CIT 480 Securing Computer Systems Network Security Concepts









- Slides: 34

CIT 480: Securing Computer Systems Network Security Concepts

Topics 1. 2. 3. 4. 5. 6. 7. Policies and Assurance Protocols and Layers Layer 2 Network Concepts MAC Spoofing ARP Spoofing Network Sniffing

Network Security Policy Usage policies – Define acceptable uses for organization members, partners, and other user classes. Risk analysis – Identify assets. – Evaluate importance. – Determine security policy for each asset based on importance.

Detecting Problems Change management process – Require security approval of network changes. Intrusion detection – Automated network and/or host based intrusion detection systems. Network scans – Scan network for rogue/missing machines. – Verify security status of each network device. Log monitoring – Monitor sensitive logs (e. g. firewall) in real time.

Network Mission Assurance 1. Asset identification 1. Systems and information assets. 2. Infrastructure model and control 1. Network diagrams and inventory database. 2. Change control. 3. Threat analysis and prediction 4. Response coordination 1. Attack identification. 2. Incident response team.

Network Hardening Network device integrity – Firmware and OS patches. – Password quality and change policies. Secure protocols – Secure management protocols: SSH, SNMP 3 + encrypt. – Encrypt all sensitive data + use MACs for integrity. Network design – Isolate sensitive/dangerous devices via firewalls, VLANs. – Compartmentalize different information asset classes. Network access control – Restrict access to Ethernet ports and wireless access.

Protocols A protocol defines the rules for communication between computers. Two primary types of protocols: Connectionless protocol • Sends data out as soon as there is enough data to be transmitted • E. g. , user datagram protocol (UDP) Connection-oriented protocol • • Provides a reliable connection stream between two nodes Consists of set up, transmission, and tear down phases Creates virtual circuit-switched network E. g. , transmission control protocol (TCP)

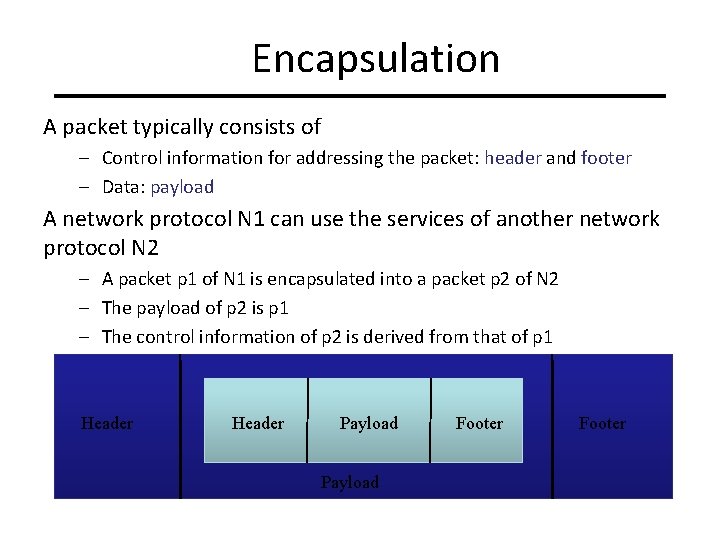
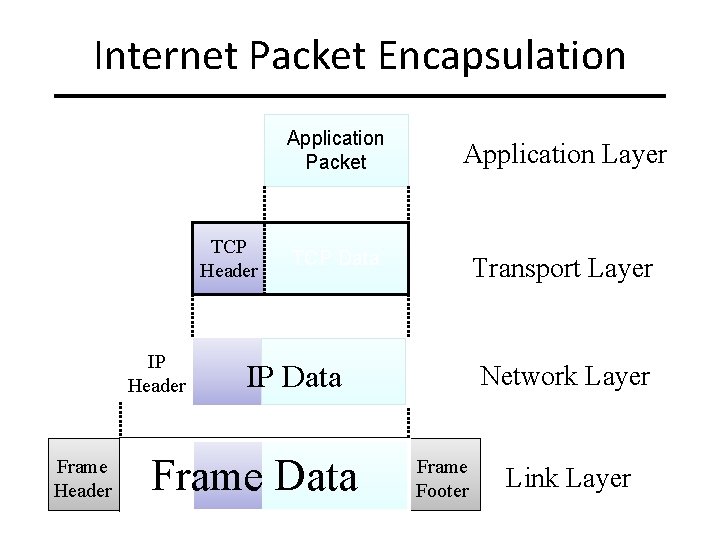
Encapsulation A packet typically consists of – Control information for addressing the packet: header and footer – Data: payload A network protocol N 1 can use the services of another network protocol N 2 – A packet p 1 of N 1 is encapsulated into a packet p 2 of N 2 – The payload of p 2 is p 1 – The control information of p 2 is derived from that of p 1 Header Payload Footer

Network Layers Network models typically use a stack of layers – Higher layers use the services of lower layers via encapsulation – A layer can be implemented in hardware or software – The bottommost layer must be in hardware A network device may implement several layers A communication channel between two nodes is established for each layer – Actual channel at the bottom layer – Virtual channel at higher layers

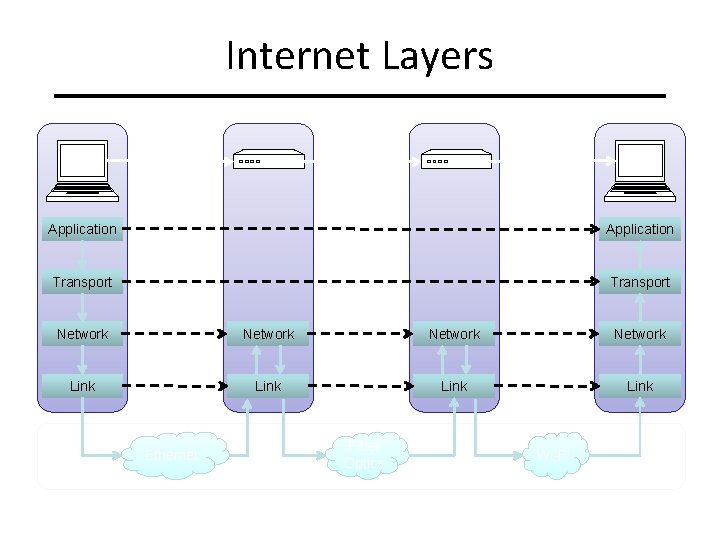
Internet Layers Application Transport Network Link Ethernet Fiber Optics Physical Layer Wi-Fi

Intermediate Layers Link layer – Local area network: Ethernet, Wi. Fi, optical fiber – 48 -bit media access control (MAC) addresses – Packets called frames Network layer – – Internet-wide communication Best effort transmission 32 -bit internet protocol (IP) addresses in IPv 4 128 -bit IP addresses in IPv 6 Transport layer – 16 -bit addresses (ports) for classes of applications – Connection-oriented transmission layer protocol (TCP) – Connectionless user datagram protocol (UDP)

Internet Packet Encapsulation TCP Header IP Header Frame Header Application Packet Application Layer TCP Data Transport Layer IP Data Frame Data Network Layer Frame Footer Link Layer

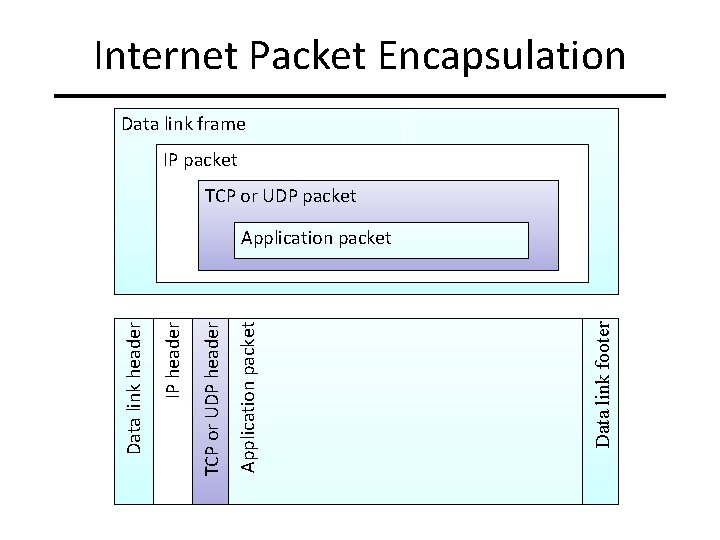
Internet Packet Encapsulation Data link frame IP packet TCP or UDP packet Data link footer Application packet TCP or UDP header IP header Data link header Application packet

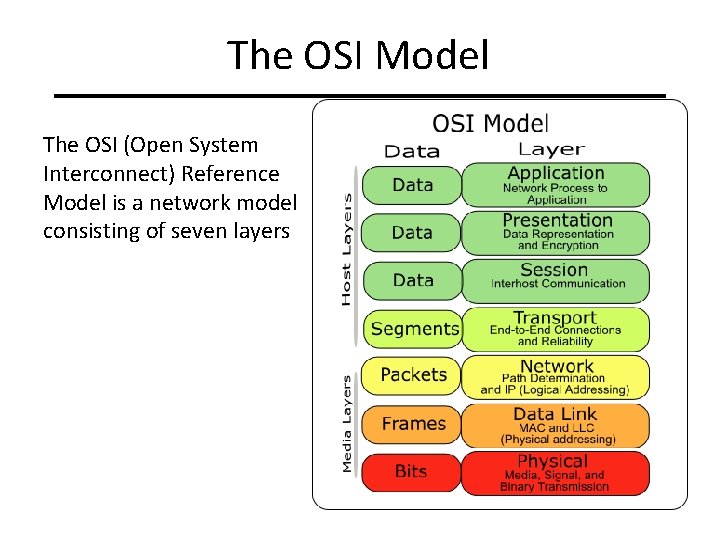
The OSI Model The OSI (Open System Interconnect) Reference Model is a network model consisting of seven layers

Network Interfaces Network interface: device connecting a computer to a network, such as an Ethernet or Wi. Fi card. – A computer may have multiple network interfaces. – Most local area networks, including Ethernet and Wi. Fi, broadcast frames, so all hosts on the LAN receive them. – In regular mode, each network interface sends only packets destined for it to OS for processing. – Network sniffing can be accomplished by configuring the network interface to send all frames (promiscuous mode) to OS for processing.

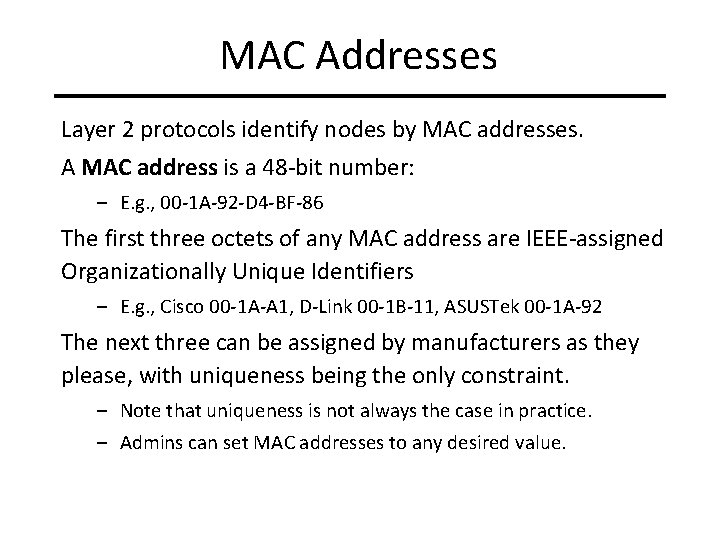
MAC Addresses Layer 2 protocols identify nodes by MAC addresses. A MAC address is a 48 -bit number: – E. g. , 00 -1 A-92 -D 4 -BF-86 The first three octets of any MAC address are IEEE-assigned Organizationally Unique Identifiers – E. g. , Cisco 00 -1 A-A 1, D-Link 00 -1 B-11, ASUSTek 00 -1 A-92 The next three can be assigned by manufacturers as they please, with uniqueness being the only constraint. – Note that uniqueness is not always the case in practice. – Admins can set MAC addresses to any desired value.

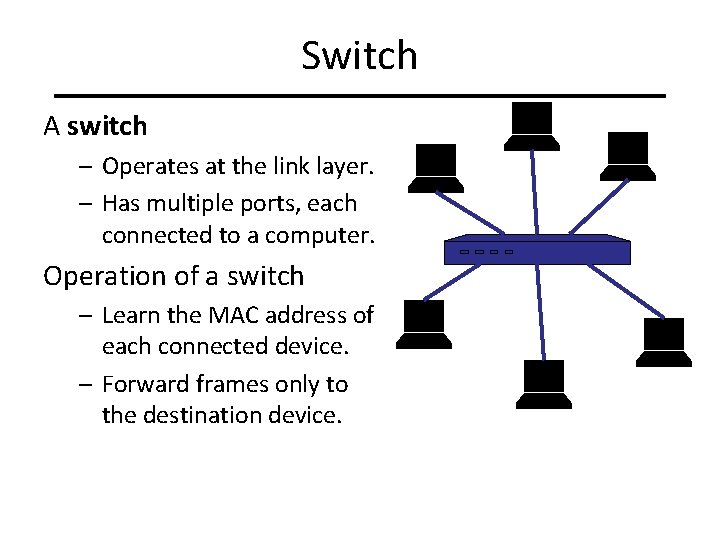
Switch A switch – Operates at the link layer. – Has multiple ports, each connected to a computer. Operation of a switch – Learn the MAC address of each connected device. – Forward frames only to the destination device.

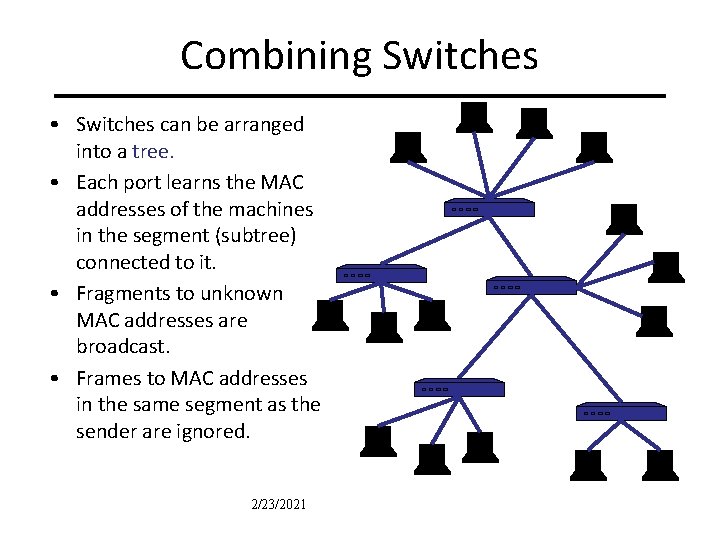
Combining Switches • Switches can be arranged into a tree. • Each port learns the MAC addresses of the machines in the segment (subtree) connected to it. • Fragments to unknown MAC addresses are broadcast. • Frames to MAC addresses in the same segment as the sender are ignored. 2/23/2021

MAC Address Filtering A switch can be configured to provide service only to machines with specific MAC addresses – Users must register devices with network admin. A MAC spoofing attack impersonates another PC – Find out MAC address of target machine. – Threat sets MAC address of his PC to that of target. – Turn off or unplug target machine. Countermeasures to MAC spoofing: – Block switch port when machine is turned off. – Disable duplicate MAC addresses.

Viewing and Changing MAC Addresses Viewing the MAC addresses of the interfaces of a machine – Linux: ifconfig – Windows: ipconfig /all Changing a MAC address in Linux – Stop the networking service: /etc/init. d/network stop – Change the MAC address: ifconfig eth 0 hw ether <MAC-address> – Start the networking service: /etc/init. d/network start Changing a MAC address in Windows – – Open the Network Connections applet Access the properties for the network interface Click “Configure …” In the advanced tab, change the network address to the desired value Changing a MAC address requires administrator privileges

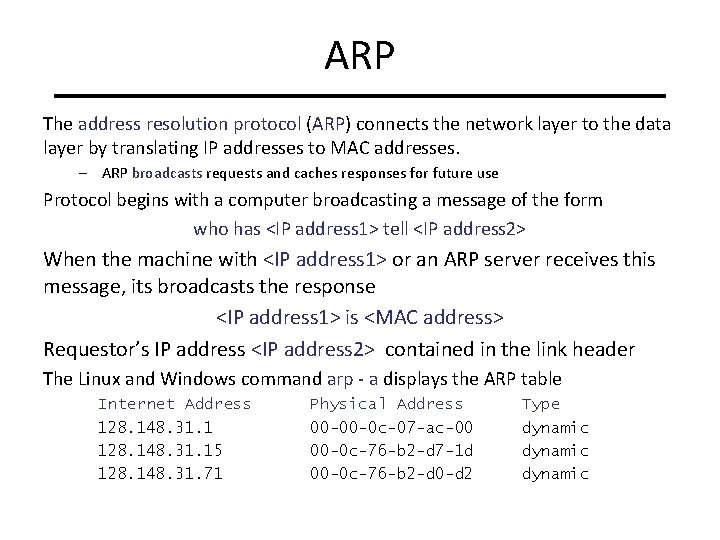
ARP The address resolution protocol (ARP) connects the network layer to the data layer by translating IP addresses to MAC addresses. – ARP broadcasts requests and caches responses for future use Protocol begins with a computer broadcasting a message of the form who has <IP address 1> tell <IP address 2> When the machine with <IP address 1> or an ARP server receives this message, its broadcasts the response <IP address 1> is <MAC address> Requestor’s IP address <IP address 2> contained in the link header The Linux and Windows command arp - a displays the ARP table Internet Address 128. 148. 31. 15 128. 148. 31. 71 Physical Address 00 -00 -0 c-07 -ac-00 00 -0 c-76 -b 2 -d 7 -1 d 00 -0 c-76 -b 2 -d 0 -d 2 Type dynamic

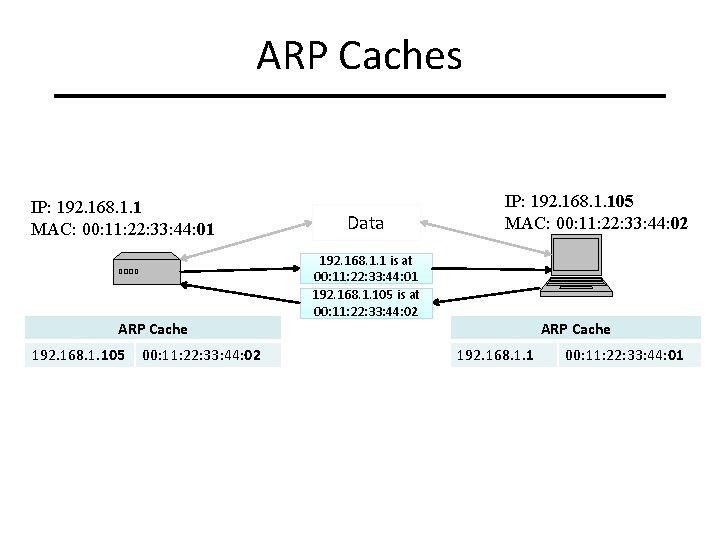
ARP Caches IP: 192. 168. 1. 1 MAC: 00: 11: 22: 33: 44: 01 ARP Cache 192. 168. 1. 105 00: 11: 22: 33: 44: 02 Data IP: 192. 168. 1. 105 MAC: 00: 11: 22: 33: 44: 02 192. 168. 1. 1 is at 00: 11: 22: 33: 44: 01 192. 168. 1. 105 is at 00: 11: 22: 33: 44: 02 ARP Cache 192. 168. 1. 1 00: 11: 22: 33: 44: 01

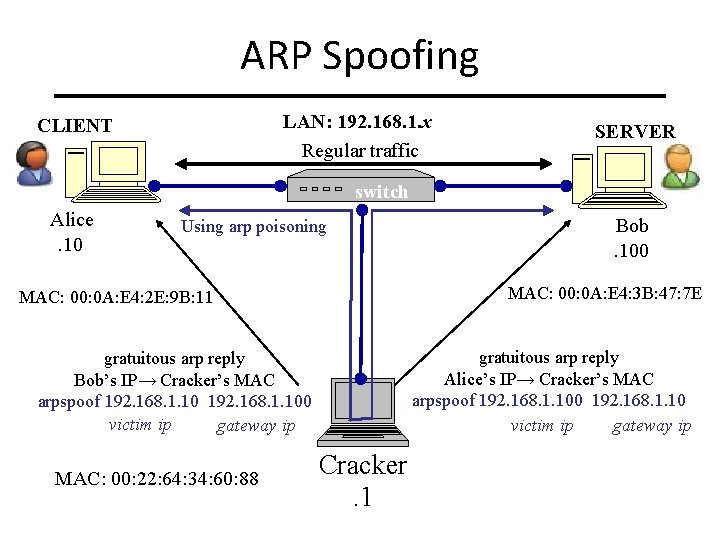
ARP Spoofing ARP table updated when ARP response is received – Requests are not tracked – ARP announcements are not authenticated, so A rogue machine can spoof other machines – Rogue sends ARP redirecting IP to its MAC – Network traffic destined for that IP sent to rogue machine by all hosts on subnet including switch. Countering ARP spoofing – Use static ARP table. – Requires admin to reconfigure each time a new host is added or a host is removed from the subnet.

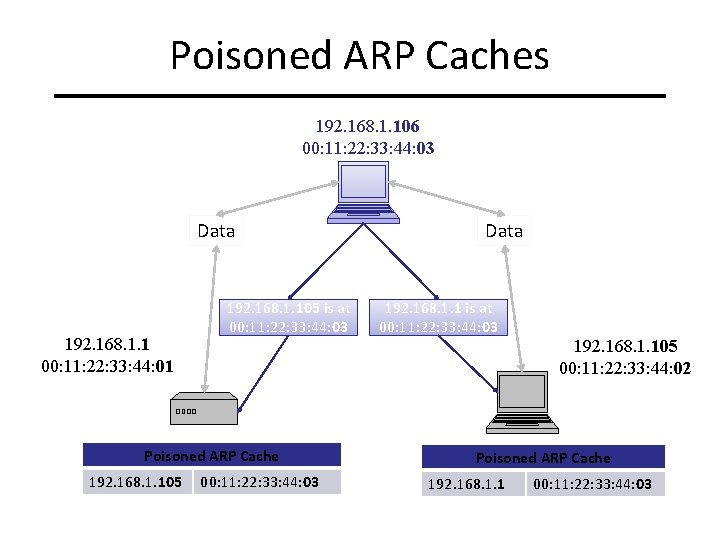
Poisoned ARP Caches 192. 168. 1. 106 00: 11: 22: 33: 44: 03 Data 192. 168. 1. 1 00: 11: 22: 33: 44: 01 192. 168. 1. 105 is at 00: 11: 22: 33: 44: 03 Poisoned ARP Cache 192. 168. 1. 105 00: 11: 22: 33: 44: 03 Data 192. 168. 1. 1 is at 00: 11: 22: 33: 44: 03 192. 168. 1. 105 00: 11: 22: 33: 44: 02 Poisoned ARP Cache 192. 168. 1. 1 00: 11: 22: 33: 44: 03

ARP Spoofing LAN: 192. 168. 1. x Regular traffic CLIENT SERVER switch Alice. 10 Using arp poisoning MAC: 00: 0 A: E 4: 3 B: 47: 7 E MAC: 00: 0 A: E 4: 2 E: 9 B: 11 gratuitous arp reply Alice’s IP→ Cracker’s MAC arpspoof 192. 168. 1. 100 192. 168. 1. 10 victim ip gateway ip gratuitous arp reply Bob’s IP→ Cracker’s MAC arpspoof 192. 168. 1. 100 victim ip gateway ip MAC: 00: 22: 64: 34: 60: 88 Bob. 100 Cracker. 1

Telnet Protocol (RFC 854) Telnet is a protocol that provides unencrypted communication to another machine to issue commands and receive output. – Allows remote shell access like ssh. – Sends whatever you type. – Prints whatever comes back. Telnet client can connect to any TCP port – Useful for testing TCP services (ASCII based protocols) like HTTP, SMTP, etc.

Packet Sniffing Packet sniffing is the process of intercepting and observing traffic on a network. – If packets are not encrypted, attacker can read confidential data, such as passwords, etc. Wired networks – Broadcast traffic is observable by all hosts. – Hubs send all packets to all hosts on subnet. – Switches send packets only to destination host, but ARP poisoning can let attacker see all packets. Wireless networks – Sniffer can see all packets.

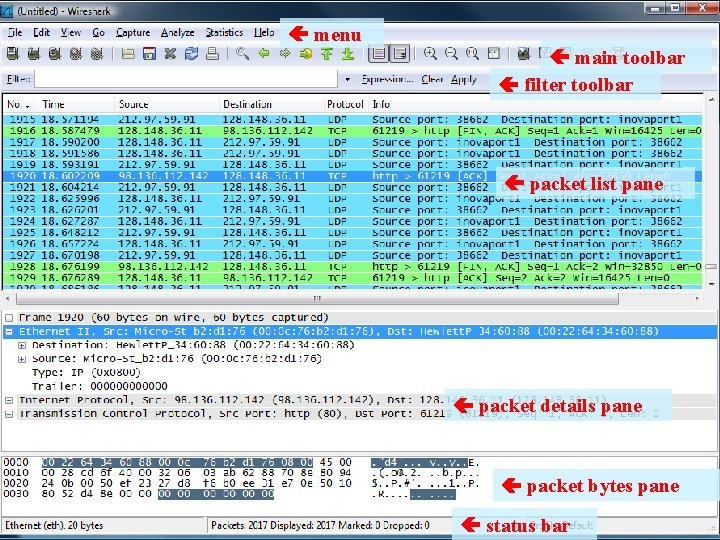
menu main toolbar filter toolbar packet list pane packet details pane packet bytes pane status bar

Packet Sniffer Applications Legitimate applications – Debug network problems. – Monitor network usage. – Network intrusion detection. Attacker applications – View confidential information. – Gather data required for other attacks, especially spoofing attacks.

Defending against Sniffing Encrypt traffic – Use application level encryption, e. g. HTTPS instead of HTTP, SSH instead of telnet. – Use network level encryption, like WPA 2 or IPsec, where possible. – Traffic patterns can still be observed. Use wired networks with switches – Use static ARP tables to avoid ARP spoofing. – Limits attacker to broadcasts and packets directed to attacker controlled machines.

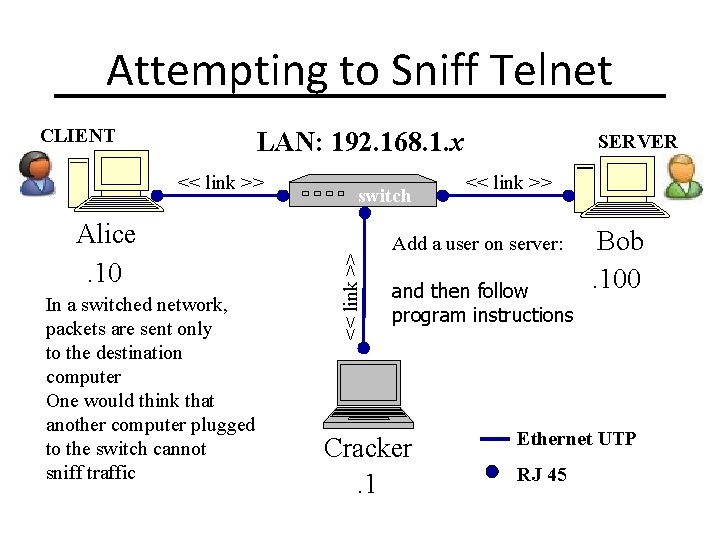
Attempting to Sniff Telnet CLIENT LAN: 192. 168. 1. x Alice. 10 In a switched network, packets are sent only to the destination computer One would think that another computer plugged to the switch cannot sniff traffic switch << link >> SERVER << link >> Add a user on server: adduser and then follow program instructions Cracker. 1 Bob. 100 Ethernet UTP RJ 45

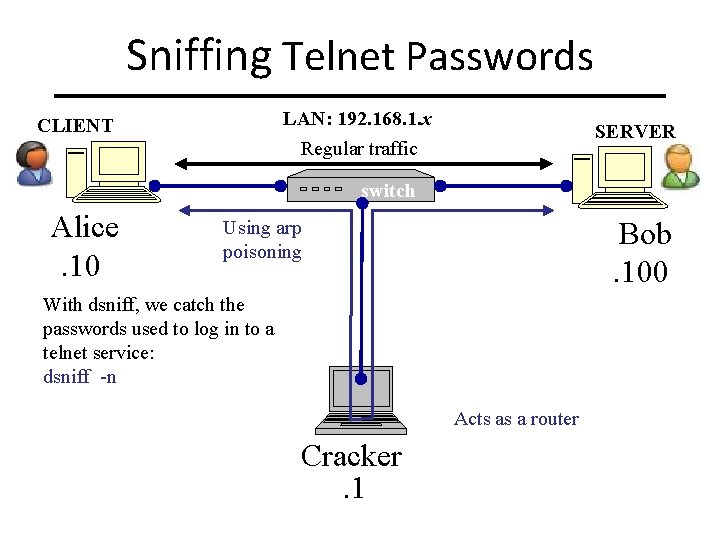
Sniffing Telnet Passwords LAN: 192. 168. 1. x Regular traffic CLIENT SERVER switch Alice. 10 Bob. 100 Using arp poisoning With dsniff, we catch the passwords used to log in to a telnet service: dsniff -n Acts as a router Cracker. 1

Key Points 1. Layer 2 concepts – Hosts identified by 48 -bit MAC addresses. – OS can spoof MACs by setting to any value. – Switches manage layer 2 traffic. 2. ARP translates IPs to MACs so packets can be delivered on hosts on local subnet. – There is no authentication. – ARP spoofing can be used to receive frames destined for other hosts. 3. Network sniffing – View confidential network traffic of other hosts. – ARP spoofing can let attacker sniff even if switches used.

References 1. Cisco, Network Security Policies: Best Practices White Paper, http: //www. cisco. com/c/en/us/support/docs/ava ilability/high-availability/13601 -secpol. html 2. Goodrich and Tammasia, Introduction to Computer Security, Pearson, 2011. 3. NSA, Hardening Network Infrastructure, http: //www. nsa. gov/ia/_files/factsheets/Hardeni ng_Network_Infrastructure_FS. pdf