Securing Channels of Communication Secure Sockets Layer SSL







- Slides: 13

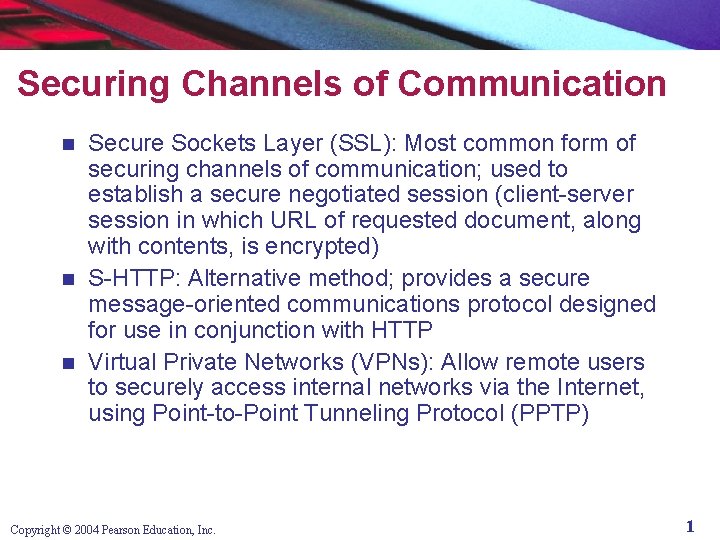
Securing Channels of Communication Secure Sockets Layer (SSL): Most common form of securing channels of communication; used to establish a secure negotiated session (client-server session in which URL of requested document, along with contents, is encrypted) n S-HTTP: Alternative method; provides a secure message-oriented communications protocol designed for use in conjunction with HTTP n Virtual Private Networks (VPNs): Allow remote users to securely access internal networks via the Internet, using Point-to-Point Tunneling Protocol (PPTP) n Copyright © 2004 Pearson Education, Inc. 1

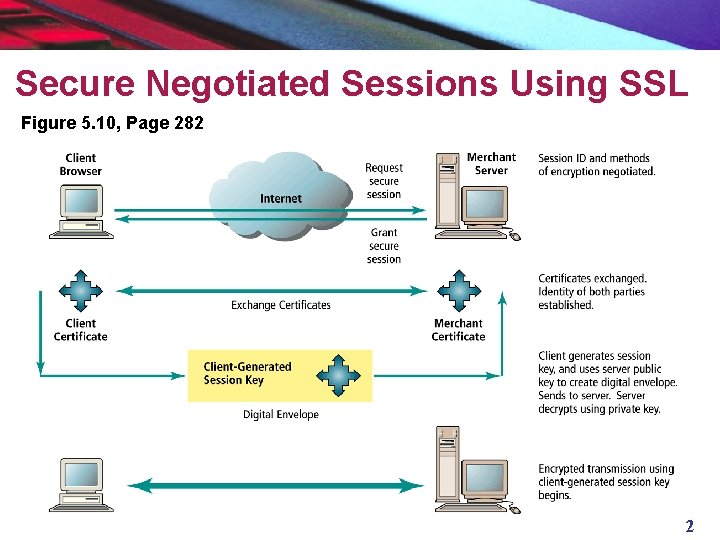
Secure Negotiated Sessions Using SSL Figure 5. 10, Page 282 2

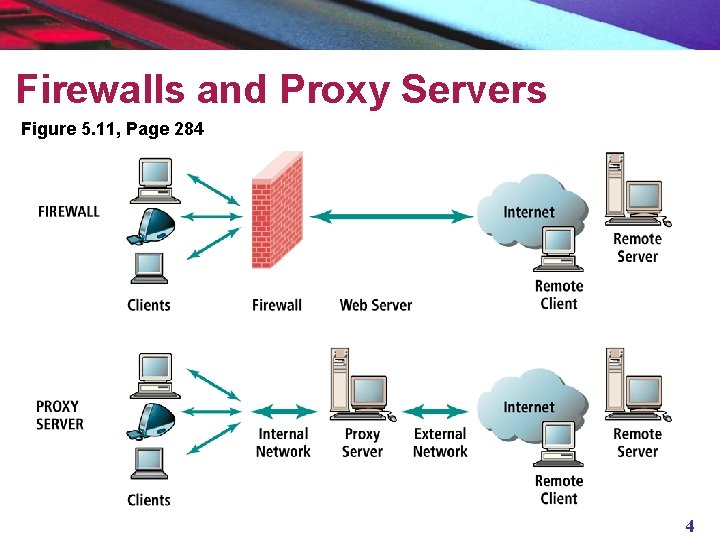
Protecting Networks: Firewalls and Proxy Servers Firewall: Software application that acts as a filter between a company’s private network and the Internet n Firewall methods include: § Packet filters § Application gateways n Proxy servers: Software servers that handle all communications originating from for being sent to the Internet (act as “spokesperson” or “bodyguard” for the organization) n Copyright © 2004 Pearson Education, Inc. 3

Firewalls and Proxy Servers Figure 5. 11, Page 284 4

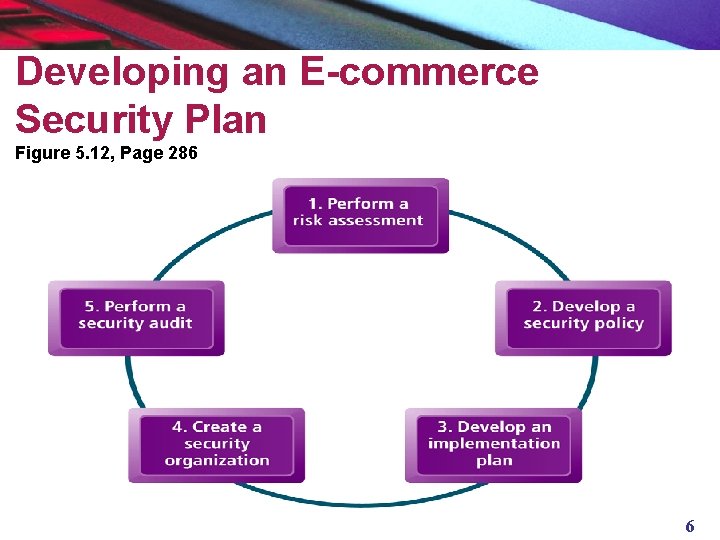
A Security Plan: Management Policies n Steps in developing a security plan: § Perform risk assessment – assessment of risks and points of vulnerability § Develop security policy – set of statements prioritizing information risks, identifying acceptable risk targets and identifying mechanisms for achieving targets § Develop implementation plan – action steps needed to achieve security plan goals § Create security organization – in charge of security; educates and trains users, keeps management aware of security issues; administers access controls, authentication procedures and authorization policies § Perform security audit – review of security practices and procedures Copyright © 2004 Pearson Education, Inc. 5

Developing an E-commerce Security Plan Figure 5. 12, Page 286 6

Insight on Business: Tiger Teams – Hiring Hackers to Locate Threats Tiger team: Group whose sole job activity is attempting to break into a site n Originated in 1970 s with U. S. Air Force n By 1980 s-1990 s, had spread to corporate arena n Most use just “white hats” and refuse to hire known grey or black hats n Copyright © 2004 Pearson Education, Inc. 7

The Role of Laws and Public Policy n n n New laws have granted local and national authorities new tools and mechanisms for identifying, tracing and prosecuting cybercriminals National Infrastructure Protection Center – unit within FBI whose mission is to identify and combat threats against U. S. technology and telecommunications infrastructure USA Patriot Act Homeland Security Act Government policies and controls on encryption software Copyright © 2004 Pearson Education, Inc. 8

E-commerce Security Legislation Table 5. 3, Page 290 9

Government Efforts to Regulate and Control Encryption Table 5. 4, Page 292 10

OECD Guidelines n 2002 Organization for Economic Cooperation and Development (OECD) Guidelines for the Security of Information Systems and Networks has Nine principles: § Awareness § Responsibility § Response § Ethics § Democracy § Risk assessment § Security design and implementation § Security management § Reassessment Copyright © 2004 Pearson Education, Inc. 11

Veri. Sign: The Web’s Security Blanket Page 294 12

Case Study: Veri. Sign: The Web’s Security Blanket n n n University of Pittsburgh’s e-Store an example of Internet trust (security) services offered by Veri. Sign has grown early expertise in public key encryption into related Internet security infrastructure businesses Dominates the Web site encryption services market with over 75% market share Provides secure payment services Provides businesses and government agencies with managed security services Provides domain name registration, and manages the. com and. net domains Copyright © 2004 Pearson Education, Inc. 13