Cisco Systems Inc All rights reserved 2004 2005





![Standard Numbered Access List Format Router(config)# access-list-number {deny | permit} source [source-wildcard] Austin 2(config)# Standard Numbered Access List Format Router(config)# access-list-number {deny | permit} source [source-wildcard] Austin 2(config)#](https://slidetodoc.com/presentation_image_h/d4c96f16ad43404c55a3a26d9e4d0d06/image-12.jpg)










- Slides: 56

© Cisco Systems, Inc. All rights reserved. © 2004, 2005 Cisco 1 1

Network Security 1 Module 8 – Configure Filtering on a Router © 2005 Cisco Systems, Inc. All rights reserved. 2

Learning Objectives 8. 1 Filtering Technologies 8. 2 Cisco IOS Firewall Context-Based Access Control 8. 3 Configure Cisco IOS Firewall Context-Based Access Control © 2005 Cisco Systems, Inc. All rights reserved. 3

Module 8 – Configure Filtering on a Router 8. 1 Filtering Technologies © 2005 Cisco Systems, Inc. All rights reserved. 4

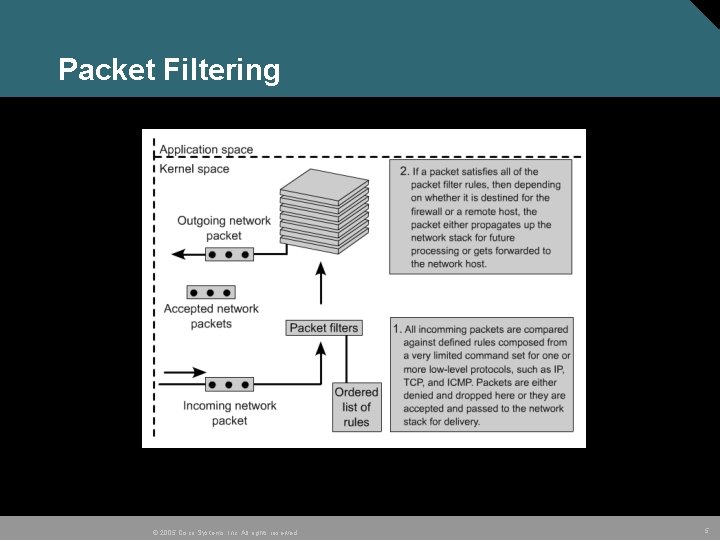
Packet Filtering © 2005 Cisco Systems, Inc. All rights reserved. 5

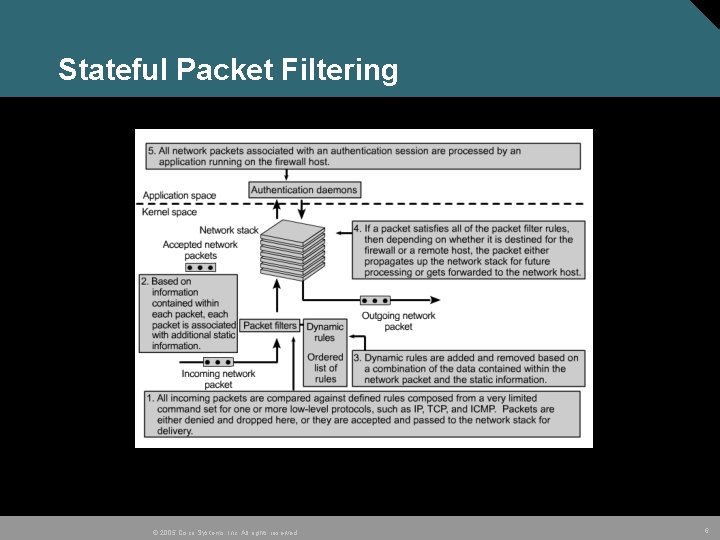
Stateful Packet Filtering © 2005 Cisco Systems, Inc. All rights reserved. 6

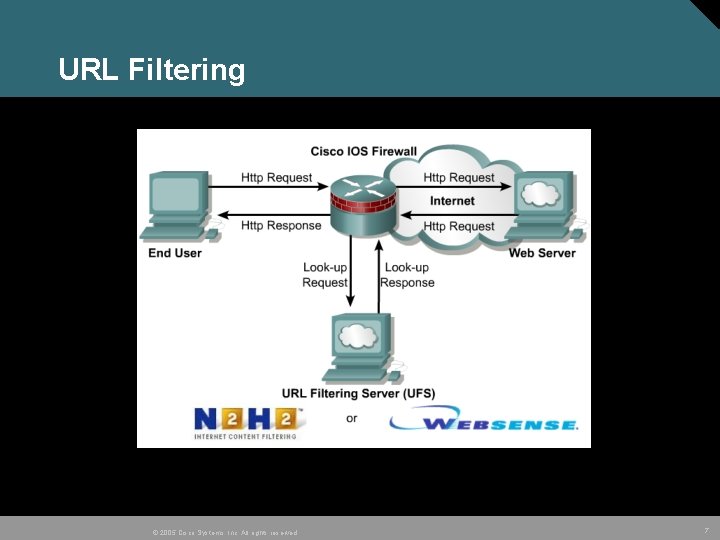
URL Filtering © 2005 Cisco Systems, Inc. All rights reserved. 7

Cisco IOS ACLs Provide traffic filtering by: Source and destination IP addresses Source and destination ports Can be used to implement a filtering firewall Ports are opened permanently to allow traffic, creating a security vulnerability. Do not work with applications that negotiate ports dynamically. © 2005 Cisco Systems, Inc. All rights reserved. 8

Access Control List (ACL) Review © 2005 Cisco Systems, Inc. All rights reserved. 9

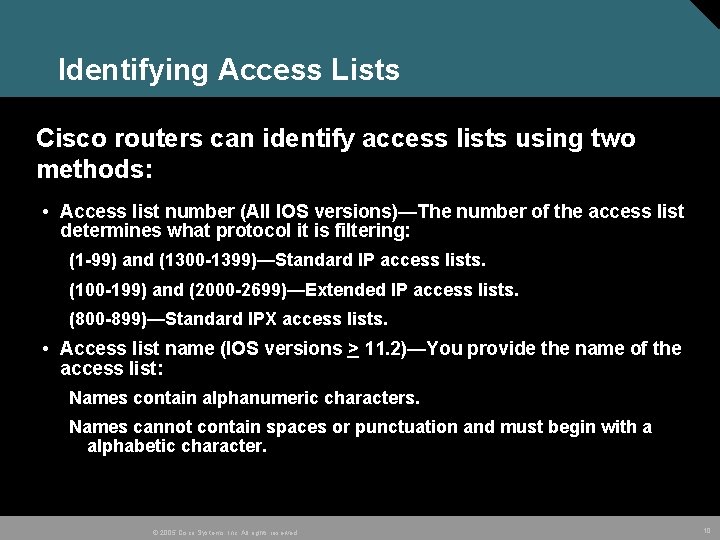
Identifying Access Lists Cisco routers can identify access lists using two methods: • Access list number (All IOS versions)—The number of the access list determines what protocol it is filtering: (1 -99) and (1300 -1399)—Standard IP access lists. (100 -199) and (2000 -2699)—Extended IP access lists. (800 -899)—Standard IPX access lists. • Access list name (IOS versions > 11. 2)—You provide the name of the access list: Names contain alphanumeric characters. Names cannot contain spaces or punctuation and must begin with a alphabetic character. © 2005 Cisco Systems, Inc. All rights reserved. 10

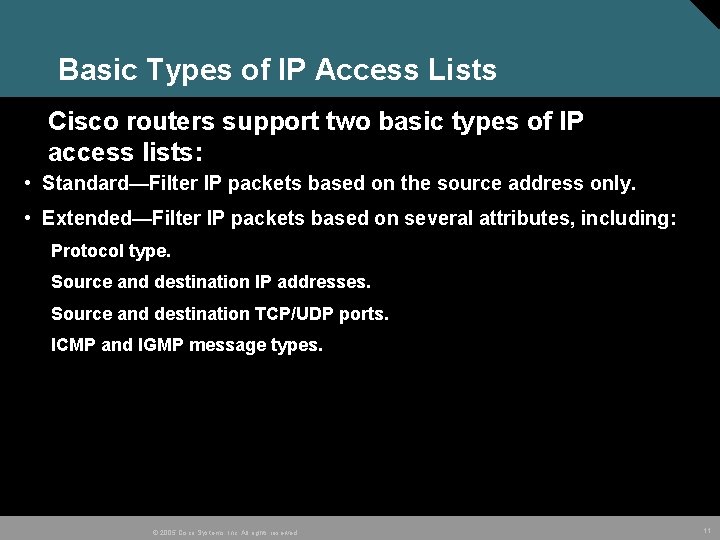
Basic Types of IP Access Lists Cisco routers support two basic types of IP access lists: • Standard—Filter IP packets based on the source address only. • Extended—Filter IP packets based on several attributes, including: Protocol type. Source and destination IP addresses. Source and destination TCP/UDP ports. ICMP and IGMP message types. © 2005 Cisco Systems, Inc. All rights reserved. 11
![Standard Numbered Access List Format Routerconfig accesslistnumber deny permit source sourcewildcard Austin 2config Standard Numbered Access List Format Router(config)# access-list-number {deny | permit} source [source-wildcard] Austin 2(config)#](https://slidetodoc.com/presentation_image_h/d4c96f16ad43404c55a3a26d9e4d0d06/image-12.jpg)
Standard Numbered Access List Format Router(config)# access-list-number {deny | permit} source [source-wildcard] Austin 2(config)# access-list 2 permit 36. 48. 0. 3 Austin 2(config)# access-list 2 deny 36. 48. 0. 0. 255 Austin 2(config)# access-list 2 permit 36. 0. 0. 0 0. 255 Austin 2(config)# interface e 0/1 Austin 2(config-if)# ip access-group 2 in © 2005 Cisco Systems, Inc. All rights reserved. 12

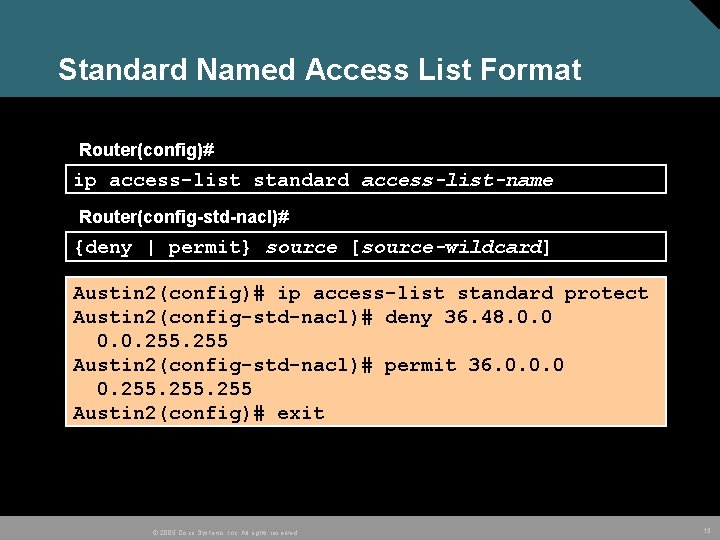
Standard Named Access List Format Router(config)# ip access-list standard access-list-name Router(config-std-nacl)# {deny | permit} source [source-wildcard] Austin 2(config)# ip access-list standard protect Austin 2(config-std-nacl)# deny 36. 48. 0. 0. 255 Austin 2(config-std-nacl)# permit 36. 0. 0. 0 0. 255 Austin 2(config)# exit © 2005 Cisco Systems, Inc. All rights reserved. 13

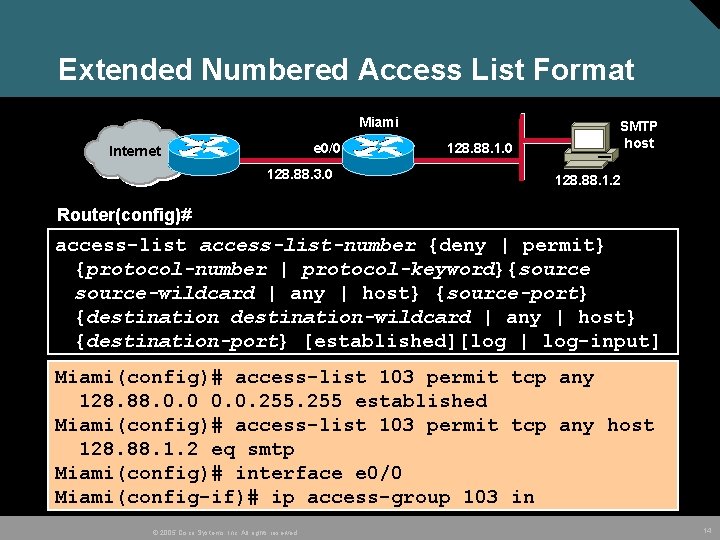
Extended Numbered Access List Format Miami e 0/0 Internet 128. 88. 3. 0 128. 88. 1. 0 SMTP host 128. 88. 1. 2 Router(config)# access-list-number {deny | permit} {protocol-number | protocol-keyword}{source-wildcard | any | host} {source-port} {destination-wildcard | any | host} {destination-port} [established][log | log-input] Miami(config)# access-list 103 permit tcp any 128. 88. 0. 0. 255 established Miami(config)# access-list 103 permit tcp any host 128. 88. 1. 2 eq smtp Miami(config)# interface e 0/0 Miami(config-if)# ip access-group 103 in © 2005 Cisco Systems, Inc. All rights reserved. 14

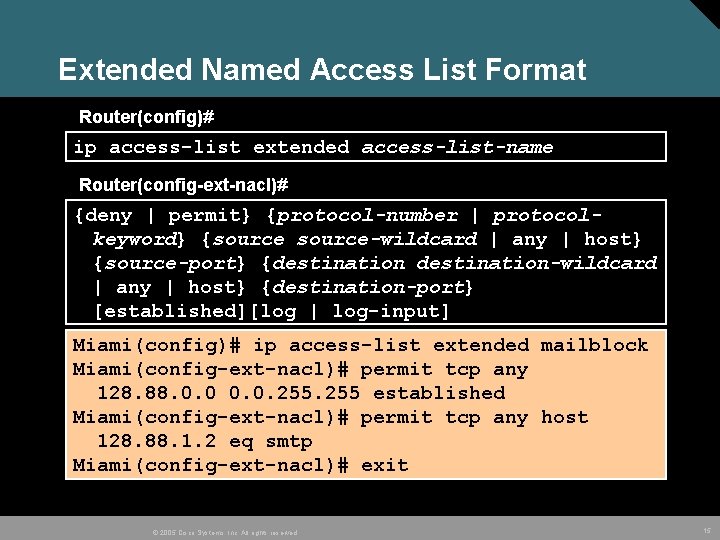
Extended Named Access List Format Router(config)# ip access-list extended access-list-name Router(config-ext-nacl)# {deny | permit} {protocol-number | protocolkeyword} {source-wildcard | any | host} {source-port} {destination-wildcard | any | host} {destination-port} [established][log | log-input] Miami(config)# ip access-list extended mailblock Miami(config-ext-nacl)# permit tcp any 128. 88. 0. 0. 255 established Miami(config-ext-nacl)# permit tcp any host 128. 88. 1. 2 eq smtp Miami(config-ext-nacl)# exit © 2005 Cisco Systems, Inc. All rights reserved. 15

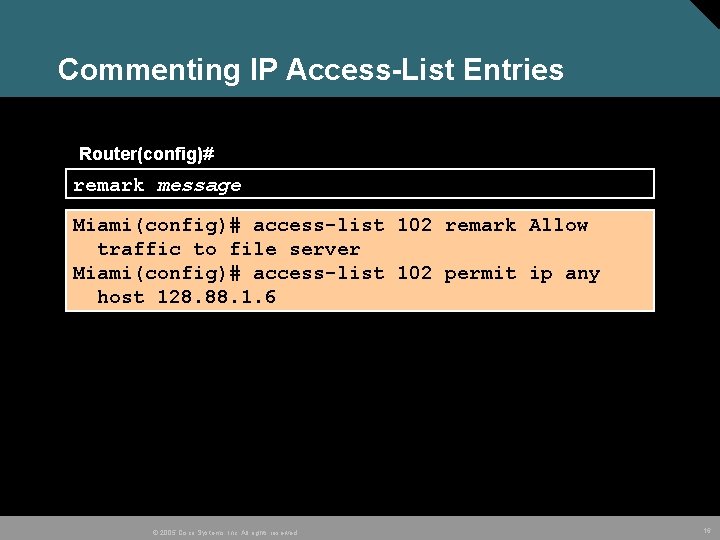
Commenting IP Access-List Entries Router(config)# remark message Miami(config)# access-list 102 remark Allow traffic to file server Miami(config)# access-list 102 permit ip any host 128. 88. 1. 6 © 2005 Cisco Systems, Inc. All rights reserved. 16

Basic Rules for Developing Access Lists Here are some basic rules you should follow when developing access lists: • Rule #1—Write it out! Get a piece of paper and write out what you want this access list to accomplish. This is the time to think about potential problems. • Rule #2—Setup a development system. Allows you to copy and paste statements easily. Allows you to develop a library of access lists. Store the files as ASCII text files. • Rule #3—Apply access list to a router and test. If at all possible, run your access lists in a test environment before placing them into production. © 2005 Cisco Systems, Inc. All rights reserved. 17

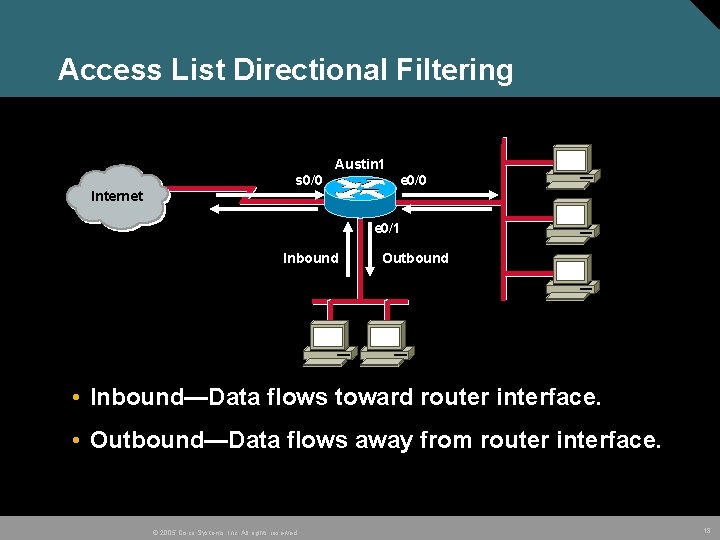
Access List Directional Filtering Austin 1 s 0/0 e 0/0 Internet e 0/1 Inbound Outbound • Inbound—Data flows toward router interface. • Outbound—Data flows away from router interface. © 2005 Cisco Systems, Inc. All rights reserved. 18

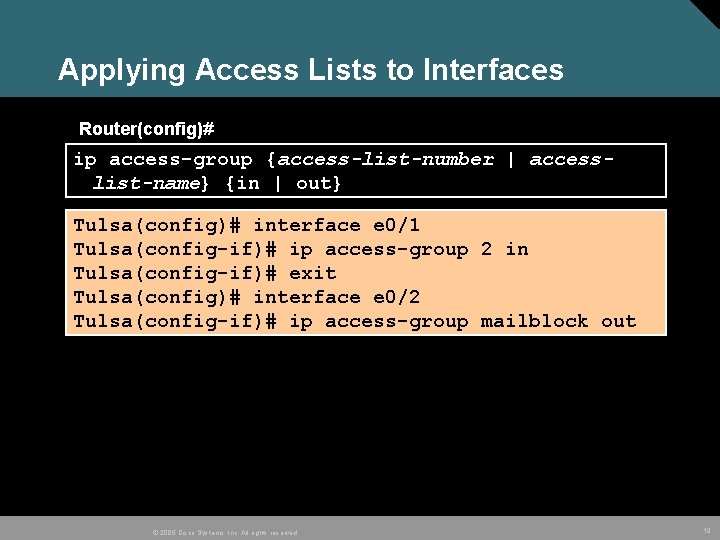
Applying Access Lists to Interfaces Router(config)# ip access-group {access-list-number | accesslist-name} {in | out} Tulsa(config)# interface e 0/1 Tulsa(config-if)# ip access-group 2 in Tulsa(config-if)# exit Tulsa(config)# interface e 0/2 Tulsa(config-if)# ip access-group mailblock out © 2005 Cisco Systems, Inc. All rights reserved. 19

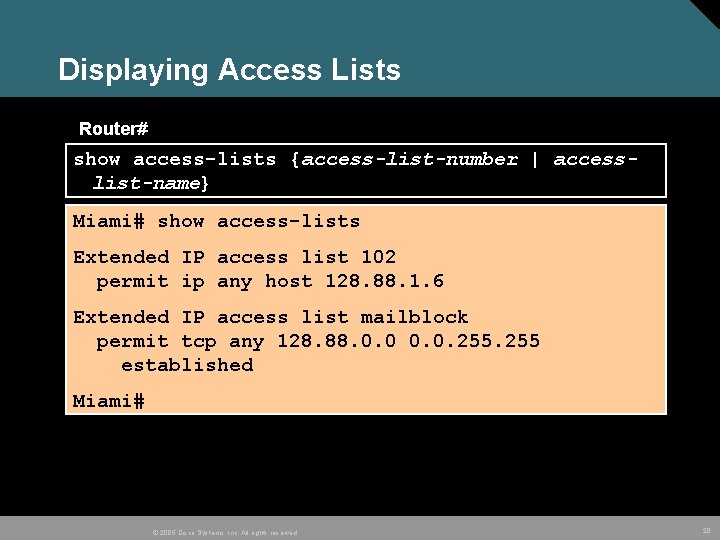
Displaying Access Lists Router# show access-lists {access-list-number | accesslist-name} Miami# show access-lists Extended IP access list 102 permit ip any host 128. 88. 1. 6 Extended IP access list mailblock permit tcp any 128. 88. 0. 0. 255 established Miami# © 2005 Cisco Systems, Inc. All rights reserved. 20

Module 8 – Configure Filtering on a Router 8. 2 Cisco IOS Firewall Context-Based Access Control © 2005 Cisco Systems, Inc. All rights reserved. 21

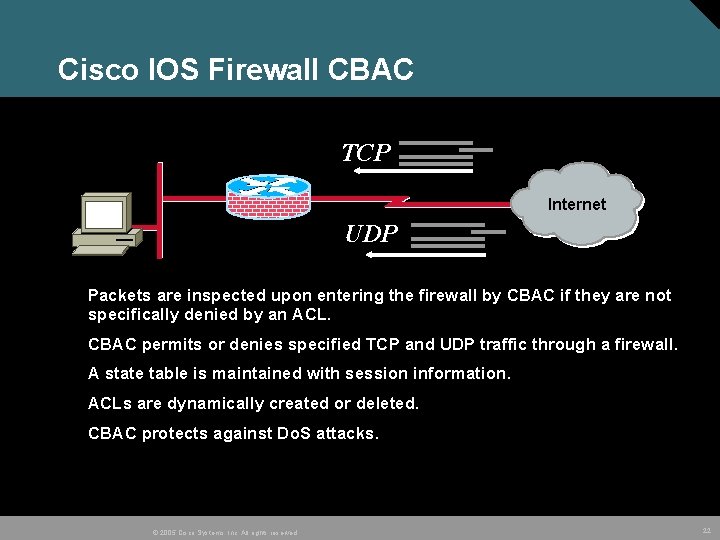
Cisco IOS Firewall CBAC TCP Internet UDP Packets are inspected upon entering the firewall by CBAC if they are not specifically denied by an ACL. CBAC permits or denies specified TCP and UDP traffic through a firewall. A state table is maintained with session information. ACLs are dynamically created or deleted. CBAC protects against Do. S attacks. © 2005 Cisco Systems, Inc. All rights reserved. 22

How CBAC Works © 2005 Cisco Systems, Inc. All rights reserved. 23

CBAC Supported Protocols © 2005 Cisco Systems, Inc. All rights reserved. 24

Alerts and Audit Trails © 2005 Cisco Systems, Inc. All rights reserved. 25

Module 8 – Configure Filtering on a Router 8. 3 Configure Cisco IOS Firewall Context. Based Access Control © 2005 Cisco Systems, Inc. All rights reserved. 26

CBAC Configuration Pick an Interface – Internal or External. Configure IP Access Lists at the interface Set audit trails and alerts. Set global timeouts and thresholds. Define PAM. Define inspection rules. Apply inspection rules and ACLs to interfaces. Test and verify. © 2005 Cisco Systems, Inc. All rights reserved. 27

Enable Audit Trails and Alerts Router(config)# ip inspect audit-trail • Enables the delivery of audit trail messages using Syslog Router(config)# no ip inspect alert-off • Enables real-time alerts Router(config)# © 2005 Cisco Systems, Inc. All rights reserved. logging on logging 10. 0. 0. 3 ip inspect audit-trail no ip inspect alert-off 28

Set global timeouts - TCP SYN and FIN Wait Times © 2005 Cisco Systems, Inc. All rights reserved. 29

Set global timeouts - TCP, UDP, and DNS Idle Times © 2005 Cisco Systems, Inc. All rights reserved. 30

Global Half-Opened Connection Limits © 2005 Cisco Systems, Inc. All rights reserved. 31

Global Half-Opened Connection Limits © 2005 Cisco Systems, Inc. All rights reserved. 32

Half-open connection limits by host © 2005 Cisco Systems, Inc. All rights reserved. 33

Port-to-Application Mapping Overview © 2005 Cisco Systems, Inc. All rights reserved. 34

User-Defined Port Mapping © 2005 Cisco Systems, Inc. All rights reserved. 35

Display PAM Configuration © 2005 Cisco Systems, Inc. All rights reserved. 36

Inspection Rules for Application Protocols © 2005 Cisco Systems, Inc. All rights reserved. 37

Inspection Rules for Java © 2005 Cisco Systems, Inc. All rights reserved. 38

Inspection Rules for RPC Applications © 2005 Cisco Systems, Inc. All rights reserved. 39

Inspection Rules for SMTP Applications © 2005 Cisco Systems, Inc. All rights reserved. 40

Inspection Rules for IP Packet Fragmentation © 2005 Cisco Systems, Inc. All rights reserved. 41

Define inspection rules for ICMP © 2005 Cisco Systems, Inc. All rights reserved. 42

Applying Inspection Rules and ACLs © 2005 Cisco Systems, Inc. All rights reserved. 43

General Rules for Applying Inspection Rules and ACLs Interface where traffic initiates Apply ACL on the inward direction that permits only wanted traffic. Apply rule on the inward direction that inspects wanted traffic. All other interfaces Apply ACL on the inward direction that denies all unwanted traffic. © 2005 Cisco Systems, Inc. All rights reserved. 44

Example—Two Interface Firewall © 2005 Cisco Systems, Inc. All rights reserved. 45

Outbound Traffic © 2005 Cisco Systems, Inc. All rights reserved. 46

Inbound Traffic © 2005 Cisco Systems, Inc. All rights reserved. 47

Example—Three-Interface Firewall © 2005 Cisco Systems, Inc. All rights reserved. 48

Outbound Traffic © 2005 Cisco Systems, Inc. All rights reserved. 49

Inbound Traffic © 2005 Cisco Systems, Inc. All rights reserved. 50

DMZ-Bound Traffic © 2005 Cisco Systems, Inc. All rights reserved. 51

show Commands © 2005 Cisco Systems, Inc. All rights reserved. • 52

debug Commands © 2005 Cisco Systems, Inc. All rights reserved. 53

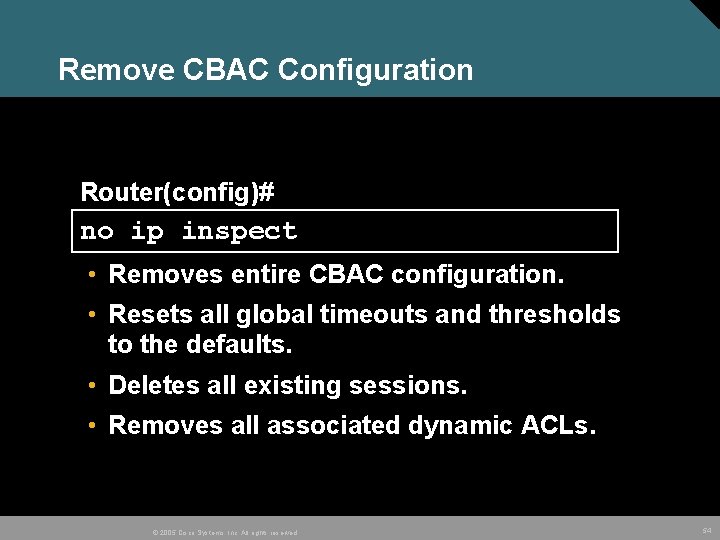
Remove CBAC Configuration Router(config)# no ip inspect • Removes entire CBAC configuration. • Resets all global timeouts and thresholds to the defaults. • Deletes all existing sessions. • Removes all associated dynamic ACLs. © 2005 Cisco Systems, Inc. All rights reserved. 54

Firewall and ACL Main Window © 2005 Cisco Systems, Inc. All rights reserved. 55

© 2005, Cisco Systems, Inc. All rights reserved. 56
 2012 pearson education inc
2012 pearson education inc Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Pearson education inc. all rights reserved
Pearson education inc. all rights reserved Pearson education inc all rights reserved
Pearson education inc all rights reserved 2010 pearson education inc
2010 pearson education inc All rights reserved example
All rights reserved example Copyright 2015 all rights reserved
Copyright 2015 all rights reserved All rights reserved sentence
All rights reserved sentence Freesound content licence
Freesound content licence Confidential all rights reserved
Confidential all rights reserved Sentinel repetition
Sentinel repetition Copyright © 2015 all rights reserved
Copyright © 2015 all rights reserved Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Microsoft corporation. all rights reserved.
Microsoft corporation. all rights reserved. Dell all rights reserved copyright 2009
Dell all rights reserved copyright 2009 Warning all rights reserved
Warning all rights reserved Siprop
Siprop All rights reserved formula
All rights reserved formula Warning all rights reserved
Warning all rights reserved Confidential all rights reserved
Confidential all rights reserved Microsoft corporation. all rights reserved
Microsoft corporation. all rights reserved Copyright © 2018 all rights reserved
Copyright © 2018 all rights reserved Gssllc
Gssllc Confidential all rights reserved
Confidential all rights reserved Airbus deutschland gmbh
Airbus deutschland gmbh R rights reserved
R rights reserved Rights reserved
Rights reserved 2004 pearson education benjamin cummings
2004 pearson education benjamin cummings Child rights act 2005 images
Child rights act 2005 images Child rights act 2005 images
Child rights act 2005 images Child rights act 2005 images
Child rights act 2005 images 2005 pearson prentice hall inc
2005 pearson prentice hall inc 2005 pearson prentice hall inc
2005 pearson prentice hall inc Positive rights and negative rights
Positive rights and negative rights Define littoral rights
Define littoral rights Legal rights and moral rights
Legal rights and moral rights Legal rights and moral rights
Legal rights and moral rights What are negative rights
What are negative rights Negative rights vs positive rights
Negative rights vs positive rights Rosalind hursthouse
Rosalind hursthouse Negative right
Negative right Name all the lines name all the segments name all the rays
Name all the lines name all the segments name all the rays Cisco 1832i mobility express
Cisco 1832i mobility express Travel document systems inc
Travel document systems inc Opw fuel management
Opw fuel management Cyber power systems inc
Cyber power systems inc Applied systems inc subsidiaries
Applied systems inc subsidiaries Uticom
Uticom Global imaging systems inc
Global imaging systems inc Environmental systems research institute inc
Environmental systems research institute inc Multiplex systems inc
Multiplex systems inc Preferred systems inc
Preferred systems inc Control data systems inc
Control data systems inc Educational data systems inc
Educational data systems inc Advanced fluid systems inc
Advanced fluid systems inc Oli systems
Oli systems