Cisco Systems Inc All rights reserved 2004 2005



















- Slides: 47

© Cisco Systems, Inc. All rights reserved. © 2004, 2005 Cisco 1 1

Network Security 1 Module 4 – Trust and Identity Technology © 2005 Cisco Systems, Inc. All rights reserved. 2

Learning Objectives 4. 1 AAA 4. 2 Authentication Technologies 4. 3 Identity Based Networking Services (IBNS) 4. 4 Network Admission Control (NAC) © 2005 Cisco Systems, Inc. All rights reserved. 3

Module 1 – Trust and Identity Technology 4. 1 AAA © 2005 Cisco Systems, Inc. All rights reserved. 4

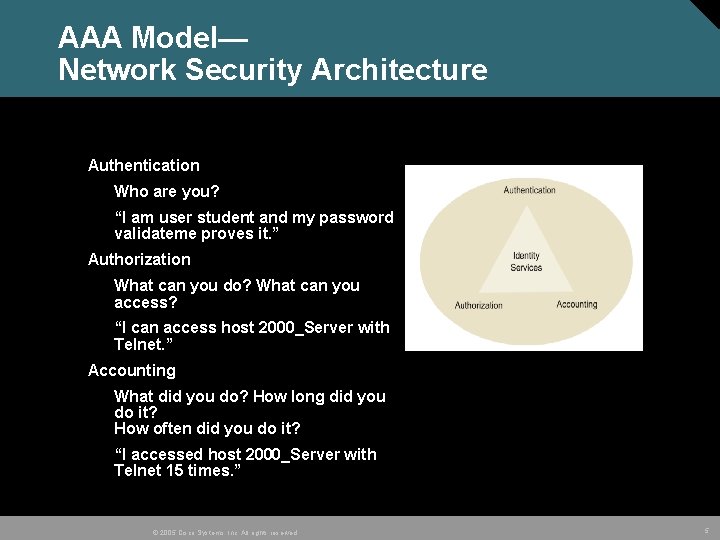
AAA Model— Network Security Architecture Authentication Who are you? “I am user student and my password validateme proves it. ” Authorization What can you do? What can you access? “I can access host 2000_Server with Telnet. ” Accounting What did you do? How long did you do it? How often did you do it? “I accessed host 2000_Server with Telnet 15 times. ” © 2005 Cisco Systems, Inc. All rights reserved. 5

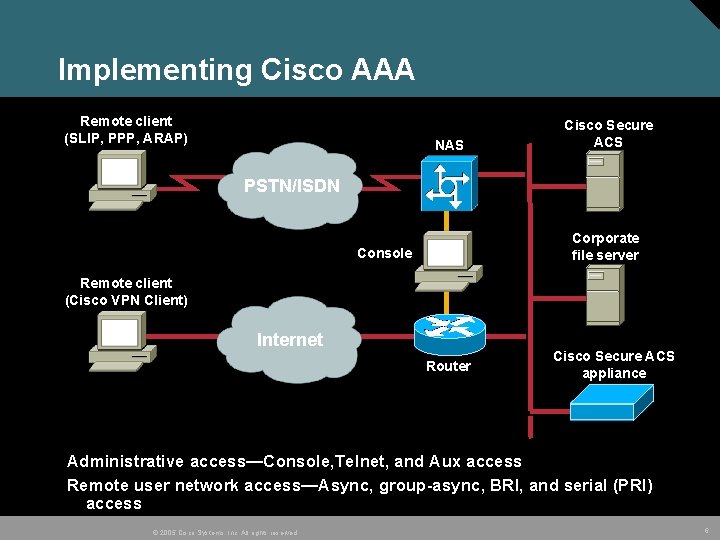
Implementing Cisco AAA Remote client (SLIP, PPP, ARAP) NAS Cisco Secure ACS PSTN/ISDN Corporate file server Console Remote client (Cisco VPN Client) Internet Router Cisco Secure ACS appliance Administrative access—Console, Telnet, and Aux access Remote user network access—Async, group-async, BRI, and serial (PRI) access © 2005 Cisco Systems, Inc. All rights reserved. 6

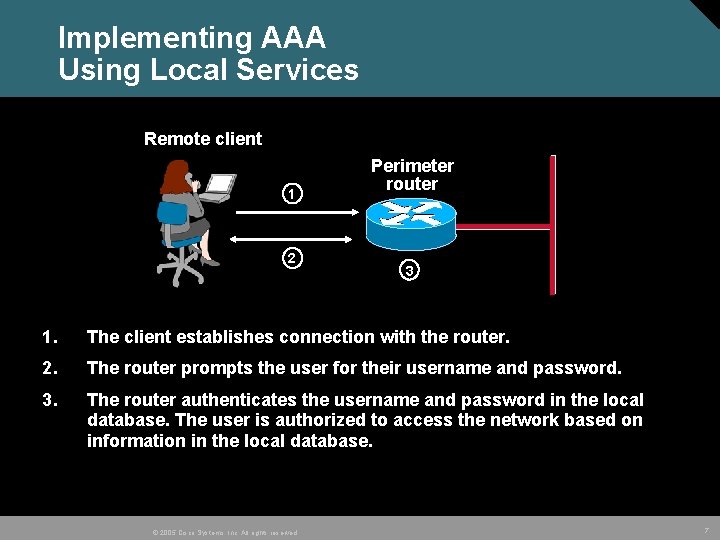
Implementing AAA Using Local Services Remote client 1 2 Perimeter router 3 1. The client establishes connection with the router. 2. The router prompts the user for their username and password. 3. The router authenticates the username and password in the local database. The user is authorized to access the network based on information in the local database. © 2005 Cisco Systems, Inc. All rights reserved. 7

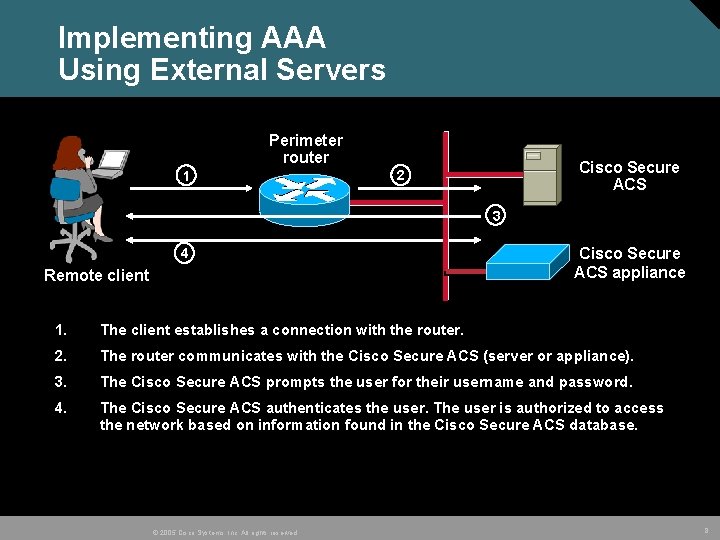
Implementing AAA Using External Servers Perimeter router 1 Cisco Secure ACS 2 3 4 Remote client Cisco Secure ACS appliance 1. The client establishes a connection with the router. 2. The router communicates with the Cisco Secure ACS (server or appliance). 3. The Cisco Secure ACS prompts the user for their username and password. 4. The Cisco Secure ACS authenticates the user. The user is authorized to access the network based on information found in the Cisco Secure ACS database. © 2005 Cisco Systems, Inc. All rights reserved. 8

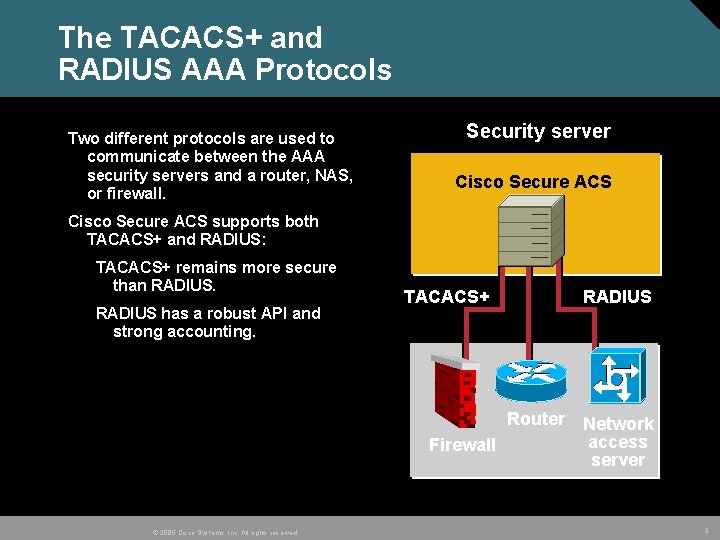
The TACACS+ and RADIUS AAA Protocols Two different protocols are used to communicate between the AAA security servers and a router, NAS, or firewall. Security server Cisco Secure ACS supports both TACACS+ and RADIUS: TACACS+ remains more secure than RADIUS has a robust API and strong accounting. TACACS+ RADIUS Router Network access Firewall server © 2005 Cisco Systems, Inc. All rights reserved. 9

TACACS • TACACS RFC 1492, forwards username and password information to a centralized server. • XTACACS Extensions that Cisco added to the TACACS protocol Multi-protocol and can authorize connections with SLIP, enable, PPP IP or IPX, ARA, EXEC, and Telnet. • TACACS+ Enhanced and continually improved version of TACACS that allows a TACACS+ server to provide the services of AAA independently. Completely new version of the TACACS protocol referenced by RFC 1492 and developed by Cisco. Not compatible with XTACACS+ has been submitted to the IETF as a draft proposal. © 2005 Cisco Systems, Inc. All rights reserved. 10

RADIUS • Alternative to TACACS+ • RADIUS is an access server AAA protocol developed by Livingston Enterprises, Inc (now part of Lucent Technologies). • Distributed security that secures remote access to networks and protects network services against unauthorized access. • RADIUS is comprised of three components: Protocol with a frame format that uses UDP/IP Server Client © 2005 Cisco Systems, Inc. All rights reserved. 11

RADIUS 3 versions • IETF with approximately 63 attributes – RFC 2138, and RADIUS accounting in RFC 2139. • Cisco implementation supporting approximately 58 attributes. Cisco IOS software and Cisco Secure ACS. • Lucent supporting over 254 attributes © 2005 Cisco Systems, Inc. All rights reserved. 12

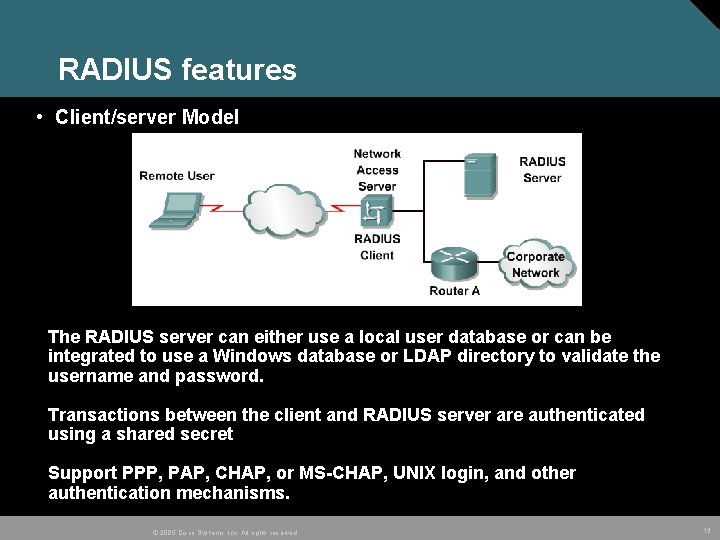
RADIUS features • Client/server Model The RADIUS server can either use a local user database or can be integrated to use a Windows database or LDAP directory to validate the username and password. Transactions between the client and RADIUS server are authenticated using a shared secret Support PPP, PAP, CHAP, or MS-CHAP, UNIX login, and other authentication mechanisms. © 2005 Cisco Systems, Inc. All rights reserved. 13

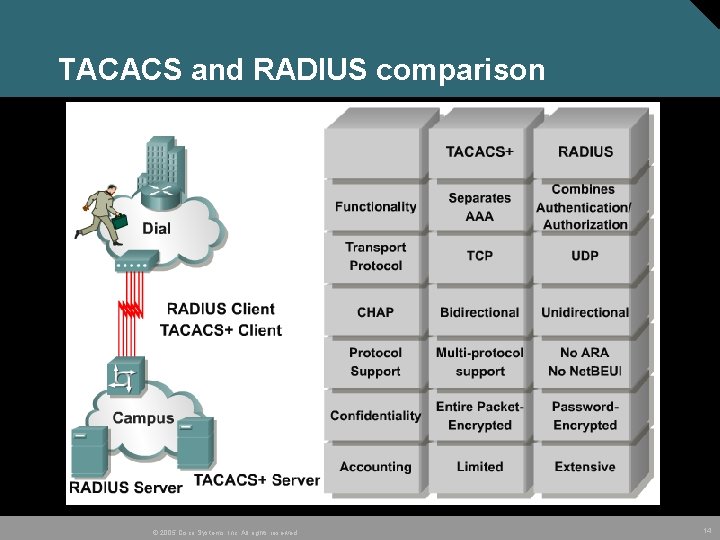
TACACS and RADIUS comparison © 2005 Cisco Systems, Inc. All rights reserved. 14

Module 1 – Trust and Identity Technology 4. 2 Authentication Technologies © 2005 Cisco Systems, Inc. All rights reserved. 15

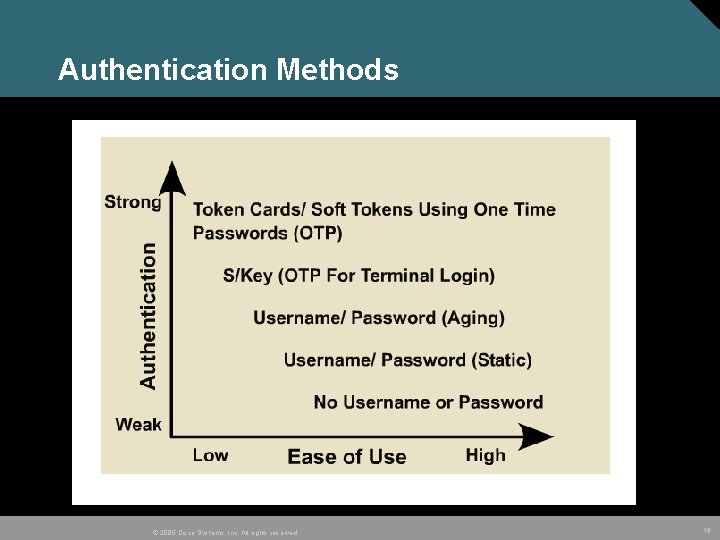
Authentication Methods © 2005 Cisco Systems, Inc. All rights reserved. 16

Username / Password authentication • A static username/password authentication method Remains the same until changed by the system administrator or user. Playback attacks, eavesdropping, theft, and password cracking programs. The attacker will continue to have access until the administrator or user chooses to change it. • Aging username/password authentication User is forced to change the password after a set time, usually 30 to 60 days. Mitigates some risk, still susceptible to attacks until the password is changed. © 2005 Cisco Systems, Inc. All rights reserved. 17

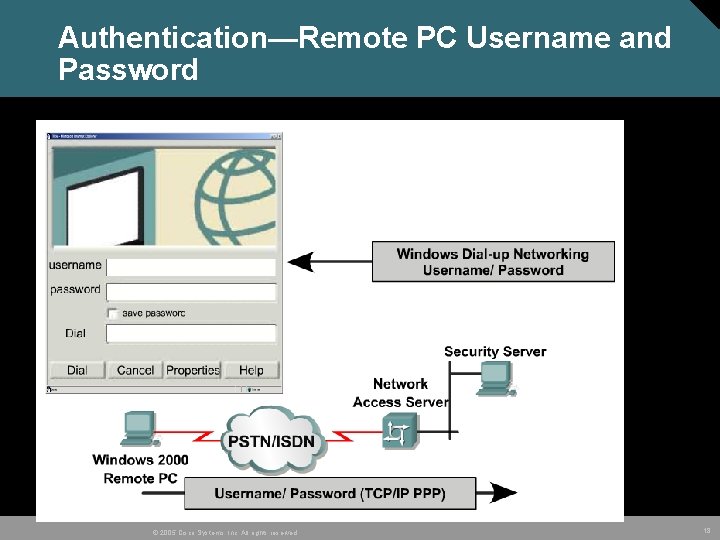
Authentication—Remote PC Username and Password © 2005 Cisco Systems, Inc. All rights reserved. 18

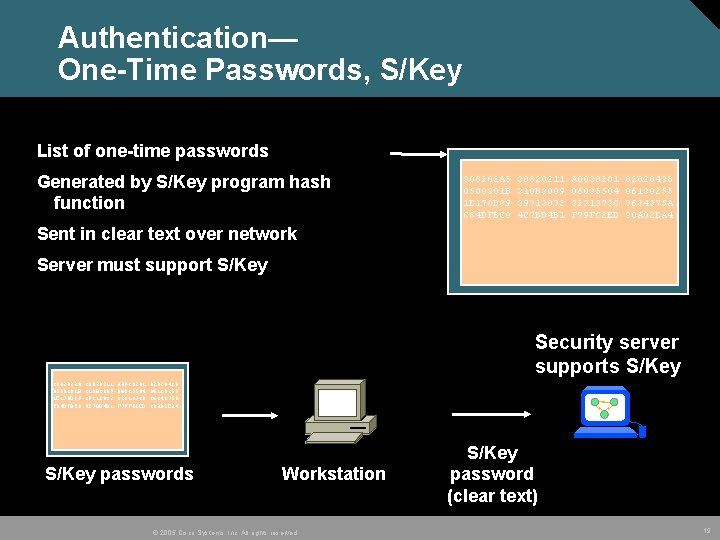
Authentication— One-Time Passwords, S/Key List of one-time passwords Generated by S/Key program hash function 308202 A 8 0500301 B 1 E 170 D 39 C 84 DFBC 0 30820211 310 B 3009 39313032 4 C 7 BD 4 B 1 A 0030201 06035504 32313730 F 79 FC 2 ED 02020438 06130255 3634375 A 30 A 02 EA 4 Sent in clear text over network Server must support S/Key Security server supports S/Key 308202 A 8 0500301 B 1 E 170 D 39 C 84 DFBC 0 30820211 310 B 3009 39313032 4 C 7 BD 4 B 1 A 0030201 06035504 32313730 F 79 FC 2 ED 02020438 06130255 3634375 A 30 A 02 EA 4 S/Key passwords Workstation © 2005 Cisco Systems, Inc. All rights reserved. S/Key password (clear text) 19

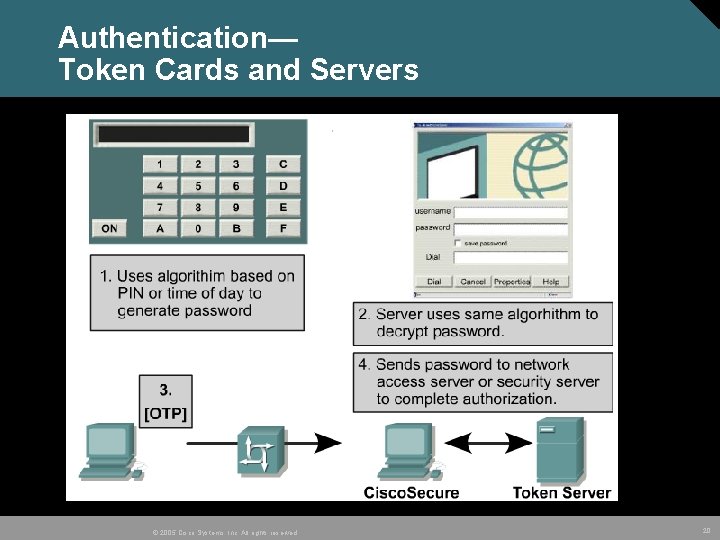
Authentication— Token Cards and Servers Cisco Secure ACS © 2005 Cisco Systems, Inc. All rights reserved. 20

Token Card and Server Methods • Two token card and server methods are used : • Time-based Card contains a key and generates a token or password using a PIN number. Password is loosely synchronized to the token server Server compares the token received with a token generated internally • Challenge-response Card contains a key Server sends a random character string to client Token card computes a cryptographic function using the stored key Results are sent back to the server © 2005 Cisco Systems, Inc. All rights reserved. 21

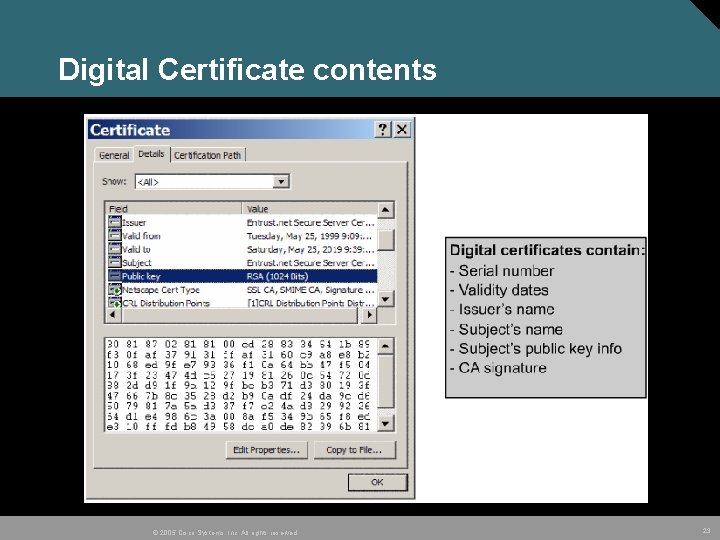
Digital Certificates • Digital signature. Encrypted hash that is appended to a document. Can be used to confirm the identity of the sender and the integrity of the document. • Based on a combination of public key encryption and secure one-way hash function algorithms. © 2005 Cisco Systems, Inc. All rights reserved. 22

Digital Certificate contents © 2005 Cisco Systems, Inc. All rights reserved. 23

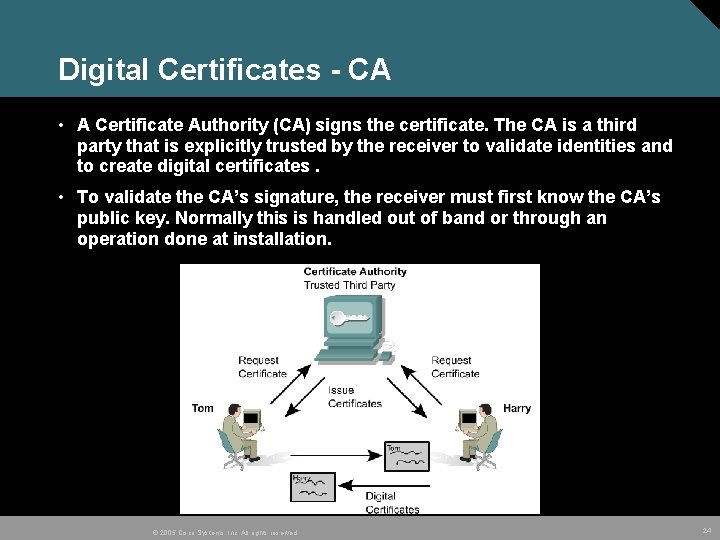
Digital Certificates - CA • A Certificate Authority (CA) signs the certificate. The CA is a third party that is explicitly trusted by the receiver to validate identities and to create digital certificates. • To validate the CA’s signature, the receiver must first know the CA’s public key. Normally this is handled out of band or through an operation done at installation. © 2005 Cisco Systems, Inc. All rights reserved. 24

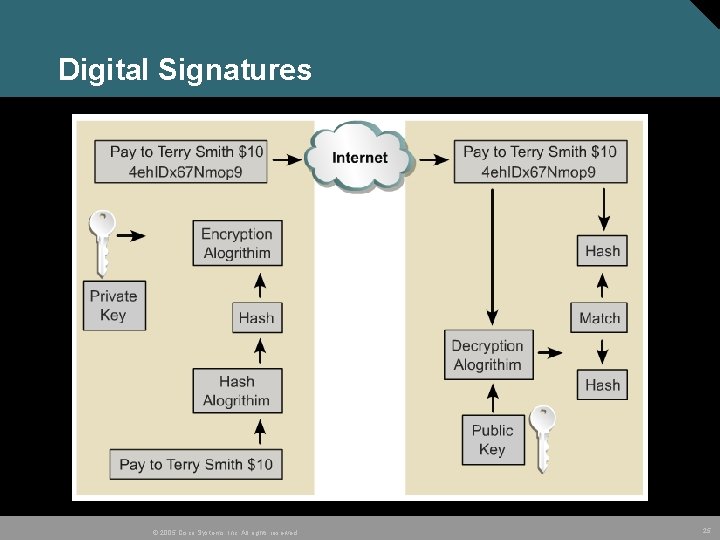
Digital Signatures © 2005 Cisco Systems, Inc. All rights reserved. 25

Digital Signatures • Digital signatures are much more scalable than pre-shared keys. • Without digital signatures and certificates keys must be manually shared new device added to the network requires a configuration change on every other device. • Using digital certificates, each device is enrolled with a CA. When two devices wish to communicate, they exchange certificates and digitally sign data to authenticate each other. • The two common digital signature algorithms are RSA and Directory System Agent (DSA). © 2005 Cisco Systems, Inc. All rights reserved. 26

Biometrics • Measuring a unique physical characteristic about an individual as an identification mechanism. • Most Common - Fingerprint scanning and voice recognition. • Other technologies - Face recognition and signature recognition. • The integration of biometrics in the security policy will provide a solid foundation for developing a secure environment. © 2005 Cisco Systems, Inc. All rights reserved. 27

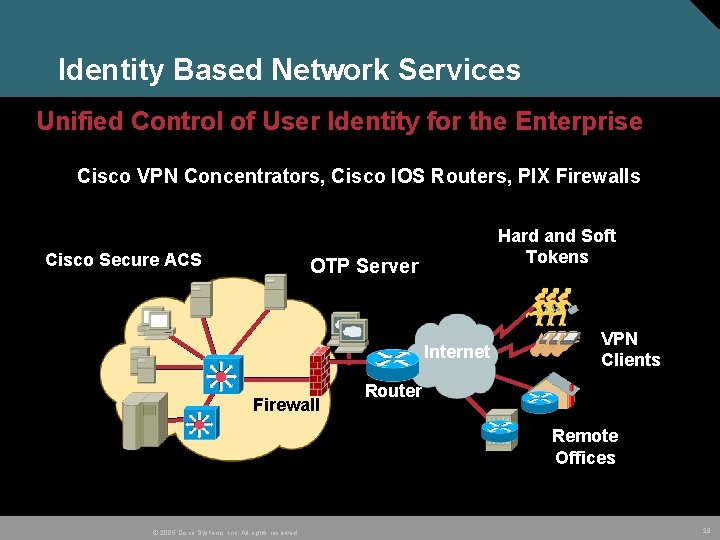
Module 1 – Trust and Identity Technology 4. 3 Identity Based Networking Services (IBNS) © 2005 Cisco Systems, Inc. All rights reserved. 28

Identity Based Network Services Unified Control of User Identity for the Enterprise Cisco VPN Concentrators, Cisco IOS Routers, PIX Firewalls Cisco Secure ACS Hard and Soft Tokens OTP Server Internet Firewall VPN Clients Router Remote Offices © 2005 Cisco Systems, Inc. All rights reserved. 29

Cisco Identity Based Networking Services (IBNS) • Integrated solution combining several Cisco products that offer authentication, access control, and user policies to secure network connectivity and resources. • Features and Benefits Intelligent adaptability for offering greater flexibility and mobility to stratified users – Creating user or group profiles with policies A combination of authentication, access control, and user policies to secure network connectivity and resources User productivity gains and reduced operating costs – Providing security and greater flexibility for wired or wireless network access © 2005 Cisco Systems, Inc. All rights reserved. 30

Cisco Identity Based Networking Services (IBNS) • Solution for increasing the security of physical and logical access to an enterprise network that is built on the IEEE 802. 1 x standard. • IBNS and 802. 1 x are supported on all Cisco switches, Cisco ACS Server, Cisco Aironet Access Points. Access control and policy enforcement at the user and port levels. Associates identified entities with policies • Standards-based implementation of port security • Centrally managed by a RADIUS server (Cisco Secure ACS) © 2005 Cisco Systems, Inc. All rights reserved. 31

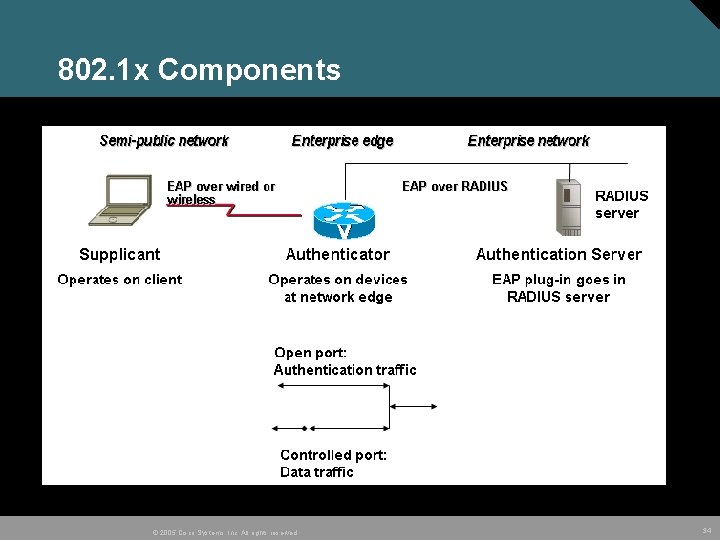
802. 1 x • Standardized framework defined by the IEEE, designed to provide port-based network access. • 802. 1 x authenticates network clients using information unique to the client and with credentials known only to the client. • This service is called port-level authentication It is offered to a single endpoint for a given physical port. © 2005 Cisco Systems, Inc. All rights reserved. 32

802. 1 x Components • Supplicant - Endpoint that is seeking network access • Authenticator - Device to which the supplicant directly connects and through which the supplicant obtains network access permission • Authentication server - Responsible for actually authenticating the supplicant. © 2005 Cisco Systems, Inc. All rights reserved. 33

802. 1 x Components © 2005 Cisco Systems, Inc. All rights reserved. 34

802. 1 x Process • Consists of exchanges of Extensible Authentication Protocol (EAP) messages • Occurs between the supplicant and the authentication server • Authenticator Transparent relay Point of enforcement for any policy the authentication server send back • New link layer protocol, 802. 1 x Between the supplicant and the authenticator. • RADIUS protocol over UDP. Between the supplicant and authentication server © 2005 Cisco Systems, Inc. All rights reserved. 35

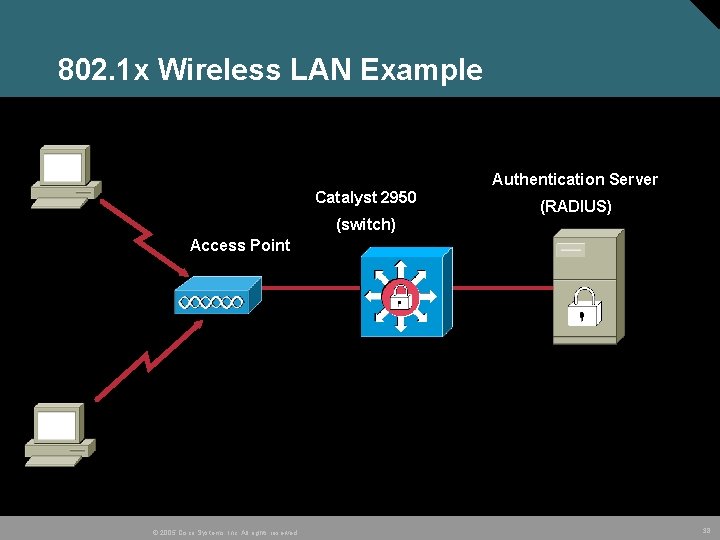
802. 1 x End User (client) Catalyst 2950 (switch) © 2005 Cisco Systems, Inc. All rights reserved. Authentication Server (RADIUS) 36

802. 1 x Benefits Feature Benefit 802. 1 x Authenticator Support Enables interaction between the supplicant component on workstations and application of appropriate policy. MAC Address Authentication Adds support for devices such as IP phones that do not presently include 802. 1 x supplicant support. Default Authorization Policy Permits access for unauthenticated devices to basic network service. Multiple DHCP Pools Authenticated users can be assigned IP addresses from a different IP range than unauthenticated users, allowing network traffic policy application by address range. © 2005 Cisco Systems, Inc. All rights reserved. 37

802. 1 x Wireless LAN Example Authentication Server Catalyst 2950 (RADIUS) (switch) Access Point © 2005 Cisco Systems, Inc. All rights reserved. 38

Module 1 – Trust and Identity Technology 4. 4 Network Admission Control (NAC) © 2005 Cisco Systems, Inc. All rights reserved. 39

NAC • Uses the network infrastructure to enforce security policy compliance on all devices seeking to access network computing resources, thereby limiting damage from viruses and worms. • Provide network access to endpoint devices - Fully compliant with established security policy. • Identify noncompliant devices and deny them access, place them in a quarantined area, or give them restricted access to network resources. • NAC is part of the Cisco Self-Defending Network • Create greater intelligence in the network to automatically identify, prevent, and adapt to security threats • By combining information about endpoint security status with network admission enforcement, NAC enables organizations to dramatically improve the security of their computing © 2005 Cisco Systems, Inc. All rights reserved. 40

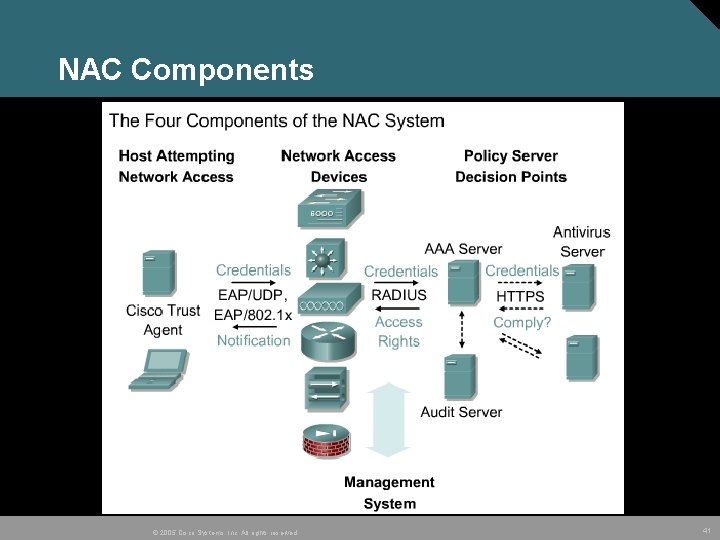
NAC Components © 2005 Cisco Systems, Inc. All rights reserved. 41

NAC Components • Endpoint security software, such as antivirus software, and the Cisco Trust Agent – • collects security state information from software clients, and communicates this information to the connected Cisco network. • Network access devices – Enforce admission control policy. These devices demand host credentials and relay this information to policy servers. • Policy server – Responsible for evaluating the endpoint security information relayed from network devices and for determining the appropriate access policy to apply. • Management system – Provision the appropriate NAC elements and provide monitoring and reporting operational tools. Cisco. Works VPN/Security Management Solution (VMS) Cisco. Works Security Information Management Solution (SIMS ) © 2005 Cisco Systems, Inc. All rights reserved. 42

NAC Phases NAC Phase 1 Cisco routers communicating with the Cisco Trust Agent to gather endpoint security credentials and enforce admission control policy. The Cisco Trust Agent software allows NAC to use existing Cisco network devices, Cisco Security Agent software, and co-sponsor security software, including antivirus software. Router ACLs will restrict the communications between noncompliant hosts and other systems in the network. NAC currently support endpoints running Microsoft Windows NT, XP, and 2000 operating systems. © 2005 Cisco Systems, Inc. All rights reserved. 43

NAC Phases • NAC Phase 2 • Cisco switches will be able to assign noncompliant hosts to quarantine VLAN segments on which only remediation servers reside. • NAC will also support IPSec remote access platforms, such as the VPN 3000 concentrators, and expand support for additional endpoint operating systems. • Future NAC releases will support additional access devices, such as firewalls and wireless access points, and continue to expand the platforms which it will support. © 2005 Cisco Systems, Inc. All rights reserved. 44

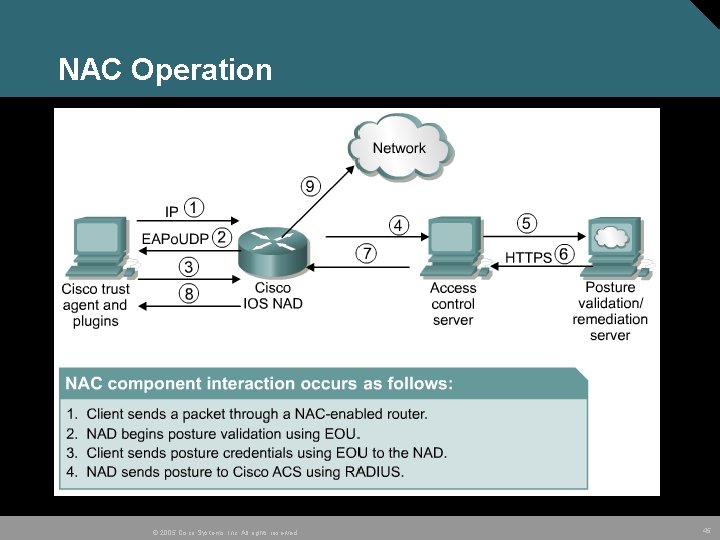
NAC Operation © 2005 Cisco Systems, Inc. All rights reserved. 45

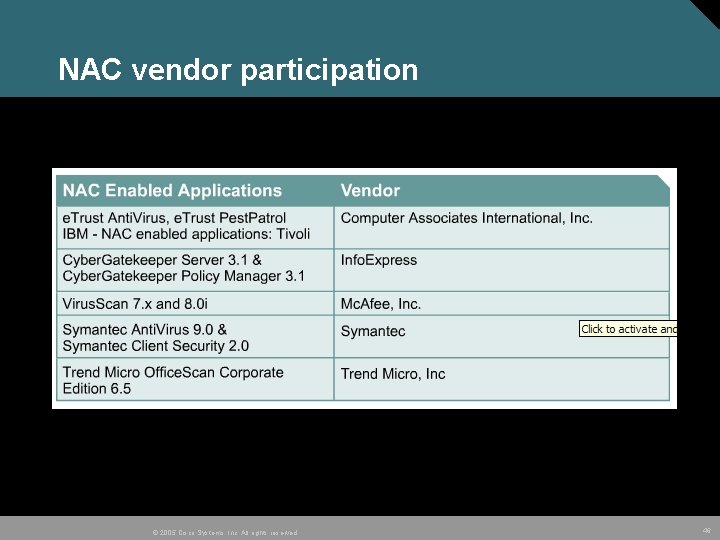
NAC vendor participation © 2005 Cisco Systems, Inc. All rights reserved. 46

© 2005, Cisco Systems, Inc. All rights reserved. 47
 Pearson education inc all rights reserved
Pearson education inc all rights reserved Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Copyright 2010 pearson education inc
Copyright 2010 pearson education inc 2010 pearson education inc
2010 pearson education inc All rights reserved example
All rights reserved example Copyright 2015 all rights reserved
Copyright 2015 all rights reserved All rights reserved sentence
All rights reserved sentence Freesound content licence
Freesound content licence Confidential all rights reserved
Confidential all rights reserved Sentinel controlled repetition
Sentinel controlled repetition Copyright © 2015 all rights reserved
Copyright © 2015 all rights reserved Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Dell all rights reserved copyright 2009
Dell all rights reserved copyright 2009 Warning all rights reserved
Warning all rights reserved Siprop
Siprop All rights reserved formula
All rights reserved formula Warning all rights reserved
Warning all rights reserved Confidential all rights reserved
Confidential all rights reserved Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Copyright © 2018 all rights reserved
Copyright © 2018 all rights reserved Gssllc
Gssllc Confidential all rights reserved
Confidential all rights reserved Confidential all rights reserved
Confidential all rights reserved R rights reserved
R rights reserved Rights reserved
Rights reserved Pearson
Pearson Lida jacob ias
Lida jacob ias Existanxe
Existanxe Child rights act 2005 images
Child rights act 2005 images 2005 pearson prentice hall inc
2005 pearson prentice hall inc 2005 pearson prentice hall inc
2005 pearson prentice hall inc Positive rights vs negative rights
Positive rights vs negative rights What is littoral rights
What is littoral rights Moral duties
Moral duties Legal rights vs moral rights
Legal rights vs moral rights Positive and negative rights
Positive and negative rights Negative rights
Negative rights Negative right
Negative right Negative right
Negative right Name
Name Mobility express とは
Mobility express とは Travel document systems inc
Travel document systems inc Petro vend k800
Petro vend k800 Cyberpower headquarters
Cyberpower headquarters Applied systems inc subsidiaries
Applied systems inc subsidiaries