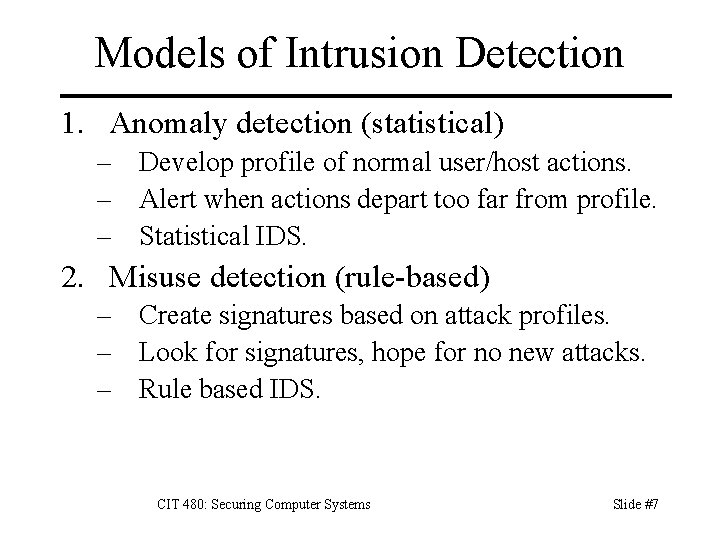
Models of Intrusion Detection 1. Anomaly detection (statistical) – Develop profile of normal user/host actions. – Alert when actions depart too far from profile. – Statistical IDS. 2. Misuse detection (rule-based) – Create signatures based on attack profiles. – Look for signatures, hope for no new attacks. – Rule based IDS. CIT 480: Securing Computer Systems Slide #7

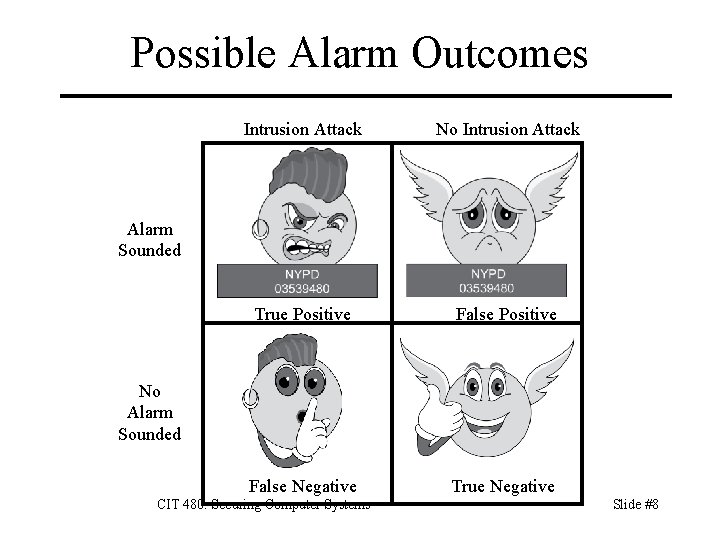
Possible Alarm Outcomes Intrusion Attack No Intrusion Attack True Positive False Negative True Negative Alarm Sounded No Alarm Sounded CIT 480: Securing Computer Systems Slide #8

Base-Rate Fallacy • Difficult to create IDS with high true-positive rate and low false-negative rate. • If #intrusions small compared to normal traffic, then IDS will produce many false positives for each intrusion. • Effectiveness of IDS can be misinterpreted due to a statistical error known as the base-rate fallacy. • This type of error occurs when the probability of some conditional event is assessed without considering the “base rate” of that event. CIT 480: Securing Computer Systems Slide #9

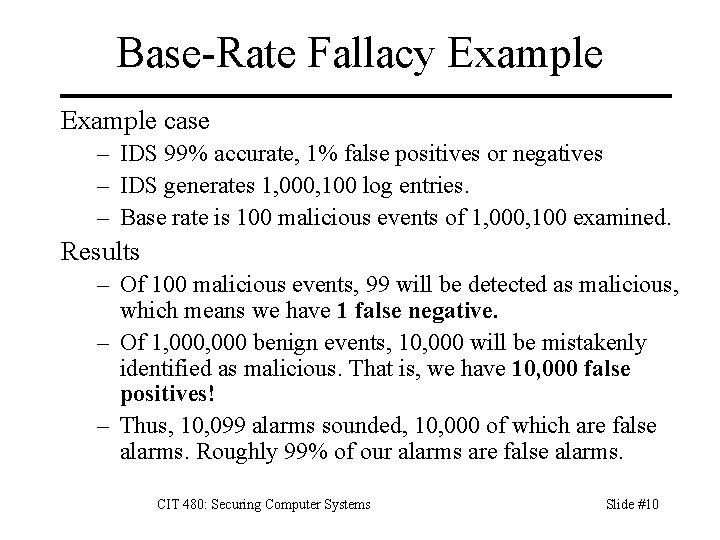
Base-Rate Fallacy Example case – IDS 99% accurate, 1% false positives or negatives – IDS generates 1, 000, 100 log entries. – Base rate is 100 malicious events of 1, 000, 100 examined. Results – Of 100 malicious events, 99 will be detected as malicious, which means we have 1 false negative. – Of 1, 000 benign events, 10, 000 will be mistakenly identified as malicious. That is, we have 10, 000 false positives! – Thus, 10, 099 alarms sounded, 10, 000 of which are false alarms. Roughly 99% of our alarms are false alarms. CIT 480: Securing Computer Systems Slide #10

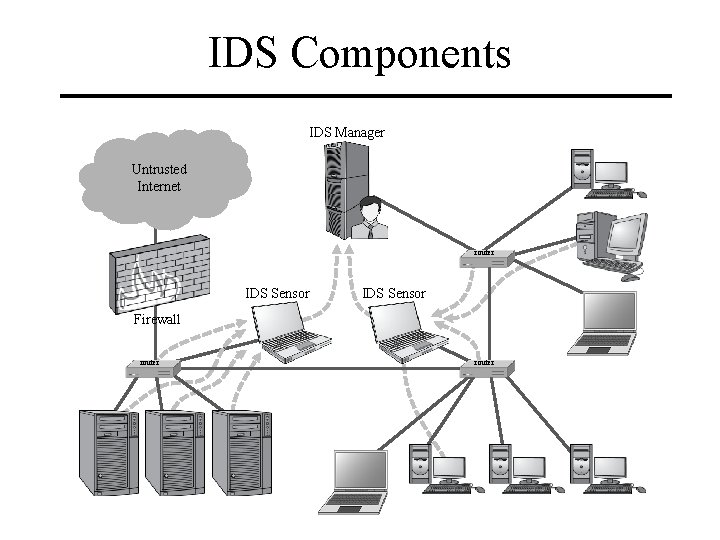
IDS Components IDS Manager Untrusted Internet router IDS Sensor Firewall router

IDS Architecture An IDS is essentially a sophisticated audit system – Sensors gathers data for analysis from hosts or network. – Manager analyzes data obtained from sensors according to its internal rules. – Notifier acts on manager results. • May simply notify security officer. • May reconfigure sensors or manager to alter collection, analysis methods. • May activate response mechanism. CIT 480: Securing Computer Systems Slide #12

Host-Based Sensors 1. Obtain information from logs – – – May use many logs as sources. May be security-related or not. May use virtual logs if agent is part of the kernel. 2. Agent generates its information – – Analyzes state of system. Treats results of analysis as log data. CIT 480: Securing Computer Systems Slide #13

Network-Based Sensors Sniff traffic from network. – Use hubs, SPAN ports, or taps to see traffic. – Need sensors on all switches to see entire network. – Deep packet inspection (DPI). Sensor needs same view of traffic as destination – Attacker may send packets with TTL set so that they arrive at destination but expire before reaching sensor. – Packet fragmentation and reassembly works differently on different OSes, so sensor sees different packet than destination in some cases. End-to-end encryption defeats content monitoring – Not traffic analysis, though. Slide #14

Aggregation of Information Sensors produce information at multiple layers of abstraction. – Application-monitoring sensors provide one view of an event. – System-monitoring sensors provide a different view of an event. – Network-monitoring sensors provide yet another view (involving many packets) of an event. CIT 480: Securing Computer Systems Slide #15

Notifier • Accepts information from manager • Takes appropriate action – Page, call, IM, or e-mail security officer. – Rate-limit contacts so a single problem does not result in an overwhelming flood of notices. – Respond to attack. • Often GUIs – Use visualization to convey information. CIT 480: Securing Computer Systems Slide #16

Example NIDS: snort Network Intrusion Detection System – Sniffs packets off wire. – Checks packets for matches against rule sets. – Logs detected signs of misuse. – Alerts adminstrator when misuse detected. CIT 480: Securing Computer Systems Slide #17

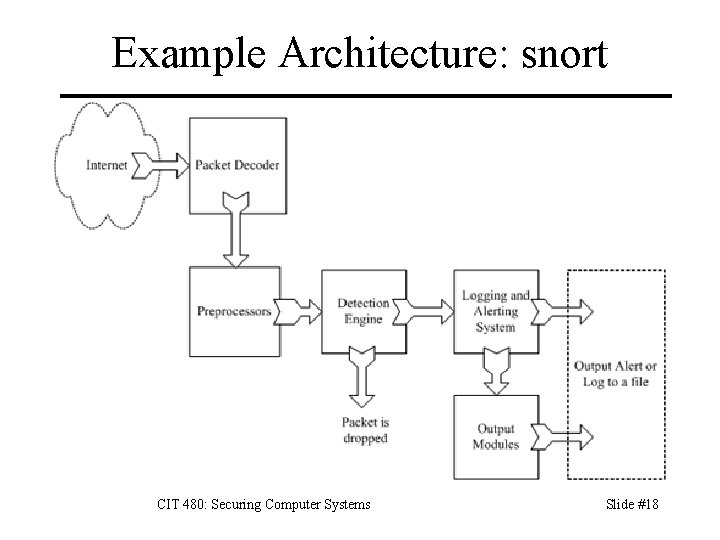
Example Architecture: snort CIT 480: Securing Computer Systems Slide #18

Snort Rules Rule Header – – Action: pass, log, alert Network Protocol Source Address (Host or Network) + Port Destination Address (Host or Network) + Port Rule Body – Content: packet ASCII or binary content – TCP/IP flags and options to match – Message to log, indicating nature of misuse detected CIT 480: Securing Computer Systems Slide #19

Snort Rule Example: rule for ssh shell code exploit alert tcp $EXTERNAL_NET any -> $HOME_NET 22 (msg: "EXPLOIT ssh CRC 32 overflow NOOP"; flow: to_server, established; content: "|90 90 90 90 90|"; reference: bugtraq, 2347; reference: cve, CVE-20010144; classtype: shellcode-detect; sid: 1326; rev: 3; ) CIT 480: Securing Computer Systems Slide #20

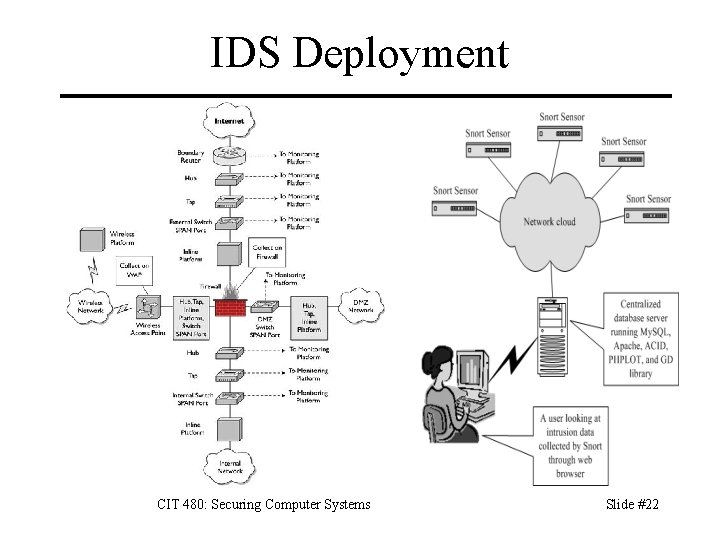
IDS Deployment IDS deployment should reflect your threat model. Major classes of attackers: 1. External attackers intruding from Internet. 2. Internal attackers intruding from your LANs. Where should you place IDS systems? 1. 2. 3. 4. Perimeter (outside firewall) DMZ Intranet Wireless CIT 480: Securing Computer Systems Slide #21

IDS Deployment CIT 480: Securing Computer Systems Slide #22

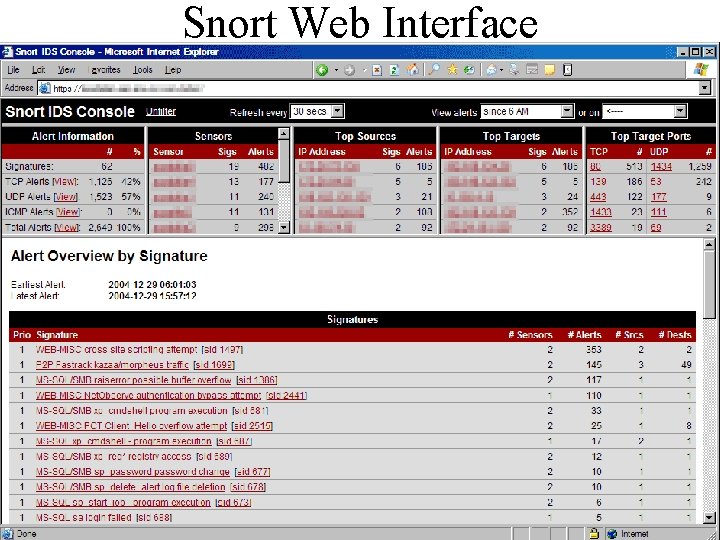
Snort Web Interface CIT 480: Securing Computer Systems Slide #23

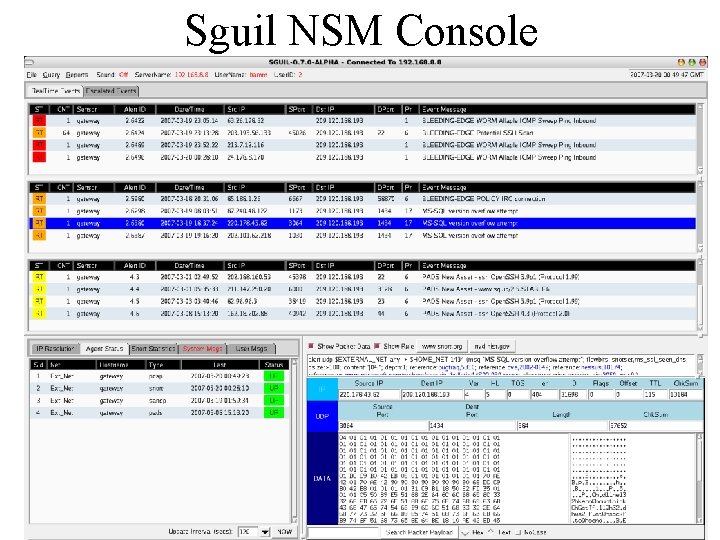
Sguil NSM Console

Intrusion Prevention Systems What else can you do with IDS alerts? – Identify attack before it completes. – Prevent it from completing. How to prevent attacks? – Directly: IPS drops packets, kills TCP sessions. – Indirectly: IPS modifies firewall rules. Is IPS a good idea? – How do you deal with false positives? CIT 480: Securing Computer Systems Slide #25

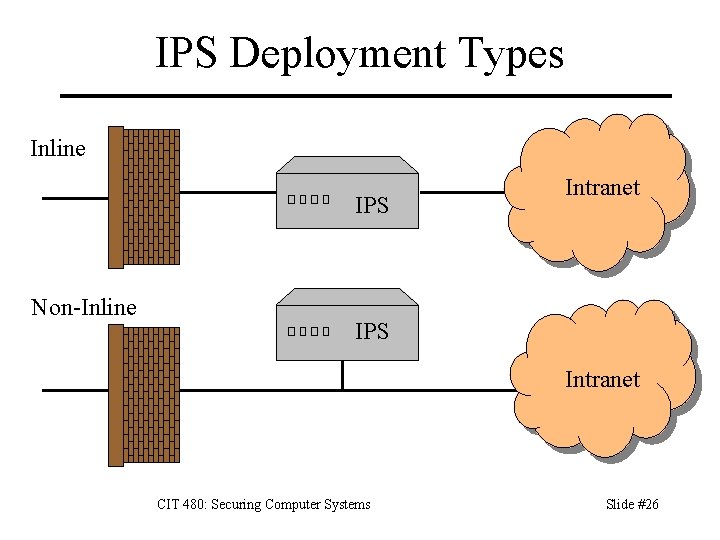
IPS Deployment Types Inline IPS Non-Inline Intranet IPS Intranet CIT 480: Securing Computer Systems Slide #26

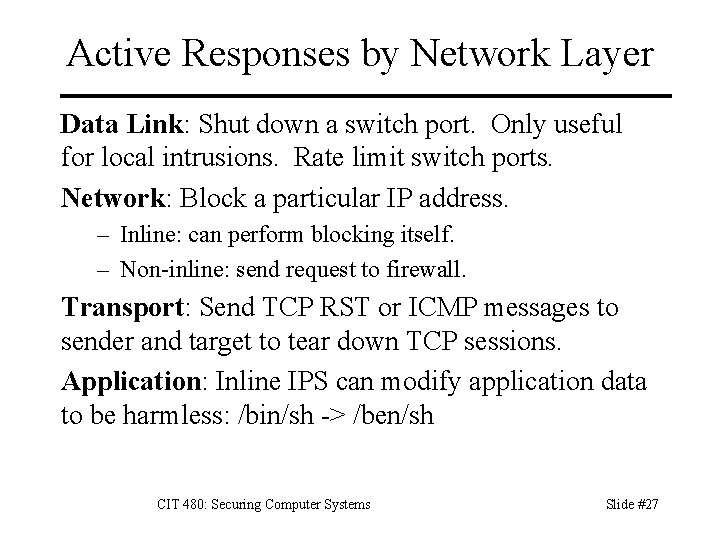
Active Responses by Network Layer Data Link: Shut down a switch port. Only useful for local intrusions. Rate limit switch ports. Network: Block a particular IP address. – Inline: can perform blocking itself. – Non-inline: send request to firewall. Transport: Send TCP RST or ICMP messages to sender and target to tear down TCP sessions. Application: Inline IPS can modify application data to be harmless: /bin/sh -> /ben/sh CIT 480: Securing Computer Systems Slide #27

Host IDS and IPS Anti-virus and anti-spyware – AVG anti-virus, Spy. Bot S&D Log monitors – swatch, logwatch Integrity checkers – tripwire, osiris, samhain – Monitor file checksums, etc. Application shims – mod_security (usually called a WAF) CIT 480: Securing Computer Systems Slide #28

Evading IDS and IPS Alter appearance to prevent sig match – URL encode parameters to avoid match. – Use ‘ or 783>412 -- for SQL injection. Alter context – Change TTL so IDS sees different packets than target hosts receives. – Fragment packets so that IDS and target host reassemble the packets differently. CIT 480: Securing Computer Systems Slide #29

Fragment Evasion Techniques Flood of fragments – Do. S via heavy use of CPU/RAM on IDS. Tiny fragment – Break attack into multiple fragments, none of which match signature. – ex: frag 1: “cat /etc”, frag 2: “/shadow” Overlapping fragments – Offset of later fragments overwrites earlier fragments. – ex: frag 1: “cat /etc/fred”, frag 2: offset=10, “shadow” – Different OSes deal differently with overlapping. CIT 480: Securing Computer Systems Slide #30

Web Evasion Techniques URL encoding – GET /%63%67%69%2 d%62%69%6 e/bad. cgi /. / directory insertion – GET /. /cgi-bin/. /bad. cgi Long directory insertion – GET /junklongdirectorypathstuffhereuseless/. . /cgi-bin/bad. cgi – IDS may only read first part of URL for speed. Tab separation – GET<tab>/cgi-bin/bad. cgi – Tabs usually work on servers, but may not be in sig. Case sensitivity – GET /CGI-BIN/bad. cgi – Windows filenames are case insensitive, but signature may not be. CIT 480: Securing Computer Systems Slide #31

Countering Evasion Keep IDS/IPS signatures up to date. – On daily or weekly basis. Use both host and network IDS/IPS. – Host-based harder to evade as runs on host. – Fragment attacks can’t evade host IDS. – Network IDS still useful as overall monitor. Tune IDS/IPS to handle based on experience – False positives – False negatives CIT 480: Securing Computer Systems Slide #32

Key Points 1. Models of IDS: – Anomaly detection: unexpected events (statistical IDS. ) – Misuse detection: violations of policy (rule-based IDS). 2. IDS Architecture: sensors, manager, notifier. 3. Host vs. Network IDS – Host: agent on host checks files, processes to detect attacks. – Network: sniffs and analyzes packets to detect intrusions. 4. IPS – Stop intrusions, but what about false positives? – Inline vs. non-inline: how do prevention techniques differ? 5. IDS/IPS Evasion – Alter appearance to avoid signature match. – Alter context to so IDS interprets differently than host. CIT 480: Securing Computer Systems Slide #33

References 1. 2. 3. 4. 5. 6. 7. 8. 9. Richard Bejtlich, The Tao of Network Security Monitoring, Addison-Wesley, 2004. William Cheswick, Steven Bellovin, and Avriel Rubin, Firewalls and Internet Security, 2 nd edition, 2003. Goodrich and Tammasia, Introduction to Computer Security, Pearson, 2011. The Honeynet Project, Know Your Enemy, 2 nd edition, Addison-Wesley, 2004. Richard A. Kemmerer and Giovanni Vigna, “Intrusion Detection: A Brief History and Overview, ” IEEE Security & Privacy, v 1 n 1, Apr 2002, pp 2730. Steven Northcutt and Julie Novak, Network Intrusion Detection, 3 rd edition, New Riders, 2002. Michael Rash et. al. , Intrusion Prevention and Active Response, Syngress, 2005. Rafiq Rehman, Intrusion Detection Systems with Snort: Advanced IDS Techniques Using Snort, Apache, My. SQL, PHP, and ACID, Prentice Hall, 2003. Ed Skoudis, Counter Hack Reloaded 2/e, Prentice Hall, 2006. CIT 480: Securing Computer Systems Slide #34