CIT 480 Securing Computer Systems Secure Design Principles






















- Slides: 37

CIT 480: Securing Computer Systems Secure Design Principles

Topics 1. Attack Surface 2. Attack Trees 3. Secure Design Principles

Attack Surface Attack surface: the set of ways an application can be attacked. Used to measure attackability of a system. – The larger the attack surface of a system, the more likely an attacker is to exploit its vulnerabilities and the more damage is likely to result from attack. – Compare to measuring vulnerability by counting number of reported security bugs. – Both are useful measures of security, but have very different meanings.

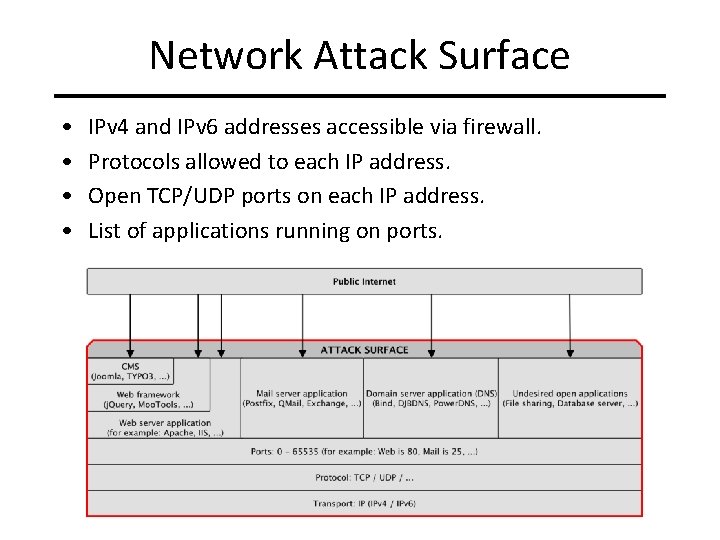
Network Attack Surface • • IPv 4 and IPv 6 addresses accessible via firewall. Protocols allowed to each IP address. Open TCP/UDP ports on each IP address. List of applications running on ports.

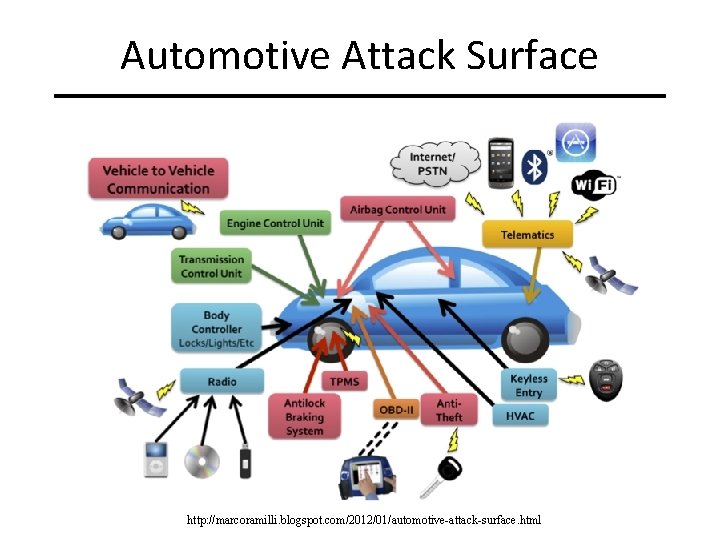
Automotive Attack Surface http: //marcoramilli. blogspot. com/2012/01/automotive-attack-surface. html

Why Attack Surface Reduction? If your code is perfect, why worry? – All code has a nonzero probability of containing vulnerabilities. – Even if code is perfect now, new vulns arise. • Format string vulnerability was discovered in 1999. • A particular application was immune to XML injection until you added an XML storage feature. Allows focus on more dangerous code. – ASR eliminates unnecessary exposures. – Allows focus on required exposures.

Attack Surface Reduction 1. Reduce code that executes by default. 1. Disable features not all users need. 2. Restrict who can access the code. 1. Require authentication to access. 2. Request admin to access dangerous functions. 3. Reduce privilege level of code. 1. Prefer code running as user to admin. 2. Prefer SETGID to SETUID.

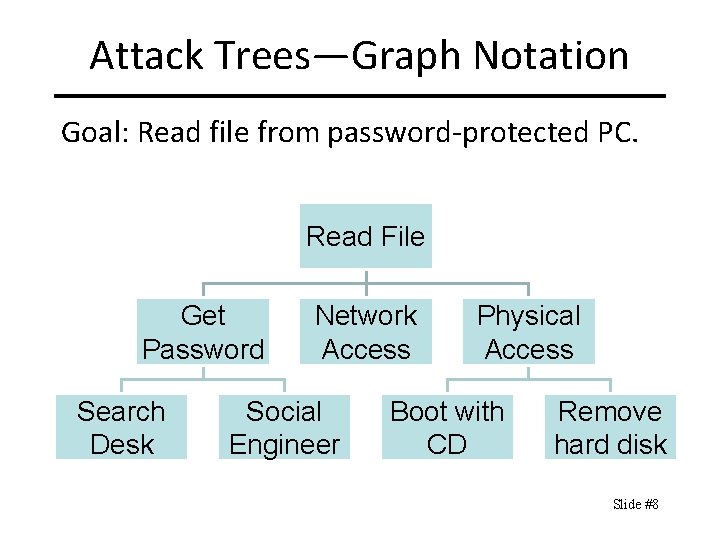
Attack Trees—Graph Notation Goal: Read file from password-protected PC. Read File Get Password Search Desk Network Access Social Engineer Physical Access Boot with CD Remove hard disk Slide #8

Attack Trees—Text Notation Goal: Read message sent from one PC to another. 1. Convince sender to reveal message. 1. 1 Blackmail. 1. 2 Bribe. 2. Read message when entered on sender’s PC. 1. 1 Visually monitor PC screen. 1. 2 Monitor EM radiation from screen. 3. Read message when stored on receiver’s PC. 1. 1 Get physical access to hard drive. 1. 2 Infect user with spyware. 4. Read message in transit. 1. 1 Sniff network. 1. 2 Usurp control of mail server. Slide #9

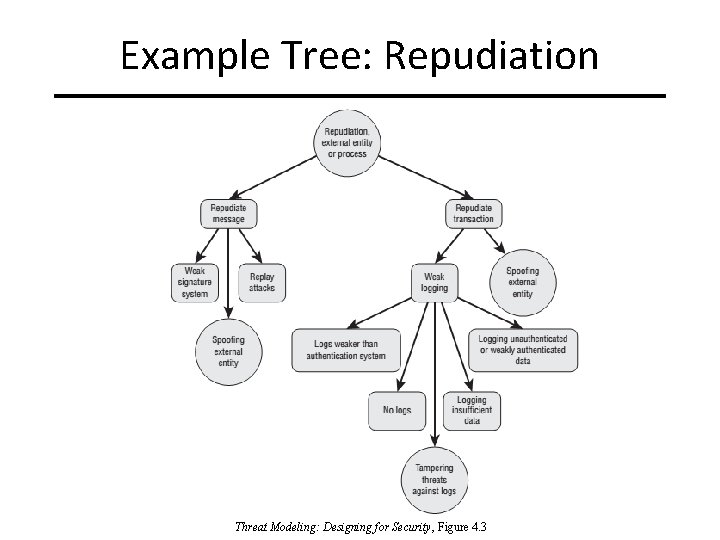
Example Tree: Repudiation Threat Modeling: Designing for Security, Figure 4. 3

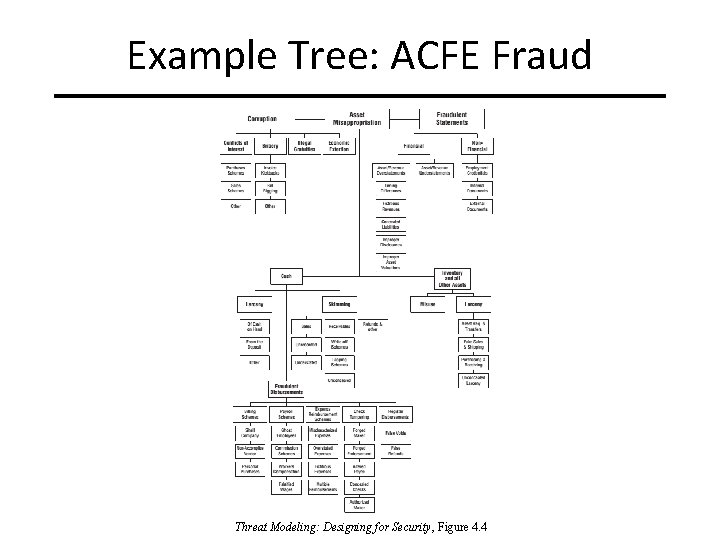
Example Tree: ACFE Fraud Threat Modeling: Designing for Security, Figure 4. 4

Security Design Principles 1. 2. 3. 4. 5. 6. 7. 8. Least Privilege Fail-Safe Defaults Economy of Mechanism Complete Mediation Open Design Separation of Privilege Least Common Mechanism Psychological Acceptability

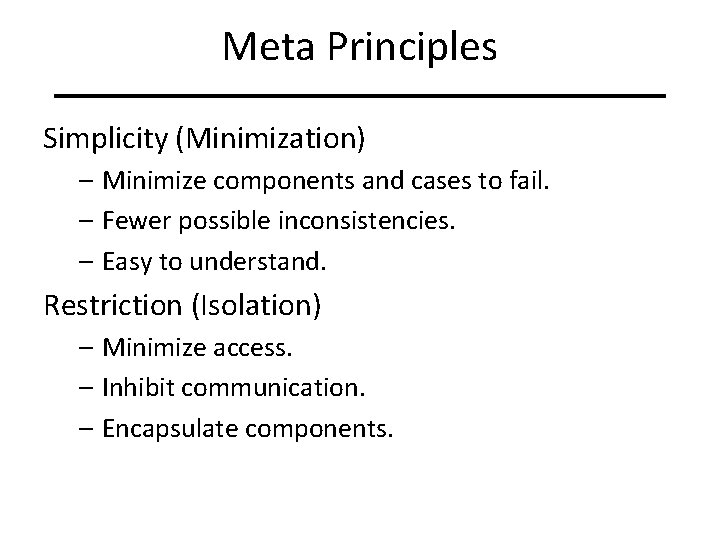
Meta Principles Simplicity (Minimization) – Minimize components and cases to fail. – Fewer possible inconsistencies. – Easy to understand. Restriction (Isolation) – Minimize access. – Inhibit communication. – Encapsulate components.

Least Privilege A subject should be given only those privileges necessary to complete its task. – Function, not identity, controls. – Rights added as needed, discarded after use. – Minimal protection domain. Most common violation: – Running as administrator or root. – Use runas or sudo instead.

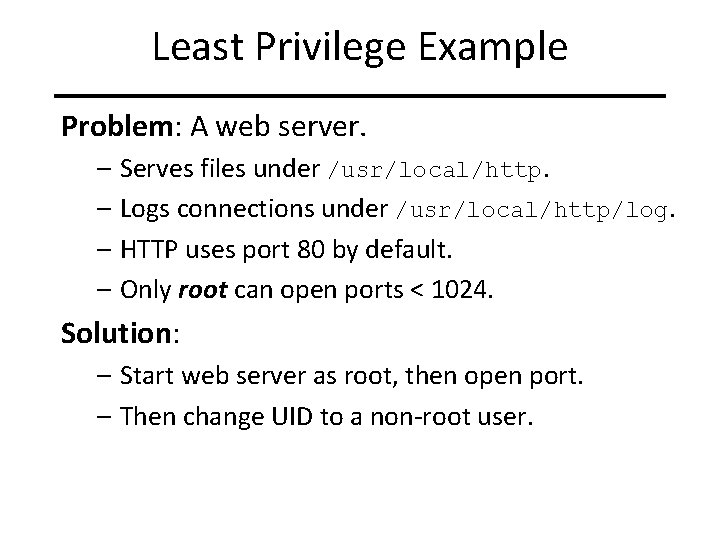
Least Privilege Example Problem: A web server. – Serves files under /usr/local/http. – Logs connections under /usr/local/http/log. – HTTP uses port 80 by default. – Only root can open ports < 1024. Solution: – Start web server as root, then open port. – Then change UID to a non-root user.

How do we run with least privilege? List required resources and special tasks – Files – Network connections – Change user account – Backup data Determine what access you need to resources – Access Control model – Do you need create, read, write, append, etc. ?

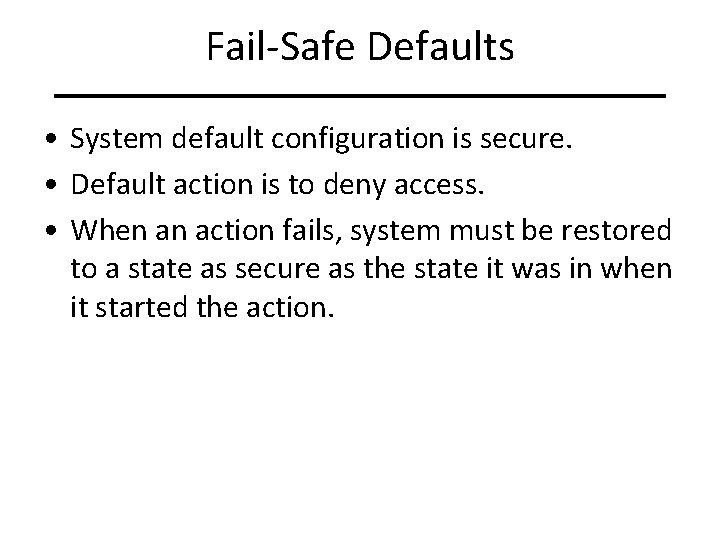
Fail-Safe Defaults • System default configuration is secure. • Default action is to deny access. • When an action fails, system must be restored to a state as secure as the state it was in when it started the action.

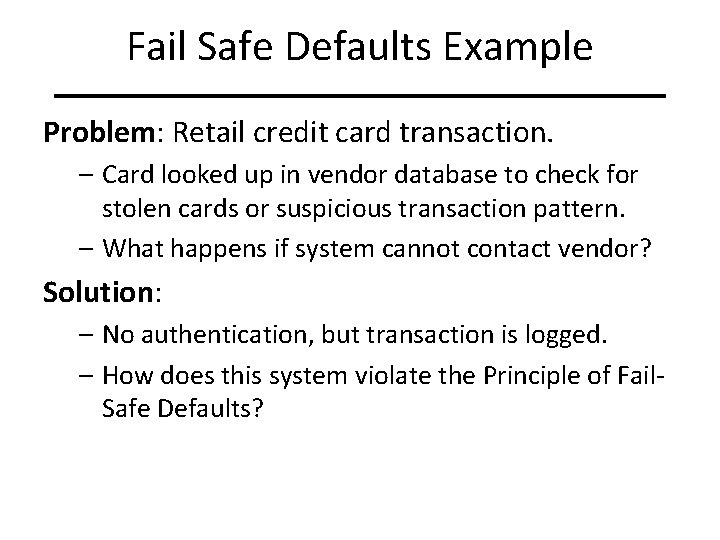
Fail Safe Defaults Example Problem: Retail credit card transaction. – Card looked up in vendor database to check for stolen cards or suspicious transaction pattern. – What happens if system cannot contact vendor? Solution: – No authentication, but transaction is logged. – How does this system violate the Principle of Fail. Safe Defaults?

Fail Safe Defaults Example Problem: MS Office Macro Viruses. – MS office files can contain Visual Basic code (macros. ) – MS Office automatically executes certain macros when opening a MS Office file. – Users can turn off automatic execution. – Don’t mix code and data! Solution: – MS Office XP has automatic execution of macros turned off by default. – While the solution is a fail-safe default, does it follow least privilege too?

Economy of Mechanism Keep system as simple as possible. – Use the simplest solution that works. – Fewer cases and components to fail. – Can review all code of a small application. Reuse known secure solutions – i. e. , don’t write your own cryptography.

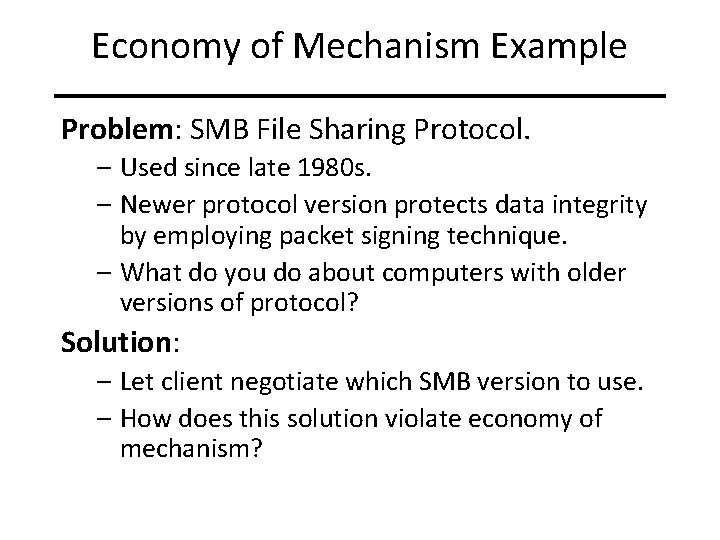
Economy of Mechanism Example Problem: SMB File Sharing Protocol. – Used since late 1980 s. – Newer protocol version protects data integrity by employing packet signing technique. – What do you do about computers with older versions of protocol? Solution: – Let client negotiate which SMB version to use. – How does this solution violate economy of mechanism?

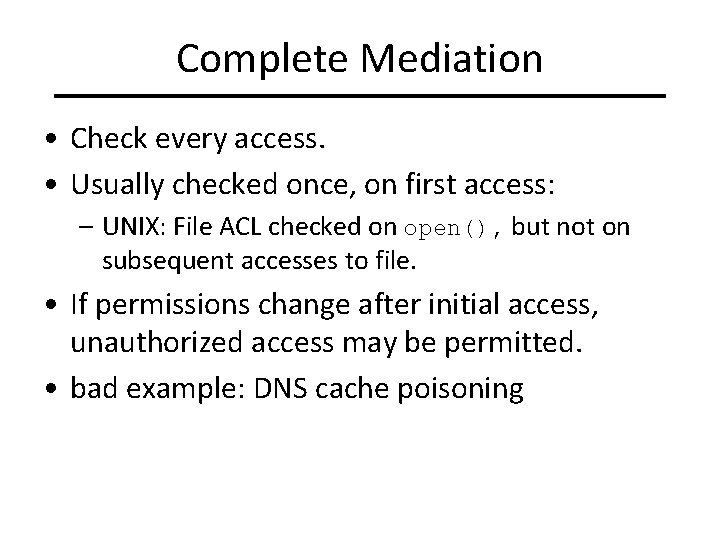
Complete Mediation • Check every access. • Usually checked once, on first access: – UNIX: File ACL checked on open(), but not on subsequent accesses to file. • If permissions change after initial access, unauthorized access may be permitted. • bad example: DNS cache poisoning

Open Design Security should not depend on secrecy of design or implementation. – i. e. Don’t rely on “Security through obscurity” – Makes expert public scrutiny possible. – Still need to keep keys and passwords secret. Cannot maintain secrecy of clients – Customers can reverse engineer hardware and software with decompilers, disassemblers, logic analyzers, etc. CSC 666: Secure Software Engineering

Open Design Example: Problem: MPAA wants control over DVDs. – Region coding, unskippable commercials. Solution: CSS (Content Scrambling System) – CSS algorithm kept secret. – DVD Players need player key to decrypt disk key on DVD to descript movie for playing. • Encryption uses 40 -bit keys. • People without keys can copy but not play DVDs. Result: CSS algorithm reverse engineered. – Weakness allows disk key to be recovered in an attack of complexity 225, which takes only a few seconds.

Separation of Privilege Require multiple conditions to grant access. – Separation of duty – Compartmentalization (encapsulation) – Defence in depth

Separation of Duty Functions are divided so that one entity does not have control over all parts of a transaction. Example: – Different persons must initiate a purchase and authorize a purchase. – Two different people may be required to arm and fire a nuclear missile.

Compartmentalization Problem: A security violation in one process should not affect others. Solution: Virtual Memory – Each process has its own address space. – Isolates memory accesses in process. – In what ways is this solution flawed? • i. e. , how can the compartments communicate? – How could we improve compartmentalization of processes?

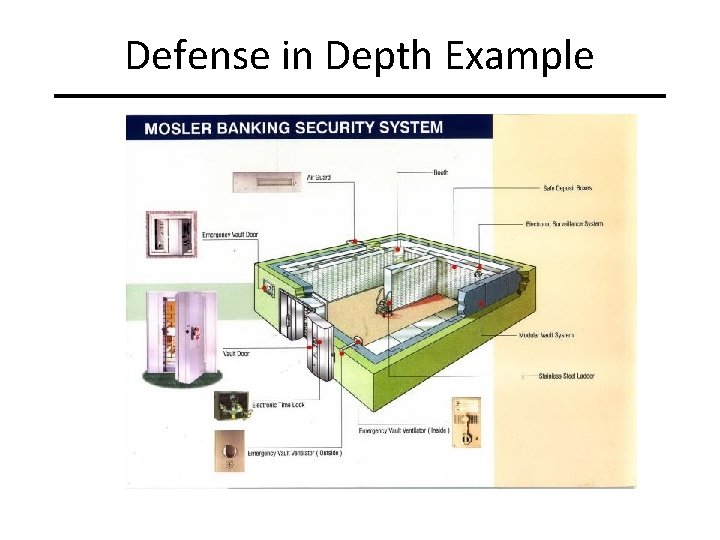
Defence in Depth Diverse defensive strategies – Multiple layers of defences – And different types of defences. • Protection (firewall, password) • Detection (anti-virus, NIDS) • Reaction (CIRT) – If one layer pierced, next layer may stop.

Defense in Depth Example

Least Common Mechanisms used to access resources should not be shared. – Information can flow along shared channels. Examples – Shared directories like /tmp – Shared memory like CPU caches, TLB Tradeoffs – Contradicts Economy of Mechanism

Least Common Mechanism Problem: – Compromising web server allows attacker access to entire machine that the web server runs on. Solution – Run web server as non-root user. – Attacker still gains “other” access to filesystem. – Attacker may be able to elevate privilege. Better solution – Run web server in a container or VM. – Web server compromise only impacts VM.

Psychological Acceptability Security mechanisms should not add to the difficulty of accessing a resource. – Usability: Ease of installation, configuration, and use. Hide complexity introduced by security mechanisms. – Principle of Least Astonishment: Design should match user’s experience, expectations, and mental models. Follow UI conventions.

Are these examples acceptable? 1. Requiring a password before making a purchase with stored credit card. 2. Requiring credit card entry for any purchase and refusing to store credit card information. 3. SSL certificate error dialog box asking user to continue or not. 4. SSL certificate error refusal message, with no decision to make.

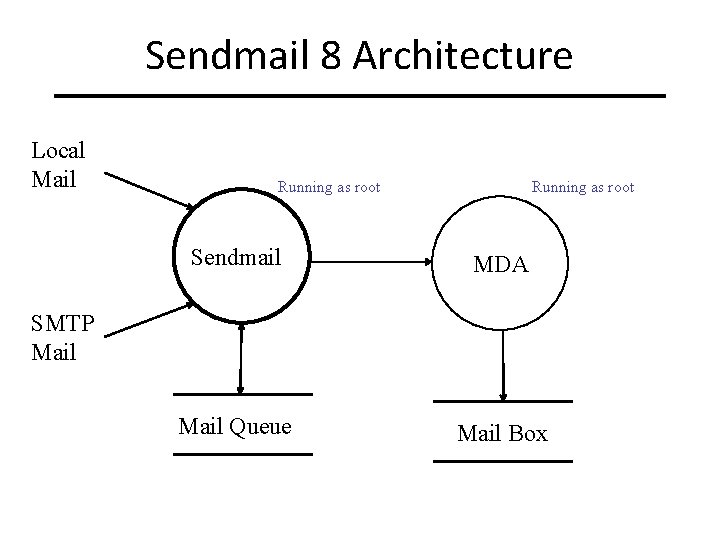
Sendmail 8 Architecture Local Mail Running as root Sendmail MDA Mail Queue Mail Box SMTP Mail

What principles are found in qmail?

Key Points § Attack Surface – Measure of how easy it is to attack a system. – Reduce AS by reducing code, limiting who can access code, and reducing code privilege. § Attack Trees – Method to model attacks and plan defenses. § Secure Design Principles 1. 2. 3. 4. 5. 6. 7. Least Privilege Fail-Safe Defaults Economy of Mechanism Complete Mediation Open Design Separation of Privilege Least Common Mechanism 8. Psychological Acceptability

References 1. Bishop, Matt, Introduction to Computer Security, Addison-Wesley, 2005. 2. Graff, Mark and van Wyk, Kenneth, Secure Coding: Principles & Practices, O’Reilly, 2003. 3. Howard, Michael and Le. Blanc, David, Writing Secure Code, 2 nd edition, Microsoft Press, 2003. 4. Olzak, Tom, Enterprise Security: A Practitioner’s Guide, http: //resources. infosecinstitute. com/attacksurface-reduction/ 5. Viega, John, and Mc. Graw, Gary, Building Secure Software, Addison-Wesley, 2002. 6. Wheeler, David, Secure Programming for UNIX and Linux HOWTO, http: //www. dwheeler. com/secureprograms/Secure-Programs-HOWTO/index. html, 2003.