CIT 480 Securing Computer Systems Operating System Security











![Example Syslog Messages Feb 11 10: 17: 01 localhost /USR/SBIN/CRON[1971]: (root) CMD ( run-parts Example Syslog Messages Feb 11 10: 17: 01 localhost /USR/SBIN/CRON[1971]: (root) CMD ( run-parts](https://slidetodoc.com/presentation_image/580410e6ab6caf931344882c82ca7062/image-25.jpg)

- Slides: 26

CIT 480: Securing Computer Systems Operating System Security CIT 480: Securing Computer Systems Slide #1

Topics 1. OS Security Features 2. Bypassing OS Security 1. Boot time security 2. BIOS security 3. System Logs CIT 480: Securing Computer Systems Slide #2

OS Security Features 1. 2. 3. 4. 5. 6. Authentication Access Control Auditing (Logging) Encryption (Filesystems) Isolation (VM) Patching (Updates) CIT 480: Securing Computer Systems Slide #3

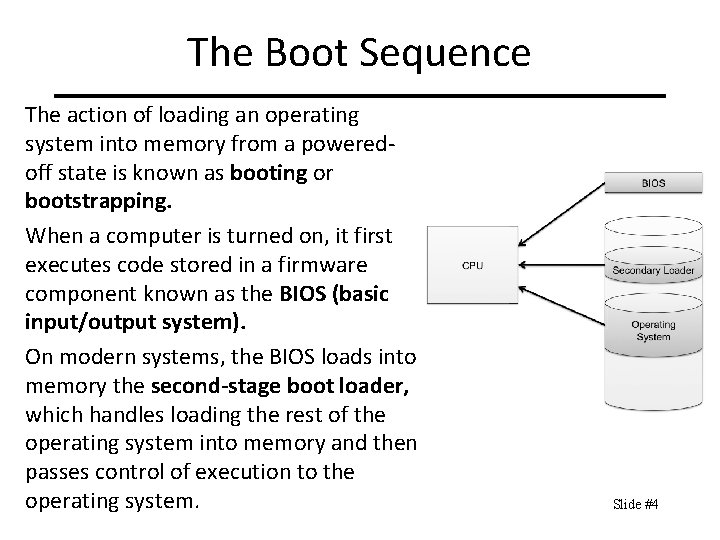
The Boot Sequence The action of loading an operating system into memory from a poweredoff state is known as booting or bootstrapping. When a computer is turned on, it first executes code stored in a firmware component known as the BIOS (basic input/output system). On modern systems, the BIOS loads into memory the second-stage boot loader, which handles loading the rest of the operating system into memory and then passes control of execution to the operating system. Slide #4

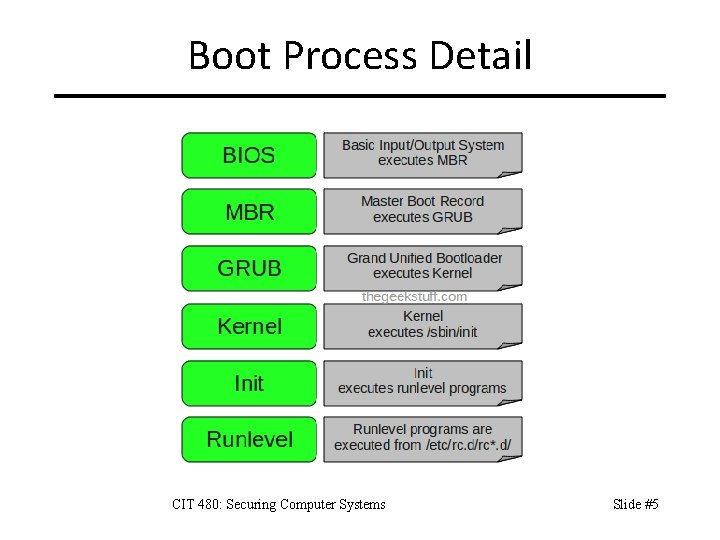
Boot Process Detail CIT 480: Securing Computer Systems Slide #5

BIOS CIT 480: Securing Computer Systems Slide #6

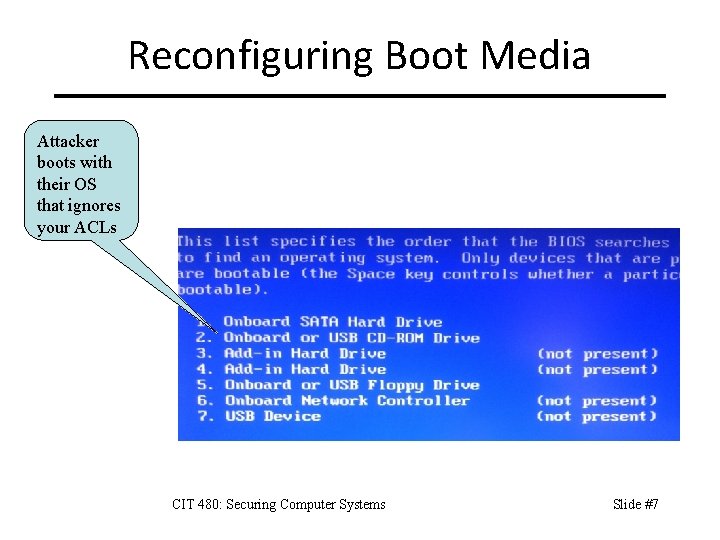
Reconfiguring Boot Media Attacker boots with their OS that ignores your ACLs CIT 480: Securing Computer Systems Slide #7

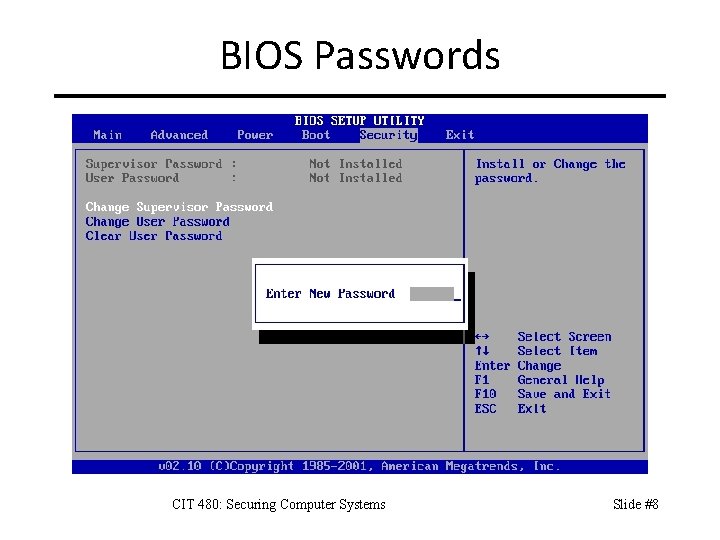
BIOS Passwords CIT 480: Securing Computer Systems Slide #8

Removing the BIOS Password CIT 480: Securing Computer Systems Slide #9

Protecting the BIOS Password CIT 480: Securing Computer Systems Slide #10

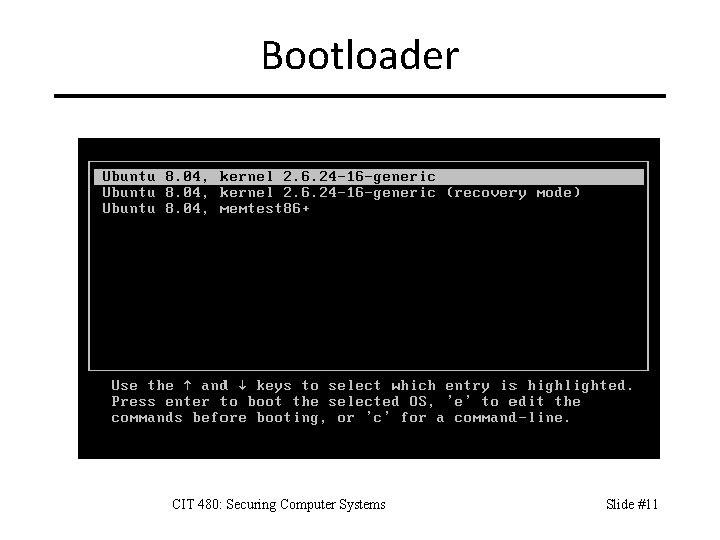
Bootloader CIT 480: Securing Computer Systems Slide #11

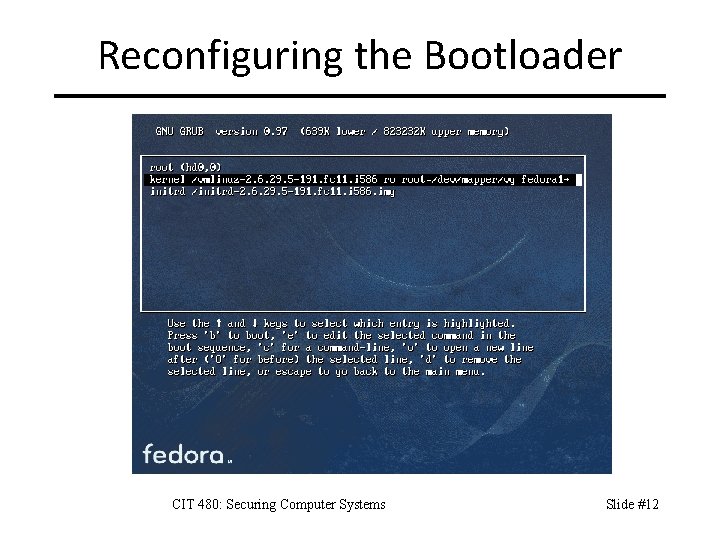
Reconfiguring the Bootloader CIT 480: Securing Computer Systems Slide #12

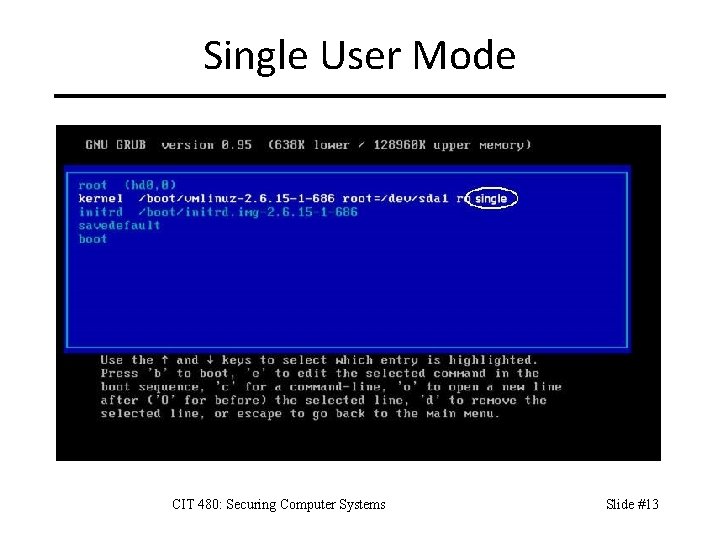
Single User Mode CIT 480: Securing Computer Systems Slide #13

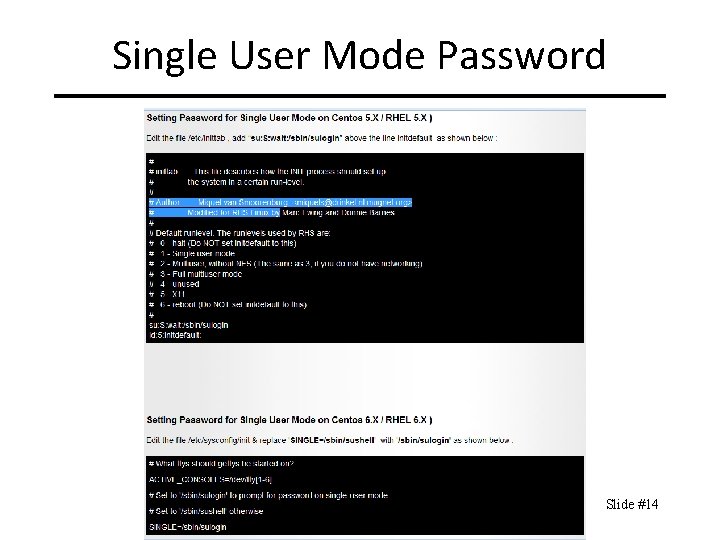
Single User Mode Password CIT 480: Securing Computer Systems Slide #14

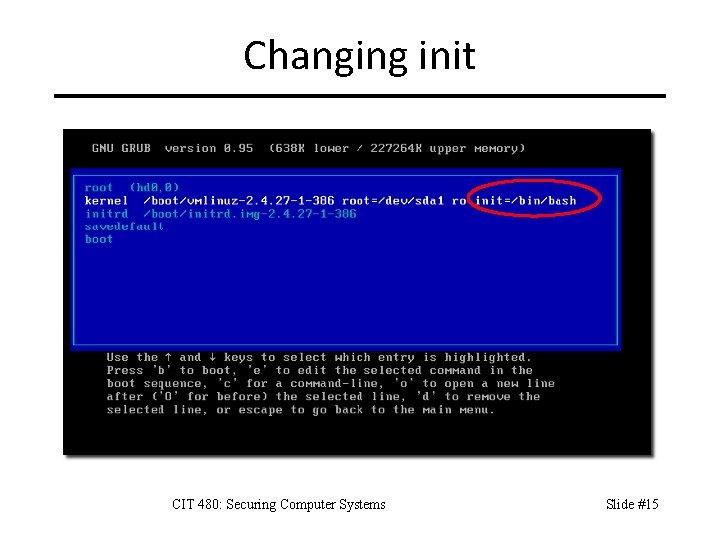
Changing init CIT 480: Securing Computer Systems Slide #15

GRUB Password CIT 480: Securing Computer Systems Slide #16

Hibernation Modern machines have the ability to go into a powered-off state known as hibernation. While going into hibernation, the OS stores the contents of machine’s memory into a hibernation file (such as hiberfil. sys) on disk so the computer can be quickly restored later. 1. User closes a laptop computer, putting it into hibernation. 2. Attacker copies the hiberfil. sys file to discover any unencrypted passwords that were stored in memory when the computer was put into hibernation. Slide #17

Cold Memory Attack CIT 480: Securing Computer Systems Slide #18

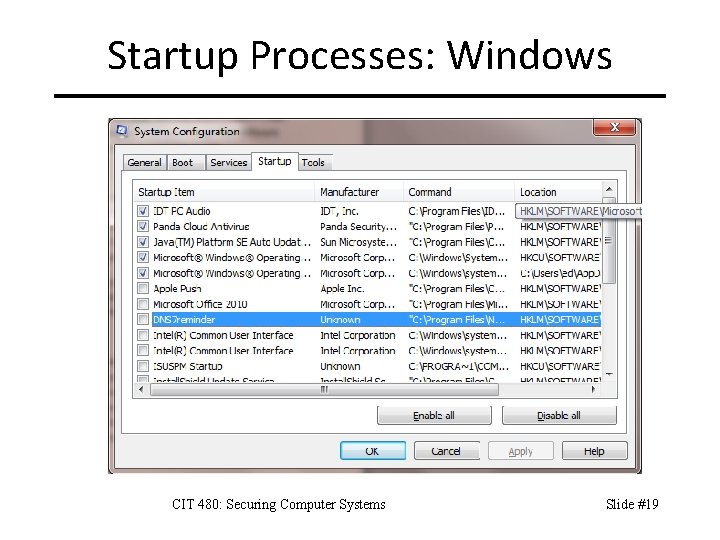
Startup Processes: Windows CIT 480: Securing Computer Systems Slide #19

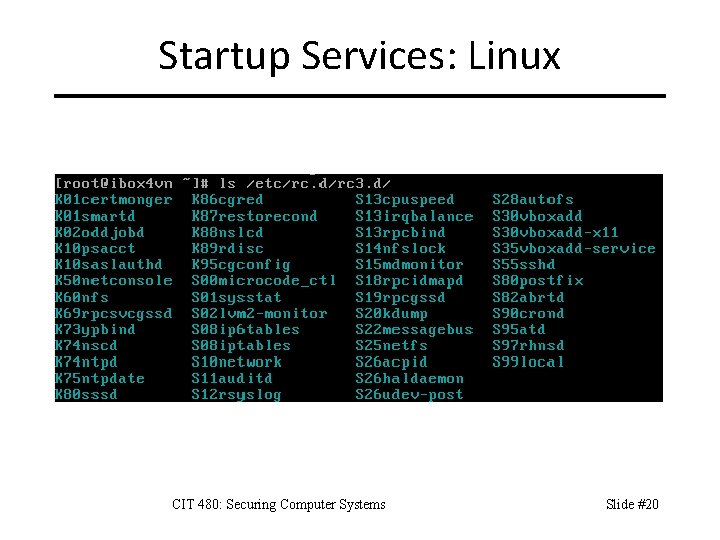
Startup Services: Linux CIT 480: Securing Computer Systems Slide #20

System Logs record status and error conditions. Where do log messages come from? – Kernel – Accounting system – System services Logging methods: – Service records own logs (apache, cron). – Service uses system service to manage logs. CIT 480: Securing Computer Systems Slide #21

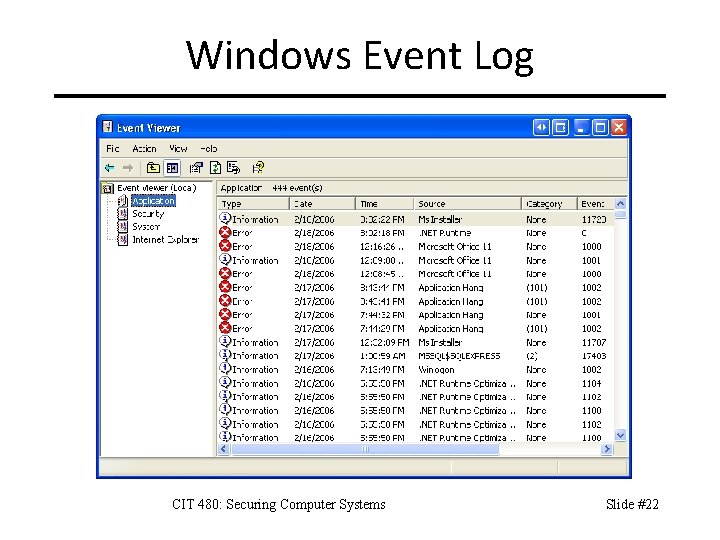
Windows Event Log CIT 480: Securing Computer Systems Slide #22

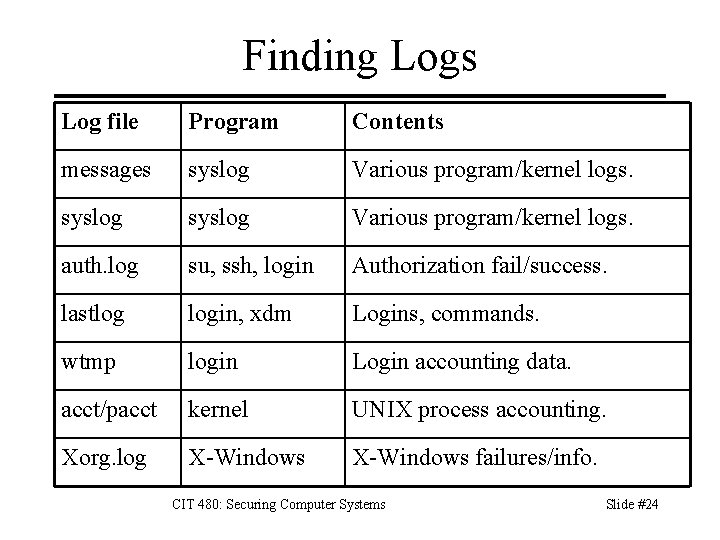
Finding UNIX Logs Most logs are stored under – /var/log – /var/adm Check syslog's configuration – /etc/syslog. conf To find other logs, read startup scripts – /etc/init. d/* – and manuals for services started by scripts. CIT 480: Securing Computer Systems Slide #23

Finding Logs Log file Program Contents messages syslog Various program/kernel logs. auth. log su, ssh, login Authorization fail/success. lastlog login, xdm Logins, commands. wtmp login Login accounting data. acct/pacct kernel UNIX process accounting. Xorg. log X-Windows failures/info. CIT 480: Securing Computer Systems Slide #24
![Example Syslog Messages Feb 11 10 17 01 localhost USRSBINCRON1971 root CMD runparts Example Syslog Messages Feb 11 10: 17: 01 localhost /USR/SBIN/CRON[1971]: (root) CMD ( run-parts](https://slidetodoc.com/presentation_image/580410e6ab6caf931344882c82ca7062/image-25.jpg)
Example Syslog Messages Feb 11 10: 17: 01 localhost /USR/SBIN/CRON[1971]: (root) CMD ( run-parts --report /etc/cron. hourly) Feb 11 10: 37: 22 localhost -- MARK -Feb 11 10: 51: 11 localhost dhclient: DHCPREQUEST on eth 1 to 192. 168. 1. 1 port 67 Feb 11 10: 51: 11 localhost dhclient: DHCPACK from 10. 42. 1. 1 Feb 11 10: 51: 11 localhost dhclient: bound to 10. 42. 1. 55 -- renewal in 35330 seconds. Feb 11 14: 37: 22 localhost -- MARK -Feb 11 14: 44: 21 localhost mysqld[7340]: 060211 14: 44: 21 /usr/sbin/mysqld: Normal shutdown Feb 12 04: 46: 42 localhost sshd[29093]: Address 218. 30. 101 maps to ns. thundernet. co. kr, but this does not map back to the address POSSIBLE BREAKIN ATTEMPT! Feb 12 04: 46: 44 localhost sshd[29097]: Invalid user matt from : : ffff: 218. 30. 101 CIT 480: Securing Computer Systems Slide #25

References 1. Anderson, Security Engineering 2 nd Edition, Wiley, 2008. 2. Goodrich and Tammasia, Introduction to Computer Security, Pearson, 2011. CIT 480: Securing Computer Systems Slide #26