CIT 480 Securing Computer Systems Capture the Flag


![Hexadecimal Encoding Encode each byte as 2 hex digits [0 -9 A-F] – 8 Hexadecimal Encoding Encode each byte as 2 hex digits [0 -9 A-F] – 8](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-3.jpg)
![Other Bases Base 32 – Digits: [A-Z 2 -7] – Useful when encoding must Other Bases Base 32 – Digits: [A-Z 2 -7] – Useful when encoding must](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-9.jpg)
![Looking Inside Files strings –a [-n N] filename – Find ASCII strings in binary Looking Inside Files strings –a [-n N] filename – Find ASCII strings in binary](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-16.jpg)


![XOR String Decryption >>> plain_array = [] >>> for letter in ciphertext: . . XOR String Decryption >>> plain_array = [] >>> for letter in ciphertext: . .](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-29.jpg)
![XOR Encryption Function >>> def xorcrypt(string, key): . . . crypt_array = []. . XOR Encryption Function >>> def xorcrypt(string, key): . . . crypt_array = []. .](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-30.jpg)


- Slides: 38

CIT 480: Securing Computer Systems Capture the Flag CIT 480: Securing Computer Systems Slide #1

Topics 1. 2. 3. 4. 5. 6. Threats Cybercrimes Attacks, Attack Surface, and Exploits Malware Vulnerabilities Mitigations and Patches CIT 480: Securing Computer Systems Slide #2
![Hexadecimal Encoding Encode each byte as 2 hex digits 0 9 AF 8 Hexadecimal Encoding Encode each byte as 2 hex digits [0 -9 A-F] – 8](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-3.jpg)
Hexadecimal Encoding Encode each byte as 2 hex digits [0 -9 A-F] – 8 -bit byte ranges from 0 to 255. – Hex digits equivalently range from 00 to FF. – Case insensitive: can use [0 -9 a-f] or [0 -9 A-F]. Text encoding requires 2 x space of binary – Humanly readable format for binary data. – Used by hex editors, wireshark, etc. – URL-encoding is hexadecimal encoding where each byte is preceded by % symbol. Sometimes called base 16 encoding. CIT 480: Securing Computer Systems Slide #3

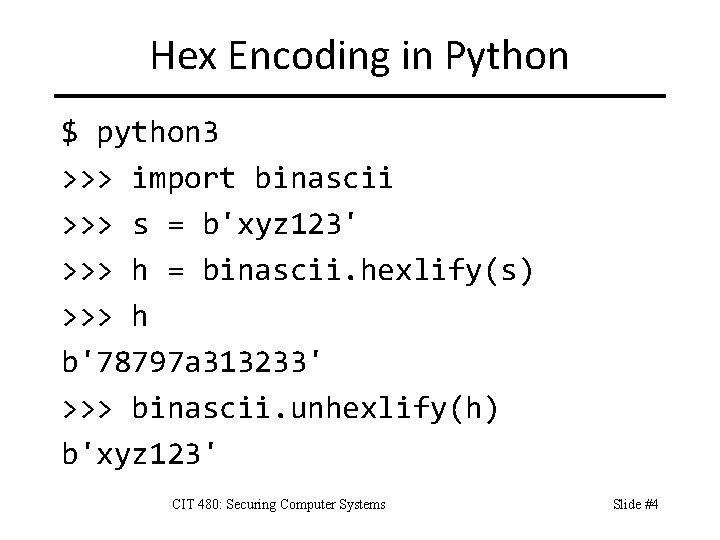
Hex Encoding in Python $ python 3 >>> import binascii >>> s = b'xyz 123' >>> h = binascii. hexlify(s) >>> h b'78797 a 313233' >>> binascii. unhexlify(h) b'xyz 123' CIT 480: Securing Computer Systems Slide #4

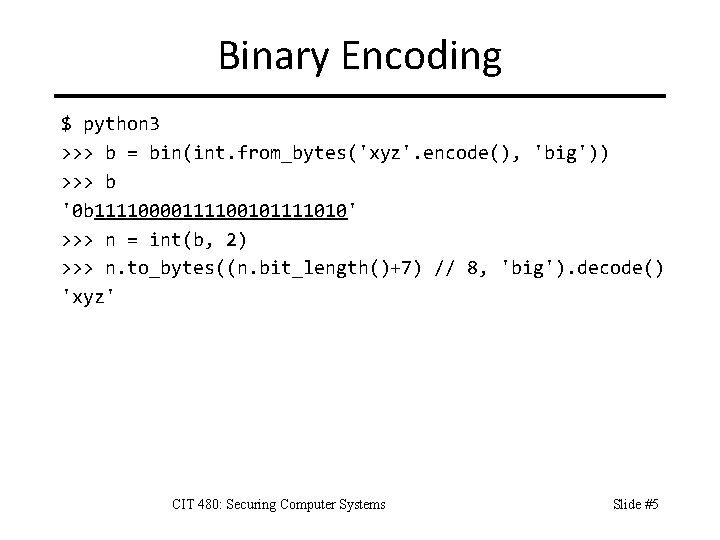
Binary Encoding $ python 3 >>> b = bin(int. from_bytes('xyz'. encode(), 'big')) >>> b '0 b 11110000111100101111010' >>> n = int(b, 2) >>> n. to_bytes((n. bit_length()+7) // 8, 'big'). decode() 'xyz' CIT 480: Securing Computer Systems Slide #5

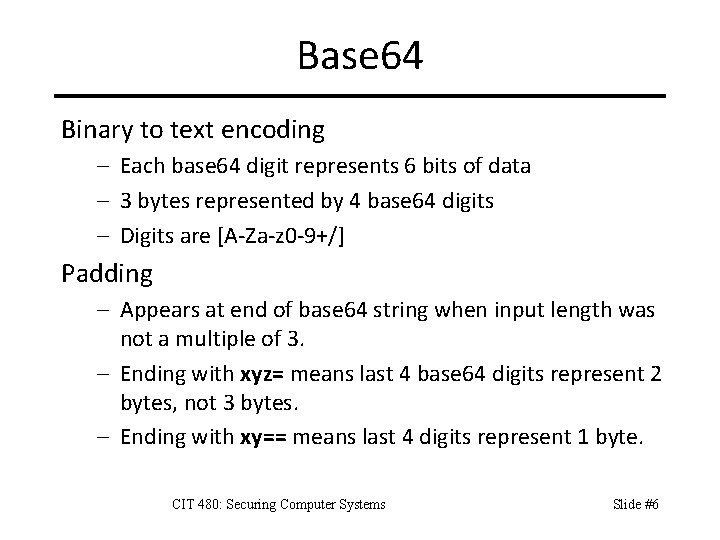
Base 64 Binary to text encoding – Each base 64 digit represents 6 bits of data – 3 bytes represented by 4 base 64 digits – Digits are [A-Za-z 0 -9+/] Padding – Appears at end of base 64 string when input length was not a multiple of 3. – Ending with xyz= means last 4 base 64 digits represent 2 bytes, not 3 bytes. – Ending with xy== means last 4 digits represent 1 byte. CIT 480: Securing Computer Systems Slide #6

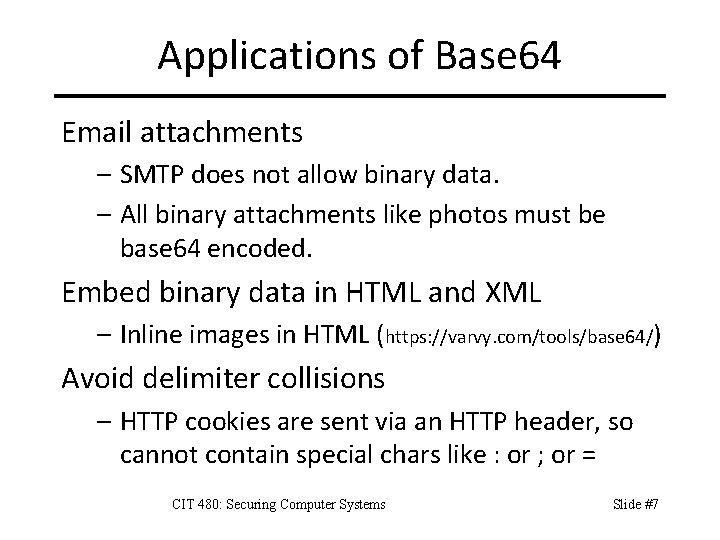
Applications of Base 64 Email attachments – SMTP does not allow binary data. – All binary attachments like photos must be base 64 encoded. Embed binary data in HTML and XML – Inline images in HTML (https: //varvy. com/tools/base 64/) Avoid delimiter collisions – HTTP cookies are sent via an HTTP header, so cannot contain special chars like : or ; or = CIT 480: Securing Computer Systems Slide #7

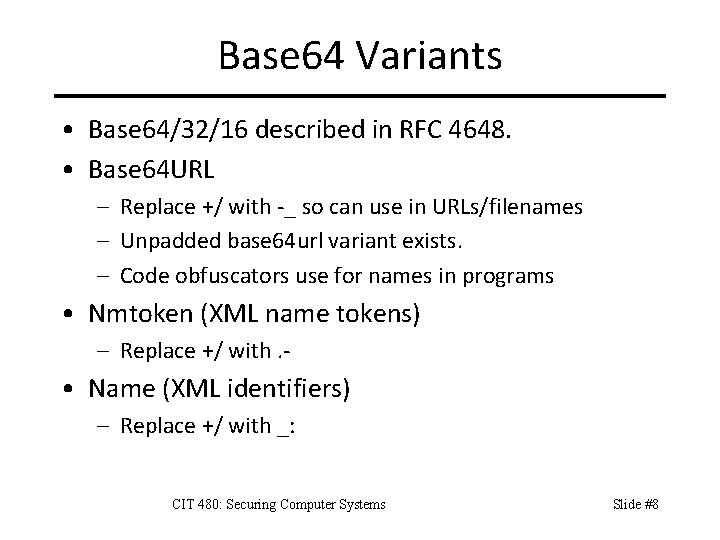
Base 64 Variants • Base 64/32/16 described in RFC 4648. • Base 64 URL – Replace +/ with -_ so can use in URLs/filenames – Unpadded base 64 url variant exists. – Code obfuscators use for names in programs • Nmtoken (XML name tokens) – Replace +/ with. - • Name (XML identifiers) – Replace +/ with _: CIT 480: Securing Computer Systems Slide #8
![Other Bases Base 32 Digits AZ 2 7 Useful when encoding must Other Bases Base 32 – Digits: [A-Z 2 -7] – Useful when encoding must](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-9.jpg)
Other Bases Base 32 – Digits: [A-Z 2 -7] – Useful when encoding must be case insensitive, such as when used as filenames on Windows. Base 36 – Digits: [A-Z 0 -9] Base 58 – Digits: Base 64 – similar chars(O/0, 1/l), +, / – Used for encoding large integers for human manual data entry. CIT 480: Securing Computer Systems Slide #9

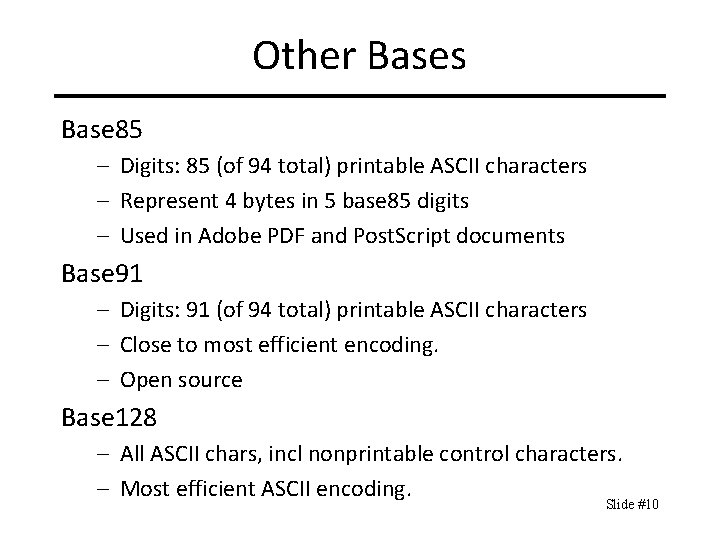
Other Bases Base 85 – Digits: 85 (of 94 total) printable ASCII characters – Represent 4 bytes in 5 base 85 digits – Used in Adobe PDF and Post. Script documents Base 91 – Digits: 91 (of 94 total) printable ASCII characters – Close to most efficient encoding. – Open source Base 128 – All ASCII chars, incl nonprintable control characters. – Most efficient ASCII encoding. Slide #10

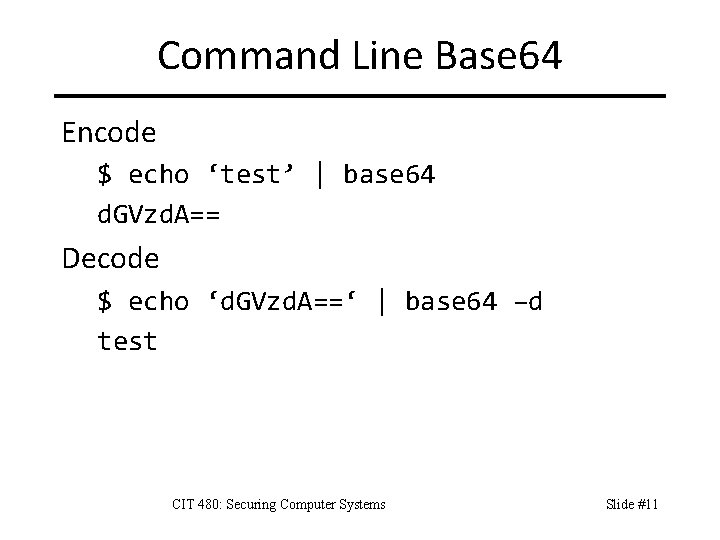
Command Line Base 64 Encode $ echo ‘test’ | base 64 d. GVzd. A== Decode $ echo ‘d. GVzd. A==‘ | base 64 –d test CIT 480: Securing Computer Systems Slide #11

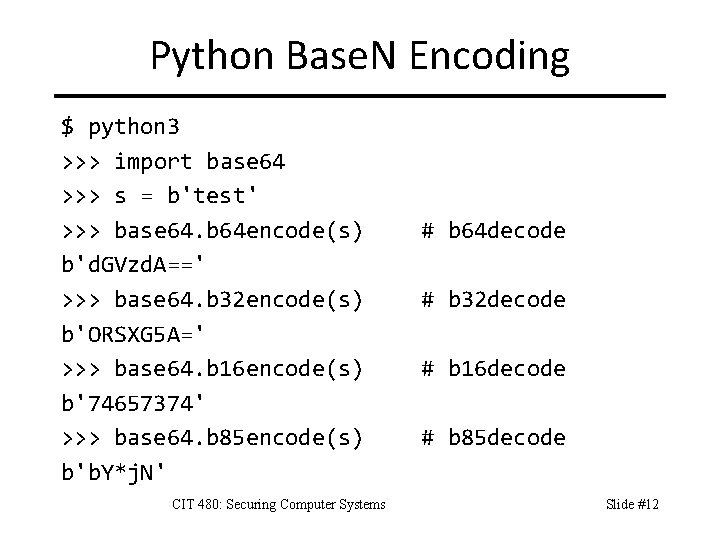
Python Base. N Encoding $ python 3 >>> import base 64 >>> s = b'test' >>> base 64. b 64 encode(s) b'd. GVzd. A==' >>> base 64. b 32 encode(s) b'ORSXG 5 A=' >>> base 64. b 16 encode(s) b'74657374' >>> base 64. b 85 encode(s) b'b. Y*j. N' CIT 480: Securing Computer Systems # b 64 decode # b 32 decode # b 16 decode # b 85 decode Slide #12

Files and Formats File types can be identified by – Suffix: Windows uses to determine which application to launch. – Magic number: The first few bytes of a file specify the type of the file. The file command on UNIX uses this to identify file types. – Content-Type header: Web browsers use this HTTP response header to determine how to process file. Types are specified using MIME types like text/plain or image/jpg. CIT 480: Securing Computer Systems Slide #13

Magic Numbers Type Suffix Magic Number (Bytes) ASCII Content GIF image . gif 47 49 46 38 39 GIF 89 PNG image . png 89 50 43 47 . PNG MP 3 audio . mp 3 49 44 33 ID 3 Windows DLL . dll 4 D 5 A MZ Word Document . docx 50 4 B 03 04 PK PDF document . pdf 25 50 44 46 %PDF ZIP archive . zip 50 4 B 03 04 PK CIT 480: Securing Computer Systems Slide #14

Office Documents are ZIPs $ unzip Door. Schedule. docx Archive: Door. Schedule. docx inflating: [Content_Types]. xml inflating: _rels/. rels inflating: word/_rels/document. xml. rels inflating: word/document. xml inflating: word/endnotes. xml inflating: word/footnotes. xml inflating: word/theme 1. xml inflating: word/settings. xml … CIT 480: Securing Computer Systems Slide #15
![Looking Inside Files strings a n N filename Find ASCII strings in binary Looking Inside Files strings –a [-n N] filename – Find ASCII strings in binary](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-16.jpg)
Looking Inside Files strings –a [-n N] filename – Find ASCII strings in binary file – N is minimum string length (N=4 by default) strings filename | grep pattern – Some files have many strings. – Grep lets you search for a specific pattern CIT 480: Securing Computer Systems Slide #16

Hex Editors Hex editor programs: ghex, bless, xxd, and many more Slide #17

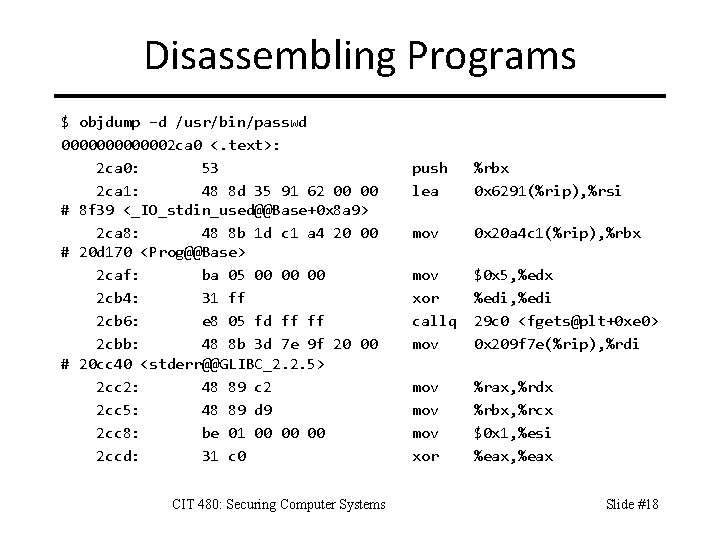
Disassembling Programs $ objdump –d /usr/bin/passwd 0000002 ca 0 <. text>: 2 ca 0: 53 2 ca 1: 48 8 d 35 91 62 00 00 # 8 f 39 <_IO_stdin_used@@Base+0 x 8 a 9> 2 ca 8: 48 8 b 1 d c 1 a 4 20 00 # 20 d 170 <Prog@@Base> 2 caf: ba 05 00 00 00 2 cb 4: 31 ff 2 cb 6: e 8 05 fd ff ff 2 cbb: 48 8 b 3 d 7 e 9 f 20 00 # 20 cc 40 <stderr@@GLIBC_2. 2. 5> 2 cc 2: 48 89 c 2 2 cc 5: 48 89 d 9 2 cc 8: be 01 00 00 00 2 ccd: 31 c 0 CIT 480: Securing Computer Systems push lea %rbx 0 x 6291(%rip), %rsi mov 0 x 20 a 4 c 1(%rip), %rbx mov xor callq mov $0 x 5, %edx %edi, %edi 29 c 0 <fgets@plt+0 xe 0> 0 x 209 f 7 e(%rip), %rdi mov mov xor %rax, %rdx %rbx, %rcx $0 x 1, %esi %eax, %eax Slide #18

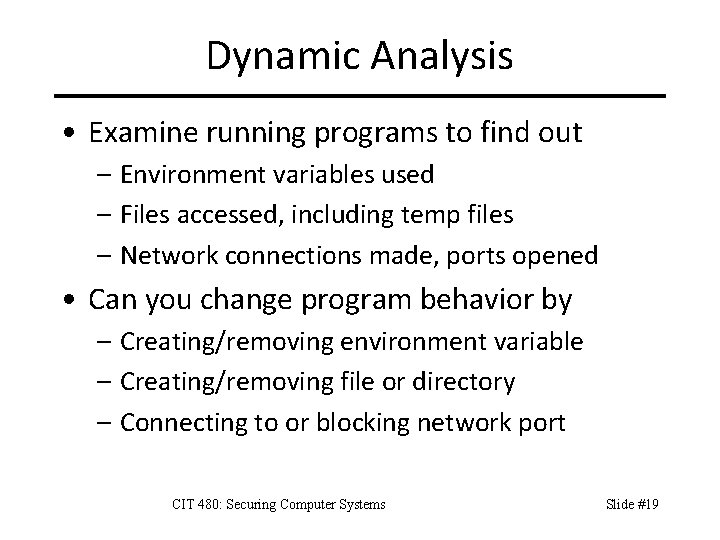
Dynamic Analysis • Examine running programs to find out – Environment variables used – Files accessed, including temp files – Network connections made, ports opened • Can you change program behavior by – Creating/removing environment variable – Creating/removing file or directory – Connecting to or blocking network port CIT 480: Securing Computer Systems Slide #19

Library Calls $ ltrace /bin/ls # ltrace –p allows tracing of existing process __libc_start_main(0 x 402 a 00, 1, 0 x 7 ffe 86 fe 6028, 0 x 413 bb 0 <unfinished. . . > strrchr("/bin/ls", '/') = "/ls" setlocale(LC_ALL, "" <unfinished. . . > getopt_long(1, 0 x 7 ffcb 77 b 8 ee 8, "abcdfghiklmnopqrstuvw: x. ABCDFGHI: ". . . , 0 x 414 da 0, -1) = -1 getenv("LS_BLOCK_SIZE") = nil getenv(“TZ") = nil readdir(0 x 196 cca 0) = 0 x 196 ccd 0 strlen("bin") =3 malloc(4) = 0 x 1974 ce 0 memcpy(0 x 1974 ce 0, "bin�", 4) = 0 x 1974 ce 0 CIT 480: Securing Computer Systems Slide #20

System Calls $ strace /bin/ls # strace –p allows tracing of existing process execve("/bin/ls", ["/bin/ls"], [/* 111 vars */]) = 0 brk(NULL) = 0 x 1162000 access("/etc/ld. so. nohwcap", F_OK) = -1 ENOENT (No such file or directory) access("/etc/ld. so. preload", R_OK) = -1 ENOENT (No such file or directory) open("/etc/ld. so. cache", O_RDONLY|O_CLOEXEC) = 3 fstat(3, {st_mode=S_IFREG|0644, st_size=130618, . . . }) = 0 mmap(NULL, 130618, PROT_READ, MAP_PRIVATE, 3, 0) = 0 x 7 f 5643 cd 5000 close(3) =0 access("/etc/ld. so. nohwcap”, F_OK) = -1 ENOENT CIT 480: Securing Computer Systems Slide #21

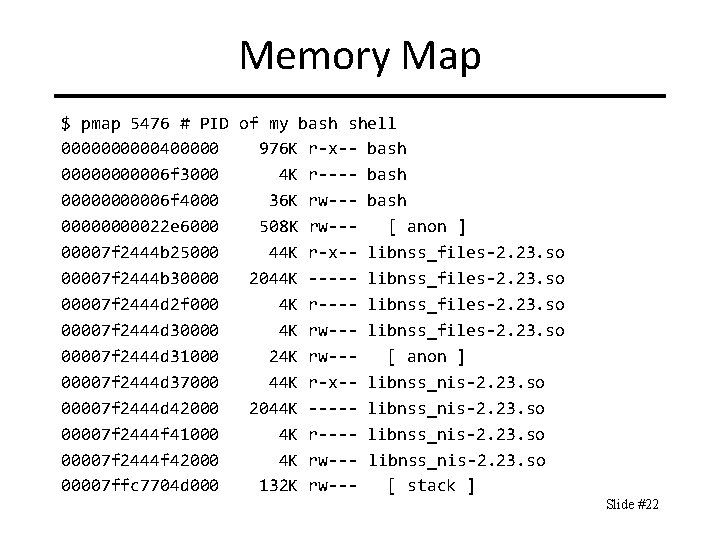
Memory Map $ pmap 5476 # PID of my bash shell 00000400000 976 K r-x-- bash 000006 f 3000 4 K r---- bash 000006 f 4000 36 K rw--- bash 0000022 e 6000 508 K rw--[ anon ] 00007 f 2444 b 25000 44 K r-x-- libnss_files-2. 23. so 00007 f 2444 b 30000 2044 K ----- libnss_files-2. 23. so 00007 f 2444 d 2 f 000 4 K r---- libnss_files-2. 23. so 00007 f 2444 d 30000 4 K rw--- libnss_files-2. 23. so 00007 f 2444 d 31000 24 K rw--[ anon ] 00007 f 2444 d 37000 44 K r-x-- libnss_nis-2. 23. so 00007 f 2444 d 42000 2044 K ----- libnss_nis-2. 23. so 00007 f 2444 f 41000 4 K r---- libnss_nis-2. 23. so 00007 f 2444 f 42000 4 K rw--- libnss_nis-2. 23. so 00007 ffc 7704 d 000 132 K rw--[ stack ] Slide #22

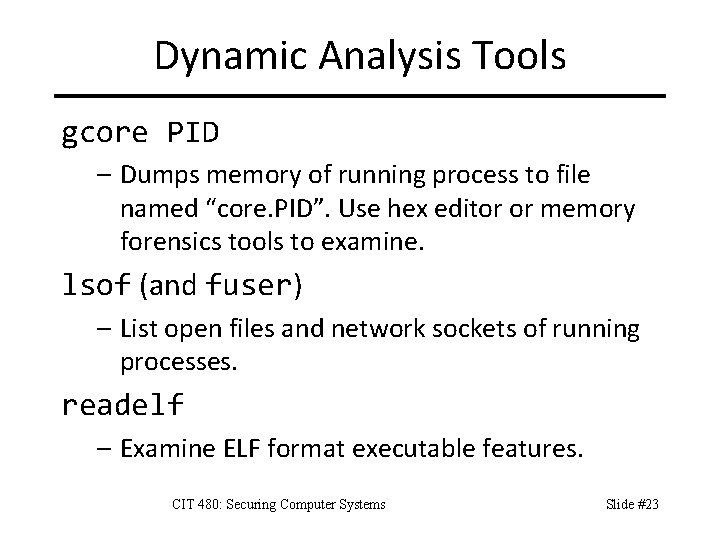
Dynamic Analysis Tools gcore PID – Dumps memory of running process to file named “core. PID”. Use hex editor or memory forensics tools to examine. lsof (and fuser) – List open files and network sockets of running processes. readelf – Examine ELF format executable features. CIT 480: Securing Computer Systems Slide #23

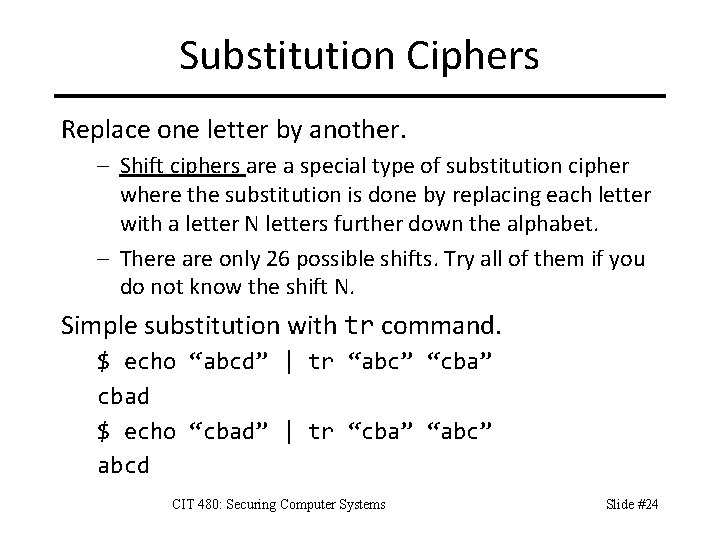
Substitution Ciphers Replace one letter by another. – Shift ciphers are a special type of substitution cipher where the substitution is done by replacing each letter with a letter N letters further down the alphabet. – There are only 26 possible shifts. Try all of them if you do not know the shift N. Simple substitution with tr command. $ echo “abcd” | tr “abc” “cba” cbad $ echo “cbad” | tr “cba” “abc” abcd CIT 480: Securing Computer Systems Slide #24

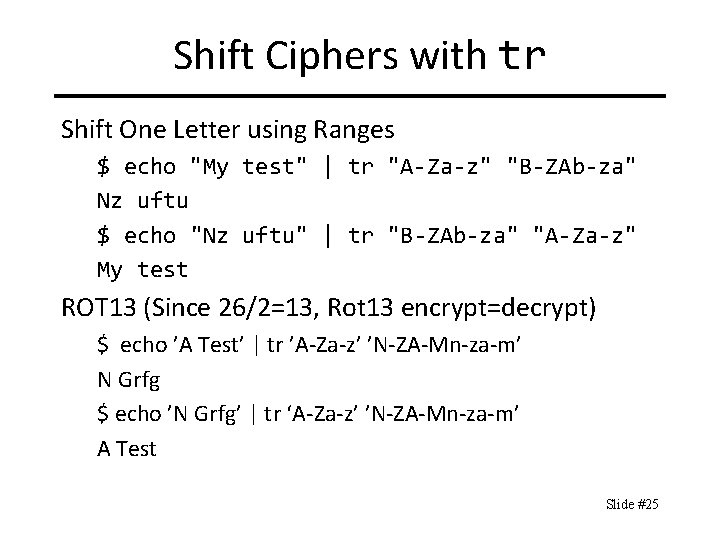
Shift Ciphers with tr Shift One Letter using Ranges $ echo "My test" | tr "A-Za-z" "B-ZAb-za" Nz uftu $ echo "Nz uftu" | tr "B-ZAb-za" "A-Za-z" My test ROT 13 (Since 26/2=13, Rot 13 encrypt=decrypt) $ echo ’A Test’ | tr ’A-Za-z’ ’N-ZA-Mn-za-m’ N Grfg $ echo ’N Grfg’ | tr ‘A-Za-z’ ’N-ZA-Mn-za-m’ A Test Slide #25

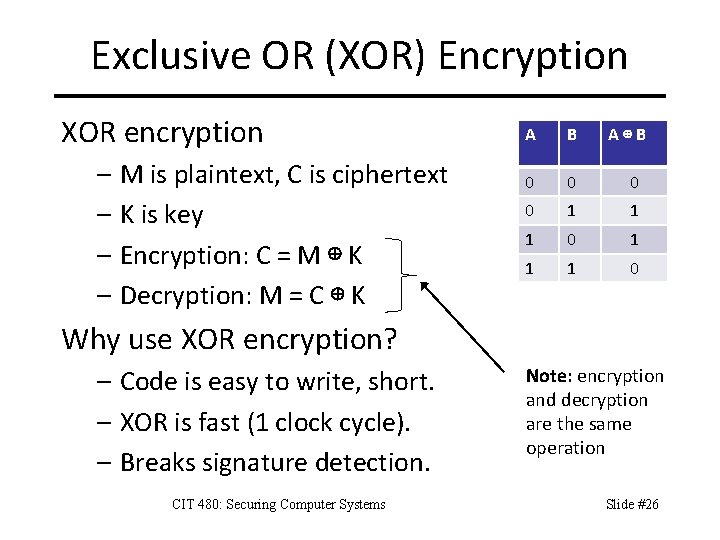
Exclusive OR (XOR) Encryption XOR encryption – M is plaintext, C is ciphertext – K is key – Encryption: C = M ⊕ K – Decryption: M = C ⊕ K A B A⊕B 0 0 1 1 1 0 Why use XOR encryption? – Code is easy to write, short. – XOR is fast (1 clock cycle). – Breaks signature detection. CIT 480: Securing Computer Systems Note: encryption and decryption are the same operation Slide #26

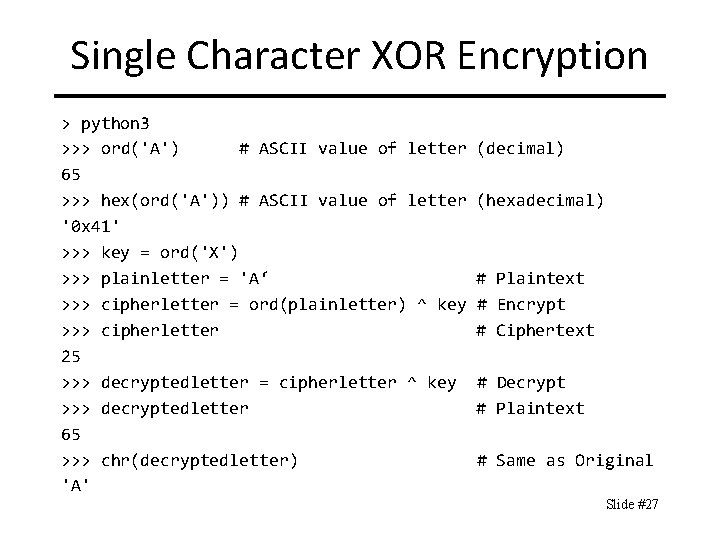
Single Character XOR Encryption > python 3 >>> ord('A') # ASCII value of letter 65 >>> hex(ord('A')) # ASCII value of letter '0 x 41' >>> key = ord('X') >>> plainletter = 'A‘ >>> cipherletter = ord(plainletter) ^ key >>> cipherletter 25 >>> decryptedletter = cipherletter ^ key >>> decryptedletter 65 >>> chr(decryptedletter) 'A' (decimal) (hexadecimal) # Plaintext # Encrypt # Ciphertext # Decrypt # Plaintext # Same as Original Slide #27

XOR String Encryption >>> plaintext = "Gaul is divided into 3 parts. " >>> cipher_array = [] >>> key = ord('X') >>> for letter in plaintext: . . . cipher_array. append(chr(ord(letter) ^ key)). . . >>> ciphertext = ''. join(cipher_array) >>> ciphertext 'x 1 f 9 -4 x 1+x<1. 1<=<x 16, 7 xkx(9*, +v' CIT 480: Securing Computer Systems Slide #28
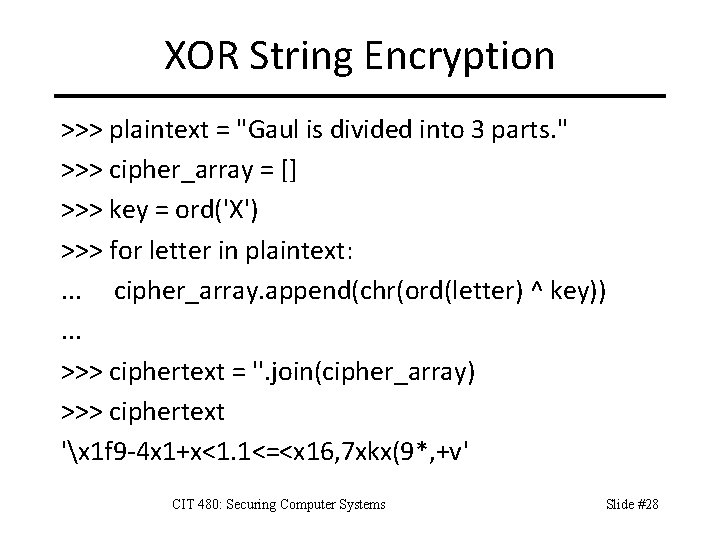
![XOR String Decryption plainarray for letter in ciphertext XOR String Decryption >>> plain_array = [] >>> for letter in ciphertext: . .](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-29.jpg)
XOR String Decryption >>> plain_array = [] >>> for letter in ciphertext: . . . plain_array. append(chr(ord(letter) ^ key)). . . >>> plaintext = ''. join(plain_array) >>> plaintext 'Gaul is divided into 3 parts. ' CIT 480: Securing Computer Systems Slide #29
![XOR Encryption Function def xorcryptstring key cryptarray XOR Encryption Function >>> def xorcrypt(string, key): . . . crypt_array = []. .](https://slidetodoc.com/presentation_image_h/7fe11a1da8797d5d50d06fb71890cb0e/image-30.jpg)
XOR Encryption Function >>> def xorcrypt(string, key): . . . crypt_array = []. . . for letter in string: . . . crypt_array. append(chr(ord(letter) ^ key)). . . return ''. join(crypt_array). . . >>> ciphertext = xorcrypt("Gaul is divided into 3 parts. ", ord('A')) >>> ciphertext 'x 06 4 -a(2 a%(7(%$%a(/5. ara 1 352 o' >>> plaintext = xorcrypt(ciphertext, ord('A')) >>> plaintext 'Gaul is divided into 3 parts. ' CIT 480: Securing Computer Systems Slide #30

Brute Force XOR Decryption >>> # Try all 8 -bit keys. >>> # Write one file for each decryption. >>> for key in range(0, 256): . . . txt = xorcrypt(ciphertext, key). . . fn = str(key) + '. txt'. . . fh = open(fn, 'w'). . . fh. write(txt). . . fh. close() CIT 480: Securing Computer Systems Slide #31

Brute Force XOR Decryption Examine 256 candidate decryptions. – Look for ASCII text if expect text message. – Use “file *. txt” to determine file type if not sure of type of data. Very few candidate decryption files will have a valid magic number. – If executable, try running in sandbox. – Otherwise, use appropriate software to see the document, image, audio, etc. CIT 480: Securing Computer Systems Slide #32

XOR Extensions • XOR encryption can encrypt binary data – Not just ASCII text. – No longer need ord() and chr() functions. • XOR encryption keys not limited to 8 -bits. – Longer keys encrypt multiple letters at once. – Longer keys make brute force take longer. CIT 480: Securing Computer Systems Slide #33

Network Analysis CIT 480: Securing Computer Systems Slide #34

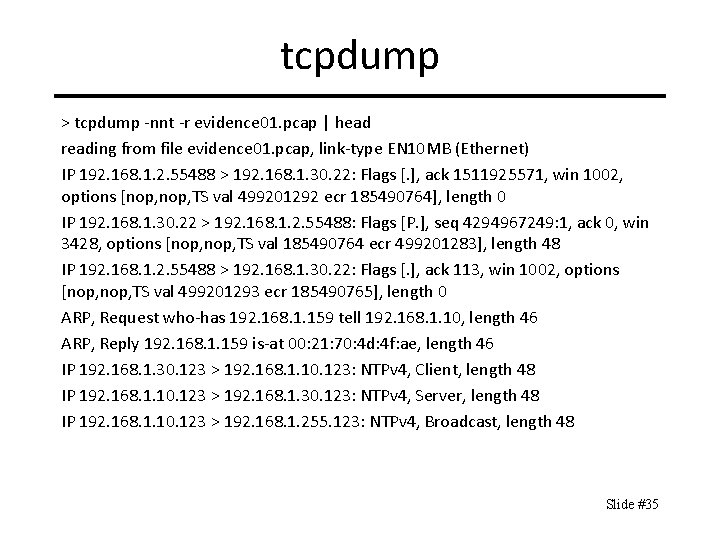
tcpdump > tcpdump -nnt -r evidence 01. pcap | head reading from file evidence 01. pcap, link-type EN 10 MB (Ethernet) IP 192. 168. 1. 2. 55488 > 192. 168. 1. 30. 22: Flags [. ], ack 1511925571, win 1002, options [nop, TS val 499201292 ecr 185490764], length 0 IP 192. 168. 1. 30. 22 > 192. 168. 1. 2. 55488: Flags [P. ], seq 4294967249: 1, ack 0, win 3428, options [nop, TS val 185490764 ecr 499201283], length 48 IP 192. 168. 1. 2. 55488 > 192. 168. 1. 30. 22: Flags [. ], ack 113, win 1002, options [nop, TS val 499201293 ecr 185490765], length 0 ARP, Request who-has 192. 168. 1. 159 tell 192. 168. 1. 10, length 46 ARP, Reply 192. 168. 1. 159 is-at 00: 21: 70: 4 d: 4 f: ae, length 46 IP 192. 168. 1. 30. 123 > 192. 168. 1. 10. 123: NTPv 4, Client, length 48 IP 192. 168. 1. 10. 123 > 192. 168. 1. 30. 123: NTPv 4, Server, length 48 IP 192. 168. 1. 10. 123 > 192. 168. 1. 255. 123: NTPv 4, Broadcast, length 48 Slide #35

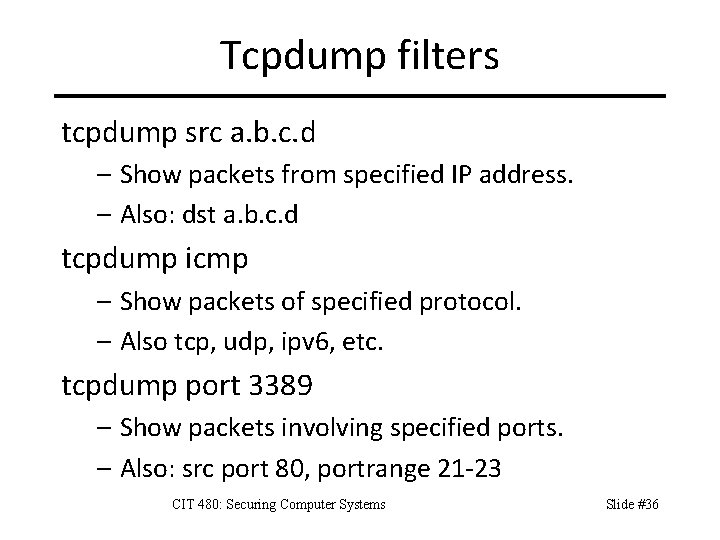
Tcpdump filters tcpdump src a. b. c. d – Show packets from specified IP address. – Also: dst a. b. c. d tcpdump icmp – Show packets of specified protocol. – Also tcp, udp, ipv 6, etc. tcpdump port 3389 – Show packets involving specified ports. – Also: src port 80, portrange 21 -23 CIT 480: Securing Computer Systems Slide #36

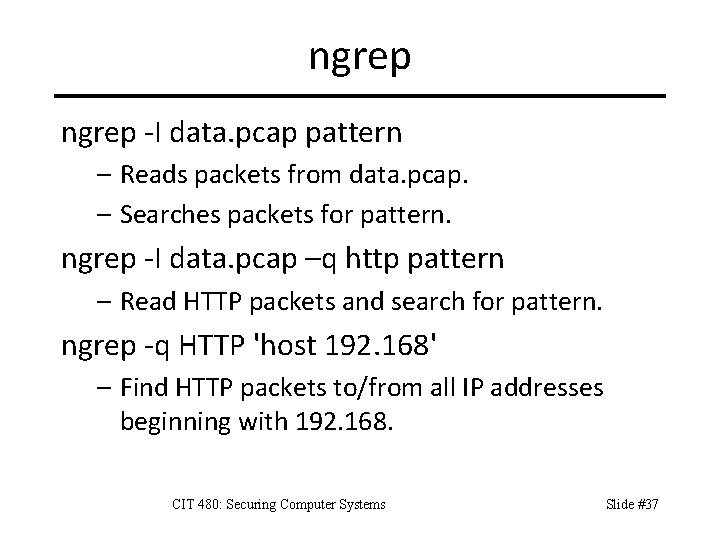
ngrep -I data. pcap pattern – Reads packets from data. pcap. – Searches packets for pattern. ngrep -I data. pcap –q http pattern – Read HTTP packets and search for pattern. ngrep -q HTTP 'host 192. 168' – Find HTTP packets to/from all IP addresses beginning with 192. 168. CIT 480: Securing Computer Systems Slide #37

Resources 1. CTF Tools, https: //github. com/zardus/ctf-tools 2. CTF Writeups, https: //github. com/ctfs 3. Cybersecurity Resources, https: //faculty. cs. nku. edu/~waldenj/securityresources. html CIT 480: Securing Computer Systems Slide #38