Cisco Systems Inc All rights reserved 2004 2005

































- Slides: 67

© Cisco Systems, Inc. All rights reserved. © 2004, 2005 Cisco 1 1

© 2005 Cisco Systems, Inc. All rights reserved. 2

© 2005 Cisco Systems, Inc. All rights reserved. 3

© 2005 Cisco Systems, Inc. All rights reserved. 4

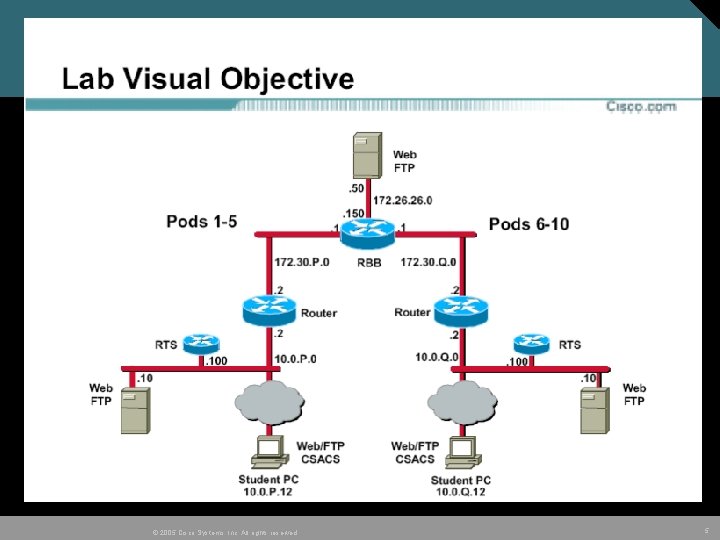
© 2005 Cisco Systems, Inc. All rights reserved. 5

Network Security 1 Module 1 – Overview of Network Security © 2005 Cisco Systems, Inc. All rights reserved. 6

Learning Objectives 1. 1 Introduction to Network Security 1. 2 Introduction to Vulnerabilities, Threats, and Attacks 1. 3 Attack Examples 1. 4 Vulnerability Analysis © 2005 Cisco Systems, Inc. All rights reserved. 7

Module 1 – Overview of Network Security 1. 1 Introduction to Network Security © 2005 Cisco Systems, Inc. All rights reserved. 8

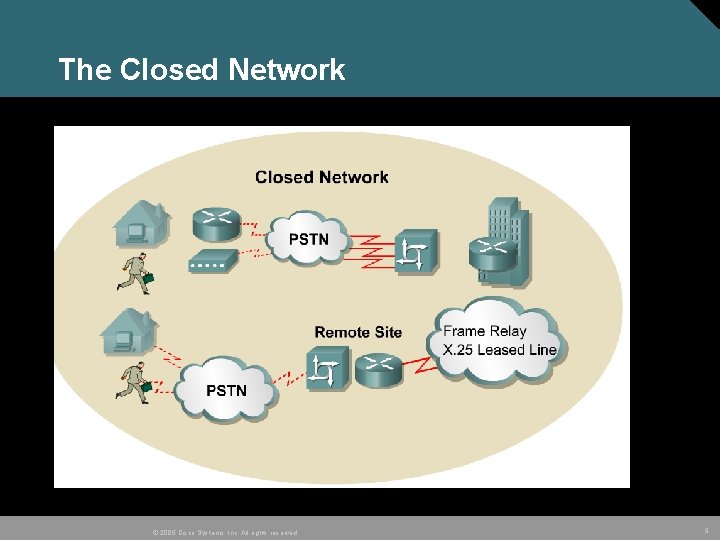
The Closed Network © 2005 Cisco Systems, Inc. All rights reserved. 9

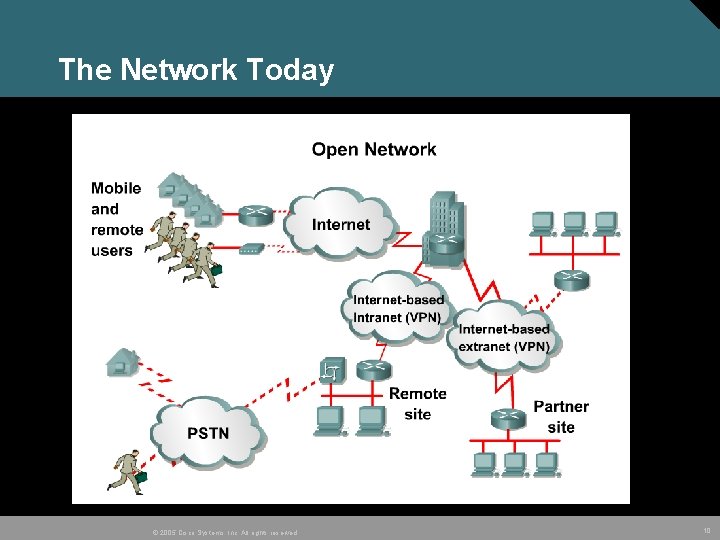
The Network Today © 2005 Cisco Systems, Inc. All rights reserved. 10

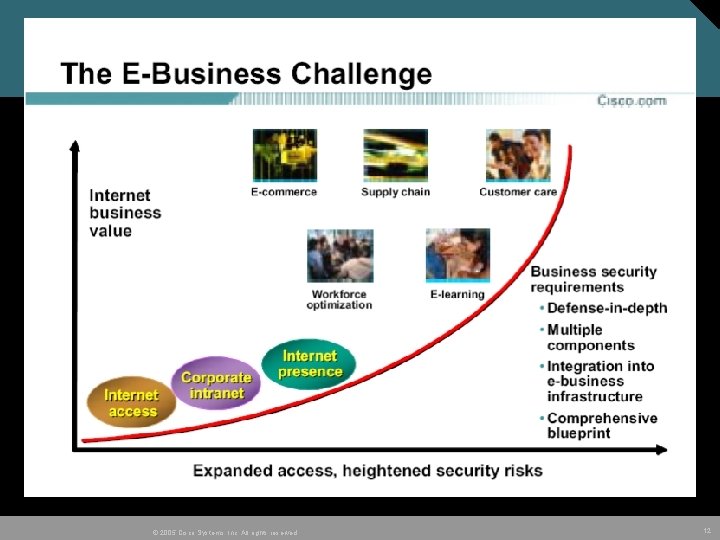
© 2005 Cisco Systems, Inc. All rights reserved. 11

© 2005 Cisco Systems, Inc. All rights reserved. 12

Identifying potential risks to network security • Identify the components of the network, evaluate the importance of each component, and then apply an appropriate level of security Asset Identification Vulnerability Assessment Threat Identification © 2005 Cisco Systems, Inc. All rights reserved. 13

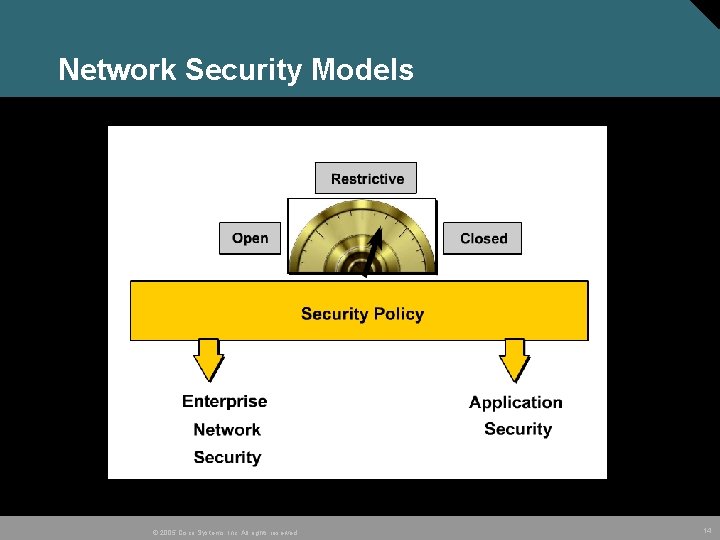
Network Security Models © 2005 Cisco Systems, Inc. All rights reserved. 14

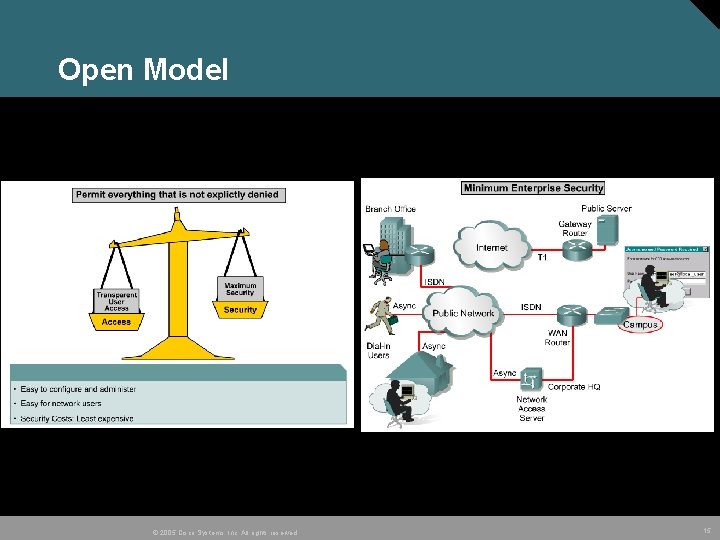
Open Model © 2005 Cisco Systems, Inc. All rights reserved. 15

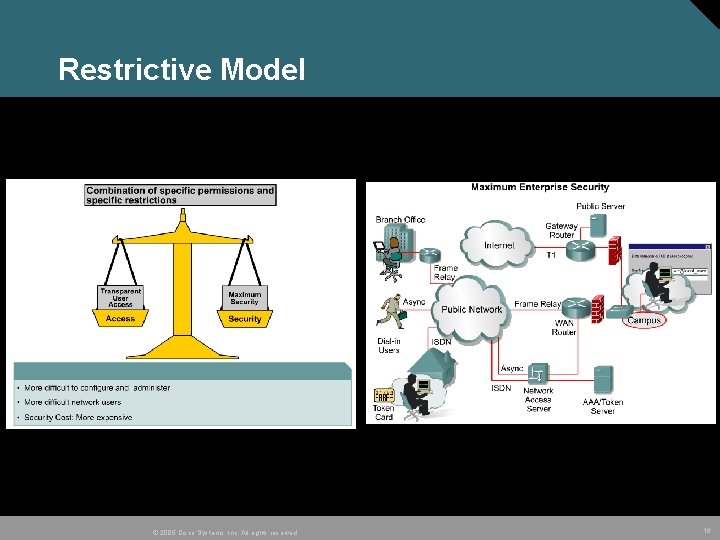
Restrictive Model © 2005 Cisco Systems, Inc. All rights reserved. 16

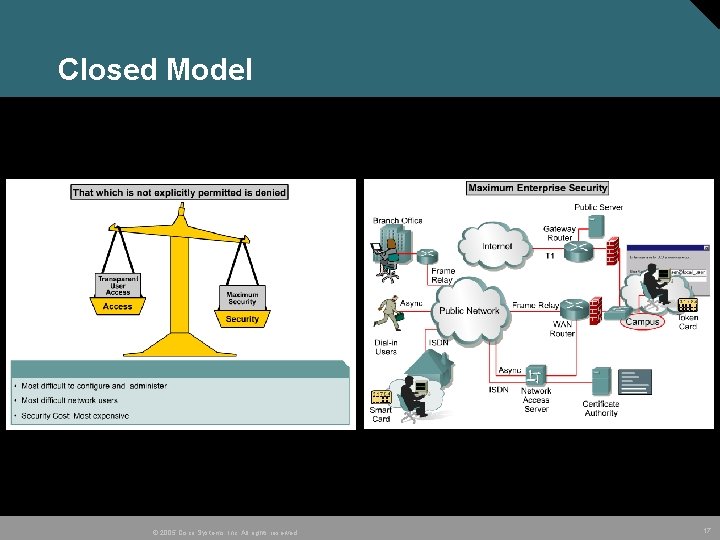
Closed Model © 2005 Cisco Systems, Inc. All rights reserved. 17

Trends that Affect Security • Increase of network attacks • Increased sophistication of attacks • Increased dependence on the network • Lack of trained personnel • Lack of awareness • Lack of security policies • Wireless access • Legislation • Litigation © 2005 Cisco Systems, Inc. All rights reserved. 18

Legal and Governmental Policy Issues Organizations that operate vulnerable networks will face increasing and substantial liability. US Federal legislation mandating security includes the following: GLB financial services legislation Government Information Security Reform Act HIPAA CIPA © 2005 Cisco Systems, Inc. All rights reserved. 19

Information Security Associations • Information on detecting and responding to security threats. • Operating system weaknesses • Best practices for security • Security training and certification • Provide organizations with an objective review of security products. • For example, Common Criteria, FIPS 140, and ICSA are some of the independent certifications and evaluations © 2005 Cisco Systems, Inc. All rights reserved. 20

Module 1 – Overview of Network Security 1. 2 Introduction to Vulnerabilities, Threats, and Attacks © 2005 Cisco Systems, Inc. All rights reserved. 21

Introduction to Vulnerabilities, Threats, and Attacks • Vulnerabilities = Weakness • Threats = Take advantage of security weakness • Attacks = tools, scripts, and programs to exploit weakness © 2005 Cisco Systems, Inc. All rights reserved. 22

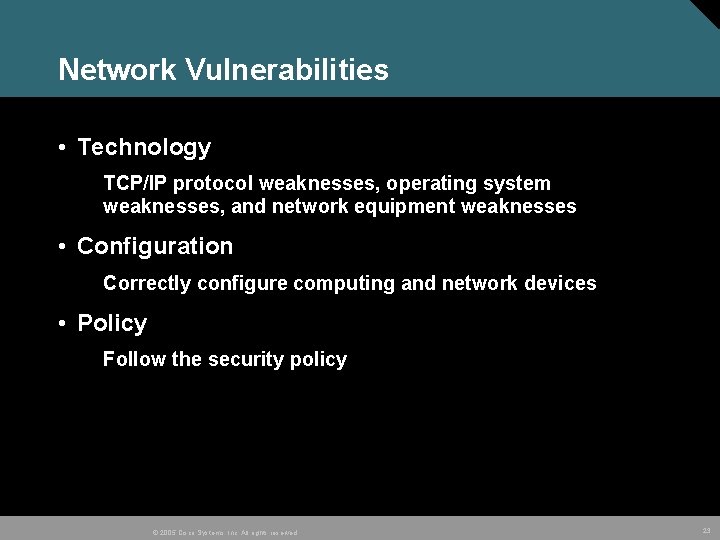
Network Vulnerabilities • Technology TCP/IP protocol weaknesses, operating system weaknesses, and network equipment weaknesses • Configuration Correctly configure computing and network devices • Policy Follow the security policy © 2005 Cisco Systems, Inc. All rights reserved. 23

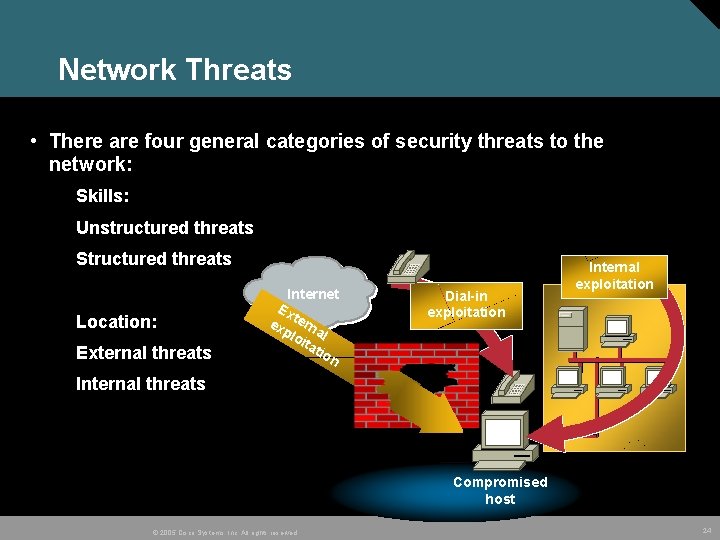
Network Threats • There are four general categories of security threats to the network: Skills: Unstructured threats Structured threats Location: External threats Internet Ex ex tern plo al ita tio n Dial-in exploitation Internal threats Compromised host © 2005 Cisco Systems, Inc. All rights reserved. 24

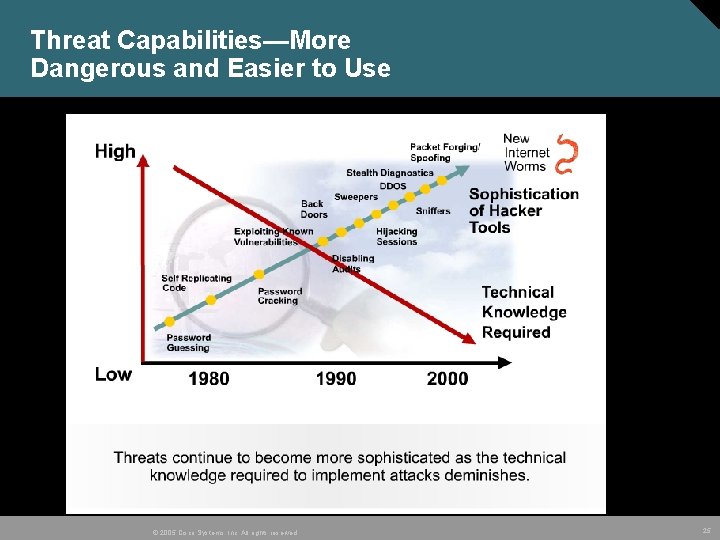
Threat Capabilities—More Dangerous and Easier to Use © 2005 Cisco Systems, Inc. All rights reserved. 25

Groups of individuals • Hacker • Cracker • Phreaker • Spammer • Phisher • White hat • Black hat © 2005 Cisco Systems, Inc. All rights reserved. 26

Four Classes of Network Attacks Reconnaissance attacks Access attacks Denial of service attacks Worms, viruses, and Trojan horses © 2005 Cisco Systems, Inc. All rights reserved. 27

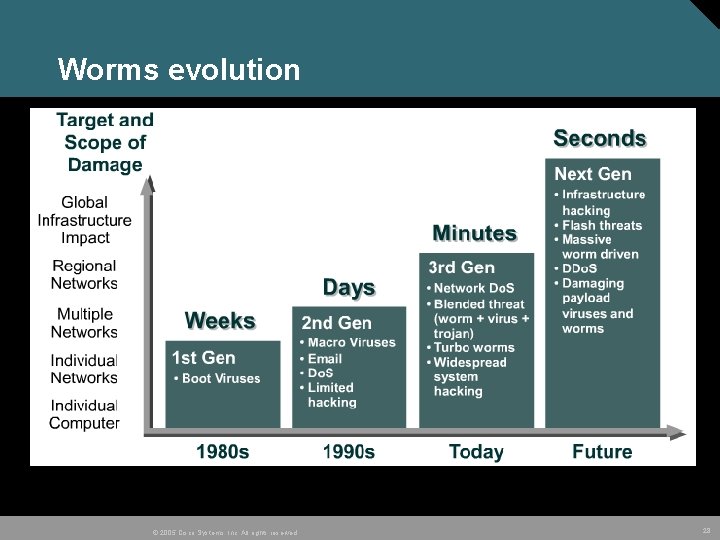
Worms evolution © 2005 Cisco Systems, Inc. All rights reserved. 28

Module 1 – Overview of Network Security 1. 3 Attack Examples © 2005 Cisco Systems, Inc. All rights reserved. 29

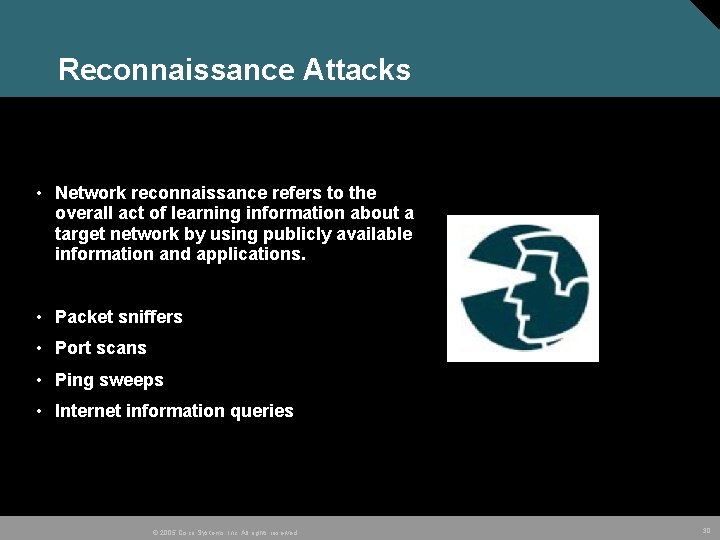
Reconnaissance Attacks • Network reconnaissance refers to the overall act of learning information about a target network by using publicly available information and applications. • Packet sniffers • Port scans • Ping sweeps • Internet information queries © 2005 Cisco Systems, Inc. All rights reserved. 30

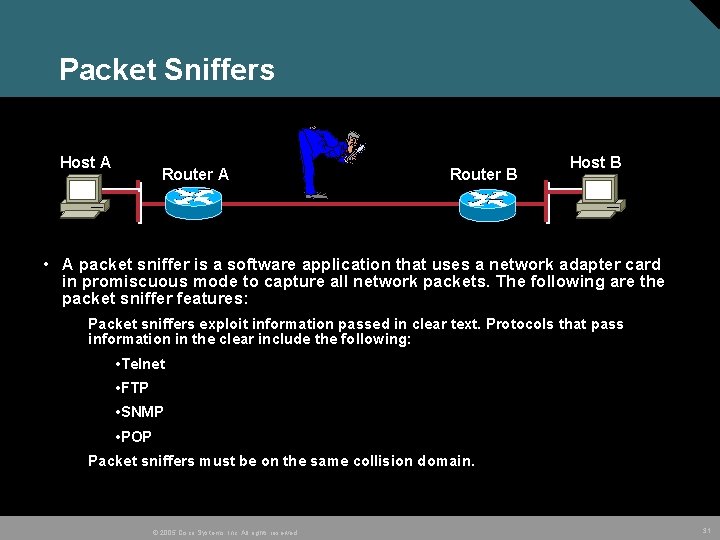
Packet Sniffers Host A Router B Host B • A packet sniffer is a software application that uses a network adapter card in promiscuous mode to capture all network packets. The following are the packet sniffer features: Packet sniffers exploit information passed in clear text. Protocols that pass information in the clear include the following: • Telnet • FTP • SNMP • POP Packet sniffers must be on the same collision domain. © 2005 Cisco Systems, Inc. All rights reserved. 31

Packet Sniffer Mitigation Host A Router B Host B • The following techniques and tools can be used to mitigate sniffers: Authentication—Using strong authentication, such as one-time passwords, is a first option for defense against packet sniffers. Switched infrastructure—Deploy a switched infrastructure to counter the use of packet sniffers in your environment. Antisniffer tools—Use these tools to employ software and hardware designed to detect the use of sniffers on a network. Cryptography—The most effective method for countering packet sniffers does not prevent or detect packet sniffers, but rather renders them irrelevant. © 2005 Cisco Systems, Inc. All rights reserved. 32

© 2005 Cisco Systems, Inc. All rights reserved. 33

© 2005 Cisco Systems, Inc. All rights reserved. 34

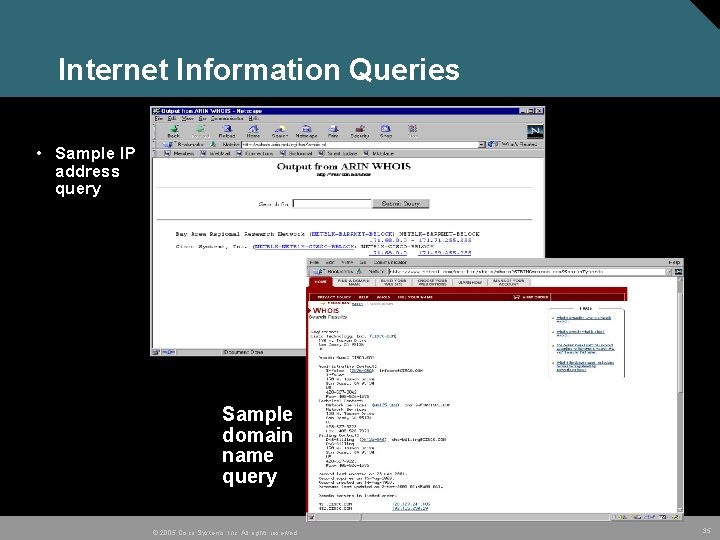
Internet Information Queries • Sample IP address query Sample domain name query © 2005 Cisco Systems, Inc. All rights reserved. 35

© 2005 Cisco Systems, Inc. All rights reserved. 36

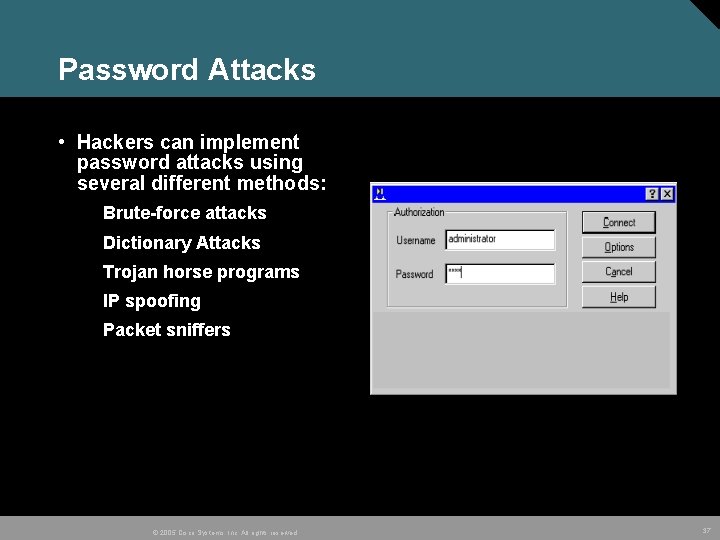
Password Attacks • Hackers can implement password attacks using several different methods: Brute-force attacks Dictionary Attacks Trojan horse programs IP spoofing Packet sniffers © 2005 Cisco Systems, Inc. All rights reserved. 37

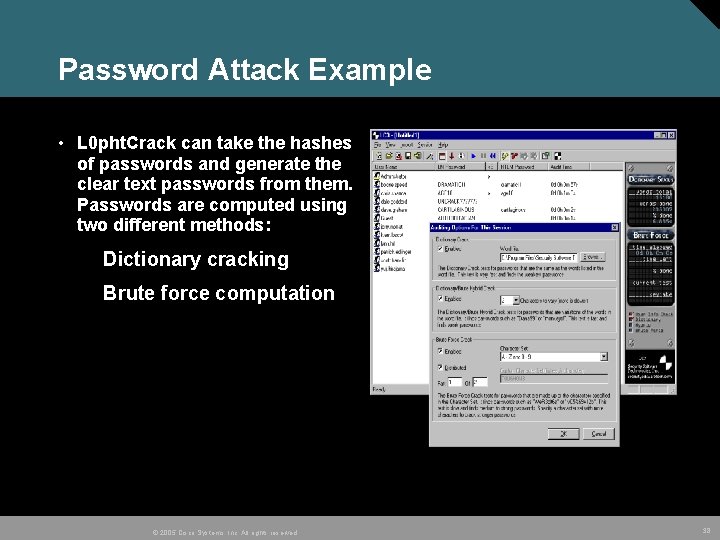
Password Attack Example • L 0 pht. Crack can take the hashes of passwords and generate the clear text passwords from them. Passwords are computed using two different methods: Dictionary cracking Brute force computation © 2005 Cisco Systems, Inc. All rights reserved. 38

Password Attacks Mitigation • The following are mitigation techniques: Do not allow users to use the same password on multiple systems. Disable accounts after a certain number of unsuccessful login attempts. Do not use plain text passwords. OTP or a cryptographic password is recommended. Use “strong” passwords. Strong passwords are at least eight characters long and contain uppercase letters, lowercase letters, numbers, and special characters. © 2005 Cisco Systems, Inc. All rights reserved. 39

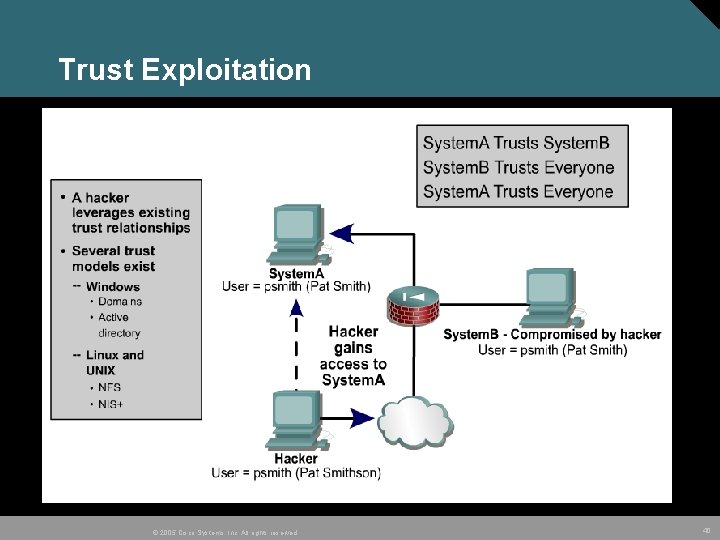
Trust Exploitation © 2005 Cisco Systems, Inc. All rights reserved. 40

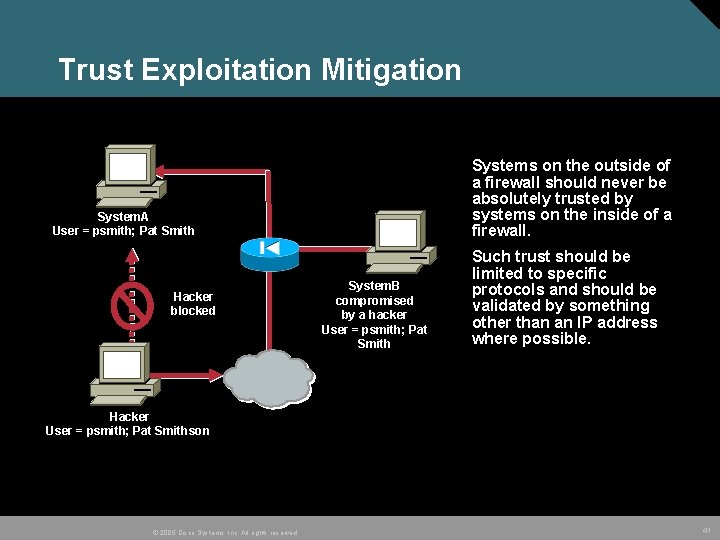
Trust Exploitation Mitigation Systems on the outside of a firewall should never be absolutely trusted by systems on the inside of a firewall. System. A User = psmith; Pat Smith Hacker blocked System. B compromised by a hacker User = psmith; Pat Smith Such trust should be limited to specific protocols and should be validated by something other than an IP address where possible. Hacker User = psmith; Pat Smithson © 2005 Cisco Systems, Inc. All rights reserved. 41

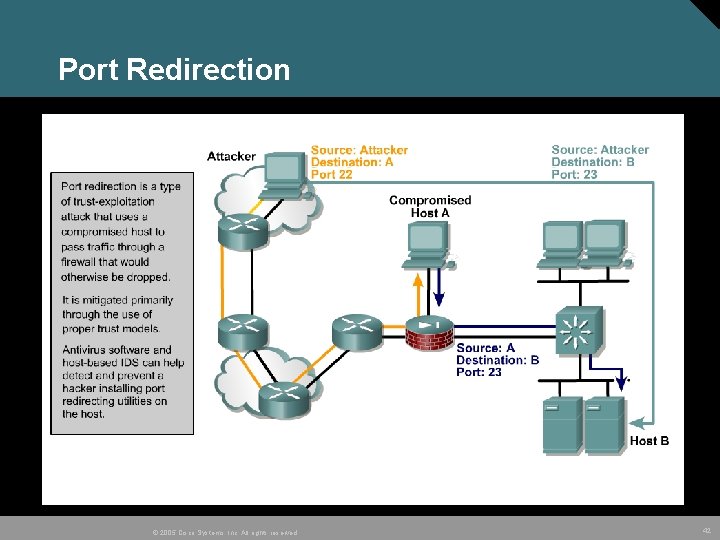
Port Redirection © 2005 Cisco Systems, Inc. All rights reserved. 42

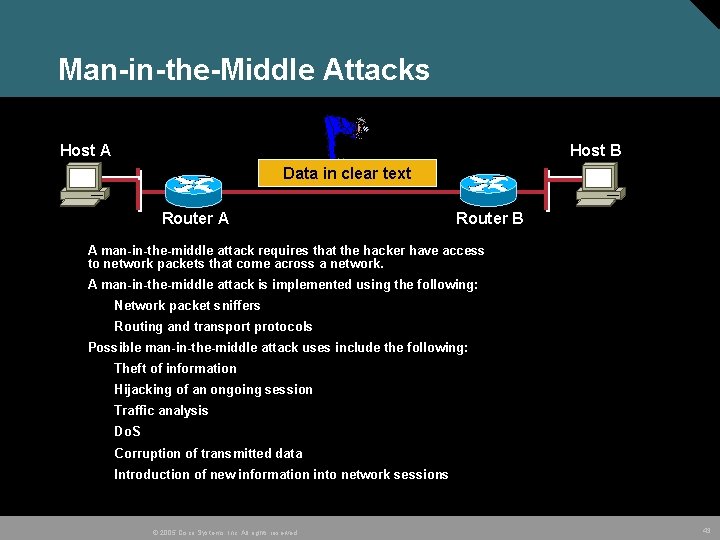
Man-in-the-Middle Attacks Host A Host B Data in clear text Router A Router B A man-in-the-middle attack requires that the hacker have access to network packets that come across a network. A man-in-the-middle attack is implemented using the following: Network packet sniffers Routing and transport protocols Possible man-in-the-middle attack uses include the following: Theft of information Hijacking of an ongoing session Traffic analysis Do. S Corruption of transmitted data Introduction of new information into network sessions © 2005 Cisco Systems, Inc. All rights reserved. 43

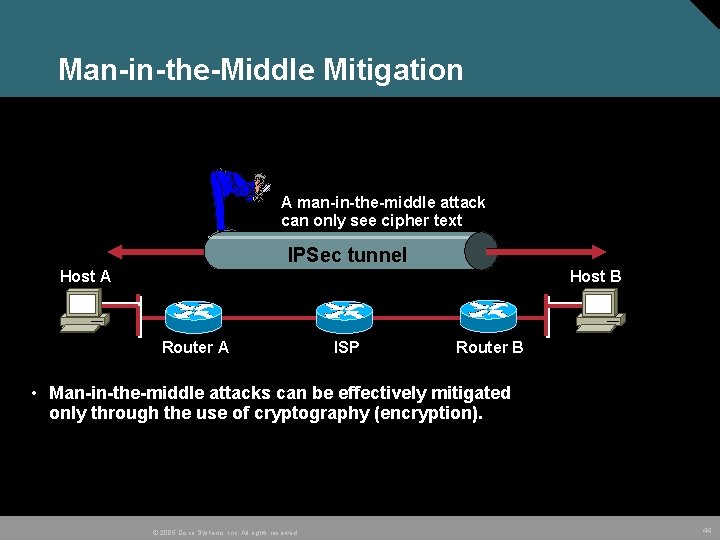
Man-in-the-Middle Mitigation A man-in-the-middle attack can only see cipher text IPSec tunnel Host A Host B Router A ISP Router B • Man-in-the-middle attacks can be effectively mitigated only through the use of cryptography (encryption). © 2005 Cisco Systems, Inc. All rights reserved. 44

Social Engineering • Intruder can trick a member of an organization into giving over valuable information • Phishing Using email or other types of messages in an attempt to trick others into providing sensitive information Contain hyperlinks that appear to be legitimate, but will actually cause the user to visit a phony site Information it is recorded for the phisher to use © 2005 Cisco Systems, Inc. All rights reserved. 45

© 2005 Cisco Systems, Inc. All rights reserved. 46

© 2005 Cisco Systems, Inc. All rights reserved. 47

IP Spoofing IP spoofing occurs when a hacker inside or outside a network impersonates the conversations of a trusted computer. Two general techniques are used during IP spoofing: A hacker uses an IP address that is within the range of trusted IP addresses. A hacker uses an authorized external IP address that is trusted. Uses for IP spoofing include the following: IP spoofing is usually limited to the injection of malicious data or commands into an existing stream of data. A hacker changes the routing tables to point to the spoofed IP address, then the hacker can receive all the network packets that are addressed to the spoofed address and reply just as any trusted user can. © 2005 Cisco Systems, Inc. All rights reserved. 48

IP Spoofing Mitigation • The threat of IP spoofing can be reduced, but not eliminated, through the following measures: Access control—The most common method for preventing IP spoofing is to properly configure access control. RFC 2827 filtering—You can prevent users of your network from spoofing other networks (and be a good Internet citizen at the same time) by preventing any outbound traffic on your network that does not have a source address in your organization's own IP range. Additional authentication that does not use IP-based authentication— Examples of this include the following: Cryptographic (recommended) Strong, two-factor, one-time passwords © 2005 Cisco Systems, Inc. All rights reserved. 49

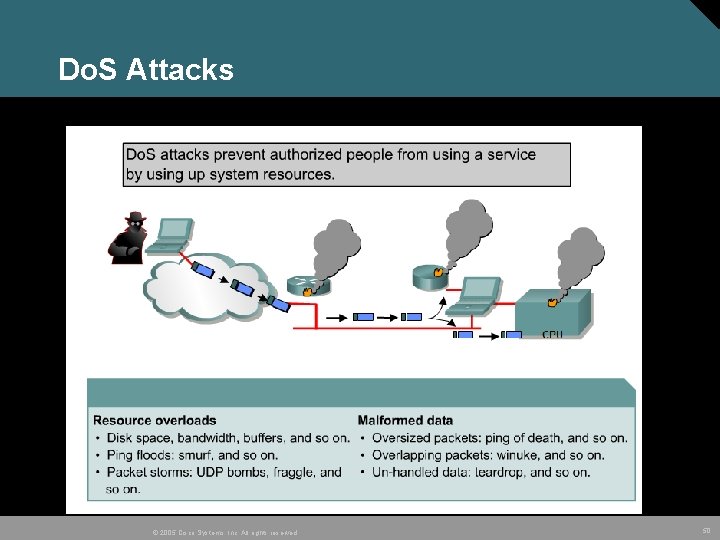
Do. S Attacks © 2005 Cisco Systems, Inc. All rights reserved. 50

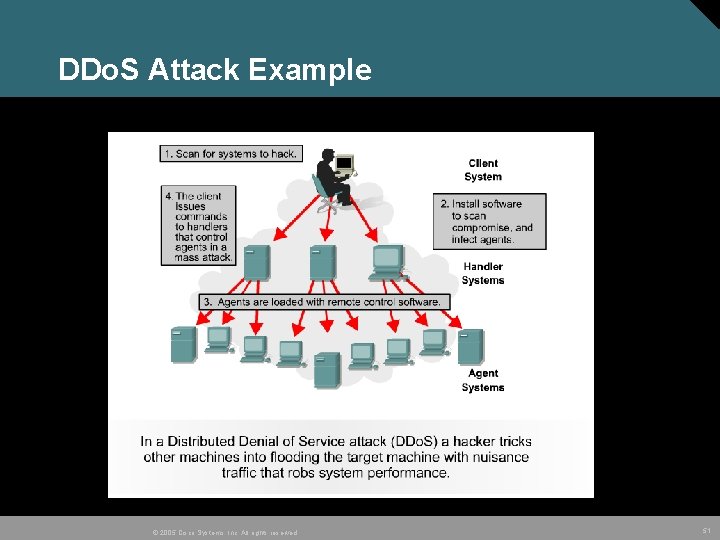
DDo. S Attack Example © 2005 Cisco Systems, Inc. All rights reserved. 51

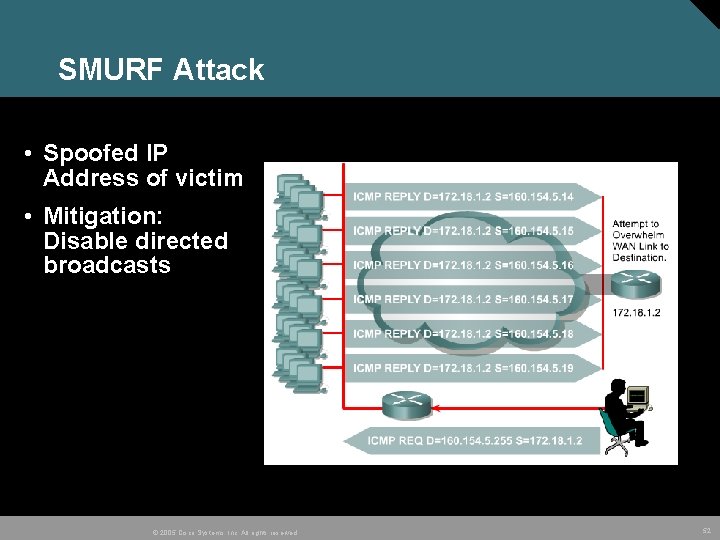
SMURF Attack • Spoofed IP Address of victim • Mitigation: Disable directed broadcasts © 2005 Cisco Systems, Inc. All rights reserved. 52

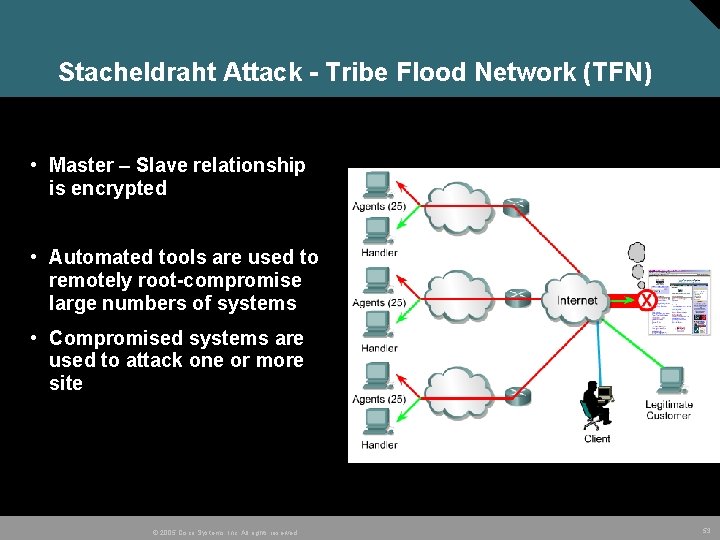
Stacheldraht Attack - Tribe Flood Network (TFN) • Master – Slave relationship is encrypted • Automated tools are used to remotely root-compromise large numbers of systems • Compromised systems are used to attack one or more site © 2005 Cisco Systems, Inc. All rights reserved. 53

Do. S Attack Mitigation • The threat of Do. S attacks can be reduced through the following three methods: Antispoof features—Proper configuration of antispoof features on your routers and firewalls Anti-Do. S features—Proper configuration of anti-Do. S features on routers and firewalls Traffic rate limiting—Implement traffic rate limiting with the networks ISP © 2005 Cisco Systems, Inc. All rights reserved. 54

© 2005 Cisco Systems, Inc. All rights reserved. 55

© 2005 Cisco Systems, Inc. All rights reserved. 56

© 2005 Cisco Systems, Inc. All rights reserved. 57

© 2005 Cisco Systems, Inc. All rights reserved. 58

Application Layer Attacks • Application layer attacks have the following characteristics: Exploit well known weaknesses, such as protocols, that are intrinsic to an application or system (for example, sendmail, HTTP, and FTP) Often use ports that are allowed through a firewall (for example, TCP port 80 used in an attack against a web server behind a firewall) Can never be completely eliminated, because new vulnerabilities are always being discovered © 2005 Cisco Systems, Inc. All rights reserved. 59

Application Layer Attacks Mitigation • Some measures you can take to reduce your risks are as follows: Read operating system and network log files, or have them analyzed by log analysis applications. Subscribe to mailing lists that publicize vulnerabilities. Keep your operating system and applications current with the latest patches. IDSs can scan for known attacks, monitor and log attacks, and in some cases, prevent attacks. © 2005 Cisco Systems, Inc. All rights reserved. 60

Module 1 – Overview of Network Security 1. 4 Vulnerability Analysis © 2005 Cisco Systems, Inc. All rights reserved. 61

Policy review © 2005 Cisco Systems, Inc. All rights reserved. 62

Network analysis • Cisco Auto. Secure • Cisco Output Interpreter • National Security Agency (NSA) Cisco Router Security Configuration Guides • Cisco Router Audit Tool (RAT) © 2005 Cisco Systems, Inc. All rights reserved. 63

Auto Secure To secure the management and forwarding planes of the router, use the auto secure command in privileged EXEC mode. auto secure [management | forwarding] [no-interact] Syntax Description • management (Optional) Only the management plane will be secured. • forwarding (Optional) Only the forwarding plane will be secured. • no-interact (Optional) The user will not be prompted for any interactive configurations. If this keyword is not enabled, the command will show the user the noninteractive configuration and the interactive configurations thereafter. © 2005 Cisco Systems, Inc. All rights reserved. 64

Host analysis • Types of applications and services • Services and ports that are not necessary should be disabled or blocked. • All operating systems should be patched as needed. • Antivirus software should be installed and kept up to date. –Network Mapper (Nmap) –Nessus © 2005 Cisco Systems, Inc. All rights reserved. 65

Analysis tools • Knoppix-STD –encryption tools –forensics tools –firewall tools –intrusion detection tools –network utilities –password tools –packet sniffers –vulnerability assessment tools –wireless tools • Microsoft Baseline Security Analyzer –Windows 2000, Windows XP, and Windows Server 2003 –Report outlining potential vulnerabilities and the steps required to correct them © 2005 Cisco Systems, Inc. All rights reserved. 66

© 2005, Cisco Systems, Inc. All rights reserved. 67
 2012 pearson education inc
2012 pearson education inc Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Copyright 2010 pearson education inc
Copyright 2010 pearson education inc 2010 pearson education inc
2010 pearson education inc All rights reserved example
All rights reserved example Copyright 2015 all rights reserved
Copyright 2015 all rights reserved All rights reserved sentence
All rights reserved sentence Freesound content licence
Freesound content licence Confidential all rights reserved
Confidential all rights reserved Sentinel repetition
Sentinel repetition Copyright 2015 all rights reserved
Copyright 2015 all rights reserved Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Dell all rights reserved copyright 2009
Dell all rights reserved copyright 2009 Warning all rights reserved
Warning all rights reserved Siprop
Siprop All rights reserved formula
All rights reserved formula Warning all rights reserved
Warning all rights reserved Confidential all rights reserved
Confidential all rights reserved Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Copyright © 2018 all rights reserved
Copyright © 2018 all rights reserved Gssllc
Gssllc Confidential all rights reserved
Confidential all rights reserved Airbus deutschland gmbh
Airbus deutschland gmbh R rights reserved
R rights reserved Rights reserved
Rights reserved Pearson
Pearson Lida jacob ias
Lida jacob ias Existanxe
Existanxe Child rights act 2005 images
Child rights act 2005 images 2005 pearson prentice hall inc
2005 pearson prentice hall inc 2005 pearson prentice hall inc
2005 pearson prentice hall inc Positive rights and negative rights
Positive rights and negative rights Riparian and littoral rights
Riparian and littoral rights Duty towards self
Duty towards self Legal rights and moral rights
Legal rights and moral rights What are negative rights
What are negative rights Negative rights vs positive rights
Negative rights vs positive rights Negative rights vs positive rights
Negative rights vs positive rights Positive rights and negative rights
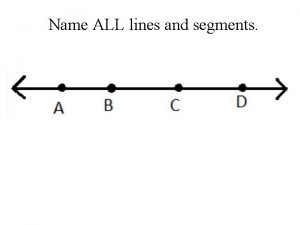
Positive rights and negative rights Name three line segments
Name three line segments Cisco mobility express solution
Cisco mobility express solution Travel document systems inc
Travel document systems inc Petro vend k800
Petro vend k800 Cyber power solutions
Cyber power solutions Applied systems inc subsidiaries
Applied systems inc subsidiaries Uticom
Uticom Global imaging systems inc
Global imaging systems inc Environmental systems research institute
Environmental systems research institute Multiplex ceo
Multiplex ceo Preferred systems inc
Preferred systems inc Control data systems inc
Control data systems inc Educational data systems inc
Educational data systems inc Advanced fluid power
Advanced fluid power Oli systems
Oli systems Klein marine systems
Klein marine systems Diversified air systems inc
Diversified air systems inc Fox systems inc
Fox systems inc Advanced cooling systems inc
Advanced cooling systems inc What are delegated reserved and concurrent powers
What are delegated reserved and concurrent powers Implied powers
Implied powers Reserved powers.
Reserved powers. Mpls concepts
Mpls concepts Social facilitation example psychology
Social facilitation example psychology Find the names of sailors who have reserved a red boat
Find the names of sailors who have reserved a red boat Reserved address
Reserved address