Cisco Systems Inc All rights reserved 2004 2005


















- Slides: 33

© Cisco Systems, Inc. All rights reserved. © 2004, 2005 Cisco 1 1

Network Security 1 Module 10 – Configure Filtering on a Switch © 2005 Cisco Systems, Inc. All rights reserved. 2

Learning Objectives 10. 1 Introduction to Layer 2 Attacks 10. 2 MAC Address, ARP, and DHCP Vulnerabilities 10. 3 VLAN Vulnerabilities 10. 4 Spanning-Tree Protocol Vulnerabilities © 2005 Cisco Systems, Inc. All rights reserved. 3

Module 10 – Configure Filtering on a Switch 10. 1 Introduction to Layer 2 Attacks © 2005 Cisco Systems, Inc. All rights reserved. 4

Types of Attacks © 2005 Cisco Systems, Inc. All rights reserved. 5

Module 10 – Configure Filtering on a Switch 10. 2 MAC Address, ARP, and DHCP Vulnerabilities © 2005 Cisco Systems, Inc. All rights reserved. 6

CAM Table Overflow Attack © 2005 Cisco Systems, Inc. All rights reserved. 7

Mitigating the CAM Table Overflow Attack © 2005 Cisco Systems, Inc. All rights reserved. 8

Mitigating the CAM Table Overflow Attack © 2005 Cisco Systems, Inc. All rights reserved. 9

MAC Spoofing – Man in the Middle Attacks © 2005 Cisco Systems, Inc. All rights reserved. 10

Mitigating MAC Spoofing Attacks – Cisco IOS © 2005 Cisco Systems, Inc. All rights reserved. 11

ARP Spoofing © 2005 Cisco Systems, Inc. All rights reserved. 12

Mitigating ARP Spoofing with DHCP Snooping © 2005 Cisco Systems, Inc. All rights reserved. 13

Mitigating ARP Spoofing with DHCP Snooping © 2005 Cisco Systems, Inc. All rights reserved. 14

DHCP Starvation © 2005 Cisco Systems, Inc. All rights reserved. 15

Commands to Mitigate DHCP Starvation Attacks © 2005 Cisco Systems, Inc. All rights reserved. 16

Module 10 – Configure Filtering on a Switch 10. 3 VLAN Vulnerabilities © 2005 Cisco Systems, Inc. All rights reserved. 17

Switch Spoofing • Network attacker configures a system to spoof itself as a switch. • Requires Network attacker be capable of emulating either ISL or 802. 1 q along with Dynamic Trunk Protocol (DTP). • Can make a system appear to be a switch with a trunk port. © 2005 Cisco Systems, Inc. All rights reserved. 18

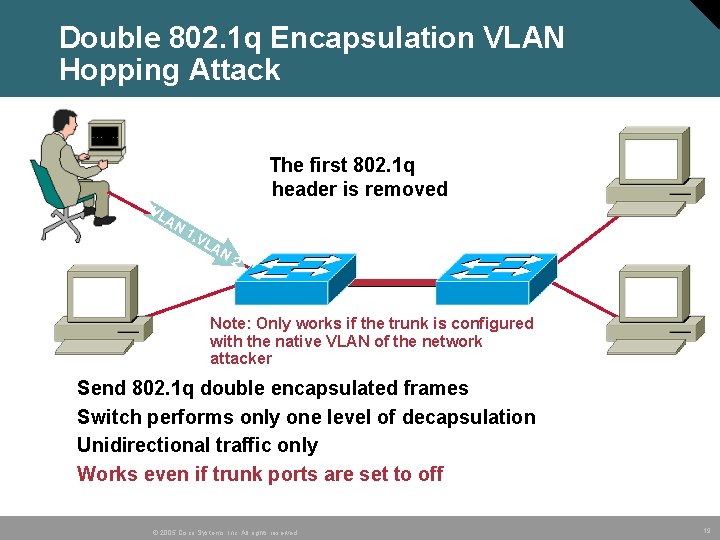
Double 802. 1 q Encapsulation VLAN Hopping Attack The first 802. 1 q header is removed VL AN 1, V LA N 2 Note: Only works if the trunk is configured with the native VLAN of the network attacker • • Send 802. 1 q double encapsulated frames Switch performs only one level of decapsulation Unidirectional traffic only Works even if trunk ports are set to off © 2005 Cisco Systems, Inc. All rights reserved. 19

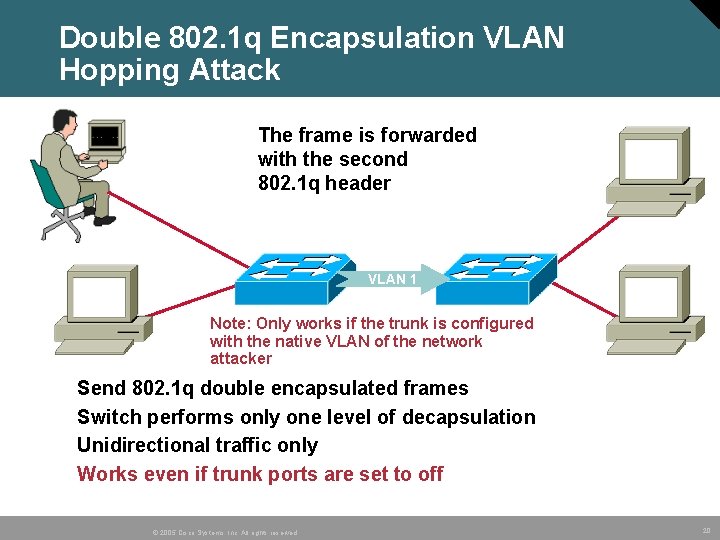
Double 802. 1 q Encapsulation VLAN Hopping Attack The frame is forwarded with the second 802. 1 q header VLAN 1 Note: Only works if the trunk is configured with the native VLAN of the network attacker • • Send 802. 1 q double encapsulated frames Switch performs only one level of decapsulation Unidirectional traffic only Works even if trunk ports are set to off © 2005 Cisco Systems, Inc. All rights reserved. 20

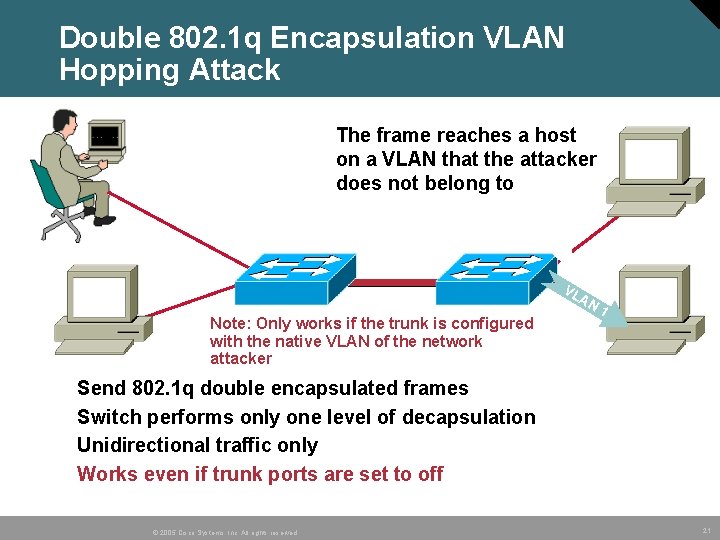
Double 802. 1 q Encapsulation VLAN Hopping Attack The frame reaches a host on a VLAN that the attacker does not belong to VL A N Note: Only works if the trunk is configured with the native VLAN of the network attacker • • 1 Send 802. 1 q double encapsulated frames Switch performs only one level of decapsulation Unidirectional traffic only Works even if trunk ports are set to off © 2005 Cisco Systems, Inc. All rights reserved. 21

Security Best Practices for VLANs and Trunking - Mitigating VLAN hopping attacks • Always use a dedicated VLAN ID for all trunk ports • Disable unused ports and put them in an unused VLAN • Be paranoid – Do not use VLAN 1 for anything • Disable auto-trunking on user facing ports (DTP off) • Explicitly configure trunking on infrastructure ports • Use all tagged mode for the native VLAN on trunks © 2005 Cisco Systems, Inc. All rights reserved. 22

Private VLAN vulnerabilities • Private VLANs are a common mechanism to restrict communications between systems on the same logical IP subnet. • Limit the ports within a VLAN that can communicate with other ports in the same VLAN. • Isolated ports within a VLAN can communicate only with promiscuous ports. • Community ports can communicate only with other members of the same community and promiscuous ports. • One network attack capable of bypassing the network security of private VLANs involves the use of a proxy to bypass access restrictions to a private VLAN. © 2005 Cisco Systems, Inc. All rights reserved. 23

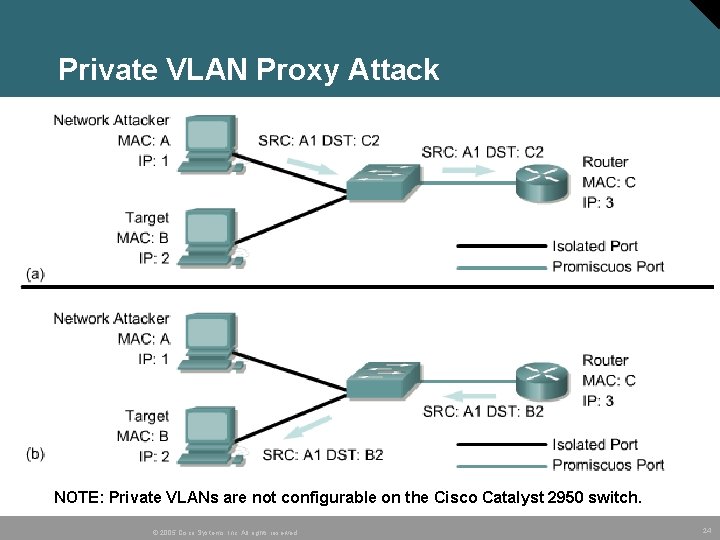
Private VLAN Proxy Attack NOTE: Private VLANs are not configurable on the Cisco Catalyst 2950 switch. © 2005 Cisco Systems, Inc. All rights reserved. 24

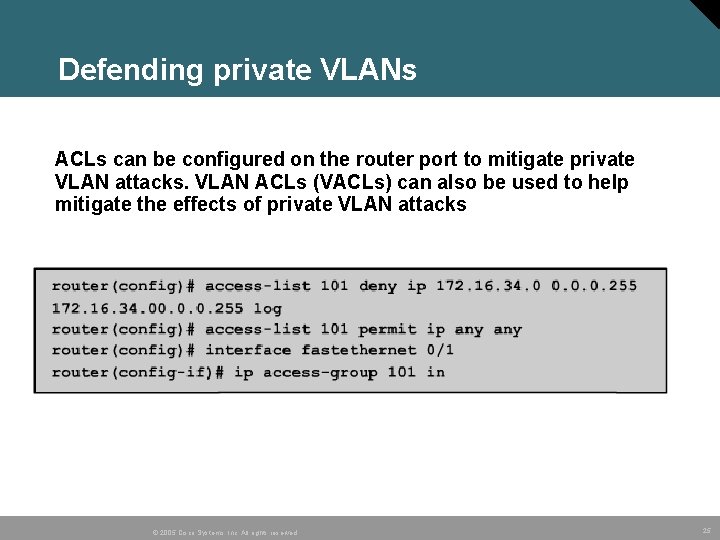
Defending private VLANs • ACLs can be configured on the router port to mitigate private VLAN attacks. VLAN ACLs (VACLs) can also be used to help mitigate the effects of private VLAN attacks © 2005 Cisco Systems, Inc. All rights reserved. 25

Module 10 – Configure Filtering on a Switch 10. 4 Spanning-Tree Vulnerabilities © 2005 Cisco Systems, Inc. All rights reserved. 26

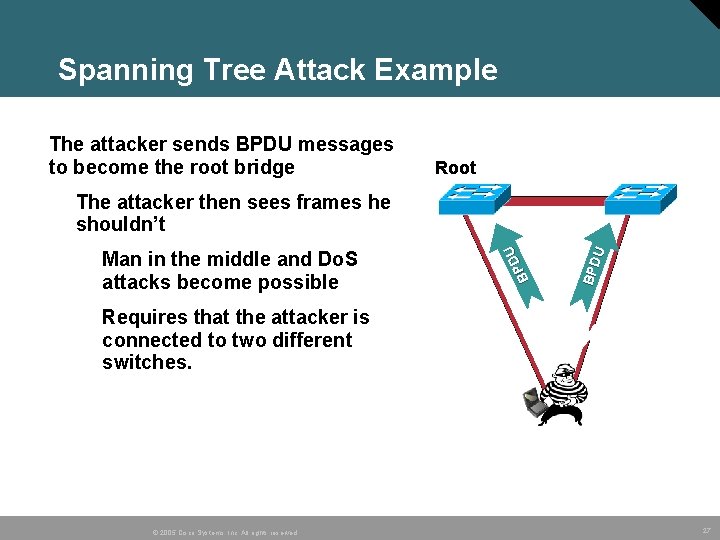
Spanning Tree Attack Example • The attacker sends BPDU messages to become the root bridge Root Access Switches Requires that the attacker is connected to two different switches. © 2005 Cisco Systems, Inc. All rights reserved. BPD U Man in the middle and Do. S attacks become possible DU P B The attacker then sees frames he shouldn’t X Blocked 27

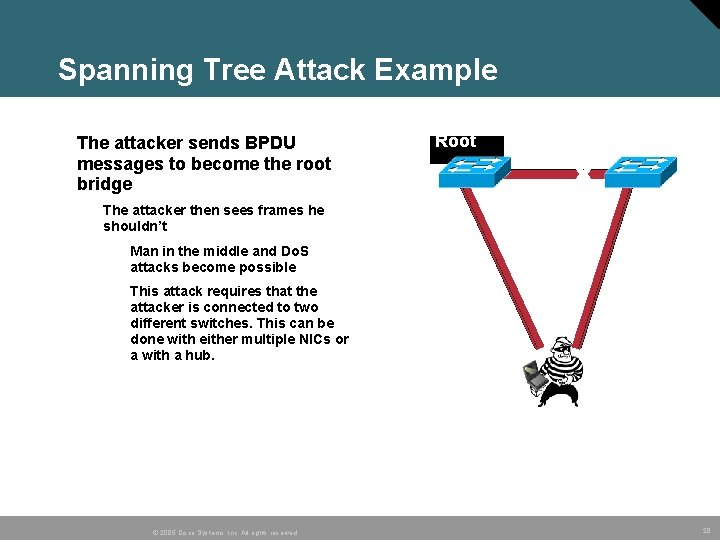
Spanning Tree Attack Example • The attacker sends BPDU messages to become the root bridge Access Switches Root Blocked X The attacker then sees frames he shouldn’t Man in the middle and Do. S attacks become possible This attack requires that the attacker is connected to two different switches. This can be done with either multiple NICs or a with a hub. Root © 2005 Cisco Systems, Inc. All rights reserved. 28

Preventing Spanning-Tree Protocol manipulation • Spanning-Tree Protocol Guard • Enable root guard or loop guard on all the VLANs associated with the selected interface. Root guard restricts which interface is allowed to be the Spanning -Tree root port or the path to the root for the switch. Loop guard prevents alternate or root ports from becoming designated ports when a failure creates a unidirectional link. © 2005 Cisco Systems, Inc. All rights reserved. 29

Preventing Spanning-Tree Protocol manipulation Spanning-Tree Protocol BPDU Guard Globally enable BPDU filtering on Port Fast-enabled ports –Prevents the switch port from sending or receiving BPDUs BPDU guard feature on Port Fast-enabled ports –Puts Port Fast-enabled ports that receive BPDUs in an error-disabled state Port Fast feature on all nontrunking ports. © 2005 Cisco Systems, Inc. All rights reserved. 30

Best Practices © 2005 Cisco Systems, Inc. All rights reserved. 31

Best Practices © 2005 Cisco Systems, Inc. All rights reserved. 32

© 2005, Cisco Systems, Inc. All rights reserved. 33